04.10.15
Posted in Europe, Patents at 4:20 am by Dr. Roy Schestowitz

Summary: Article from Le Monde translated into English
THE French article which was mentioned the other day is attempting to be balanced by speaking to the Frenchman Battistelli and French proponents of software patents, UPC etc. (Michel Barnier for example). While we can find some factual errors and glaring omissions in the article or the way certain things are framed, it does introduce some interesting observations, some of which are new.
Someone has provided us with an English translation of the article and we can now present it in full (translation making it fair use):
A ‘so good’ office
The European Patent Office (EPO) looks like a happy world, which like any happiness, is appreciated but until now was hidden. Who knows this international organisation? For nearly forty years it has recorded the patents filed by businesses in Europe and it employs 7,000 people, mostly based in the headquarters in Munich, Germany, and at Ryswick, a suburb of The Hague in
the Netherlands. Many employees of all nationalities, quietly being pampered, are receiving higher wages and more benefits than even the unionists of this modern Babel and feel favorable.
Yet behind its peaceful facade, another reality is now described from the inside. Poisoned atmosphere, staff at the edge of a nervous breakdown, monitored, marked, pressurised, subjected to productivity goals which are always higher. Recalcitrants are summoned by the security officers to take their goods in the hour and are accompanied under escort to the exit. And some come to extreme gestures. A 55-year-old man was tied up by some colleagues because he was banging his head against a wall. Another one was scarifying himself.
More dramatic late March, a German committed suicide in a public garden in the Bavarian capital. He was on sick leave for depression and had spoken with friends about his apprehension as to achieve productivity goals. July 8, 2013, a Belgian officer threw himself out of the window of his office in The Hague. Two other employees, one French and one German, committed suicide at their Munich home. Before ending his days in May 2012, the French had requested a transfer, because he felt harassed by his superior. The German, who had criticised the attitude of the management in managing the distress of this colleague was immediately suspended and expelled from the premises. He committed suicide Sept. 3, 2014, the day he received a convocation from the Disciplinary Committee.
In this context of extreme tension, slings and arrows started. The daily life of the Office is punctuated by strikes (22 days in 2014) and demonstrations. “Social relationships are very bad,” said one employee who, like all the others, requested anonymity. The main union of the house, SUEPO (an acronym which stands for Staff Union of the European Patent Office), to which almost half of employees are members, accuses Benoît Battistelli, the president appointed in 2010 and renewed in 2014. The French would abuse a principle inscribed since the beginning in the statutes of Office: legal immunity.
“Authoritarian drift”
The EPO was born in 1977 from an agreement signed by the States of the European Community, has been extended to the Union of Twenty-Eight and afterwards to other countries, from Switzerland to the Balkans, to count today [as many as] 38 members. Like most international organisations, the EPO has a status of extraterritoriality. It has its own rules on taxation, social security,
pension or labor law. It does not depend on national justice. The only legal recourse is the Arbitral Tribunal of the International Labour Organisation (ILO). “This immunity is a fundamental condition of functioning and independence, explains Benoît Battistelli. We are present in five countries and are counting many nationalities among our employees. What law should apply to them?”
Until then, the organisation knew how to cuddle highly qualified staff, mostly made up of PhDs and engineers from leading schools. Brain boxes [were] able to examine in German, English, French, the three official languages, and patent applications filed by the laboratories of Siemens, Philips, Samsung and others. Aces were able to detect flaws or “borrowings” from competitors in technical documents that can reach 200 pages. Starting Salary: 5000 euros per month, taxable at 6%, plus expatriation bonuses. The salaries can reach 15,000 euros in late career for 40 hours per week and three months of vacation. The Office pays the medical expenses and education of children, including enrolment fees in the best American universities.
The EPO has a considerable operating budget, 2 billion euros, up 20% in five years, making it the largest European organisation, just after the Brussels Commission. Companies around the world come to register their inventions: 274,000 applications in 2014, again rising steadily. The Office finances itself with the examination fee and the annual fees paid by the patents’ applicants.
Listening to SUEPO, this economic and legal independence has yet been perverted by the arrival of Benoît Battistelli, a technocrat of 64 years formed at the french “École nationale d’administration”. The new boss would succumb to an “authoritarian drift” and to “dictatorial tactics”. It would be surrounded by an inner circle at his sole devotion, formed almost entirely of French individuals coming like him from the National Intellectual Property Institute (INPI). Benoît Battistelli would have transformed the tenth floor of the Munich headquarters, by means of a stylish and expensive renovation, in a fortress from which he rules the institution.
To denounce the colleagues
Still, according to its detractors, the management uses and abuses an “investigation unit” which, for each site, is responsible for investigating breaches. In the German headquarters, this internal police has been called… the Stasi. A document gives obligation to the employees to collaborate with this investigation unit and to denounce the faults of others, under penalty of sanctions. “There were more disciplinary procedures in the past two years than in the previous thirty years,” complained a staff representative.
The counterweights for the presidency, provided by the statutes, were gradually eliminated, continues SUEPO. The union was expelled from the EPO premises in November 2014. “We had eight days to pack up”. The right to strike was limited: it is subject to a complex procedure and the president may oppose to it by requisition. Several staff representatives, unprotected, are under penalty of sanctions for having supported colleagues.
“We are aware that our salaries are more than decent. But from which income level the human rights do not apply anymore?” asks a Munich employee.
Recently, a judge of the Board of appeal – which handles appeals of rejected patent – was suspended and forcibly thrown out. He is suspected of having slandered anonymously a member of management, the Croat Zeljko Topic, referring to corruption cases that would affect him in his country. But the judge is in principle independent. His colleagues protested collectively to the President against what they consider an abuse of power.
“Fantasies”
“A wall of silence reigns now in this organization,” agrees Philip Cordery, socialist member of parliament of French abroad. “People who are working at the EPO inform me regularly of their malaise. There is a clear abuse of the extraterritorial status which does not mean impunity”.
Lengthily, methodically, Benoît Battistelli refutes attacks on him. He even agreed to entrust Le Monde his contract and discloses his salary, “around 250,000 euros per year.” He denounced the “fantasies” for caricaturing the Office into a Banana Republic. “The EPO is the victim of a two years campaign to undermine the integrity and honesty of its leaders.” He and
his entourage received anonymous letters, sometimes accompanied by swastikas. He declares himself as a victim of a cabal just because he wanted to clarify the roles of everybody, to introduce formal rules, when the organization used to be a de facto joint management. He denounced “racist attacks” against his Croatian deputy. To use suicides against him would fall under bad procedure: “I am deeply shocked by attempts to exploit these tragedies. This subject is too serious for lending itself to controversy”. He ensures that “the investigation unit acts independently”.
The President has the support of the Administrative Council, comprised of representatives from 38 states. He was reappointed unanimously in 2014. Benoît Battistelli was mandated to make the institution more productive and more competitive against the competition of other offices worldwide. EPO procedures are three times more expensive than its US counterpart, even though, because of the precision of the work, the patents it grants are twenty times less often attacked in the courts. “We have to adapt our way of working, our regulatory framework to allow the agency to ensure its future,” he says. And that future is called “Unitary European patent”, a simplified procedure whose objective is “to make innovation cheaper and easier for companies,” said Michel Barnier, former European Commissioner for Internal Market and Services. “We want to make these savings at the expense of staff of the office,” retorted a trade unionist.
SUEPO multiplied complaints before national courts. “But we meet with the principle of immunity,” says Amélie Lefebvre, which represents the union in France. The Hague Court of Appeal has however driven a wedge in a judgment delivered on 17 February. The judges ruled that the immunity was “disproportionate” and did not guarantee “the protection of fundamental rights”. They even estimated their decision applicable elsewhere in Europe.
The Government of the Netherlands, fearing that this decision makes ]changes to] some other similar organisations on its territory, immediately condemned this decision and refused to run it. The case takes a politic turn. Philip Cordery sent letters to the European Commission or to the Directorate General of the ILO, relaying concerns of the staff. Member of parliament Pierre-Yves Le BORGN’ and Senator Jean-Yves Leconte, other socialist representatives of French abroad, called out successive ministers of economy, to no avail so far. Elsewhere, some parliamentarians of Italy, the Netherlands, Luxembourg, Poland and Cyprus have launched similar initiatives.
At the last board of the EPO, on 25 and 26 of March, discordant voices were heard and a Communiqué called for a “resumption of social dialogue”. Not sure that this attempt at conciliation will be enough to appease encysted hatreds. The violence of the mail exchanges between the president and SUEPO proves that between these two there is a death struggle.
Any corrections to this translation should be reported to us to ensure accuracy. █
Permalink
 Send this to a friend
Send this to a friend
04.09.15
Posted in News Roundup at 7:00 pm by Dr. Roy Schestowitz

Contents
-
A few years ago NCR took a fresh look at ATM operations. Cloud computing was becoming more powerful and NCR decided that banks could achieve significant efficiency by moving to a thin client ATM. It chose Android as its first operating operating system but may consider others in the future.
-
You might not think of Dell as a big name in tablets — not on the level of, say, Apple or Samsung. In fact, though, the once-stodgy PC maker sells one of our favorite Android tabs, the Venue 8 7000, which won a Best of CES award and earned a strong score of 84 in our review. Now, the company is back with a 10-inch edition (the Venue 10), and it’s basically a blown-up version of the original, just with some improved ergonomics.
-
-
On Monday, April 20, the Linux Users’ Group of Davis will offer a presentation on KDE Connect, software that lets a phone and computer easily share files, control each other and more.
For example, users can receive their phone notifications on their computer, use their phone as a remote control for their desktop, and easily share photos and other files between devices without using cables.
-
The Instagram account of Snoop Dogg is a mishmash of ideas and various aspects of the artist’s life, but it’s also a personal account. This is where he decided to post a screenshot from a game (GTA IV most probably) of him using a Linux-powered laptop.
-
Desktop
-
Dell announced recently that a new edition of its XPS 13 Ultrabook is now available for purchase on the company’s website, designed especially for developers.
-
The Large Hadron Collider at CERN has been restarted after a two-year hiatus, and it looks like some of the researchers are using Ubuntu and a whole lot of other Linux-related props.
-
Server
-
-
HP has invested billions in its cloud offerings. Now, out of the blue sky, HP is leaving the public cloud business behind.
-
Partnership Enables Stronger DevOps Practices so Companies Can Deploy Applications Faster While Reducing Errors
-
Cumulus Networks, home of a Linux-of-choice for white-box switches, has linked arms with Puppet Labs and joined its Puppet Supported Program.
While it’s “just another” certification from one angle, Puppet’s Carl Caum told The Register it’s important to the company.
He said while there are plenty of tools to manage equipment in the software-defined networks (SDN) space, these pieces of software can only work via the equipment vendors’ APIs – the networking devices themselves remain black boxes.
-
Dell and Red Hat have announced an enhanced edition of the Dell Red Hat Cloud Solution, a co-engineered, enterprise-grade private-cloud solution based on OpenStack. We’ve covered the OpenStack-focused alliance between the two powerful companies before, and the announcement is one of several from Red Hat this week. Working with Red Hat, Dell is effectively becoming an OEM for Red Hat’s software solutions.
-
Converting a dead Xbox 360 to a Linux server is not as difficult as it seems, especially if you only use the case of the console. It’s still a nice try, and it will make a nice addition to the living room.
-
Kernel Space
-
Canonical, through John Johansen, announced today, April 8, that new kernel updates for the Ubuntu 14.04 LTS (Trusty Tahr) and Ubuntu 12.04 LTS (Precise Pangolin) are available to users via the default software repositories of the respective distributions.
-
The Linux Foundation, the nonprofit organization dedicated to accelerating the growth of Linux and collaborative development, today announced it will host the Internet Security Research Group (ISRG) and its Let’s Encrypt project, a free, automated and open security certificate authority for the public’s benefit. Let’s Encrypt allows website owners to obtain security certificates within minutes, enabling a safer web experience for all.
-
The Linux Foundation will now host the Internet Security Research Group and its Let’s Encrypt platform, which provides secure, open SSL encryption for websites.
-
As part of an effort to make encryption a standard component of every application, the Linux Foundation launched its open source Let’s Encrypt project along with its intention to provide access to a free certificate management service.
-
The Linux Foundation is to host an open encryption project aimed at providing a free and easy way to protect the huge amount of data passed over the internet every day.
This data includes usernames and passwords, credit card data, cookies, and other types of sensitive or personal information.
-
The Linux Foundation is lending support to the Let’s Encrypt project, to make it both free and simple for any Web server to encrypt connections
-
The Linux Foundation has lined up financial support for a group producing an easier way to encrypt Web site and mobile device traffic.
-
-
Open Source Encryption For Everyone [Ed: but to make encryption work one must use it on top of a Free software stack]
This version of the software is designed for Windows desktop computers, but further versions for other operating systems and mobile devices are in the pipeline. The research team is also working on various add-ons, including one that supports ad hoc encryption.
-
Graphics Stack
-
After almost two years of the X.Org Foundation’s Board of Directors pursuing a merger with SPI, the 2015 X.Org Elections have ended and the results were sent out to X.Org members last night.
-
While AMD has yet to make the Catalyst 15.3 Beta Linux graphics driver available for download from their web-site, they released the driver to Canonical and as such this new AMD Linux driver has been available in Ubuntu 15.04 for a few weeks. Canonical is now back-porting this proprietary driver back into Ubuntu 14.04 LTS Trusty Tahr.
-
Applications
-
Plasma 5 is about to become part of the mainstream Linux distributions, and we are getting more and more feedback about this new platform. This blog post is a reaction to this increasing feedback from our users.
Plasma5 introduces the KDE Frameworks 5 platform (or KF5) which uses Qt5 as it’s foundation. This new platform aims to replace the legacy KDE4 platform, which was mainly the old monolithic kdelibs. More and more applications got ported to this new platform. Just stay tuned with the next release announcement, which is imminent. However, some applications, and among them some important ones, are not yet ported to the KF5 platform. And this brings on, or more appropriately reminds, the coinstalability matter.
-
Andrea Scarpino announced today, April 8, that the Choqok instant messenger application used by default in the KDE desktop environment is about to be ported to the KDE Frameworks 5 infrastructures.
-
Of course, for popular bugzilla fields we should make sure the command line tool has an explicit and document option, but this takes the pressure off of us to add an option for every custom Red Hat extension.
-
-
Instructionals/Technical
-
-
-
-
-
-
-
-
-
-
-
The Linux Learner Bundle is a crash course in Linux for beginners and you can learn Linux in just 5 days and we have the Linux Learner Bundle for just $49 a saving of 91% off the normal retail price of $601 in the Geeky Gadgets Deals store.
-
Games
-
Aside from demonstrating that Linux CAN be used for gaming, SteamOS will have another great advantage for the Linux gaming community: it will bring a lot of casual gamers that will be looking for a different experience into the world of Linux. This move should increase the percentage of Linux gamers enough to make PC gamers curious, and game developers willing to take a leap of faith and create games for Linux as well.
-
OpenTTD, an open source simulation game based on the popular Microprose title Transport Tycoon written by Chris Sawyer, has been upgraded once more and the developers have added a number of features and important.
-
I have been waiting rather impatiently for this, as the initial Linux release of Chivalry: Medieval Warfare contained many crash to desktop bugs.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
A Calligra developer wrote an interesting post on his blog informing users about the progress made on porting the KDE’s number one office suite to the next-generation KDE Frameworks 5 and Qt 5 technologies that are being used in the KDE Plasma 5 desktop environment.
-
Last month, in March, with the 2.9.0 release done, we Calligra developers followed our plans and started a branch named “frameworks”, to work on version 3.0, to be the first version based on Qt5 and KDE Frameworks 5. Calligra 3.0 should not see any new features, the focus is purely on getting the port to the new platform done without any regressions.
-
The great team of developers behind the KDE Project met in February 2015 in the Blue Systems office in Barcelona, Spain, to discuss and plan the upcoming features that will be implemented in the highly anticipated KDE Plasma 5.3 release.
-
-
New Releases
-
Every revolution starts with a small step. Semplice 7 is ours.
-
Eugenio Paolantonio announced on April 8, 2015, the immediate availability for download of his Semplice 7 Linux operating system, a Debian Sid-based distribution powered by the latest Linux 3.19.3 kernel and built around the Openbox window manager.
-
Evolve OS recently changed its name to Solus and the developers are now trying to put some order into the normal chaos that surrounds most of the distros. They intend to have a precise schedule and to work on several important features.
-
Bella OS is a beautiful and user friendly 64bit Linux desktop operating system.
Launch release version 2.2 is now live!
-
Screenshots
-
Arch Family
-
The Manjaro Linux development team announced a few days ago that a new update is available for its stable operating systems, Manjaro Linux 0.8.12, bringing all sorts of improvements and the latest versions of pre-installed components.
-
A few days ago, Manjaro Linux developer Philip Müller informed all Manjaro users that the SSL (Secure Sockets Layer) certificate of their manjaro.org website where the Wiki and Forum of the project are hosted has expired and that they forgot to update it in time to not create any accessibility issues.
-
Red Hat Family
-
Open Source software developer Red Hat (RHT) is hosting its annual North American Partner Conference this week in Orlando, where more than 350 partners are gathered to hear company executives discuss the past fiscal year and to learn more about what is in store for resellers in 2015.
-
Red Hat senior manager, Colin McCabe, has laid out the opportunities and possibilities businesses should consider when deciding on implementing and open source solutions.
“Open source is a great fit for any organisation that is looking to innovate more rapidly and effectively, and to save costs and increase the bottom line,” he said.
“At Red Hat, we’ve been working for over two decades to maintain the open source model. It’s in Red Hat’s DNA to unravel complex technology challenges ranging from Cloud applications to content management using open source solutions. Red Hat is part of different open source communities and works on a variety of projects.
-
Red Hat, Inc. (NYSE: RHT), the world’s leading provider of open source solutions, today announced the winners of its annual Red Hat North American Partner Awards. The winners were announced last night at an event held during the Red Hat North American Partner Conference in Orlando, Fla.
-
Fedora
-
While Fedora developers did a good job getting out the Fedora 22 Alpha on time, the beta release of Fedora 22 will come at least one week late.
At today’s Go/No-Go meeting it was decided F22 Beta isn’t ready to ship next week but will have to be delayed by one week at least to take care of unresolved blocker bugs. This beta delay pushes back all future F22 milestones — including the release of F22 final expected to take place in May.
-
Debian Family
-
The Debian Project Leader electsions are going on. This is the yearly election for the leader, where members of the project vote for a new leader for a year. The debate this year seemed to me to be quite quiet, and voting activity seems to not be very high, either. Pity. Many years ago, the election period used to be quite energetic, bringing up some quite good viewpoints.
-
Derivatives
-
Canonical/Ubuntu
-
digiKam is an Open-Source project Photos management software, specially for KDE but you can use it on Ubuntu or others distros too. In digiKam photos are organized in albums which can be sorted chronologically, by folder layout or by custom collections. Developers recently released digiKam 4.9.0 with 33 bug fixes. Developers main focus is on digiKam 5.0 release, as it is supposed to be a major release of digiKam.
-
We were recently informed by Željko Popivoda, the developer of the Linux AIO project that builds all sorts of Live DVDs with multiple editions of an operating system, that there’s an update for the Linux AIO Ubuntu Live DVD.
-
Canonical has a series of automated testing methods for Ubuntu Touch which helps them weed out most of the bugs and problems before publishing updates for the operating system, and now they have set up a new lab that should find apps that are draining the battery.
-
I work as a systems administrator and frequently write and speak about my work in that role. My current position is with HP on the OpenStack Project Infrastructure where we maintain dozens of static systems that developers interface with for their work on OpenStack and a fleet of hundreds of worker servers that run all of the tests that are done against the code before it’s merged. This infrastructure is fully open source, with all of our system configurations, Puppet tooling and projects we used available via git here. Since I have a passion for both systems administration and open source, it’s been quite the dream job for me as I work with colleagues from around the world, across several companies.
-
Details about a Libtasn1 vulnerability that was affecting Ubuntu 14.10, Ubuntu 14.04 LTS, Ubuntu 12.04 LTS, and Ubuntu 10.04 LTS have been published in a security notice by Canonical.
-
Canonical has been talking about convergence for a while now, but it’s still difficult to explain it to new users without some visual aid. A new video has been posted showing the Ubuntu web browser, an application developed initially for the phone OS, running in the desktop edition Ubuntu 15.04.
-
ZaReason and System76 have each launched Intel NUC style mini-PCs running Ubuntu on 5th Gen. Intel Core “Broadwell” processors, starting at about $500.
-
The Ubuntu MX4 is yet to receive an official price or release date, but our opening impressions of it are very positive.
Featuring a premium design, innovative operating system, and decent internal specifications the MX4 looks like a great smartphone.
We also have to praise Canonical for the great work it’s done over the past year to improve Ubuntu mobile’s stability and performance, and can’t wait to test the OS more thoroughly.
-
Flavours and Variants
-
Gabriele Martina announced on April 8 the immediate availability for download of the SalentOS 14.04.2 Linux distribution based on the upstream Ubuntu 14.04.2 LTS (Trusty Tahr) operating system from Canonical.
