09.24.13
Posted in GNU/Linux, IBM, Red Hat at 10:43 am by Dr. Roy Schestowitz

Summary: Why the platform which Richard Stallman created should be evaluated in terms of its adherence to core values, not market value
IBM received a lot of attention a week ago, owing to a promise it had made before. This is significant because Microsoft is bound to suffer the most [1]. Investment is what they call it [2,3] and it’s hardly news [4]. “Innovation” is another word that gets thrown around [5], but not the F word. Yes, Freedom. To IBM, this word is scary; either it means “cheap” or that ‘radical’ thing Richard Stallman talks about. To companies like IBM, it’s still all about money. GNU/Linux pundit SJVN alludes to Red Hat as such [6] now that there are some financial results which, despite early optimism [7,8,9] and beating of expectations [10], Wall Street is not even so excited about [11-14]. But the problem is this: rather than focus on the genesis of GNU/Linux, which was about freedom and users’ control, here we are talking about billions of dollars — sometimes made by selling proprietary software from IBM, installed on very proprietary hardware. If this is progress for GNU/Linux, it’s merely fiscal progress. Our rights online are still perpetually eroding (e.g. the Internet has become a military-grade surveillance platform), perhaps because companies which bear our flag put profit before principles. █
Related/contextual items from the news:
-
Not long ago, Microsoft ruled the computing empire with near-monopolies in PC operating systems, web browsers and productivity applications. The company’s reign, however, was dominated by discord. Competitors complained about Microsoft’s predatory business practices. Users bemoaned the company’s software as a necessary evil.
Fast forward to 2013. Once revered and feared, Microsoft is a shell of its former self. Far from the software and technology leader it used to be, the company now makes repeated missteps in emerging markets such as cloud computing, mobile, search and social.
-
IBM is investing $1 billion in new Linux and open source technologies for IBM’s Power Systems servers.
-
-
The computer giant on Tuesday plans to pledge that it will spend $1 billion over four or five years on Linux and related open-source technologies for use on its Power line of server systems, which is based on the internally developed chip technology of the same name.
-
As many of you know, IBM has a long standing commitment to open source innovation and Linux in particular. We have been part of the Linux Foundation and all its exciting events from day one. Of course, IBM will be part of LinuxCon 2013 – again as a Platinum sponsor. A large team of IBMers is heading to New Orleans next week, where we look forward to connecting with both creators and consumers of the open technology that we come together to celebrate. We have a variety of interesting sessions and fun activities planned for you. Here are some of the highlights:
-
Red Hat’s second quarter was another roaring success no matter by any standard.
-
Wall Street is optimistic about Red Hat , which is slated to report its second quarter results on Monday, September 23, 2013. Analysts project a profit of 22 cents a share, a rise from 20 cents per share a year ago.
-
Red Hat has a popular following among both customers and investors, as it has in many ways helped to disrupt the dominant business model in the industry. Early in its history, many were skeptical that the company could actually profit from open-source software, citing the many companies that locked customers into their proprietary platforms in the hopes of compelling repeat business. Yet years later, Red Hat continues to thrive as demand for flexible solutions is greater than ever. Let’s take an early look at what’s been happening with Red Hat over the past quarter and what we’re likely to see in its report.
-
-
Shares of Linux software company Red Hat fell as much as 9 percent in after-hours trading Monday even though the company reported quarterly revenue and net income that exceeded Wall Street’s expectations.
-
-
-
-
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, GNU/Linux at 10:25 am by Dr. Roy Schestowitz

Wittelsbacher Fountain in Munich, Germany
Summary: Reports on adoption and success stories for GNU/Linux, gathered in recent days or weeks
YEARS ago when this Web site was young there was legitimate concern that Microsoft’s patent assault — waged with Novell’s help — would suppress the free adoption of GNU/Linux. Ever since Microsoft lost its momentum in businesses, then released Windows Vista, announced losses to the public and laid off staff (while first-tier managers fled the company) things have looked somewhat different. Then came Android world domination, which made Linux the de facto platform almost everywhere except desktops and servers. In desktops and servers, however, progress has been made by GNU/Linux and earlier this month we saw some key news from Germany [1,2], China [3], Argentina [4], and the UK [5], to name just four countries. We are going to cover more such examples in days to come, including some government adoptions.
