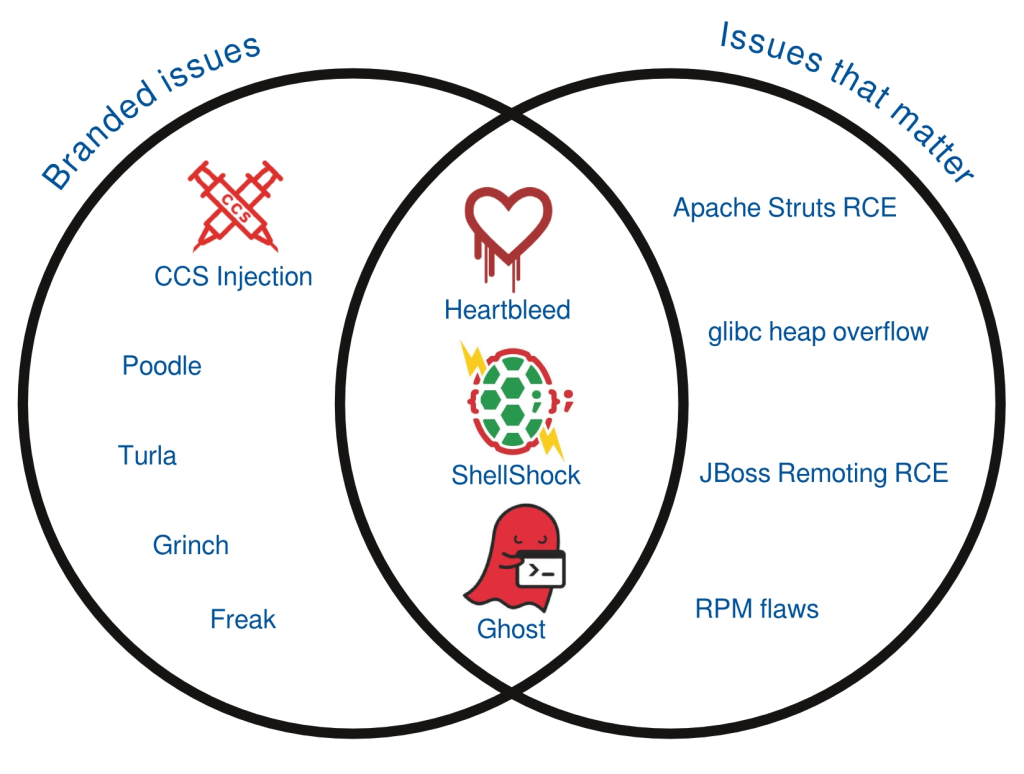
Image courtesy of Red Hat, demonstrating lack of correlation between severity and logos/brands
Summary: Many journalists bamboozled into becoming couriers of CrowdStrike, an insecurity firm which tries to market itself using a name and logo for a very old bug
THERE is a disproportionate level of coverage not of Free software but of bugs in Free software. We last wrote about it only days ago
A firm called CrowdStrike (who? Exactly!) is trying to emulate the 'success' of previous FUD campaigns. Now is the time to check who's a real journalist (fact-checking) and who's just serving PR campaigns like "VENOM", a shameless FUD campaign from CrowdStrike.
The whole "VENOM" nonsense was covered in a good article titled
"VENOM hype and pre-planned marketing campaign panned by experts". To quote: "On Wednesday, CrowdStrike released details on CVE-2015-3456, also known as Venom. Venom is a vulnerability in the floppy drive emulation code used by many virtualization platforms.
"However, while it’s possible that a large number of systems are impacted by this flaw, it isn’t something that can be passively exploited.
"Several security experts discussed the flaw online, focusing on the marketing and the media attention that it generated – including some over-hyped headlines. Most media organizations were briefed ahead of time about the discovery and gagged by embargo until the Venom website launched, so they had plenty of time to write.
"Many media articles compared Venom to Heartbleed, which is an apples to oranges comparison. If anything, the only commonality is the fact that both flaws had a pre-planned marketing campaign."
Here comes the "Heartbleed" brand. Yet again. They're using names that are scary (even all caps, like "GHOST") because it's so much easier to sell than "CVE-2015-3456". Journalists rarely have the technical knowledge to analyse a bug or a flaw, so they assume bugs and logos are indicative of severity.
