05.14.15
Links 15/5/2015: Skrooge Releases, Linux 3.14.42, Linux 3.10.78
![]()
Contents
GNU/Linux
-
An Unlikely Ambassador
I would consider myself an unlikely Linux ambassador. Not that I hide any Linux use or fascination but that I am not out there on a mission to encourage or convert people to Linux. Mostly it would be an occasional conversation about me using Linux for something or a conversation where I am explaining that there are more operating systems then just Windows or OS X. Most of the time my Linux conversations are with those that already have some connection to Linux. To be honest I have probably been a much bigger “Ambassador” to LibreOffice than to Linux; and I am not an uber LibreOffice or ODF fan boy but one that believes for most basic users it will work just fine without all the Microsoft expense. All of that has taken a slight detour within the past couple of weeks.
-
Desktop
-
HP is Putin Ubuntu Linux on Russian computers
Some Windows partners, such as Dell, offer Linux-based operating systems as an alternative, but this is few and far between. HP, however, is planing to sell machines in Russia running the Ubuntu operating system. I suppose you could say the company is Putin (puttin’) Linux on the desktop there!
-
Legacy Modernization Applications for Linux
Like many companies, your company may depend on Linux for its main operating system. For nearly a quarter century, Linux has been pivotal for organizations all over the world. While it definitely comes with a number of benefits, it’s important to remember that any system built on Linux is still susceptible to old age. After enough time, your software could even become obsolete. According to Gartner, for example, the average data center is nine years old. However, after seven years, Gartner says that these data centers begin becoming outmoded. This helps illustrate why legacy modernization is such a vital process to carry out regularly.
-
Terminal Emulation Applications for Linux
-
-
Kernel Space
-
Linux 3.14.42
I’m announcing the release of the 3.14.42 kernel.
-
Linux 3.10.78
-
Four Remote Packet-of-Death Vulnerabilities In The Linux Kernel
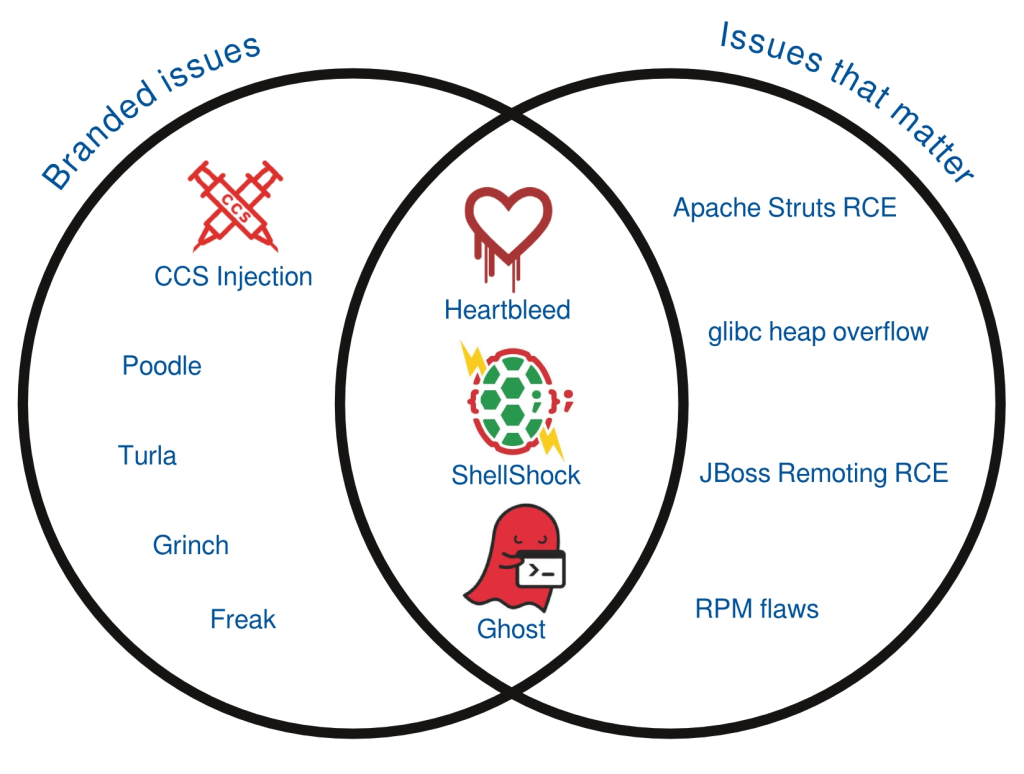
Just this morning the major VENOM security vulnerability was made public while a few hours later, a kernel developer has gone public with four “remote packet of death” vulnerabilities affecting a mainline Linux kernel WLAN driver.
-
Graphics Stack
-
First Point Release of Mozilla Firefox 38.0 Patches Nvidia Optimus Crash
After only two days from the announcement of Firefox 38.0, Mozilla pushed the first point release of the web browser to users worldwide via the built-in updater.
-
-
-
Applications
-
Camicri Cube Server: An Offline And Portable Package Manager For Debian, Ubuntu, And Linux Mint
As we all know, we must have an Internet connection in our Linux system for downloading and installing applications, right? Yes of course! But wait, what are you going to do if you don’t have an Internet connection, or the Internet connection is dead slow? This will be definitely a headache while downloading and installing packages in your Linux desktop using slow Internet connection.
-
Instructionals/Technical
-
Games
-
Our Linux Game Release Calendar Is Now Live
I’ve worked over the last few days in my coding cave to bring a new feature, a release calendar for Linux games!
-
Arduboy Could Spark Retro Gaming Revolution
Arduboy, a new pocket-sized 8-bit game device, has ignited a firestorm of interest on Kickstarter. With 27 days to go, the campaign already has drawn contributions of more than eight times its modest $25k goal.
-
Lethal League launched on Mac & Linux – Added secret playable character
-
Players can now play together and against their friends and foes on Windows PC, Mac or Linux in any combination
-
-
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Skrooge 1.12.0 released
The Skrooge Team announces the release 1.12.0 version of its popular Personal Finances Manager based on KDE Frameworks.
-
Skrooge 2.0.0 Beta available
The Skrooge Team announces the availability of 1.99.75 version of its popular Personal Finances Manager based on KDE Frameworks. This is a Beta version intended for users willing to help us by testing the KF5 port before the final Release.
-
Simple Qt container optimization you should do on your code
Most of us know we shouldn’t let our containers detach. QList, QVector, QString, etc. are implicitly shared. Copying them is cheap, but when we call a non const member function it will detach and trigger a deep copy.
-
Qt 5.5 Now Plans To Ship At The End Of June
Qt 5.5 has been running behind schedule for some time while now The Qt Company is trying to get it back on track and to officially ship Qt 5.5 by the end of next month.
-
-
GNOME Desktop/GTK
-
GNOME Asia 2015 impressio
I must to congrat all the enthusiasm and effort from many young students supported by experienced people, leaded by Estu Fardani. There are lots of Linux users in Indonesia and I saw the willing to contribute with the GNOME project. I met Estu in person and I found more friendly local people: my new dear friend Deetah, Harris, Utian, Aris, Kukuh, Fahmi, Moco, Pico, Siska, Lenin & the awsome Sendy!
-
GNOME 3.16.2 released
The second update of GNOME 3.16 is out with many bug fixes, documentation improvements, translations updates, and more. We hope you’ll like it.
-
GNOME 3.16.2 Released
GNOME 3.16.2 was announced this afternoon by Red Hat’s Matthias Clasen. The GNOME 3.16.2 release contains numerous bug fixes, documentation updates, translation updates, and other minor work. GNOME 3.16.2 release information can be found via this mailing list post.
-
Orca Open Source Screen Reader Receives Major Update for GNOME 3.16.2
We reported earlier this week that the hard-working developers behind the acclaimed GNOME desktop environment used by default in numerous GNU/Linux distributions, including Ubuntu GNOME and Fedora, are preparing the second and last point release of GNOME 3.16.
-
GNOME Shell and Mutter Get Minor Updates for GNOME 3.16.2
The GNOME Project has just announced the general availability of the GNOME 3.16.2 desktop environment, the second and last maintenance release of the 3.16 series.
-
-
-
Distributions
-
The death of Foresight Linux
There are many different Linux distributions, and some last for longer periods of time than others. Foresight Linux is a distribution that has finally reached the end of the road, and will no longer be developed.
-
Reviews
-
First Look at Manjaro Linux with elementary OS’ Beautiful Pantheon Desktop
Today, we take a closer look at a brand-new edition of the popular Arch Linux-based Manjaro operating system, Manjaro Pantheon, created by a member of the Manjaro community by the name of Stefano Capitani.
-
-
New Releases
-
ConnochaetOS 14.1 is released
I’m happy to announce the release of ConnochaetOS 14.1.
-
-
Red Hat Family
-
Red Hat Wins SIIA Software CODiE Awards for Best Cloud Management Solution and Best Open Source Innovation
Red Hat CloudForms and Red Hat Enterprise Linux 7 Earn Prestigious Industry Recognition
-
Fedora
-
The One Problem I Have So Far With Fedora’s DNF Package Manager
There’s one gripe I continue to have with DNF but at least it doesn’t mean the end of the world… DNF is mostly a drop-in replacement to the Yum command and when calling yum on Fedora 22 it will end up redirecting to dnf. One of the few exceptions though to where DNF is a drop-in replacement for Yum is supporting the –skip-broken argument.
-
Fedora 21 vs. Fedora 22 Benchmarks
For those curious how the performance of Fedora 22 is shaking out, here’s some early benchmarks comparing the Fedora Workstation 21 and Fedora Workstation 22 (with all updates as of the final freeze) in various workloads.
Plenty of Fedora 22 benchmarks are in the works now that this Red Hat backed Linux distribution is gearing up for release and has settled down with its many changes and new features. The Fedora 22 state tested was with the Linux 4.0.2 kernel, GNOME Shell 3.16.1, Mesa 10.5.4, and GCC 5.1.1 while using an EXT4 file-system. On the same exact Intel ultrabook, Fedora 21 was also re-benchmarked both in stock form and with all available updates as of 12 May.
-
-
-
Debian Family
-
Debian-Based Univention Corporate Server 4.0-2 Brings Docker Integration
Univention, through Maren Abatielos, had the great pleasure of informing Softpedia about the immediate availability for download of the second point release of their Debian-based Univention Corporate Server 4.0 Linux operating system.
-
Derivatives
-
Canonical/Ubuntu
-
Samsung takes on Ubuntu Core with MIPS32 Arduino-compliant Artik IoT platform
SAMSUNG HAS ANNOUNCED the Artik 1 MIPS32-based Internet of Things (IoT)-sympathetic motherboard.
The dual-core processor, powered by two MIPS microAptiv cores in a high-low 250MHz/80MHz configuration, also includes Bluetooth Smart (LE), flash storage and a crypto-engine.
-
Canonical Will Keep Linux Kernel 3.19 Alive for Ubuntu 15.04 Until July 2016
Today, May 13, we report that the Ubuntu Kernel Team, through Kamal Mostafa, is proud to announce that they will keep the 3.19 kernel branch alive for one more year, until July 2016, especially for their Ubuntu 15.04 operating system.
-
Ubuntu Touch Devel to Move to Wily Werewolf Base Soon
The stable branch of the Ubuntu Touch operating system is currently based on Ubuntu 14.10, but it’s about to move to Ubuntu 15.04. That means the development version of the mobile operating system is about to switch to Ubuntu 15.10.
-
Canonical Closes Libtasn1 Vulnerability in Ubuntu 15.04
Canonical has revealed details about a Libtasn1 vulnerability that has been found and fixed in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS and Ubuntu 12.04 operating systems.
-
-
-
-
-
Devices/Embedded
-
Mouser adds to open source board sales channel
The distributor’s Open Source Hardware Technology website now has an updated product selector which allows users to select a board from 30 different parameters including processor type and speed, memory and expansion capabilities, wireless and wired networking, user interface options, video connectivity.
-
CHIP: $9 Linux ‘micro-computer’ hits $1m Kickstarter funding in four days
THE CHIP ‘MICRO-COMPUTER’ that costs just $9 (£5.85) has reached over $1m in funding just four days after arriving on Kickstarter.
-
Raspberry Pi Model B+ price cut to just $25
The Raspberry Pi B+, which was previously priced at $35, has had its price cut to just $25. The price cuts have already gone into effect on the primary Raspberry Pi stockist websites: RS Components in the UK (£16) and MCM Electronics in the US ($25).
According to Raspberry Pi, the price reduction was made possible by “production optimizations,” though no specifics were given. At first glance, there don’t appear to be any board- or component-level changes, though Raspberry Pi might not have updated its product images yet.
-
Phones
-
Tizen
-
Samsung India and MSME Ministry to Launch Tizen Development Courses
Samsung India have teamed up with union micro, small and medium enterprises ministry on Wednesday to open MSME-Samsung Digital Academy, which will offer courses to train young developers in the fine art of Tizen application development. We have already seen Tizen on the Samsung Z1 Smartphone, Samsung 2015 range of TVs and there is more to come.
-
Moneycontrol Markets Tizen app for the Samsung Z1
Use the application to get real time stock quotes on BSE and NSE, Sensex, Nifty, and other Indian and Global market Indices, manage and keep track of your investment portfolio, watch CNBC-TV18, CNBC AWAAZ, CNBC Prime HD and CNBC Bajar Live and get in-depth coverage & analysis of financial markets, economy and business.
-
-
Android
-
Nexus 4 & Nexus 5 Android 5.1.1 Release Details Emerge
The Nexus 4 Android 5.1.1 update is confirmed, the Nexus 6 Android 5.1.1 update is confirmed and the Nexus 5 Android 5.1.1 release is imminent.
-
Galaxy S6 and S6 Edge Android 5.1 update coming in June?
Samsung did a pretty good job updating its flagship devices to Lollipop, but with Google moving the goal posts by releasing Android 5.1, the Korean giant found itself playing OTA catch-up once again.
-
Android 5.0 Lollipop update for Samsung Galaxy Note 2, Galaxy S4 Spark on Sprint rolls out
Sprint is giving its Galaxy S4 Spark and Note 2 customers some Android 5.0 Lollipop loving after recently releasing the said update last May 8.
-
Android M Might Be Unveiled At Google I/O: Here Are Some Features To Expect
-
Google’s Android-for-all program comes to Europe
Google’s bid to democratize Android just reached Europe. The internet giant has announced that Turkey will get its first Android One smartphone, the General Mobile 4G, on May 15th. The device is strictly middling given its 5-inch 720p display, Snapdragon 410 processor, 13-megapixel rear camera and 5-megapixel front cam, but it will be the first Android One device to offer LTE. It’s fairly affordable, too, at about $263 contract-free. There’s no mention of where Google’s initiative will go next, but the company hints that Turkey might not be the last European nation to get an Android One phone — you may eventually find one sitting in a shop near you.
-
2 easy ways to child-proof your Android or iOS device
-
Livescribe’s Android app is now available for all to download
-
Android 5.1 Lollipop Update Arrival For Galaxy S6 And Galaxy S6 Edge Confirmed: Find Out When Will It Arrive
The Samsung Galaxy S6 and the Galaxy S6 Edge are shipped with Android 5.0.2 Lollipop out of the box, but both S6 models are poised to receive the most recent Android 5.1 Lollipop upgrade in the next month, Canadian carrier Rogers’ Community Forums page reveals.
-
Nexus 5 Should Get Android 5.1.1 (LMY48B) Any Time Now, According To Sprint
We’ve seen Android 5.1.1 roll out to the Nexus 9, the aging Nexus 10, and the underwhelming Nexus Player. Now it looks like the latest version of Android is ready to come to phones.
-
AT&T Rolls Out Android 5.0.2 Lollipop Update For Galaxy Tab S 10.5
Similar to other Android Lollipop updates, AT&T will be releasing the over-the-air package in stages. As such, users will have to wait a bit more to finally receive the update in their tablets, ranging from a wait of a few days to perhaps as long as a couple of weeks.
-
The best gallery app alternatives for Android
You take a lot of pictures with your smartphone. Whether it’s a top-of-the-line shooter like the Galaxy S6 or a middle-of-the-road device it’s always at the ready for that photogenic moment.
-
Sprint Says Nexus 5 is Getting Android 5.1.1 “LMY48B” Update This Week
According to Sprint support, the Nexus 5 is set to receive an update this week to Android 5.1.1 build LMY48B (Sprint says it was supposed to start May 11). The update is listed as being nothing more than the update to 5.1.1 with included “security enhancements.” Tough to say what those security enhancements are, but in general, the update is expected to be quite minor.
-
Great deals: 3 top-shelf Android phones are cheaper than ever right now
One of the great things about top Android smartphones is that the older they get, the more affordable they become, since newer models come along and retailers start cutting the price of the older handsets. So if you’re not really interested in buying one of the latest Android flagships available in stores right now, you can always look for a better deal a top-shelf model that’s a year old or even just a few months old.
-
Nexus 4 Android 5.1.1 Release: What to Expect
The Nexus 4 Android 5.1.1 update is confirmed which means that owners of the aging former flagship should be making the jump from Android 5.1 Lollipop soon. With that in mind, we take a look at what you can expect from Google and its Nexus 4 Android 5.1.1 release.
-
Moto E (2nd Gen) 4G LTE Now Receiving Update to Android 5.1
It looks like Moto E (2nd Gen) 4G LTE owners are in for a treat today, as Motorola appears to be pushing out an update to Android 5.1. The update is arriving on phones as build 23.11.15, which is the same version we first outed a week ago when we pointed out the fact that Motorola was on the verge of unleashing a wave of 5.1 updates to a variety of devices.
-
Samsung Galaxy S6 And S6 Edge Expected To Receive Android 5.1 Update In June
According to an OS Upgrade report published by Canadian phone company Rogers Wireless, the Samsung Galaxy S6 and Samsung Galaxy S6 Edge smartphones are expected to receive the Android 5.1 software update next month. Since Rogers Wireless is expecting an Android 5.1 update before the end of June, it means many other phone carriers will also likely offer the upgrade around the same time or earlier.
-
Meerkat for Android is out of beta on Google Play
Meerkat has not only beaten its Twitter-owned rival Periscope to Android devices, it’s also shed its Beta phase according to a Tweet published Wednesday. The Meerkat for Android live streaming video apps operates just as its iOS counterpart does, allowing users to share real-time feeds with their Twitter followers. Conversely, Periscope’s Android debut is still coming “soon! We’re working on it,” per a post on the app’s blog published April 1st.
-
iPad, Android users get images support for Google Docs and Slides
Last week I was stuck with an iPad to do some pending work. I was traveling and my laptop broke leaving me with my Nexus 6 and an iPad. That’s when I realized that Google Docs for iPad was in a sorry state (actually the whole iPad experience was extremely poor compared to Android, I will write about it some time later).
-
Google Releases Open Source Game Sample Utilizing Google Fit and Android Wear
Google has released Games in Motion, an open source game sample to demonstrate how developers can make games using Google Fit and Android Wear.
-
How I use Android: Android VP Brian Rakowski
-
-
-
Free Software/Open Source
-
In Free Software, it’s okay to be imperfect, as long as you’re open and honest about it
In the FOSS world, people seem more likely to really see the person, not just the community they belong to. And from a person, they expect that they really and honestly feel sorry if they made a mistake. And they seem to be more forgiving if a FOSS contributor admits a mistake and apologizes than if a proprietary software company does. It’s not only individuals, though. It seems like even companies in the FOSS field are expected to be more open and honest than those in the proprietary software field.
-
Free Software and Free Culture: Open Source’s Influence on Society
In an age when Microsoft (MSFT) is floating the idea of open-sourcing even Windows, it’s clear that open source has pretty much conquered the world of software—or the parts of it that matter, at least. But, in a lot of ways, the weight of open source is now extending into many other realms, defining how people interact and collaborate well beyond the context of computers. That’s a fascinating issue, and it gives the key to understanding what could be the ultimate legacy of the free and open source software movements.
-
5 open source remakes of classic PC games you won’t want to miss
Buying the latest games will typically get you top-quality graphics and an iTunes-ready soundtrack, but that won’t necessarily translate into compelling gameplay. And even if it does, there’s no guarantee you’ll be kept entertained for more than a few hours. The solution? Try one of these open source takes on classic PC games.
Sure, the graphics won’t be as good. There is no chance you’ll want to download the soundtrack, and there will probably be odd glitches and bugs here and there. But, you can be sure the central concept will be great (it’s what inspired the remake in the first place). It’ll have been developed by people who love it, rather than just because they want your cash. And as, in most cases, the projects are still evolving — with new features, content, missions, expansion packs — you’ll want to keep playing for a long, long time.
-
Google stomps on scammers — and helps open source
A recent rules change to Google Adwords may make it easier for open source projects to protect their good reputation
-
Cloud Security Alliance, Waverley Labs Collaborate On Open-Source Software-Defined Perimeter Spec
The Cloud Security Alliance (CSA), a group that promotes security best practices for cloud computing, is making progress on its plans to develop a software-defined perimeter (SDP) framework for protecting Internet-connected systems against a range of security threats.
-
Web Browsers
-
Mozilla
-
Letter To Mozilla
We are a group of Free Software advocates from Melbourne Australia and supporters of the Mozilla Foundation and its goals. While we would usually hold Mozilla in high esteem, on this International Day Against DRM we feel compelled to join the FSF and Defective By Design in condemning Mozilla’s decision to include proprietary mechanisms (Encrypted Media Extensions) in Firefox.
We understand that you are trying to do what makes content owners comfortable lest they not allow their content on your browser; you have outlined this in the article “DRM and the Challenge of Serving Users”. However it seems that your focus is on the short term, compromising your values to retain existing users, rather than protecting them in the longer term. That article significantly neglects any mention of the harms caused by such proprietary technologies, and how they lead users to inflict this harm upon themselves.
-
FREE Firefox?
The challenge is, going from the Firefox start page, find a way to download the FREE version, without using external websites (so no Google search).
-
-
-
SaaS/Big Data
-
Nexenta Extends Its Market Leadership in Open Source-driven Software-Defined Storage at OpenStack Summit; End-to-End Integration Into OpenStack Framework
-
Pentaho ignites Apache Spark orchestration
Orlando-based open source analytics company Pentaho is ‘in the process of being acquired’ by Hitachi Data Systems, but the brand appears strong enough to be retained 100% intact inside of the new parent company.
-
How to become a valued OpenStack contributor
Most PTL’s are elected because they are the most technical contributor on a particular project. They are rarely elected for leadership skills. Most of our top technical contributors struggle with leadership, and naturally shy away from it. This frequently leads to dysfunction in community dynamics, as the PTL continues to focus on contributing at a very high level, and puts limited effort into leadership work. Doing things like setting project vision, tracking and celebrating milestones, providing team members with actionable feedback, and sharing the project vision with community members outside the project are all good ways of exhibiting leadership. Doing those things as a part time effort can yield limited results in terms of team unity, and effectiveness. My suggestion to open source project leaders is to earmark considerable time for leadership work, and scale back direct contribution work. A well empowered, motivated, and effective team can produce much more velocity than a PTL individually focused on strong contribution, and ignoring leadership responsibilities in order to do it.
-
-
CMS
-
Open source a clear choice for CMS development
As time went on, we simply continued to ride the open source path. We assembled a huge collection of functional applications we had built for client sites that could be added to and modified for new ones. Shopping carts, contact forms, opt-in email list managers, employment opportunity listings, content editors, slide shows, all built as open source using PHP.
A few years later came the emergence of Content Management Systems, which contained—as a package—many of the functional elements we previously had relied upon our own resources to create. Drupal, Joomla!, WordPress, and others were emerging as the default new development platforms for most digital agencies who had followed the same path as ours.
-
-
FSF/FSFE/GNU/SFLC
-
Free Software Foundation announces deputy director search
The Free Software Foundation (FSF), a Boston-based 501(c)(3) charity with a worldwide mission to protect freedoms critical to the computer-using public, would love to find an experienced, Boston-based deputy director to expand our leadership team.
-
-
Licensing
-
Linux Foundation Updates SPDX Compliance Effort
Back in 2010, the Linux Foundation first launched its Software Package Data Exchange (SPDX) effort that helps to build out and identify software components in a standardized manner. Since then, use of SPDX has grown, and on May 12 the SPDX 2.0 specification was announced. The new specification aims to be even more comprehensive in helping organizations understand the open-source licenses that are used as part of an application deployment.
-
-
Openness/Sharing
-
Open Source Project Hopes To Offer $23,000 EV With 186 Miles Range
An open source project is currently in the works to build an electric vehicle powered by in-wheel motors.
The goals are ambitious: 1) Build an electric vehicle with a minimum range of 186 miles that can theoretically be put into production and sold for under $22,700. 2) Share the design so that others can replicate or customize the platform. 3) Do it all in less than a year.
-
Leftovers
-
Hardware
-
SSDs have a problem: They’re getting too fast, too soon
SSD performance is outstripping interfaces faster than standards bodies can make them
-
Death and the unplugged SSD: How much you really need to worry about data retention
The word is out: Your SSD won’t retain your data forever when you unplug it. Yup, you’ll never be able to go on vacation again without toting your SSD along. It’s incapable of surviving for two weeks without you, poor thing.
-
-
Security
-
Security advisories for Wednesday
-
GPU could be the next hacker target
The new Windows malware, which is intended as a demonstration, is called WIN_JELLY and acts as a Remote Access Tool or Trojan (RAT)
-
Whistleblower Claims Cybersecurity Company Generated Fake Data Breaches To Sell Protective Services
Tiversa would allegedly turn over “information” about these fake breaches to the FTC and push the agency to come down hard on the companies who refused to hire it. Once the FTC started asking questions, Tiversa would again approach these companies and ask them if they’d reconsidered the use of their services.
-
-
Defence/Police/Secrecy/Aggression
-
The Jeb Bush Adviser Who Should Scare You
Paul Wolfowitz not only championed the Iraq War—he obsessively promoted a bizarre conspiracy theory.
-
Ignorance and attempts to rewrite WWII history – that’s what makes me sick
Everybody in this country is perfectly aware of the fact that we were allies with the British, the French, and of course, the Americans whom we gloriously linked-up with on the River Elbe in April 1945. But we also remember how from the very beginning, in 1939, the West was hoping to orient Hitler to the East and make the German socialists and the Russian communists kill each other. Yes, Moscow did get tons of American supplies under the Lend-Lease Act passed in 1941, and the Northern convoys to Murmansk were a manifestation of real heroism by the Royal Navy. We also cherish the memory of the French Normandie-Niemen air squadron and Le Resistance, but the Russians will never forget that we had to suffer three long years, until our brothers in arms finally landed in Normandy in 1944. That reduced the distance between D-day and VE-Day for them to just 10 months, while for the Russians it was 46 long months of war… For the first time since 1941 Moscow really celebrated Victory on March, 26, 1944 – the day the Soviet troops crossed the River Prut and recaptured the state border. By the time the allies crossed the Channel three months later the Red Army had started its victorious march across Europe, liberating Romania, Hungary, Bulgaria, Czechoslovakia, Austria and Norway. The heaviest price we paid during this operation was for ousting German troops from Poland: 600,000 Soviet soldiers were killed on Polish soil.
-
-
Transparency Reporting
-
Born Kneeling
Rusbridger and his extraordinary wig go on and on as a pretend opposition outlet, their reputation much dented by recent hysterical unionist output which exceeds the Daily Express. But Rusbridger’s continued usefulness to the establishment is not in doubt. The pose of publishing the most harmless of Prince Charles’ letters does little to help a threadbare disguise.
-
-
Censorship
-
David Cameron to unveil new limits on extremists’ activities in Queen’s speech
A counter-terrorism bill including plans for extremism disruption orders designed to restrict those trying to radicalise young people is to be included in the Queen’s speech, David Cameron will tell the national security council on Wednesday.
The orders, the product of an extremism task force set up by the prime minister, were proposed during the last parliament in March, but were largely vetoed by the Liberal Democrats on the grounds of free speech. They were subsequently revived in the Conservative manifesto.
-
-
Privacy
-
[tor-relays] Please enable IPv6 on your relay!
-
Exposure to ideologically diverse news and opinion on Facebook
Exposure to news, opinion and civic information increasingly occurs through social media. How do these online networks influence exposure to perspectives that cut across ideological lines? Using de-identified data, we examined how 10.1 million U.S. Facebook users interact with socially shared news. We directly measured ideological homophily in friend networks, and examine the extent to which heterogeneous friends could potentially expose individuals to cross-cutting content. We then quantified the extent to which individuals encounter comparatively more or less diverse content while interacting via Facebook’s algorithmically ranked News Feed, and further studied users’ choices to click through to ideologically discordant content. Compared to algorithmic ranking, individuals’ choices about what to consume had a stronger effect limiting exposure to cross-cutting content.
-
NSA’s Loudest Defenders Have Financial Ties to NSA Contractors
The Intercept’s Lee Fang has highlighted a few examples of loud National Security Agency allies that have financial ties to the agency and mass surveillance. The list includes Stewart Baker, the general counsel to the NSA from 1992 through 1994, Fox News military analyst Jack Keane, Retired General Wesley Clark, former Central Intelligence Agency chief James Woolsey, former Republican National Committee chair Jim Gilmore, former NSA director Mike McConnell, and Center for Strategic and International Studies President John Hamre. They have surfaced regularly in the media to denounce Snowden, and in the case of Woolsey, to call for Snowden to be “hanged by his neck”.
-
Many of the NSA’s Loudest Defenders Have Financial Ties to NSA Contractors
Due to the secretive nature of the agency’s work, NSA contracts are often shielded from public disclosure, and identifying financial links between pundits and the agency’s web of partners is tricky. But the work of journalists and whistleblowers such as James Bamford, who was assigned to an NSA unit while serving in the Navy, gives us a sense of which companies work for U.S. intelligence agencies. Drawing largely from these disclosures, The Intercept has identified several former government and military officials whose voices have shaped the public discourse around government spying and surveillance issues but whose financial ties to NSA contractors have received little attention. These pundits have played a key role in the public debate as the White House and the agency itself have struggled to defend the most controversial spying programs revealed by Snowden’s documents.
-
House votes overwhelmingly to end NSA’s mass collection of phone records
The House overwhelmingly passed a bipartisan bill Wednesday to dial back the once-secret National Security Agency program that collects and stores data from nearly every landline or cellphone call dialed or received in the United States.
-
Senator Bob Corker Says NSA Should Be Spying On More Americans, Not Fewer
Senator Bob Corker, who heads the Senate Foreign Relations Committee, appears to now be calling for the NSA to spy on more Americans, rather than fewer, arguing that the metadata collection program that is currently being debated in Congress is so small that he considers it negligent.
-
Corker calls NSA surveillance program shockingly small
Senate Foreign Relations Committee Chairman Bob Corker said Wednesday he was shocked to learn this week how little data the National Security Agency is actually amassing in its controversial collection of Americans’ phone records.
-
The NSA’s Call Record Program, a 9/11 Hijacker, and the Failure of Bulk Collection
The fact is, U.S. intelligence agencies knew of al-Mihdhar long before 9/11 and had the ability find him. In the years, months, and days before 9/11, the NSA already had access to a massive database of Americans’ call records. Analysts—at NSA or CIA—could have easily searched the database for calls made from the U.S. to the safehouse in Yemen. They simply didn’t.
-
-
Civil Rights
-
U.S. marshal involved in road rage incident in South County
A U.S. marshal was among four people cited for assault in an apparent case of road rage Sunday, authorities said.
A man who was involved in the incident told a TV reporter that it began with a honk and moved to a parking lot, where a man in another vehicle approached him holding a gun and punched him in the face with it.
-
-
Internet/Net Neutrality
-
Cable Industry Tries To Distance Itself From Decades Of Poor Service By Eliminating The Word ‘Cable’
Annoyance with the cable industry appears to have reached the tipping point, with consumers fed up with skyrocketing prices, inflexible programming options and some of the worst customer service in any U.S. industry. The cable industry’s ingenious solution? Stop using the word cable. Last week, the cable industry held its annual trade conference, previously dubbed “The Cable Show.” Trying to distance itself from the aging, negative associations with the word “cable,” the industry has decided to rename the conference The Internet & Television Expo.
-


















 Content is available under CC-BY-SA
Content is available under CC-BY-SA