10.09.16
Posted in Europe, Patents at 9:56 am by Dr. Roy Schestowitz

Summary: The endless lobbying and selfish aspirations of Team UPC are going nowhere but the grave, albeit the scope of patents at the EPO (related to litigiousness and spurious/frivolous lawsuits) is still a cause for concern, especially now that Battistelli turns the EPO into another SIPO or INPI (rubberstamping operation with no effective controls)
THE UPC is in complete and utter disarray. We hardly ever hear about the UPC anymore, especially since the (in)famous speech of the British Prime Minister. A few days ago we saw Bristows LLP/UPC, a key British component of Team UPC, saying that Richard Gordon’s opinion “provides limited comfort” (this was also mentioned in IP Kat, where a lot of the UPC boosters hang out these days)
“We hardly ever hear about the UPC anymore, especially since the (in)famous speech of the British Prime Minister.”Who is this of “limited comfort” to? Team UPC, surely. The back room schemers and liars don’t want to accept that the UPC is dead, if not only in the UK then in Europe as a whole. As Bristows reveals, it actually sponsored this ‘opinion’, so it’s about as legitimate as those 'studies' Battistelli will present this coming week. To quote Bristows (emphasis ours): “The opinion of Richard Gordon QC and Tom Pascoe (here) has been widely reported as providing reassurance that there are no legal difficulties in the way of the UK participating in the UPC post-Brexit. As one of the sponsors of the opinion, Bristows does not share this viewpoint. The opinion merely reaches its conclusions “on balance” and other views remain perfectly credible. Moreover, it is a purely legal analysis and does not, of course, comment upon the political realities of the requirements it sets forth. The opinion makes it very clear that several boxes would have to be ticked in order to maximise the chances of the CJEU deeming the system legal, which are more or less inconceivable in the present political climate, especially following the Prime Minister’s speech at the recent Conservative Party conference. At least in the short term there is virtually zero chance of the UK ratifying the UPC Agreement, and the real question arising is: what are the longer term prospects for salvaging the UPC project – with UK participation?”
“Bristows is also, unsurprisingly, lobbying for software patents and all things that patent trolls love. It’s all about patent and litigation scope. For them, the more the merrier.”Nothing. Forget about it. Deal with the fact that you advertised fake jobs that did not exist and probably will never exist. That’s how unethical the people of Bristows have become and this is why we don’t merely single them out; we just know who the enemy of a sane patent system is. Bristows just wants lots of lots of litigation; that’s what Bristows profits from. Don’t let them get their way as any litigation comes at the rather great expense of people who actually produce things or buy things. Bristows is also, unsurprisingly, lobbying for software patents and all things that patent trolls love. It’s all about patent and litigation scope. For them, the more the merrier.
In other news, patents on genetics have taken a massive blow because according to this new report:
The 9-month-old patent battle over CRISPR, a novel genome-editing tool that could have immense commercial value, has taken two surprising twists.
[...]
In last week’s filing, attorneys for the Broad Institute asked patent officials to remove two of its issued patents that focus on saCas9 from the original case, as well as two other patents (and a few affiliated claims in other patents) that describe techniques for enabling the CRISPR-Cas9 construct to target the nucleus of a eukaryotic cell.
Patents on life, along with patents on algorithms, are extremely controversial. For good reasons, too. Both appear to be on their decline/demise in the US right now (if not globally). Companies know this. Recall Mayo.
“Patents on life, along with patents on algorithms, are extremely controversial. For good reasons, too.”Meanwhile, regarding the EPO Hepatitis C patent/s which we mentioned here the other day (expectation of decision noted a week earlier), there are more articles about the subject [1, 2, 3, 4] and to quote one of them: “Following the development from the EPO, MdM already claims that “the EPO’s decision means that sofosbuvir in itself is not protected by a patent any more.” However, Gilead was quick to refute the claim. STAT news quotes a Gilead spokesman’s statement which maintained the patent.”
There are various groups that combat patent maximalism in medicine. One of them the opportunists in the EPO now try to associate with for cheap PR stunts. “To support #MedsPaL,” the EPO wrote, “we are working in close collaboration with @inapichile, @EPOorg & @OnapiRD.”
Fro those who don’t know what MedsPaL is, see this new article from IP Watch. To quote:
A new database was launched this week to facilitate navigation through the patent field and increase transparency surrounding the patent status of medicines and licences.
The Medicines Patent Pool (MPP), Chile’s National Institute of Industrial Property (INAPI), and global health initiative UNITAID held a side event at the WIPO General Assemblies on 5 October. The event was held to present “MedsPaL”, the MPP’s Medicines Patent and Licenses Database, discuss the difficulties in navigating the patent field, and report on the activities by regional and national patent offices, which could inform and build on the new database.
Why would MedsPaL wish to be associated in any way with the EPO, where abuses against people are so frequent and cancer patients are shamefully disliked? And speaking of association issues, Research and Markets seems to have taken an interest in the EPO [1, 2] and it plans to give seminars in London next month. To quote a portion from one of those two new press releases:
The problem/solution’ approach is not officially part of the EPC, but is a criterion which has been developed by case law. It is now is hard to find a decision of the Boards of Appeal which do not rely on the problem/solution approach in order to decide upon inventive step. It looks easy, but when applied, it should be applied correctly. This is not just a formal matter, but a substantial issue of first importance.
One thing that Research and Markets overlooks is that today’s EPO violates the EPC on a regular basis, e.g. [1, 2]. It also attacks the Boards of Appeal (see, e.g., [1, 2, 3, 4]), the body/apparatus that’s supposed to ensure high patent quality at the EPO and can no longer properly do its job because of understaffing, lack of independence etc. — especially now that Battistelli puts a mortal end to patent quality at the Office (necessitating these boards the most). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, Europe, Patents at 8:59 am by Dr. Roy Schestowitz
…Not to mention lies about performance [1, 2]

Source (original): Rospatent
Summary: Battistelli’s house of cards, or the empire/castle of lies, continues to build up ahead of the upcoming “Social Conference”, which is little more than a union-busting enabler and tranquiliser for the delegates of the Administrative Council
Jesper Kongstad, the Chairman of the Administrative Council (AC), could save staff representatives at the EPO but chose not to. It’s part of a pattern of indifference from the Administrative Council towards EPO staff and protectionism for Team Battistelli. One begins to wonder if the Administrative Council has been so thoroughly infiltrated or incentivised to basically stop doing its job and practically become just an extension — not a supervisor — of the Office.
A couple of days ago, writing in the IP Kat blog that no longer covers EPO scandals, one comment said: “It doesn’t seem to be possible to post further comments. Has the thread reached its limit ?”
No comment since. We don’t know why (maybe a manual ending to a discussion).
“One begins to wonder if the Administrative Council has been so thoroughly infiltrated or incentivised to basically stop doing its job and practically become just an extension — not a supervisor — of the Office.”EPO staff has been losing its voice since the EPO bullied some publications like ours (including the infamous ban on IP Kat) and paid a lot of money to control the rest. The EPO did all this whilst attacking the EPO unions, which also constitute the staff’s voice. The European Patent Office, which is unaccountable, is now a totally rogue institution without effective controls (either inside or outside). It’s even worse than WIPO, where Gurry just got away with everything (stories about this subject can be found in our daily links since Friday). Based on this tweet, Battistelli’s lobbying event (charade) that costs millions of Euros will carry on. Who’s to say no? Who can even say no? Now that Battistelli is wasting millions of Euros on bogus ‘studies’ will the Administrative Council hold him accountable? Will anyone ever treat Battistelli as anything other than some kind of monarch? The EPC that establishes the status quo was supposed to ensure this would not happen, but right now the EPO is pretending to care for the EPC — all this while it violates the EPC on a regular basis, e.g. [1, 2].
“EPO staff has been losing its voice since the EPO bullied some publications like ours (including the infamous ban on IP Kat) and paid a lot of money to control the rest.”Next week there is a major propaganda campaign from Battistelli. The target audience is the Administrative Council and Battistelli’s lapdog (or pet chinchilla), Jesper Kongstad. We don’t expect too see any dissent in the campaign’s event because staff representatives have already been intentionally blocked from entering (we wrote a couple of articles about this before). The Local Staff Committee at The Hague met about a week ago and plans to demonstrate in a few days. "Social Conference" nonsense from Battistelli surely and understandably irritates those whom it will lie about (in their absence).
“Meanwhile,” one person wrote, “the President is trying to sew together fig leaves, and has called for a “Social Conference”. [...] The SUEPO Committee hopes and counts on staff to provide a clear and solid mandate – one that can be reasonably expected to terminate the abuses of the present management and restore (inter alia) the union rights at the EPO.”
“”Social Conference” nonsense from Battistelli surely and understandably irritates those whom it will lie about (in their absence).”Protests in Munich will start in just two days. We reckon that a lot of it will fall on Jesper Kongstad’s deaf ears, but hopefully politicians and the media will continue to press for justice. The EPO is spending over a million Euros per year controlling the media through FTI Consulting and additional money is spent paying the media directly for puff pieces, so the latter (media) might have priorities other than to cover protests. Media blackout won’t affect Techrights and in fact I took two day off work next week, to enable me to cover what goes on in Munich and The Hague (please get in touch with us regarding any updates before, throughout, and after). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Intellectual Monopoly at 7:41 am by Dr. Roy Schestowitz
 Summary: A closer look at the “FJORDBLINK” trademark and what happened to the entity which registered it in Denmark (where the Chairman of the Administrative Council of the European Patent Organisation is still in charge)
Summary: A closer look at the “FJORDBLINK” trademark and what happened to the entity which registered it in Denmark (where the Chairman of the Administrative Council of the European Patent Organisation is still in charge)
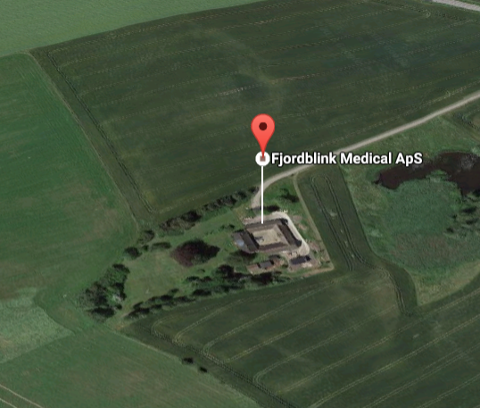
IN OUR fourth part of the series we wrote about a company connected to the Chairman of the Administrative Council of the European Patent Organisation (EPO), but there’s a side story that merits a mention at least in the addenda.
We managed to find a copy of a product brochure for the birth pool marketed by FJORDBLINK MEDICAL ApS [PDF]. The product brochure is dated May 2015.
“According to official CVR records this company ceased trading on 10 October 2013. It is unclear what has exactly has happened to the “FJORDBLINK” trademark registered by FJORDBLINK MEDICAL P/S or who, if anybody, is the current assignee.”There is a small mystery here that we have been unable to solve so far. The brochure refers to the name “FJORDBLINK” as a registered trademark. According to our research, the trademark is indeed registered both in Denmark and also as a European trademark [PDF] with the EUIPO in Alicante [PDF]. In Denmark it is registered under the number VR 2011 02145.
As a European trademark it is registered under the EU Trademark number 011266764. However, as we noted in a previous article the trademark was not registered by FJORDBLINK MEDICAL ApS (CVR number 25942507) but by another entity with a confusingly similar name: FJORDBLINK MEDICAL P/S (CVR number 33392737).
The CVR number 33392737 leads to a defunct limited partnership company by the name of FOME P/S with an address at Vibelandsvej 8, Valby, 3200 Helsinge. Between 31 December 2010 and 11 April 2013 the company operated under the name FJORDBLINK MEDICAL P/S and its registered address was in Randers where Helle Jahn Jørgensen resides.
According to official CVR records this company ceased trading on 10 October 2013. It is unclear what has exactly has happened to the “FJORDBLINK” trademark registered by FJORDBLINK MEDICAL P/S or who, if anybody, is the current assignee.
If anyone wishes to help us find out, please get in contact. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 7:18 am by Dr. Roy Schestowitz
Summary: Some more views of the Bremelandsgård farmstead, courtesy of Google Maps, demonstrating overlap between FJORDBLINK MEDICAL ApS and Jesper Kongstad’s residence
IN OUR previous post we wrote about a company connected to the Chairman of the Administrative Council of the European Patent Organisation (EPO) and explained why it’s of interest to us. This post contains additional information and observations including images.
If one types in the following company names into the search facility on Google Maps it recognises them and locates the company at the Bremelandsgård farmstead:
- Bremelandsgård v/Jesper Kongstad (the fur farming sole proprietorship) — to be covered in part 5 of our series
- FJORDBLINK MEDICAL ApS (the medical device company)
Google Maps was used to generate the following views of the farmstead, some with company tags (automatically provided by Google Maps) and some without.


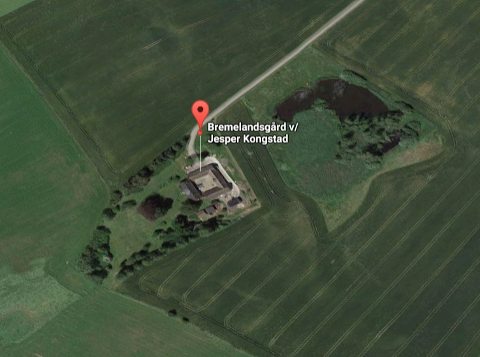
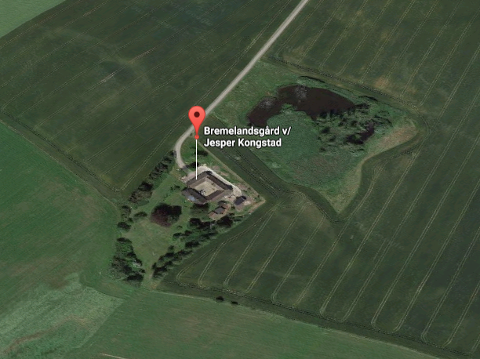
Part 5 will focus an another controversial aspect of the above farmhouse/mansion. It’s probably a lot more than just a house for ordinary people, akin to the mansion of Kim Dotcom in New Zealand. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 6:55 am by Dr. Roy Schestowitz

Photo credit: DKPTO at Flickr
Summary: The next installment of the Danish saga, this time dealing with the connections between Jesper Kongstad and a private company known as FJORDBLINK MEDICAL ApS
THE END of last week culminated in part 3 about the business ventures of Jesper Kongstad, Chairman of the Administrative Council of the European Patent Organisation (EPO). In the previous article we provided an overview of the Kongstad family business conglomerate which to seems to be mainly controlled via the holding company BREMELAND HOLDING ApS whose shareholders are Jesper and Majbritt Kongstad and their three sons.
“During the time when the Jørgensens were living in Horsens Ms. Jahn Jørgensen was active in local politics as a elected councilor for the Venstre party which forms the current minority government in Denmark.”In this contribution we will take a closer look at FJORDBLINK MEDICAL ApS (CVR number 25942507) which is a private limited company 100% owned by BREMELAND HOLDING Aps. The main business of FJORDBLINK is “to develop, produce, sell and trade with medical devices”.
It should be recalled that the registered address of both BREMELAND HOLDING ApS and FJORDBLINK MEDICAL ApS is Vibelandsvej 8, Valby, 3200 Helsinge which coincidentally corresponds to that of the current Kongstad family home “Bremelandsgård” (Danish for “Bremelands farm”).
“As far as can be determined, the original priority filing for protection was filed with the DKPTO on 19 November 2014.”The English language Web site of FJORDBLINK MEDICAL ApS can be found at en.fjordblink.com.
According to the FJORDBLINK Web site, the CEO and Administrative Director is Ms. Helle Jahn who according to the Danish Central Business Register (CVR) also goes by the name of Helle Jahn Jørgensen. Not a lot is known about Ms. Jahn Jørgensen apart from the fact that she used to operate a number of small businesses including a driving school and a trading company involved in “port-related activities” in the harbour town of Horsens on the eastern coast of Denmark’s Jutland peninsula. According to available information she is married to Michael Junk Jørgensen.
“The proprietor of the utility model is registered as FJORDBLINK MEDICAL ApS of Vibelandsvej 8, Valby, 3200 Helsinge. As noted above this corresponds to the address of the current Kongstad family home.”From the CVR it appears that Michael Jørgensen is a director of TELKO DENMARK A/S which is a wholly owned subsidiary of TELKO OY a Helsinki-based company (Finland) which according to its Web site, Telko.com, is “a distributor of chemicals and polymers with local offices and warehouses in Nordic, Baltic Eastern European countries and Central Asia”.
During the time when the Jørgensens were living in Horsens Ms. Jahn Jørgensen was active in local politics as a elected councilor for the Venstre party which forms the current minority government in Denmark. As noted in an earlier article, the Minister in charge of the DKPTO is Troels Lund Poulsen, a prominent member of Venstre. It seems that the Jørgensens moved to Randers further north on the Jutland peninsula around 2013 or 2014 and it is not known if Ms. Jahn Jørgensen is still an active member of Venstre.
Returning now to FJORDBLINK MEDICAL ApS, according to information published on its Web site it has a wide-ranging network of distributors both in Europe (Germany, the Netherlands, Belgium, Italy, Portugal, Bulgaria, Greece, and Romania) and globally (China, India and Iran).
“Helle Jahn Jørgensen, the CEO of the company is named as the inventor.”Its main product is a device called the “Medical Birth Pool” which, according to its Web site was developed in collaboration with leading midwives at Danish hospitals for pain relieving water birth: “Fjordblink ® Medical’s product concept combines maximum comfort and safety for women in labor with professional requirements for functionality, ergonomics, and hygiene. Fjordblink ® Medical birth pools are therefore developed as a medical device and FJORDBLINK Medical is certified in accordance with the DS/EN ISO 13485 ISO standard.”
An interesting detail concerning the “Medical Birth Pool” is that intellectual property rights protection has been secured for it in the form of a so-called “utility model” which is also known as a “Gebrauchsmuster” in Germany.
As far as can be determined, the original priority filing for protection was filed with the DKPTO on 19 November 2014. The publication number of the Danish Utility Model Publication (“Brugsmodelskrift”) is DK 2014 00163 U3.
“The previous company name STRANDHØJ HOLDING ApS is understood to refer to the previous Kongstad family…”The proprietor of the utility model is registered as FJORDBLINK MEDICAL ApS of Vibelandsvej 8, Valby, 3200 Helsinge. As noted above this corresponds to the address of the current Kongstad family home. Helle Jahn Jørgensen, the CEO of the company is named as the inventor.
The corresponding German “Gebrauchsmuster” has the publication number DE 20 2014 105 549 U1. In line with the company’s global marketing ambitions the utility model protection has also been registered in China under the publication number CN 204337017 U [PDF].
According to data in the CVR, FJORDBLINK MEDICAL ApS was originally founded on 1 March 2001. From 28 December 2001 until 6 July 2006 it appears to have operated under the name KONGSTAD HOLDING ApS and from 7 July 2006 until 11 April 2013 under the name STRANDHØJ HOLDING ApS. The name FJORDBLINK MEDICAL ApS was adopted in 2013.
“Prior to 2013 it seems that Majbritt Kongstad acted as CEO and that Jesper Kongstad was the Chairperson of the Board of Directors.”The previous company name STRANDHØJ HOLDING ApS is understood to refer to the previous Kongstad family residence “Strandhøj” located at Højagervej 6, 2960 Rungsted (Google Street View).
Prior to 2013 it seems that Majbritt Kongstad acted as CEO and that Jesper Kongstad was the Chairperson of the Board of Directors. The annual accounts for the company for the period 01.01.2011 – 31.12.2011 when it was operating under the name STRANDHØJ HOLDING ApS were signed off by Jesper Kongstad on 31 May 2012. Details are in this PDF.
“In fact, during the years 2011 to 2015 significant losses were continuously registered.”In April 2013 the company underwent some internal restructuring. Majbritt Kongstad resigned her position as CEO and was replaced in this role by Helle Jahn Jørgensen. At the same time Ms. Kongstad was appointed as Chair of the Board of Directors. The other member of the Board of Directors is a Danish lawyer Ernst Ulrik Bayer who is associated with the prominent Copenhagen law firm Molke Leth.
A perusal of the company’s financial statements also reveals some interesting information. It seems that the company has not been a commercial success so far. In fact, during the years 2011 to 2015 significant losses were continuously registered. Based on CVR figures, the operating result for 2015 was a deficit of 2,412,563 DKK (approx – 323,400 EUR). In 2014 the deficit was 1,447,343 DKK (approx. – 194.014 EUR). The operating losses for the years 2013, 2012 and 2011 were respectively 928.393 DKK (approx. – 124.449 EUR), -3,842,877 DKK (approx. – 515.131 EUR) and 109.388 DKR (approx. – 14.663 EUR).
“The certificate of registration is dated 14 September 2011 and signed by the Director General of the DKPTO, Mr. Jesper Kongstad.”The annual report for 2015 contains a statement to the effect that the company has used important resources on development and quality assurance, and that 2016 again is expected to generate an operating loss (due to product development, documentation, quality assurance and marketing) while 2017 should yield an operating profit. BREMELAND HOLDING Aps, the owner of the company and the main holding company of the Kongstad family conglomerate is named as the guarantor for the deficit in 2016 while an unidentified third party has apparently given a guarantee for the company’s liabilities. See this PDF.