This patch Tuesday Microsoft revealed 40+ vulnerabilities. Not a single one had a brand name, logo, etc. Here is how IDG covered
46 flaws publicly disclosed by Microsoft just for this Tuesday (
Microsoft hides even more flaws). So many flaws were collectively covered in one article and yet there are no logos; none has any branding.
"VENOM" has become the latest example of what we
call bugs with
branding. This has got to stop because it corrupts journalism and makes the field of computer security almost synonymous with marketing or advertising. CrowdStrike used ALL CAPS (for emphasis rather than acronym) and connotation with poison to market itself, an insecurity firm, after finding a floppy drive bug from over a decade ago. There is
a logo too (the first example we found of it), not just branding for this bug, dubbed "VENOM".
Bug branding (turning number into branding-friendly FUD) seems to have adopted the ALL CAPS convention from "GHOST", only for extra scare. This FUD has surfaced even in Linux-centric sites, which played along with the marketing campaign. Red Hat [1] and SJVN [2], even Phoronix [3] and Softpedia [4], have covered it by now, despite no focus on security news there.
Branding for bugs leads to stupid headlines
that are more poetic than factual and are very light on facts. There is little substance there. This whole recipe (bug+brand name+logo=lots of publicity without much merit) has been repeatedly exploited to give a bad name to FOSS security. A lot of headlines try to connect this to the "Heartbleed" brand. Headlines that we have found so far (links below) include "New Venom bug hits data centers, but it's hardly Heartbleed", "Venom bug could allow hackers to take over cloud servers - and experts say it could be worse than Heartbleed", "New Venom flaw may be worse than Heartbleed, researchers warn", and "Venom vulnerability more dangerous than Heartbleed, targets most virtual machines".
Zack Whittaker (former Microsoft staff) covered it like this in the CBS-owned tech tabloid, ZDNet: "Bigger than Heartbleed, 'Venom' security vulnerability threatens most datacenters"
Here is that "Heartbleed" brand again. "Please Stop Comparing Every Security Flaw to Heartbleed," said one good headline from Gizmodo (that's just how they covered this marketing campaign).
The word/brand "Heartbleed" was
made up by
a Microsoft-connected firm. Watch coverage from Microsoft-friendly sites and you will find headlines like: "Heartbleed, eat your heart out: VENOM vuln poisons countless VMs"
Dan Goodin, a
foe of
FOSS (from a security angle), brings in the NSA and Bitcoin to add FUD amid this branded bug/buzz. He wrote about the latest branded bug not once but twice (see links below). He is squeezing the most FOSS FUD out of it (opportunism). Kim Komando chose the headline "New bug taking over the Internet". No sensationalism here? One press release said "Better Business Bureau Says Most Don't Need to Worry" [about the branded bug], so there is some objectivity out there too, or an effort to calm people down.
Watch carefully how the bug is marketed in the media: Logo with SVG-like transparency; for a bug! Looks like it was prepared by graphics/marketing professionals. Are insecurity firms now liaising with marketing firms to professionally draw SVG logos for bugs? More logos for simple bugs (we found several, but one main logo) are circulating, usually with photos of snakes. See the complete list [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17,
18,
19,
20,
21,
22,
23,
24,
25,
26,
27,
28,
29,
30,
31,
32,
33,
34,
35,
36] as of this morning. How much more of this FUD is going to circulate before journalists realise that they make a mountain out of a molehill?
⬆
Related/contextual items from the news:
-
CVE-2015-3456 (aka VENOM) is a security flaw in the QEMU’s Floppy Disk Controller (FDC) emulation. It can be exploited by a malicious guest user with access to the FDC I/O ports by issuing specially crafted FDC commands to the controller. It can result in guest controlled execution of arbitrary code in, and with privileges of, the corresponding QEMU process on the host. Worst case scenario this can be guest to host exit with the root privileges.
-
The QEMU fix itself is now available in source code. Red Hat has been working on the fix since last week.
-
Popular virtualization platforms relying on the virtual Floppy Disk Controller code from QEMU (Quick Emulator) are susceptible to a vulnerability that allows executing code outside the guest machine.

