
Then a few days ago I began to think of using Windows again. I’m still not sure why. Maybe it is this Covid thing. One feels more and more frustrated and tied down. That feeling finds different pegs to express itself upon. I felt fed up with my Linux version of Zoom, I couldn’t see my students most of the time. I felt irritated with my Linux version of Microsoft Teams, I could see only four faces of my colleagues at a time (on the rare occasions that they switched on their cameras). I couldn’t scan from my mother’s all-in-one printer-cum-scanner. I couldn’t buy a new printer-cum-scanner because the new ones weren’t supported in Linux either.
Maybe Windows would be better. I would be able to see more people, use more devices, feel happier and the sky would be blue again. So I got my university’s ever-helpful IT folks to install Windows and MS Office on my laptop. That was two days ago. And today I am back to Linux.
Why? Well, yes it is true that lots of devices work better with Windows, especially the newest ones. The apple of my eye, the stylus my university gave me to write on a whiteboard during online classes, directly converts my handwriting into computer text on Microsoft OneNote. More features of my mother’s printer-scanner work now. Even the sound on YouTube is better. The sound hardware company Realtek has special device drivers for sound under Windows. Nothing like that for Linux. I can hear it fine there, to be sure, but there is an extra oomph in my headphones under Windows.
The other side is that Windows grabs you with a bear hug. It takes much more space on my hard disk. It eats up a huge amount of RAM. Opening programs takes longer than on my Linux installation. And sometimes they still don’t work. I opened a complicated file made on a previous version of MS Word in the latest MS Word on my laptop. It froze. I tried again, it froze again. Then I tried it on the open source LibreOffice which I had been using on Linux. It sprang onto my screen in a fraction of a second.
Starting and closing Windows can be a pain. It wants to install updates again and again. Even otherwise it takes a long time for my desktop to be usable. And then everything is slower than on Linux. Mine is a relatively new laptop. But this must be torture on an older machine, I thought.
Chris attempts a Lizard intervention and gets sucked into Mike's Green tinted data center paradise.
Plus our thoughts on the Raspberry Pi 400, and Apple's secret weapon.
pi 400, 3d printing, power woes fixed
H2O.ai is driving an open AI movement. Doc Searls and Jonathan Bennet talk with Sri Ambati, the founder of H2O.ai, about the H2O Driverless AI; it is an automatic machine learning platform for the enterprise and helps data scientists across the world in every industry be more productive and get more accurate results. They talk about how H2O.ai responding to COVID-19 challenges with their expertise and new AI Apps that help companies get results with AI. They also discuss the future of AI and the importance of an open AI movement.
I'm announcing the release of the 5.9.4 kernel.
This is only a bugfix for the 5.9.3 kernel release which had some problems with some symlinks for the powerpc selftests. This problem was caused by issues in going from git->patch->quilt->git and things got a bit messed up. To resolve this, I reverted the offending patch and a prerequsite one, and then used 'git cherry-pick' to backport the patches properly, which preserved the links correctly.
Many thanks to Marc Aurèle La Franc and others for helping me notice this and provide some solutions for it.
If you had no issues with these files in 5.9.3, no need to upgrade at this time.
The updated 5.9.y git tree can be found at: git://git.kernel.org/pub/scm/linux/kernel/git/stable/linux-stable.git linux-5.9.y and can be browsed at the normal kernel.org git web browser: https://git.kernel.org/?p=linux/kernel/git/stable/linux-s...
thanks,
greg k-h
Greg Kroah-Hartman has released stable kernel 5.9.4.
Two new technologies, BTF and CO-RE, are paving the way for BPF to become a billion dollar industry. Right now there are many BPF (eBPF) startups building networking, security, and performance products (and more in stealth), yet requiring customers to install LLVM, Clang, and kernel headers – which can consume over 100 Mbytes of storage – to use BPF is an adoption drag. BTF and CO-RE eliminate these dependencies at runtime, not only making BPF more practical for embedded Linux environments, but for adoption everywhere. These technologies are: - BTF: BPF Type Format, which provides struct information to avoid needing Clang and kernel headers. - CO-RE: BPF Compile-Once Run-Everywhere, which allows compiled BPF bytecode to be relocatable, avoiding the need for recompilation by LLVM. Clang and LLVM are still required for compilation, but the result is a lightweight ELF binary that includes the precompiled BPF bytecode and can be run everywhere.
Address-space isolation is the technique of removing a range of memory from one or more address spaces as a way of preventing accidental or malicious access to that memory. Since the disclosure of the Meltdown and Spectre vulnerabilities, the kernel has used one form of address-space isolation to make kernel memory completely inaccessible to user-space processes, for example. There has been a steady level of interest in using similar techniques to protect memory in other contexts; two patches implementing new isolation mechanisms are getting closer to being ready for merging into the mainline kernel.
