07.08.15
Posted in Free/Libre Software, FUD, Google, Microsoft at 8:33 am by Dr. Roy Schestowitz

Summary: CIO, a Web site of IDG, smears Microsoft’s competition by quoting sources that are closely aligned with and/or subservient to Microsoft
AN old ‘friend’, a branch of Microsoft AstroTurfing ‘Consumer’ ‘Watchdog’, has just reared its ugly head again with help from IDG‘s “CIO” (a misleading site name). Consumer Watchdog is not a watchdog and it’s not for consumers. IDG should know better than that by now. Consumer Watchdog is an attack dog and a front group against Google. Right now it complains that Google is not censoring enough (as if censorship is a good thing). Remember that censorship is not privacy and “Consumer Watchdog” cares only about making Google look bad, it never cared about privacy at all.
To quote the nonsense from IDG’s “CIO” site (neglecting to correctly identify the messenger): “Consumer Watchdog will file a complaint against Google with the U.S. Federal Trade Commission Tuesday, said John Simpson, director of the group’s Privacy Project. The complaint will ask the FTC to rule that Google, by declining to delete search engine links on request from U.S. residents, is an unfair business practice that violates the U.S. FTC Act.”
‘Consumer’ ‘Watchdog’ has a Privacy Project? That’s just hilarious. That’s would be like BP forming a “green group”. Moreover, it is hilarious that IDG covers “privacy” and pretends that it cares about the concept because CIO, for example, based on NoScript, want to run a massive number of scripts on my machine from just about thirty different domains! Holy cow! The reader is the product and browsing habits are up for sale to so many entities at the same time. The same is true for other sites of IDG (there are many of them).
“The original source of that really bad scraper site is a CIO trash opinion piece,” wrote someone to us. IDG has become complicit in lobbying and AstroTurfing, whether it realises this or not.
Another new piece of garbage came from IDG only a short while ago, quoting XenSource (Microsoft-friendly as we have shown many times in past years) as some kind of authority on FOSS. This is again mischaracterising the messenger to give the messenger undeserved credibility. That’s like calling Richard Stallman an “open core” proponent. The headline boldly states that “open source business model is a failure” and the body belatedly adds vital context to this headline: “That’s the conclusion of Peter Levine, a partner at Andreessen Horowitz, the Silicon Valley venture capital firm that backed Facebook, Skype, Twitter and Box as startups. Levine is also former CEO of XenSource, a company that commercialized products based on the open source Xen hypervisor.”
“…sites that pretend to offer ‘news’ often just treat readers (audience) as the product, selling the audience to the real client (the advertiser or agenda setter).”Levine is not a truly technical person and he ignores plenty of evidence that open source as a business model works, and often works very well. A lot of people can easily claim that the proprietary software business model is inherently flawed because very few proprietary software companies sell stuff (only a few giants do). A lot of those claiming that no open source business model can work also say FOSS is sexist, racist, not secure, brings licence/liceinsing risk, etc. — the very same things that can be said about proprietary software. If only 10% of Free/libre software companies manage to survive in the long term (based on level of sustainable income) it might not be any different, statistically, from their proprietary counterparts. The company my wife and I work for does manage to make income from Free/libre software development and maintenance. This company is far from the only one in Europe and many are doing very well. Proprietary software is not a business model. Free/libre software development is not a business model either. It’s modality of distribution/development. People buy services, not zeros and ones. For IDG to publish and republish misleading headlines like “Why the open source business model is a failure” is merely to provoke. For IDG to call ‘Consumer’ ‘Watchdog’ a “privacy group” (even in the headline) and to label censorship “right to be forgotten” is to reveal sheer bias. Remember that Microsoft is a huge client of IDG (advertising, IDC contracts and so on), so maybe we oughtn’t be very shocked by that. Here is a great new example of proprietary software advertment disguised as an article. It bashes Free/libre software as a whole, too, while promoting one particular piece of proprietary software in Computer Weekly.
Watch out what you read because there is plenty of agenda on sale everywhere. Moreover, sites that pretend to offer ‘news’ often just treat readers (audience) as the product, selling the audience to the real client (the advertiser or agenda setter). That’s their business model. Very unethical. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft, Security, Windows at 7:43 am by Dr. Roy Schestowitz
A game of perception alternation
“Well, it’s in the brand. The image you create around the brand. That’s why I need you in this company. Because nobody in this company, or in this industry, really understands that. And if we can have the perception, I can create the reality. With the combination of the reality and the perception, nobody will ever beat us.”
–Bill Gates
Summary: More AstroTurfing for Vista 10, including shameless promotion of the mere perception of it being ‘open’ and ‘secure’
THINGS must be working out pretty well for Microsoft’s PR agencies when/if even some Linux sites are willing to promote the NSA-friendly (hyper-visor runs only on Windows) Hyper-V. This is a little frustrating because it is not hard to see what it’s all about for Microsoft, whose software is made insecure by design. As FOSS Force put it the other day:
I assume that most enterprise users of Microsoft products already know not to trust Redmond to handle Windows’ security. I worry, however, about the poor consumer who plops a thousand dollars down for a laptop, and thinks it’s just fine to stop in to use the free Wi-Fi at Mickey Dee’s for a quick check of the bank account while being protected by nothing more than the best Redmond has to offer.
It looks like Vista 10 will remain as flawed and inherently insecure and its predecessors, no matter how much AstroTurfing Microsoft does (it gets worse by the day, as perception changing is the goal with official release day imminent) and how much openwashing Microsoft constantly does. It’s hard to keep up with the propaganda and refute it quickly enough.
Yesterday we spotted Microsoft’s propaganda channel (Channel 9) brainwashing Microsoft staff and readers of Channel 9, implicitly telling them that Visual Studio “open source”. Openwashing of SAP [1] and Apple [2] (below) could also be found in the news yesterday, so not only Microsoft does this. Remember that both companies were asked (if not demanded) by Russia to reveal their source code last year, for fear of back doors. We don’t know if SAP and Apple ever complied. █
Related/contextual items from the news:
-
SAP SE is dedicated to helping businesses respond to market demands around the clock, according to Steve Lucas, president of Platform Solutions at SAP. Its partnership with Red Hat, Inc. is a key part of its strategy. In an interview with theCUBE at RedHat Summit, Lucas explained further.
-
Recently, Apple released its programming language, Swift 2, to the public. By releasing Swift to the open source community, Apple is giving software developers more access to and control over the programming language. This release opens up a myriad of exciting possibilities for application development, software advancements and increased functionality.
Permalink
 Send this to a friend
Send this to a friend
Posted in Apple, Europe, Patents at 7:19 am by Dr. Roy Schestowitz
Who’s copying who?

Summary: Europe is being drained by the patent industry (lawyers, judges, etc.) while the US gradually takes on the problem
“So Software isn’t Patentable in the EU but the EPO is ignoring the Law?”
That’s a comment made the other day by “AntiSoftwarePat” over at Twitter. Well, we have already shown many other instances where the EPO ignores the law — knowingly too — including the extension of patent scope (in order to artificially elevate patents count).
The Unitary Patent will take expansion of patent scope even further, transcending borders. “UK Unitary Patent ratification before Brexit referendum, Mr Cameron is taking risks by giving EU super patent powers,” wrote the FFII’s President regarding this new article about UK-IPO. “In a statement sent to Out-Law.com,” said the author, “the IPO ruled out ratification of the Agreement this year but said that it intends to complete the “domestic preparations” for ratification ahead of the UK referendum on whether the country should remain in the EU, which is scheduled for some time in 2017.”
So they are jumping the gun. The public isn’t even taken into account.
