02.06.14
Posted in Free/Libre Software at 6:13 am by Dr. Roy Schestowitz
Summary: Phones and tablets with Firefox OS are said to be on their way and Firefox 27 is out
Mozilla has just released Firefox 27 [1,2], which is quickly improving owing to expansion features [3,4] (I find it a little buggy under Android, still). Firefox OS, which is based on Linux, has been making headlines and it is still coming along nicely [5] while Mozilla asks for help in delivering a tablet with Firefox OS [6]. To Mozilla’s credit, as we noted before, the company throws the P word around quite a lot (privacy is the P word), even in NPR [7]. Some readers noted that Mozilla is actually just pretending to care about privacy, but compared to Google, Apple, and especially Microsoft, Mozilla has shown a good track record on privacy. Sure, it relies to some degree on advertisers and Google, but Mozilla itself is not doing the spying. Moreover, it provides tools for blocking surveillance, even as part of the browser’s core. █
Related/contextual items from the news:
-
-
There are 13 security advisories attached to the Firefox 27 release, four of them ranked as being critical. As is common in nearly all Firefox release updates, one of the critical updates is for a group of vulnerabilities that Mozilla labels “Miscellaneous memory safety hazards.”
-
-
-
The smartphone is currently dominated by two big systems; Android and iOS. But there are others in the run. With Microsoft struggling to get anyone to voluntarily use Windows Phone, maybe Sailfish OS, Ubuntu Touch and/or Firefox OS will make a difference. It’s this last one I attended a talk about at FOSDEM. So here it goes; The current state of Firefox OS, and what we can expect for the future.
-
The Consumer Electronics Show (CES) took place recently in Las Vegas, and Mozilla officials made headlines there as they revealed plans to take the Firefox OS mobile platform to devices other than smartphones, and a new deal between Panasonic and Mozilla to drive smart, HTML 5-fluent televisions. It’s all part of Mozilla’s ongoing effort to focus on mobile technology and new platforms.
-
The scandal over NSA snooping has caused many adverse reactions, but one of the more notable ones has just come from Mozilla’s chief privacy officer Alex Fowler. Speaking with NPR, with the interview coming just after President Obama’s public comments about government surveillance reform, Fowler said that the threat of a balkanized Internet is real. And indeed, some countries are proposing limitations on Internet use that would effectively keep users dealing with information produced within their own countries’ borders.
Permalink
 Send this to a friend
Send this to a friend
Posted in Red Hat, Security at 6:00 am by Dr. Roy Schestowitz
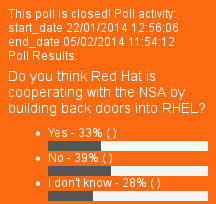
Summary: News about Red Hat, including renewed suspicions that the company is too close to the NSA, not merely a business partner
wE BEGAN writing about Red Hat and NSA as its major client only a few months ago [1,2], mainly because we had found a claim by Red Hat staff that patches from the NSA were being passed to Torvalds via Red Hat. We later had that confirmed by Red Hat staff. This definitely does not inspire confidence because we already know that the NSA wanted to put back doors in Linux.
The latest such post about Red Hat and the NSA comes from FOSS Force, where Christine concludes: “If Red Hat isn’t working hand-in-hand with the NSA in its efforts to spy on us, then this poll obviously represents a public relations problem for the Raleigh, North Carolina based company. Although it’s doubtful that many, if any, of those taking this poll are Red Hat customers, we can only assume that results such as we’re seeing here indicate a potential problem of perception even outside the free software community. It wouldn’t bode well for Red Hat if these sentiments were to spread to include it’s user base.”
Christine is being very kind to Red Hat. She may be right, but many of her readers seem to agree that Red Hat could have been used by the NSA for back doors. Less than 40% trust Red Hat.
In other news about Red Hat (more positive news), here are the latest press releases, which barely received any press coverage:
News about Red Hat also still revolves around CentOS (the CentOS news is old, but it’s still abound [1]), OpenStack [2,3,4], or ‘cloud’, which usually means surveillance-friendly setups, sometimes with CIA in the loop [5]. Virtualisation too is in Red Hat’s pitch [6,7,8], not to mention Red Hat staff [9]. There seems to be a recruitment drive in Red Hat’s OpenSource.com, with emphasis on women this month [10-17]. Only one other site [18] seems to have dedicated an article to women in FOSS/software in the same period of time. There is nothing wrong with that, it’s just an observation.