Linus Torvalds released 5.10-rc1 and closed the 5.10 merge window on October 25; by that time, 13,903 non-merge changesets had been pulled into the mainline repository. Of those, over 6,700 were merged since LWN's summary of the first half of the merge window. A fair number of interesting features found their way into the kernel among those commits; read on to catch up with what's coming in 5.10.
The seccomp() system call allows user space to load one or more (classic) BPF programs to be run whenever the calling process invokes a system call. Those programs can examine (to an extent) the arguments to each call and inform the kernel whether the call should be allowed to proceed or not. This feature is used in a number of containerization solutions (and beyond) as a way of reducing the kernel's attack surface. In some situations, though, using seccomp() can result in a significant performance reduction. There are currently two patch sets in circulation that are aimed at reducing the overhead of seccomp() for one common use case. The argument-inspection feature of seccomp() is useful in a number of settings; it can, for example, block a write() call to any file descriptor other than the standard output. But many real-world use cases do not take advantage of this capability; instead, they make decisions based only on which system call is being invoked while paying no attention to the arguments to those calls. It turns out that the BPF mechanism is far from optimal for this case, which must be implemented as a long series of comparisons against the system-call number. The overhead of these comparisons can be reduced by using smarter algorithms (checking for the most commonly used system calls first, for example), but there are limits to how fast it can be. This overhead makes every system call slower.
Much of this work is wasted. If a seccomp() configuration of this type allows read() once, it will allow it every time, but the kernel must work it out the hard way each time regardless. If there were some way of knowing that a given seccomp() filter program allows or denies specific system calls without looking at their arguments, it would be possible to implement those decisions much more quickly.
While the Linux 5.10 merge window passed a week and a half ago, similar to the Navi Blockchain SKU being added as a "fix", the Green Sardine enablement is also being submitted as a fix for this current kernel version.
At the start of October AMD sent out Linux driver bits for Green Sardine as a forthcoming APU platform. The Green Sardine hardware enablement from the graphics perspective basically has the AMDGPU driver follow the Renoir/Vega code paths but with different firmware files and other minor alterations. Green Sardine might be the Linux codename for the "Cezanne" Ryzen 5000 series APUs.
Stretchly is a helpful program that reminds you to periodically take short breaks when you are working on the computer. According to the application, "Taking regular breaks when using a computer is scientifically proven to be important for your physical and mental well-being.", and Stretchly is specifically designed to help you take these breaks. By default, it will remind you to take a short 20 second break every 10 minutes, and a longer 5 minute break every 30 minutes.
When you start Stretchly, it will run in the system tray. Clicking on the icon will open up a menu from which you can quickly check how long it will be until the next break starts, and also easily skip to the next long or mini breaks, or pause all breaks for a certain amount of time.
BpyTOP is another Linux command-line utility for resource monitoring among many other utilities like a top, Htop, Bashtop, etc. bashtop users can expect similar features in bpytop since bpytop is ported from bashtop and completely written in Python. Bpytop is available for various linux distributions and macOS.
MongoDB has mongod (Mongo Deamon) to run an instance of MongoDB on your computer or server.
We generally use the Linux operating system on Desktop or Laptop because on Android it is not stable to use GUI-based Linux OS, however, the command line will be. Yes, we can set up Kali on Android, which is popular and known for its security testing tools.
So, let’s start with the tutorial, and yes you don’t need to do any modification in your Android OS that would temper the warranty of your phone.
I haven't been to some of my favorite sites for a while, having other events that were keeping me busy - you know, Life. However, I happened to go to one of my favorite GIMP sites the other day - GIMP Learn. I know I can always find something new to learn, and that day was no exception. One of the most talented people on the site, a lady named Pat625, had posted a fine tutorial a while back, and I was just now able to go through it. The actual tutorial is here, and it is wonderful, so I thought I'd share it with you.
Create a new file, 1,000 px X 1,000 px, with a white background. Using the guides you can pull from the left-side and top rulers, place them at 500 px. If you will check the bar at the bottom of your window, you will see "Add Guide" and it will show you when your guide is at 500 px. Your canvas will look like this:
Today we are looking at how to install Netbeans 12 on a Chromebook. Please follow the video/audio guide as a tutorial where we explain the process step by step and use the commands below.
If you have any questions, please contact us via a YouTube comment and we would be happy to assist you!
Today we are looking at how to install FreeCAD in Ubuntu 20.04. The process is rather easy as you can see in the video tutorial. A person opens a terminal and runs the command below in it. Enjoy!
In this video, we are looking at how to install FreeCAD on Ubuntu 20.04.
Server security is the topmost priority for every system administrator. Besides having third-party security tools like Firewall, DDoS protection, etc. it is extremely important to keep every piece of code up-to-date on your production server.
When your application is in production, upgrading it is riskier. If your server is powered by Linux, Linux distributions keep releasing new versions every now and then. Each major release contains bug fixes, security updates, and new tools.
Upgrading a production server without any preparation is a big mistake. An unprepared upgrade can cause permanent data loss, poor server performance, and customer loss. In this article, I will list some important steps to take before initiating a server upgrade.