“Hey, let’s patent life,” some folks may think (they can make a lot of money from that). According to this article from a London-based blog of lawyers, “Life sciences come to life again, this time in Berlin”. To quote: “Arrangements are now being made for the training of judges, the provision of court facilities and the projecting of existing patenting and dispute resolution techniques on to a fresh canvas. This is a scenario in which the accumulated experience, knowledge and wisdom of the life science sector cannot be relied upon in the absence of rigorous double-checking against a new framework for patenting, new litigation rules and — this is going to hurt the most — a set of complex transitional provisions.”
This shows that Europe is rushing (even fast-tracking) these expansions without public consent. While the US is narrowing down patent scope, Europe seems to be expanding patent scope.
A new article from the US (CBS) asks: “What would ‘real’ patent reform look like?”
The author correctly points out that “last year, the US Supreme Court issued a number of patent-related decisions that drew modest limits around both the process and substance of newly created categories of patents, including for software and business methods. Courts and the Patent Office became more aggressive about rejecting or overturning applications that should never have been granted. As a result, the overheated market for low-quality patents collapsed.”
The whole patent system in its current form is so utterly corrupt, biased and inherently protectionist (that’s just its goal, not publication). Too few people are willing to say that. Watch what Apple is patenting right now [1, 2]. It’s computer vision, i.e. software patents, on selfies! Will Europe go down the same abyss? hopefully not. European citizens need to educate themselves about what today’s patent system really is and who it benefits. █
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Red Hat, Security at 6:47 am by Dr. Roy Schestowitz
Red Hat and back doors: poll from FOSS Force
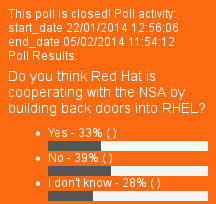
Summary: The return of XKEYSCORE to some media outlets (not news anymore) brings us back to debating Red Hat’s role (also not really news)
QUITE a few sites (see [1-3] below) seem to be talking about Red Hat’s special (but no longer secret) relationship with the NSA, which is not at all news. The NSA uses a lot of RHEL (and also Fedora) on some malicious spying equipment, based on various NSA leaks. We already wrote a great deal about this back in 2013 [1, 2, 3, 4]. The only new thing we learn from the latest articles is that Red Hat continues to refuse to remark on the subject, even when asked by journalists (see the first article below). █
Related/contextual items from the news:
-
A little over two years ago, the first disclosures about the massive surveillance operation being carried out by the NSA were made in the Guardian, thanks to an intrepid contractor named Edward Snowden.
Now comes the rather disturbing information that the NSA runs its XKEYSCORE program — an application that the Intercept, the website run by journalist Glenn Greenwald, describes as NSA’s Google for private communications — for the most part on Red Hat Linux servers.
-
If report is correct, Red Hat’s marketing department has a very tricky customer reference
-
SELinux is a product of the NSA and some worried when it was added to Red Hat, Fedora, and later many other distributions. Even before Snowden revealed the massive government spying, having the NSA anywhere near Linux activated certain Spidey-senses. Now we learn that SELinux may have had an exploit for bypassing the security enforcements. Italian software company Hacking Team, who admits to providing “technology to the worldwide law enforcement and intelligence communities,” has been selling technology to governments (most with bad human rights records) to assist in gathering surveillance data on citizens, groups, journalists, and other governments. Recently Hacking Team was hacked and their information has been leaked onto the Internet. Besides the SELinux exploit, it’s been reported that the FBI, U.S. Army, and the Drug Enforcement Agency are or were customers of Hacking Team’s services.
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 6:44 am by Dr. Roy Schestowitz

Contents
-
Desktop
-
In fact, her prowress around Linux and FOSS is to such a high degree that it makes her father proud beyond words. Recently she was having some problems with Linux Mint for which the solution, she decided, was to upgrade to Rafaela 17.2 shortly before it was ready for prime time. I started into the litany of what to do in a upgrade, and she shushed her old man — “I got this Dad,” before adding the family head shake accompanied by the word, “Sheesh.”
-
It’s great having a little netbook that I don’t actually care about. It cost a few hundred, years ago, and rather than spend a few more hundred now for a new one, it serves its function and I care even less about it. That’s wonderful for the thing I use it for most – travel – because if it gets stolen, who cares? Working in the cloud on terrible hardware — it feels a lot like freedom.
-
Server
-
The architectural change in Cloud computing sparked by Docker is a rare occurrence. And a few key practices made Docker, Inc. successful enough to bring about this critical change. First, Docker realized the importance of agility in infrastructure and capitalized on this.
Businesses like Amazon proved that using an agile application is critical to business survival. “If you’re not trying to learn how to take advantage of agile infrastructure, of agile applications, you’re going to be left behind,” Scott Johnston, SVP of Product at Docker, told theCube at DockerCon 2015.
-
Kernel Space
-
The father of the Linux project, Linus Torvalds, talked about Valve and its potential role in the Linux ecosystem with the upcoming gaming consoles.
-
Gummiboot is dead, of course, because it was spun into systemd to form systemd’s SD-Boot (U)EFI boot manager. SD-Boot has been in there since systemd 220 as an optional feature and can be used for doing some cool stuff.
-
-
While Linux is open-source, which allows people to change it as they please, Torvalds remains the lone official arbiter of the software, guiding how Linux evolves. He is The Decider.
-
Graphics Stack
-
Applications
-
I first started using ntop about eight or nine years ago. I was technology director of a K-12 public school, and we were looking for network analysis tools that would not break our budget. I found ntop through a Google search and installed it on an extra computer we had that was running CentOS.
-
-
-
Laptop Mode Tools is a power-saving package for Linux systems, which lets users increase the life expectancy of a laptop’s battery. A new version has been released and is now available for download.
-
Today the ownCloud community released ownCloud 8.1. You might think it sounds like a smaller release because we called this 8.1 instead of 9.0 but you’d be wrong. The contributor community hasn’t slowed down, quite the opposite. By the end of last year we decided to do smaller releases instead of huge ones. Because of that we will jump to a major version number only once a year and will increase the minor version number for the other releases. So this one is called 8.1 but it’s a major new version. So what is in 8.1?
-
Instructionals/Technical
-
Desktop Environments/WMs
-
If you are new to Linux then I’m sure you are giving up lots of time choosing Desktop Environment of your Linux Distribution. You are probably thinking to give a try to each one of them but that’s very time consuming. That’s why here I’m reviewing the 5 Best Linux Desktop Environments with the pros & cons. The article gives you what you should know for choosing a DE. So let’s get started!
-
K Desktop Environment/KDE SC/Qt
-
-
-
The Kexi report plugin has reached milestone 1 (build and display). In Kexi 3, the report plugin is powered by the new KReport library, which has been separated out of Calligra into it’s own repository to allow re-use by other projects.
-
3D visualization in LabPlot is supporting now several types of data:
Spreadsheet
Matrix
File sources (currently only .obj and .stl files)
-
I’d like to introduce KDE Reports, a web app that shows graphical reports that can help you get insight about activity going on with different KDE projects.
-
Repeating what became a constant on last years, KDE project is bringing an eventful series of presentations and activities on community driven software to the FISL, the Fórum Internacional de Software LIvre, which will be realized at Porto Alegre, south of Brazil, starting July 7.
-
GNOME Desktop/GTK
-
As you may know, GNOME Commander is an open-source two panel file manager similar to Norton Commander or Midnight Commander, being very popular among the Linux power users.
Among others, it has support for tabs, permits the users to select or deselect files, has support for FTP, SAMBA, folder bookmarks and history, integrated command-line, embedded file viewer and other useful features.
-
-
New Releases
-
The upgrade is the first in two years since BackTrack Linux was redeveloped and relaunched as Kali Linux in May 2013. It has followed two-year upgrade cycles since 2011 when a new version was released every 12 months
-
Arch Family
-
Manjaro Linux 0.8.13 has received a new update pack, the third for this development cycle, and the devs have upgraded a lot of the biggest packages, including LibreOffice and some of the supported desktop environments.
-
Slackware Family
-
LibreOffice galore! Last week saw the announcement of the latest in the 4.x series, and I decided to build LibreOffice 4.4.4 packages. This time however, they are created for Slackware 14.1. The stable release of Slackware deserves the latest stable office suite to keep you guys productive.
-
Red Hat Family
-
A little over two years ago, the first disclosures about the massive surveillance operation being carried out by the NSA were made in the Guardian, thanks to an intrepid contractor named Edward Snowden.
Now comes the rather disturbing information that the NSA runs its XKEYSCORE program — an application that the Intercept, the website run by journalist Glenn Greenwald, describes as NSA’s Google for private communications — for the most part on Red Hat Linux servers.
-
If report is correct, Red Hat’s marketing department has a very tricky customer reference
-
SELinux is a product of the NSA and some worried when it was added to Red Hat, Fedora, and later many other distributions. Even before Snowden revealed the massive government spying, having the NSA anywhere near Linux activated certain Spidey-senses. Now we learn that SELinux may have had an exploit for bypassing the security enforcements. Italian software company Hacking Team, who admits to providing “technology to the worldwide law enforcement and intelligence communities,” has been selling technology to governments (most with bad human rights records) to assist in gathering surveillance data on citizens, groups, journalists, and other governments. Recently Hacking Team was hacked and their information has been leaked onto the Internet. Besides the SELinux exploit, it’s been reported that the FBI, U.S. Army, and the Drug Enforcement Agency are or were customers of Hacking Team’s services.
-
Gaining entry to the open-source community can seem daunting to customers unfamiliar with the territory. Red Hat CEO Jim Whitehurst said that might be because they don’t understand that it isn’t just one large community, but several different ones.
“There are thousands of open-source communities, and the each have their own culture. They each have their own norms, ways of working, you know, personalities. And breaking in isn’t easy,” Whitehurst said.
-
-
Sell-side Wall Street analysts are anticipating Red Hat, Inc. (NYSE:RHT) will post a current quarter earnings per share of $0.29. This figure is based on the combined estimates of the analysts that cover the company. For the period ending on 2015-05-31 the company reported earnings per share of $0.31. Based on the latest public information, the firm is slated to next report earnings on or around 2015-09-17.
-
Fedora
-
Fedora 22 GNOME felt very snappy for me. All windows opened and closed very quickly in the Live session. There were no bugs or crashes during my Live run. The system was stable.
However, I felt quite uncomfortable in the system itself. I think it is partially because I am not very familiar with GNOME 3, and its concept is not very close to my heart.
But I must admit that in many places Fedora 22 left the impression of something unfinished, still requiring polishing. I’ve never felt this in recent releases of Ubuntu or Linux Mint. Some applications like Weather or Map still lack features that we take for granted in similar web tools.
I wish the Fedora team success in improving their system in future releases, and see them soon!
-
Debian Family
-
Plans have been laid for making GCC 5 the default compiler in Debian Unstable by month’s end. With the move to GCC5 comes libstdc++6 ABI breakage.
GCC 5 is a huge compiler update and offers a ton of new features/functionality but for a distribution moving to it comes some ABI incompatibilities in the libstdc++6 standard library. There is also potential package breaks due to defaulting to C++11 as the default C++ language version.
-
Derivatives
-
Canonical/Ubuntu
-
Ubuntu has daily images for its development cycle, and you can always download the latest version for the distros that is being worked on right at the moment. Or at least you could until Ubuntu 15.10. It seems that no image has passed testing for a few weeks.
-
-
Ubuntu developers are working on a new OTA update for Ubuntu Touch, and it looks like it’s coming along just fine. Even better, the new Meizu MX4 Ubuntu Edition got some special attention, and the battery life will be much better.
-
Canonical has numerous hardware partners around the world, and Lenovo is one of them. The two companies are now planning to release devices with Ubuntu Linux preloaded in India, starting with the Thinkpad L450 laptop.
-
-
-
-
-
-
-
-
-
As you may know, Canonical is constantly updating its Ubuntu Touch operating system, the OTA-5 Update being scheduled for release in mid-July.
-
At first glance, you may want to equate the Intel Compute Stick with Live USB devices of the type that you can create yourself at sites like Pendrive Linux. What’s different about the Intel Compute Stick, though, is that storage and all of the hardware resources necessary to run a computer are onboard. Users just need a display to get going, and they can add wireless mice and keyboards through Bluetooth.
-
A cups-filters vulnerability has been identified and corrected in the Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS operating system.
-
Flavours and Variants
-
Linux Mint 17.2 “Rafaela” MATE was launched last week and, as usual, I installed it on my machines to see how this distro is progressing. I found a refreshed, faster and more feature-rich distro that’s well worth trying.
-
-
Advantech is prepping an Intel Quark based IoT gateway that runs Yocto Linux and offers PoE support. mini-PCIe expansion, and web-based device management.
-
Phones
-
Hardware and software outfit Jolla is to give up making hardware, with that part of the business set to be taken on by a new, yet-to-be-announced company, with Jolla then concentrating on its Sailfish OS.
-
Tizen
-
As part of the spread of Tizen education in India, Samsung will train the youth of the Telangana Academy on innovative digital technologies based on the Tizen operating system.
-
Android
-
Apple isn’t shy about taking great features from Android, its number-one rival in smartphones and tablets.
That’s not necessarily a bad thing — it shows Apple is willing to adapt to customer demand. By doing that, it’s giving people more incentive to switch from Android to the iPhone. In fact, Tim Cook couldn’t stop talking about “switchers” — people switching from Android to the iPhone — during the company’s most recent earnings call in April.
-
What: Shares of smartphone manufacturer BlackBerry (NASDAQ:BBRY) fell 14% in June, according to S&P Capital IQ data, as concerns about the Canadian company’s path forward remained in doubt amid another disappointing quarterly earnings report. But while Wall Street seemed unsure about BlackBerry’s path forward, CEO John Chen seemed decidedly more sanguine about its prospects.
-
-
Enterprise needs are a different beast from those of SMBs. Few areas define this as clearly as storage. Instead of storing a few hundred gigabytes, you’re looking at terabytes and maybe even petabytes. Failover, redundancy, security, backups—all essential when it comes to enterprise storage.
You might think the only viable solutions for such tasks are proprietary solutions. Fortunately, for businesses and those working within them, that assumption is incorrect. Open source has come a long way and now powers the backbone of enterprise computing—and that includes storage. Don’t believe me? Take a look at the following 10 reasons why open source could be the right storage solution for your organization.
-
We all know that open source software isn’t always pretty. Una Kravets, a front end developer at IBM, will be speaking at OSCON this year about getting more designers involved in our projects. While it’s easy for developers to see that working together produces better software, it’s not always that way for designers who are trained to work alone. I had the chance to interview Una about open source, design, and her upcoming talk.
-
I’ve been involved with open source software since 1994. At that time I was working for a solution provider, and a customer asked us to implement a seamless authentication system for mobile users. Neither RADIUS or TACACS met our needs, and we had to build a custom solution. Luckily enough, we didn’t need to start from scratch, as we were able to borrow some open source code.
-
-
Events
-
In addition to picking up technical skills, networking, and learning about products and services in the expo, OSCON attendees can learn practical community-building tricks. In this interview, Kara Sowles (community initiatives manager at Puppet Labs) and Francesca Krihely give advice for hosting a community event. They’ll be teaching a half-day tutorial on planning and running tech events at OSCON 2015 in Portland.
-
Web Browsers
-
Mozilla
-
Emma Irwin is a participation designer at Mozilla who dedicates a lot of volunteer time to educating and empowering adults and youth on the web through making. She has a background as web developer and lives in a small Vancouver Island town with her husband and three daughters.
-
As you may already know, Firefox is being developed on three separate channels. First, the features are implemented in the developer branch, they reach the beta channel when enough tests have been performed and finally, some of the new features from the betas get included in the stable version of Firefox.
Recently, Firefox 40.0 Beta 1 has been released, bringing improved scrolling, graphics and video playback performance for Linux. And Mozilla claims that this improvements are Linux specific.
-
-
Firefox is about to undergo some dramatic changes, according to Mozilla. Most notably, it sounds like future versions of Firefox will focus on Firefox-esque features such as Private Browsing Mode, while features that are unpolished or otherwise not very useful will be stripped out of the browser entirely. Furthermore, it looks like Mozilla is finally getting serious about moving Firefox away from XUL and XBL, though it isn’t clear if they will be replaced with open Web technologies (HTML, CSS, JS) or native UI.
-
Firefox has gone through a rough time over the last couple of years, with increased competition from Chrome and other browsers. Now the browser’s developers are planning big changes to Firefox. Will these changes win back users and developers who have abandoned Firefox?
-
SaaS/Big Data
-
The next major OpenStack cloud platform release is set to debut in October and is codenamed : Liberty but what follows Liberty? OpenStack Foundation members have voted and the winning name is Meiji.
-
Databases
-
In June, Bloomberg conducted a survey of 20 startups valued at $1 billion or more, reporting, “None of the companies surveyed indicated they had a large Oracle database deployment for their main services though many used bits of Oracle software to run aspects of their organizations.”
-
Security
-
Server admins and developers beware: The OpenSSL Project plans to release security updates Thursday for its widely used cryptographic library that will fix a high severity vulnerability.
OpenSSL implements multiple cryptographic protocols and algorithms including TLS (Transport Layer Security), which underpins encryption on the Web as part of protocols like HTTPS (HTTP Secure), IMAPS (Internet Message Access Protocol Secure) and SMTPS (Simple Mail Transfer Protocol Secure).
-
A few days earlier, small USB drives had been inserted into the company’s computers. They were programmed to intercept the nine-digit PINs that controlled access to DP World’s shipping containers. Besides fruit, metals, and other legitimate cargo, some of these containers carried millions of euros in heroin and cocaine. To get their drugs out of the port, often traffickers use low-tech methods: They hire runners to jump fences, break open containers, and sprint away before guards can catch them, earning as much as €10,000 ($11,200) a trip. Stealing PIN codes is more elegant and less risky. Whoever has the codes can pull into the terminal, enter the PIN into a keypad, wait as robot-controlled loaders put the container on their truck, and drive off—sometimes minutes ahead of the cargo’s legitimate owner.
[...]
There was only one condition of the release: Van De Moere had to give Okul an intensive training session on Linux, the operating system on which Metasploit, the hacking software, is based. A few weeks later, according to police and interviews, he did so over one weekend at a Holiday Inn in Ghent. In November, Van De Moere returned two antennas and had a couple of beers with Okul. That was the last either man would see of the Turks.
-
Joanna Rutkowska came up with the idea of Anti Evil Maid. This can take two slightly different forms. In both, a secret phrase is generated and encrypted with the TPM. In the first form, this is then stored on a USB stick. If the user suspects that their system has been tampered with, they boot from the USB stick. If the PCR values are good, the secret will be successfully decrypted and printed on the screen. The user verifies that the secret phrase is correct and reboots, satisfied that their system hasn’t been tampered with. The downside to this approach is that most boots will not perform this verification, and so you rely on the user being able to make a reasonable judgement about whether it’s necessary on a specific boot.
-
Defence/Police/Secrecy/Aggression
-
Of all the voices challenging the Israeli military’s occupation of the Palestinian Territories, those of Israeli soldiers stand out as powerful insights from within the military establishment.
Avner Gvaryahu is director of public outreach for Breaking the Silence, a group of Israeli veterans who are working to dismantle the traditional narrative put forth by their own military establishment. The former soldiers founded the organization in 2004 after realizing they shared deep misgivings about what they had seen and done while serving in the Occupied Palestinian Territories. They felt a moral obligation to present the truth, and over the past decade, they have collected, fact-checked, and published over a thousand testimonies from soldiers of ranks high and low. These testimonies reflect a deterioration of moral standards and worrying shifting of the rules of engagement. Through lectures, reports, and other public events, Breaking the Silence has brought to light what so many try to ignore: the grim reality of what it takes to sustain a military occupation of an entire population.
-
We have companies that recruit and control active armies of mercenaries, which are responsible for thousands of deaths overseas. I detest the violence of “ISIS” but it is not morally different from Executive Outcomes machine gunning villages from helicopters in Angola or from Aegis killing random vehicle occupants in Iraq who happened to be near their convoys. Yet Tony Buckingham and Tim Spicer became extremely rich after founding their careers on the latter killings, and now are respected figures in the London establishment. Apparently killing for money is good; only killing for religion is bad.
-
Finance
-
Greek banks are preparing contingency plans for a possible “bail-in” of depositors amid fears the country is heading for financial collapse, bankers and businesspeople with knowledge of the measures said on Friday.
-
The unexpectedly strong No in the Greek referendum was a historical vote, cast in a desperate situation. In my work I often use the well-known joke from the last decade of the Soviet Union about Rabinovitch, a Jew who wants to emigrate. The bureaucrat at the emigration office asks him why, and Rabinovitch answers: “There are two reasons why. The first is that I’m afraid that in the Soviet Union the Communists will lose power, and the new power will put all the blame for the Communist crimes on us, Jews – there will again be anti-Jewish pogroms . . .”
-
Greek Prime Minister Alexis Tsipras has arrived in Brussels for an emergency eurozone summit two days after Greek voters overwhelmingly turned down the terms of an international bailout in a historic rejection of austerity. On Sunday, Greeks, by a 61-to-39-percent margin, voted against further budget cuts and tax hikes in exchange for a rescue package from European creditors. Tsipras is scrambling to present a new bailout proposal as Greek banks remain shut down. If Greek banks run out of money and the country has to print its own currency, it could mean a state leaving the euro for the first time since it was launched in 1999. Euclid Tsakalotos was sworn in Monday as Greece’s new finance minister, replacing Yanis Varoufakis, who resigned following Sunday’s referendum. Tsakalotos, who has called for a “Europe of equals,” had served as Greece’s main bailout negotiator and has been a member of Syriza for nearly a decade. Like Varoufakis, Tsakalotos has been a vocal opponent of fiscal austerity imposed by the core of the eurozone, saying it has unnecessarily impoverished Greece. We go to Athens to speak with Paul Mason, economics editor at Channel 4 News, and economics professor Richard Wolff.
-
The EU elites, referred to as “creditors” but actually representing Europe’s large financial institutions, are repeatedly described as “mainstream”. That is presumably supposed to confer legitimacy on them and suggest they represent Europe and Europeans. But there is nothing “mainstream” about these unaccountable elites trying to bring about “regime change” in Greece by bleeding the country of hope. If they succeed and Syriza goes down, Greece will end up with real extremists – either the neo-Nazis of Golden Dawn or the country’s crony elites who got Greece into this mess, with the aid of the wider European elites, in the first place. What “mainstream” opinion in the rest of Europe thinks about Greece, Syriza or the European project is impossible to gauge because most European countries are too terrified to put such questions to their electorates in the way Syriza has done. – See more at: http://www.jonathan-cook.net/blog/2015-07-06/how-the-media-discredit-greek-democracy/#sthash.XwlWGfHp.dpuf
-
PR/AstroTurf/Lobbying
-
Several former commissioners are making the most of their status to gain access to EU policymakers.
-
Censorship
-
A long-running copyright fight between the Electronic Frontier Foundation and Universal Music over fair use in the digital age was considered by an appeals court today, a full eight years after the lawsuit began.
EFF and its client Stephanie Lenz sued Universal Music Group back in 2007, saying that the music giant should have realized Lenz’s home video of her son Holden dancing to Prince’s “Let’s Go Crazy” was clearly fair use. Under EFF’s view of the Digital Millennium Copyright Act, Universal should have to pay damages for a wrongful takedown.
-
Privacy
-
The Netherlands has launched a public consultation (in Dutch) on a draft bill (Google Translate) that updates the country’s existing Intelligence & Security Act of 2002. The proposed bill is wide-ranging, covering things like the use of DNA samples and the opening of letters, but a key part concerns the regulation of bulk surveillance online. As Matthijs R. Koot explains in a blog post, under the new law, mandatory cooperation will be required from “not only providers of public electronic communications networks and services, but also providers to closed user groups, including telcos, access providers, hosting providers and website operators.”
Importantly, domestic interception is explicitly allowed: “The services are authorized to, using a technical aid, wiretap, receive, record and listen to any form of telecommunications or data transfer via an automated work [a computerised system] regardless of location.” However, a new constraint on bulk collection is introduced: all such interceptions must be conducted in a “purpose-oriented manner.” As Koot notes, this aims to “limit the hay stack created using non-specific interception to relevant information,” although it is not yet clear how broad those “purposes” can be.
-
Influential group of international cryptographers and computer scientists says proposals will open door to criminals and malicious nation states
-
After suffering a massive hack, the controversial surveillance tech company Hacking Team is scrambling to limit the damage as well as trying to figure out exactly how the attackers hacked their systems.
-
Former Attorney General Eric Holder said today that a “possibility exists” for the Justice Department to cut a deal with former NSA contractor Edward Snowden that would allow him to return to the United States from Moscow.
-
The number of vulnerabilities in the wild is growing. The number of exploits, as well as the speed of those exploits — in the case of Heartbleed, only four hours from the publication of the vulnerability to a circulating exploit — is somewhat disheartening, if not all that surprising.
-
Internet/Net Neutrality
-
Last week my inbox got flooded by PR comments about how the Internet was running out of addresses, as ARIN (American Registry of Internet Numbers) and its public relations people were warning about IPv4 address availability.
Permalink
 Send this to a friend
Send this to a friend
07.07.15
Posted in America, Microsoft, Patents at 6:57 am by Dr. Roy Schestowitz

Summary: Latest developments surrounding software patents and patent trolls in the United States
For somewhat of a change, today we have some good news. Amid complaints about the patent system (see for example “Patent abuse hurts in Lansing, nation”) the USPTO‘s Michelle Lee, whom we wrote about before [1, 2, 3, 4, 5], remarks on patent reform at The Center for Strategic and International Studies (CSIS) Patent Reform Forum. She said that “there are certain changes that only Congress can make via legislation. Which is why I’m pleased that patent litigation reform legislation is currently moving forward.”
“Legacy of software patents may be short-lived if this carries on.”But with or without a reform (Congress involvement), there are changes that are made at the courts. According to patent lawyers and the pro-patents circles (even lawyers’ sites), “the Federal Circuit has affirmed that Intellectual Ventures’ asserted patent claims are invalid for lacking eligible subject matter. Intellectual Ventures v. Capital One (Fed. Cir. 2015) (Patent Nos. 8,083,137, 7,603,382, and 7,260,587).”
This is Microsoft’s patent troll, which also attacks Android/Linux these days. “The Federal Circuit on Monday rejected patent licensing giant Intellectual Ventures Management LLC’s bid to overturn the invalidation of several online banking patents it asserted against Capital One Financial Corp., saying they cover abstract ideas under the standard set by the U.S. Supreme Court’s landmark Alice ruling.”
What we have here is Alice vs. Microsoft’s main troll and the ruler, surprisingly enough, is the court most friendly towards software patents (and their originator). This is pretty big news. Those who celebrate it are on a roll. “Matthew Moore argued three Federal Circuit appeals in a single week in May,” says The Recorder. “He won all three cases.” See page two of the original decision [PDF] to see Moore’s involvement in this case. These people now know how to kill software patents even in the most hostile environment (CAFC). Legacy of software patents may be short-lived if this carries on.
On the other hand, Newegg, which was hit with millions in ‘damages’ due to software patents, finds out that it is unable to appeal. As a trolls expert put it: “Online retailer Newegg has developed a reputation for taking on so-called “patent trolls,” even when that means going through lengthy litigation and unpredictable jury trials.
“The company’s last patent trial concluded in November 2013, when Newegg faced off against a patent troll called TQP Development. TQP used US Patent No. 5,412,730 to make a vast claim to basic Internet encryption technologies, saying that anyone using the common combination of SSL and the RC5 encryption algorithm was infringing. By the time of the trial with Newegg, TQP had sued more than 120 companies and earned $45 million in settlement payments.”
This comes after a 20-month delay, so it basically predates the SCOTUS ruling regarding Alice — a ruling that would have possibly helped Newegg win this case. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 5:45 am by Dr. Roy Schestowitz

Contents
-
When Rick migrated us over to Linux, I had no idea what Linux was or why it would be any better than the Windows systems we had been using. I had seriously considered changing the whole operation to Macs, until the sticker shock set in. The fact that Rick assured me the hack would have not occurred on Linux was surely one of the reasons I went along. With some online guidance from Rick, I installed Linux on my personal/work computer at home under a dual boot. Prior to that, I had been looking at a lot of screen shots of Linux systems. A lot of them.
-
I got out of the Army mid-2003 and started my IT career. I worked my way through the ranks from help desk to Admin, and later to Engineer and Architect. As my career progressed, I took positions as a Linux Engineer for companies like Dell and Sprint. I maintained Linux infrastructures that processed life-saving information for a private company in conjunction with the National Weather Service headquarters.
-
I also mentioned that it was inconvenient to use port 443 for SSH, because it meant I couldn’t host secure Web sites on that server. Fred graciously pointed me to sslh, which is an awesome little program that multiplexes (or maybe de-multiplexes?) network traffic based on the type of traffic it sees. In simple terms, it means that sslh will listen for incoming connections on a port like 443, and if it’s a request for a Web page, it will send the request to Apache. If it’s an SSH request, it sends it to the SSH dæmon. It also has support for OpenVPN traffic, XMPP traffic and tinc.
-
Desktop
-
Over the years, I’ve heard both Windows users and Linux enthusiasts make the claim that professional media production on Linux is impossible. While there may be some workflows so over-engineered that legacy software is a must, I firmly believe that, with effort, using Linux for media production is doable.
-
-
Citrix has made good on its April promise to deliver virtual Linux desktops, today announcing it’s ready to roll out penguin-powered pretend PCs.
The company snuck the penguin-powered desktops into Feature Pack 2 for XenApp and XenDesktop 7.6. For now, Citrix says says you can choose from Red Hat Enterprise Linux 6.6 Workstation and Server, or SUSE Linux Enterprise Desktop and Server 11 Service Pack 3, the two distros the company says its customers have asked for the most.
-
Canonical, the commercial sponsor of Ubuntu, has announced that Lenovo will start shipping Ubuntu preloaded devices starting with ThinkPad L450 laptop series this month. The laptops will be on sale at selected commercial resellers and distributors at Rs 40,000.
-
Server
-
Linux container technology is the latest computing trend sweeping the computing world. A lot of financial and technical investors, Linux software programmers, and customers are betting that containers will change the way businesses manage their computer systems—from deployment to maintenance. Container technology has become its own ecosystem with no less than 60 companies supporting some aspect of the technology. But what exactly are Linux containers, and how can they help you?
-
The industry is excited about containers in application development, and it will yield significant value in the application-centric cloud
-
IBM has introduced enterprise-class containers to make it easier for clients to deliver production applications across their hybrid environments.
-
The survey, commissioned by Red Hat and conducted by TechValidate, assessed enterprise adoption plans for application containers. The survey sought responses from more than 383 global IT decision makers and professionals from April 28 to May 5. The organizations polled ranged from Fortune 500 companies to state and local governments.
-
Kernel Space
-
If all goes according to plan, the Linux 4.2 kernel merge window will close this afternoon followed by the immediate release of the Linux 4.2-rc1 test version. With all major pull requests having already been submitted for Linux 4.2, here’s an overview of the exciting new features and changed functionality to look forward to with this kernel version to officially debut later this summer!
-
Linus Torvalds has revealed that the first Release Candidate for Linux kernel 4.2 has arrived and that it’s one of the biggest ever to land. It’s big because it comes with AMD GPU register description headers, among other things.
-
As you may know, Kernel 3.19 has reached EOL (end of life), but because it is used by default on Ubuntu 15.04 Vivid Vervet, the development has been adopted by Canonical.
-
The annual Kernel Summit for 2015 will be held October 26th through the 28th in Seoul, South Korea, overlapping with the Korea Linux Forum, which will be on October 26th.
-
A few more input driver updates were mailed in this morning for the Linux 4.2 kernel. This second input update for this next kernel version has better Xbox Wireless Controller support thanks to a patch from Valve.
-
Graphics Stack
-
Rob Clark has shared a new blog post today about “happy (gpu) independence day” with his work on the open-source Freedreno driver for freeing Qualcomm Linux users of the Adreno binary blob.
-
Benchmarks
-
Now that I seem to have found a workaround for my Core i7 5775C Broadwell Linux issue that resulted in very frequent kernel panics, it’s off to the benchmark races. Here are some preliminary Linux benchmark figures for this first socketed Intel Broadwell LGA-1150 desktop CPU with Iris 6200 graphics.
-
Applications
-
-
-
-
Instructionals/Technical
-
Games
-
Torque 3D 3.7 was released last week as the new version of this advanced game engine that’s been open-source for the past three years.
Torque 3D 3.7 offers large improvements for Linux and OpenGL rendering support. The Linux client support for this game engine should now be in place in full while some bugs are still being worked out.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
For those running KDE on a systemd-based Linux system, the KDE Control Module for controlling this init system and its options has been updated.
-
Systemd-kcm 1.2.0 was released four days ago. Systemd-kcm is a KDE control module for graphically managing systemd and related services such as logind.
-
GNOME Desktop/GTK
-
The GNOME developers are working to improve the functionality and looks of some of the core apps in the stack, and it looks like Photos is just one of them. Allan Day has explained some of the changes that are going to be made to Photos, and they are quite impressive.
-
-
Reviews
-
Alpine Linux has become one of the most frequently requested distributions on my list of projects to review. Alpine is an independent distribution which, as the project’s front page tells us, is “a security-oriented, lightweight Linux distribution based on musl libc and busybox.” The project’s About page goes into more detail: “Alpine Linux is a very simple distribution that will try to stay out of your way. It uses its own package manager, called apk, the OpenRC init system, script driven set-ups and that’s it! This provides you with a simple, crystal-clear Linux environment without all the noise. You can then add on top of that just the packages you need for your project, so whether it’s building a home PVR, or an iSCSI storage controller, a wafer-thin mail server container, or a rock-solid embedded switch, nothing else will get in the way.”
-
New Releases
-
4MLinux, a mini Linux distribution that is focused on the 4Ms of computing, Maintenance (system rescue Live CD), Multimedia (e.g., playing video DVDs), Miniserver (using the inetd daemon), and Mystery (Linux games), has been upgraded to version 13 and is now ready for download.
-
The Solus project is moving very fast, and its developers have managed to push another release out the door, this time with a lot of fixes that have been spotted and repaired in a very short amount of time.
-
Screenshots/Screencasts
-
Ballnux/SUSE
-
The openSUSE community has spoken, and the name and version of the new openSUSE release have been chosen. The project is undergoing some major changes, and they had to illustrate that with a name that sells it.
-
Red Hat Family
-
As Red Hat, Inc.’s offerings become more enterprise-ready — and widely adopted — demands on its projects continue to increase. Ashesh Badani, GM of Cloud Product Strategy at Red Hat, joined theCUBE at RedHat Summit to talk about how its pipeline is structured to deliver reliable results.
-
Equity Analysts at the Mizuho Securities maintains the rating on Red Hat, Inc. (NYSE:RHT). The brokerage firm has issued a Buy rating on the shares. The Analysts at the ratings agency raises the price target from $85 per share to $88 per share.
-
Red Hat (NYSE: RHT) now offers Enterprise Linux for SAP HANA on the Amazon Web Services marketplace, ExecutiveBiz reported Thursday.
Red Hat said Wednesday it sees the listing as providing clients more avenues with which to implement big data workload deployments and data analysis work.
-
The availability of Red Hat Enterprise Linux for SAP HANA has been expanded to Amazon Web Services (AWS), Red Hat announced.
-
Fedora
-
On my Lenovo ThinkPad X1 Carbon I’ve been running Fedora 21 for the past five months to great success. While I was using Ubuntu Linux on my “most main system” (and various Linux distributions on the dozens of other systems at Phoronix and in the test lab), prior to that I was a Fedora user back in the early days of Fedora (Core).
-
Debian Family
-
Neil McGovern is the new Debian project leader, and he already made some contributions and opened up some important discussions within the project from his new position. He also revealed what he’s using on a daily basis.
-
Derivatives
-
Canonical/Ubuntu
-
Canonical has revealed some details in a security notice about a few Oxide vulnerabilities that have been found and repaired in Ubuntu 15.04, Ubuntu 14.10, and Ubuntu 14.04 LTS operating systems.
-
GPS Navigation is a free app for Ubuntu Touch, and it’s been getting constant updates for the past few weeks. It’s still in the development stages, but it looks like it’s coming together just nicely.
-
A large part of the work that’s been done for Unity 8 is focused on making it looks and feel like Unity 7. Canonical is not trying to reinvent Unity; it’s rewriting it for the future.
-
Intel has launched a Compute Stick in India. While the Intel stick will be available on Flipkart, iBall had also partnered with Intel to release its own stick-computer. Intel’s Compute stick will enable a user to transform a basic HDMI Tv or monitor into a fully functioning entry level computer.
-
-
Flavours and Variants
-
Linux Mint 17.2 is the opposite. It’s focused on real improvements and polish for the desktops we use today. Like Linux Mint 17 and 17.1, the latest release is based on the stable Ubuntu 14.04 LTS core It’s basically the same under-the-hood. Instead, Mint’s developers have spent their time polishing and improving the desktop experience.
-
-
We love Python at the Raspberry Pi Foundation—it’s our go-to general purpose programming language for most projects and activities. Our home-brewed, Pi-optimized Linux distribution Raspbian (a Debian variant) ships with a number of different languages and educational tools (Scratch, Ruby, Java, C, Wolfram, Mathematica, and, of course, the numerous others available in Linux), but the one we and many others tend to choose is Python.
-
A startup called Audeme has crossed the halfway mark on a $12,000 Kickstarter project for its MOVI (My Own Voice Interface) speech I/O shield for Arduino single board computers. An $80 early bird package ships in Feb. 2016, and a $100 package ships in Dec. 2015. The fundraising project ends on Aug. 10. The packages include access to low level serial interfaces that will enable developers to use MOVI with other SBCs such as the Raspberry Pi, says Audeme.
-
Phones
-
Tizen
-
The Samsung Z3 SM-Z300H is going to be the second Tizen based Smartphone to begin testing in India and hopefully final release. We Initially reported on the existence of the Z3 with Sammobile confirming it will be the next Tizen mobile phone to be released. Now our friends at Best Tizen Apps have noticed a shipment of a few “SM-Z300H” Smartphones making the journey from Korea to Bangalore India, reported for testing purposes. The phone is shipped as costing $205 USD per unit around 13,039 INR, but this is more of a speculated price and does not reflect final retail pricing.
-
-
Why would a software company choose to change its product from proprietary to open source? It turns out there are many good reasons, says Dan Mihai Dumitriu, CEO and CTO of networking software company Midokura. In this interview with The Enterprisers Project, Dumitriu explains the benefits.
-
Anthropologists who traveled to the jungle to study various tribes would debate (half jokingly) whether to “go native”—that is, whether to adopt the lifestyle of the people they were trying to understand, or to keep their distance (and scientific objectivity). It was a research design choice, but also a fundamental choice about one’s identity as a more-than-interested visitor.
-
Stormy Peters and Avni Khatri will present Grow an organization by planting volunteers at OSCON 2015. Peters is the vice president of technical evangelism at the Cloud Foundry and Khatri is president of Kids on Computers. In this talk, they share their experiences and lessons for growing a healthy garden of volunteers.
-
This question came up during conversations with Red Hat’s Chris Wright, a Linux kernel developer and a principal software engineer with the company.
Of course, in non-tech business speak, upstream tends to refer to production processes that involves searching for (and extracting) raw materials — in software, this is not the case.
-
Web Browsers
-
Mozilla
-
Mozilla has already announced the first Beta for Firefox 40, and it looks like Linux users are going to get some important improvements for scrolling and video playback, among other things.
-
The Logjam SSL/TLS vulnerability is among the 13 security advisories in latest stable release of the open-source Firefox Web browser.
-
-
MOZILLA HAS RELEASED the latest edition of Firefox, version 39, squishing four major bugs and adding the new features first seen in recent beta versions.
-
The best reason to adopt the new version is its repairs for three critical bugs. Detailed here, the flaws include memory corruption and “exploitable crashes.” A further two “high” severity flaws, half a dozen rated “moderate” and a single “low” severity bug have also been squashed.
-
SaaS/Big Data
-
Oracle/Java/LibreOffice
-
LibreOffice 5.0 is planned for release in early August and today Charles H. Schulz said this is “an unique release.” When it comes to features and styles Schulz said the broad range of changes and improvements will be easily visible to the user. With things like the Breeze iconset, enhancements to the sidebar, and improved menus “this is a very special and exciting release.”
-
CMS
-
It sparked a heated debate. At that point, Open Source Software (OSS) wasn’t as widely received in the enterprise as it is today and many thought that its perceived advantage was limited to price (as in “it’s free software”).
-
Business
-
Openwashing
-
SAP SE is dedicated to helping businesses respond to market demands around the clock, according to Steve Lucas, president of Platform Solutions at SAP. Its partnership with Red Hat, Inc. is a key part of its strategy. In an interview with theCUBE at RedHat Summit, Lucas explained further.
-
Recently, Apple released its programming language, Swift 2, to the public. By releasing Swift to the open source community, Apple is giving software developers more access to and control over the programming language. This release opens up a myriad of exciting possibilities for application development, software advancements and increased functionality.
-
Project Releases
-
Powerful video editor Shotcut has been updated again by its developers, and they’ve made some huge improvements to the application. To be fair, pretty much any update for Shotcut is impressive, but this one is an important one.
-
Public Services/Government
-
The European Commission is about to make available as open source a prototype of LEOS, a software solution for drafting and automatic processing of legal texts. The software currently supports legal texts issued by the EC, yet can be extended to support other legislative processes.
-
Openness/Sharing
-
Film producer James Cameron has announced that his innovative rotating Sun Flower design will be freely available to the public.
-
-
Hardware
-
Thomas told Business Insider that in late 2013, after analyzing his budgets, he realized that keeping his own computers simply wasn’t a good idea.
-
Defence/Police/Secrecy/Aggression
-
She endorses using cluster bombs, toxic agents and nuclear weapons in US war theaters. She calls them deterrents that “keep the peace.” She was one of only six Democrat senators opposed to blocking deployment of untested missile defense systems – first-strike weapons entirely for offense.
-
From 1964 to 1973, the US dropped two million tons of bombs on Laos. The horrendous effects are still being felt.
-
Environment/Energy/Wildlife
-
Finance
-
It is great news for majority of Ecuadorian citizens – but terrible nightmare for the ‘elites’.
They no longer feel unique, no longer is this country their huge, private playground and a milking cow. The ‘elites’ still have money and their villas, as well as servants, luxury cars and regular trips to those lands they are faithfully serving – North America and Europe.
But their status is diminishing. No longer they feel admired, no longer they are feared. Increasingly they are forced to play by rules and to respect local laws. That would be unimaginable just ten years ago. For some, this is the end of the world!
The rich, the ‘elites’, are sour losers. In fact, they have no idea how to accept defeat. Never before in the history of this country they actually had to. To them this is new reality, this nation ruled by the government, which is working on behalf of the people. The ‘elites’ feel let down, cheated, even humiliated. They have no idea how to respect democracy (rule of the people). They only know how to make decisions, and to give orders, and to loot.
This could lead to inevitable conflict, and Ecuador is not an exception. To greater or smaller extend, the same is happening in Venezuela, Bolivia, Brazil, Argentina, Uruguay and even in Chile. Immediately after people vote a socialist government in, immediately after the government begins working for the majority, the elites start reacting. Their goal is clear and predictable: to discredit the administration and to reverse the course.
-
After securing a ‘no’ vote at Greek referendum on bailout, Finance Minister Yanis Varoufakis resigned, saying it would help Prime Minister Alexis Tsipras negotiate a better deal with foreign creditors.
-
So from 2010 to 2015, Greece has cut government spending from roughly 13 billion euros to 10 billion euros–a cut of 23 percent. Unsurprisingly, this has had a devastating effect on Greece’s economy, with unemployment stuck above 25 percent since the end of 2012.
In the Washington Post‘s eyes, though, Greece has not yet demonstrated the willingness to “trim its spending” that would merit a bailout.
-
I think the lesson from this is that the 21st Century corporate and banking state is beyond amelioration. Any change needs to be a fundamental challenge to the system. It will seem strange to future generations that a system developed whereby middlemen who facilitated real economic transactions by handling currency, came to dominate the world by creating a mathematical nexus of currency that bore no meaningful relationship to real movements of commodities.
-
Censorship
-
Reddit has been on a very rocky road lately, and now some of the site’s users are demanding that CEO Ellen Pao be replaced. The petition to remove Pao follows the CEO’s decision to remove popular Reddit employee Victoria Taylor.
-
More than 130,000 people have signed a petition demanding the removal of Ellen Pao, Reddit Inc.’s interim chief executive officer, after she dismissed an executive and was accused of censoring online message boards.
-
Privacy
-
Every time anyone uses a computer to send an e-mail, watch a video, do a Google search, or update a Facebook status, the National Security Agency (NSA) is probably collecting and collating that activity on one of its many servers.
XKEYSCORE — the codename of the computer code used by the NSA to perform these actions — is massive and more intrusive than most people understand.
-
On Sunday, while most of Twitter was watching the Women’s World Cup – an amazing game from start to finish – one of the world’s most notorious security firms was being hacked.
-
Imagine you are the target of a phishing attack: Someone sends you an email attachment containing malware. Your email service provider shares the attachment with the government, so that others can configure their computer systems to spot similar attacks. The next day, your provider gets a call. It’s the Department of Homeland Security (DHS), and they’re curious. The malware appears to be from Turkey. Why, DHS wants to know, might someone in Turkey be interested in attacking you? So, would your email company please share all your emails with the government? Knowing more about you, investigators might better understand the attack.
-
Social media sites such as Twitter and YouTube would be required to report videos and other content posted by suspected terrorists to federal authorities under legislation approved this past week by the Senate Intelligence Committee.
The measure, contained in the 2016 intelligence authorization, which still has to be voted on by the full Senate, is an effort to help intelligence and law enforcement officials detect threats from the Islamic State and other terrorist groups.
-
Civil Rights
-
The FBI, Drug Enforcement Administration and U.S. Army have all bought controversial software that allows users to take remote control of suspects’ computers, recording their calls, emails, keystrokes and even activating their cameras, according to internal documents hacked from the software’s Italian manufacturer.
-
Internet/Net Neutrality
-
EU officials jubilantly announced a deal on setting internet rules and ending roaming surcharges early Tuesday morning but the details of the deal contain several loose ends.
-
Remarkably, this buyout of cyberspace has garnered almost no protest or media attention, in contrast to every other development in cyberspace such as the Communications Decency Act, and cyberporn. What hasn’t been discussed is the public’s right to free speech in cyberspace. What is obvious is that speech in cyberspace will not be free if we allow big business to control every square inch of the Net.
-
Intellectual Monopolies
-
Copyrights
-
Israeli Internet providers are no longer required to block access to Popcorn Time websites. A District Court has lifted a preliminary injunction arguing that access restrictions are ineffective. The decision is a major disappointment for the local anti-piracy outfit ZIRA, which was also ordered to pay the legal fees of one of the ISPs.
Permalink
 Send this to a friend
Send this to a friend
07.06.15
Posted in Site News at 5:53 am by Dr. Roy Schestowitz

Summary: Kyocera is again being targeted by Microsoft, using patent aggression, with a secret settlement being reached whose negative impact on Android remains to be seen
AS LONGTIME readers may recall, back in 2007 Microsoft picked Kyocera for its anti-Linux patent campaign, leading us to years of research and protests, even when Kyocera adopted Android, only to be sued by Microsoft earlier this year (with ‘partners’ like these, who needs enemies?). Kyocera is not “just peanuts”; despite not being so well known in Western nations, this is a company with 68,185 employees (not much smaller than Microsoft, which is still on the process of shrinking based on what I privately get told by Microsoft staff).
“Kyocera is not allowed to speak about what Microsoft did to it, for that might damage Microsoft’s reputation or harm Microsoft’s future efforts to blackmail other companies using patents.”US News has this new article titled “Microsoft Seeks a Comeback – But Is It Too Late?” The article alleges that Microsoft is falling way behind Google/Android/Linux. No wonder Microsoft is has been in layoffs mode for half a decade or so, with pace of layoffs increasing over time. Microsoft is now relying more and more on patents; Kyocera is a victim again, as this time it actually fought in court (unlike that time in 2007 where it just bent over).
According to Tech Times, there has just been a secret settlement with all details unknown. Kyocera is not allowed to speak about what Microsoft did to it, for that might damage Microsoft’s reputation or harm Microsoft’s future efforts to blackmail other companies using patents.
“A few months ago,” Tech Times wrote, “Microsoft filed a lawsuit against Kyocera, claiming that three Android smartphones from the Japanese company violated seven Microsoft patents. The smartphones in question were the Duraforce (pictured), Brigadier and Hydro. The patents, meanwhile, cover a wide range of mobile technologies that Microsoft alleged the Android devices violated.
“Microsoft has dozens of licensing agreements in place with Android OEMs, including Samsung, but it will not back out of a litigation if it doesn’t reach an amicable agreement. Microsoft went after Kyocera in March, asking a Seattle court for a U.S. sales ban on the three phones that infringed its patents.”
Microsoft is euphemistically calling racketeering “Technology Sharing Agreement” in its short press release. To quote the Microsoft press release: “In addition to strengthening the partnership between the two companies, it also resolves a patent-infringement lawsuit brought earlier this year in U.S. District Court. The remaining details of the agreement are confidential.”
The words “strengthening the partnership” serve to insinuate that Microsoft uses patent pressure (and rising litigation costs) to coerce Kyocera into becoming Microsoft’s vassal, just as Microsoft did to Samsung shortly before suing Kyocera (March 2015).
The Samsung settlement had conditions from Microsoft, essentially turning Samsung’s Android devices into “Microsoft Android” devices (this has actually been confirmed since the settlement, after mere speculations and rumours). So, there is nothing peaceful about it. This is blackmail. The loaded gun of the Mafia in this case is a pile of patents, usually software patents.
Tech Times does not cover any of this, but the report concludes with: “It remains unclear, however, just how much Kyocera will pay to use Microsoft’s patents.”
So it is possible that Microsoft got Kyocera to pay Microsoft for Android and also preinstall Microsoft malware on future Kyocera handsets. How nice of Microsoft… what a peaceful company.
Looking for any additional takes on this, we only found a proponent of software patents (“AmeriKat”) commenting poorly in a lawyers’ blog. Remarking on these attacks on Android, he wrote that “Kyocera follows Barnes and Noble, Foxconn, Invetec and Samsung in the line of companies that have recently settled with Microsoft.”
“It’s about Microsoft forcing companies to turn to Windows or “Microsoft Android”, making malware with surveillance (spyware) mandatory installed apps.”It’s hardly a settlement. It’s extortion. Microsoft essentially killed Barnes and Noble by tilting it in Windows’ direction in exchange for a so-called ‘settlement’ (we wrote a lot about this) and Samsung did this in exchange for becoming courier of Microsoft rather than an Android company. Kyocera may turn out to be just more of the same. It’s about Microsoft forcing companies to turn to Windows or “Microsoft Android”, making malware with surveillance (spyware) mandatory installed apps.
Curiously enough, in China (where many Microsoft bits of software are now officially banned for use by government agencies) Samsung is now facing a lawsuit over installed apps. We may safely assume that since Samsung agreed to preinstall Microsoft malware on many of its devices (after patent extortion) the Chinese government won’t be too happy. To quote the Shanghai Daily, “Shanghai Consumer Rights Protection Commission yesterday formally announced it has taken legal action against manufacturers Samsung and Oppo over their practice of pre-installing apps on their smartphones.
“The Shanghai No. 1 Intermediate People’s Court said on Wednesday it had accepted separate cases against Tianjin Samsung Telecommunications Technology Co Ltd and Guangdong Oppo Mobile Telecommunications Co Ltd.
“We may safely assume that since Samsung agreed to preinstall Microsoft malware on many of its devices, the Chinese government won’t be too happy.”“Tao Ailian, secretary-general of the commission, said it filed the public interest lawsuits after investigating complaints from the public about unwanted apps.
“In a study of 20 smartphones, the commission found several that were sold with apps already installed, many of which could not be removed. It also claimed that some phones “stole” cellular data.”
For many users of Galaxy devices, Microsoft malware is clearly “unwanted apps”, so maybe the Shanghai Consumer Rights Protection Commission should also go after Microsoft, both for racketeering, for bundling, and maybe also for mass surveillance, for which it is most notorious (far worse than Google). █
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- 2017: Latest Year That the Unitary Patent (UPC) is Still Stuck in a Limbo
The issues associated with the UPC, especially in light of ongoing negotiations of Britain's exit from the EU, remain too big a barrier to any implementation this year (and probably future years too)
- Links 7/1/2017: Linux 4.9.1, Wine 2.0 RC4
Links for the day
- India Keeps Rejecting Software Patents in Spite of Pressure From Large Foreign Multinationals
India's resilience in the face of incredible pressure to allow software patents is essential for the success of India's growing software industry and more effort is needed to thwart corporate colonisation through patents in India itself
- Links 6/1/2017: Irssi 1.0.0, KaOS 2017.01 Released
Links for the day
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA