Prof Nils Melzer, Cybertorture & Debian Open Source vendettas
Reprinted with permission from Daniel Pocock.
In February 2020, The Guardian reported on work undertaken by Prof Nils Melzer, United Nations Special Rapporteur on Torture and Other Cruel, Inhuman or Degrading Treatment or Punishment concerning the subject of Cybertorture.
This is not exactly the stuff of tin-foil hats. It encompasses a growing range of risks to almost every business where the managers and employees are using the Internet as part of their job, through their mobile phones or in their personal time.
For example, people have noted that the recent crash of the Silicon Valley Bank happened faster than any bank run before it, thanks to the behavior of social media. Whether it was by accident or by design, it happened.
Initially, I couldn't find many reports using the word Cybertorture. Nonetheless, the journalist also mentions the more general term psychological torture. I went looking for the original documents about the subject.
The OHCHR web site has a link to an official report from the 43rd session of the Human Rights Council investigating the subject of Psychological torture and in fact the word "Cybertorture" does appear there in the text from the office of the Special Rapporteur.
The Special Rapporteur observes that psychological torture occurs in a wide variety of contexts, including ordinary criminal investigations, police detention, “stop-and-search” operations, intelligence gathering, medical, psychiatric and social care, immigration, administrative and coercive detention, as well as in social contexts such as domestic violence, mobbing, cyberbullying and political or discriminatory persecution.
Therefore, it seems perfectly reasonable to ask if Cybertorture may also occur in the operations of open source organizations. I previously mentioned it in my analysis of amateur-hour Codes of Conduct and now I intend to explore it in more depth.
The full report (22 pages) is available to download here. Section III(E) is dedicated to Cybertorture.
71. A particular area of concern, which does not appear to have received sufficient attention, is the possible use of various forms of information and communication technology (“cybertechnology”) for the purposes of torture. Although the promotion, protection and enjoyment of human rights on the Internet has been repeatedly addressed by the Human Rights Council (see A/HRC/32/L.20; and A/HRC/38/L.10/Rev.1), torture has been understood primarily as a tool used to obstruct the exercise of the right to freedom of expression on the Internet, and not as a violation of human rights that could be committed through the use of cybertechnology.
That sounds familiar. Remember the scandal of the FSFE Communications Policy?
72. This seems surprising given that some of the characteristics of cyberspace make it an environment highly conducive to abuse and exploitation, most notably a vast power asymmetry, virtually guaranteed anonymity and almost complete impunity. States, corporate actors and organized criminals not only have the capacity to conduct cyberoperations inflicting severe suffering on countless individuals, but may well decide to do so for any of the purposes of torture. It is therefore necessary to briefly explore, in a preliminary manner, the conceivability and basic contours of what could be described as “cybertorture”.
How do these anonymous organized criminals disguise themselves?
Look for cowards who write Conduct Team, Community Team and CARE Team emails.
Look for cowards who communicate through lawyers.
Nonetheless, the most evil case of psychological torture that I know of is not anticipated in the report. It is a hideous crime and I'll come back to that at some point. Sadly, it is analogous to Debian culture.
Here I'll look at some of the attributes of Cybertorture that we can already see.
Imposters
The Non-Developing Debian Developers seem to be a good example of imposters. In some cases it looks like they are simply giving voting rights to their girlfriends.
One of these "developers" wrote the following on her Github profile:
I don’t know how to code, but I do have blue hair.
Are these the words of a developer? Or is this somebody's girlfriend who was given a Debian title without coding?
Anonymous emails / Team emails
Here is an example from FOSDEM.
Subject: Re: [FOSDEM-Conduct] Date: Sat, 19 Nov 2022 17:19:22 +0000 (UTC) From: FOSDEM Conduct Team <conduct@fosdem.org> To: [volunteers / victims]
Dear [volunteers / victims],
The FOSDEM Conduct team would like to inform you that, as has been communicated before, you are banned from formal participation in FOSDEM events. This decision is final. We opt to have no further discussion with you.
FOSDEM Conduct Team
Notice the hint of Nazism in the email. Hitler wanted a final solution for Jews and the Conduct team wants a final solution for people who ask questions.
Threats
I previously described an email that Laura Arjona sent to my Outreachy intern behind my back:
Thus, we are considering requesting a rejection of your application to the bursaries team.
Amateur-hour Codes of Conduct
As noted in my blog about amateur-hour Codes of Conduct:
Nobody wants to sound like that guy with the tin foil hat spreading conspiracy theories about these matters. Nonetheless, if the PsyOps risks anticipated by Prof Melzer did exist, they would be concealed in broad daylight under the guise of these unsafe Codes of Conduct.
Attacking the person, not the issue
In football terms, we would say playing the man and not the ball.