Do you wish to insert content (such as advertisement or a link) right in the middle of the Jekyll page? We can do that by using the content as an array and a forloop. Here is how.
The game mechanics resemble the first Castlevania, but much more difficult. And, despite all its positive aspects, it seems that the game's creators put an insane difficulty just to artificially lengthen its duration.
Other than that, the mechanics are bad. The character does an automatic animation when performing a sequence of three sword attacks. Now, if you need to jump, it won't happen, because the character will be locked in the animation sequence. And, as the game is very dynamic, it will kill Bathorin many times. But, as he already died, it doesn't stop the game from continuing. The character just respawns at the nearest check-point. Yes, the game has this flaw. There is no way to save anywhere you want, but only at check-points, which can be very frustrating, depending on the stage you are in.
Other than that, when striking with the sword, the character advances one step for each sequence of three sword hits. In abyss edges, or with nearby traps (and the game has many), this can kill the character easily.
The fantastic tactics game from Mimimi Games is finished, with the final Money for the Vultures now available for Desperados III allowing you visit a location from previous games.
Desperados III: Money for the Vultures - Part 3: Once More With Feeling (what a mouthful!) brings the Season Pass to a conclusion and leads the gang back to "Eagles Nest", the legendary bandit fortress in the middle of the desert. This area, they say, is bigger and looks better than it ever has in Desperados and a fitting location to end Money for the Vultures. Looks like a whole lot of fun to sneak through.
While Unity itself has long supported producing Linux builds of games and applications built with it, the actual Editor for Linux is still not fully supported - but that will change.
To be clear, there is a Linux version of the Unity Editor right now and that's been a thing since 2015 in experimental form. Back in April 2019 they announced that the Linux Editor would be moving from experimental into preview, meaning it was on the road to a full release. Later in May 2019, Unity then actually properly announced the Unity Editor for Linux with a planned release date with Unity 2019.3.
Sadly it didn't happen when expected, it was delayed with no exact date other than 2020 which they're now announcing again they're not going to hit. In a forum post going into more detail, the good news is that Unity appear to be firmly committed to bringing the Unity Editor for Linux into official status.
Do you ever get that impulse to buy that new, shiny electronic device on a whim? Just get in the car and drive the fifteen or thirty minutes to get to Walmart or Best Buy and buy it, without waiting the two or three days when ordering online?
You know where this is going. After learning that Sony’s new DualSense controller for the PlayStation 5 has been released prior to the console itself, and discovering that it’s compatible with devices other than Sony’s own, I immediately went to my local Target store after getting an oil change for my car.
Heh… the amount of time that you spend at the electronics department, viewing every sort of gadget that the store has. It’s everybody’s little toy store. That shot of endorphins that spike to your head after buying the device, taking it home, and unboxing it for the first time. And taking pictures of it for the sake of review, like this one.
In the last few months, we witnessed the massive release of the two most popular Linux desktop environments, GNOME 3.38, and KDE Plasma 5.20.
If you’re specifically waiting for the new release of a lightweight desktop like Xfce 4.16, you should check out one of the best contenders LXQt, which has just launched a new version, LXQt 0.16.0.
It's time to crown the best of the best Linux desktop distributions for 2020. I'm going to say this up front: Chances are pretty good your distribution isn't on this list. If not, there's no need to fret. The very fact that you are using Linux on the desktop should be reward enough. Why? Because you are using an operating system that is superior in many ways. It may not be perfect (no operating system is), but it's still Linux, which means you're working with a desktop platform that's flexible, reliable, and fun to use.
In the end, I have to claim a few of the vast number of distributions to be somehow above the rest. With the exception of a couple of distributions, this is never an easy task. And this year, it's even harder because some of the usual candidates have fallen by the wayside. But who knows what next year will bring? Besides, the one thing you can count on with the Linux community is that they are always working hard to develop something new and impressive.
Such is the case with this year's candidates. With that, let's get on with the list. '
If you’ve been keeping up with the latest Linux distributions, you must have noticed that 32-bit support has been dropped from most of the popular Linux distributions. Arch Linux, Ubuntu, Fedora, everyone has dropped the support for this older architecture.
But, what if you have vintage hardware with you that still needs to be revived or you want to make use of it for something? Fret not, there are still a few options left to choose from for your 32-bit system.
In this article, I’ve tried to compile some of the best Linux distributions that will keep on supporting 32-bit platform for next few years.
Contrary to popular belief, Apple did not invent the concept of the app store; another US software developer came up with a working equivalent as far back as 2001.
Lindows (now known as Linspire after a legal battle with Microsoft), had a feature called Click ‘n’ Run - or CNR (not as catchy) - which allowed users to click one button to install an application.
Lindows was a Linux-based distribution that wanted to encourage its users to embrace a subscription model, which included handing over personal details. But it was too far ahead of its time, with infrastructures like CDN and payment gateways still in their infancy.
