11.03.13
Posted in Action at 3:28 pm by Dr. Roy Schestowitz

Summary: How Edward Snowden’s download (copying) of an untold number of unspecified documents (from Microsoft SharePoint) enables everyone in the NSA to leak more documents and attribute this to Snowden (who enjoys asylum)
HERE in Britain, Bonfire Night is already being celebrated by some people. Many let loose their fireworks during the weekend, just before the actual night which is when people work (it’s not a national holiday), so there are explosions outside as I write this. Bonfire Night is about Guy Fawkes, which became famous for the mask of Anonymous, the collective of online activists. Anonymity is a valuable tool for activists. If people can do particular actions without being held accountable for these actions, then that can be used for bad (trolling/cracking) but also for good (whistleblowing/retribution against power). Some — especially the rich and the powerful — try to use the bad cases in order to ban the latter. It helps them keep their power and it helps them keep secret their abuses (if any).
“In a sense, Snowden would be a perfect ‘mask’ for anonymous whistleblowers.”Earlier today, Asher Wolf and many other activists retweeted me saying “Perhaps #snowden is becoming the real-life Guy Fawkes, the anonymous persona through which anonymous leakers claim leaks to have come from” (source).
For context see [1,2] as it suggests that the NSA now has several unknown leakers, whose leaked documents probably get attributed to Snowden in order to protect their jobs. In a sense, Snowden would be a perfect ‘mask’ for anonymous whistleblowers. The NSA does not really know what documents Snowden downloaded to leak to the press (Microsoft SharePoint logging must be defunct), so anything which leaks from the NSA can just be assumed — even wrongly — to have come from Snowden. Suffice to say, it leaves the NSA even more vulnerable. There can be dozens of leakers still working for the NSA, but the NSA cannot know if that’s the case and thus it cannot find out who they are. Snowden gives them the perfect cover. Each NSA whistleblower can just say “I am Edward Snowden” and get away with it when it’s published, leading to another reforming scandal. Maybe one say privacy can be restored thanks to Snowden’s actions [3]. █
Related/contextual items from the news:
-
Jesselyn Radack is a civil liberties attorney with the Government Accountability Project who has been in contact with Edward Snowden. In an ABC News interview, she reported that other NSA insiders have been inspired by Snowden’s bravery and sacrifice and have come forward with further revelations about the organization’s excess, criminality and lawlessness. She says that the Obama administration’s war on whistleblowers has backfired, squandering the administration’s credibility with its own operatives and inspiring them to speak out.
-
But the legal threats and high-level condemnation haven’t kept others from coming forward with new information, Radack said.
“There definitely could be more revelations in addition to those that Snowden has revealed and that are continuing to come out,” she told ABC News.
-
The steady trickle of revelations of government snooping that continues to seep from the Edward Snowden documents is serving to keep attention riveted on how privacy in the digital age ought to be defined.
That’ most probably not to the liking of Google and Facebook. In January 2010, Facebook founder and CEO Mark Zuckerberg infamously declared that the expectation of privacy was no longer a social norm, and, in October 2010, then Google chairman Eric Schmidt said “Google policy is to get right up to the creepy line and not cross it.”
Permalink
 Send this to a friend
Send this to a friend
Posted in Action at 2:54 pm by Dr. Roy Schestowitz

Image credit: AP Photo/Eraldo Peres
Summary: The UK is cheapening terrorism by just equating it with investigative journalism that looks into abuses of international laws
Without independent media, we cannot enforce a law that's adhering to justice as an uninformed public becomes too weak to speak out against those in power (they can rewrite the law to legalise their injustices). Here in the UK we have a chilling war on journalism right now [1, 2, 3, 4, 5]. Threats are being sent to journalists by our ‘elected’ officials and hard-drives are being destroyed on demand for political reasons.