The classic example of this could be Jacob Appelbaum. Here are the yet-to-be-published threads on debian-private:

The Debian gangsters responded with attacks on Mr Appelbaum's reputation and his home. They wanted to avoid the more significant question about Debian / NSA relations.

Tone nazis / word nazis
You write an email about an important issue and somebody makes a reply about the tone of the email without any comment on the issue itself. This includes attacks on sarcasm.
People call it tone policing but I feel that term is too favorable. Police serve a useful purpose in many situations. The term tone police is confusing and disparaging to real police.
It is better to use a word like tone nazi or tone fascism. Please don't call them tone police.
Attacking your metaphor
This is a cousin of the tone nazis.
You use a metaphor to make a point, for example, reference to the Debian Christmas lynchings uses the word lynching as a metaphor.
As in the case of the tone nazis, people discuss the metaphor and avoid discussion of the actual issue.
Spreading rumors about people
We can see an example of this in the case of the violent attack on Ted Walther (krooger) at DebConf6 in Mexico.
Ted was a candidate in the election for Debian Project Leader. We can see his platform in 2005 and another platform in 2006.
When he arrived at the DebConf6 dinner with a female guest in 2006, political rivals spread rumors that the woman was a prostitute.
This rumor was based on two facts: she was a woman and she was Mexican. It was therefore sexist and racist. This is Debian.
Privacy violations
I felt the pain of this personally. Carla suffers from an eating disorder. People from Debian, FSFE and FOSDEM spread rumors about abuse.
Carla didn't ask for this. At FOSDEM, Molly de Blanc got up in the Legal and Policy issues dev-room, introduced herself as a Debian Developer and President of the OSI and encouraged people to join the whisper network and spread rumors about Carla's eating disorder.
Forgeries, impersonation and Deep Fakes
This is only getting worse with deep fakes and other methods of impersonation.
Deception
I covered the topic of deception in my blog about Debian Modern Slavery.
Don't reply
Every now and then a message appears on debian-private, the gossip network, ordering volunteers not to reply to a particular person.
Many of the volunteers are like sheep and they are quickly intimidated by these orders without asking any questions.
Manipulating people and inciting a mob
This is the opposite of the Don't reply tactic. Rather than beating people into silent submission, people are whipped up into a frenzied mob.
The world was shocked by the sight of Donald Trump's mob sacking the US Capitol in January 2020.
We saw the same phenomena in the mob against Dr Richard Stallman during Easter 2021.
One of the key points about this mob phenomena are the people who were exploited in the heat of the moment and then after some thought asked to remove their names from the lynching. The cyberbullies who ran this mob have locked the github petition so that people can't remove their names any more.
Demonization, exaggeration
Have a look at the Pentagon employee Paul Tagliamonte obliterating the gulag metaphor.
The gulag metaphor is quite appropriate for any system of secret punishments. Tagliamonte blows it out of the water by escalating it to questions of summary execution.
In fact, the very reason for PsyOps is to avoid the blood stains associated with executions.
Use of words or images that have a personal impact
The feminazis set up a doxxing site to attack Jacob Appelbaum. According to Appelbaum:
The people behind the website against me used photos from a dear friend - she was really unhappy as she not only didn't authorize it, it wasn't something she supported.
These people who violate copyright on photos now insist on the invincibility of their trademark rights. Go figure.
In fact, we can see the same pattern with Molly de Blanc's use of cat torture at FOSDEM.
This is the picture of a cat behind bars that de Blanc used at FOSDEM to vilify us:

Carla and I had cats. That is why de Blanc chose cat pictures for her campaign of harassment against us.
Cats don't belong behind bars. They are experts on violating any Code of Conduct. This is how they walk on the dinner table, sleep on the dinner table and tear down the Christmas Tree.



Suddenly cutting a discussion
An important philosophical issue is being discussed on an open source mailing list and all of a sudden somebody insists that it must stop.
Humiliation in front of others
Somebody sends you an insult and they CC other people on the same email.
Any publicly visible insult in social media, Github or any other platform.
Secret acts of shaming
Even more serious than the public acts of shaming, the secret acts of shaming are a recipe for disaster, leading to consequences like alcohol and drug dependency, self harm or even suicide.
These secret acts of shaming mirror the tactics of pedophiles. Pedophiles hope that the shame of abuse, known only to the victim and the abuser, will prevent the victim speaking to any third party.
We see the tactic being deployed by Enrico Zini in his message to Dr Norbert Preining:
We are sending this email privately, leaving its disclosure as your decision (although traces in public databases are unavoidable).
Dr Preining and I have been courageous enough to call their bluff and expose these pedophile tactics.
In many cases, pedophiles hope that secrecy will allow them to return to the same victim and commit further acts of abuse. Notice the following in Zini's message to Dr Preining, where he encourages Dr Preining to continue doing work for Debian under these oppressive terms:
All packages in which you are currently listed as maintainer or uploader will be added to your Debian Maintainer whitelist as soon as possible.
Condescending and belittling people
A good example of this comes from my trip to FOSSASIA. The Debian Project Leader (DPL) Chris Lamb insisted that I should spend another hour looking on AirBNB to find cheaper accommodation.
This type of thing demonstrates a total disrespect for the value of my time. Accommodation in Singapore is expensive, there is no easy way around that.
Subject: Re: travel request: FOSSASIA March 2018, Singapore Date: Tue, 16 Jan 2018 05:59:49 +0530 From: Chris Lamb <lamby@debian.org> To: Daniel Pocock <daniel@pocock.pro>, leader@debian.org
Hi Daniel,
> Accommodation: EUR 500
Can you confirm this amount? It seems rather high for a short conference; I stayed in .sg for about 3 weeks on this amount last year!
Regards,
-- ,''`. : :' : Chris Lamb `. `'` lamby@debian.org / chris-lamb.co.uk `-
Using pawns
Dr Preining shared examples of the threats he received from Enrico Zini in Italy.
Zini appears to be something of a pawn. People like Chris Lamb are pulling Zini's puppet strings. Lamb was a coward who couldn't look people in the eye so he used Zini to send messages like that.
Lamb is a total coward. He used Zini to send me insults in September 2018. At the same time, Lamb was sending emails behind my back to denounce me. He used Zini as a shield. Pity the little Italian pawn.
Using organizations and organization names to spread defamation
Look at how a series of organizations were strong-armed to publish defamation about Jacob Appelbaum in 2016.
Linux Australia is a particularly good example of a gullible board. On 22 June 2016, they stated they would wait for the matter to become clearer before deciding if any response was necessary. Eight days later, on 1 July 2016, Linux Australia published a long email publicly denouncing Jacob Appelbaum. They reached the decision to do that in just eight days, but seven years later, the situation hasn't actually changed: not one person ever filed a police complaint against Appelbaum. Linux Australia was suckered or bullied into making that statement.
Outsiders are frequently deceived to believe that an organization like Linux Australia made a credible inquiry into the matter. In reality, one or two gullible board members were suckered into the hysteria and the rest of them were asleep at the wheel.
Inconsistencies
For five years now people have been spreading the rumor that I had a relationship with my Google Summer of Code intern.
The problem with this rumor is that the woman was already engaged before starting the internship. She actually got married in the middle of the GSoC internship.
Here is Ariadne Conill spreading rumours about a mentor (me) girlfriending one of the GSoC interns:
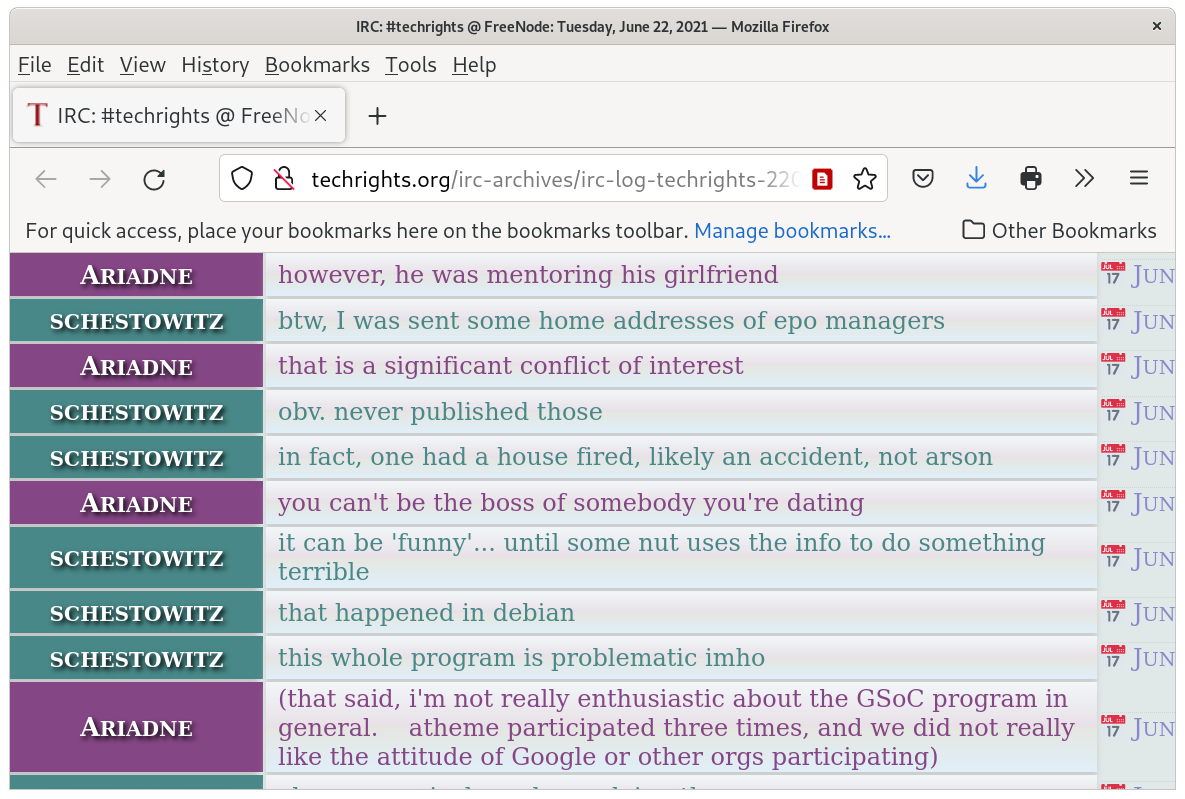
The last female intern I was responsible for is Elena Gjevukaj. In the middle of her internship, she sent me a picture of her wedding.
Oops. Debian lies. Ariadne lies. If the woman got married in the middle of the internship then it is both very rude and very absurd for Debian people to suggest she was my girlfriend.
Subject: Surprise Date: Wed, 15 Aug 2018 01:14:54 +0200 From: Elena Gjevukaj <gjevukaje@gmail.com> To: Daniel Pocock <daniel@pocock.pro>
We got married! 😂

The Debian / Google vendetta against this woman and I is horrendous.
More details are available on Outreachy.Dating.
Reference to secret victims
This is a common scam in open source organizations. Some little fascist pretends to be acting on behalf of a woman or some other vulnerable victim. There is no evidence and no names are permitted.
Blocking communications
We see them maliciously putting the email addresses of certain volunteers onto spam blacklists.
The Stasi did evil stuff like this. There are various emails on debian-private where Alexander Wirt (formorer) admits putting people on blacklists.
Claims that people are quitting or refusing to join
This is another gangster tactic used to vilify somebody. In fact, if people are quitting, it is usually because of the overall problems in the culture and not because of any one individual scapegoat.
The culture of humiliating people and making public statements about people is a big turn-off for many people, especially women. Most people don't care who is right or wrong, as soon as they see somebody being humiliated they run a mile.
Yet the little cyberbullies still insist that they have to punish some scapegoat because other people are quitting.
Menial tasks and chores
If people are quitting, it is most likely because of menial tasks and chores.
FSFE's demand for developers to run their REUSE tool and the similar DEP-5 requirement in Debian shows how completely out of touch they are with the interests of volunteers.
Aggressive emails sent at night and on weekends
Look at the lynching of Dr Richard Stallman, it started on a Sunday.
Setting deadlines for volunteers
Two days is hardly enough time to find begin to read, let alone reply to, all the nonsense that appeared in the Jacob Appelbaum lynching.
Subject: Expulsion of Jacob Appelbaum <error> Date: Sat, 18 Jun 2016 21:41:50 +0200 From: Debian Account Managers <da-manager@debian.org> Organization: Ganneff To: debian-private <debian-private@lists.debian.org> CC: error@debian.org, jacob@appelbaum.net, leader@debian.org
[...]
Most of these testimonies have been sent to debian-private in a way that is accessible to all Debian Developers (including Jacob). Two days ago we emailed Jacob directly, forewarning him of this decision and soliciting his input. We have received no reply, and the deadline we set has lapsed.
[...]
Isolation treatments (like solitary confinement)
Here is that brutal cat picture from FOSDEM 2019 where Molly de Blanc, the former Debian leader's girlfriend, not being a developer herself, suggested isolation punishments:

Here is an example from the case of Michael Kappes at FSFE:
Subject: Re: [GA] Fwd: Konsequenzen Date: Fri, 26 Jan 2018 17:13:07 +0100 From: Erik Albers <eal@fsfe.org> (employee bullying volunteers) To: Jonas Oberg <jonas@fsfe.org> CC: ga@lists.fsfe.org
Hi Jonas,
On 23.01.2018 11:44, Jonas Oberg wrote: >> We will report after that.
There have been even more CoC breaches by this person on our mailing list recently but I do not see the need going so much into detail. The CARE informed the person in question to be exluded from any local meet-ups for three months and that he is put on moderation on all FSFE mailing lists in the same time. His access to his blog is also deactivated for 6 months and he is not allowed to participate in any official FSFE representation, including but not limited to participate in booths or give talks in the name of FSFE.
...
Intrusion on significant dates
Dr Norbert Preining writes about how Debian mafia attacked him on his birthday.
This is horrible but no big surprise. In 2018 the same gangsters attacked Dr Preining and I at Christmas.
In 2021, the crazy mob attacked Dr Richard Stallman over the Easter holiday season.
In my own case, they attacked me on the wedding anniversary, on my birthday and again on Christmas eve.
They attacked me after my father died and they attack me again on the anniversary of his death. █