I live in Denmark on Zealand, in the western part, not far from the sea.
We live in an old half-timbered house from 1776. I have spent the last seven years renovating it completely, so we do not have to think about repairs in the future.
The weather in Denmark has changed a lot in the last 20 years, as has the rest of the weather in the rest of the world. We have just had 10 days with 31-32oC (87.8-89.6oF) degree heat. That is a lot in Denmark, when the average daytime temperature is 18.4oC (65oF) in August.
[...]
My interest in Linux started in 1998. There was an article in a Danish newspaper.
It sounded interesting, but I forgot about it until there was a CD with Red Hat 5.2 in a Danish IT magazine in February 1999.
I used Windows 95 at that time. I got a larger hard drive in my old Olivetti computer, and installed it as a dual boot with Windows 95. I was immediately sold.
In March 1999, I deleted Windows, and installed openSUSE 6.0. I have only used Linux since. Why did I switch to Linux? What interested me was that it was free and open, and you could do whatever you wanted with it. I have tried further 14 other distributions down the road.
The fact that PCLinuxOS is a rolling release is a big plus. PCLinuxOS is rock solid stable, with tons of packages available in the repos. If you want a solid, stable, dependable Linux operating system, then you cannot go wrong with this distro. The forums are full of helpful members that will help with all sorts of issues. This is the way Linux should be. It is the distro for me, and here I intend to stay.
What specific equipment do you currently use with PCLinuxOS? My desktop is an Intel Core i7-9700 4.7GHz 8-Core CPU. My laptop is a Lenovo ThinkPad L540 Processor: 2.6 GHz, Intel(R) Core(TM) i5-4300M CPU @ 2.60GHz.
My wife and daughter have a Lenovo ThinkPad T400 IntelCore2Duo processor P8400 (2.26GHz), 3-MBL2 cache. All computers with PCLinuxOS MATE, so we call ourselves the Linux family.
Thanks to profiling and classification, social networks have become giant echo chambers, real bubbles that keep people away instead of bringing them closer, and create an illusion about the perceived reality that is very powerful and real. I already had the opportunity, using YouTube, to access a channel of extremist ideas, in political terms, with a YouTuber who had a strong speech against his opponents, and often insulted people who did not share his opinion. I will not mention the channel or YouTuber, since he does not deserve advertising or any other means to spread his extremist views. And, I accessed his channel a long time ago when it was a small channel, and when videos from his channel appeared on my timeline again, I chose to ignore them. It was content that is not important to me.
Okay, his videos never appeared on my timeline again. Some time passed, about two years, more or less, and I was curious: Did that guy's channel close? No more videos of him ever appeared on my timeline, and I thought he had shut down his channel and given up. I looked for the channel, searching in YouTube, and there was his channel, firm and strong, with over 100 thousand subscribers. And I was speechless: Yeah, being rude and spreading hate speech is worth it. Gee, I'm doing it wrong, with my innocent Linux videos. I should speak ill of others and gain followers.
However, this classification that applications make of the public transformed the internet into echo chambers, which separated people by their tendencies, their profiles. The danger of that? It was simple: minorities think they are majorities, think that everyone thinks the same way (because the algorithm hides different ideas) and creates a distorted view of reality. Thus, groups of people on social networks cannot be analyzed as majorities, or minorities. In fact, it's not even possible to know its size, since the algorithms make it difficult for people with different characteristics to interact, creating bubbles and filling these bubbles with certain groups, each classified in a different way, which is not transparent to its users.
That was the lesson that my wife and I received early in October. The person delivering that message? My seven year old son, Ryan.
On an otherwise calm October 11, that "calm" was shattered when Ryan's grandmother -- my 78 year old mother -- fell at her home next door while cooking dinner, hit her head on the kitchen cabinets, and was unconscious. My 15 year old niece ran over to our house, crying and telling my wife that Grandma had fallen, and there was blood everywhere, and she wasn't waking up.
Now, my wife and I have the same occupation. We're both respiratory therapists, just at different hospitals. We are quite accustomed to dealing with emergency situations. As for me ... I was at work at a small hospital 40 miles away. My wife was at home, with the kids (Ryan and Lexi), cleaning the house.
Quickly, my wife asked if anyone had called 911, as she quickly put on some different clothes other than the ragged ones she was wearing to clean the house. Hearing this, and unbeknownst to anyone else, Ryan picked up the phone and called 911 himself, for his grandmother.
Fedora 33 was just released at the end of October but already a number of change proposals are building up for Fedora 34 due out next spring.
Fedora 34 has already seen some proposals around security enhancements, a 64-bit ARM KDE Plasma desktop spin, further compressing the install media, switching the KDE spin to using Wayland by default, and more. Over the past day there have been some additional change proposals published.
The Council is putting out a new process to allow community members to publish videos on the official Fedora Project YouTube Channel. The objective behind this proposal is both to encourage more people to contribute and to bring more attention to the channel. The proposal has three parts: the content, the format, the process.