A further interesting detail in this saga concerns the registration of the name “FJORDBLINK” as a trademark in the Danish Register of Trade Marks under the number VR 2011 02145.
The official DKPTO correspondence concerning the registration of the trademark can be found online here.
The certificate of registration is dated 14 September 2011 and signed by the Director General of the DKPTO, Mr. Jesper Kongstad. According to the certificate the registration is valid for a period of ten years. See this PDF.
“The trademark registration application on behalf of FJORDBLINK MEDICAL P/S was apparently filed by Ms. Helle Jahn (Jørgensen) who was subsequently appointed as CEO of FJORDBLINK MEDICAL ApS in 2013.”What is striking here is the fact that the application for the trademark registration was filed in the name of FJORDBLINK MEDICAL P/S (CVR number 33392737) rather than by FJORDBLINK MEDICAL ApS (CVR number 25942507). The trademark registration application on behalf of FJORDBLINK MEDICAL P/S was apparently filed by Ms. Helle Jahn (Jørgensen) who was subsequently appointed as CEO of FJORDBLINK MEDICAL ApS in 2013. PDF here.
The CVR number 33392737 leads to a defunct limited partnership company by the name of FOME P/S with an address at Vibelandsvej 8, Valby, 3200 Helsinge.
It appears that between 31 December 2010 and 11 April 2013 the company operated under the name FJORDBLINK MEDICAL P/S and that its registered address during that period was in Randers where Helle Jahn Jørgensen resides.
According to the CVR, Majbritt Kongstad was appointed as CEO of this company on 12 April 2013 and the address was changed to Vibelandsvej 8, Valby, 3200 Helsinge. At around the same time, the lawyer Ernst Ulrik Bayer and Asger Kongstad, apparently a son of Jesper and Majbritt Kongstad, were appointed to the Board of Directors.
“The case of FJORDBLINK MEDICAL seems to throw up a lot of unanswered questions about potential conflicts of interest and there are a number of as yet unsolved riddles about its operations.”Some time thereafter on 10 October 2013 the company appears to have ceased trading. In view of the dissolution of FJORDBLINK MEDICAL P/S is unclear what has happened to the “FJORDBLINK” trademark and who, if anybody is the current assignee.
The case of FJORDBLINK MEDICAL seems to throw up a lot of unanswered questions about potential conflicts of interest and there are a number of as yet unsolved riddles about its operations. Perhaps somebody will be able to carry out further investigation in order to clarify these matters.
In case of link erosion or critical material going offline we have decided to make local copies of some documents. Included are the following items:
- Copies of utility model certificates referred to in the text for China
[PDF], Germany [PDF], and Denmark [PDF].
- Copies of documents relating
[PDF] to the “FJORDLAND” trademark registration [PDF] (in Danish).
- Copy of “Strandhoj” annual accounts
[TIF] for 2011 signed off by Jesper Kongstad on 31 May 2012.
- One further interesting detail concerning FJORDBLINK MEDICAL ApS which has come to light is worth highlighting. The official correspondence relating to the utility model application in Denmark is available online via the DKPTO’s Web site. One of the documents submitted with the application is a power of attorney which is co-signed by Majbritt Kongstad and Helle Jahn (Jørgensen). A copy of the power of attorney is now on our server
[PDF], in order to assure/ensure it remains available/accessible to all.
Addendum/addenda, containing more visual items, will be published separately. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 2:26 am by Dr. Roy Schestowitz

Contents
-
One of the main Linux draws is its customization, and one of the most important areas is the desktop environment. Of the Linux desktop environments, GNOME and KDE are two of the leading environments. Tyrell Wellick (Martin Wallström) says to protagonist Elliot, “So I see you’re running Gnome! You know I’m actually on KDE myself.” Those familiar with Linux and its environments will appreciate this moment, especially Wellick’s follow up, “Yeah, I know what you’re thinking, I’m an executive running Linux, why am I even running Linux?”
Not only do we learn about KDE and GNOME, but there’s even a bit about the perception of Linux use in the enterprise (hint: it’s usually relegated to sysadmins and tech specialists, not execs).
-
Yes! You read right. While the world is realizing the power of Linux, on the other hand there are also people who are often found debating in the communities like, Reddit about how bad Linux is due to several problems. Several issues that are raised are actually myths about Linux. So here is a try from LinuxAndUbuntu to cover and clear some of the most talked Linux myths.
-
Desktop
-
Microsoft may have used its Ignite conference to trumpet Windows 10 now running on 400 million devices, but the operating system’s market share went backwards in September according to two of three traffic-watchers we track each month.
StatCounter Global Stats has Windows 10 at 24.42 per cent desktop OS market share for September, down just .01 per cent from its August share. Netmarketshare recorded a sharper dip, from August’s 22.99 per cent to a September reading of 22.53 per cent.
Both firms, as we’ve often pointed out, rely on sniffing web traffic for their numbers and that’s far from a certain way of figuring out who’s running what. Indeed, StatCounter has recently recorded a surge in “Unknown” desktop operating systems, up from 4.06 per cent in June to 6.42 per cent in September, suggesting tracking and/or methodological issues.
-
The recent Microsoft Windows 10 Anniversary Update ruffled more than a few feathers as many users are experiencing a reboot cycle.
These things are bound to happen when a company takes a cavalier attitude and constantly slipstreams updates. This is unlike the previous era of the neverending patch Tuesday. The difference: these Windows 10 updates are not optional.
-
There is much talk in the Linux world about the mythical “average user.” There is no such thing with Linux. First off, people who use Linux usually are those who know a thing or two about computers to begin with and want to take advantage of all the choices Linux offers. Linux has been considered the place for nerds, hackers and programmers for years. These folks are NOT typical at all. Secondly, it is unfortunate but true that most advanced Linux users are completely out of touch with what an average user really is.
The vast majority Windows and Mac users are those who have learned just enough to get done what they need to get done. They’re clueless about how the machines they use everyday get those tasks accomplished and the idea of popping open a bash terminal to work with configuration files or fix problems is way out of their comfort zones. This does not mean that Linux can’t offer them a safe and friendly environment to work in, far from it. Linux offers a wide variety of Graphical User Interfaces (GUIs) that make working with a Linux box a point and click affair.
-
Server
-
Docker founder Solomon Hykes officially announced the debut of the open-source Infrakit toolkit this week, in a bid to further enable DevOps to actually work.
-
Kernel Space
-
Linux creator Linus Torvalds this week apologized for including in the just-released Linux 4.8 kernel a bug fix that crashed it. The bug the dev was trying to fix has existed since Linux 3.15, “but the fix is clearly worse than the bug … since that original bug has never killed my machine,” Torvalds wrote.
-
-
-
-
-
-
-
After announcing the release of Linux kernel 4.8.1, Greg Kroah-Hartman had the pleasure of informing the community about the release of the twenty-fourth maintenance update to the Linux 4.4 LTS series.
Linux 4.4 LTS is a long-term supported kernel branch, used by some of the most stable GNU/Linux distributions, including Alpine Linux 3.4, Linux Lite 3, and Ubuntu 16.04 LTS (Xenial Xerus), and it will receive point releases that bring bug fixes and security patches, along with updated drivers for a few more years. Linux kernel 4.4.24 LTS is the latest build, and it comes just one week after the release of Linux kernel 4.4.23 LTS.
-
There is support for a number of new ARM platforms with the in-development Linux 4.9 kernel.
-
The MD subsystem updates were sent out earlier this week for the Linux 4.9 kernel merge window with a few improvements/features to note.
-
This morning the protection keys syscall interface was submitted for the Linux 4.9 merge window, the last step of adding Protection Keys support to the Linux kernel.
-
-
Graphics Stack
-
-
-
While GNOME is frequently brought up for its well-vetted Wayland support when using the latest packages, the Enlightenment desktop has also been progressing very well with its Wayland compositor and they continue making improvements to their display stack. One of these important pieces has been the Ecore_Drm2 library.
Ecore_Drm2 is part of EFL 1.18 and is their new abstraction layer for interfacing with Linux’s DRM (Direct Rendering Manager, of course).
-
On Thursday the RADV open-source Radeon Vulkan driver was merged into mainline Mesa and I provided bleeding-edge RADV vs. AMDGPU-PRO benchmark results for these two independent AMD Linux Vulkan driver implementations, plus comparison results to the OpenGL drivers in the same games. For those that have been wondering how the NVIDIA proprietary Vulkan driver compares to AMD’s two Vulkan driver options, here are some fresh benchmark results.
-
Applications
-
The tint package is now on CRAN. Its name stands for Tint Is Not Tufte and it offers a fresh take on the excellent Tufte-style html (and now also pdf) presentations.
-
Instructionals/Technical
-
Wine or Emulation
-
For those sticking to Wine 1.8.x stable releases until Wine 2.0 is released around the end of the year, Wine 1.8.5 is the latest and greatest.
Wine 1.8.5 doesn’t incorporate any of the new features building up in the Wine 1.9 development series but simply back-ports some bug fixes.
-
The Wine maintenance release 1.8.5 is now available.
-
The Wine team released yesterday sixth stable release of 1.8 branch of Wine. Version 1.8.5 has many small changes including 58 bugfixes.
This stable release contains bugfixes, new features are included in development releases from 1.9 branch.
-
Games
-
LINUX GAMING –
X-Plane, one of the most realistic flight simulators that continues to be cross-platform, will be released “this holiday season” and it offers more flying improvements and much better visuals.
The X-Plane crew announced today, “X-Plane 11 is the detailed, realistic, and modern simulator you’ve been waiting for. And it’s coming this holiday season.”
X-Plane 11 is slated to have a completely redesigned UI, improved 3D high-definition cockpits, new effects, realistic avionics, “living” airports, and a variety of new buildings, roads, and other scenery.
-
‘Enclave’ [Steam] is another Wine-port from Topware Interactive who promised to bring their older published titles to Linux. I’m totally okay with this, and it’s currently in Beta.
Wine enables us to play a great many things we otherwise wouldn’t be able to, so for developers to actually test it and release their old games with a build of Wine that works well, can only be good for us in the long run.
-
For the second time in only a few months, Overkill has managed to push out an update for PAYDAY 2 [Steam] that has completely broken the Linux version.
The developers have noted they are aware of it, but no solution has been offered as of right now.
-
-
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Today, October 8, 2016, KDE announced the monthly release of the KDE Frameworks project, a collection of over 70 add-on libraries to the Qt5 GUI (Graphical User Interface) toolkit.
-
-
-
-
New Releases
-
After announcing last month the release of his AryaLinux 2016.08 distribution with the MATE 1.15 desktop environment, developer Chandrakant Singh is now proud to announce the Xfce edition.
-
Superb Mini Server finally got a new updated version release after a long time period.Yes, After a long awaited time,the previous version of SMS(Superb Mini Server)2.0.8 which was released back in 2015,now in 2016 got a new release of SMS 2.0.9.
Even if the releases are less-frequent,this slackware based distribution really makes a good amount of users,who works with servers,mostly looks at this fellow distro,because of set of applications available and the environment is completely perfect for those who love to work with the web-server based developments and managements.
-
OpenSUSE/SUSE
-
-
-
In our latest report, we promised you would not have to wait another three weeks to hear (or read) from us. And here we are again, but not with any of the anticipated topics (build time reduction and Euruko 2016), but with a call for help in a topic that could really make a difference for (open)SUSE.
Nowadays, YaST team is trying to fix a long-standing issue in the installer: low-vision accessibility. In the past, a user could get a high-contrast mode just pressing shift+F4 during installation. Unfortunately, that feature does not work anymore and, to be honest, changing to a high-contrast palette is not enough. Other adjustments, like setting better font sizes, should be taken into account.
Another option is to use the textmode installation and set some obscure variable (Y2NCURSES_COLOR_THEME) to get the high-contrast mode. But it sounds like the opposite to user friendly.
-
Red Hat Family
-
Finance
-
Fedora
-
The development cycle of Fedora 25 has suffered two setbacks causing the release dates to slip, the last time with the Alpha. But not today. The release team agreed that the Beta is ready to go on time. This will be the last public build before the Final, so now is the time to report those bugs. Fedora 25 will bring some new features to test, like Ctrl-Shift-e to type in Emoji.
Jan Kurik posted this afternoon to the developers mailing list that the Fedora 25 Beta Go/No-Go Meeting had ended in a Go. There were five accepted blocker bugs earlier but the fixes are in and the team set about deciding on two proposed. The first concerned the Anaconda installer failing on RAID when it’s in a “migrating state.” It’s reproducible by creating a new RAID-1 set and immediate starting the install. However, the team decided that since the install will complete if the user waits for the initial sync to complete it wasn’t serious enough to hold up the Beta. They plan on having it fixed for Final as they’ve already decided it’s an accepted Final blocker.
-
Debian Family
-
Derivatives
-
After announcing the release of DebEX KDE Live DVD Build 161001, GNU/Linux developer Arne Exton informs us today about the availability of a new build of his DebEX GNOME Live DVD.
-
Finally a new update of many TeX related packages: all the texlive-* including the binary packages, and biber have been updated to the latest release. This upload was delayed by my travels around the world, as well as the necessity to package a new Perl module (libdatetime-calendar-julian-perl) as required by new Biber. Also, my new job leaves me only the weekends for packaging. Anyway, the packages are now uploaded and should appear soon on your friendly local server.
-
Canonical/Ubuntu
-
Looking for a Linux icon set that’s a little understated and less in your face? Check out Victory.
Bombastic name aside, there’s nothing particularly imposing about the Victory icon set. It doesn’t dominant the desktop in the way that something that some modern themes, like the bright and bashful Kylin icon set, do.
-
-
Ubuntu and machine learning is helping to bring a sense of touch to our computers, in pioneering work being done by computer scientists at the University of St Andrews.
-
-
The release date of Ubuntu 16.10 is now less than a week away — but do you plan to upgrade to the ‘Yakkety Yak’ once it arrives?
-
-
NXP unveiled its automotive i.MX8 Quad with four Cortex-A53 cores, two Cortex-M4F cores, and two GPUs. The QuadPlus and QuadMax add one and two -A72 cores.
Freescale teased its automotive i.MX8 family in 2015 before the company was acquired by NXP, a process that may have contributed to the SoC family’s delays. The first three i.MX8 models are now due to sample in Q1 2017, says NXP, which has already built a development kit for the SoC, shown farther below. In addition, plans have leaked for future i.MX8 models for multimedia and low-power IoT applications, including dual-core models (see farther below).
-
Phones
-
Tizen
-
-
-
Today, the Samsung Z3 (model SM-Z300H) smartphone got a little software update in India, taking it to version Z300HDDU0BP12. This update only measure in at 5.9MB, so nothing much to really brag about, but still worth updating. This is a maintenance release and does not bring any new features with it and is mainly for performance and bug-fixes. No change log has been provided.
-
-
Android
-
Xiaomi has officially started to sell its Google Android TV 6.0-based set-top-boxes in the U.S. The Xiaomi Mi Box STB boasts with a rather powerful SoC, an HDMI 2.0a (4K, 60 fps, HDR) video output, a Bluetooth remote with voice search feature as well as a $69 price tag. The combination of modern, capable hardware and a relatively affordable price will improve chances of Xiaomi’s STB to become popular among those who use Google’s Android TV platform.
The Xiaomi Mi is powered by Amlogic’s S905X-H SoC (four ARM Cortex-A53 cores at 2.0 GHz, five ARM Mali-450MP clusters) and is equipped with 2 GB of DDR3 memory, 8 GB of NAND flash, a wireless module supporting Wi-Fi 802.11ac and Bluetooth 4.0, a USB port as well as an HDMI 2.0a output with HDCP 2.2 and CEC. Xiaomi bundles a Bluetooth remote with a mic and voice search feature with its STB for extra convenience. In addition, the company sells its Mi Game Controller for those, who would like to play Android games on TV.
-
-
-
-
-
-
-
-
-
-
Chinese hardware upstart LeEco accidentally showed off key parts of its device lineup two weeks before the company is set to officially launch its US business Friday. The leak, which was first spotted by AndroidPolice, revealed two budget-phones as well as four different TV sets based on Google’s Android TV platform.
Product shots also show numerous LeEco-branded apps, suggesting that the company wants to use its devices to grow its entertainment services, much like it has done in China. A LeEco spokesperson didn’t immediately respond to a request for comment.
-
Last weekend, we told you that the Nokia D1C had been run through the Geekbench benchmark test. Under the terms of Microsoft’s purchase of Nokia Services and Devices back in 2014 (when the deal closed), Nokia was not allowed to produce a smartphone using the Nokia name until the fourth quarter of 2016. Now that we are in that time frame, it is more than a coincidence that an Android powered, Nokia branded phone was recently benchmarked.
The Geekbench test revealed that the device will be powered by the Snapdragon 430 chipset, and will carry 3GB of RAM. That obviously is just a small peek at the Nokia D1C’s specs. But today, the handset was run through AnTuTu, and that benchmark test has provided us with a much larger look at the phone’s specs.
-
Google is drawing a line under the Nexus brand and opening up a fresh front in the smartphone wars. The Google Pixel and Pixel XL are the first smartphones to be “Made by Google.” They may have been manufactured by HTC, but make no mistake, that G on the back is very important.
This is a major strategy shift for Google, and one that is long overdue. By taking end-to-end control of software and hardware, Google can elevate Android to the next level, addressing its major shortcomings. It’s a move that shows a willingness to stand toe-to-toe against Apple and shrug off any lingering deference to dominant Android partners like Samsung.
-
-
-
-
-
-
-
-
When I watched Chad Fowler’s GOTO Amsterdam 2014 Keynote it got me thinking about what our aims should be in life.
He mentions Joel Spolsky’s post from 2001: Good Software Takes Ten Years. Get Used To It, and says software typically only lasts five years so rarely gets to be very good.
He asks, what does it take create legacy software with a positive meaning, that is software so good that you are fondly remembered for it for many years to come.
How many very famous developers, or ex-developers are there in the world. You may disagree, but I would argue that Bill Gates is the only living person with worldwide fame partly associated with writing code.
Only big company CEOs have any chance of becoming a household name. Even Sir Tim Berners Lee has only about half as many Twitter followers as Grumpy Cat.
-
A top AT&T executive said the company will launch its Enhanced Control, Orchestration, Management, and Policy (ECOMP) platform into open source by the first quarter of 2017. And the Linux Foundation will be the host of the open source project.
In a blog post, Chris Rice, SVP of AT&T Labs Domain 2.0 Architecture and Design, said that after the company developed ECOMP, it received a tremendous amount of feedback from service providers and virtual network function (VNF) providers that wanted more details about the platform. He also said the companies wanted AT&T to publicly state that it was going to open source the project.
-
It’s autumn/fall technology conference season… but you already knew that, so what’s coming next? O’Reilly’s OSCON event is just around the corner and the conference itself has seen the launch of many new projects from OpenOffice.org to OpenStack.
-
We talk a great deal on Techdirt about the importance of free speech alongside the importance of not damning technological tools for the way third parties choose to use them. These matters can delve into minutiae in the American and Western forms of this conversation, with discussions about Section 230 protections and the like. But in other parts of the world, the conversation is much different.
Back in 2008 in Iran, for instance, the government there elected to imprison a Canadian resident of Iranian lineage, initially under a death sentence, but later commuting that sentence to mere life imprisonment. His crime? Saeed Malekpour created some open source code for sharing photos on the internet that others within Iran used for pornography.
-
As medical implants become more common, sophisticated and versatile, understanding the code that runs them is vital. A pacemaker or insulin-releasing implant can be lifesaving, but they are also vulnerable not just to malicious attacks, but also to faulty code. For commercial reasons, companies have been reluctant to open up their code to researchers. But with lives at stake, we need to be allowed to take a peek under the hood.
Over the past few years several researchers have revealed lethal vulnerabilities in the code that runs some medical implants. The late Barnaby Jack, for example, showed that pacemakers could be “hacked” to deliver lethal electric shocks. Jay Radcliffe demonstrated a way of wirelessly making an implanted insulin pump deliver a lethal dose of insulin.
But “bugs” in the code are also an issue. Researcher Marie Moe recently discovered this first-hand, when her Implantable Cardioverter Defibrillator (ICD) unexpectedly went into “safe mode”. This caused her heart rate to drop by half, with drastic consequences.
It took months for Moe to figure out what went wrong with her implant, and this was made harder because the code running in the ICD was proprietary, or closed-source. The reason? Reverse-engineering closed-source code is a crime under various laws, including the US Digital Millennium Copyright Act 1998. It is a violation of copyright, theft of intellectual property, and may be an infringement of patent law.
-
Google has released open-sourced Cartographer, a real-time simultaneous localization and mapping (SLAM) library in 2D and 3D with ROS (Robot Operating System) support. This technology which works with the open source ROS can be used by developers for many things, such as robots, drones and self-driving cars.
-
LinuxCon
-
-
-
Jim Zemlin raises an eyebrow when I say Hyperledger is rather outside Linux Foundation’s usual domain, being a bit, er, consumery.
“It’s totally enterprise,” the Foundation’s executive director tells me. “It’s infrastructure.” Just like Linux, he reckons. Hyperledger is the layer above the operating system, above Linux.
Linux is the Linux Foundation’s oldest and hardest of hard-core projects – a technology fundamental that drives economies.
-
J.P. Morgan Chase is developing a blockchain, commonly referred to as a public ledger, atop a crypto-network called Ethereum.
The system, dubbed “Quorum,” is designed to toe the line between private and public in the realm of shuffling derivatives and payments. The idea is to satisfy regulators who need seamless access to financial goings-on, while protecting the privacy of parties that don’t wish to reveal their identities nor the details of their transactions to the general public.