Taking into account Linux/Android and GNU/Linux, the presence of Linux on the Web is rapidly growing [6]. Microsoft has hardly even got majority market share over there. Its prominence is quickly declining. █
Related/contextual items from the news:
-
The southern German city of Munich has come up with a novel solution for its Windows XP-using citizens, whose operating system will be officially unsupported by Microsoft in April next year.
-
Windows XP users in Germany’s third largest city are being offered free upgrades to Ubuntu ahead of termination of Microsoft support for the OS next Spring.
-
China has been in the spotlight lately. Most recently, the country was rumored to be the major catalyst for the “low cost” iPhone 5c. However, this has largely been discredited since the phone was revealed to not be “low cost”, but instead a relatively expensive, premium device. However, China is still a major player in the computer market and manufacturers are chomping at the bit to take advantage of it. Today, Canonical announces that Hewlett Packard is focused on the nation and will be selling Ubuntu-based laptops in its 1,500 retail stores.
-
The news has been full of headlines of happenings at this year’s LinuxCon, but one tiny little headline stands out today as different. Although it hasn’t made it into English speaking press yet, it seems the Argentine government has sponsored the development of a Linux distribution to be used on all state provided education computers.
-
-
The highlights:
Android/Linux 5.67%
GNU/Linux 2.06%
That Other OS 51.26%
If we only consider non-mobile PCs, TOS gets 70.7% of page-views
Permalink
 Send this to a friend
Send this to a friend
09.23.13
Posted in GNU/Linux, KDE at 5:05 am by Dr. Roy Schestowitz

Summary: Qt5 finds its way into the very core of KDE, arguably the best desktop environment in the world (most features-rich)
The K Desktop Environment (KDE) has undergone some major changes in recent years, development-wise. Some say that development stagnated, whereas others say that it’s as good as ever before. The death of Nokia in Microsoft’s hands has certainly not helped the toolkit upon which KDE is based (Qt), but there are signs of progress because the lead KWin developer merged in Qt5 [1,2], with evident development pace accompanying this milestone [3-6].
Amarok, which was seemingly abandoned for some time after a botched bunch of releases, is back in active development with funding from Google [7] and old KDE applications refuse to become deprecated [8] (Krusader and Konqueror are still better than Dolphin in many respects). There are even active surveys [9] regarding the development of KDE and polls which determine the best KDE distro of 2013 [10].
KDE is anything but dead. It’s my desktop environment of choice and after some bad reputation it received in the 4.0-4.1 releases people should definitely give it a go. It’s now hopping on the Qt5 train, later to be followed by the “5″ branch of KDE — the first major leap in several years. █
Related/contextual items from the news:
-
Almost a month since my last blog post. And of course lots of work in KWin in the frameworks-scratch branch since then – about 160 commits. Today I finally reached the next milestone: dogfooding. I dared to replace the KWin of my working session by the new version based on Qt 5 and it’s useable.
-
The next-generation KDE KWin window manager for KDE Frameworks 5 and using the Qt 5.x tool-kit is quickly entering a usable state and can now handle “dogfeeding” by its developers.
-
-
-
-
-
Once upon a time Linux had what I think was the best music player/manager, its name was Amarok and people even brought it up as a way to try convince others to move to Linux, intelligent playlists, auto fetching of cover arts, lyrics, last.fm integration, etc, and it was great. Fast forward a few years (almost a decade to be fair) and now Amarok and all KDE music players seems to be lacking, with KDE 5.0 maybe this is the time to fix it.
-
Find out 10 reasons why you should try Krusader, a twin-pane file manager that might be faster than Dolphin on older computers or just a better match for your computing habits.
-
Björn Balazs has posted the results of a recent user survey in a “study about the requirements for the screen management tool KScreen.” The purpose was to find out how important screen management is to users and which setting configurations are needed most to aid in development of the Kscreen.
-
Normally, at the end of the year, I tend to run my best annual distro roundups, choosing the finest among five operating systems or flavors thereof that showed the greatest promise in terms of stability, usability, elegance, support, and other curious items in the outgoing twelve-month period. But I have never dedicated much thought to selecting the best implementation of any one particular desktop environment, regardless of the system underneath.