I was assigned 6.25 hours of work by Freexian's Debian LTS initiative and carried over 17.5 hours from earlier months. I worked 11.5 hours this month and returned 7.75 hours to the pool, so I will carry over 4.5 hours to December.
[...]
I updated linux (4.9 kernel) to include upstream stable fixes, and issued DLA-2420-1. This resulted in a regression on some Xen PV environments. Ian Jackson identified the upstream fix for this, which had not yet been applied to all the stable branches that needed it. I made a further update with just that fix, and issued DLA-2420-2.
The developers of the Ubuntu Touch operating system for smartphones and tablets have released Ubuntu Touch OTA-14. Coming just a little over a month after OTA-13, the biggest changes include support for installing the Linux-based operating system on additional hardware, including mobile devices running Android 9.
Among other things, that means you can now install Ubuntu Touch on Google Nexus 6P or Xiaomi Redmi 4X smartphones or a Sony Xperia Z4 tablet.
It also means that when the Volla Phone ships, the Ubuntu version of that smartphone should be fairly well supported.
Ubuntu 21.04 daily builds are now available for download, kickstarting official development on the release that devs have dubbed the ‘Hirsute Hippo’.
A new live .ISO will be produced each day between now and mid April, which is when the final stable release of Ubuntu 21.04 is due for release.
There’s not an awful lot of “new” stuff to see in the images at the time of writing but that will change as development kicks into gear, new apps are packaged, and upstream development trickles on down.
Many testers install an early daily build and update it every day until the final, stable release arrives — though naturally there’s high chance of hitting bugs, breakages and other bumps in the road during the ride to release town!
On the 22nd of October, the 20.10 release was launched, an Ubuntu Desktop image optimised for the Raspberry Pi. It brings together Ubuntu and Raspberry Pi for educators, inventors and entrepreneurs, bringing the world’s most open platform to the world’s most accessible hardware.
The Librem 5 has been under development for several years. It was one of the first modern Linux smartphones to be announced, and Purism has been one of the major forces behind the modern surge in phone-friendly Linux operating systems.
The smartphone will be able to support a variety of open source operating systems, but it will ship with a mobile version of Purism’s PureOS that features the phosh (phone shell) user interface designed by Purism to make the OS touch-friendly.
Since phosh is open source, it’s also been adopted as one of the optional user interfaces for other smartphone Linux projects such as postmarketOS and Manjaro Mobile. If you buy a PinePhone Community Edition phone with either of those operating systems pre-installed, phosh is the default user interface.
But the Librem 5 is a bit more powerful than the PinePhone. It has a faster processor and a larger battery. It also has a much higher price tag – the PinePhone sells for $150 to $200, while the Librem 5 costs $749.
Raspberry Pi has been selling tiny, inexpensive computers and accessories since 2012. But while Raspberry Pi hardware has become popular with enthusiasts and home users, the organization’s single-board computers were originally targeted at students, educators, and makers.
The new Raspberry Pi 400 is something different: a full-fledged computer stuffed inside a keyboard. It’s basically a modern take on the Commodore 64 and similar personal computers from decades past.
A key difference? The Raspberry Pi 400 is incredibly affordable, with prices starting at just $70.
Infineon’s “Optiga Trust-M eval kit” is a Pi add-on for evaluating the ZigBee Alliance’s Connected Home over IP home automation standard. The eval kit is built around a Trust-M Shield2Go board equipped with the EAL6+-compliant Trust-M security chip.
Infineon Technologies, which is primarily known in these pages for its widely used Optiga TPM security chips, has announced a Raspberry Pi add-on equipped with a different security technology called Optiga Trust. Specifically it integrates an Optiga Trust-M Shield2Go board equipped with its Optiga Trust-M security chip, which complies with the Common Criteria Certified EAL6+ (high) spec. Although the Optiga Trust-M eval kit can be used to evaluate the Trust-M technology, which provides anchor of trust security technology for connecting IoT devices to the cloud, it’s primary purpose is to evaluate the ZigBee Alliance’s Connected Home over IP automation standard.
DM&P Vortex86EX2 is a dual-core x86 processor that supports legacy ISA and PCI interfaces, and designed in a way that makes it capable of running two OS independently, easy with its own BIOS, without the need for virtualization, nor a hypervisor.
At the time, we also covered the Vortex86EX2 evaluation board from the company, but the first commercial product that has come to my attention is ICOP VEX2-6415 Vortex86EX2 SBC designed for automation and IoT, and which the company says support “Windows Embedded Compact 7, Windows Embedded Compact 6, various of (sic) Linux distribution, QNX, and even the legacy but still popular DOS”.
The Librem 5 can now change from factors easily. Connect it to a powered USB-C dock to enable desktop mode. Or connect it to a laptop dock to turn your phone into a fully working laptop.
The software is quickly improving around connection and detachment of the docks. Settings has a new section to configure any attached displays.