-
SaaS/Back End
-
Recently, we caught up with Kavitha Mariappan, who is Vice President of Marketing at Databricks, for a guest post on open source tools and data science. In this arena, she took special note of The R Project (“R”), which is a popular open source language and runtime environment for advanced analytics. She also highlighted Apache Spark and its distributed in-memory data processing, which is fueling next-generation data science.
Now, R users can leverage the popular dplyr package to sift and work with Apache Spark data. Via the sparklyr package, a dplyr interface for Spark, users can filter and aggregate Spark datasets then bring them into R for analysis and visualization, according to an RStudio blog post.
-
The latest release of widely deployed open-source cloud platform improves security, virtualization and networking.
The open-source OpenStack project released OpenStack Newton on Oct. 6, providing the second major milestone update for the cloud platform in 2016.
OpenStack Newton follows the Mitaka release, which debuted in April with a focus on simplifying cloud operations. In contrast, OpenStack Newton provides a long list of incremental updates and improvements, including improved security, container support and networking capabilities.
-
OpenStack, the massive open source project that helps enterprises run the equivalent of AWS in their own data centers, is launching the 14th major version of its software today. Newton, as this new version is called, shows how OpenStack has matured over the last few years. The focus this time is on making some of the core OpenStack services more scalable and resilient. In addition, though, the update also includes a couple of major new features. The project now better supports containers and bare metal servers, for example.
In total, more than 2,500 developers and users contributed to Newton. That gives you a pretty good sense of the scale of this project, which includes support for core data center services like compute, storage and networking, but also a wide range of smaller projects.
-
The OpenStack community today released Newton, and it’s hard to believe that this is the 14th version of the most widely deployed open source software for building clouds. “New features in the Ironic bare metal provisioning service, Magnum container orchestration cluster manager, and Kuryr container networking project more seamlessly integrate containers, virtual and physical infrastructure under one control plane,” the announcement notes. “These new capabilities address more use cases for organizations with heterogeneous environments, who are looking for speed and better developer experience with new technologies like containers, alongside workloads that require virtual machines or higher availability architectures.”
Here is more on what’s under the hood and how this new version embraces virtualization and containers.
The 14th release improves the user experience for container cluster management and networking, and the Newton release addresses scalability and resiliency. These capabilities will be demonstrated at the upcoming OpenStack Summit, happening October 25-28, in Barcelona Spain.
“The OpenStack community is focused on making clouds work better for users. This is clearly evident in the Newton release, which tackles users’ biggest needs, giving cloud operators and app developers greater security, resiliency and choice,” said Jonathan Bryce, executive director of the OpenStack Foundation. “The new features and enhancements in Newton underscore the power of OpenStack: it handles more workloads in more ways across more industries worldwide. OpenStack is a cloud platform that ties everything together—compute, network, storage, and innovative cloud technologies.”
-
Oracle/Java/LibreOffice
-
We’ve been informed by The Document Foundation’s Italo Vignoli that the next major release of the popular LibreOffice office suite, version 5.3, will soon enter development and the first bug hunting session takes place in two weeks.
-
FSF/FSFE/GNU/SFLC
-
DNS allows to resolve the name of an IP address. This is sometimes called “reverse lookup”. In fact, it is actually “normal” resolution of a PTR record. The name of such a record would be, for example, 4.4.8.8.in-addr.arpa. The .arpa TLD is managed by IANA.
This blogpost is meant to spread ideas that have been exchanged via private email and might be interesting for a broader audience. If you feel like you have useful comments, don’t hesitate to do so.
-
Openness/Sharing/Collaboration
-
Programming/Development
-
Release 7.12 of GDB, the GNU Debugger, is now available via anonymous FTP. GDB is a source-level debugger for Ada, C, C++, Objective-C, Pascal and many other languages. GDB can target (i.e., debug programs running on) more than a dozen different processor architectures, and GDB itself can run on most popular GNU/Linux, Unix and Microsoft Windows variants.
-
GDB 7.12 is now available as the latest feature release of the GNU Debugger.
Arguably most exciting about GDB 7.12 is that it now supports debugging programs written in Rust! But if Rust support doesn’t excite you, there is also some Fortran support improvements and various Python language enhancements.
-
In her LinuxCon Europe talk, “The Set of Programmers: How Math Restricts Us,” Carol Smith, Education Partnership Manager at GitHub, got us thinking about how math requirements impact our ability to bring more people into the field of computer programming.
Carol kicked off her talk with a story about how she traveled to New Zealand with two friends, Boris and Natasha (not their real names), and learned that Boris has agoraphobia, which causes him extreme anxiety in open spaces. New Zealand, as it turns out, is full of wide open spaces. During one hike, Boris really struggled with crossing the long bridge across a gully. The more he told himself he could do it, the harder it was. He felt like he should be able to do this and felt like he was the only person who couldn’t do it. A lot of people get this feeling when they try to do math. They feel like everyone else can do math, and the more they think this, the more they feel like they are the only person who can’t do math.
-
Yes it is. But it is also limited to build the Rust crate. It does one thing, very well, and easily.
Although I’m writing a GNOME application and this needs more than building the code. So I decided I need to wrap the build process into automake.
Let’s start with Autoconf for Rust Project. This post is a great introduction to solving the problem and give an actual example on doing it even though the author just uses autoconf. I need automake too, but this is a good start.
-
We have seen a changing of the guard in the past few years as software takes center stage and once-beloved hardware simply becomes a canvas for developers. The ability to code is an important skill for the production of any modern technology, especially a product that falls within the “internet of things.” If IoT developers are to create the next big thing in tech, they will need to know the most important and popular IoT coding languages. Here is a list of top coding languages providing the backbone of IoT software:
-
Nexedi, an open source software company based in France, has filed a lawsuit against Apple in Paris alleging that Apple’s App Store contract is unfair.
In a blog post, founder and CEO Jean-Paul Smets and UI designer Sven Franck said that the company has undertaken the lawsuit to force Apple to improve its support for the latest web technology in iOS.
Smets and Franck point to technical shortcomings in mobile Safari such as lack of support for HTML5 service workers, webRTC, and WebM – web technologies necessary for running applications like the OfficeJS spreadsheet and Hubl.in online conferencing.
-
The primary reason for starting this lawsuit is because we hope that it will help Apple to sooner support the latest Web and HTML5 standards on its iOS platform – the operating system used by all iPhones.
Anyone running html5test (http://html5test.com/) on his iPhone will find out that current iOS support of HTML5 Web technologies is lagging behind other platforms.
-
Standards/Consortia
-
With “Vulkan Next” likely not debuting until 2017, the Vulkan 1.0.x point releases continue with minor fixes to the Vulkan documentation.
-
On Thursday evening, Beer found himself locked out of his Skype account and had to chase Microsoft support for help.
His emails finally made their way to Microsoft’s Global Escalation Services.
On Friday evening, he was told that there were multiple users who were having trouble signing into their Skype accounts. “I believe we may be experiencing a bit of an outage,” the escalation supervisor wrote.
-
Security
-
-
Imagine for a moment that you are a security engineer who discovers a backdoor that your company execs have been trying to hide from your team. Would you quit on ethical grounds or stay so that you can prevent this from happening again? I don’t think there is one right answer. Personally I am grateful both for those who left and blew the whistle, and for those who stayed to protect Yahoo’s 800 million users.
Part of the job function of security engineers and pen testers is being ready for the moment you encounter something that you think should be disclosed but your company wants to keep secret. Think about what you would be willing to lose. Be prepared to escalate internally. Know the terms of your NDA and your exit agreement; try your best to honor them. Most of all, keep pushing for end-to-end encryption.
-
Hacker attacks that try to take down websites with a flood of bogus traffic, technically known as Distributed Denial of Service (DDoS) attacks, have become a daily occurrence on the internet. The rise of DDoS has created a cottage industry of companies dedicated to mitigating the attacks, and, on the flip side, professional DDoS-for-hire services and gangs.
Now, a group of security researchers wants to name and shame not only the hackers responsible for such crippling attacks, but also the internet providers and traffic carriers that enable them by turning a blind eye to their actions, with a project called SpoofIT.
-
I wrote the original cyber-vulnerability letter to the White House in 1994, and instead of acting responsibly, the US Government allowed NSA — with the active complicty of US communicaitons and computing provider CEOs — to compromise all US offerings. Not only are the communications and computing devices and related consulting compromised, but so are larger offerings (e.g. Boeing aircraft, which come with a computer system pre-configured for US Government remote control take-over — Lufthansa is reported to have discovered this and at great expense removed all US computers from every aircraft). NOTE: I am quite certain about both of the above indictments, but only a proper European Commission investigation can satisfy the public interest; I believe that the same problems infect C4I systems from China, France, Israel, and Russia, and I do not believe most people are aware that the electrical system is now easily used to enter computers that are nominally disconnected from the Internet.
-
A new vulnerability has been discovered that could shut down most Linux systems using a command short enough to fit in a tweet.
-
I’ve just read an interesting article entitled “who makes the IoT things under attack“, explaining that devices connected to the Internet such as router, IP cameras, IP Phones, etc.. may be used by Botnet to launch DDoS attacks, and they do so using the default username and password. So you may think once you’ve updated the firmware when available, and changes the default admin/admin in the user interface, you’d be relatively safe. You’d be wrong, because the malware mentioned in the article, Mirai, uses Telnet or SSH trying a bunch of default username and password.
That made me curious, so I scanned the ports on my TP-Link wireless router and ZTE ZXHN F600W fiber-to-the-home GPON modem pictured below, and installed by my Internet provider, the biggest in the country I live, so there may be hundred of thousands or millions of such modems in the country with the same default settings.
-
As I noted just the other day, cybersecurity should be a defensive game. Going offensive is really, really dangerous, because things will get worse, and we really don’t know what the capabilities of the other side(s) truly are. Focus on protecting critical infrastructure, not on some meaingless symbolic strike back.
But, of course, in this day and age, people seem to feel that every action requires some sort of reaction, and in a computer security realm, that’s just stupid. But it seems to be where we’re inevitably heading. The cybersecurity firms will get wonderfully rich off of this. But almost everyone will be less safe as a result.
-
Defence/Aggression
-
Saudi-led warplanes struck a funeral at a community hall in the Yemeni capital Sanaa, the country’s Houthi-run administration said on Saturday, but the coalition denied any role in the attack. More than 140 mourners were killed, according to local health officials cited by the United Nations, in an attack that prompted a strong rebuke from Washington, a key Saudi ally.
Jamie McGoldrick, a UN official in charge of humanitarian efforts in the country, said more than 525 were injured.
The death toll was 82, according to Ghazi Ismail, the administration’s acting health minister. The reason for the discrepancy in numbers was not immediately clear.
-
Russian forces could shoot down coalition jets if the United States launches airstrikes against pro-government forces in Syria, the Russian ministry of defence has said.
American officials have reportedly discussed using limited airstrikes to force Bashar al-Assad’s government to halt its assault on Aleppo and return the negotiating table after a ceasefire collapsed last month.
In Moscow’s starkest warning yet against Western intervention in the war, Russia’s chief military spokesman said that any airstrikes on government-held territory in Syria would be considered a “clear threat” to Russian servicemen.
-
Despite our unorthodox presidential election, America’s overseas military bases are largely taken for granted in today’s foreign policy debates. The U.S. maintains a veritable empire of military bases throughout the world—about 800 of them in more than 70 countries. Many view our bases as a symbol of our status as the dominant world power. But America’s forward-deployed military posture incurs substantial costs and disadvantages, exposing the U.S. to vulnerabilities and unintended consequences.
Our overseas bases simply do not pay enough dividends when it comes to core national interests. Here are seven reasons why it’s time to close them.
-
It is a plain lie that Russia was responsible for the leak of the Democratic National Committee emails to WikiLeaks. It is quite extraordinary that the Obama administration formally adopted the accusation yesterday.
The US motivation is apparently to attempt to discredit in advance the further Hillary material that WikiLeaks plans to release in the coming month. The official statement that the leak was “consistent with the methods and motivation of Russian directed efforts” is carefully written by the NSA and, when you analyse it, extremely weak. What it says is “there is no evidence whatsoever but this is the sort of thing we think the Russians do”. As it happens, I have direct knowledge that there could not have been any evidence as it was not the Russians.
-
What must the world think watching the US presidential campaign? Over time US political campaigns have become more unreal and less related to voters’ concerns, but the current one is so unreal as to be absurd.
The offshoring of American jobs by global corporations and the deregulation of the US financial system have resulted in American economic failure. One might think that this would be an issue in a presidential campaign.
The neoconservative ideology of US world hegemony is driving the US and its vassals into conflict with Russia and China. The risks of nuclear war are higher than at any previous time in history. One might think that this also would be an issue in a presidential campaign.
Instead, the issues are Trump’s legal use of tax laws and his non-hostile attitude toward President Putin of Russia.
-
What Freedland does not understand is that it was hatred of his political bubble chums which caused Brexit in the first place. The official Remain campaign director was Jack Straw’s son Will. Peter Mandelson was Vice-President. The top-down campaign was devoid of popular enthusiasm with an almost total lack of popular engagement and community events. It continually paraded figures like Blair, Cameron, Osborne, Straw, Clegg, Kinnock and others, which gave ordinary people a chance to give those they rightly despise a political kick in the pants by voting against their will. Brexit has been caused by a justified hatred of the UK political class.
That those who caused the disaster see themselves as the answer to it is laughable. I remain hopeful that the English in particular will recover from the wave of jingoism which appears to have swept over them like a plague. But resistance must be organic and arise from the people themselves. I hope to see the emergence of a new, untainted and dynamic generation of young activists. My generation have bequeathed a terrible legacy.
-
Transparency/Investigative Reporting
-
In April 2015 the New York Times published a story about a company called “Uranium One” which was sold to Russian government-controlled interests, giving Russia effective control of one-fifth of all uranium production capacity in the United States. Since uranium is considered a strategic asset, with implications for the production of nuclear weapons, the deal had to be approved by a committee composed of representatives from a number of US government agencies. Among the agencies that eventually signed off the deal was the State Department, then headed by Secretary Clinton. The Committee on Foreign Investment in the United States (CFIUS) comprises, among others, the secretaries of the Treasury, Defense, Homeland Security, Commerce and Energy.
[...]
What the Clinton campaign spokesman failed to disclose, however, was the fact that a few days before sending his rebuttal to the New York Times, Jose Fernandez wrote on the evening of the 17 April 2015 to John Podesta following a phone call from Mr Podesta (Email ID 2053): “John, It was good to talk to you this afternoon, and I appreciate your taking the time to call. As I mentioned, I would like to do all I can to support Secretary Clinton, and would welcome your advice and help in steering me to the right persons in the campaign”.
Five days after this email (22 April 2015), Clinton spokesman Brian Fallon wrote a memo to the New York Times, declaring that “Jose Fernandez has personally attested that ‘Secretary Clinton never intervened with me on any CFIUS matter’,” but Fallon failed to mention that Fernandez was hardly a neutral witness in this case, considering that he had agreed with John Podesta to play a role in the Clinton campaign.
The emails show that the contacts between John Podesta and Jose Fernandez go back to the time of internal Clinton campaign concern about the then-forthcoming book and movie “Clinton Cash” by Peter Schweizer on the financial dealings of the Clinton Foundation.
-
Assange, the notorious founder of Wikileaks, detailed plans to unleash a fresh batch of leaked documents each week until the November 7 presidential election. The first of these leaks was due yesterday, but instead of documents intended to derail the Clinton campaign, we got a plug of Assange’s book and an echo of previous statements that the leaks would come once a week between now and the election.
The documents are said to expose Clinton, the military, the oil industry, and Google.
Seriously. Google.
Eric Schmidt, former CEO of Google and its current chairman seems to be the lynchpin in Assange’s new master plan. In an excerpt from his 2014 book ‘When Google Met Wikileaks,’ Assange accuses Schmidt of having ties to the State Department when Hillary Clinton was Secretary of State and working closely with her campaign.
-
The controversial whistleblower organization WikiLeaks on Friday released emails that they say are linked to Hillary Clinton campaign chairman John Podesta.
While much of the new batch of hacked emails are benign newsletters and shared articles, one note in particular has gotten attention for offering a glimpse into Hillary Clinton’s paid Wall Street speeches. The email depicts Clinton acknowledging the security issues with using her BlackBerry and suggests that she considers herself a political moderate. It also alleges that she dreams of “open trade and open borders,” among other topics.
But some of the most intriguing excerpts come when Clinton is addressing issues of Wall Street while actually on Wall Street. In the hacked email, the Democratic presidential nominee discusses the “rigged system,” and the causes of and solutions to the financial crisis in an unguarded tone, framing large banks and investment firms as partners rather than problems.
-
Environment/Energy/Wildlife/Nature
-
Solar panels generated more electricity than coal in the past six months in a historic year for getting energy from the sun in the UK, according to a new analysis.
Research by the Carbon Brief website found that solar generated nearly 7,000 gigawatt hours of electricity between April and September, about 10 per cent more than the 6,300GwH produced by coal during the same period.
The figures represent a dramatic turnaround in the UK’s electricity supplies.
The first ever day when solar produced more than coal was only on 9 April – when there was no coal-fired electricity for the first time since 1882. But then May became the first ever month when this happened.
-
Four minutes before 10am on Friday morning, Reuters provided an update on the death toll in Haiti. At a minimum, the news agency said, 572 people had lost their lives as a result of Hurricane Matthew.
At almost precisely the same time, CNN was broadcasting live footage of the storm as it passed northwest along the coast of Florida, from where more than two million people had fled. The winds were strong, the waves powerful and there was genuine concern about the potentially deadly impact of the storm surge.
But at that moment, the number of US fatalities as a result of the category four storm was zero. The Haitian death toll barely made a mention in the network’s rolling coverage.
-
Hurricane Matthew’s devastation in Haiti has left the nation facing a humanitarian crisis as corporate media shifts its focus to the storm’s encroachment onto U.S. shores.
As the brief U.S. news coverage of Haiti dissipates, aid groups on the ground are still struggling to reach the most impacted regions, while residents grapple with flooding, mudslides, and a shortage of shelters. The storm’s 145 mile-per-hour winds also took down a bridge, tore the roofs off of houses, and damaged at least one hospital and clinic.
Matthew killed at least 11 people in the Caribbean on Tuesday, with five of those in Haiti, including a 26-year-old man who was attempting to rescue a child from a rushing river, according to the Weather Channel. However, civil protection officials warned that the death toll is hard to calculate due to the extensive damage.
“It’s the worst hurricane that I’ve seen during my life,” one official, Fidele Nicolas of Nippes, told the Associated Press. “It destroyed schools, roads, other structures.”
Marie Alta Jean-Baptiste, director of the Civil Protection Agency, also said Tuesday, “It’s much too early to know how bad things are but we do know there are a lot of houses that have been destroyed or damaged in the south.”
-
NOAA-supported scientists working in the Hawaiian Archipelago have characterized the most extensive deep coral reefs on record. They found several large areas with 100 percent coral cover and concluded that deep coral reefs have twice as many species that are unique to Hawaii than their shallow-water counterparts.
-
Finance
-
Leading foreign academics from the LSE acting as expert advisers to the UK government were told they would not be asked to contribute to government work and analysis on Brexit because they are not British nationals.
The news was met with outrage by many academics, while legal experts questioned whether it could be legal under anti-discrimination laws and senior politicians criticised it as bewildering.
“It is utterly baffling that the government is turning down expert, independent advice on Brexit simply because someone is from another country,” said Nick Clegg, the Liberal Democrats’ EU spokesman.
“This is yet more evidence of the Conservatives’ alarming embrace of petty chauvinism over rational policymaking.”
Sara Hagemann, an assistant professor at the London School of Economics who specialises in EU policymaking processes, EU treaty matters, the role of national parliaments and the consequences of EU enlargements, said she had been told her services would not be required.
-
In an attempt to keep the EU-Canada trade deal CETA on track, the European Commission has drawn up a declaration aimed at reassuring those worried by the implications of the deal. A five page document was leaked last night and has been scrutinised by lawyers and trade experts.
Guy Taylor, the trade campaigner for Global Justice Now said
“These leaked documents prove just how much trouble this toxic trade deal is in. They show a panicky commission in Brussels issuing a series of defensive declarations, organising extraordinary meetings of ministers, and staying in a permanent state of crisis to try and legitimise a trade deal that is deeply unpopular and deeply undemocratic.
-
Britons are EU citizens too. What’s missing from the practical arguments about Brexit is the recognition that a solemn social contract is being destroyed
[...]
Theresa May values “the spirit of citizenship”. I know because she said so in her speech at the Conservative party conference. She waxed lyrical about an ethos “that means you respect the bonds and obligations that make our society work. That means a commitment to the men and women who live around you.”
Forgive me if I choke on my rich tea biscuit, Theresa. I have a citizenship that I am proud of, that links me to a wider community, that guarantees me rights and freedoms, and it’s being revoked against my will.
-
James Galbraith’s articles and interviews collected in his book Welcome to the Poisoned Chalice trace his growing exasperation at the “troika” – the European Central Bank (ECB), IMF and EU bureaucracy – which refused to loosen their demand that Greece impoverish its economy to a degree worse than the Great Depression. The fight against Greece was, in a nutshell, a rejection of parliamentary democracy after the incoming Syriza coalition of left-wing parties won election in January 2015 on a platform of resisting austerity and privatization.