“Threats are being sent to journalists by our ‘elected’ officials and hard-drives are being destroyed on demand for political reasons.”An MI5 whistleblower, the ‘British Snowden’ as some might prefer to refer to her, speaks about the lack of spy oversight [1]. Basically, if you make it illegal to report about spies, then you make it impossible for the public to scrutinise those spies when they break ethical guidelines, violate the law, or put to shame the original contracts that legitimise their budget (taxpayers’ money). The BBC World Service, not a Russian media outlet for a change, gave this ‘British Snowden’ a platform (or a “propaganda platform” as the US State Department might call it).
The latest news from the Snowden saga is that David Miranda, the partner of Glenn Greenwald (Assange equivalent), has been harassed for political reasons [2,3]. Great move, Cameron et al.
A few months ago, after passing the passport control area in Manchester Airport I was hanging around for a bit near two offices used for interrogating people under the pretext of “terrorism”. The doors had a notice on them, alluding to this law which facilitated a vague process as means of “counter terrorism”. It’s a fairly new process. Terrorism as it is described in the media (synonymised these days with radical Islamisation) is not a new thing; what’s new are the laws and the retribution, e.g. drone strikes, long/indefinite detainment without charges, torture for false confessions to be derived, etc. In Britain we had issues with the IRA too, but the same type of actions by Irish militants/extremists did not facilitate harassment of journalists and their family members who are in transit in airports. For the term “terrorist” to be applicable at all, as per the definition of the word, physical violence must be involved. Trying to label leakers and/or their publishers “terrorists” is to merely cheapen the term and over time make it virtually meaningless, just like the term “pirates”. █
Related/contextual items from the news:
-
-
Security services in the United Kingdom have accused David Miranda, the husband of journalist Glenn Greenwald, of being “involved in espionage activity” when he traveled from Berlin to Heathrow Airport on his way back to Brazil, where he lives with Greenwald.
-
The detention of the partner of a former Guardian journalist has triggered fresh concerns after it emerged that a key reason cited by police for holding him under terrorism powers was the belief that he was promoting a “political or ideological cause”.
The revelation has alarmed leading human rights groups and a Tory MP, who said the justification appeared to be without foundation and threatened to have damaging consequences for investigative journalism.
David Miranda is the partner of Glenn Greenwald, the journalist who – often in collaboration with the Guardian – has broken many stories about the extent and scope of spying by the US National Security Agency. Miranda was stopped at Heathrow airport in August and held by the Metropolitan police for nine hours while on his way home to Brazil.
Miranda, it has been claimed, was carrying some 58,000 encrypted UK intelligence documents. He had spent a week in Berlin visiting a journalist, Laura Poitras, who has worked with Greenwald on many of his stories, which have been based on information leaked by the former NSA contractor Edward Snowden.
[...]
Greenwald was equally scathing, tweeting: “UK govt beats its mighty chest, now explicitly equates journalism with ‘terrorism’ and ‘espionage’.”
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, FSF at 2:18 pm by Dr. Roy Schestowitz

Summary: The “DarkMail Alliance” is announced and other options emerge as freedom- and privacy-respecting means of electronic communication
WITH the exception of some projects like Ubuntu, Free software tends to respect users’ privacy and if it doesn’t, then those users can modify the software to remove privacy-violating code (as some Ubuntu derivatives typically do). The NSA scandal received some special coverage in LinuxCon Europe [1] because it is very relevant to GNU/Linux users. There were attempts to put back doors in Linux.
The founder of the FSFE, who moved on to Kolab some years ago, is now using Switzerland’s unique privacy policies to offer users privacy-respecting and freedom-respecting E-mail [2]. He is not alone. There are several companies, including one of the PGP founder (original developer), which now use the demand for privacy-respecting E-mail to create secure alternatives [3,4] (“DarkMail Alliance”). A month from now in Manchester we’ll also have a CryptoParty with the FSFE, helping people configure their machines for improved privacy. My wife and I will be there for help.
The bottom line is, in this age of Microsoft collusion with the NSA we have some very strong arguments with which to persuade people to embrace Free/libre software. It is about human dignity, not just the ability to modify source code, dodge abusive monopolies, and of course save money. My wife, for example, happily uses KDE and Android, knowing that GNU/Linux is now only technically superior to the alternatives but also more respectful towards her human rights. Techrights was recently designed with emphasis on privacy and the next few posts will deal with privacy alone. █
Related/contextual items from the news:
-
Today he is Chief Research Officer at F-Secure in Finland and a just-confirmed keynote speaker for LinuxCon/CloudOpen Europe taking place October 21-23, 2013 in Edinburgh. Hypponen will be talking about the biggest computer security story of the year, that of the NSA and PRISM, in a talk titled “Living in a Surveillance State.” He is also expected to talk about the role the Linux community can play in ensuring the security and privacy of the Internet and mobile devices.
-
-
Silent Circle CTO: “What we’re getting rid of is SMTP.”
-
Dark Mail will provide end-to-end encryption, including email metadata
-
Edward Snowden revelations of mass spying programmes such as PRISM and Tempora show that something needs to be done to protect our private online activities from the prying eyes of GCHQ and the NSA. There’s currently a great deal of interest surrounding these issues and as a result people are seeking to find tools which will help them protect and secure their email, instant messages and web browsing.
This can be done, to an extent, through the use of encryption technology, so on 7th December, we’ll be teaming up with Free Software Foundation Europe to organise a Cryptoparty in Manchester.
Permalink
 Send this to a friend
Send this to a friend
Posted in TechBytes Video at 1:50 pm by Dr. Roy Schestowitz

Direct download as Ogg (00:03:17, 10.8 MB)
Summary: Dr. Richard Stallman, the Free Software Foundation’s founder, speaks about injustices in the US penal system
Made entirely using Free/libre software, heavily compressed for performance on the Web at quality’s expense
Permalink
 Send this to a friend
Send this to a friend
11.01.13
Posted in GNU/Linux, Google at 10:47 am by Dr. Roy Schestowitz

Section of the Whitney umbrella, an example of pinch point singularity
Summary: Android pinches to unzoom Apple’s hypePhone, which was all about hype after all; competition within Android is growing
According to analysis from a Nokia observer [1], Apple is affected profoundly by the rise of Android, which is based on Linux as its kernel. The Nexus 5, with version “KitKat” of Android, is just one of the products that make hypePhone (‘iPhone’) seem overpriced and technically inferior [2]. Hardware support for Android is improving [3] and so are the applications [4,5] and functionality [6]. Security is reasonably strong [7] and Samsung, based on reports [8,9] wants to take Android to another level because there’s increasing competition (Samsung’s Ballnux has become quite expensive and Google helps partners like ASUS or its own Motorola). Little by little, as Android becomes the primary game in town, Apple is becoming the next Nokia. The big competition these days is among brands that sell Android, not between proprietary operating systems (definitely not as they are in the minority). █
Related/contextual items from the news:
-
-
The much hyped 24 October Google Play event turned out to be hoax by some blogger from Geek.com, but there is no doubt the next upgrade to Google’s Nexus phone is due. KitKat is already in work and this is that time of the year – just before the festival season when Google announces its new phones.
-
ARM announced an embedded version of its ARMv8 architecture that will add virtualization and lightweight Linux support to the next of generation Cortex-R processors. The ARMv8-R architecture is 32-bit, but borrows features from the 64-bit ARMv8-A such as hardware-based virtualization and a more advanced MPU, enabling safety-critical embedded applications like automotive computers to run RTOSes, bare metal code, and Linux and Android on a single processor.
-
-
-
-
Until now, Google hasn’t talked about malware on Android because it did not have the data or analytic platform to back its security claims. But that changed dramatically today when Google’s Android Security chief Adrian Ludwig reported data showing that less than an estimated 0.001% of app installations on Android are able to evade the system’s multi-layered defenses and cause harm to users. Android, built on an open innovation model, has quietly resisted the locked down, total control model spawned by decades of Windows malware. Ludwig spoke today at the Virus Bulletin conference in Berlin because he has the data to dispute the claims of pervasive Android malware threats.