Permalink
 Send this to a friend
Send this to a friend
Posted in Apple, GNU/Linux at 4:31 am by Dr. Roy Schestowitz
Summary: What we can copy from Apple and what we oughtn’t ever copy, only abolish
IMITATING Apple’s business practices in order to advance GNU/Linux is not a good idea. Imitating Apple’s presentation, however, may be acceptable (Apple’s patent aggression aside because it’s trigger-happy w.r.t. lawsuits). One thing which Apple is undoubtedly good at is marketing, unless or until it gets caught. Years ago we covered examples where Apple essentially bribed or influenced some bloggers to help manufacture some hype for the hypePad and days ago Apple got caught paying homeless people to pretend to want Apple gadgets rather than a home [1]. That’s just utterly rogue. Think different. Think Apple.
Anyway, there are several Ubuntu-based distributions which try to imitate the appearance (and sometimes behaviour) of Apple’s platforms. Pear OS [2] and Elementary OS [3] are just two of them and they are likely to meet just limited success because they aim at converting Apple fan, who would probably be disappointed as GNU/Linux can’t meet the expectation of being Apple. The many efforts to sell GNU/Linux as a “cheap Windows” (see Xandros, Linspire and several other defunct companies) were never successful because even with Wine GNU/Linux was unable to imitate Windows reliably enough. GNU/Linux is not Windows. And it’s not supposed to be.
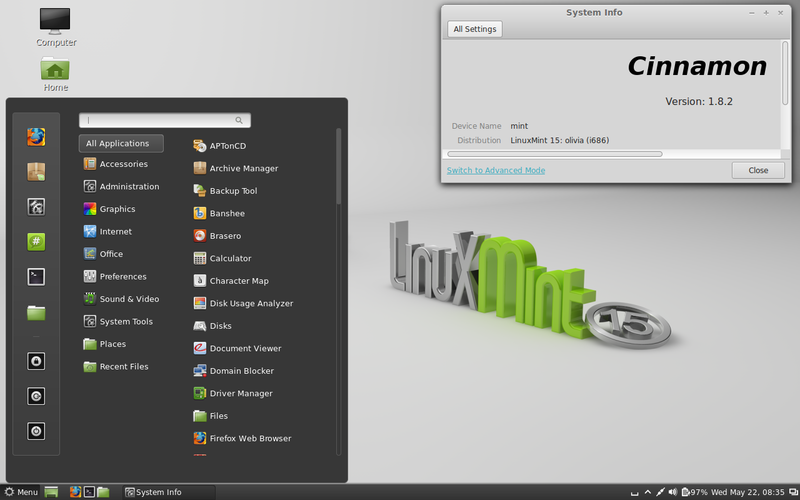
“Nobody deserves Apple-branded products as a gift; it’s not a gift, it’s a digital jail in shrink-wrapped boxes.”One distribution which uses some Apple-like graphics but does not go too far in imitating Apple is Linux Mint and right now it tries Apple’s method of selling hardware tied to the operating system [4-6]. Linux Mint is currently the distribution I install for GNU/Linux converts because it gives them the polish of Mac OSuX while not pretending to be Mac OSuX. It is easy to use (good out-of-the-box experience) and it removes the need to be technical for those who are not.
On the technical side, Apple fails on the basics [7], copies Android/Linux [8], and uses technical tricks to punish and restrict customers [9]. Nobody deserves Apple-branded products as a gift; it’s not a gift, it’s a digital jail in shrink-wrapped boxes. █
Related/contextual items from the news:
-
A businessman scheming to get his profit-minded hands on dozens of new iPhones allegedly recruited about 100 homeless people from Skid Row in Los Angeles to wait in line overnight at the Pasadena Apple Store, but many were left unpaid and stranded after his plan was exposed, local media reported Friday.
-
David Tavares, the father of the Pear OS distribution, has just shared a screenshot on Google+, teasing Linux users with the iOS 7-inspired look of his upcoming Pear OS 8 operating system.
-
Perhaps it’s a holdover from the Apple Depression of the 1990s, but I sometimes wonder where I would go if I ever needed to leave the Mac.
-
The MintBox 2 is now available and can be ordered from CompuLab at http://fit-pc.com/web/products/mintbox/
-
Clement Lefebvre, the founding father of the extremely popular Linux Mint operating system, had the pleasure of announcing today, September 13, that the next-gen MintBox mini PC is available for purchase.
-
Linux Gizmos reports that the MintBox mini-PC is shipping with Linux Mint 15 and Core i5 processors. This is a neat little computer, and I particularly like the fact that Linux Mint is the default distro on it.
-
-
Today in Open Source: Did iOS 7 borrow ideas from Android? Plus: Linux Defenders and dangerous patents, and the launch date of Ubuntu Touch 1.0
-
The Free Software Foundation encourages users to avoid all Apple products, in the interest of their own freedom and the freedom of those around them.