You’ll also find a new dock toggle in the top dropdown. This allows you to drag around windows freely as well as disables the onscreen keyboard.
TenFourFox Feature Parity Release 29 beta 1 is now available (downloads, hashes, release notes). Raphaël's JavaScript toggle is back in the Tools menu but actually OlgaTPark gets most of the credit this release for some important backports from mainline Firefox, including fixes to DOM fetch which should improve a number of sites and adding a key combination (Command-Option-R in the default en-US locale) to toggle Reader View. These features require new locale strings, so expect new language packs with this release (tip of the hat to Chris T who maintains them). The usual bug and security fixes apply as well. FPR29 will come out parallel with Firefox 78.5/83 on or about November 17.
Twenty years ago, in 2000, the OpenOffice (OO.org) source code was open sourced by Sun Microsystems. I remember it well. Back then, in my naivete as a Windows user, I was excited about the announcement. It wasn't as a contributor or programmer, but I was excited about the growth potential for an office suite other than Microsoft Office, which has/had always been consistently priced out of my reach or budget.
In those days, OpenOffice was managed and developed by Sun Microsystems. This was after Sun purchased StarOffice from its German owners in 1999. Prior to that, StarOffice originated as StarWriter in 1985.
THEN came along Microsoft's introduction of the OOXML (Office Open XML) document format, which especially created havoc for users of anything other than Microsoft Office. We see them today, represented with the familiar *.docx, *.xlsx and *.pptx file extensions. For quite a while, OO.org users were stymied in their attempts to open, read, or edit OOXML documents. Kludgy extensions and workarounds were presented (from what I remember), but none of them "cured" the problem. Plus, Oracle was incredibly slow to address the issues and concerns over the lack of OO.org users to be able to read these new office document file formats.
I remember having to ask users of MS Office (at that time) to PLEASE send me any Office files in the older *.doc/*.xls/*.ppt formats, just to ensure that I would be able to open, read, and possibly edit those files. For a file format that was presented as a unifying force for office documents, it sure seemed to create a LOT of havoc for users of anything that was not Microsoft created or blessed.
Senaite is a free open-source self-hosted laboratory information management system (LIMS) that built for enterprise. It offers several features which are cost and resources effective with a rich set of add-ons and a strong supportive community of developers behind it.
In this article we demonstrate Senaite's features and how it helps enterprise through an efficient management for labs, lab equipments and reduce the turnaround time.
GNU Autoconf, a widely used build tool that shines at compatibility with a variety of Unixes, has accumulated many improvements since its last release in 2012 — and there are patches awaiting review. While many projects have switched to other build systems, interest in Autoconf remains. Now, a small team (disclaimer: including me) is rejuvenating it, working through some deferred maintenance and code review. A testable beta is now out, a new stable release is due in early November, and interested parties can build on this momentum to further refresh the rest of the GNU Build System (also known as Autotools).
[...]
Autoconf has built-in support for various compiled languages: C, C++, Objective C, Objective C++, Fortran, Erlang, and Go. More crucially, it performs feature detection with knowledge of a wide variety of POSIX platforms. If you are building new software that has few arcane dependencies and your users are all on modern Linuxes plus FreeBSD, or if you want to make Ninja build files, perhaps you'd be better served using alternatives such as CMake, SCons, or Meson — and indeed many projects have switched away from the GNU Build System over the years, including GTK+ and KDE. Complaints that the GNU Build System is slow, complex, and hard to use have been aired (including in LWN's comment threads) for years. However, if your customers need to be able to build a shared library on Solaris, AIX, HP-UX, IRIX, and all the BSDs, then Autoconf will come in handy.
In this article, we will explore another type of programming language used in the data science field. Apart from the Python programming language, R programming is one of the most popular programming languages used for statistical analysis of data. R programming is not only limited to statistical analysis but also expand its functionalities to a graphical representation of data. R was primarily written in C and Fortran programming languages.
A group of statisticians, also known as R Development Core Team, developed R programming and under GNU General Public License 4 distribution. R’s reputation in the field of data science is quite impressive. R programming is quite unique in implementation compared to C, Pascal, Python, Java, and other programming languages.
[...]
In this example, different age groups plots in a graphical way. This might not be a good representation, but what I want to emphasize in this article is the usage of ggplot or R programming in general. Using the ggplot package, you can incorporate beautification in your graphs, too.
Anyways, there are a lot of packages available that you can explore in CRAN or in R depending on your needs. Furthermore, most of these packages are open source and free. Don’t be afraid to use this resource out; you’ll be amazed at how it improves your programming process!
Ed J has taken over maintenance of my suite of GraphViz2 modules.
The first change has been to split it into multiple distros, so that anyone using just GraphViz2 will have a much smaller download and only 6 pre-reqs.
Another change is to rework the decision, which I copied from the original www.graphviz.org, and which meant nodes and port names were joined with a colon. For e.g. MS Windows users wanting to represent disk names like C:, this is clearly problematic.