-
AstroTurf/Lobbying/Politics
-
Excerpts of Hillary Clinton’s remarks during paid speeches to Goldman Sachs, Deutsche Bank, Morgan Stanley, and other groups were leaked online Friday afternoon by WikiLeaks. Clinton, who was paid upwards of $225,000 per speech, earned more than $22 million on the paid speaking circuit after resigning as secretary of state.
The excerpts are revealed in an email from Tony Carrk, the research director of the Clinton campaign, to John Podesta, the campaign chairman, and other top campaign officials. Carrk, who did not respond to a request for comment, highlighted in the memo the most politically damaging quotes from each paid speech, under headers including “CLINTON ADMITS SHE IS OUT OF TOUCH,” “CLINTON SAYS YOU NEED TO HAVE A PRIVATE AND PUBLIC POSITION ON POLICY,” and “CLINTON REMARKS ARE PRO KEYSTONE AND PRO TRADE.”
The wealth Clinton accumulated was a topic at the paid events.
Discussing middle class economic anxieties, Clinton told a crowd at a Goldman Sachs-sponsored speech that she is now “kind of far removed because the life I’ve lived and the economic, you know, fortunes that my husband and I now enjoy, but I haven’t forgotten it.”
But the discussions were also an opportunity for Clinton to speak candidly about policy, politics, and her approach to governing.
-
The Office of the Director of National Intelligence and the Department of Homeland Security today jointly charged that the Russian government was responsible for directing a series of intrusions into the networks of US political organizations and state election boards. In a “joint security statement,” officials from the two agencies declared they were “confident” that the government of President Vladimir Putin was behind the hacks and the publication of data obtained from them—some of it doctored—specifically to impact the results of the upcoming US elections.
-
The U.S. said publicly for the first time that intelligence agencies are “confident that the Russian government directed” the hacking of American political groups and leaked stolen material in order to interfere with the Nov. 8 election.
“These thefts and disclosures are intended to interfere with the U.S. election process,” the Office of Director of National Intelligence and the Department of Homeland Security said in a joint statement on Friday. “We believe, based on the scope and sensitivity of these efforts, that only Russia’s senior-most officials could have authorized these activities.”
While intelligence officials had previously said privately that they blamed Russia for the attacks, Friday’s announcement puts pressure on President Barack Obama’s administration to respond even as relations with Moscow rapidly deteriorate over everything from Syria and Ukraine to nuclear cooperation.
-
In an official statement today, the Director of National Intelligence and Department of Homeland Security officially blamed Russia for stealing and publishing archived emails from the Democratic National Committee this summer.
“The recent disclosures of alleged hacked e-mails on sites like DCLeaks.com and WikiLeaks and by the Guccifer 2.0 online persona are consistent with the methods and motivations of Russian-directed efforts,” the statement reads. “We believe, based on the scope and sensitivity of these efforts, that only Russia’s senior-most officials could have authorized these activities.”
-
Republican strategist Ana Navarro delivered a passionate rebuke of Donald Trump during an appearance on CNN Friday night.
Reacting to sexually aggressive comments about women the GOP nominee made in a leaked tape from 2005, Navarro said it was high time for the Republican party to call him out.
“How many times does he get away with saying something misogynistic before we call him a misogynist?” she asked. “How many times does he get away with saying something sexist before we acknowledge that he is a sexist? It is time to condemn the man.”
The former Jeb Bush supporter and John McCain adviser called Trump a “pig” and said his comments were “vile.”
-
With only 31 days to go until Election Day, a growing number of elected Republicans are demanding Donald Trump, their party’s nominee for president, step down.
-
States With an October 11 Voter Registration Deadline Florida, Georgia, Illinois, Indiana, Kentucky, Louisiana, Michigan, Montana, New Mexico, Ohio, Pennsylvania, Tennessee, Texas, Utah Territories: American Samoa, District of ColumbiaNext to November 8, the most significant day in the electoral calendar this cycle may be October 11. That’s the deadline for voter registration in 16 states and territories, representing some two-fifths of the US population. The list includes seven of the top 10 states in terms of electoral votes, and several of the most hotly contested campaign battlegrounds, including Florida, Ohio and Pennsylvania.
In the 2012 election, some 66 million eligible voters, or 30 percent of the total, were unable to vote due to lack of registration. Unregistered voters account for the bulk of the US’s comparatively low voter turnout, as 90 percent of citizens who register typically go on to vote. Compared with registered voters, those who don’t register are more likely to be young, lower-income and people of color.
Despite this—or perhaps because of this—corporate media have done little to alert the public about the upcoming deadline, or about voter registration in general. A search of Nexis transcripts from the three major broadcast news outlets—ABC, CBS and NBC—turned up no stories on any news show talking about registration deadlines over the past month. (These networks do have information about voter registration deadlines on their websites—but people looking online for information about the deadlines are people who don’t need to be informed that there are deadlines.) Considering the way shows like Meet the Press and This Week and Face the Nation are obsessed with the minutiae of campaign strategy, the failure to discuss the critical factor of the voter registration timeline seems like a major gap.
-
Here’s how:
— Two days before the second presidential debate, the government of the United States officially accused Russia of a hacking campaign aimed at interfering in the U.S. election. In a joint statement, absent any specifics or technical details, the Department of Homeland Security and the Director of National Intelligence stated “the recent [hacked email] disclosures… are consistent with the methods and motivations of Russian-directed efforts… based on the scope and sensitivity of these efforts, only Russia’s senior-most officials could have authorized these activities.”
— The statement goes on to detail how only Democratic servers were attacked, meaning the American government is claiming that Russia is trying to throw the election to Donald Trump, plain and simple. It is left unsaid why the Russians would risk cyberwar with the United States to do this, as many have suggested Trump is a neocon in spirit whose loose finger will be on the nuclear button from day one. Clinton is much more of a political realist, comfortable with the business-as-usual of the past eight years that has gone in Russia’s favor in the Ukraine and Syria. She in fact seems like the stable known known, always a preference.
— Though the first “Russian” hacks were reported in July, it is only 48 hours before the second presidential debate that the statement was released. It could easily have been held until Monday, there is no national security urgency for this to come out Friday. However, with the timing, Trump, essentially tied with Clinton in the polls, will now spend much of the debate defending himself. Since the statement includes no details, only accusations, it is hard to see how anyone could defend themselves. It would be near-impossible for Trump to come out ahead Sunday night; this is a near-coup.
— Despite the certainty with which the U.S. government has accused Russia of trying to influence the election by hacking into secured email servers, the FBI maintains there is no evidence the Russians or anyone else accessed Clinton unsecured, unencrypted email server laden with actual classified materials, including during Clinton’s first trip to Moscow when she sent and received encrypted email over the Internet and WiFi.
-
Censorship/Free Speech
-
For some 11 months, the makers of the new movie “I’m Not Ashamed” about the young girl who was the first victim of the Columbine killers in Colorado in 1999 were unable to promote their movie through Youtube.
The trailer was taken down late in 2015, and the movie’s entire channel then was suspended.
It’s back now, with the movie opening on Oct. 21, but the makers still want to know why the Internet company took the damaging action.
-
Standing in Rudder Tower, the building named after his former rival, award-winning journalist and Aggie Tom DeFrank told the story of The Battalion’s censorship from Texas A&M administration during his time as an editor exactly 50 years ago on the birthday of the university.
DeFrank is currently a contributing editor for the National Journal and was the White House correspondent for Newsweek. DeFrank has covered every president since President Lyndon B. Johnson, and has written a book on President Ford titled “When I’m Gone.”
DeFrank was the speaker during the latest Aggie Agora session, a seminar and speaker series meant to educate students and community members willing to come. DeFrank’s speech focused on his time at The Battalion dealing with his advisor, Jim Lindsey, and James Earl Rudder, the 16th president of Texas A&M University, for articles depicting the university in a non-flattering light. The events eventually led to DeFrank being fired from The Battalion.
-
A statue of Mahatma Gandhi will be removed from a university campus in Ghana after professors launched a petition claiming the revered Indian independence leader and thinker was racist.
The statue of Gandhi was unveiled in June at the University of Ghana campus in Accra by Pranab Mukherjee, the president of India, as a symbol of close ties between the two countries.
-
It could be bought for just under £20 and was described as a “sexy Saudi burka Islamic costume” with “a lovely soft stretch material”.
Amazon users outraged by the product branded the online store as “disgusting racists”.
One person said: “You’re all disgusting racists. My culture is not your costume.”
While another commented: “A person’s culture is NOT a fancy dress costume,” and one more added: “Is this some sort of mockery to the religion.”
-
While we’ll try to keep the grave-dancing at a minimum, it wasn’t difficult to see this coming. Game publisher Digital Homicide has something of a history of lashing out against any negative reviews it might receive, of which there are many. Whether it is more high profile targets like well-followed YouTube game reviewers, or merely lowly Steam customers that offered reviews of Digital Homicide games, the company has taken to simply suing everyone for all the things as its reaction. It seemed easy to recognize that this was not a winning business strategy in general, but when Steam reacted to the latest attempts at litigation by simply dropping all Digital Homicide games from its store, things clearly became dire for the company.
And now the story comes to a close with a conclusion pretty much everyone saw coming: Digital Homicide has filed a motion to dismiss its lawsuit against those Steam customers, declaring the company to be financially ruined and unable to move forward with the litigation.
-
A couple weeks ago, notorious developer of crappy Steam games Digital Homicide made waves by suing 100 anonymous Steam users, who they deemed a “hate and harassment group,” for $18 million. Now, however, the suit’s been dismissed.
In a motion to dismiss filed last week, Digital Homicide said that their business had been “destroyed,” rendering them unable to continue pursuing the suit. On Friday, it was approved.
-
Waving a large Palestinian flag and holding signs reading “Stop censoring our movement,” some 15 protesters gathered outside of Mark Zuckerberg’s San Francisco house on Friday to protest Facebook’s temporary suspension of social media accounts that belong to Palestinian journalists.
Nick Pardee, a member of the Party for Socialism and Liberation, which put the protest together said the suspension of Palestinian accounts showed a pro-Israel bias. Accounts in Israel, including those of government officials, are not removed despite inciting violence against Palestine, he said.
“These people are genocidal, and Mark Zuckerberg has no interest in censoring them,” he said.
-
Ben Affleck may have sat down for a slew of in-depth interviews promoting his new film The Accountant this week, but chances are you won’t get to see them in full.
-
Derry City and Strabane District Council has asked newsagents to stop selling the Sun to show “solidarity” with the families of the 1989 Hillsborough Stadium disaster, which was gratuitously misreported by the Tory tabloid. The council also backed a Liverpool-based campaign for all shops to boycott the newspaper.
The request was proposed by Independent councillor Paul Gallagher, who has previously stood for the Irish Republican Socialist Party (IRSP), the political wing of the INLA. His motion received unanimous backing from Sinn Féin, the largest party on the council, and the SDLP. All the unionists abstained, apart from one who voted against.
-
The disappointment is echoed by others in the audience as many are still unsure where the festival stands with its ongoing controversy over artistic freedom.
Still, most are staying hopeful the festival will return to its former glory, back to normal again.
For the past two years, Asia’s premier film festival has been in a fierce battle with the Busan metropolitan Government over its decision to screen a documentary that the Busan city mayor and former BIFF chairman adamantly opposed.
The contentious film, The Diving Bell, criticized the South Korean Government’s rescue efforts in the aftermath of the Sewol Ferry disaster, which took the lives of more than 300, most of whom were high school students.
-
The Supreme Court urged on Friday the federal government to stop harassing the director of feature film ‘Maalik’ and submit a report on objectionable content in the movie.
Meanwhile, the Central Board of Film Censors (CBFC) admitted before the court that the ban on ‘Maalik’ had been imposed without investigating complainants.
The court observed that there was nothing objectionable in the film under Section 9 of the Motion Pictures Ordinance, 1979.
The two-judge bench, comprising Justice Umar Ata Bandial and Justice Qazi Faez Isa, is hearing the federal government’s appeal against the Sindh High Court judgment.
-
-
-
-
-
-
-
-
Privacy/Surveillance
-
I’ve reviewed Oliver Stone’s movie Snowden elsewhere, and it’s well worth seeing just as a movie. But of course the issues brought up by Snowden the man, and Snowden the movie, are more complex than fit into two hours.
-
The article goes on to say, “The information believed to have been stolen by Mr. Martin appears to be different in nature from Mr. Snowden’s theft, which included documents that described the depth and breadth of the NSA’s surveillance.”
The problem with all this talk about the “theft” and “stealing” of secrets is that while Snowden, one of the most prominent whistleblowers of the modern era, has indeed been charged by the federal government with theft—along with two violations of the Espionage Act—he’s been convicted of no crime. Were he to stand trial, he would no doubt try to offer a public interest defense of his actions—as the Parliamentary Assembly of the Council of Europe has urged that he be allowed to do—saying that the need to expose government wrongdoing overrode the law against unauthorized release of government documents.
The Times may believe that such a defense would be unsuccessful—and no doubt many legal experts would agree with that assessment. Still, it’s unusual for journalists to assume that someone accused of a crime is guilty, in effect taking the role of judge and jury upon themselves.
Such an assumption is particularly problematic in this case, because the same section of the legal code that is used to charge Snowden with theft of “any record, voucher, money, or thing of value” also criminalizes “whoever receives, conceals, or retains the same with intent to convert it to his use or gain, knowing it to have been embezzled, stolen, purloined or converted.” There is no explicit exception for journalists there, any more than there’s an exception for whistleblowers.
If we’re going to call Snowden’s documents “stolen,” then journalists frequently receive “stolen” records from sources and use them as the basis for stories—as the Times itself has done with documents released by Snowden. If Snowden is a thief, then the New York Times is a fence.
-
In a shift from an earlier proposal, the Federal Communications Commission’s final rules to regulate the privacy practices of internet service providers are expected to be in line with the Federal Trade Commission’s approach, according to telecom and agency sources.
FCC Chairman Tom Wheeler has two other big-ticket items on his year-end agenda, cable set-top boxes and pricing for business data lines used by banks, hospitals and the like. As such, it appears the top telecom regulator will grant the private sector’s pleas to make the new privacy regulations distinguish between “sensitive” and “nonsensitive” data.
-
I’m guessing this is the same source who went to both publications, but it continues to raise more questions about this. Forcing Yahoo to actually install code is a big, big deal and gets back to the questions raised by the DOJ trying to force Apple to do the same thing. And, once again, this is the kind of thing the government isn’t supposed to be able to do in secret. Yes, individual orders and details about who or what is being searched can and should be kept secret, but requiring a company to install code that sniffs through every email… that’s not how these things are supposed to work.
-
The National Security Agency came out in support of encryption again Wednesday, but privacy advocates were quick to contest the agency’s stance, criticizing it for having a different definition of the term than others.
Glenn Gerstell, general counsel for the NSA, stressed that the agency believes in strong encryption multiple times during a panel, “Privacy vs. Security: Beyond the Zero-Sum Game,” at Cambridge Cyber Summit here at MIT, on Wednesday.
-
-
-
-
-
Technology has always played an inextricable role in spying, and today, that means one or more data centers underpin any spying operation.
It comes as no surprise that a US surveillance outpost in the UK has a data center, as revealed by a story published last month by The Intercept, the aggressively anti-NSA investigative online magazine published by First Look Media. The story reveals an unprecedented amount of detail about the activities taking place at Menwith Hill Station, relying on classified US government documents leaked by former NSA contractor Edward Snowden.
Glenn Greenwald, one of The Intercept’s founding editors, was one of the key journalists who wrote the first series of stories based on the Snowden leaks in 2013. Greenwald wrote his for The Guardian.
-
Ex-Yahoo employees have spoken anonymously to Motherboard about the news that Yahoo had built an “email scanner” for a US security agency, likely the FBI or the NSA. These sources — at least one of whom worked on the security team — say that in actuality, the NSA or FBI had secretly installed a “rootkit” on Yahoo’s mail servers and that this was discovered by the Yahoo security team (who had not been apprised of it), who, believing the company had been hacked, sounded the alarm, only to have the company executives tell them that the US government had installed the tool.
The sources in the article say that the “rootkit” was “buggy” and “poorly designed.”
In the security world, a rootkit is a program that changes the operating system to create administrative (“root”) access that is invisible to the system’s actual administrator. For example, in 2005, Sony-BMG put a covert rootkit installer on more than six million audio CDs; when inserted into Windows computers, these CDs silently updated the Windows kernel so that it would not report the existence of files or processes whose names started with “$sys$”. Then the CDs installed an anti-ripping program that started with $sys$ and tried to shut down any attempt to rip an audio CD — because the program started with $sys$, users and their anti-virus software couldn’t see the programs’ files on their drives, nor would the programs appear in the computers’ process list.
-
So, one of the things in the USA Freedom Act is a provision requiring that the White House declassify any “novel interpretations” of the law in ordering surveillance. This was to avoid the situations, such as under the Section 215 program, where the intelligence community reads words to mean things differently than anyone else would read them. Now, given what we’ve learned so far about the Yahoo email scanning case and the fact that it clearly goes beyond what people thought the law enabled, it seems clear that there’s some interpretation somewhere that’s “novel.”
-
Furthermore, it finds that the 68-day gap between the seizure and search was unreasonable. The state argued that the investigation was “complex,” but the court points out investigators obtained five other search warrants during that same time period.
Even if it had been more timely in its acquisition of a warrant, that still wouldn’t have been able to rescue the evidence it located on the suspect’s phone. Because the underlying seizure was performed without probable cause, the use of a warrant for the search did nothing but create a paper trail for “poisoned fruit.”
Hopefully this reversal will deter future seizure attempts by state and local law enforcement. Without the ruling in place, anything from cars to computers could end up being taken and held by police under the assumption that criminals use such items. That’s not probable cause. That’s not even reasonable suspicion. It’s fishing expeditions waiting to happen and speculation taking precedent over Fourth Amendment protections.
-
Well, this is somewhat unexpected. Earlier this year, we noted that Congress was working on a plan to undermine the Privacy and Civil Liberties Oversight Board (PCLOB). But apparently, the Intelligence Community, in the form of Director of National Intelligence, James Clapper, is against this idea.
The PCLOB was initially created as part of the PATRIOT Act, but was basically given no real power. In 2007, Congress finally gave it a bit more power and independence, only to watch both the Bush and Obama administrations ignore it by not appointing anyone to the board. That finally changed in 2012 — just in time for the Snowden leaks (though it has been without a chairperson, since the last one left earlier this year). The PCLOB then put out a scathing report about the NSA’s mass surveillance on Americans under the Section 215 program, though it wasn’t as concerned about PRISM and upstream collection under the Section 702 program. For years now, the PCLOB has supposedly been investigating surveillance under Executive Order 12333, which we’ve been told by insiders is the main program the NSA relies on for surveillance (the others just fill in the gaps).
-
After the US/EU “safe harbor” on data protection was tossed out thanks to NSA spying being incompatible with EU rights, everyone had tried to patch things up with the so-called “Privacy Shield.” As we noted at the time, as long as the NSA’s mass surveillance remained in place, the Privacy Shield agreement would fail as well. This wasn’t that difficult to predict.
And there are already some challenges to the Privacy Shield underway, including by Max Schrems, who brought the original challenge that invalidated the old safe harbor. But things may have accelerated a bit this week with the story of Yahoo scanning all emails. This news has woken up a bunch of EU politicians and data protection officials, leading to some serious questions about whether it violates the Privacy Shield agreement.
-
The Snowden Effect continues. In addition to actual oversight finally being applied to surveillance programs, the breadth and scope of some programs continues to be narrowed. Some of this narrowing has been forced on the NSA by legislation. But some of it also appears to be shame-related. It’s no longer as acceptable to harvest vast amounts of data domestically, apparently.
Shane Harris at The Daily Beast notes that the latest Inspector General’s report [PDF] details a sharp decline in Section 215 requests since Snowden’s debut leak in June 2013.
-
Imagine a futuristic society in which robots are deployed to everybody’s house, fulfilling a mission to scan the inside of each and every residence. Does that mental image look far-off and futuristic? Well, this week’s Yahoo e-mail surveillance revelations perhaps prove this intrusive robot scenario has already arrived in the digital world.
Days ago, Reuters cited anonymous sources and reported that Yahoo covertly built a secret “custom software program to search all of its customers’ incoming e-mails for specific information.” Yahoo, the report noted, “complied with a classified US government directive, scanning hundreds of millions of Yahoo Mail accounts at the behest of the National Security Agency or FBI.”
Reuters then followed up, saying Yahoo acted at the behest of the secret Foreign Intelligence Surveillance Court. Not to be outdone, The New York Times reported Yahoo used its system designed to scan for child pornography and spam to search for messages containing an undisclosed “signature.” The Times said a FISA judge found probable cause to believe that this digital signature “was uniquely used by a foreign power.” The scanning has ceased, the report noted, but neither of the news agencies said how long the search lasted and when it began.
Yahoo denies how the reports portrayed its assistance, saying they are “misleading.” Other tech companies have denied participating in such surveillance as it was outlined in those reports.
-
Elizabeth Martin told the New York Times she would be shocked if her former husband Harold, whom she has not seen since 2009, betrayed his country by deliberately passing on government secrets.
Harold Martin, 51, from Glen Burnie, Maryland, was secretly arrested by the FBI in August after federal prosecutors said he illegally removed highly classified information and stored the material in his home and car. Martin worked for the same NSA contractor, Booz Allen Hamilton, that employed the whistleblower Edward Snowden, but his own motive remains a mystery.
-
Investigators have little doubt that a National Security Agency contractor arrested in August hoarded mountains of classified material, but so far they’ve found no evidence that he leaked anything to anyone, The New York Times reported Friday.
-
“While very few details are available about the case of another NSA contractor stealing confidential information, based on the information available thus far, there are some observations that can be made.
Mainly, there is no easy way to characterize insider threats.
-
-
On a half-dozen occasions in the last three years, top-secret information has leaked from the National Security Agency and appeared on the web. Government analysts concluded with alarm that the documents, including intercepted communications from Europe and Japan and the computer code for the N.S.A.’s hacking tools, had not come from the huge collection taken by Edward J. Snowden.
That meant there was at least one more leaker still at large, and when F.B.I. agents found in August that a former agency contractor had been taking home top-secret material, they thought they might have the culprit.
Now they are not so sure.
Harold T. Martin III, the contractor arrested by the F.B.I. on Aug. 27, brazenly violated basic security rules, taking home a staggering quantity of highly classified material. He had been doing this undetected, agency officials were chagrined to learn, since the late 1990s. But, officials say, they have not been able to definitively connect Mr. Martin, 51, a Navy veteran, to the leaked documents.
-
European Union privacy watchdogs are concerned by reports that Yahoo has been secretly scanning its users’ email at the request of U.S. intelligence services.
“It goes far beyond what is acceptable,” said Johannes Caspar, Commissioner for Data Protection and Freedom of Information in Hamburg, Germany.
Reuters reported on Tuesday that Yahoo had built a system for U.S. government agencies to search all of its users’ incoming emails. Other tech companies were quick to distance themselves, saying they would have challenged any such request in court.
-
The revelation this week that Yahoo scanned the incoming emails of hundreds of millions of Yahoo users set off a storm of condemnation. The real outrage is that this kind of government surveillance, frequently abetted by the collaboration of telecom and tech companies, is pervasive and has little or no oversight.
As told by Reuters and the New York Times, Yahoo received a secret order last year from a judge of the Foreign Intelligence Surveillance Court (FISC) that compelled the company to customize an existing scanning system (used to find and report child pornography and malware) to search emails for a computer “signature” tied to the communications of a state-sponsored terrorist organization. Emails containing the signature were turned over to the NSA or FBI — and Yahoo was barred from disclosing the matter.
-
-
Earlier this year, as you recall, there were two big cases in which the DOJ and FBI sought to force Apple to make significant technological changes to iPhone software in order to allow the DOJ to brute force the passcode on some iPhones used by some criminals. Eventually, after Apple (and others) pushed back, and public opinion was turning against the FBI, the DOJ miraculously announced that it found its way into both iPhones and the cases were dropped. But the issue of forcing companies (and Apple especially) to backdoor their way into encrypted iPhones certainly has not been dropped. And it appears that the FBI may be testing the waters to see if it can try again.
-
IT IS TIME to look up déjà vu in the dictionary. The FBI needs to unlock another iPhone and it still doesn’t know how to do it, despite making all that fuss about the San Bernadino one.
A report on Wired from an FBI press conference after a mass stabbing in America said that the FBI is in possession of an iPhone that belonged to now dead assailant Dahir Adan.
FBI special agent Rich Thorton told the conference that it would be handy to get into the phone and find out more about Adan, but that the FBI can’t. He explained that the search for a solution is on. Again.
“Dahir Adan’s iPhone is locked. We are in the process of assessing our legal and technical options to gain access to this device and the data it may contain,” he said.
We thought that the FBI had this sorted. The agency made a lot of fuss when it set about breaking into the iPhone 5C of San Bernardino gunman Syed Farook earlier this year.
-
Facebook is watching you.
The social media giant won the “Big Brother” Award in Belgium on Thursday. The award is named after the dystopian government surveillance in George Orwell’s “1984,” and given to the “biggest privacy-offender of the year,” according to the Flemish League for Human rights, which runs the awards, and its partners.
Facebook, nominated by international digital advocacy group EDRi, won after being criticized for its default privacy settings in a unanimous decision. The social network didn’t respond to requests for comment.
“Facebook has access to a wide range of personal data, and it tracks your movements across the web, whether you are logged in or not,” EDRi said. “And the devil is in the default: To opt out, you are expected to navigate Facebook’s complex web of settings.”
-
Civil Rights/Policing
-
It’s harder to get the police to believe somebody has 26 bodies buried in their backyard — which is probably why the police so rarely get tipped off about that sort of thing.
-
On May 31, the city of Chicago agreed to settle a whistleblower lawsuit brought by two police officers who allege they suffered retaliation for reporting and investigating criminal activity by fellow officers. The settlement, for $2 million, was announced moments before the trial was to begin.
As the trial date approached, city lawyers had made a motion to exclude the words “code of silence” from the proceedings. Not only was the motion denied, but the judge ruled that Mayor Rahm Emanuel could be called to testify about what he meant when he used the term in a speech he delivered to the City Council last December, at the height of the political firestorm provoked by the police shooting of 17-year-old Laquan McDonald.
In that speech, Emanuel broke with the city’s long history of denying the existence of the code of silence. He spoke of “problems at the very heart of the policing profession,” and said: “This problem is sometimes referred to as the Thin Blue Line. Other times it’s referred to as the code of silence. It is the tendency to ignore, deny, or in some cases cover up the bad actions of a colleague or colleagues.”
-
-
-
-
My flight touched down at Bangkok’s Suvarnabhumi airport without any problems, at about midnight on 5 October. I had been invited to share my experiences of Hong Kong’s umbrella movement at two universities in Bangkok and to talk about becoming a young politician.
But as I left the plane, I started to feel paranoid that officials at the immigration counter might take me away and deport me back to Hong Kong on the very same flight. A strange feeling came over me. I could see more staff than usual ahead of me. But there was nowhere else to go. When I stepped on to the bridge leading off the plane, I saw a crowd of immigration police. I knew something was wrong.
What surprised me was that, unlike when I was refused entry to Malaysia – in May 2015, this time I didn’t have to go to the counter to be taken away. This time the officials came to meet me.
They asked if I was Joshua Wong. I told them I was.
-
A prominent local media executive fired from Yahoo last year has filed a lawsuit accusing CEO Marissa Mayer of leading a campaign to purge male employees.
“Mayer encouraged and fostered the use of (an employee performance-rating system) to accommodate management’s subjective biases and personal opinions, to the detriment of Yahoo’s male employees,” said the suit by Scott Ard filed this week in federal district court in San Jose.
Ard, who worked for Yahoo for 3 ½ years until January 2015, is now editor-in-chief of the Silicon Valley Business Journal. His lawsuit also claims that Yahoo illegally fired large numbers of workers ousted under a performance-rating system imposed by Mayer. That allegation was not tied to gender.
Yahoo spokeswoman Carolyn Clark defended the company’s hiring and performance-review processes, which she said are guided by “fairness.”
“This lawsuit has no merit. With the unwavering support of our CEO, we are focused on hiring employees with broad and varied backgrounds, and perspectives,” Clark said. “Our performance-review process was developed to allow employees at all levels of the company to receive meaningful, regular and actionable feedback from others.
-
The complaint (PDF) filed by Scott Ard says that Yahoo’s “stack ranking” system was “without oversight or accountability” and was “more arbitrary and discriminatory” than stack ranking used by other companies.
The lawsuit claims that Yahoo’s Media Org employees were ranked from 0.0 to 5.0 before being subject to a “calibration” process by higher-level management. Ard claims employees weren’t told their numeric ranking but were only informed of their “Bucket” ranking, labeled “Greatly Exceeds, “Exceeds,” “Achieves,” “Occasionally Misses,” or “Misses.”
Ard was hired at Yahoo in 2011, where he had editorial control of the Yahoo.com homepage. In 2014, following a leadership change that put Chief Marketing Officer Kathy Savitt in charge of Media Org, Ard was shifted to a role in which he managed Yahoo Autos, Yahoo Shopping, and Yahoo Small Business.
-
Vanessa Rodel didn’t realize she was sheltering the most wanted man in the world until the morning after he showed up unexpectedly at her door.
Her houseguest from the United States had requested a newspaper. She discovered his high-profile identity when she recognized Edward Snowden’s face on the front page of the Hong Kong daily.
“I said ‘oh my God,’” Rodel told CNN. “The most wanted man in the world is in my house!”
The next Snowden arrested?
Rodel — who fled the Philippines — is one of several asylum seekers in Hong Kong who are now going public with a secret they kept for years.
For weeks in 2013, these impoverished people took turns hiding the man behind one of the biggest intelligence leaks in US history.
-
It’s one thing to bring in an e-voting system that most experts say is a bad idea in theory. But making it effectively illegal to point out flaws that exist in practice is really asking for trouble. Unless this proposed law is changed to allow independent scrutiny of the systems, Argentina will probably find this out the hard way.
-
Just last week, there were fresh claims about CIA torture of detainees at a black site in Afghanistan. Two Tunisian men told Human Rights Watch they were strapped to a board and held with their heads upside down in a barrel of water. They were beaten with metal rods, anally raped and threatened with a makeshift electric chair.
Yet the Senate Intelligence Committee, led by Sen. Richard Burr, still won’t release its full report on what was done to CIA captives.
-
In short: the government has not barred foreign academics from providing policy advice, at least not in any legal or other formal way.
To do so would be almost certainly unlawful: for example, the government would be in breach of the law of public procurement if it discriminated in favour of UK citizens instead of EU citizens when commissioning research services.
And there is no such bar set out in any published government document; it seems not to be in any contract specification or tendering document; and there does not even seem to be any written communication from the FCO stating the bar.
But senior managers at the London School of Economics (LSE) believed they had been told by the Foreign and Commonwealth Office (FCO) that there was now such a bar.
How did LSE senior managers come to believe the FCO had said there was such a bar?
-
History demonstrates the evils that arise from whipping up popular xenophobic nationalism. After the Tories trumpeted that companies will have to declare how many foreigners they employ, that foreign doctors will be phased out of the NHS, that taxi drivers will have to prove their immigration status, that fewer foreigners will be allowed to study at British universities and that landlords will have to check the papers of their foreign tenants, we will now be told by Theresa May that to oppose this surge of fascism is elitism. I call it fascist after careful consideration; I don’t know what else to call it. Immigrants to Britain are going to be hauled up to produce documents at numerous moments of daily life to prove their right to be here. They will not yet need to be identified by yellow stars, but anybody who does not see the direction of travel is a fool.
The ability of politicians and media to whip up popular racism is well demonstrated historical fact. I am simply appalled by the catalogue I have outlined above. It is astonishing to me that popular opinion, particularly in England, has been conditioned to the point where outright racism has become the accepted everyday level of political discourse. And it is not just the Tories. Blairites are using populist anti-immigrant rhetoric as their most potent attack on Corbyn. Rachel Reeves made a speech last week that channelled Enoch Powell in predicting violent reaction to immigrants, and in some ways was worse than Powell’s classical allusion. But while Powell’s anti-immigrant rant ended his chances of becoming Prime Minister in a more decent age, Reeves is firmly in today’s UK establishment mainstream.
The argument that immigration is impacting the living standards of ordinary working people is a demonstrable falsehood. If mass immigration made a country’s people poorer, then Germany and the USA would have the lowest living standards for ordinary citizens in the world. An economy is not a thing of fixed size with a set number of jobs. If it were not for immigration, there would have been no economic growth in the UK at all since the millennium.
-
But Burton seems not to be alone in feeling the need to convey that message to a young audience. The animated film How to Train Your Dragon 2 also featured an all-white cast of characters—except for the villain, Drago Bludvist, who is depicted as dark-skinned, hook-nosed and dreadlocked, and voiced by Djimon Hounsou, an actor from Benin…
-
Internet Policy/Net Neutrality
-
Facebook is reportedly bringing its campaign to connect millions more people to the Web to its own backyard.
As The Washington Post reports, the social network is reportedly in talks with government officials and wireless carriers to bring its Free Basics mobile app to North America and serve the 37 million US residents who are not currently using the Internet. Facebook is reportedly looking for a way to roll out Free Basics without running afoul of net neutrality rules, which derailed the program in India.
Similar to global versions, the US Free Basics would target low-income and rural Americans who can’t afford a reliable, high-speed Web connection at home or on their phone. The app allows folks to stretch their data plans by offering free Internet access to online resources like news, health information, and job offers.
Exactly which apps will be included have not been determined, though Facebook will likely be among them.
-
The hack of the Democratic National Committee this past summer, allegedly by Russia, prompted a political firestorm, but didn’t cause even a ripple in the US economy.
But imagine the economic firestorm that would result if online attackers brought the entire internet down, even temporarily.
You may not have to imagine it, according to Bruce Schneier, CTO of Resilient Systems, cryptography guru, blogger and international authority on internet security. In a recent post titled, “Someone is Learning How to Take Down the Internet,” he wrote that he had been told by multiple sources that, ““someone has been probing the defenses of … some of the major companies that provide the basic infrastructure that makes the Internet work.”
But according to some of his fellow security experts, you don’t really need to imagine it, since the chances of the internet really being taken down are remote. And even if it happens, it won’t cause catastrophic damage. Several commenters on Schneier’s post wondered why even hostile actors would want to take down the internet, since if they do, they won’t be able to use it either.
-
For years, we’ve noted how there’s absolutely zero financial or technical justification for usage caps on fixed-line networks. They don’t really help manage congestion, and as any incumbent ISP earnings report indicates, flat-rate broadband has proven incredibly profitable. But thanks to limited competition, caps are a great way to raise rates, hamstring streaming video competitors, and give incumbents a distinct advantage for their own services (aka zero rating). Ultimately, caps disadvantage startups and small businesses, while making broadband more expensive and confusing for everyone.
Needless to say, Comcast is pursuing this option with reckless abandon.
-
DRM
-
This week, the chief arbiter of Web standards, Tim Berners-Lee, decided not to exercise his power to extend the development timeline for the Encrypted Media Extensions (EME) Web technology standard. The EME standardization effort, sponsored by streaming giants like Google and Netflix, aims to make it cheaper and more efficient to impose Digital Restrictions Management (DRM) systems on Web users. The streaming companies’ representatives within the World Wide Web Consortium (W3C) were unable to finish EME within the time allotted by the W3C, and had asked Berners-Lee for an extension through next year.
Berners-Lee made his surprising decision on Tuesday, as explained in an email announcement by W3C representative Philippe Le Hégaret. Instead of granting a time extension — as he has already done once — Berners-Lee delegated the decision to the W3C’s general decision-making body, the Advisory Committee. The Advisory Committee includes diverse entities from universities to companies to nonprofits, and it is divided as to whether EME should be part of Web standards. It is entirely possible that the Advisory Committee will reject the time extension and terminate EME development, marking an important victory for the free Web.
-
HP to remove DRM from printers: In a statement that was full of we-did-it-to-protect-you rhetoric, HP has said that it’s going to remove DRM that it installed as an update on certain models of its printers that prevented users from using ink cartridges with security chips not manufactured by HP.
-
Intellectual Monopolies
-
The member governments of the UN World Intellectual Property Organization, after considering a confidential UN investigation report on whistleblower charges against WIPO Director General Francis Gurry, have decided to end the case without discipline, WIPO has said. Instead, members are working to bolster whistleblower protections, internal oversight and procurement procedures at the agency for the future.
-
Member governments of the UN World Intellectual Property Organization (WIPO) are working intensively in a closed-door session today to make changes to the way allegations of wrongdoing against high-ranking WIPO officials are handled. What is not clear from the secretive discussions is whether any action will be taken against the director general as a result of a UN investigation of his activities, for which the UN report is on the meeting agenda.
-
Backpage.com has been the target of lots of moralizing, grandstanding law enforcement types, who absolutely hate the fact that there’s a classified site out there where some users use it for prostitution (I know that some of the comments will discuss the question of whether or not prostitution should even be a crime, but right now it is, and so this article won’t focus on that other discussion). As we’ve noted time and time again, it’s bizarre that law enforcement folks keep blaming the platforms, when those platforms are actually really useful for law enforcement to track down, arrest, prosecute and convict people actually breaking the law. Still, the grandstanding forced Craigslist to completely shut down its adult section, and most of that traffic moved over to Backpage.
And now, the CEO of Backpage, Carl Ferrer, has been arrested in Texas for “pimping,” with both Texas Attorney General Ken Paxton and California Attorney General Kamala Harris pushing out grandstanding press releases to talk about how tough on prostitution and pimping they are.
There’s just one big problem in all of this: the charges are almost certainly completely bogus, and Harris and Paxton are flat out ignoring federal law on this matter. Specifically, they’re ignoring the law we talk about all the time: Section 230 of the Communications Decency Act. As we’ve noted over and over again, CDA 230 says that internet platforms are not liable for the content created by users. There’s an exception for federal criminal acts, but not for states. Various state Attorneys General have been whining about this for years, and demanding Section 230 get a new exception just for them, but that hasn’t happened. So Harris and Paxton clearly know about Section 230, and clearly know that they’re just ignoring the law. They apparently don’t care. They’re either too focused on the publicity grandstanding value of pretending like they’re “tough on crime,” or they’re hoping that by presenting emotional stories, they’ll win over judges and convince them to ignore Section 230.
-
The news that WIPO member states have endorsed a decision taken by the organisation’s Coordination Committee to drop any further investigation of the allegations of serious misconduct levelled against the organisation’s Director-General Francis Gurry is no surprise; a few days ago this blog predicted it would happen. However, for anyone who believes that the IP system is best served by transparency and accountability, the fact this outcome was so predictable does not make it any less depressing.
Ever since the then WIPO deputy Director-General James Pooley first accused Gurry of being involved in taking WIPO staff members’ DNA and in interfering to alter the outcome of a procurement process in his April 2014 Report of Misconduct, IAM has taken no position on the claims. We don’t know if they were true; but we do know that they should have been investigated quickly, thoroughly, independently and with full protection for witnesses.
-
Copyrights
-
It seems each day more people are willing to share ever more personal things on the Internet. Along these lines, in May of this year Kali Kanongataa a California resident used Facebook to live stream his wife giving birth. After portions the live stream ended up on television and publicized on the Internet, he sued ABC and Yahoo for allegedly infringing his copyright by displaying the video.
The day after the live stream, ABC’s “Good Morning America” ran a short segment about the live stream and showed a brief excerpt from the video that was up loaded by Mr. Kanogataa which had been widely viewed online since this airing. The clip also appeared on Yahoo, which has a partnership with ABC.
-
Pokémon Go is not available to buy in India so the game is being heavily pirated by fans. With legal moves underway to try and bring this behavior to a halt, the Gujarat High Court is now seeking advice on how to stop downloads to protect the public interest.
-
Streaming piracy is on the rise with the popular media center Kodi at the center of attention. While Kodi itself is a neutral platform, millions of people use third-party add-ons to turn it into the ultimate pirate machine. In less than a year, the leading add-on repository has seen the number of unique users double, which may be just the beginning.
Permalink
 Send this to a friend
Send this to a friend
10.07.16
Posted in News Roundup at 10:06 pm by Dr. Roy Schestowitz

Contents
-
There are plenty of useful and well-thought-out features on Tesla’s 17-in touchscreen, but the internet browser is not one of them. For years now, we have been used to high-speed internet browsing on our laptops, desktop and now even or phones, but Tesla’s browser is so slow that it feels like it’s from another era.
Model S and X owners have been asking for an update to the browser for a long time and unfortunately, it didn’t come with the recent 8.0 update, but Tesla CEO Elon Musk said yesterday that it will with an upcoming update, which will likely be in December.
Tesla’s operating system is built on a modified version of Linux Ubuntu. Musk says that Tesla aims to upgrade the Linux OS to 4.4 in Tesla vehicles in December. That’s when he expects they will be able to update the browser.
-
Desktop/Microsoft
-
Perhaps the world has gone truly mad. Or maybe Microsoft’s trying to pull the wool over our eyes prior to its major shift in patching strategy — the patchocalypse — widely anticipated this month. It’s even possible Microsoft wants to bring back the “Get Windows 10″ campaign, to drive Windows’ reputation even deeper into the dirt.
A Microsoft spokesman says it isn’t bringing back the “Get Windows 10″ campaign, but our old nemesis KB 2952664 reappeared suddenly yesterday afternoon, and Windows users are livid — and scared.
-
Login issues at Skype have bitten iTWire, with editor-in-chief Stan Beer being told his account has been suspended. After 16 hours of waiting, he is still unable to log in, and Microsoft now says it has lost his account and all its data.
A furious Beer would not rule out legal action. “This is unacceptable. I have been using my account practically every day for the past 10 years. It is vital to the operation of my company. If I do not have it reinstated immediately I will have no alternative but to consider my options and take legal action,” he said.
An email just received from Microsoft’s support team said: “We have checked our records and your account does not exist in the Microsoft system. Please check the spelling of your account. If you are sure this is the correct Microsoft account, it is also possible that it has expired due to inactivity.
“Your account will expire if you do not sign in regularly or within the first 10 days after registration. When the account is deleted, all messages, folders, and contacts are deleted as well. Incoming messages will be sent back to the sender as undeliverable, but the user name is immediately available for registration.”
After suffering repeated issues with Windows over many years, Beer thought he had escaped the clutches of Microsoft when he switched to OS X.
But last evening he was given a sharp reminder that the Typhoid Mary of the Internet has a long reach and can still foul up one’s day.
-
When you have data you want to get rid of forever, whom are you going to call? There’s one sure place to go: Redmond. You are assured of losing your data when you hand it to Microsoft.
The company is not in the habit of keeping backups. That’s so yesterday.
No, Microsoft is out there in front of them all, modern-looking chief executive Satya Nadella in the lead, preaching the gospel of getting rid of the old and welcoming in the new.
The bitter truth must now be acknowledged: veteran tech journo Bob Cringely said it first and I have repeated it for some time, but never seen it up so close. Microsoft is a marketing company, not a technology company.
-
When Lenovo released the Yoga 900-13ISK2 it became apparent that Linux and BSD users could not rely on closed source BIOSes. Of course while it is rather naive to think that a Microsoft Signature Edition PC would be Linux friendly, one could hope that at least it would not be Linux or BSD hostile. On further analysis one can see that this is not the case, and any would-be Linux user is in for a very difficult time trying to load any operating system other than Windows 10.
The exact reasons for this problem boil down to the inability of the BIOS to set Advanced Host Controller Interface (AHCI) mode for the SSD. Now I knew long ago that closed source BIOSes could become a problem back in the mid-1990s. I’ve spent considerable time researching the ways one can obtain a computer with FOSS firmware.
Before I go into the specifics of which computers actually have a BIOS with freely available source code allow me to recap some computer history. When we look at the original IBM PC BIOS we can see that it’s been well analyzed and that no other operating systems have been locked out. In addition to this there was no way to alter the BIOS save for swapping out the BIOS chip and putting in a different one. So for several years people didn’t give much thought to the BIOS, as long as their computer booted they could load whatever operating system they wanted, be it Unix, Minix, MS-DOS, CP/M, etc.
-
Server
-
With ContainerCon Europe currently underway in Berlin, we want to share some of the great progress the Open Container Initiative (OCI) has made.
The OCI was launched with the express purpose of developing standards for the container format and runtime that will give everyone the ability to fully commit to container technologies today without worrying that their current choice of infrastructure, cloud provider or tooling will lock them in.
-
A tweak to Microsoft’s Outlook.com cloud service has blocked a good number of people from accessing their messages.
Specifically, the baffling and unannounced change affects Outlook.com users with connected accounts: these are email accounts hosted on third-party servers (such as a company’s private server or an ISP’s mail server) that are accessed via the Outlook.com cloud. People with this setup are no longer able to send or receive mail through Redmond’s webmail service.
Reg reader David Barrett, who runs an internet-facing server for his friends and a UK health charity, said the issue has left those users who run Outlook.com with outside mail systems unable to get their email for days now.
“It happened around the end of last week/over the weekend and seems to have been a gradual rollout,” he told us.
-
Kernel Space
-
TODAY’S Legend of Linux is Ralf Flaxa, president of engineering at Suse (that’s the one with the gecko logo).
Flaxa has worked on Linux since the beginning and has been at Suse since 2002 in charge of several projects that have been rolled out not just at Suse but across the whole Linux ecosystem.
-
The release v2.29 (now rc1) is without dramatical changes, the small exception is libsmartcols where we have many improvements.
The old good cal(1) is more user-friendly now. It’s possible to specify month by name (e.g. “cal January 2017″) and use relative placeholders,
-
Today, October 7, 2016, renowned Linux kernel maintainer Greg Kroah-Hartman proudly announced the availability of the first point release to the latest Linux 4.8 kernel series.
-
-
-
-
Linux pioneer Linus Torvalds is a stand-up guy — he says what he feels. There’s no sugarcoating, and he’ll admit to faults, like recent issues with the Linux 4.8 kernel.
He was full of surprises at last week’s Linaro Connect conference, when he was asked about his favorite chip architecture. He didn’t blink before saying it was x86, not ARM.
It may have been the long history of x86 with PCs that influenced his answer. There’s little fragmentation of software and hardware with x86, and things just work.
Read more
-
-
With Intel’s 3D Xpoint Optane technology beginning to appear as extremely fast non-volatile memory and other advancing efforts in the NVDIMM space like ReRAM, persistent memory was a popular topic at this week’s LinuxCon Europe event in Berlin.
Persistent memory is about non-volatime memory that retains data while being DMA-capable and offer memory-like performance. There’s been a lot of work building up in this space from libraries supporting it to DAX (Direct Access) support in Linux file-systems for use on persistent memory. Several presentations were done this week about the latest tech and Linux support for it.
-
The F2FS (Flash-Friendly File-System) and EXT4 file-system feature updates have been sent in for the Linux 4.9 merge window.
-
The Intel Integrated Sensor Hub (ISH) is supported in the Linux 4.9 kernel code for benefiting Cherrytrail mobile/convertible/ultrabook hardware and newer.
The Intel ISH is an on-package sensor hub used on some systems in place of external sensor hubs. The ISH provides sensors like detecting device rotation, automatic backlight adjustment, and can also be responsible for some low-power sleep states. This is for Cherrytrail and newer, including some Skylake notebooks.
-
-
Graphics Stack
-
-
-
-
The open source OpenGL driver AMD radeonsi is now extremely close to having full OpenGL 4.4 support, and OpenGL 4.5 is now complete.
I’ve said it before, and I will say it again, the progress on open drivers in the past year has been pretty amazing.
Recently “GL_ARB_query_buffer_object” was added in for radeonsi (OpenGL 4.4), leaving only “GL_ARB_enhanced_layouts” left for full OpenGL 4.4 support.
-
Applications
-
-
Ubuntu Phone has an unofficial Instagram app called Instagraph, but (until now) there was no desktop client available for Ubuntu desktop.
Although Instagram is (imo) best experienced through its official mobile apps, you can login and browse your feed via the Instagram website.
But, next time you go to reach for your phone or open a new tab to browse your feed, try Ramme instead.
-
Proprietary
-
WhatsApp, the widely used free messaging system is now available on many platforms and operating systems. Previously, it was only available for the major platforms such as Android and iOS, but it has recently become available for ChromeOS – based devices like the Chromebooks and it seems to continue this trend of availability on as many platforms as possible.
-
Instructionals/Technical
-
-
-
In the course of my job at Red Hat, I work with Docker containers on Fedora Atomic host every day. The Atomic Host from Project Atomic is a lightweight container OS that can run Linux containers in Docker format. It’s been modified for efficiency, making it optimal to use as a Docker run-time system for cloud environments.
Fortunately I’ve found a great way to manage containers running on the host: Cockpit. Cockpit is a remote manager for GNU/Linux servers with a nice Web UI. It lets me manage servers and containers running on the host. You can read more about Cockpit in this overview article previously published here. However, I also wanted to automate running containers on the host, which I’ve done using Ansible.
Note that we cannot use the dnf command on the Atomic Host. The host is designed not as a general purpose OS, but to be more fit for containers and other purposes. But it’s still very easy to set up applications and services on the Atomic Host. This post shows you how to automate and simplify this process.
-
Wine or Emulation
-
The Wine Staging release 1.9.20 is now available.
-
The Wine Staging development team announced recently the release and immediate availability of the Wine Staging 1.9.20 maintenance update for GNU/Linux operating systems.
Coming hot on the heels of the Wine 1.9.20 development release, which brought reimplementation of the clipboard API (Application Programming Interface), message handling in WebServices component, multiple new API Set libraries, as well as a bunch of bug fixes, Wine Staging 1.9.20 adds some improvements on its own end.
-
Games
-
Here’s a way to grab Tomb Raider while supporting the porter Feral Interactive directly, it’s currently dirt-cheap on the Feral store.
£4.49 for a major game like Tomb Raider until the 13th of October. It has it’s issues with performance in places, sure, but since the patch it is better. I still hope they are able to push it a little more in future, but at that price it’s a fantastic deal.
Could be something ideal to start your weekend with, let me know if you plan to pick it up, and what you think to it!
-
-
-
-
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Qt 5.8 will include IoT-oriented “Qt Lite” technology that enables fine-grained configuration and supports small-footprint IoT gizmos without OpenGL.
The Qt Company announced a Qt Lite project that aims to extend the Qt development framework to smaller footprint Internet of Things devices with as little as 16MB RAM and flash. The Qt Lite technology will initially appear in Qt 5.8, including a more flexible configuration system for the cross-platform development framework, as well as a new 2D renderer for devices that can’t run OpenGL. Qt Lite also provides a more accessible, lightweight set of development tools.
-
KDE Neon, the newly popular distribution produced by KDE and Kubuntu developer Jonathan Riddell and based on Ubuntu is now available in version 5.8. The best part of this latest release? It includes the latest long term stable release of Plasma 5.8. You can get additional details about this release from Jonathan Riddell’s blog.
-
-
GNOME Desktop/GTK
-
Now that my time as an intern is over, I want to take a moment to thank Outreachy for giving me the opportunity to be a part of this amazing experience. Also a big thank you to my mentor Jim Hall and the GNOME design team (Allan and Jakub) for the guidance and encouragements they provided throughout these months. And finally, a thank you to GNOME community for being awesome ^_^
-
-
New Releases
-
The Linux Lite 3.2 Beta release has arrived for developer testing and to give an idea about the recent changes made to the Linux Lite distro. It now features a new Lite Desktop widget. The GRUB bootloader has been set to its default configuration which enables multibooting other operating systems alongside Linux Lite.
-
Arch Family
-
This linux desktop is an homage to one of our favorite distributions, Arch Linux-and reader KudalGadgil shared it with us in our desktop show and tell pool. Here’s how you can get a similar look.
-
Slackware Family
-
The developers of the Slackware-based, server-oriented Superb Mini Server (SMS) GNU/Linux distribution announced recently the release of the ninth maintenance update in the stable 2.0 series of the operating system.
-
Red Hat Family
-
The day several Redhat trainers and industry folks met to talk about best practices and give feedback on the vision and mission ( and speed of progression) of Redhat Enterprise Linux (RHEL) and upstream / downstream projects and products. Among one of the most popular Sessions was the one by Robin Price and Martin Priesler on OpenSCAP which was a standing room only session with nearly 1/3 of attendants in attendance for this talk / session. Rita Carroll and others setup a interest list for those that would like to attend another OpenSCAP Workshop (mainly centered on a hands-on event but other venues seemed open for debate). If you’d be interested regardless of whether you like me were in attendance please email Rita @ rita@redhat.com with a simple subject line referencing OpenSCAP Workshop (Tysons Area).
-
When an application developer or architect tasked with exploring the possibilities that containerized applications offer, nothing is easier than the Red Hat Container Development Kit (CDK).
The Red Hat CDK has all the Cloud tooling you need for your local OSX, Linux or Windows environment and it has a few containers pre-configured for you to explore.
-
-
Finance
-
Fedora
-
I had a great time at the Libre Application Summit in sunny, hipster moustachioed Portland – many thanks to Sri for inviting me. Sorry this blog post is a bit late, but things have been really busy with the Fedora 25 Beta release (which we signed off on today).
For a first year conference without a crazy marketing budget or anything, attendance was great – it was a good size for the venue, the number of sessions, and the social events, things felt busy and there was a lot of people-getting-to-know-each-other going on. Sri, Adelia and friends did a great job of finding a good venue and getting a solid wifi network, providing food and coffee, and setting up some fun social events.
-
The first step in this is to make sure that the subject completely design team fedora. A second step is to check the validity according to legal terms.
In this category are the rules established by the international community and the teams fedora.
-
Alex Larsson from the Flatpak project, an open source initiative sponsored by Red Hat in an attempt to make cross-platform app deployment easier, announced on October 6, 2016, the release of Flatpak 0.6.12.
-
Back in August Fedora 25 switched to using Wayland by default in time for the project’s alpha release. With next week’s beta release, Fedora 25 is still using Wayland by default and it looks like it will remain that way unless any showstoppers appear.
Initially it wasn’t clear if Fedora 25 would continue using Wayland by default as it neared the final release, but so far so good. Adam Williamson of Fedora QA confirmed in the forums, “Wayland is the default for Fedora Workstation in F25 Beta, and barring any crazy showstoppers we didn’t know about showing up between now and Final, is likely to be the default for Final too.”
-
The beta of Fedora 25 will be released on-time next week.
It’s a bit rare in the Fedora space, but all relevant parties have signed off on the Fedora 25 Beta for it to ship on-time, 11 October. Often Fedora releases are challenged by delays due to blocker bugs, including earlier with Fedora 25 Alpha, but all appears to be in shape for shipping the beta next week.
-
GNOME Outreachy is a global program that offers historically underrepresented people of gender and race stipends to write code for several participating FOSS projects . Inspired by Google Summer Of Code, Outreachy offers participants hands-on internships for contributing to open source projects.
In 2016, the Outreachy internship dates are from December 6, 2016 to March 6, 2017. Participants work remotely from home while getting guidance from an assigned mentor and collaborating within their project’s community.
-
Debian Family
-
To help out making life for LEGO constructors in Debian easier, please join us on our IRC channel #debian-lego and join the Debian LEGO team in the Alioth project we created yesterday. A mailing list is not yet created, but we are working on it. 
-
People keep ignoring the status of the Pacemaker HA stack in Debian Jessie. Most people think that they should stick to Debian Wheezy.
Why does this happen? Perhaps little or none publicity of the situation.
Since some time now, Debian contains a Pacemaker stack which is ready to use in both Debian Jessie and in Debian Stretch.
-
-
Derivatives
-
Canonical/Ubuntu
-
Canonical’s Sergio Schvezov announced recently the release and immediate availability of the Snapcraft 2.19 tool for creating Snap universal packages, in the Ubuntu 16.04 LTS and Ubuntu 16.10 repos.
-
Dell just launched its new XPS 13 Developer Edition laptop in the US and European markets, and, as usual, they’re partnering with Canonical to deliver you the best Ubuntu Desktop experience as possible.
For those of you that aren’t aware yet, the Dell XPS 13 Developer Edition laptop was made possible as a part of a project called Sputnik, which attempted to identify the needs of developer when running an open source operating system like Ubuntu, which is currently one of the most popular GNU/Linux distributions in the world. Therefore, Dell XPS 13 Developer Edition laptop now ships with Ubuntu 16.04 LTS (Xenial Xerus).
-
A few hours ago, October 6, 2016, Canonical’s Adam Conrad announced that the upcoming Ubuntu 16.10 (Yakkety Yak) operating system has entered the Final Freeze development stage.
-
Flavours and Variants
-
Ubuntu MATE project leader Martin Wimpress announced today, October 6, 2016, that the latest MATE 1.16 desktop environment has landed in the stable repositories of the upcoming Ubuntu MATE 16.10 (Yakkety Yak) operating system.
-
-
SolidRun has updated its tiny, Linux-ready i.MX6 based MicroSoM modules with optional eMMC and NOR flash, improved FlexCAN, and TI WiLink8 wireless.
SolidRun has refurbished its NXP i.MX6-based MicroSoM computer-on-modules with new rev 1.5 versions featuring optional eMMC and/or NOR flash, among other additions. Despite some minor mechanical redesigns, the modules have the same 47 x 30mm dimensions, and are backward compatible. They can be plugged into existing MicroSoM companion products such as SolidRun’s sandwich-style, open-spec HummingBoard SBCs and CuBox-i mini-PCs. All the modules continue to run Linux or Android.
-
Logic Supply informs Softpedia about a recent case study they’re doing featuring drone control specialists Desert Rotor, a drone controller company that uses their ML100 industrial PC for its next-gen UAV control system.
First, we’d like to inform the reader that Logic Supply is the leading industrial and embedded computer hardware manufacturer. The company is being known for creating some of the most powerful industrial products, from mini and rugged panel PCs and thin client computers to dust-resistant, fanless, and ventless units that can be used in virtualization and IoT (Internet of Things) markets, or other applications.
-
Phones
-
Tizen
-
It is no secret that Samsung uses Spreadtrum’s SOCs for most of its budget and mid range smartphones. Spreadtrum’s current best chip happens to be the SC9860- a 16nm process based 2GHz octacore 64 bit Cortex A53 SOC; these are chipset specifications from the yester-year and the technology is now moving into more powerful heterogeneous architectures involving ARM’s Cortex A73, A72 and A57 standards(and the low powered A53 cores for better battery efficiency). Now, this might not make any sense to a normal user. But over at Samsung, Spreadtrum’s slow development pace for its chips seems to be holding the Korean smartphone giant down from offering better (or more) midrange products.
-
Android
-
The smart car market hasn’t exactly settled along the usual Google vs Apple camps and some do take both sides, if not their own. When BMW launched its BMW Connected service early this year, it seemed to have actually put up a stake on Apple’s iOS side of the fence. Apparently, it was only bidding its time. In its new update, the service finally gets its first Android app. But that’s not the only thing that’s new, as BMW Connected is also gaining support for the Apple Watch 2 and Amazon’s Alexa.
-
-
-
Google got us all hot and bothered with the launch of a new pair of smartphones earlier this week, but you can be forgiven for missing a major announcement regarding Android.
The details of the latest version of the operating system, 7.1 Nougat, have been revealed, and it’s missing some of the key features Google waxed lyrical about on Tuesday.
The biggest news is that Google Assistant, which is sort of like a souped-up version of Siri for Android, will remain exclusive to the Pixel and Pixel XL, in the near future at least. The virtual helper played a central role in Google’s event, with the company taking time to demonstrate how it supports two-way conversation and learns from you as you spend more time using it.
-
If, after seeing all the software goodies on Google’s new Pixel phones, you hoped that some of those cool features will trickle down to other Android phones capable of running Android 7.1 Nougat, you’ll be disappointed.
Google’s smart personal assistant Assistant (Google did not do us a favor when naming this one), as well as unlimited, free backup for full-resolution photos and videos will remain Pixel-only for the time being. Somewhat less surprisingly, non-stop customer support service won’t be included, either.
-
-
-
-
-
-
There were big changes announced at Google this week as the company’s “Google Hardware” team came out of hiding and announced a slew of products. The star of the show was definitely the Google Pixel, Google’s new pair of smartphones that the company is saying it designed while using HTC as a manufacturer. The advent of Pixel phones means Google is an Android OEM again, harkening back to the days when it owned Motorola. This time, though, the company is serious about hardware and software integration.
Android, however, is the world’s most popular operating system because of OEM partners like Samsung, Huawei, Xiaomi, and LG. And if Google wants Android to continue to deliver Google services to billions of people, it will still need all those partners. Google once again has a delicate balancing act to pull off. The company must do its best to deliver a Google-y Android phone while not stealing the thunder from other OEMs or putting them at a serious competitive disadvantage.
-
It has been one year since Syrian-Palestinian open technology leader Bassel Khartabil disappeared from his prison cell in Syria.
Bassel served as the public affiliate for Creative Commons Syria and contributed to Mozilla Firefox, Wikipedia, and other open communities online. He also was the CTO of Al-Aous, a publishing and research institution dedicated to archaeological sciences and arts in Syria. In November 2012, Foreign Policy named Bassel one of the world’s 100 top global thinkers.
-
Open source employees in Europe have it good, especially when we compare that market to the rest of the world. This is according to a new report by Dice and The Linux Foundation. The report says that out of 1,000 European respondents 60 percent believe it would be fairly easy to find a new job this year. Globally, the figure stands at about 50 percent.
“Demand for open source talent is growing and companies struggle to find experienced professionals to fill open roles”, says Bob Melk, president of Dice. “Rising salaries for open source professionals indicate companies recognize the need to attract, recruit and retain qualified open source professionals on a global scale. Regardless of where they reside around the world, these professionals are motivated by the opportunity to work on interesting projects”.
Most sought after skills are application development, the report says, adding that European businesses are doing more than their counterparts in other parts of the world in order to keep hold of the staff. Four out of ten professionals in Europe say the best part about their jobs is that they get to work on interesting projects, as well as the fact that they get to use “cutting-edge technology”.
-
Google has released a new open-source font called Noto, which supports 800 languages and covers 110 writing systems.
Short for ‘No more Tofu’, the name of the new typeface is a nod to what people call the default white boxes that appear when a computer doesn’t understand a character on a website.
“One of the goals of the project was to support every language and every character, so one of the things we wanted to do was make sure there’s no tofu for all our users,” said Bob Jung, an director of internationalization at Google.
-
Cartographer, which Google initially used internally only, enables real-time mapping inside buildings, the company says.
Like it often does, Google has released into the open-source community an indoor mapping tool called Cartographer that it has used internally.
Cartographer is designed to enable what is known as real-time simultaneous localization and mapping (SLAM)—or the ability to build a 2D or 3D map while at the same time keeping track of an individual or robotic agent’s location within that map.
The algorithms used in SLAM combine data from various sensors such as Light Detection and Ranging (LIDAR) systems and cameras to determine the position of an object within an environment and to map that environment.
-
Free Code Camp is an organization that teaches people to code. As part of this free training, student coders produce free code needed by nonprofit organizations. Free Code Camp doesn’t accept donations, but you can support them by buying t-shirts, hoodies and audiobooks through their store.
-
Web Browsers
-
Mozilla
-
We are happy to support National Cyber Security Awareness Month (NCSAM), a global effort between government and industry to ensure everyone has the resources they need to be safer, more secure and better able to protect their personal information online.
We’ve talked about how cybersecurity is a shared responsibility, and that is the theme for National Cybersecurity Awareness Month – the Internet is a shared resource and securing it is our shared responsibility. This means technology companies, governments, and even users have to work together to protect and improve the security of the Internet. We all have to do our part to make the Internet safer and more secure for everyone. This is a time for all Internet users to Stop. Think. Connect. This month, and all year long, we want to help you be more “CyberAware.”
-
CMS
-
This article will be about OTRS, a ticket system we’re using at the FSFE for handling things like swag orders, internship applications and so on. But it could actually be about any software. OTRS just happened to be in the line of fire this time.
This will be an example in how to (not) manage user expectations. You may know the principle of least astonishment, and this will be a typical example of where it fails. The problem is in how a program communicates (or fails to communicate) to the user what it will do based on some input.
The design principle of least astonishment simply means you should aim for designing your software in a way that what the user expects should happen when performing a certain operation, should also happen. If something else happens, that’s bad design.
-
Education
-
People turn to public libraries for answers, and a lot of times libraries are superb at providing them. But when it comes to providing answers about open source, libraries have an uneven track record.
What can we do to make this better so that more people can turn to their public library to learn about open source software, hardware, and principles?
Right now, if you walked into my public library and pelted me with questions about open source—like, “What is it?” “How does it work?” “How can I use open source?”—I’d rattle off answers so fast you’d be walking out with a new tool or technology under your belt. Open source is a big world, so of course there are some things I don’t know, but guess what? We have the Internet and books right at our finger tips. Saying that you don’t know the answer is fine, and patrons will respect you for it. The key is helping them find the answer.
-
BSD
-
Today, October 6, 2016, Jim Thompson from the pfSense project has had the great pleasure of announcing the release and immediate availability of the pfSense 2.3.2-p1 maintenance update to the open source BSD-based firewall distro.
-
Last week news came out that the FreeBSD 11.0 release wasn’t going to happen as planned but it needed to be respun due to security issues. The release was supposed to happen on 3 October, but three days later we find out it needed to be re-spun again and is still going through testing.
-
FSF/FSFE/GNU/SFLC
-
So ActivityPub is nearing Candidate Recommendation status. If you want to hear a lot more about that whole process of getting there, and my recent trip to TPAC, and more, I wrote a post on the MediaGoblin blog about it.
Last night my brother Stephen came over and he was talking about how he wished ActivityPub was more of a “transactional” system. I’ve been thinking about this myself. ActivityPub as it is designed is made for the social network of 2014 more or less: trying to reproduce what the silos do, which is mutate a big database for specific objects, but reproduce that in a distributed way. Well, mutating distributed systems is a bit risky. Can we do better, without throwing out the majority of the system? I think it’s possible, with a couple of tweaks.
-
-
We’re still not over how cool it was to see so many from our community join the FSFE Summit in September. It was a good experience and we’re keen to repeat it. One of the highlights was the ending keynote where Julia Reda called out proprietary software as a threat to democracy. Be sure to view the keynote and some of the other talks from the Summit, either on our YouTube channel, or from our download server where you can get the available videos in webm format.
We also celebrated the FSFE’s 15th birthday in C-Base with a ceremony where we honored many of our local heroes from around Europe. C-Base has kindly provided a recording of the ceremony if you’re interested in hearing the story of some of our heroes, all of whom you can find working in one of the FSFE’s teams today.
-
Public Services/Government
-
Open code with Russian services preferred, unless good excuses can be found
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
I firmly believe that in the absence of any intentional organizational strategy a person’s workspace becomes a reflection of their mind. Like bits of knowledge stored in the brain, tools and assets instinctively find themselves organized in a way that feels right to the individual.
If this holds true, it stands to reason that, more often than not, our workspaces are always naturally trending away from being tidy and highly-functional. At this point, the odds are good that I’m just trying to rationalize why my office is an unmitigated disaster most of the time, but since you’ve made it this far, let’s make one more assumption: No two people are exactly alike, therefore no two workspaces are exactly alike.
With this assertion firmly in place, I’d like to share a few things I’ve implemented for creating my workspace that have worked well for my brain. Your workspace will look different, but the practices I chose to follow here can be used for anyone looking to match their setup to their brain.
-
Programming/Development
-
RPM of PHPUnit version 5.6 are available in remi repository for Fedorra ≥ 22 and for Enterprise Linux (CentOS, RHEL…).
-
For over a year, Apple’s software has been the subject of more derision than might be expected for a company of its size.
Developer Marco Arment took Apple to task early last year, arguing that OS X (recently rebranded macOS) is full of embarrassing bugs and that the company is trying to do too much on unrealistic deadlines.
Arment subsequently disavowed his post because of the widespread media attention it received. But there was blood in the water and the feeding frenzy has continued at Apple’s expense, at least in part because controversy, manufactured or not, drives online traffic.
-
Science
-
The bumblebee brain is puny, at least compared with the massive and fatty organ locked in your skull. At about 0.0002 percent the volume of yours, bee brains are close in size to the seeds stuck on a hamburger bun. Thinking about insect brains in terms of size alone, however, is a trap. The intelligence of sesame-brained bugs should not be underestimated.
A study reported in the journal PLOS Biology on Tuesday, for instance, takes bee smarts in a surprising direction: Scientists from the Queen Mary University of London suggest that the “insects possess the essential cognitive elements for cultural transmission,” as they wrote in their new paper. It is possible to teach a single bee a new trick, in other words, and a different bee can learn that behavior from her peer.
-
Digital publishers may be pouring time and energy into cranking up their video operations, but for a lot of their potential viewers, text is still the way to go.
New data from Pew Research finds that, when it comes to the news, younger adults still prefer words over moving images. While 46 percent of Americans overall say they prefer to watch the news over reading it, that number is far lower for Americans between the ages of 18 and 29 — only 38 percent of that group named video as their preferred news consumption format. In contrast, 42 percent said that they actually prefer text (which they prefer to read online, of course). Just 19 percent of young adults named listening as their preference. (“Smelling the news” was not an option.)
-
Hardware
-
In the early 2000s, Fujitsu was one of the top 5 PC makers globally. Today, it’s a loss-making enterprise that’s seen its market eroded by smartphones and tablets. The margins have squeezed, and IT conglomerate Fujitsu has been working to offload its non-core businesses and improve profitability. The company spun off its PC division as a separate business in February, a move that’s typically a precursor to a sale or other major restructuring option.
-
Health/Nutrition
-
Hurricane Matthew is whipping away at Florida’s shores this week—threatening lives and homes and parties.
If you know any Floridians, you know that no one is really freaking out yet. We are masters of disaster in the worst kind of way, having endured hurricanes, tornados, weird crimes, Rick Scott, and a growing Zika virus problem in the past year alone. That’s why business owners in Miami this week were prepping for Hurricane Matthew with a kind of calm, cooperative indifference.
-
Voters in four states appear likely to approve ballot measures that would legalize marijuana for recreational purposes, according to recent surveys, while voters are split on the question in a fifth state.
The polls, taken over the last few weeks, demonstrate a seismic shift in the politics of pot. Even a decade ago, voters rewarded politicians who promised to redouble the war on drugs. After November’s elections, nearly a quarter of Americans could live in states where marijuana consumption is legal.
But proponents and opponents alike say that polls taken before Election Day often overstate support for legal marijuana measures.
“If the pro-legalization side is not at 55 percent at this point, it will likely lose,” said Sean Noble, an Arizona-based Republican strategist working against that state’s legalization measure, Proposition 205. “We know that polling on legalization generally overperforms actual results.”
-
Plans to impose a total ban on abortion have sparked a massive uncontrolled explosion of anger in Poland. On Monday 3 October a strike of Polish women was called, inspired by the example of Icelandic women, who held a nationwide strike in 1975. In Warsaw, over 50,000 demonstrated in the pouring rain, in Wroclaw 30,000 and Krakow 25,000. Tens of thousands more demonstrated all across the country. In Poznan, there were clashes with the police, while in Kielce demonstrators demolished a controversial homphobic exhibition. Even the police’s conservative estimates talk about 98,000 people demonstrating in over 143 separate protests across the country. Meanwhile, the left party Razem estimated that over 140,000 people had protested on the streets throughout the country. These are easily the biggest ever protests in defence of abortion rights in Poland, far exceeding the protests in 1993, when the current ban on abortion was introduced.
The first wave of the movement started in spring with the anouncement that a right-wing pressure group had collected over 100,000 signatures (finally they collected 400,000) required to submit a draft law to the Polish parliament which would impose a total ban on abortion and punish women with up to three years in prison. The barbarity of the proposals is illustrated by the fact that all miscarriages would be treated as suspected abortions and would be subject to criminal investigation.
However, already Poland has one of the most restrictive anti-abortion laws in Europe, allowing abortion only in the case of rape, a threat to the health or life of the woman, or deformation of the foetus. In practice, even when these conditions are fulfilled abortion is often prevented by doctors who exploit the so-called “conscience clause” and impose their own religious beliefs on patients by refusing vital treatment.
-
Security
-
-
-
-
If your gpg key is too valuable for you to feel comfortable with backing it up to the cloud using keysafe, here’s an alternative that might appeal more.
Keysafe can now back up some shares of the key to local media, and other shares to the cloud. You can arrange things so that the key can’t be restored without access to some of the local media and some of the cloud servers, as well as your password.
For example, I have 3 USB sticks, and there are 3 keysafe servers. So let’s make 6 shares total of my gpg secret key and require any 4 of them to restore it.
-
CHANGING PASSWORDS is just too much for some people, according to research, and causes them to do stupid things.
This is called ‘security fatigue’, apparently, and comes straight from the National Institute of Standards and Technology (NIST) and a collection of clipboards and pens.
“After updating your password for the umpteenth time, have you resorted to using one you know you’ll remember because you’ve used it before? Have you ever given up on an online purchase because you just didn’t feel like creating a new account?” asked NIST.
“If you have done any of those things, it might be the result of ‘security fatigue’. It exposes online users to risk and costs businesses money in lost customers.”
-
Recent research from IDC shows a clear picture: IT organizations are increasingly unhappy about BYOD and now want to curtail or end the practice.
Their stated concern: The costs are too high and the savings too low. But those concerns are misguided and likely masking a secret agenda to regain control over mobile devices, not to save money. Face it: BYOD was never popular with IT.
-
Defence/Aggression
-
Like those from a battering ram, the hits just keep coming from the recently elected president of the Philippines, Rodrigo Duterte.
Saying this week that President Obama could “go to hell,” Duterte has threatened to jettison decades of close security cooperation with the United States, suggesting Manila would turn to China or Russia for support.
The latest anti-U.S. vitriol came as U.S. Marines and sailors practiced amphibious landings and other exercises with Philippine troops at coastal sites close to the strategic shipping lanes and disputed islands in the South China Sea, a regional hot spot.
The joint exercises began Tuesday and are scheduled to run until Oct. 12. Last week, Duterte said this would be the final round of joint exercises with the U.S. military.
-
Environment/Energy/Wildlife/Nature
-
The report warns that future generations may be forced to use “negative emissions” measures to forcibly extract CO2 from the atmosphere as temperatures keep rising. (Photo: Joe Brusky/flickr/cc)
Fossil fuels must be taxed out of existence to ensure that future generations are not saddled with a world of rising seas and extreme weather—and all the costs that come with them—according to a new research paper by renowned climate scientist and Columbia University professor James Hansen.
-
On October 5, the United Nations proudly announced that enough countries had agreed to the Paris Agreement for it to go into effect, 30 days from now. That’s great. But if you are a bit confused about what exactly this news means, fear not. I’m here to break it all down.
-
Vast swathes of Southwestern United States — a region already grappling with parched conditions — may now have to brace for another threat — decadeslong “megadroughts.”
According to a new study published Wednesday in the journal Science Advances, there is roughly a 70 to 90 percent chance that the Southwest would experience a megadrought — an extreme dry spell lasting 35 years or more — before the end of the century. And, if precipitation is below normal, it’s 99 percent certain that such an event will occur.
“Megadroughts are rare events, occurring only once or twice each millennium. In earlier work, we showed that climate change boosts the chances of a megadrought, but in this paper we investigated how cutting fossil fuel emissions reduces this risk,” lead author Toby Ault, a professor of Earth and atmospheric sciences at Cornell University, said in a statement. “The increase in risk is not due to any particular change in the dynamic circulation of the atmosphere. It’s because the projected increase in atmospheric demand for moisture from the land surface will shift the soil moisture balance.”
The present-day Earth is 1 degree Celsius hotter than it was 150 years ago. The Paris climate agreement, which is to come into force next month, aims to restrict this rise to below 2 degrees Celsius — a target that many experts now believe is almost certain to be breached.
-
Hurricane Matthew is already feared to have caused seven deaths after it hit Haiti and the Dominican Republic on Tuesday, bringing 145mph winds, pounding rain and storm surges to coastal communities.
The category 4 storm, the strongest hurricane to hit Haiti in 50 years, is expected to surge northwards towards Florida’s east coast and up the south-eastern US coast by the weekend. It follows September’s Hurricane Hermine, which was the first hurricane to hit Florida in nearly 11 years.
-
States of emergency have been declared in Florida, Georgia and the Carolinas as Hurricane Matthew barrels toward the Southeast coastline. More than 2 million people have been urged to evacuate their homes. The record-breaking storm has already killed at least 26 people in Haiti and four in the Dominican Republic. The storm is soon expected to hit the Bahamas and then strengthen as it moves toward Florida. Meteorologists are predicting Matthew could be the strongest hurricane to hit the United States since Wilma in 2005. Many scientists are saying climate change has intensified Hurricane Matthew because warmer ocean waters help create stronger hurricanes. Matthew is already the longest-lived Category 4 or 5 hurricane in the Eastern Caribbean on record. To talk more about Hurricane Matthew and climate change, we speak to Guardian journalist Oliver Milman and Michael Mann, a distinguished professor of atmospheric science at Penn State University. His latest book, co-authored with political cartoonist Tom Toles, is titled “The Madhouse Effect: How Climate Change Denial Is Threatening Our Planet, Destroying Our Politics, and Driving Us Crazy.” Mann is also author of “The Hockey Stick and the Climate Wars: Dispatches from the Front Lines.”
-
Hurricane Matthew’s eyewall continues to brush parts of Florida’s northeast coast with high winds and storm surge flooding, and will spread those impacts, in addition to potentially serious rainfall flooding into Georgia, South Carolina, and southern North Carolina through at least Saturday night.
-
Finance
-
The UK will trigger Article 50 of the Treaty of Lisbon, triggering the formal two-year Brexit negotiation process, by the end of March 2017, the prime minister has announced.
The government also intends to publish a ‘Great Repeal Bill’ which, once given effect, will remove the 1972 European Communities Act from the UK statute book and enshrine any EU laws in effect on the date of the UK’s exit from the EU into UK law, Theresa May told the Conservative Party annual conference.
May said that the process would give UK businesses and workers “maximum certainty as we leave” the EU, while retaining the government’s right to “amend, repeal and improve any law it chooses” at a later date. EU law expert Guy Lougher of Pinsent Masons, the law firm behind Out-Law.com, said that the comments provided “a helpful indication of the government’s intentions and priorities”.
“Although the prime minister has indicated her opposition to the shorthand labels of ‘soft Brexit’ and ‘hard Brexit’, it appears that the government’s negotiation intentions and the likely outcome are closer to the latter than the former,” he said.
-
Trump’s business “genius” relies on stiffing creditors and contractors, laying off workers and driving the equity of investors down while he just walks away.
-
Privatization is bad news for federal, state and local government workers, and the communities where they live. That’s according to a new report released Wednesday by In the Public Interest, a research group focused on the effects of privatization.
The study, “How Privatization Increases Inequality,” explores the role privatization plays in the American economy—compiling data on the estimated $1.5 trillion of state and local contracts doled out each year.
“A lot of decisions are small,” says Donald Cohen, executive director of In the Public Interest, but “if you add all that up, it’s very significant.”
-
AstroTurf/Lobbying/Politics
-
But Facebook’s most powerful political tool may be one that’s hiding in plain sight. Consider the “I Voted” button.
The button, dubbed by Facebook a “voter megaphone”, allows users to report whether they have voted and shows which of their friends have also voted.
-
Video of Mike Pence denying Trump said any of the horrible, racist, stupid, uninformed and generally embarrassing things he spouts all day long, matched with Trump saying the stuff.
-
She’s a dark horse in the presidential race, but green party nominee, Dr. Jill Stein could have a big impact on the outcome.
Stein is campaigning in L.A. for a few days – trying to convince voters that she is the better choice. Green Party presidential candidate Jill Stein will make a campaign stop Thursday at Cal State Northridge.
Stein is polling around the 2% mark in most of the national polls, but that is enough to sway the election to the winner.
-
After the first presidential debate on September 26, CNN hosted a focus group at the University of Richmond. According to Justin Smith, one of the 28 people included in the panels, CNN censored those who said they would be voting for a third party, declaring them “undecided.”.
“Out of 28 panel members, five said they were decided on Clinton, two said they were decided on Trump, and 12 said they were going to vote 3rd party. But once they saw the response, they reshot the segment and replaced ‘3rd party’ with ‘still undecided.’ You’ll noticed on the live feed, I refused to raise my hand,” wrote Smith in a Facebook post. Smith is supporting Evan McMullin, former CIA operations officer and former chief policy director for the House Republican Conference in the U.S. House of Representatives, for president. “They then said they were going to reshoot it, except this time they changed ‘3rd party’ to ‘undecided.’ Some of us asked about the third party option, and they ignored us. They then said they were going to shoot it again, and still asked for ‘undecided’ voters and left out ‘3rd party.’ A lot of the members voted ‘undecided’ because it was the only option other than Trump or Clinton.” Smith posted the CNN video of the focus group and wrote that in the video he refused to raise his hand and vote “undecided” as a protest.
-
WikiLeaks series on deals involving Hillary Clinton campaign Chairman John Podesta. Mr Podesta is a long-term associate of the Clintons and was President Bill Clinton’s Chief of Staff from 1998 until 2001. Mr Podesta also owns the Podesta Group with his brother Tony, a major lobbying firm and is the Chair of the Center for American Progress (CAP), a Washington DC-based think tank.
-
Donald Trump bragged in vulgar terms about kissing, groping and trying to have sex with women during a 2005 conversation caught on a hot microphone, saying that “when you’re a star, they let you do it,” according to a video obtained by The Washington Post.
The video captures Trump talking with Billy Bush, then of “Access Hollywood,” on a bus with the show’s name written across the side. They were arriving on the set of “Days of Our Lives” to tape a segment about Trump’s cameo on the soap opera.
-
Censorship/Free Speech
-
Back in 2008, then Senator Joe Lieberman went on a ridiculous pro-censorship campaign, demanding that YouTube take down any “terrorist” videos. For reasons I still don’t understand, YouTube complied. As a result, watchdogs documenting Syrian atrocities had them censored from YouTube, because YouTube determined them to be in “violation” of its guidelines in publishing “shocking and offensive videos.”
That was a few years ago, and it seems like the problem has only gotten worse — as have the ridiculous calls for YouTube and other platforms to be the giant censor in the digital sky. The latest victim? Would you believe it’s the European Parliament itself? Marietje Schaake, a really wonderful Member of the European Parliament (and a Techdirt reader), tweeted that the video she had posted of a European Parliament debate on “anti-torture” was taken down for “violating community guidelines.” Really.
-
Donald Trump’s outright contempt for journalists and press freedom is well known—but in the past month he has outdone himself.
In the span of a long weekend in mid-September, Trump threatened to sue The New York Times, his staff had a Vice reporter arrested outside a campaign event, and he blamed the New York terrorist bombings on “freedom of the press.”
This weekend, Trump struck again. After the Times’ huge scoop detailing how he took an almost billion-dollar loss on his 1995 taxes, Trump’s lawyer threatened “prompt initiation of appropriate legal action” against the Times once more. By my count, it is at least the 11th time Trump has threatened to sue a news organization or journalist during his campaign for president.
I had intended to quantify how many journalists or news commentators Trump has threatened to sue over his lifetime, but that quickly turned into a fool’s errand. A simple Google search of “Trump threatens to sue” will return an overwhelming number of stories. In the past decade alone, he’s sued a former Times journalist who wrote a book about him that he later admitted he didn’t even read; he’s threatened to sue former View host Rosie O’Donnell for allegations that have been shown over and over again during this campaign to be correct; he’s sued HBO’s Bill Maher over a joke bet that involved proving he was not, in fact, born an orangutan.
-
Donald Trump keeps insisting that he’s a strong supporter of the 2nd Amendment of the Bill of Rights, but he appears to have skipped right past the 1st Amendment. We’ve discussed his stated plans to “open up” libel laws and his regular threats to sue newspapers for reporting on him in ways he dislikes. Trevor Timm, of the Freedom of the Press Foundation, recently tried to count how many times Trump had threatened to sue the media since his campaign began (ignoring all the threats from before the campaign).
-
THE PIRATE BAY is not a place you want to go, at least not according to the Chrome and Firefox browsers which have taken to warning people that the pages are perhaps poisoned and definitely deceptive.
A post on TorrentFreak said that users are batting their heads against a blocking wall when they try to access magnets and that kind of stuff.
We took to the water today in search of The Pirate Bay on Firefox. Virgin Media has put a cage around the site, but you can still get to it. Once there we were able to get to the main page, but no further.
A search, with a capital R for research, took us to a page of links that took us to another page, but not one that we expect The Pirate Bay user base will enjoy.
-
Chrome and Firefox are again blocking direct access to The Pirate Bay’s download pages. According to Google’s safe browsing program, ThePirateBay.org is a “deceptive site” that may steal user information. The TPB crew has been alerted to the issue and hope it will be resolved soon.