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Ubuntu at 3:53 am by Dr. Roy Schestowitz
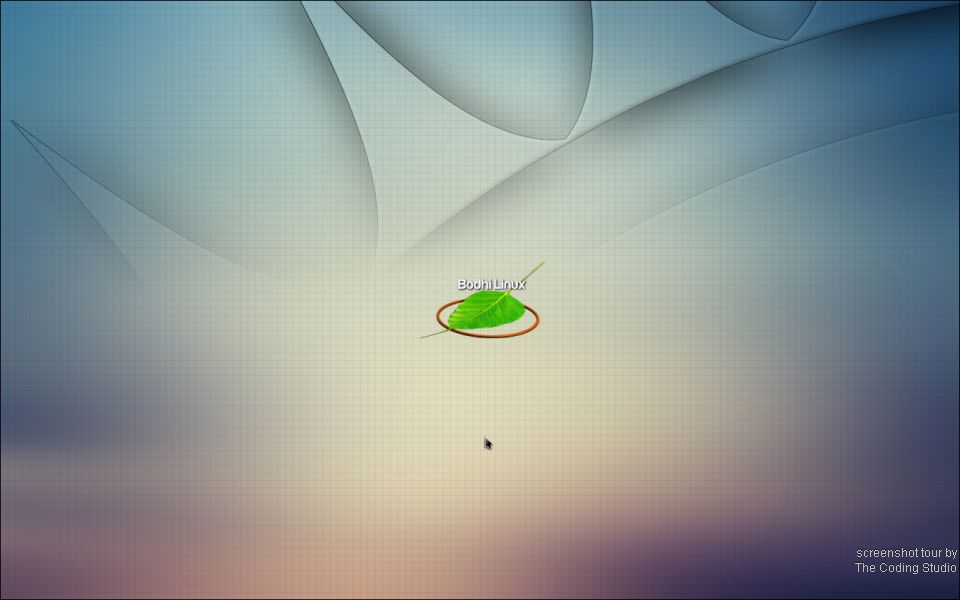
Summary: Bodhi Linux 2.4.0 brings with it a panacea for old desktops in need of a free/libre, cutting-edge and powerful operating system
Bodhi Linux is, for the most part, a one-person project [1] which rose to fame [2] a couple of years ago, earning a lot of coverage and observing many ISO downloads. Bodhi Linux is a GNU/Linux distribution based on Ubuntu and it is probably the most popular Enlightenment-based distribution that is derived from Ubuntu (putting aside obscure ones, there have been about half a dozen such distributions in the past half a decade).
“Enlightenment is compatible with very old computers, so for machines that are lesser capable consider giving Bodhi Linux a try.”I was a regular user of Enlightenment over a decade ago (I used it for development with GTK) and surely it does not get the credit or the reputation it deserves. Enlightenment is compatible with very old computers, so for machines that are lesser capable consider giving Bodhi Linux a try. Here are some screenshots [3] of the latest release.
The lead developer, Jeff Hoogland, is a very cool person who is adhering to some decent values. This is not a distribution motivated by financial interests. Some community distros were warped to accommodate such interests much to users’ chagrin. █
Related/contextual items from the news:
-
It has been close to six months since our last Bodhi Linux release – far too long! This is just our normal update release – meaning if you are already a Bodhi user and have been running your system updates then you already have all these additions running on your system!
-
After six months of hard work, Jeff Hoogland announced on September 12 that the final release of the Bodhi Linux 2.4.0 operating system was available for download, bringing improvements and bugfixes.
-
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Red Hat at 3:35 am by Dr. Roy Schestowitz
Wallpaper candidate for Fedora 20

Summary: Fedora 20 is coming and DNF is being introduced as a replacement for Yum
THE developer of Yum died a few months ago and Fedora is poised to replace Yum, introducing instead DNF, which is similar but still experimental [1]. Fedora 20 is already being prepared for release [2], despite some delays [3].
Fedora has a short support span, which is my main reason for no longer installing it. Keeping Fedora up to date has been possible using Yum and Red Hat is now trying to improve the update process of RHEL, which Techrights uses in CentOS form. █
Related/contextual items from the news:
-
Talked about last year prior to the introduction of Fedora 18 was DNF, a new experimental RPM package manager to replace Yum. DNF has been bundled as an experimental option that can live in parallel to Yum, but there hasn’t been too much to report on the project as of late, except today they’re out with a new release.
