

In the 70's, the motto that propelled the then young company Microsoft was the one in the picture above: A computer on every desk, in every house, and running Microsoft software.
Well, after more than 40 years, this sad prophecy is about to come true, thanks to the Pluton chip, yet another attack on user freedom, perpetrated by one of the most abusive companies in existence.
But, what is the Pluton chip?
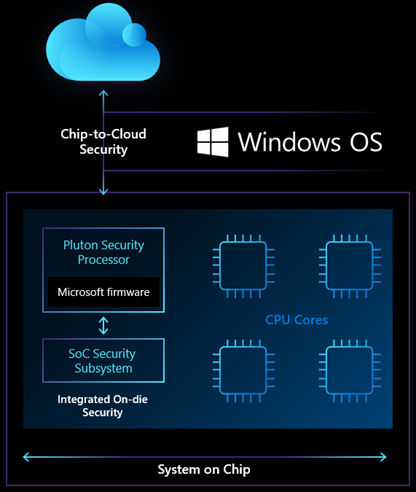
The Pluton chip was announced on November 17, 2020, on the Microsoft blog. The Pluton chip acts as an extension of the TPM (trusted platform module) platform. The trusted module platform, TPM, acts as a verifier on what the operating system can run, remote attestation, and other restrictions. The TPM module is usually a separate circuit, mounted on the computer's motherboard (although, over the years, several TPM implementations have emerged).
As the TPM module needs to communicate with the computer's CPU, the information that travels between the module and the CPU can be accessed, analyzed and reverse engineered with the information collected. Thus, it is possible to hack a TPM module. Then comes the Pluton chip.
According to Microsoft's blog post: "The Pluton project removes the potential for this communication channel (between the CPU and the TPM module) to be attacked by building security directly into the CPU." That is, the TPM module, with the Pluton chip, is inside the microprocessor. That is, it is a SOC inside the CPU, eliminating the external module entirely.
The Pluton chip is not new, in fact it has been used before
The Pluton project was introduced as part of the integrated hardware and security capabilities of the operating system in the Xbox One console released in 2013 by Microsoft in partnership with AMD and also within Azure sphere. In fact, what Microsoft intended with this project was to prevent modded Xboxes from entering the Xbox network blocking their access to Microsoft's network. The project worked so well that they decided to expand to microcomputers.
 Block diagram of the Pluton chip
Block diagram of the Pluton chipThe concept of a security module that restricts the use of a computer is not unique to Microsoft. Apple also implements a similar technology, Secure Enclave, and Google, with Android, also implements SecureNet.
The reason behind Pluton is legit...
All the reasoning behind Pluton is legit. It is to ensure security in the internet of things (IoT), and it is correct to look for it. Because they are extremely frugal devices with no real processing power, they cannot afford to have sophisticated encryption and protection schemes.
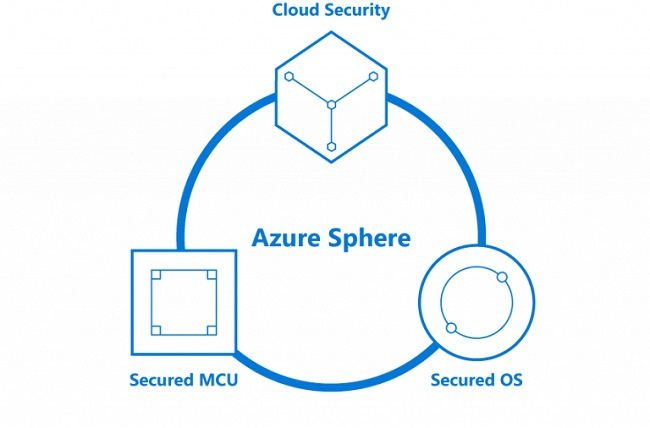
To better understand the Pluton chip, it is necessary to know how Microsoft's cloud security scheme for IoT devices, Microsoft Azure Sphere, works.
The Microsoft Azure Sphere concept is based on the fact that the SOC processors that power the IoT devices that exist today can no longer be trusted. Because they are based on old technologies, they are not prepared for the security demands of a connected world. Microsoft has released a solution to address this problem, Azure Sphere. This Microsoft solution is now ready to go into production. Azure Sphere is a secure, high-end application platform with built-in communication and security capabilities for cross-industry IoT devices. The idea of Azure Sphere is to have a line of trust, from the IoT device to the Azure servers in the cloud.
This would be achieved through the integration of 3 elements, which work as one: a brand new security silicon chip (a microcontroller with Pluton technology already built in), the Azure Sphere OS operating system and the Azure Security Service. sphere. These components come together to create a chain of trust between the cloud and the devices.
The operating system Azure OS is Linux-like, and the microcontrollers are already starting to be produced by the Taiwanese company MediaTek.
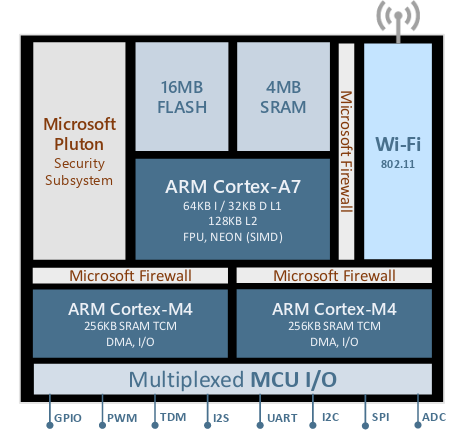 MT3620 Azure Sphere Chip Architecture
MT3620 Azure Sphere Chip ArchitectureThe road to hell...
As the saying goes, the road to hell is paved with good intentions, and despite a legitimate concern for internet security, in the age of connected devices, this "security" opens up an avenue of possibilities for Microsoft to abuse again, the market, users and laws (let's face it, the laws are not yet ready for our new digital age).
Now, what could go wrong? All, let's recall an interesting case in which Microsoft, even indirectly, abused its customers.
Stuxnet, or How Windows Helped Bring Down Iranian Nuclear Power Plants
Stuxnet is a computer worm specifically designed to attack the SCADA operating system developed by Siemens and used to control Iranian uranium enrichment centrifuges. It was discovered in June 2010 by the Belarusian antivirus company VirusBlokAda. It is the first worm discovered that spies on and reprograms industrial systems. It was specifically written to attack the SCADA industrial control system, used to control and monitor industrial processes. Stuxnet is able to reprogram PLCs and hide the changes.
Stuxnet's design and architecture are not domain specific and could be adapted as a platform to attack modern SCADA and PLC systems (e.g. in factory assembly lines or power plants).

Later, and with the help of Edward Snowden's revelations, it emerged that Stuxnet was part of an espionage and cyber warfare program called Operation Olympic Games (Operation Olympic Games was a covert and still unrecognized campaign of sabotage through of cyber nuisances, directed at Iranian nuclear facilities, likely by the United States and Israel. As reported, it is one of the first known uses of offensive cyber weapons. Initiated under the George W. Bush administration in 2006, the Olympic Games were accelerated under the Obama presidency, which heeded Bush's advice to continue cyberattacks on Iranian nuclear facilities at Natanz. Bush believed the strategy was the only way to prevent a conventional Israeli attack on Iranian nuclear facilities).
David Emm, a senior security researcher at Kaspersky Labs, told the Guardian: "We think the sophistication, purpose and intelligence of Stuxnet suggest the involvement of a state.