Python has keyword arguments for functions that is a useful (and popular) feature; it can make reading the code more clear and eliminate the possibility of passing arguments in the wrong order. Python can also index an object in various ways to refer to a subset or an aspect of the object. Bringing the idea of keywords to indexing would provide a way to get the clarity benefit for indexing operations; doing so has been discussed in Python circles for a long time. Some renewed interest, in the form of lengthy discussions on the python-ideas mailing list and a new Python enhancement proposal (PEP), look like they just might take keyword indexing over the finish line.
Back in 2014, PEP 472 ("Support for indexing with keyword arguments") was created to push the idea, but it was rejected in 2019, largely because it failed to "gain any traction" in the interim. Since then, it has featured twice in lengthy python-ideas threads. Caleb Donovick raised it roughly a year ago, which generated a lively thread. Then, in May, Andras Tantos brought it up again, though he did not get much of a response for several months. But when Stefano Borini, one of the PEP 472 authors, replied in July, the ball started rolling.
I keep up with what's happening in my field by following a number of blogs and an occasional email list. I don't read everything posted in all of these, but by scanning the topics in a feed reader, I can keep up with what's going on, without wasting a lot of time.
Scrapy is an open-source web scraping framework, and it does a lot more than just a library. It manages requests, parses HTML webpages, collects data, and saves it to the desired format. Hence, you don’t need separate libraries for every other step. You can also use middlewares in scrapy. Middlewares are sort of 'plugins' that add additional functionalities to scrapy. There are plenty of open-source middlewares that we can attach to scrapy for extra features. This article will teach you how to collect data from webpages using scrapy. More specifically, we will be scraping Craigslist, and collect some real state data from their webpage. It would be good to have some prior HTML/CSS experience but you can proceed even if you are not familiar with HTML as a tiny portion of this article has been dedicated to HTML.
In the context of public key cryptography, certificates are a way to prove the identity of the owner of a public key.
While public key cryptography allows us to communicate securely through an insecure network, it leaves the problem of identity untouched. Once we established an encrypted communication we can be sure that the data we send and receive cannot be read or tampered with by third parties. But how can we be sure that the entity on the other side of the communication channel, with which we initiated the communication, is what it claims to be?
In other words, the messages cannot be read or modified by malicious third-parties, but what if we established communication with a malicious actor in the first place? Such a situation can arise during a man-in-the-middle attack, where the low-level network communication is hijacked by a malicious actor who pretends to be the desired recipient of the communication.
In the context of the Internet, and in particular of the World Wide Web, the main concern is that the server that provides services we log into (think of every service that has your personal or financial data like you bank, Google, Facebook, Netflix, etc.) is run by the company that we trust and not by an attacker who wants to steal our data.
In this post I will try to clarify the main components of the certificates system and to explain the meaning of the major acronyms and names that you might hear when you deal with this part of web development.
Both AWK and cut use numbers rather than names when operating on fields.
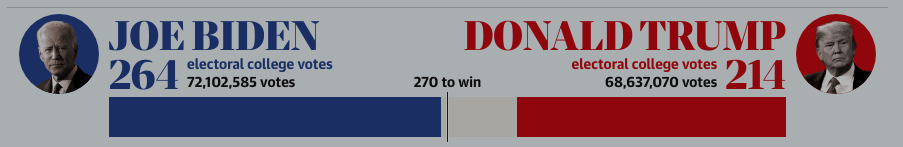
Joe Biden has said he is confident of winning the US presidency but held back from declaring a win as he secured the key battleground states of Michigan and Wisconsin.
Mr Biden, who has received more than 71,000,000 votes, the most votes in US history, was joined by his running mate Kamala Harris at the news conference, as he edges closer to the 270 electoral votes needed to win the presidency.
"I will govern as an American president," Mr Biden said, before adding: "There will be no red states and blue states when we win. Just the United States of America."
Speaking in Delaware, as votes continued to be counted for several US states, Mr Biden said: "It's clear that we're winning enough states to reach 270 electoral votes needed to win the presidency."
Svante Pääbo created the science of detecting Neanderthal DNA in archeological samples (and living humans) almost single-handedly (see Neanderthal Man: In Search of Lost Genomes). So it will come as little surprise to many that he published a paper in September describing his discovery of a gene derived from our Neanderthal ancestors (and inherited by modern humans) that encodes a risk factor for infection with the etiological agent for COVID-19, SARS-CoV-2.
The paper, entitled "The major genetic risk factor for severe COVID-19 is inherited from Neanderthals" and published in Nature, builds on genetic association studies that disclosed a gene cluster located on human chromosome 3 that relates to respiratory failure in response to COVID infection. Separately, other researchers had shown that this cluster was a "major risk factor" for severe COVID symptoms in 3,200 infected, hospitalized patients. In this paper, Dr. Pääbo and his collaborator show that the genetic element responsible for this phenotype resides in a 50 kilobase (kb) genomic segment inherited from our Neanderthal ancestors and is disproportionately found in humans from South Asia (50%) as compared with Europeans (16%).