-
Half of the submission period for the Supplemental Wallpaper for Fedora 20 is over now.
-
-
If you want the newest of the new open-source software, you use Fedora Linux, but if you use Red Hat Enterprise Linux in your business, you had to wait for major releases… until now.
Permalink
 Send this to a friend
Send this to a friend
09.20.13
Posted in GNU/Linux, Kernel, Security at 11:20 am by Dr. Roy Schestowitz
Photo by Kevin
Summary: Humour used to avoid answering a serious question about whether the NSA asked for a Linux backdoor
LINUX is the most widely used operating system kernel and its annual event which we wrote about earlier today, both positively and critically, had one interesting nugget of information [1]. Torvalds responded with a joke and an ambiguity to a serious question about an important matter. Torvalds and his Linux Foundation colleagues who sign off kernels on an almost weekly basis [2] owe a more serious response to people who put Linux in governments and large enterprises (most of them outside the United States). Humour has its place, but when millions of people die due to imperialism that relies on global surveillance, then some seriousness is required. Having read some dubious text about the NSA’s SELinux and some real attempts to plant back doors in all sorts of operating systems and even a CMS like WordPress (some attempts were successful and catastrophic), I think that we deserve a serious, unambiguous answer.
“Torvalds responded with a joke and an ambiguity to a serious question about an important matter.”As a token or a relevant reminder of what the NSA does and how it does it I am appending some of the latest news bits about the NSA and about privacy in general. It turns out that complicity from developers and corporations — not necessarily hacking or cracking — is what enables to NSA to access almost every bit of information around the world, even financial transactions outside the United States. Wikileaks (i.e. journalism with an edge) was almost silenced using illegal financial embargoes that got overturned only years later (after a court battle). Worth noting, as iophk put it, is the war on journalism which we saw here in the UK last month (David Miranda). It is a classic “war on journalism,” he explained, noting that “Slashdot is now part of that by providing a platform for those that want to require reporters to rat on sources. The part about the 5th amendment is just a distraction from steamrolling over protection of confidentiality of sources in journalism.”
“Note the strawman about raping,” he said. █
Related/contextual items from the news:
-
Torvalds responds to a question about whether the U.S. government asked him to put a backdoor in Linux, and explains why he’s a developer and how others can be.
[...]
Torvalds responded “no” while nodding his head “yes,” as the audience broke into spontaneous laughter.
-
Greg Kroah-Hartman also announced today, September 14, that the twelfth maintenance release for the 3.10 LTS branch of the Linux kernel is now available for download.
-
The United States’ NSA intelligence agency is interested in international payments processed by companies including Visa, SPIEGEL has learned. It has even set up its own financial database to track money flows through a “tailored access operations” division.
-
The NSA has been widely monitoring international banking and credit card transactions, a new report says referencing Edward Snowden’s leak. The agency targeted Visa customers and global financial service SWIFT and created its own money flows database.
-
The Obama administration secretly won permission from a surveillance court in 2011 to reverse restrictions on the National Security Agency’s use of intercepted phone calls and e-mails, permitting the agency to search deliberately for Americans’ communications in its massive databases, according to interviews with government officials and recently declassified material.
-
It accidentally published the real name of one of its young models, who had been working as Ancilla Tilia. Her mother, who shared her real surname, started getting some uncomfortable calls.
-
The Swedish National Defence Radio Establishment (FRA) has repeatedly broken the laws and pushed legal boundaries in its surveillance operations, according to revelations by the Swedish media on Monday.
-
-
-
Newly released documents reveal how the government uses border crossings to seize and examine travelers’ electronic devices instead of obtaining a search warrant to gain access to the data.
-
In the UK mobile Internet providers are required to block content that may be considered “harmful” to children. The filter mainly targets adult oriented content, but one provider now says that VPN services also fall into this category as they allow kids to bypass age restrictions. Down Under a similar filtering proposal is making headlines today, but after a policy backflip it appears that Australia may escape a mandatory Internet filter for now.
-
INTERNET RIGHTS GROUP the Electronic Frontier Foundation has won a legal victory that will force the release of hundreds of NSA surveillance related documents that date back at least nine years.
-
Intelligence-gathering agency has created working groups to access contacts lists, SMS, and user location on the three most popular mobile platforms, according to classified documents viewed by Spiegel.