The bottom line is this: we need clarifications from Red Hat where it matters. The silence on this matter has been deafening and if Red Hat says nothing to alleviate these worries, then this may actually contribute further to distrust. Red Hat is developing many core components in GNU/Linux systems and when NSA is using Red Hat to submit patches (created by the NSA) we do need some reassurances. It’s not just SELinux. Red Hat should identify very clearly which patches have come from the NSA so that extra scrutiny can be applied. Knowing what the NSA has done to NIST, RSA etc. it would also be wise to ostracise the NSA when it comes to patches. █
Related/contextual items from the news:
-
-
Among the several reasons for Red Hat to embrace CentOS, its erstwhile copycatting nemesis, one explanation has largely been overlooked: The cloud made them do it. More specifically, OpenStack made them do it.
Red Hat had all but sewn up the market for Linux in the data center. But in the cloud, the market for Linux is both wide open—and perhaps nonexistent.
-
-
If the advent of object-based storage à la OpenStack Swift is one sign of the decline of traditional storage technologies, the momentum of software-defined storage is yet more evidence that the future of data storage for the cloud and the enterprise is changing. And open source giant Red Hat (RHT) is the latest vendor to jump on board, with the announcement of new software-defined storage options for Red Hat partners that could have a wide impact across the channel.
-
-
-
-
The RHEV 3.3 release is built on top of the open-source oVirt project, which is led by Red Hat. The new release adds support for the Red Hat Enterprise Linux 6.5 platform, improves performance and supports a wider array of systems.
-
I believe that the open source community as a whole would benefit if more open source developers considered the API and associated bindings as primary and the CLI as of secondary importance. Ideally, applications would be designed from the start with a well-defined API, a set of bindings that evolved with the API, and a CLI (if one was necessary) that was defined in a scripting language that made use of the bindings. Not only would this make the application ripe for automation, but it would likely have the added benefit of making the API better defined and more robust.
-
There are few women developers and even proportionately less working in open source communities. However, a career in OSS is ideal for women who are seeking balance in their lives whether the balance is starting a family or maintaining balance with friends and a strenuous and engaging hobby. It’s well established that there’s a shortage of women pursuing careers in computer science. UCLA’s Higher Education Research Institute found that just 0.3% of students majoring in technology-related fields are female, despite the high demand for those skills. As few as 1.5% of open source contributors are women.
-
Marie Nordin is one of the OPW interns for the Fedora Project. She is the visual designer currently in charge of badge design for Fedora Badges, an open badges based web application that helps to encourage contributors in the Fedora community by awarding them with badges for their efforts. (For example, Marie is the proud recipient of the “Pixel Ninja” badge for her work on the Fedora Design team.) I interviewed Marie, and she shared how she came to open source, what open source projects she’s currently involved with, and her advice for other young women interested in getting involved.
-
In the open source world, a women-only event seems counter-intuitive. Yet I am finding reasons for such events the more I attend them.
At the OpenStack Summit, a twice-a-year event where OpenStack contributors get together to plan the next release, the Women of OpenStack group has set up events where we invite the women first. Men aren’t excluded, but our hope is to get more OpenStack women together. I can hardly capture the value of getting together with other women in OpenStack at the Summit, but here goes.
-
We’re familiar with the statistics, and we’ve seen the photos from the tech conferences. Seas full of men. It requires patience to scan for the odd female in those auditoriums. It’s a popular topic, this scarcity of women in technology, one of the hip things to whine about these days. It’s politically correct to blame the male “priesthood” in Silicon Valley. Ask Paul Graham. He took it in the ribs after a few reckless comments about the funding practices of his startup seed accelerator, Y Combinator. He was quoted as saying, “God knows what you would do to get 13 year old girls interested in computers. I would have to stop and think about that,” in a recent article. Ouch. But, really, is he so wrong?
-
The Joomla! community, inside and outside the company, is diverse and multi-cultural. It is made up of all sorts of people with two things in common: a love for Joomla! and a willingness to reach out and help others on the other side of the keyboard.
-
-
Whether the big media producers like it or not, digital technologies have made it easier than ever for popular culture fans to create remixes or derivative works from their favorite movies, TV shows, books, and other media. And the participatory nature of the Internet has arguably helped broaden the popular definition of a “fan community” from something exclusive to comic and sci-fi fans to being inclusive of many genres and people. This includes giving wider exposure to a vast and yet often overlooked demographic in pop fandom—women—and their influence on mainstream media stories.
-
Women use the Internet 17% more than their male counterparts yet are underrepresented in programming and open source. Public libraries (and public schools) have a critical role to play with improving the dearth of diversity in coding and open source.
-
December 2013′s EOF, titled “Mars Needs Women”, visited an interesting fact: that the male/female ratio among Linux Journal readers, and Linux kernel developers, is so lopsided (male high, female low) that graphing it would produce a near-vertical line. I was hoping the piece would invite a Linux hacker on the female side of that graph to step up and move the conversation forward. And sure enough, here we have Susan Sons aka @HedgeMage.
Permalink
 Send this to a friend
Send this to a friend
Posted in Law at 5:17 am by Dr. Roy Schestowitz
Summary: Today’s and yesterday’s news items about mass surveillance and abuse
-
British intelligence ran denial-of-service attacks against chatrooms used by Anonymous and LulzSec, according to an investigation by NBC News involving Snowden confidante Glenn Greenwald.
-
-
In recent years we’ve learned that the FBI has no problem with using informants to organise, encourage, and assist computer hacking at a global level, and now it seems GCHQ has been in on the double-standards game too: launching Distributed Denial of Service (DDoS) attacks against chat servers hosted by Anonymous in 2010/2011 in order to scare off supporters of the movement.
-
Earlier today, we wrote about the latest Snowden docs, in which it was revealed that the UK spy agency, GCHQ, was engaged in DDoS attacks on people participating in Anonymous chats and other events, while also helping to identify certain participants, leading to their eventual arrests and convictions. Basically, it looks like GCHQ was engaged in widespread DDoSing, while at the same time helping to convict some kids for doing their own DDoSing. We’ve already questioned whether or not GCHQ is even supposed to be doing that to UK citizens (they’re supposed to be focused on foreign targets), but some of those convicted are already questioning how it’s right that they were convicted of the same thing that the GCHQ itself was doing to them.
-
As Americans have grown increasingly comfortable with traditional surveillance cameras, a new, far more powerful generation is being quietly deployed that can track every vehicle and person across an area the size of a small city, for several hours at a time. Although these cameras can’t read license plates or see faces, they provide such a wealth of data that police, businesses and even private individuals can use them to help identify people and track their movements.
-
-
Whistleblower Edward Snowden’s revelations have revealed that a huge capability resides within America’s National Security Agency to collect and analyse communications.
-
After closely following the National Security Agency story for two years (16+ months before anyone ever heard the name, Edward Snowden), I can honestly say that blogger and journalist Marcy Wheeler’s real-time coverage of this incredible chapter in the Orwellian history of our nation’s clandestine underbelly blows the doors off of virtually everyone (as she’s again reminding us, in multiple stories over the past day), in terms of her intensive and incisive analysis of the hard information and public statements that are being released by our government in the wake of the Snowden document leaks this past June.
-
At least four different Senate committees have jurisdiction over the leaks by former NSA contractor Edward Snowden — and now Sen. John McCain (R-Ariz.) wants to create one committee to rule them all.
McCain introduced legislation on Tuesday that would create a special new committee to investigate the NSA. He has been calling for the creation of such a committee since October, and the resolution is his first concrete step toward that goal.
-
-
Glenn Greenwald and three other journalists who were the first to report on whistleblower Edward Snowden’s leaked NSA files will receive a George Polk award for their work. That’s according to a source familiar with the plans to award the prestigious prize later this month.
-
Whoever suggests the Snowden revelations mean nothing to the lives of ordinary black people either isn’t paying close attention, or is working for the police and prison state. The federal DEA, the Justice Department’s federal drug police, have passed tons illegal NSA spying data to local police agencies and cynically coached them to lie about the sources of their evidence. It’s not exaggeration or hype. You can view the manuals online for yourself.
-
Apple co-founder Steve Wozniak says he has sympathy for companies at odds with the NSA and its surveillance tactics, but that their own dependence on server farms is part of the problem.
“I think most companies, just like Apple, start out young and idealistic,” Wozniak said at the Apps World North America convention here. “But now all these companies are going to the cloud. And with the cloud you don’t have any control.”
-
Citing worries about foreign surveillance efforts, the government of Switzerland has ordered tighter control methods on its own computer and phone technology systems in order to prevent Swiss communications from being monitored.
-
Since the revelations about the NSA from Edward Snowden’s leaks last year, Representative Jim Sensenbrenner, who authored the Patriot Act, has come out in opposition to certain NSA surveillance practices, particularly bulk collection of Americans’ telephone metadata.
-
-
For a long time Verizon was dead silent regarding their cooperation with the NSA, with the only public comment at one point being to mock Yahoo and Google for demanding greater government transparency. R
-
A flurry of new reports from major technology companies show that the government collects customer information on tens of thousands of Americans every six months as part of secret national security investigations. And the companies’ top lawyers struck a combative stance, saying the Obama administrative needs to provide more transparency about its data collection.
-
Last week, the ACLU joined a constitutional challenge to the FISA Amendments Act of 2008 (FAA), the statute that allows the NSA to engage in dragnet surveillance of Americans’ international phone calls and emails. With the Federal Defenders Office, we filed a motion on behalf of Jamshid Muhtorov, the first criminal defendant to receive notice that he had been monitored under this controversial spying law. But Mr. Muhtorov received this notice only after the Department of Justice (DOJ) abandoned its previous policy of concealing FAA surveillance in criminal cases — a policy that violated both the statute itself and defendants’ due process rights.
-
Revelations of National Security Agency surveillance programs have prompted state lawmakers around the United States to propose bills to curtail the powers of law enforcement to monitor and track citizens.
-
Angry over revelations of National Security Agency surveillance and frustrated with what they consider outdated digital privacy laws, state lawmakers around the nation are proposing bills to curtail the powers of law enforcement to monitor and track citizens.
-
“There is nothing to fear but fear itself.” Franklin D. Roosevelt was upholding the wisdom of our founding fathers. But we have governed our country by the opposite creed since 9/11.
-
-
Based upon the disturbing revelations of the NSA power abuse that continue to come into the light of transparency, it is clear that significant changes and controls need to be made in how the NSA is allowed to conduct business.
-
Last month, former Congressman Otis Pike died, and no one seemed to notice or care. That’s scary, because Pike led the House’s most intensive and threatening hearings into US intelligence community abuses, far more radical and revealing than the better-known Church Committee’s Senate hearings that took place at the same time. That Pike could die today in total obscurity, during the peak of the Snowden NSA scandal, is, as they say, a “teachable moment” —one probably not lost on today’s already spineless political class.
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 4:59 am by Dr. Roy Schestowitz
-
Hot on the heels of the first CryEngine game Kingdom Come: Deliverance to support Linux, Linux just got another game in its steadily increasing repertory of big-budget games. This time too it is an open world RPG game named Cradle. The game is being developed by Pittsburg based Mojo Game Studios, founded by students of Carnegie Melon University. The game has been in development for a year and has now been put up on Kickstarter to secure the target funding of $350,000 in 17 days. It has also managed to secure a pledge of $75k, so the situation is looking quite plausible for it to secure the necessary funding within the time limit.
-
Hotline Miami 2: Wrong Number, the highly anticipated sequel to the blood splattered and gory game Hotline Miami, will be released sometime around the third quarter of 2014. This bit of news comes from the official Twitter account of the gory top-down shooter.
-
-
-
-
The Steam Music Beta is coming soon to Big Picture and SteamOS interfaces, with desktop features soon to follow. To express interest in beta participation, join the Steam Music community group. Group members will be invited in waves, until the feature is released to everyone.
-
This will please big picture mode users and SteamOS/Steam Machine users alike, Steam is planning to add music controls built-in to Steam itself allow you to control music while gaming.
-
In-Home Streaming was part of the SteamOS announcement Valve made back in September and beta invites to the functionality have been sent to some people around the internet. Luckily I was part of that group and I can share some of it with you!
-
-
-
-
When Valve announced Steam Machines, many were concerned about the slew of different models that will be available to consumers. With so many different options and price schemes, it seems as though it may be bit muddled and perhaps problematic for Valve’s new software platform.
-
PC World explores the benefits of Steam’s beta game streaming to ancient computers that can now be used for gaming.
-
-
Linux has a prodigious library of free games many of which are released under an open source license. A large proportion of these open source games are eye catching. Popular games often have full motion video, vector graphics, 3D graphics, realistic 3D rendering, animation, texturing, a physics engine, and much more. Early computer games did not have these graphic techniques. The earliest video games were text games or text-based games that used text characters rather than vector or bitmapped graphics.
-
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 4:51 am by Dr. Roy Schestowitz
-
-
One of the amazing things about Linux is the fact that there is always something new out there to learn. A new package manager, a different desktop environment, a different philosophy, a completely different ethos.
-
FTP stands for ‘File Transfer Protocol‘ is one of the most widely used and standard protocol available over Internet. FTP works in a Server/Client architecture and is used to transfer file. Initially FTP client were command-line based. Now most of the platform comes bundled with FTP client and server program and a lot of FTP Client/Server Program is available. Here we are presenting 10 Interview Questions based on Vsftp (Very Secure File Transfer Protocol) on a Linux Server.
-
At the moment, the uTorrent server for Linux only has a web-based user interface that doesn’t allow users to click magnet links in web pages in order to add them to the download queue. So, if GuTorrent becomes reality, it will be the first ever graphical client for the uTorrent server, a.k.a. the first ever uTorrent client for Linux.
-
Maxthon Cloud Browser for Linux is not yet an official release, as it’s still in development, and it resides on the official Maxthon forums for the moment, where users can grab the latest Beta versions. It’s easily installable on Debian, Red Hat and other Linux operating systems, especially Arch Linux users, as a package is already available in AUR.
Permalink
 Send this to a friend
Send this to a friend
02.05.14
Posted in Deception, Marketing, Microsoft, Patents at 7:28 pm by Dr. Roy Schestowitz
Summary: A closer look and briefer analysis (than most) of people whom Microsoft is grooming amid perception-altering appointments
Analysis of the press release from Microsoft has been shallow and promotional. Watch out for bogus ‘reporting’ from Microsoft boosters like Peter ‘Bright’, to give just one example among hundreds or thousands jaw-dropping puff pieces. Even some Microsoft-hostile circles have offered too week a scrutiny, if any at all. Let’s sum up what it’s all about (and it’s mostly marketing, not real news).
Microsoft has a new racketeer in chief, overseeing patent extortion along with Horacio while putting a ‘gentle’ face on it. It is all just a rebranding exercise — a familiar old trick that the company behind Kin and Vista is known for. This is a persona routine that marketing companies are renowned for and villains/abusers like BP or Monsanto are (in)famous for.
Also joining the leadership is the man best known for his leadership in GNU/Linux foe Symantec and his role in Seagate, a company sometimes known for its NSA connections just like Microsoft (those three are all connected, or even four if Symantec gets counted because Seagate preinstalls Microsoft software on drives and Symantec profits from Windows). As a timely side note, avoid Seagate. They are absolutely horrible, both technically (based on new studies [1, 2]) and ethically. Today I had to print labels at a high price at some shop to send back my faulty drive to Segate (Netherlands); they shipped me a faulty drive to replace another drive that had gone faulty. Seagate is garbage.
Last but not least, Microsoft boasts the involvement of serial felon, tax evader and patent booster, who is making money by charging taxpayers for his patents against their will and through governments (as an investor in Wal-Mart, for example, his quickly-growing money hoard is at least partly funded by taxpayers, as Wal-Mart itself admits [1]).
Based on what seems like a satirical piece about Vista 8, this man who joked about Vista being crappy (video from Homer) is now complaining about Vista. To quote Homer’s analysis of the satirical piece: “Bill Gates’ first day at work in the newly created role of technology adviser got off to a rocky start yesterday as the Microsoft founder struggled for hours to install the Windows 8.1 upgrade.
“The installation hit a snag early on, sources said, when Mr. Gates repeatedly received an error message informing him that his PC ran into a problem that it could not handle and needed to restart.
“After failing to install the upgrade by lunchtime, Mr. Gates summoned the new Microsoft C.E.O. Satya Nadella, who attempted to help him with the installation, but with no success.
As Will Hill points out: “Sadly, satire: PR for Gates and advertisement for Vista 7.”
This is pretty much all over the press these days: whitewash, humour, PR, and viral marketing. There was a similar story about Ballmer trying to get rid of a virus, requiring days of work and the help of several ‘engineers’. That was in Vista days, but in court documents it turned out that Ballmer and others really did struggle with Vista and expressed concerns.
Going back to Gates, it’s all decoy, distraction, and appeal to the press. So all we have here is one fake ‘charitable’ hoarder who increases his wealth by surveillance, private police thugs (G4S), GMO etc. and two people of ethnic minorities with proximity to NSA (Azure and Seagate). This is not change or reform, it’s just like the Obama speech about the NSA.
A week or so ago Microsoft booster Julie Bort was prolonging the myth of Microsoft as “an insanely profitable company” [2] when she said Microsoft should kick Gates out of the board. This reveals that Ballmer too will continue to be involved. So here we see that the architects of illegal activities still run Microsoft. Ballmer and Gates are to Microsoft what Clapper and Alexander have been to the NSA in recent years.
Remember that Gates has had a lot to do with Microsoft’s patent extortion strategy. Now that we learn about more patent deals [3] we should remember that there is nothing “gentle” or “charitable” at Microsoft. It’s the same ruthless people, including the man who was put on trial for business crimes and was arrested when he was young (to be bailed out by his affluent family). It’s all just marketing now.
“The new patent cross-licensing agreement is designed to protect both companies from patent lawsuits,” says the Microsoft booster about Google and Cisco. What a classic mischaracterisation of patents.
Where is the criticism of Gates for rackeetering? Where are the good investigative articles from Wired, which nowadays (on a weekly basis) seems to be acting as Gates’ private perception management journal? █
Related/contextual items from the news:
-
Walmart has been in the national spotlight for their poverty wages and employees’ reliance on government assistance. In their quarterly report, Walmart is set to announce that their profits have taken a hit. In a moment of rare honesty, they cited the Republican funding cut to the federal food stamp (SNAP) program as a part of the reason for their lower profit margins, admitting that the federal food stamp program amounts to corporate welfare that subsidizes their profits.
-
Microsoft is an insanely profitable company standing on the edge of disaster. It desperately needs new thinking.
With word that 22-year Microsoft veteran Satya Nadella is likely the new CEO, attention turns to the leadership of the company’s board of directors. It will have two former CEOs, Bill Gates and Steve Ballmer.
So new thinking is unlikely to come from them.
-
Permalink
 Send this to a friend
Send this to a friend
Posted in Law at 6:22 am by Dr. Roy Schestowitz
Summary: The latest reports which uncover misconduct at NSA and its accomplices around the world
-
Google, Facebook, Microsoft and LinkedIn all made headlines today for releasing “transparency” reports about the number of users for which the U.S. government has requested data.
We now know that major Internet companies have given up personal information from between 0-15,999 user accounts, but we don’t know what exactly was given up or whether additional data was taken without the companies’ knowledge.
-
The revelations, leaks, and laws of the last few years, from warrantless wiretapping and Edward Snowden to laws like SOPA, ACTA, and now the president’s attempt to fast track TPP, have painted a portrait of a superpower increasingly at war with the net. But people like the net, they live more and more of their lives on the net, which makes this conflict politically difficult and confusing.
-
“How can they get away with that?” said Ms. Frizzell, who works in Bergheim, Texas.
In what appears to be an unintended side effect of Staples’ pricing methods—likely a function of retail competition with its rivals—the Journal’s testing also showed that areas that tended to see the discounted prices had a higher average income than areas that tended to see higher prices.
-
I have to admit that I’m consistently amazed at just how badly law enforcement in both the US and New Zealand appeared to screw up the raid and the case against Kim Dotcom. I’ve said it a few times before, but it really feels like authorities in both places actually believed the bogus Hollywood hype being spread by the MPAA about how Dotcom was really a James Bondian-villain, and acted accordingly, while ignoring any evidence to the contrary. As you know by now, the New Zealand equivalent of the NSA, the GCSB, illegally spied on Kim Dotcom and other New Zealand residents and citizens — and the New Zealand government then decided to try to hide that. While the police agreed that the spying was illegal, they declined to do anything about it, so Dotcom sued the government himself.
-
A document leaked by Edward Snowden, along with interviews with lawyers representing terrorism suspects, reveal a disturbing loophole in this once-sacred legal principle.
-
As a graduate student at the Massachusetts Institute of Technology in 1996, Amit Sahai was fascinated by the strange notion of a “zero-knowledge” proof, a type of mathematical protocol for convincing someone that something is true without revealing any details of why it is true. As Sahai mulled over this counterintuitive concept, it led him to consider an even more daring notion: What if it were possible to mask the inner workings not just of a proof, but of a computer program, so that people could use the program without being able to figure out how it worked?
-
“I think Mr. Snowden did a great service to humankind,” said Gonzalo Velasco C. “He confirmed something many ‘crazy geeks’ have been saying for years. The countries that have denied him political asylum are to be remembered as cowards.” Nobel prizes are “not only about the real merit — we have seen former war-makers get a peace price! But I doubt he is going to get this one.”
-
Mr Schroeder said he was unsurprised by the latest US spying revelation
-
Schröder, the Social Democrat chancellor who served from 1998 to 2005, appears on a list of names of people and institutions put under surveillance by the US National Security Agency (NSA) from 2002, at the start of his second mandate as German head of state.
-
German media say Angela Merkel’s predecessor was put under surveillance after opposition to military action in Iraq in 2002
-
Shenna Bellows outraised Collins in the last quarter of 2013, raking in $331,454, compared with the $314,921 raised by Collins during the same period, according to filings made with the Federal Election Commission. The margin is slight, but it’s noteworthy in part for Bellows’s vocal stance against the National Security Agency’s surveillance programs, which she derides as unconstitutional.
-
Lots of children play games and use toys related to adult careers: cops and robbers, spaceman, Operation, among many others. Playing in this manner teaches children about different jobs and inspires them to want to become doctors, cops or actors.
-
Of course, looking into it doesn’t mean very much at this point. There had been serious concerns about how the NSA and GCHQ used the attacks on Belgacom to then bug systems at the EU Parliament in Brussels. Whether or not they’ll do something in response to “just” hacking a cryptographer remains to be seen — but it should remind basically everyone in the world that the NSA/GCHQ don’t seem to have any hesitation about hacking just about anyone.
-
Arizona’s state senate panel approved a bill withdrawing state support for intelligence agencies’ collection of metadata and banning the use of warrantless data in courts. The panel becomes the first legislative body in US to try and thwart NSA spying.
The bill will now have to be approved by majority of the Senate Rules committee before it can move on to the full senate. It prohibits Arizona public employees and departments from helping intelligence agencies collect records of phone-calls and emails, as well as metadata (information on where and when the phone calls were made).
-
Fresh disclosures about national security requests indicate that Yahoo was ordered to hand over content from more accounts than other tech firms during the first six months of 2013.
-
The US National Security Agency likely collects intelligence on congressional lawmakers and members of their staff, a Justice Department official admitted at a committee hearing on Tuesday.
-
Judiciary committee warns Obama administration to back USA Freedom Act or risk losing its counter-terrorism powers
-
Rep. Mike Rogers (R-MI) has been very unhappy about the leaks by former NSA contractor Edward Snowden from the very beginning. Now the head of the powerful House Intelligence Committee has become one of several personalities at the heart of the NSA leak scandal to lash out at one of the journalists publishing stories about the documents.
-
Permalink
 Send this to a friend
Send this to a friend


















 Content is available under CC-BY-SA
Content is available under CC-BY-SA