I know ... it sounds like a horror film, huh? But TechRepublic's Jack Wallen and ZDNet's Steven J. Vaughan-Nichols both think it might be a good idea.
I just know you're screaming at the top of your lungs about now.
If you are like many Linux users, most of whom are Microsoft "refugees anyways, there are many, many reasons for your skepticism and fear. For years, Microsoft professed its intense hatred of Linux. They bragged about how they were planning to "eradicate the cancer known as Linux from the computing world.
Then, almost overnight, Microsoft professed its "love for Linux. Microsoft joined the Linux Foundation. Linux users RAGED! The "enemy was making itself comfortable ... in their OWN HOUSE! Most Linux users were afraid that it was the same ol' Microsoft up to its usual games, which involved the "triple E threat: embrace, extend, extinguish. MICROSOFT WAS GOING TO EXTINGUISH LINUX FROM WITHIN!
Actually, there are still many Linux users who haven't strayed far from initial assessment. Even in the PCLinuxOS forum, we hear it fairly regularly. Ignoring for a moment Microsoft's history of hatred towards Linux, can such a move possibly be all bad?
We don't have to look far to see the possible benefits. Back in 1999, macOS was rebased, partly, on Berkley BSD, leading to Apple joining the *nix family. Anyone would be hard pressed to argue with the results of Mac OS X (we're not talking about the costs associated with Apple products/hardware, nor the restrictive closed environment that constrains Mac OS X).
Believe it or not, Windows isn't the flagship Microsoft product any longer. It doesn't even come close to being a leading income producer for Microsoft. Instead, Microsoft finds its biggest profit leaders to be things like its cloud-based Office 365, and other "software-as-a-service (SaaS) products. Its Azure cloudspace is quite lucrative.
Microsoft migrating Windows to Linux does make sense. Instead of having a whole bevy of programmers working on proprietary, closed-source software, most of the heavy lifting would have been done by the FOSS and Linux community. You can be certain that Microsoft will tinker with the final product. They literally can't help themselves in that regard.
Companies hit by ransomware often face a dual threat: Even if they avoid paying the ransom and can restore things from scratch, about half the time the attackers also threaten to release sensitive stolen data unless the victim pays for a promise to have the data deleted. Leaving aside the notion that victims might have any real expectation the attackers will actually destroy the stolen data, new research suggests a fair number of victims who do pay up may see some or all of the stolen data published anyway.
The findings come in a report today from Coveware, a company that specializes in helping firms recover from ransomware attacks. Coveware says nearly half of all ransomware cases now include the threat to release exfiltrated data.
“Previously, when a victim of ransomware had adequate backups, they would just restore and go on with life; there was zero reason to even engage with the threat actor,” the report observes. “Now, when a threat actor steals data, a company with perfectly restorable backups is often compelled to at least engage with the threat actor to determine what data was taken.”
Coveware said it has seen ample evidence of victims seeing some or all of their stolen data published after paying to have it deleted; in other cases, the data gets published online before the victim is even given a chance to negotiate a data deletion agreement.
“Unlike negotiating for a decryption key, negotiating for the suppression of stolen data has no finite end,” the report continues. “Once a victim receives a decryption key, it can’t be taken away and does not degrade with time. With stolen data, a threat actor can return for a second payment at any point in the future. The track records are too short and evidence that defaults are selectively occurring is already collecting.”
The question of artificial intelligence as an inventor – and what it means for drug discovery
For more than 200 years, patents have been used as a means of granting exclusive property rights to an inventor, preventing novel and inventive contributions from being taken by anyone else. Recent developments in artificial intelligence (AI) technology, however, have thrown the current system – in which patents are awarded only to humans – into question.
This could have dramatic consequences for drug discovery. Patents are a central part of how pharmaceutical companies do business. Companies invest significant amounts of money into long and complex R&D cycles throughout the development of their products. Patent protection allows them to protect this investment, and continue to develop innovative new drugs and bring them to market.
But, in the case of AI crunching masses of data to assist in identifying a new drug candidate, issues can arise around the question of inventorship. This could pose the risk that a patent for a drug identified using AI technology won’t be enforceable, thereby straining the current financial model for recovering costs of drug development. And if pharma companies can’t protect their innovations with a patent, they’ll simply stop spending money on AI research, leaving many valuable new cures, particularly for rare diseases, undiscovered.
On November 3, 2020, Unified Patents, together with CableLabs, filed a second amicus brief in the refiled Intel Corp. v. Fortress Investment Group LLC, et al., and took the opportunity to help educate the Court on Fortress' now-frequent practice of using high-interest recourse loans to acquire questionable patents for serial assertion. A copy of the as-filed brief can be found below, and a copy of the original brief, which went into detail about litigation financing and other forms of serial NPE assertion, is also listed below.