"This is a very sophisticated attack - the first of its kind - and was clearly developed by a group of highly qualified people with the intention of gaining access to SCADA [Supervisory Control and Data Acquisition] systems - industrial control systems to monitor and manage industrial infrastructure or facility-based processes. In contrast to most indiscriminate cybercrime threats on the Internet, this one has been targeted at very specific targets. It is also different because there is no obvious financial motivation behind the attack - the objective appears to be sabotage of systems." What is known is that Stuxnet was created to exploit zero-day flaws that had not been made public. Windows flaws. And given Microsoft's promiscuity with government agencies, it is not impossible that the entire map to be able to launch this attack has been provided by Microsoft itself. Of course, the company was never connected to this act of digital vandalism, but the last time I checked, 2+2 was 4...
Well, you reader, you might be thinking: F@#$! the Iranians. They're a bunch of crazy fanatics, they better be sabotaged anyway. But once you open Pandora's box, everyone can be affected.
The legacy of Stuxnet
As I wrote above, once you open the door to malware, it gets loose and will damage the systems it encounters, no matter if they are allies or enemies. After all, as everyone remembers, both Saddam Hussein and Osama Bin Laden were CIA assets, trained and funded by the US government. But Stuxnet left us a legacy, its code continues to be studied, and, of course, it had heirs...
Duqu
In 2011, threat analysts discovered a new worm and named it Duqu. The striking similarities between Duqu and Stuxnet led experts to believe that the two malware strains were closely related. In fact, they were almost identical: the only difference is that Duqu was not designed to sabotage machines, but to act like spyware by capturing keystrokes and collecting system data.
Flame
An even more suspected Stuxnet-linked malware that emerged in 2012. Dubbing the new threat Flame, researchers found that the virus shared much of its code with Stuxnet, in particular the way it was designed to target the same vulnerabilities of Windows and propagate through USB storage devices.
But, why did I bring this case? Well, now, let the imagination fly, and see how, with the help of Microsoft, a tyrannical government can control its entire population, through its digital devices...
Brave New World
In the not too distant future, the following could be possible with Pluton (with some custom application development to streamline everything together):
Now, in our imagination exercise, visualize a hypothetical scenario. A user in Legal creates a document. When the user uploads it, Azure checks it against Pluton to verify that the document is likely clean and also to firmly establish who created it. When another user wants to download the document, Azure only provides a version that was encrypted with the user's Pluton public key if that user belonged to the correct department and therefore can only be read by that user.
Now, multiply this hypothetical scenario all over the world, and everyone who uses Windows applications will never have any secrets. It would be the end for privacy and anonymity. Everything you do will have to be validated by a server in the Azure cloud, and, of course, big brother will watch. Ever. Using computers will be something like being a Linux user from North Korea.
Other than that, with a dedicated chip running inside the microprocessor, what else won't it do? Will it not send my activities in forums, to some government agency? Or my emails? Or my comments on Facebook? The possibilities are endless, for evil, unfortunately.
The implications are already starting to show
At the beginning of the year, Matthew Garrett, the researcher who created the UEFI bootloader for Linux (which I do not agree with at all, as it sets a precedent for Microsoft to abuse the market, with its position of power, should not be allowed under any circumstances) said that the Pluton chip was not an attack on users' freedom to use whatever operating system they wanted, which was not a threat.
In July 2022, he recanted, when he was unable to install Linux on a high-end Thinkpad Z13, complaining that this was not a legal practice by Lenovo.
But, that's what Microsoft wants. Under the guise of enforcing security, it blocks the machine's access to the user himself, being the gatekeeper of personal computing. In other words, "my" microcomputer is over. From now on, it will be Microsoft's microcomputer, and only what it allows will run...
How to prevent that from happening?
It is up to us, the users, to boycott AMD products that contain the Pluton chip, to favor recycled or refurbished computers. And there is still more to do:
So folks, things have never been so in jeopardy as they are today. Microsoft wants to be the big brother, and dictate what everyone can run on their computers, under the benevolent guise of ensuring security. We can't afford that, or the future of personal computing and privacy will be ruined.
Finally, let's not forget that anyone who says they don't need privacy because they have nothing to hide is the same thing as not defending freedom of speech, because they have nothing to say...
Let's fight this! The scenario is ugly, and the battle will be hard! ⬆