
[PDF] for a lot more.
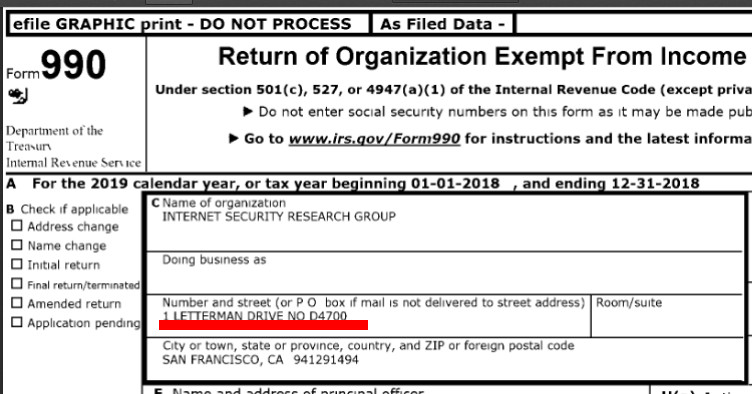
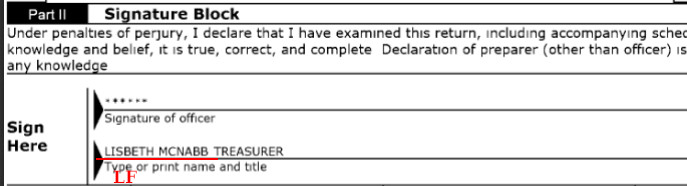
Yesterday we asserted (and then explained why) today's Linux Foundation -- or LF for short (one way to avoid the misleading name) -- works for monopolies, not Linux. It uses the "Linux" brand to market itself.
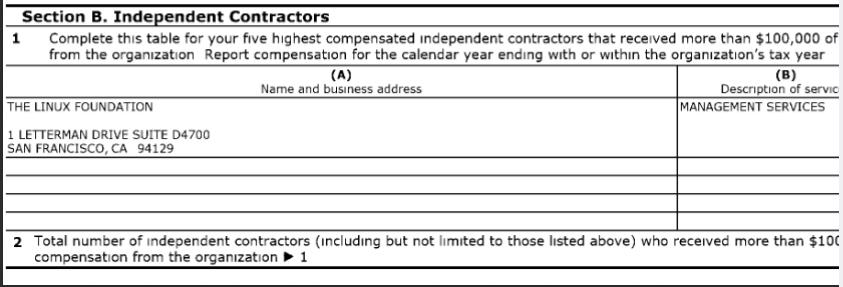
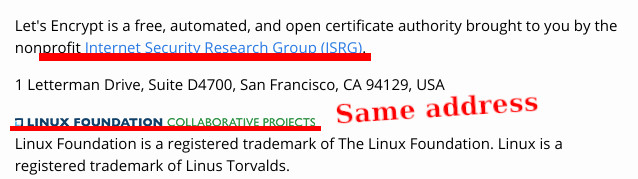
"The aspect nobody wishes to talk about is that the Let's Encrypt monopoly is reinforcing monopoly and monopolies (Let's Encrypt itself is fast becoming a monopoly and it helps large companies further monpolise and thus centralise the Web)."Look who backs this. Look who funds this. Look where the code is hosted (proprietary Microsoft GitHub). Even the site itself is outsourced to proprietary Microsoft GitHub...
Let's Encrypt is partly funded by Microsoft/GitHub and various other unsavoury companies notorious for their back doors (we can name more than a handful).
So much for security, considering how close Microsoft and the NSA have long been.
But that's not the point. That's not the most important thing.
The aspect nobody wishes to talk about is that the Let's Encrypt monopoly is reinforcing monopoly and monopolies (Let's Encrypt itself is fast becoming a monopoly and it helps large companies further monpolise and thus centralise the Web).
It may sound peculiar at first, but considering the FIDO situation we've seen it elsewhere as well. Much power can be gained -- sometimes money follows -- by making oneself the de facto standard. Then abuse and chaos may ensue, as monopolies need not compete and appease/please anyboby.
Yesterday the Let's Encrypt site published a blog post which bears a rather meaningless if not misleading headline (because a suitable headline would likely upset people right from the get-go).
Put in simple terms, sites that adopt HTTPS with the 'free' (so-called, hence scare quotes) Let's Encrypt will become inaccessible to a lot of visitors. In the name of fake 'privacy', which does nothing about spying at the endpoints (like data sales to brokers). People who think HTTPS 'means privacy' should remind themselves that companies like Facebook -- a Let's Encrypt sponsor -- use HTTPS and it does nothing to prevent Facebook from assaulting privacy like Microsoft assaults love itself. HTTPS helps secure things not at the endpoints but during transit.
LWN's headline was vastly more informative than the waffle from Let's Encrypt and it said:
Fallout from upcoming Let's Encrypt certificate changes
As described in this Let's Encrypt blog entry, certificates issued by Let's Encrypt will soon be signed solely by that organization's own root certificate, which is accepted by all modern browsers. There is one little catch, though: versions of Android prior to 7.1.1 (released in late 2016) do not recognize that certificate and will start throwing errors. "Currently, 66.2% of Android devices are running version 7.1 or above. The remaining 33.8% of Android devices will eventually start getting certificate errors when users visit sites that have a Let’s Encrypt certificate. In our communications with large integrators, we have found that this represents around 1-5% of traffic to their sites." There appears to be little to be done about this problem other than to encourage owners of older Android devices to install Firefox.
 Just one year? Hardly anything would change by then. See the comments in LWN. One person said: "Rooting old phones requires erasing them. I'd hazard that the users of those phones would be cautious about that (data loss), as opposed to current phones (loss of access to baking and game apps)."
Just one year? Hardly anything would change by then. See the comments in LWN. One person said: "Rooting old phones requires erasing them. I'd hazard that the users of those phones would be cautious about that (data loss), as opposed to current phones (loss of access to baking and game apps)."
They're pushing people to buy new so-called 'phones' (spying devices). And further down it says: "Plausibly deniable way to send users up the upgrade treadmill. C'mon, Android users! Throw away your devices, again!"
Why would anyone wish to turn away users in the name of fake 'privacy' or dubious levels of confidentiality? If the Let's Encrypt folks somehow hand over keys to the government (e.g. under Trump NSLs), then what good is it really? It not only helps monopolies but also militant empires.
Let's Encrypt may claim to be a liberating and democratising force, but that's assuming it does what it says on the tin.
An encrypted systems specialist elaborated on this. "Trust should only exist between the provider of data and the consumer," he said to us. "Any other third party introduced into the system is an attack against privacy, security, and autonomy. Don't let quacks convince you otherwise."
"The discussion should lead the user to devices and browsers that let them have a local list of public keys they trust. That's the basic function of TLS anyways. The concept of a CA needs to be binned altogether. You can still trust certs yourself on Firefox. Just ignore the browser warnings."
He added that "what [we] should tell users is to start trusting self-signed certificates in favour of certs provided by CAs. Let's Encrypt is a vehicle for maintaining the trust monopoly. It's free so people blindly just use it, without realising they're just further entrenching the trust monopoly. Anyone can generate TLS certs with openssl (or even more secure libressl; libressl is by the OpenBSD team. It's the best TLS software around. There's nothing magical about TLS certificates. If someone has something like WordPress, you can just use libressl to generate your own certs and then put a banner on the top of your info page on your website asking users to trust whichever cert you generated and hasn't expired [and] what we really need in a truly security-and-privacy respecting Web browser is one that rejects all TLS certificates by default and only accepts certs the user agrees to accept. Right now the situation is the opposite of what it should be. Users have monopolised "trust providers" dictate which certs they accept. Kind of how you do when you set up SSH. You block all public keys by default and only allow ones you trust yourself. And you, the user, have full control of your trust system. Delegation of trust mechanisms to third parties is flagrant stupidity in any security system. In summary: right now you, the user, have a dictator ordering you whom you can and cannot trust. This is absurd. Your devices and software shouldn't stop functioning when you want to take back control over your trust. The current system is a dictatorship of CAs forcing people to give up control over their trust (and by extension, their security and privacy). These are abuses against articles 12 and 19 of the Universal Declaration of Human Rights."
Don't forget that Let's Encrypt is US-based and monopolies-backed. They're not a charity, not a nonprofit either. They have motivations that aren't altruistic and we know who pays the salaries (not friends and allies of privacy, sometimes foes of it). They call themselves "[a] nonprofit Certificate Authority providing TLS certificates to 225 million websites." The Linux Foundation also calls itself "nonprofit", but we know that's a lie.
The encrypted systems specialist said he "[had] forgot[ten] to mention one other big point. The fact you can't block CAs in your browser and certain certificates is evidence enough of the malice behind the design and implementation of the web today."
The incidents of March (earlier this year) could be seen as an eye-opener. They never bothered explaining why they had issued millions of bad certificates, which they later revoked; they didn't explain what actually caused this incident and what was done about it.
As a side note, the SELinux project of Red Hat (now IBM) used to issue monthly declarations about no government interventions/involvement. Those stopped years ago. What is it they say about canaries?
"I have never seen any letsencrypt documentation say they have canaries," oiaohm wrote this morning, "and if you know USA law on the matter canaries is basically false. One of the USA encrypted email systems that is shutdown now had canaries and when the NSA with NSL stepped in they were forbid from using them. So their end users knew nothing."
A lot more discussion regarding this issue can be found in tomorrow's IRC logs. ⬆
Comments
Canta
2020-11-07 20:32:09
I agree with mostly everything. Specially the part about monopoly and CAs, and most specially about the stupidity behind "not trusting self signed certs". Yet, please consider this other argument.
When Let's Encrypt started, there was a debate about the gratis side of its certificates. "Why are those free, when people had to pay dozens or hundreds of dollars until today?". And there I saw something argued about two different functionalities for the certificates: the first one was the encryption, but the other was the identity certification. And falsing identity was a crime, and so there are economical penalties involved, and that's the part where money comes in: CAs has to pay under certain circunstances, and they work kinda like insurance for some legal issues. Let's Encrypt side of the debate said, basically, "screw identity certification, we're just encrypting, as we want everything encrypted".
If what I say is true, then Let's Encrypt is actually a force for good: because thanks to "standarized gratis certs", even when monopolized, it doesn't just break apart the need for money, but also renders the CAs absolutely irrelevant in 99.9% of the web. And so we can now talk about self signed certificates as the most basic common sense: Let's Encrypt, a CA, is also irrelevant, because "we just want encryption".
Banks, goverment, and other sensible organizations, may still need CAs. I disagree with the "trust providers are idiotic", as there are legit real life scenarios where trust providers are a decent idea (we use that in my country when you buy a house from someone, for example). Yet, it's most likely out of place when talking about stuff like having my personal blog online (unless I'm some kind of VIP, and my identity matters somehow).
So... we should be asking browsers to accept self-signed certs without ugly warnings. Lots of big tech players will agree with this, as they don't like to update hardware or depend on third parties. Let's Encrypt will die of irrelevance after that happens. And if that doesn't ever happen, then we all know what will happen: Let's Encrypt will start to behave like asses trying to exploit their monopoly, but gratis certs will be already the norm, and so others will start to also give gratis certs.
Therefore, I don't see the big deal with Let's Encrypt, monopoly or not, and I see it more like a force positive for CAs obsolescense. Now, thanks in part to Let's Encrypt, is a good time to ask for CAs removal from the game.