-
The new Snowden revelations are explosive. Basically, the NSA is able to decrypt most of the Internet. They’re doing it primarily by cheating, not by mathematics.
-
-
-
Top-secret documents leaked by former National Security Agency contractor Edward Snowden confirm that the NSA introduced weaknesses into computer security standards adopted by the National Institute of Standards and Technology, putting at risk NIST’s reputation as a disinterested purveyor of cyber guidelines.
-
I’ve heard a rumour that that nice man Mr Blair is similarly in love. Apparently, he thinks that my fingers are so pretty that he just has to have little pictures of all ten fingertips. I’d better get my nails done so that they look good – I wouldn’t want to let him down.
-
A Johns Hopkins computer science professor blogs on the NSA and is asked to take it down. I fear for academic freedom.
-
It was only a matter of time before we learned that the NSA has managed to thwart much of the encryption that protects telephone and online communication, but new revelations show the extent to which the agency, and Britain’s GCHQ, have gone to systematically undermine encryption.
Without the ability to actually crack the strongest algorithms that protect data, the intelligence agencies have systematically worked to thwart or bypass encryption using a variety of underhanded methods, according to revelations published by the New York Times and Guardian newspapers and the journalism non-profit ProPublica, based on documents leaked by NSA whistleblower Edward Snowden.
-
-
$250m-a-year US program works covertly with tech companies to insert weaknesses into products
-
“It is this culture of surveillance and monitoring that is seeping into their lives offline – and making girls feel that it is perfectly acceptable for boys to demand to know their location and what they are doing at all times.”
-
-
Starting around August 20, we started to see a sudden spike in the number of Tor clients. By now it’s unmistakable: there are millions of new Tor clients and the numbers continue to rise…
-
Today’s post covers Tor hidden services and their anonymity. In the first few paragraphs I will provide some basic, high level information on the Tor network and then talk about a way to uncover the real location of some anonymous hidden services.
-
PRISM and other recent revelations put a touch of gray in Chrome’s silver lining.
-
-
The US Drug Enforcement Administration has enlisted telecom giant AT&T to develop a massive telephone records database that may put the National Security Agency’s domestic phone surveillance to shame.
-
The latest published leak from NSA whistleblower Edward Snowden lays bare classified details of the US government’s $52.6 billion (£33.9 billion) intelligence budget, and makes the first reference in any of the Snowden documents to a “groundbreaking” US encryption-breaking effort targeted squarely at internet traffic.
-
PRIVACY HATER Facebook has released its latest raft of changes to its terms and conditions, including a small update to the way the firm makes use of its facial recognition technologies to increase the accuracy of photo-tagging.
-
Facebook is slurping mobile phone numbers from its users without explaining why, it has emerged.
-
The Washington Post reports that the NSA paid $278 million this fiscal year to tap into phone lines, e-mail and instant messages
-
-
The GCHQ listening post on Mount Troodos in Cyprus is arguably the most valued asset which the UK contributes to UK/US intelligence cooperation. The communications intercept agencies, GCHQ in the UK and NSA in the US, share all their intelligence reports (as do the CIA and MI6). Troodos is valued enormously by the NSA. It monitors all radio, satellite and microwave traffic across the Middle East, ranging from Egypt and Eastern Libya right through to the Caucasus. Even almost all landline telephone communication in this region is routed through microwave links at some stage, picked up on Troodos.
-
Finally the videos from the whistleblower track at the August international geekfest OHM 2013 in the Netherlands are beginning to emerge. Here’s one of the key sessions, the Great Spook Panel, with ex-CIA Ray McGovern, ex-FBI Coleen Rowley, ex-NSA Tom Drake, ex-Department of Justice Jesselyn Radack, and myself.
-
President Barack Obama sought Wednesday to reassure Europeans outraged over U.S. surveillance programs that his government isn’t sifting through their emails or eavesdropping on their telephone calls. He acknowledged that the programs haven’t always worked as intended, saying “we had to tighten them up.”
-
The NSA has huge capabilities – and if it wants in to your computer, it’s in. With that in mind, here are five ways to stay safe
-
The latest revelations from the Guardian give good evidence of why they have recently been the target of government harassment, and also why this is entirely unjustified.
-
If an Android device (phone or tablet) has ever logged on to a particular Wi-Fi network, then Google probably knows the Wi-Fi password. Considering how many Android devices there are, it is likely that Google can access most Wi-Fi passwords worldwide.
-
The Resolution calls on member states to regulate and effectively oversee the secret services and special procedures and to pass legislative provisions at the national level to protect whistleblowers. The resolution also calls upon the Secretary General to launch an inquiry under Article 52 of the European Convention on Human Rights.
-
-
In the previous article we set up Tor and was able to successfully use it to browse the web securely. Now we’ll take it a step further and become part of the Tor browsing network. As being an exit node holds a bit more power we’ll take it a step back and be a relay node. This means that traffic will flow in and out of our network, but no one can see it coming from us or somewhere else. Tor also states that this can provide better anonymity than just running it as a client.
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Kernel at 10:51 am by Dr. Roy Schestowitz
Christopher Columbus did not “discover” America, he invaded it

Summary: GNU is being removed from the timeline of the GNU/Linux operating system, owing not just to ignorance but also wilful omission
Linuxcon took place some while ago, giving many corporations an opportunity to spread some shameless self-serving marketing messages. This in itself is not a big issue. Corporations exist to maximise profit and they need to market themselves, sometimes selfishly. It’s when deception and false marketing are encountered that we should speak out.
Sadly, the host of Linuxcon is actually one of the biggest liars. It is not a new lie though and this accusation of ours depends on the definition of “lie”. To quote Wikipedia: “When the GNU project first started they “had an Emacs text editor with Lisp for writing editor commands, a source level debugger, a yacc-compatible parser generator, and a linker”.[3] The GNU system required its own C compiler and tools to be free software, so that these also had to be developed. By June 1987 the project had accumulated and developed free software for an assembler, an almost finished portable optimizing C compiler (GCC), an editor (GNU Emacs), and various Unix utilities (such as ls, grep, awk, make and ld).[4] They had an initial kernel that needed more updates.”
“Without the GPL, it’s unlikely that many people would have gotten involved in this kernel’s development. Linux needed GNU.”The word “Linux” is commonly used to refer to a system created 30 years ago by Richard Stallman. It was called GNU. The Linux Foundation knows this, but it exploits a misunderstanding or a confusion to remove GNU out of history and pretend Linus Torvalds started it all. This is not an accidental error and in a way they can justify themselves and insist that have said the truth. It’s a bit like a lie by omission [1]. This lie tends to perpetuate through misinformed people, owing its strength (and people’s irrational adherence to it) to inertia.
There are some jokes about Linux version numbers and Windows [2-3] (not so amusing), with some Cult of Personalities coverage revolving around Linus Torvalds [4-5], who again entertains the questions about Microsoft. Apart from that, there is some interesting bunch of numbers about Linux development [6,7], but again, developers of non-kernel parts get mostly ignored, despite the de facto definition of “Linux” being more than just this undoubtedly powerful kernel.
Having had many opportunities to speak with Stallman as of late I can truly relate to his concern about omission of GNU and Free software as a whole. It’s almost as though his life’s work (personal sacrifice) got abducted and the symptoms are everywhere we look. Be sure to remind the Linux Foundation of GNU; without GCC (GNU), there would have been no runnable Linux. Without the GPL, it’s unlikely that many people would have gotten involved in this kernel’s development. Linux needed GNU.
GNU will soon turn 30 years old and we are planning to publish special Stallman interviews to mark this important anniversary. █
Related/contextual items from the news:
-
One of the greatest impacts Linux is having on the technology industry is in the way it’s built. We often tout Linux’s success stories – from running Facebook, Amazon and Google to powering eight out of 10 financial trades to running the world’s supercomputers and mobile devices, and more. But these successes are the results of a massive collaborative development effort that is 22 years in the making and today is being studied and leveraged by everyone from software developers to business executives in industries ranging from networking to financial services to life science and more.
-
Linux 3.12 gets ‘Suicidal Squirrel’ moniker as Linux Lord recovers from SSD FAIL
-
A few minutes ago, September 14, Greg Kroah-Hartman announced that the first maintenance release for the 3.11 LTS branch of the Linux kernel is now available for download.
-
Today in Open Source: A broken SSD halts Linux changes. Plus: LinuxQuestions.org milestones, and see startup services in Linuxs
-
In a free-wheeling Q&A session Linus Torvalds and other top Linux programmers, talked about Linux, scuba-diving, and other odds and ends of the developer life.
-
Both the pace of development and the volume of code continue to grow in the open-source Linux kernel.
-
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »

























 Content is available under CC-BY-SA
Content is available under CC-BY-SA