-
-
New software tools and a developer confab highlight Samsung’s push to offer something different from all the other Android device makers. Think multiscreen.
Permalink
 Send this to a friend
Send this to a friend
Posted in GPL at 10:12 am by Dr. Roy Schestowitz
Brandon Bryant responsible for 1,626 assassinations without trial (many innocent civilians included)

Summary: How we can deal with problems of controversial or even criminal aggression when that aggression depends on Free software
SEVERAL software licences get notably criticised for having terms in them that explicitly ban use which may aid war/murder people. Linux uses the GPL, which has no such terms. The same goes for GNU.
We are increasingly made aware — even by the corporate press — of a previously-secret war waged by Linux-powered CIA-operated drones. This is one of the most disgusting wars in the world. People are being labeled based on electronic communications and then hunted down (without trial, without second assessment) by flying machines that shoot Hellfire missiles at cellphones owned by those people (so-called ‘militants’, which basically means adult males or old adolescents), never mind who’s around them at the time (just call them “human shields” after they’re dead). Nothing has increased doubt and hatred towards the United States like these dirty drone wars, which are about eliminating people almost autonomously rather than address the key issues (which may be ideological and thus addressable in other means). In Techrights alone, hundreds of daily links were posted to deal with this subject without delving into it so deeply. Contrariwise, a lot of the corporate press has helped cover up the atrocities (calling all who are killed “militants”) and parroted the Pentagon’s talking points, barely ever speaking to the people who are most affected by these drone strikes. Even this week — never mind the past few years — CNN tactlessly labels one of the murderers “American drone warrior” [1], even though he says his trainers reinforced the idea that this job was just “video game” (with real living targets).
After the war crimes in Iraq and beyond (Cheney is still not being arrested, let alone trialled [2]) we should know better the correlation between law and life. It’s not just about Arabs; the US did similar things to south Americans (see [3,4] in the news) when they had turf wars against the Soviets.
Software licences are a form of law and life is impacted by it to a great extent. One can authorise murdering people — even US citizens — without a trial in the US. That’s because laws got rewritten. The government carries out the murders with approval that goes all the way to the top (the White House and the juridical cornerstones). Software licences can be used as a tool against brutes, or at least a deterrent. If Microsoft Windows crashes drones into the ground, as it did before the US Army switched them to Linux, then that’s a good thing. It probably saves innocent lives. Let the proprietary software EULAs do the killing; use Free software licences to limit the actions of the cowardly assassins who sit down in air-conditioned offices, with or without a joystick in their hand (running a lethal, weaponised Linux-powered toy via satellite). Don’t let any of them portray themselves as victims (e.g. of “trauma”). They should be brave enough to confront families whose loves ones (mostly innocent people) they were blowing to pertinent bodyparts because they were “following orders” from CIA/NSA (they were free to quit this ‘job’ all along, nobody pointed a drone to their heads). █
Related/contextual items from the news:
-
The first time Brandon Bryant fired a Hellfire missile from his U.S. drone, it was a cold January day.
“His right leg was severed,” Bryant told CNN’s Hala Gorani, sitting in for Christiane Amanpour. “I watched him bleed out from his femoral artery.”
“It was shocking,” he said. “It’s pixelated, and it doesn’t really look real. But it was real.”
[...]
1
The “video game” aspect of his job was reinforced by his trainers, he said.
-
Richard Cheney, former Vice President of the United States of America is scheduled to speak in Toronto Ontario on 31 October 2013 at the Toronto Global Forum, hosted by the International Economic Forum of the Americas at the Metro Toronto Convention Centre.
-
Do the people of Honduras have the right to elect their own president and congress? That depends on whom you talk to. In 2009, the country’s left-of-center President Mel Zelaya was overthrown in a military coup that was heavily supported (andaccording to Zelaya, organized) by the United States government. After six months and a lot of political repression, the coup government was re-established with an election that almost the entire hemisphere – except, you guessed it, the United States – rejected as illegitimate.