-
Privacy/Surveillance
-
Not long after Edward Snowden’s revelations of massive government surveillance of the American public, Yahoo was one of the eight tech giants that called for strong reforms that would protect their customers.
And back in 2007, Yahoo went to court to challenge a government surveillance program in order to protect its users’ privacy.
Well, that was then.
Now, in a move that has outraged privacy advocates, Yahoo reportedly has helped take government intrusion to a new level. Without apparent protest, according to news reports, it built a mechanism that allowed the National Security Agency and the FBI to scan all of its users’ incoming emails for specific characters or words.
-
Verizon is pushing for a $1 billion discount off its pending $4.8 billion agreement to buy Yahoo, several sources told The Post exclusively.
The request comes on the heels of the web giant getting bludgeoned by bad news in the past few days.
Yahoo revealed two weeks ago that it had been hacked in 2014 and that usernames and passwords for 500 million accounts were swiped.
Then, earlier this week, it was learned that Yahoo had been ordered by a secret Foreign Intelligence Surveillance Court to scan emails for terrorist signatures.
“In the last day we’ve heard that [AOL boss] Tim [Armstong] is getting cold feet. He’s pretty upset about the lack of disclosure and he’s saying, ‘Can we get out of this or can we reduce the price?’” said a source familiar with Verizon’s thinking.
That might just be tough talk to get Yahoo to roll back the price. Verizon had been planning to couple Yahoo with its AOL unit to give it enough scale to be a third force to compete with Google and Facebook for digital ad dollars.
The discount is being pushed because it feels Yahoo’s value has been diminished, sources said.
-
A new case might lead the FBI and Apple into another fight over security and privacy on smartphones, following a confirmation yesterday by FBI special agent Rich Thorton that the FBI has the iPhone of Dahir Adan in its possession (via Wired).
Adan was the culprit behind the stabbing of 10 people in a Minnesota mall in mid-September, and was eventually shot and killed by police. After the event, terrorist organization ISIS claimed credit for the attack on social media, but “no evidence has emerged to suggest ISIS had a hand in planning or executing the attack.”
During a press conference in St. Cloud, Minnesota yesterday, Thorton confirmed that the FBI has Adan’s iPhone and that it is locked with a passcode. According to the special agent, the organization is “still trying to figure out how to gain access to the phone’s contents.” The issue currently is that the model and version of iOS running on the iPhone is known only to the FBI. Following the launch of iOS 8 in 2014, any iOS device running the software is encrypted to an extent that no malicious outsider — or even Apple itself — can get into the iPhone or iPad.
-
Contrary to a denial by Yahoo and a report by the New York Times, the company’s scanning program, revealed earlier this week by Reuters, provided the government with a custom-built back door into the company’s mail service — and it was so sloppily installed that it posed a privacy hazard for hundreds of millions of users, according to a former Yahoo employee with knowledge of the company’s security practices.
Despite this week’s differing media accounts, this much isn’t disputed: In 2015, Yahoo provided the U.S. government with the means to scan every single email that landed in every single Yahoo Mail inbox. The scanning was kept an absolute secret — and as this ex-Yahoo source describes, that meant keeping it a secret from security personnel who came to believe it endangered Yahoo’s hundreds of millions of unwitting customers.
The employee, who worked at Yahoo before, during, and after the installation of the email-scanning program, requested anonymity because of a nondisclosure agreement formed when the individual quit several months after the program was discovered internally last summer. The source declined to share certain specific names for fear of violating that same NDA or the NDA of others, but The Intercept has confirmed details of the source’s employment at Yahoo, which would have put the then-employee in a position to know this information.
-
Police records obtained by the Daily Dot reveal in unprecedented detail how the Obama administration enables law enforcement to suppress information about controversial phone-surveillance technology used by police throughout the United States.
The documents, which link the purchase of so-called Stingray devices to various North Carolina state and local police agencies, include a fill-in-the-blank warrant drafted by the U.S. Justice Department (DOJ) and intended for use by state and local police that extends the veil of secrecy over law enforcement’s Stingray use.
The records, originally acquired by Working Narratives under North Carolina public records law and shared with Daily Dot reporters, also offer new specifics about the capabilities of Stingrays bought by police in North Carolina from Harris Corporation, a leading U.S. manufacturer of cell-site simulators, and the company behind the original “StingRay” procured by the Pentagon and various intelligence agencies more than two decades ago. The North Carolina agencies referenced by the documents include the New Hanover County Sheriff’s Office; the Wilmington Police Department; and the North Carolina State Bureau of Investigation, an agency that reports directly to Gov. Patrick L McCrory (R).
-
In the six weeks since federal agents raided a suburban Maryland home and arrested Harold T. Martin III on suspicion of stealing classified information from the National Security Agency, another organization has quietly prepared to face the fallout: Booz Allen Hamilton, Mr. Martin’s employer.
Booz Allen, a consulting firm that earns billions of dollars by working for American intelligence agencies, has been called the world’s most profitable spy organization. News this week of Mr. Martin’s arrest in August could renew scrutiny of the firm’s operations and, more broadly, the lucrative contracting business that American intelligence now relies on to run its vast, global surveillance operations.
Mr. Martin’s arrest is the second time in three years that a Booz Allen contractor has been accused of stealing potentially damaging material from the N.S.A. The company also employed Edward J. Snowden, who spirited out a cache of documents that, in 2013, exposed the extent of American surveillance programs in the United States and around the world.
Booz Allen is one of a handful of defense and intelligence contractors that blur the line between the government’s intelligence work and private enterprise.
-
BT customers are unable to delete BT Yahoo email services – despite an exodus of users seeking to leave the security-challenged webmail biz.
Since allegations arose that Yahoo built an app to enable it to scan all of its users’ emails at the request of US intelligence, many users have sought to delete their email accounts.
That was in addition to Yahoo!’s confession last month that hackers had stolen the credentials for at least 500 million of its customer email accounts.
-
Imagining a Cashless World [Ed: Lack of anonymity in purchasing/payments now “driven in part by an epidemic of armed robberies in smaller shops,” says iophk]
A fantastic heist (we like our crimes as smart and magical as dreams) took place some years back, when a stolen helicopter landed on the roof of a cash depot in Stockholm and three masked men smashed a skylight to climb inside. It was September 23, 2009. The depot was freshly stocked in expectation of a coming Swedish payday. Armed with a Kalashnikov, the invaders held employees at bay while their accomplices outside positioned road spikes to keep cop cars from swarming the building. Fake bombs had been set among the police helicopters to delay an aerial chase. The thieves loaded bag after bag of bills into their aircraft, then departed. Seven men were later caught and sentenced, but nearly all of the stolen cash—reportedly some $6.5 million—still has not been found.
The robbery is known as the Västberga heist, and, like many capers, it became a source of public fascination. (It is the subject of Evan Ratliff’s e-book “Lifted.”) But it also earned astringent notice from some economic theorists, who saw in it a parable about the risks of paper money. Cash is the squirmy ferret of societal wealth—tricky to secure physically and, once liberated in the wild, almost impossible to get back—and money, as technology, has changed a lot in half a century. A day’s errands once called for bulging pockets. Now it’s possible to shop for groceries, pay rent, buy lunch, summon a taxi, and repay your sister for a movie without handling a checkbook, let alone fumbling with bills and coins. Most people think of card and electronic payments as conveniences, stand-ins for exchanging cold, hard cash. Yet a growing group of theorists, led in the United States by Kenneth S. Rogoff, a former chief economist at the International Monetary Fund, are embracing the idea that physical currency should be the exception rather than the rule.
-
Twitter shares plunged 20.1% Thursday after published reports said would-be suitors including Google would not bid for the struggling social media company.
Technology news outlet Recode said Google and Disney would not pursue Twitter and Apple was unlikely to buy it either, deflating the stock that had soared on takeover speculation.
Marc Benioff, CEO of Salesforce.com, considered one of the more likely suitors for Twitter, also seemed to downplay his interest during an analyst meeting at his company’s annual Dreamforce event in San Francisco.
“We look at everything and we don’t buy most things, and we haven’t agreed to buy that company,” he said Wednesday, emphasizing that Salesforce.com has a “disciplined M&A process.”
-
A Yahoo operation in 2015 to scan the incoming email of its customers for specific information identified by the U.S. government was authorized under a foreign intelligence law, U.S. government officials familiar with the matter said.
Reuters on Tuesday reported that the Yahoo program was in response to a classified U.S. government request to scan emails belonging to hundreds of millions of Yahoo users.
The revelation rekindled a long-running debate in the United States over the proper balance between digital privacy and national security.
The Department of Justice obtained the order from the Foreign Intelligence Surveillance Court, said the sources, who requested anonymity to speak freely.
-
Civil Rights/Policing
-
Tim Kaine repeatedly defended Hillary Clinton’s use of a private email server during Tuesday night’s vice-presidential debate. “The FBI did an investigation,” he said at one point, “and they concluded that there was no reasonable prosecutor who would take it further.” But such a statement is credible only if it follows a real criminal investigation—that is, the sort of investigation that the FBI and the Justice Department conduct when they actually care about a case and want convictions.
-
Google has been hit with a class-action lawsuit accusing the ad giant of discriminating against older employees.
The Northern California District Court has certified [PDF] the case brought against the Chocolate Factory, allowing aggrieved applicants aged 40 and older to join together in filing a single suit.
By certifying the case, the court allows the plaintiffs to take on Google’s legal might as a combined force, rather than individually. This, in turn, increases the likelihood of a favorable settlement from Cali-based Google.
The complaint, originally filed in April of 2015, claims that Google discriminates against job candidates over the age of 40 when screening them. The suit accuses Google of violating the US Age Discrimination in Employment Act.
-
If the Drug War is US law enforcement’s wildly-swinging fist, the DEA is its middle finger. Once the pointless brutality stops, the finger is extended to everyone — especially taxpayers.
Even the agency’s name inadvertently belies its twisted motivations: “Drug Enforcement Agency.” Without further information, the name, on its own, seems to suggest a shoring up of the drug trade, rather than an adversarial force.
The DEA has a lot of skin in the drug game. Without the steady flow of drugs, it ceases to exist. It operates with a great deal of autonomy and is often excused its worst excesses because most people agree (without much thought) that drugs are bad.
The DEA controls a vast network of confidential informants. Actually, to state it more accurately, the DEA oversees… Never mind. The DEA pays a great deal of money to confidential informants. Beyond handing out cash, the DEA apparently does little else to keep its informants in line.
A just-released Inspector General’s report [PDF] on the DEA’s use of confidential informants finds the agency has no problem paying out vast sums of money to lying informants and that it maintains a small army of otherwise-employed citizens who moonlight as cash/drug-sniffing humans for the nation’s top drug warriors.
This year’s report builds on the lowlights of last year’s examination of the DEA’s informant program, in which the OIG basically stated the entire program runs without sufficient oversight. Nothing has changed in the interim. This report includes even more details of excess, abuse, and stupidity.
-
Hundreds of people in Mumbai, India have been detained in relation to a massive telephone scam where fake callers “from the IRS” targeted Americans. In said calls, scammers tried to convince recipients that they were from the IRS in order to con victims into forking over thousands of dollars payable via prepaid credit cards.
According to The Guardian, 200 Indian police officers raided nine locations across one of India’s largest cities.
-
Indonesian police have arrested a man accused of hacking into a public billboard in Jakarta and streaming a pornographic film.
The 24-year-old IT analyst has admitted the crime, said police, for which he could face up to six years in jail.
Motorists were left in shock last week when footage from a Japanese porn film was displayed on an electronic screen in south Jakarta.
The video ran for five minutes on Friday before power was eventually cut.
However the clip had already been captured on many mobile phones and soon spread across social media.
The man, who was arrested in his office, allegedly carried out the prank after seeing login details displayed on the billboard.
-
A shopper at Westfield Valley Fair mall claims in a civil lawsuit that a security guard pulled a gun on him after he hit a traffic cone while trying to leave the mall in December.
In the Santa Clara County Superior Court filing submitted last week, San Jose resident Nicholas Buchanan, an Apple engineer, is seeking unspecified damages against the mall, a security contractor, and two security guards for a Dec. 5, 2015 encounter. The lawsuit also takes issue with how the guard who drew a pistol on Buchanan was not licensed to carry a firearm at the time.
-
RELIGIOUS authorities in the Malaysian state of Selangor has launched a mobile application that allows members of the public to report Syariah-related crimes, adding to concerns of growing Islamic fundamentalism in the Muslim-majority country.
Selangor’s Islamic Religious Department (Jais) director Haris Kasim told The Star that the app allows the public to become the eyes and ears of enforcers, making it easier for them to report offences that breach the Syariah code, such as pre-marital or extramarital sex, or alcohol consumption, which are forbidden to Muslims.
“The application, which was launched Tuesday, is simple and easy to use. Once installed on a smartphone, people can send over information and make reports to Jais very easily,” he was quoted as saying.
-
A top chess player is boycotting the World Chess Championship in Iran because women will be legally required to wear the hijab while competing.
Nazi Paikidze-Barnes, a Geogian-American chess player, is petitioning the World Chess Federation (FIDE) in a bid to change the host country of the women’s world championship competition from Iran.
“I think it’s unacceptable to host a women’s World Championship in a place where women do not have basic fundamental rights and are treated as second-class citizens,” the 22-year-old told the BBC.
-
After being arrested, Khan told a police officer: “Never get an arranged marriage bro.”
The butcher was handed a life sentence after pleading guilty to murdering Nasreen.
Manchester Crown Court heard Khan told his wife “it’s not halal for you to work with men”.
-
A 16-year-old fatally shot by a Los Angeles police officer in South Los Angeles called 911 himself before the shooting and left his family a “farewell note,” leading investigators to believe he had a “desire to end his own life,” LAPD chief Charlie Beck said Thursday.
Coroner’s officials identified the boy Thursday as Daniel Enrique Perez, who police say was shot after pointing a realistic-looking replica gun at officers.
Beck said detectives identified Perez through a cellphone he was carrying, which was used to call 911 about 20 minutes before the deadly encounter. The caller reported a man with a gun matching Perez’s description, Beck said.
-
The burqa veil is to be banned in schools and universities across Norway following similar measures in other European countries, according to the Norwegian education minister.
The country’s right-wing government confirmed it was considering “national regulations prohibiting the full-face veil in schools and universities”, a move supported by the opposition Labour Party.
Education minister Torbjorn Roe Isaksen confirmed the ban would only apply to the full-face veil and not to other Islamic headscarves including the hijab, chador and niqab.
-
Two former high-ranking CIA officials will be compelled to answer questions under oath about the agency’s brutal interrogations of terrorism suspects, a federal judge ruled Tuesday as part of a lawsuit brought against former CIA contractors by the American Civil Liberties Union.
The ruling would require Jose Rodriguez, who was the head of the CIA’s Counterterrorism Center after the Sept. 11, 2001, attacks on the United States, and John Rizzo, the agency’s former acting general counsel, to submit to depositions about a program that used methods widely condemned as torture.
“This ruling is a critical step towards accountability, and it charts a way forward for torture victims to get their day in court,” ACLU attorney Dror Ladin said in a statement released by the organization after the ruling in federal court in Spokane, Wash.
-
On a windy afternoon in February 1959, 14-year-old Craig Wade scooped up what seemed to be a crumpled rag that was blowing, tumbleweed style, across a railroad track in his hometown, Pittsfield, Massachusetts. He later told a local newspaper that he simply “likes to save things.”
-
Internet Policy/Net Neutrality
-
Facebook is in talks with the government and wireless carriers to bring its “Free Basics” internet service to the U.S., reports The Washington Post.
If the plan works, Facebook “would target low-income and rural Americans who cannot afford reliable, high-speed Internet at home or on smartphones,” the report notes.
Facebook didn’t immediately respond to a request for comment.
Free Basics isn’t a full-fledged internet provider, but rather an agreement with carriers that lets people use Facebook and other sites without it counting towards their data plan.
Facebook has run into trouble with Free Basics abroad. The program, which currently operates in 49 countries, was shut down earlier this year in India due to net neutrality concerns.
-
Intellectual Monopolies
-
Copyrights
-
As has by now been extensively reported, on 14th September the European Commission released its new copyright reform package. Prominent within this is its proposal for a new Directive on Copyright in the Digital Single Market.
The proposal contains an array of controversial offerings, but from the perspective of this intermediary liability blogger, the most interesting provision is the proposed Article 13 on ‘Certain uses of protected content by online services’. This is highly problematic in a number of different ways.
-
BitTorrent has fired its two co-CEOs Robert Delamar and Jeremy Johnson and laid of an unknown number of staffers, Variety has learned from multiple sources. BitTorrent CFO Dipak Joshi has stepped in as interim CEO.
The company is also closing its Los Angeles-based production studio and shuttering its BitTorrent Now video streaming efforts. This comes just months after BitTorrent announced a renewed focus on media under the leadership of Delamar and Johnson.
BitTorrent founder Bram Cohen laid out the changes in an email to staff earlier this week, according to a source, but layoffs apparently began as early as two weeks ago. In addition to being ousted as CEOs, Delamar and Johnson were also removed from the company’s board of directors.
The company had officially announced the appointment of Delamar and Johnson as new co-CEOs in April. At the time, the duo laid out a renewed focus on media production and distribution, which involved the opening of a new Los Angeles-based production studio.
These efforts culminated in BitTorrent Now, an ad-supported music and video streaming platform that launched in June. BitTorrent Now built on the company’s efforts to strike media distribution deals with independent artists, but didn’t actually use BitTorrent’s P2P technology for streaming.
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents, Rumour at 4:44 am by Dr. Roy Schestowitz
Being above the law, even at The Hague, helps the autocracy of Battistelli and his praetorian guard

Summary: The unaccountable, unregulated Patent Office continues its union-busting activities and is expected — some believe — to decapitate even SUEPO The Hague (representing perhaps a thousand members of staff)
THE EPO‘s management continues to behave as though it’s above the law (any country’s law and even international law). The President, for instance, is allowed to break even his own rules. That’s classic autocracy, contrary to the principles of the Rule of Law.
“The problem is, the Administrative Council has become a lapdog, not a watchdog, and we’re rather pessimistic about it. It’s now complicit.”Recently, judging by the Dutch media, EPO management found an ‘ally’ in the Advocate General, Mr. Vlas, who is similar to an Attorney General (AG) in other countries. This may depend on who’s translating and how. The management of the EPO must be happy as it means that the high court’s decisions in January will quite likely be against SUEPO, not on grounds of legitimacy of their complaint but based on technical grounds or legitimacy of enforcement, i.e. the EPO being above the law and exempt from Dutch law (even though it resides on Dutch soil).
Someone has passed us some thoughts on the matter of this legal case in the Netherlands, stating:
The Attorney General of the Netherlands has issued his opinion on the immunity of the EPO in the context of the EPO’s breaches of fundamental rights. The AG did not in the least contest the findings of the violations, and went as far as stating that “honouring the claim to immunity of jurisdiction from the national judge does not in the least mean that violations of material rights are permitted”. However, in the specific case of SUEPO’s claims, he adopted the position that as long as individual EPO employees can have recourse to the ATILO, the route to the Dutch judge is barred. SUEPO does not understand this point; SUEPO cannot see how the ATILO can enforce a union’s right to collective bargain through individual complaints about violations of individual rights. SUEPO’s lawyers are studying the matter and will consider submitting a supplementary brief. The Court will hand down its decision (which may or may not follow the opinion of the AG) on 20 January 2017.
The above suggests that this is far from over. In the mean time, a source told us that witch-hunting in The Hague continues — something which we already knew about and wrote about. “The Attorney General’s opinion comes at an unusual juncture,” we learned, “and (in spite of its conservative stance) may well push the EPO and its Administrative Council to do something about the respect of fundamental rights.”
The problem is, the Administrative Council has become a lapdog, not a watchdog, and we’re rather pessimistic about it. It’s now complicit.
“This in its own right should be cause for massive demonstrations at The Hague next week.”We learned from our source that things have escalated even further. One “should remember,” to quote, “that the council has adopted resolution CA/26/16, which the President has completely ignored. Since then, as anyone can read from the minutes of the Board 28, there are “three current investigations/ disciplinary proceedings involving SUEPO members in The Hague”. Clearly, the witch-hunt of SUEPO officials is going on, this time in The Hague. One of the targets is Laurent Prunier (Secretary of SUEPO The Hague, and member of the CSC), who has been suspended since 27.06.2016, and whose disciplinary hearing towards dismissal (and more) has just taken place on 28 and 29 September. No comment can be provided without risking compromising Laurent’s defence.”
Some people have in fact been informed that “his name has been expunged from the internal phone book even before the proceedings are closed.”
They “thus fear for the worst.”
This in its own right should be cause for massive demonstrations at The Hague next week. In Prunier's own words, these are “demonstrably fabricated accusations.”
We saw that before, did we not? █
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day
- Software Patents Continue to Collapse, But IBM, Watchtroll and David Kappos Continue to Deny and Antagonise It
The latest facts and figures about software patents, compared to the spinmeisters' creed which they profit from (because they are in the litigation business)



 Summary: A closer look at the “FJORDBLINK” trademark and what happened to the entity which registered it in Denmark (where the Chairman of the Administrative Council of the European Patent Organisation is still in charge)
Summary: A closer look at the “FJORDBLINK” trademark and what happened to the entity which registered it in Denmark (where the Chairman of the Administrative Council of the European Patent Organisation is still in charge)






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA