
f61ec70272c7d04fdf6f006ec21bc29a
The NHS and Microsoft TCO
Creative Commons Attribution-No Derivative Works 4.0
THIS article is well overdue. We planned to write about the topic as soon as the media had broken the story, but we still needed definitive proof of ambulances or ambulance services being impacted by a Windows/Microsoft shop. Now we have what we needed.
"As a little bit of background, consider reading our 2020 series about how Windows in hospitals kills a lot of people, probably more people than COVID-19 killed."The first report we saw about the ambulances was in a British tabloid, the Daily Fail (notorious and controversial domestically and abroad). My wife saw a similar story (saying "cyber attack") in the Microsoft-friendly and Bill Gates-bribed BBC (or BillBC). Calling it a "cyber attack" is misrepresenting the problem, shifting blame to another party. The Daily Fail used the same term (the headline was "Cyber attack hits two ambulance trusts leaving hospitals without access to electronic patient records").
But what really happened? As we showed recently, in the case of London's municipality, they tend to downplay if not lie about security incidents. They belittle the severity and impact.
As one associate explained early in the past week, "if it can be confirmed by a legitimate paper or authentic source, then it goes in the Windows Total Cost of Ownership (TCO) section. Too bad no news sites are onto the TCO aspect any more. It was discussed for a while about 20 or so years ago. The extra electricity used by Windows and Microsoft software in general is an environmental problem at-scale."
"But what really happened?"Not too long later we saw more reports with no substance in them, except Microsoft spin (offloading the blame).
This Microsoft Windows TCO story was published with "cyber-attack" (or "cyberattack") in the headline just 3 days ago:
Several UK NHS ambulance organizations have been struggling to record patient data and pass it to other providers following a cyber-attack aimed at health software company Ortivus.
In a statement, the Sweden-headquartered software vendor said it was subject to a cyber-attack on July 18 which hit UK customer systems within its hosted datacenter environment.
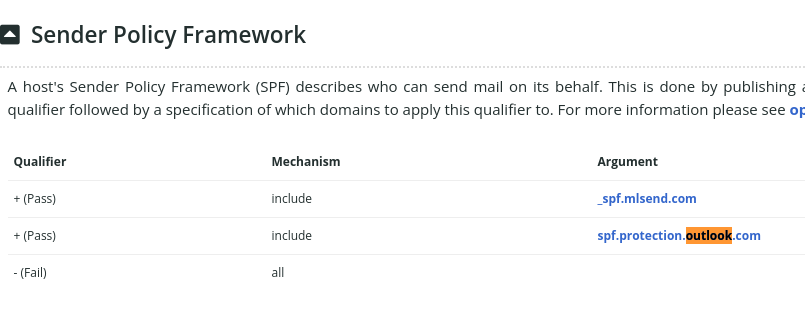
Ortivus uses Microsoft for mail. No proficient (at technology) company would do that.
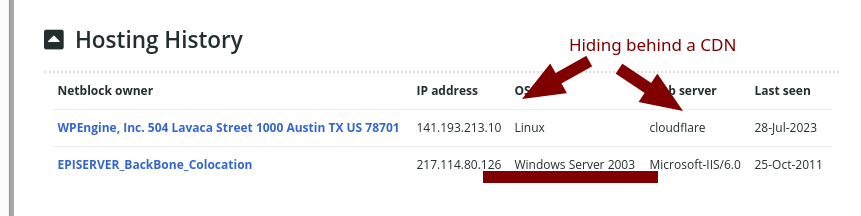
So it's a Windows shop with Clownflare as a CDN (dangerous outsourcing to another continent, to a flailing and failing company). Hiding behind a CDN is a sign of weakness. They could use something like Varnish instead. If they had skilled staff that can follow a simple manual. Microsoft drones are not skilled staff.
"The video above is taking on all the "supply chain attack" FUD which has been directed at FOSS and redirecting it back at Microsoft because this was the quintessential supply chain attack."So what we have here is no 'smoking gun' but a lot of circumstantial evidence and clue they're probably "throwing the subcontractor under the bus" to distract from Windows involvement. Since some past incidents they have been careful not to announce Windows deployments and especially not Sharepoint or other shambolic monstrosities.
The video above is taking on all the "supply chain attack" FUD which has been directed at FOSS and redirecting it back at Microsoft because this was the quintessential supply chain attack. The FOSS susceptibility is theoretical, this one was a real-life exploit using existing Microsoft deployments.
"We're meant to think that something being defective by intention will "create jobs"."One can hope this latest incidents leads to increased awareness of not just the TCO of Windows but the importance of upgrading to other systems, specifically GNU/Linux. The recent Norwegian Windows breach was a quintessential example of a supply chain compromise, one with which they've tried repeatedly to smear FOSS with. Yet in real life the first big state level one turns out to be Microsoft.
If security were part of the design, this Windows-contrived 'shortage' would not exist at all. The parable of security as an after-market add-on is conveniently named "Broken Window". We're meant to think that something being defective by intention will "create jobs". ⬆