-
In an overwhelming UN vote, 188 countries have called on the US to lift its 53-year trade embargo on Cuba. Havana has slammed the financial sanctions as a flagrant violation of human rights and said they are tantamount to genocide.
The recording-breaking opposition to the embargo saw Israel isolated as the only country to vote in support of the US. Palau, the island nation that got behind the US last year, abstained in the 22nd UN annual vote, along with Micronesia and Marshall Islands.
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, Hardware at 9:03 am by Dr. Roy Schestowitz
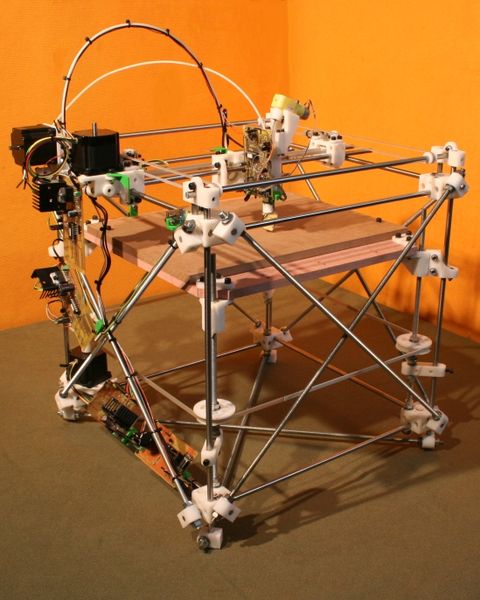
Summary: What it means to embrace so-called “Open” (freedom-respecting) hardware and why it’s a movement that we should support
Competition can be fine, especially if it’s fair. But competition brings with it some animal instincts that can be destructive (e.g. envy), so increasingly we assess a society which maximises sharing and collaboration. Not everything in life needs to be viewed like a contest. Not even philosophies, although they’re inherently different from brands of more or less the same thing.
“For the betterment of our increasingly-digital society we need to look beyond just software.”The “Open Hardware” movement is in many ways derived from the philosophy laid out by Richard Stallman about 30 years ago. It lets people experiment with the hardware they bought and it also encourages (if not forces) manufacturers to share designs in order to maximise improvement among everyone. It’s hardware liberalism, as opposed to protectionism. Selfishness and isolation get replaced by the common good, and savings are gained (for more employment, more investment) by eliminating reinventions.
There are two new stories about Open Hardware; one is about camera design and the other about why Open Hardware is revolutionary. There are many branches of freedom (or as some redefined it, “openness”) and they includes free content, free data, and free hardware (commonly known as “Open Hardware” or “Open-source hardware” these days), where “free” refers to freedom. For the betterment of our increasingly-digital society we need to look beyond just software. Sometimes hardware limits our software freedom (c/f UEFI ‘secure’ boot). The spirit of sharing is collectively beneficial to all, except to those who hoarded or blocked innovation in particular areas (i.e. created a monopoly and guarded it with new laws such as patent law). █
Related/contextual items from the news:
-
The frustration of locked-down proprietary camera firmware is one that many of us are familiar with. It’s pretty annoying to have a camera that could clearly be capable of all kinds of things but is heavily restricted by the locked-down software it is running. This is of course the origin of the Magic Lantern project, which was borne of the frustration of camera hardware that was capable of doing so much but was restricted by the built in firmware and the policies of the companies involved. It has taken a lot of work by the Magic Lantern team to gain access to the camera and to build an understanding of the way it functions, so that they could run their own software alongside the camera firmware and new features could be added.
-
Most of us that are technologically inclined are familiar with the term open source. It is often used in a software context to mean that the source code of the software is openly accessible and mutable by anyone who possesses the know-how. This software gives designers the freedom to change, improvise and customize the source code to anyone’s use. In essence, open sourcing software enables the software to become a building block rather than an opaque commodity.
Permalink
 Send this to a friend
Send this to a friend
Posted in Apple, Asia at 8:36 am by Dr. Roy Schestowitz
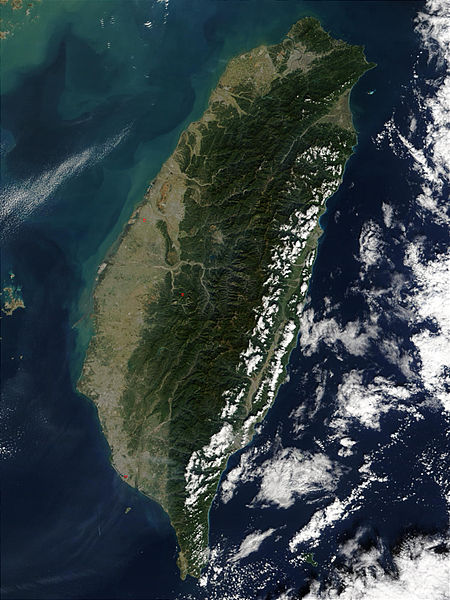
Summary: More backlash against Apple, which helps a rising oppressor change facts and conceptually take over a very large island that prides itself on high quality industries
Taiwan’s political system is mystifying. I spent a lot of time reading about the history and the current relation to PRC (essentially like ‘Greater China’ or ‘United China’). My wife worked in Taipei (electronics), so I can always hear from someone who knows this better. China has been turning into the ‘new Japan’ in the sense that it’s silently occupying and crushing dissent in neighbouring countries and islands. It expands its empire by force and by oppression. By restricting journalism it limits what the outside world knows about it. One might as well call it the Great PR Wall of China (the ‘people’s’). Taiwan has its own government and on the Internet/Web it has its own suffix, .tw.
“For Apple to simply label the Taiwanese people “Chinese” would be like calling Cypriots “Turks” or “Greek”.”For Apple, a vicious and ruthless company that detests even its own customers if they don't toe the party line (we often compare it to North Korea for this reason), using the near equivalent or prison labour makes perfect sense. Apple uses factories in areas that have weak worker/employer regulations and where pay/working hours are incredibly inhumane. Apple got bad publicity over this and it’s not too selective (different countries and provinces in Asia have different rules and practices). A country which pretends to be communist (for the ‘people’) while actually serving few billionaires (capitalism) — both domestic and foreign — is a good match for Apple, so it should make nobody wonder that Apple tries to appease and even appeal to China (Microsoft does the same thing, but that’s another story).
I was horrified when I read that Apple is now showing Taiwan as though it’s just a “province of China” [1] because it’s like China has just silently taken over (people in Taiwan are mostly prepared to fight for their lives to defend from Chinese takeover). This is insensitive and one might wonder if it’s intentional rather than an accident. It’s hard to get this type of stuff ‘wrong’. There is a known controversy here, similar to that of the Palestinian territories (among several other feuding nations/ethnic groups). Fictitious maps are the best kind of propaganda [2] because they help distort facts and misrepresent history [2]. Here in Europe there is great demonisation of immigrants (especially in Greece [3]) amid ethnic tensions and growing clannish tendencies (it’s hardly better in north America [4]). For Apple to simply label the Taiwanese people “Chinese” would be like calling Cypriots “Turks” or “Greek”. It’s beyond tactless and it is insulting to many. █
Related/contextual items from the news:
-
-
It was featured in “The West Wing,” but map dishonesty is anything but fictional. Check out this clip to get an accurate look at the size of Africa.
-
First migrants and recent immigrants were rounded up from Greece’s streets and forced into internment camps
-
A hate-crimes fugitive from Canada bought several lots in Leith and is encouraging other white supremacists to move there
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Links 6/1/2017: Irssi 1.0.0, KaOS 2017.01 Released
Links for the day
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day

























 Content is available under CC-BY-SA
Content is available under CC-BY-SA