-
After a successful release of Linux Mint 17 ‘Qiana’ and Linux Mint 17.1 ‘Rebecca’ here is a preparation for another successful release Linux Mint 17.2. On April, 8 Clem posted news on blog.linuxmint.com saying the next release Linux Mint 17.2 has been codenamed ‘Rafaela’. Here is what Rafaela means. Tell us Is it religious?
-
Recently, the developers have announced that Linux Mint 17.2 (based on Ubuntu Trusty) will be named “Rafaela”, the tradition being to use feminine names. The codenames of major releases use the next letter, from the alphabet, while the point releases’ names start all with the same letter.
-
-
At IDF Shenzhen, Intel announced plans for a rugged IoT version of the Intel Atom x3 SoC, with built in cellular radios, and both Linux and Android support.
At the Intel Development Forum (IDF) in Shenzhen, China, Intel announced a future Internet of Things version of its new Atom x3 (Sofia) system-on-chips, some of which are built by China-based Rockchip. Intel announced the Atom x3 at Mobile World Congress in early March along with the more powerful, 14nm fabricated “Cherry Trail-T” Atoms, the Atom x5 and x7.
-
Phones
-
Tizen
-
We were overjoyed to see a high profile messaging app like WhatsApp available on the Tizen Store at launch for the Samsung Z1. Now it seems the WhatsApp Android App, which used Open Mobile’s ACL technology to run on Tizen, has served its purpose and a Native App has launched today with WhatsApp Messenger being replaced.
-
Currys electronics, a UK online and In-store retailer has now got the Tizen based Samsung 2015 TV range In stock and available to buy right now!!! It seems it is only the larger branches that currently have some stock of the UE65JS9000 65″ at £3,999 and UE55JS9000 55″ at £3,099.
-
Have you ever passed your phone to someone for them to use, only to see them going through your private pictures? This is something that seems more common in the Indian sub-continent and it is VERY annoying. To the rescue we have the SecretVault App that allows you to easily hide your pictures, Videos, Audios, and any other files that you do not want others to see.
-
Android
-
It usually takes months for mobile devices to get Android updates, but Intel and Google want to slash the wait time.
Tablets and smartphones made as part of a new Intel mobile-device development program will be able to receive new Android versions and features in two weeks via over-the-air upgrades.
-
-
-
Reviews of Tim’s Apple Watch are pouring in, mixing like oil and water. Most reviewers agree that Apple’s new shiny timepiece isn’t fully perfected. That being said, the chief contention among reviews relate to degree and magnitude of imperfection. In other words, many reviewers can’t agree on (if or by) how much the Apple Watch sucks.
-
Apple has spared no opportunity to advertise how customizable its debut smartwatch is, thanks to the promised number of bands wearers will be able to swap in and out. Unsurprisingly Google wants to take some of the wind out of those sails. The company has taken this moment to highlight a set of straps available for various Android Wear devices from the likes of Clockwork Synergy, E3 Supply Co., and Worn & Wound.
-
The Apple Watch hits stores in just two weeks, and based on the reviews, it’s both an impressive bit of modern technology and a beautiful piece of jewelry. But the Apple Watch isn’t the only smartwatch on the market.
Apple’s nemesis, Google, already has its own watch operating system, Android Wear, and companies like Samsung, LG, and Motorola make smartwatches that run it. What’s more, these Google watches are less expensive than the Apple Watch and come in a host of different styles.
-
The Android 5.1 Lollipop update for the Nexus 5 is finally starting to roll out to additional owners of the smartphone almost a month after being initially announced by Google.
-
As previously announced, Sony has started pushing Android Lollipop out to Xperia Z2 and Z2 tablet devices all over the world. These updates are going out in phases and vary according to your region and carrier, so you still may have to exercise patience a bit longer.
-
As it turns out, Google has been listening to your feedback and has decided to reintroduce month view to its Calendar app. Since Google updated the Calendar app alongside the jump to Android 5.0 Lollipop, many users have been begging the company to bring back the month overview so they can see more events at one time.
-
A new Nexus 7 Android 5.1 update has been confirmed thanks to Google’s Android Open Source Project and it’s probably not the one that many Nexus 7 users were expecting.
-
-
While Sony is gearing up to release its fourth Xperia Z phone, some phablet fans are still sitting pretty with the original’s larger-than-life cousin, the Xperia Z Ultra. For those who opted to keep things pure, the GPe variant was the way to go. Fortunately, Google hasn’t forgotten about the largest phone to have been offered with stock Android, as the just a few days after Android 5.1 hit LG’s G Pad 8.3 GPe, it’s now time for the Z Ultra GPe to receive the latest Lollipop build.
-
Multitasking is great, but smartphones will never offer a multitasking experience on par with desktop devices because they just don’t have enough screen real estate. That doesn’t mean switching back and forth from app to app is the only way to go on mobile phones, however, and a great Android app called Flynx has come up with a simple and elegant solution that you really have to check out.
-
Mozilla announced Firefox for Android hit a big milestone today: 100 million downloads. The figure is confirmed on Google Play, where the app now shows the installs category is in the “100,000,000 – 500,000,000″ range.
-
For the longest time, Amazon enticed users to choose the Fire tablet with exclusive access to Prime Instant Video; despite the fact that Fire devices run a version of Android, purely Android tablets were denied the benefits of their modified brethren. Yesterday, though, that finally changed — Amazon unceremoniously made the Prime Instant Video app available to all Android tablets.
-
ScrollBack is a new, open source community management tool that offers the extensive reach of social media, the engagement and archival abilities of forums, and the interactive and real time experience of chat.
-
For those of you who are more “bah humbug” than “pass the eggnog”, Santa Tracker offers an online method of tracking Santa’s fictional progress through the logistical chore of stuffing soon-to-be-ignored amusing plastic tat down the chimneys of the world’s best-fed and most-privileged children.
-
Twenty years ago, open source was a cause. Ten years ago, it was the underdog. Today, it sits upon the Iron Throne ruling all it surveys. Software engineers now use open source frameworks, languages, and tools in almost all projects.
-
Many companies say they love open source, but what does that actually mean? Does it mean they use a lot of software other people have written? Does it mean they like that they don’t have to pay for things? Or do they understand that loving open source also means contributing back to the community the code came from?
-
Web Browsers
-
Chrome
-
High DPI screens are beginning to show in an increasing number of devices, and developers need to adjust their applications to support it. The Chromium developers have just added this feature for the Linux platform.
-
Databases
-
-
MariaDB has announced the Spring 2015 release of MariaDB Enterprise, which will include new scalability and security capabilities.
Research from Wikibon has predicted that the Big Data database market will reach $4.5 billion in 2017, which represents a large rise from $2.7bn in 2014. It is expected that SQP will represent 64% of the database market.
-
-
Google is dropping encryption into MariaDB, the fork of Oracle’s MySQL, to help shut out SQL injection attacks.
-
The MariaDB Enterprise Spring 2015 release introduces optimised server executables that are claimed to increase overall database performance by over 15 percent, as well as enhanced high availability and scalability on IBM’s Power8 server platform, and updates to the firm’s MaxScale database proxy tool to boost security.
-
CMS
-
The Git revision control system is “at the center” of Drupal’s hyper-collaborative community says Drupal core committer Angie Byron. The open source content management platform has 37,802 developers with Git commit access, and about 1,300 actively committing each month, she says.
-
Open source will remain the best way to achieve a better developer experience, and as it grows in popularity, engaging with neighbor technology will become easier. Reusing existing components and becoming more distributed will be less complex. Thanks to open source, developers are able to work faster and more efficiently, which is good for business. But this is just the beginning. Open source has taken the CMS development experience to a whole new level, and it doesn’t look like it’s slowing down anytime soon.
-
The Federal Bureau of Investigation issued an alert on April 7 about the potential danger of Islamic State (ISIS) terrorists abusing vulnerabilities in the open-source WordPress blog and content management system software.
-
Funding
-
Google has a program for their employees called 20% time that allows them to work on a side project one day a week. It’s how Carol Smith came to manage their Google Summer of Code (GSoC) program over 5 years ago. That, and learning about the job from the program manager at the time, Leslie Hawthorn, who later left Google in 2010, opening up the job for Smith.
-
BSD
-
DragonFlyBSD developers have updated their ACPI power management implementation against Intel’s ACPICA code as of yesterday.
With this commit pushed out today, it syncs the ACPICA code in the DragonFlyBSD kernel against Intel’s newest reference code. This contains the first part of upstream DragonFlyBSD support, the Windows 10 _OSI string was added, printf issue fixes, and other changes.
Details on the ACPI Component Architecture can be found at ACPICA.org.
-
Openness/Sharing
-
The Greek government has held a three-day public consultation on the re-opening of the public TV channel ERT. The consultation was opened on the national open government portal, opengov.gr, on March 9 and closed on March 12 at 10.00. In total, 583 comments were added by Greek citizens.
-
Security
-
A security flaw in New South Wales’ Internet voting system may have left as many as 66,000 votes vulnerable to interception and manipulation in a recent election, according to security researchers. Despite repeated assurances from the Electoral Commission that all Internet votes are “fully encrypted and safeguarded,” six days into online voting, Michigan Computer Science Professor J. Alex Halderman and University of Melbourne Research Fellow Vanessa Teague discovered a FREAK flaw that could allow an attacker to intercept votes and inject their own code to change those votes, all without leaving any trace of the manipulation. (FREAK stands for Factoring RSA Export Keys and refers to the exploitation of a weakness in the SSL/TLS protocol that allows attackers to force browsers to use weak encryption keys.) But instead of taking the researchers’ message to heart, officials instead attacked the messengers.
-
I figure 24 hours is about the amount of time it takes from a security patch to be released until weaponized exploits show up. After that, if you’re not patched, you’re living dangerously, depending on the nature of the bug. Bundling new features with a high risk of regression with security fixes means users wait to upgrade.
The iOS 8.3 update is 280MB. It can’t even be downloaded over the air, only via wifi. Security patches are important enough that they should always be made available separately. Then I could download them, even OTA, without fear of regression.
What aggravates me most is that this is business as usual. As always. We’re training people not to patch. Users should be embarrassed to admit they’re running unpatched software; instead it’s regarded as the prudent choice.
-
The certificate was issued by Google Internet Certificate Authority G2, which issues digital certificates for Google web sites and properties.
-
Experts have repeated conference data security warnings after it was revealed the personal details of thousands of conference delegates may have been leaked in Australia after a data breach.
-
Linux Australia had a bit of a nightmare Easter Weekend.
While the rest of us were loafing at the beach, the Penguinistas from Down Under were owning up to a pretty extensive cyberintrusion.
The team has published a decent document setting out what happened, and it went something like this:
Crooks broke into the organisation’s Conference Management server.
Crooks got root on the server.
Crooks installed a remote access Trojan (RAT) for later.
Crooks rebooted the server and activated the RAT.
Crooks “logged in” again and installed zombie malware, also known as a bot.
While the crooks had access, a conference database backup took place to the server.
Ironically, the backup that was intended to deliver one leg of the “security trinity” (availability) ended up hurting one of the other legs (confidentiality).
-
All your systems are Fedora 21, RHEL 7.1 or Ubuntu 14.02 all is working fine as the included SSSD is new enough to handle 2FA. All kerberized services can be used with 2FA w/o logging in again during the validity of your Kerberos ticket. Very convenient, very secure.
[...]
2FA works well, convenient and secure in a datacenter and office environment. Notebooks are fine as well as long as there is a network connection available. The mobile world (Smartphones and Tablets) is not yet ready for 2FA. Some issues can be worked around (with some drawbacks) while others render 2FA not usable at all (offline usage).
Hopefully there will be some smart solutions available for mobile usage soon, as mobile usage causes the most of the security headaches.
-
-
Defence/Police/Secrecy/Aggression
-
This is something out of Alice in Wonderland. The Islamic Republic of Iran, born in 1979, has not attacked another country. (With U.S. help, Iraq attacked Iran in 1980.) In contrast, Israel has attacked its Arab neighbors several times its founding, including two devastating invasions and a long occupation of Lebanon, not to mention repeated onslaughts in the Gaza Strip and the military occupation of the West Bank. Israel has also repeatedly threatened war against Iran and engaged in covert and proxy warfare, including the assassination of scientists. Even with Iran progressing toward a nuclear agreement, Israel (like the United States) continues to threaten Iran.
-
-
The former head of the CIA in Pakistan should be tried for murder and waging war against the country, a high court judge ruled on Tuesday.
Criminal charges against Jonathan Banks, the former CIA station chief in Islamabad, were ordered in relation to a December 2009 attack by a US drone which reportedly killed at least three people.
-
A Pakistani court on Tuesday ordered criminal charges to be filed against a former C.I.A. station chief and a former C.I.A. lawyer over a 2009 drone strike that killed two people.
-
As tons of desperately needed medical supplies await clearance to be flown into Yemen, aid workers warned Tuesday of an unfolding humanitarian crisis, saying at least 560 people, including dozens of children, have been killed, mostly in a Saudi-led air campaign and battles between Shiite rebels and forces loyal to the embattled president.
More than 1,700 people have been wounded and another 100,000 have fled their homes as fighting intensified over the past three weeks, the World Health Organization said.
-
The CIA’s drone base in the rippled surface of the Saudi Arabian desert has undergone major renovations over the past few years. Satellite imagery shows dozens of additions that appear to include living quarters, a new clamshell hangar for hiding aircraft and neat rows of freshly planted palm trees.
-
Last year, after concluding that many passages in the document “no longer merited secrecy,” the Second Circuit published a redacted version of the Justice Department’s July 2010 Office of Legal Council memo that approved the “targeted killing” of Anwar al-Aulaqi. The court’s view was that government officials had already disclosed much of the information they were trying to withhold. In speeches, media interviews, and congressional testimony, officials had acknowledged the government’s role in the strike that killed al-Aulaqi, explained the purported legal basis for the strike, and invoked still-secret OLC memos to reassure the public that the strike was lawful. Having done all of this, the court said, the government couldn’t plausibly claim that the entirety of the July 2010 memo was still secret, and it couldn’t lawfully withhold the entirety of the memo under the Freedom of Information Act.
From one perspective, the Second Circuit’s ruling was a victory for transparency. Human rights groups and media organizations had been calling for the release of the legal memos underlying the targeted-killing program; thanks to the Second Circuit’s ruling, one of those memos — arguably the most important one — was made public. From another perspective, the court’s ruling wasn’t very significant at all. The ruling didn’t expose secrets. By its own terms, it exposed facts and legal analysis that had already been disclosed.
-
Jameel Jaffer has a post on the government’s latest crazy-talk in the ongoing ACLU and NYT effort to liberate more drone memos. He describes how — in the government’s response to their appeal of the latest decisions on the Anwar al-Awlaki FOIA — the government claims the Court’s release of an OLC memo does not constitute official release of that memo. (Note, I wouldn’t be surprised if the government is making this claim in anticipation of orders to release torture pictures in ACLU’s torture FOIA suit that’s about to head to the 2nd Circuit.)
But there’s another interesting aspect of that brief. It provides heavily redacted discussion of the things Judge Colleen McMahon permitted the government to withhold. But it makes it clear that one of those things is a March 2002 OLC memo that offers different analysis about the assassination ban than the analysis used to kill Anwar al-Awlaki.
-
Transparency Reporting
-
The AMA saw Assange fielding questions alongside Sarah Harrison, Renata Avila and Andy Müller-Maguhn, who were all representing the Courage Foundation, an organization which runs the official defense funds of whistleblowers. Assange spoke of how he believes the NSA leaks impacted society and its relationship with the government, along with outlining his thoughts on how the public can help protect whistleblowers, and offering his opinion on whether or not the average Joe’s and Jane’s can have any influence on how the government operates in regards to the privacy of its citizens.
-
Environment/Energy/Wildlife
-
An oilfield near Gatwick airport could hold up to 100bn barrels of oil, according to a British exploration firm, in possibly the biggest onshore oil discovery in England since the 1980s.
UK Oil and Gas Investments revealed it had found a “world-class potential resource” after drilling 3,000ft below ground in West Sussex. However, UKOG said only 3-15% of the total would be recovered, based on similar finds in the US.
-
For union organizers in Colombia, the dangers of their trade were intensifying. When workers at the country’s largest independent oil company staged a strike in 2011, the Colombian military rounded them up at gunpoint and threatened violence if they failed to disband, according to human rights organizations. Similar intimidation tactics against the workers, say labor leaders, amounted to an everyday feature of life.
-
Finance
-
Hollywood moguls and the vast majority of leftist entertainers have joined forces in a last-ditch effort to bully wavering Democratic lawmakers into backing President Obama’s fast-track authority for the Trans-Pacific Partnership (TPP) as the centerpiece of what he calls his “pro-trade agenda.”
-
WikiLeaks did more than expose governmental eavesdropping and foreign policy blunders: A 2009 data dump is shedding new light on the spat between Delta, United, and American and the three largest Gulf carriers over government subsidies and Open Skies agreements.
The Business Travel Coalition, which backs retaining Open Skies agreements and is seeking to counter the U.S. carriers’ charges that Emirates, Qatar, and Etihad received $42 billion in unfair government subsidies, uncovered a U.S. congressional report, disclosed by WikiLeaks in 2009, that documents how U.S. aviation, including commercial airlines, the FAA, and airports, received $155 billion in federal direct spending from 1918 to 1998.
-
-
Last month I was asked to speak at a conference in the City of London on the ethical issues surrounding new payment systems. The audience was packed with people working on innovative things like payment apps for smart phones and ‘contactless payments,’ where you can just wave a card or a phone over a terminal.
Their new financial technologies are rapidly changing the way we pay for everything. This may be convenient, but as wand-waving and other high-tech alternatives to cash become the only ways to pay for anything, what happens if the wand loses its magic? What are the costs of becoming entirely dependent on technology in a cashless society?
[...]
This uncertainty is related to a second issue—that of anti-competitive practices. Visa and Mastercard already account for over 80 percent of the credit card market worldwide, and well over 90 per cent in many countries. The Financial Times refers to this situation as “a well-protected oligopoly” and so, for them, a good investment. Yet it also represents a hitherto unimaginable degree of control over the means of payment. Even if policies are adopted to diversify this market or—if that doesn’t work—to break up these oligopolies directly, such unprecedented levels of control raise a third area of concern in the form of peoples’ rights to privacy.
-
PR/AstroTurf/Lobbying
-
The proponents of the Trans-Pacific Partnership (TPP) are doing everything they can to try to push their case as they prepare for the fast-track vote before Congress this month. Roger Altman, a Wall Street investment banker and former Clinton administration Treasury official, weighed with a New York Times column, co-authored by Richard Haass, the president of the Council on Foreign Relations.
They begin by giving us three “myths”–all of which happen to be accurate depictions of reality. The first “myth” is that trade agreements have hurt US manufacturing workers and thereby the labor market more generally. Altman and Haas cite work by MIT economist David Autor showing that trade with China has reduced manufacturing employment by 21 percent, but then assert that the problem is trade not trade agreements.
-
Hillary Clinton is betting that if Stephanie Hannon can handle natural disasters, she can certainly handle a controversial presidential campaign.
Hannon, Google’s director or product management, has left the Internet giant to take over as the chief technology officer for Clinton’s still unannounced presidential campaign.
-
Hillary Clinton has hired Stephanie Hannon, Google’s director of product management for civic innovation and social impact, as chief technology officer for her potential presidential campaign, fueling accusations from Julian Assange that Google is in bed with the US government.
Privacy
-
The FBI wants to make us all less safe. At least that’s the implication from FBI director Jim Comey’s push to ban unbreakable encryption and deliberately weaken everyone’s security. And it’s past time that the White House makes its position clear once and for all.
Comey was back before Congress this week – this time in front of the House Appropriations Committee – imploring Congressmen to pass a law that would force tech companies to create a backdoor in any phone or communications tool that uses encryption.
-
A DEA official said, “Parallel construction is a law enforcement technique we use every day. It’s decades old, a bedrock concept.”
-
In a Chicago court, several Facebook users filed a class-action lawsuit against the social media giant for allegedly violating its users’ privacy rights to acquire the largest privately held stash of biometric face-recognition data in the world.
The court documents reveal claims that “Facebook began violating the Illinois Biometric Information Privacy Act (IBIPA) of 2008 in 2010, in a purported attempt to make the process of tagging friends easier.”
-
Have you been trying to convince friends and family to use encryption in light on the NSA revelations and had little success? Otr.to is a newly released web based chat client that requires no installation and offers OTR encryption via JavaScript libraries. With no installs necessary, sending encrypted messages to your least technical friends should be a lot less challenging.
-
Desjardins Insurance has launched a smartphone app that tracks driver behaviour in return for the promise of substantial savings on car insurance, the first of its type in Canada, the company says.
-
It’s been almost ten years since Laura Poitras’ name has been on the NSA Watch List. Every time she returns to her home country, security agents wait for her, somewhere between the gate of the plane and the US Immigration booth. They take her away to a room, confiscate her gear, her notebooks, and her videos. They question her and copy her hard drives. This has happened to her at least forty times since 2006.
-
Francesca Hogi, 40, had settled into her aisle seat for the flight from New York to London when the man assigned to the adjoining window seat arrived and refused to sit down. He said his religion prevented him from sitting beside a woman who was not his wife. Irritated but eager to get underway, she eventually agreed to move.
-
Comedy host John Oliver conducted an interview with National Security Agency whistleblower Edward Snowden in Moscow recently that was broadcast Sunday on his HBO show “Last Week Tonight with John Oliver.” In the process, Oliver exposed his solidarity with the American state and its vast, illegal spying operations. He took the opportunity of the conversation to come out harshly against Snowden’s decision to leak large quantities of NSA documents.
Pushing for a confession that his actions were potentially “harmful,” the British-born Oliver demanded to know whether Snowden had personally read every single document contained in the files that the former NSA employee transferred to journalists beginning in the summer of 2013.
“I have evaluated all of the documents that are in the archive. I do understand what I turned over,” Snowden replied.
“There’s a difference between understanding what’s in the documents and reading what’s in the documents. Because when you’re handing over thousands of NSA documents, the last thing you’d want to do is read them,” Oliver retorted sarcastically. He went on, “You have to own that. You’re giving documents with information that could be harmful.”
Oliver repeated the favored arguments of the Obama administration and intelligence establishment to the effect that the preservation of “national security” required the elimination of civil liberties, such as Fourth Amendment protections against arbitrary searches and seizures.
-
In about 10 days, Congress will take up cyber information sharing bills. And unlike past attempts, these bills are likely to pass.
That, in spite of the fact that no one has yet explained how they’ll make a significant difference in preventing hacks.
So I’m going to try to examine roughly one hack a day that immunized swift information sharing between the government and the private sector wouldn’t prevent.
-
Hundreds of thousands of travelers cross US borders every day. And none of them—save the precious few with diplomatic immunity—have any right to privacy, according to Department of Homeland Security documents recently obtained by MuckRock.
The US Department of Homeland Security’s (DHS) Privacy Impact Assessment for the Border Searches of Electronic Devices outlines the finer points of border officials’ authority to search the electronic devices of citizens and non-citizens alike crossing the US border. What becomes clear is that this authority has been broadly interpreted to mean that any device brought into or out of the country is subject to the highest level of scrutiny, even when there is no explicit probable cause.
Based upon little more than the opinion of a single US Customs and Border Patrol (CBP) officer, any device can be searched and its contents read. With approval from a supervisor, the device can be seized, its contents copied in full, or both.
-
Finally, we must briefly push back on Carrie’s statement that “changing FISA’s standard to a ‘significant purpose’ . . . has been overwhelmingly understood as an important substantive correction.” We may be traveling in somewhat different circles, but that hasn’t been our experience. Rather, among colleagues in our field, this change is widely viewed as the moment in which FISA became an existential threat to the Fourth Amendment’s warrant requirement in ordinary criminal cases. The “correction” that’s needed is to restore the primary purpose test.
-
I mention this because a lot of people seem concerned that the “cyber threat sharing” bills in congress (CISA/CISPA) will divulge private information to the NSA. This is nonsense. The issue is private information exposed to the FBI and other domestic agencies. It’s the FBI, ATF, or DEA that will come break down your door and arrest you, not the NSA.
-
Federal prosecutors have portrayed wealthy Mexican businessman José Susumo Azano Matsura as a supervillain who was always one step ahead of the law. For two decades, prosecutors said, federal agents investigated Azano for drug trafficking, money laundering, extortion and tax fraud to no avail before he was popped last year on charges he illegally donated to San Diego politicians.
But the relationship between Azano and the U.S. government is more complicated than the Justice Department has let on.
-
Trying to get a handle on hundreds of sensitive, closely held surveillance programs, a Senate committee is compiling a secret encyclopedia of American intelligence collection. It’s part of an effort to improve congressional oversight of the government’s sprawling global spying effort.
Sen. Dianne Feinstein launched the review in October 2013, after a leak by former National Security Agency systems administrator Edward Snowden disclosed that the NSA had been eavesdropping on German Chancellor Angela Merkel’s cellphone. Four months earlier, Snowden had revealed the existence of other programs that vacuumed up Americans’ and foreigners’ phone call records and electronic communications.
“We’re trying right now to look at every intelligence program,” Feinstein told The Associated Press. “There are hundreds of programs we have found … sprinkled all over. Many people in the departments don’t even know (they) are going on.”
Feinstein and other lawmakers say they were fully briefed about the most controversial programs leaked by Snowden, the NSA’s collection of American phone records and the agency’s access to U.S. tech company accounts in targeting foreigners through its PRISM program. Those programs are conducted under acts of Congress, supervised by a secret federal court.
-
A secretive U.S. Drug Enforcement Administration unit is funneling information from intelligence intercepts, wiretaps, informants and a massive database of telephone records to authorities across the nation to help them launch criminal investigations of Americans.
Although these cases rarely involve national security issues, documents reviewed by Reuters show that law enforcement agents have been directed to conceal how such investigations truly begin – not only from defense lawyers but also sometimes from prosecutors and judges.
-
The Baltimore Police Department has used secretive cellphone surveillance equipment 4,300 times and believes it is under orders by the U.S. government to withhold evidence from criminal trials and ignore subpoenas in cases where the device is used, a police detective testified Wednesday.
The unusual testimony in a criminal case marked a rare instance when details have been revealed about the surveillance devices, which the Obama administration has aggressively tried to keep secret. Citing security reasons, the government has intervened in routine state public-records cases and criminal trials, and has advised police not to disclose details.
-
He also details some of the over-inflated claims of other surveillance programs in the past — all of which were later shown to be false. But, the article doesn’t really attempt to answer the question — just raise it. In the past, we’ve noticed that the entire concept of a cost-benefit analysis seems antithetical to the way the surveillance state does business. But why is that?
-
Say what you will about the Baltimore PD and its cell tower spoofers (like… “It would rather let accused criminals go than violate its [bogus] non-disclosure agreement with the FBI…” or “It hides usage of these devices behind pen register/trap and trace warrants and then argues the two collection methods are really the same thing…”), but at least it’s making sure the hundreds of thousands of dollars it’s spent on the technology isn’t going to waste.
Civil Rights
-
On February 13, 2015, former Chicago Police Commander Jon G. Burge was released from federal custody, having served a little less than four years of his four-and-a-half year sentence for lying under oath about whether he tortured scores of African-American men during his time as commander. Less than a week before, I sat across from him in a small room in Tampa, Florida, questioning him, pursuant to a court order, yet again about his role in a torture case—this time, the case of Alonzo Smith, who was repeatedly suffocated with a plastic bag and beaten with a rubber nightstick in the basement of the Area 2 police station by two of Burge’s most violent henchmen after Burge informed him that they “would get him to talk, one way or another.”
-
The New York Times (4/7/15) released a video of a black South Carolina man Walter Scott being shot, casually and without apparent mercy, eight times in the back by white police officer Michael T. Slager. The media’s outrage after the video’s publication was righteous and swift. The state of South Carolina followed suit, filing murder charges against Slager. Indeed, the video offers no ambiguity whatsoever:
-
A white police officer in North Charleston, S.C., was charged with murder on Tuesday after a video surfaced showing him shooting in the back and killing an apparently unarmed black man while the man ran away.
The officer, Michael T. Slager, 33, said he had feared for his life because the man had taken his stun gun in a scuffle after a traffic stop on Saturday. A video, however, shows the officer firing eight times as the man, Walter L. Scott, 50, fled. The North Charleston mayor announced the state charges at a news conference Tuesday evening.
-
Bill O’Reilly cited debunked statistics to claim that more white than black Americans are killed by police officers in the wake of the fatal South Carolina police shooting of an unarmed black man.
A police officer was charged with murder in the shooting death of an unarmed black man in North Charleston, South Carolina on April 7, as reported by The New York Times. The Times noted that “the shooting came on the heels of high-profile instances of police officers’ using lethal force in New York, Cleveland, Ferguson, Mo., and elsewhere. The deaths have set off a national debate over whether the police are too quick to use force, particularly in cases involving black men.”
-
This series of ethnic stereotypes becomes Oren’s whole prism for interpreting the negotiations, which are “an ideal example of how not to buy a Middle Eastern carpet.” He argues: “The Security Council’s five permanent members plus Germany could have offered the lowest possible price as their final bid—take it or leave it. Iran would have had little choice but to sell the carpet.”
When the US and its negotiating partners “recogniz[ed] the Islamic Republic’s right to enrich and to maintain its nuclear facilities,” Oren scolds: “The haggling had scarcely begun and already the merchant profited.” Actually, the right to a peaceful nuclear program was guaranteed to Iran when it signed the Nuclear Non-Proliferation Treaty (FAIR Blog, 4/8/13), but there isn’t really a stereotype that involves the customers of a “merchant” agreeing to respect international law.
-
There’s not an ounce of probable cause to search me at the airport — as I was today at LAX. To violate my body. To touch my breasts. To grope my hair. To have the blue latex-gloved hand of Sharonda Juana Walker, feel inside my turtleneck.
And no, I don’t go through the scanners, and the metal detector line wasn’t an option at just before 7 a.m., when I got to the airport to leave for…no, not an ISIS meet-and-greet but an evolutionary psychology conference in Boston. Apparently, the sparse traffic at the airport at this hour leaves them plenty of time to feel up travelers.
-
The witness hailed as a hero for capturing the shooting of Walter Scott on camera has come forward to speak publicly about the incident for the first time.
Identified by NBC News as Feidin Santana, the man whose video made headlines around the world described the “emotional” moment he handed his vital evidence over to the Scott family.
Mr Santana’s video showed 33-year-old Officer Michael Slager shooting Mr Scott in the back as he runs away, and the witness said he only came forward when the police’s version of events – that Mr Scott had seized control of the officer’s Taser – appeared in the media.
-
Anyone with a sliver of vision and a shred of morality can see this.
South Carolina Patrolman Michael Slager cowardly hid behind his badge when he claimed he felt threatened by Scott after pulling him over for a faulty brake light. Slager alleged that Scott reached for the officer’s stun gun and his life was in danger – Slager said he had no other option but to kill Scott.
Slager lied. Video evidence does not.
That video showed the world that the real victim was Scott, who was shot in the back as he attempted to run from Slager. And the real criminal is Slager, a man who resorted to lethal force after a mere traffic stop.
The facts are clear-cut and the video evidence is undeniable. So why do I keep hearing this statement?
-
A video supplied to The New York Times, showing the shooting death of 50-year-old Walter Scott at the hands of a South Carolina police officer, appears on first viewing to be the latest example of an unarmed black person killed unnecessarily by a white cop.
But it’s so much more than that. Because three days elapsed between the shooting and the publication of the video of the shooting, the Scott incident became an illuminating case study in the routinized process through which police officers, departments and attorneys frame the use of deadly force by American cops in the most sympathetic possible terms, often claiming fear of the very people they killed. In the days after the shooting, the police version of events — an utterly typical example of the form — was trotted out, only to be sharply contradicted when the video surfaced. In most cases like this, there is no video, no definitive, undisputed record of much of what happened, and thus no way to rebut inaccurate statements by the police.
-
Secret mass surveillance conducted by the Drug Enforcement Administration is falling under renewed scrutiny after fresh revelations about the broad scope of the agency’s electronic spying.
-
When Bruce E. Ivins, an Army microbiologist, took a fatal overdose of Tylenol in 2008, the government declared that he had been responsible for the anthrax letter attacks of 2001, which killed five people and set off a nationwide panic, and closed the case.
Now, a former senior F.B.I. agent who ran the anthrax investigation for four years says that the bureau gathered “a staggering amount of exculpatory evidence” regarding Dr. Ivins that remains secret. The former agent, Richard L. Lambert, who spent 24 years at the F.B.I., says he believes it is possible that Dr. Ivins was the anthrax mailer, but he does not think prosecutors could have convicted him had he lived to face criminal charges.
In a lawsuit filed in federal court in Tennessee last Thursday, Mr. Lambert accused the bureau of trying “to railroad the prosecution of Ivins” and, after his suicide, creating “an elaborate perception management campaign” to bolster its claim that he was guilty. Mr. Lambert’s lawsuit accuses the bureau and the Justice Department of forcing his dismissal from a job as senior counterintelligence officer at the Energy Department’s lab in Oak Ridge, Tenn., in retaliation for his dissent on the anthrax case.
-
It was a nasty kind of deja vu at the Times of Israel on Thursday after the website caused an uproar by publishing and then removing an op-ed calling for the mass murder of Palestinians.
-
On a late spring evening eight years ago, police pulled over my mother’s 1997 Oldsmobile Aurora, in the suburb of St. Ann, Missouri, as she raced to pick up a relative from St. Louis’s Lambert International Airport. “Do you know why I stopped you?” the officer asked. “No I don’t,” my mother answered. The police charged her with speeding, but she did not receive a mere ticket. Instead, an officer ran my mother’s name and told her that since she had failed to appear in court for driving without a license, there was a six-year-old warrant out for her arrest. “I just started crying. I couldn’t believe it,” my mother said. The police arrested her and hauled her off to St. Louis County Jail, where authorities eventually allowed her one phone call, which she placed to my stepfather. He said, shaking his head, “I was surprised because I knew she didn’t have no warrants.”
-
Spontaneous dancing remains outlawed in Sweden except in venues with special “dance licences” after a majority in parliament voted down a move to free the feet.
-
Particularly given that the only question of those I posed for my book that Miller did not answer was whether she saw Cheney on the trip to Aspen that she used to explain Scooter Libby’s Aspen letter, I find her admission that she did and does speak to Cheney — though had not, about the war — telling. (Remember, too, that Cheney did not release journalists he had spoken to to reveal him as a source in the way everyone else in the Executive Branch did.)
Miller goes on to present a nonsense story about how Fitzgerald misled her and caused her to testify incorrectly, falsely testifying to the grand jury that Libby had told her Plame was at the CIA back in June. It doesn’t make sense — and doesn’t do anything to undermine the other evidence that would have been sufficient to convict Libby, notably Libby’s own notes and David Addington’s testimony as well as a second, far more important, meeting between Libby and Miller just days before Novak outed Plame.
Maybe Miller just has no fucking clue what got presented at the trial?
But having presented a flimsy excuse to question the verdict against Libby, Miller has presented others with an opportunity to point to another detail she includes in her book: that Fitzgerald offered to drop the charges against Libby if he would testify against Cheney. Again, that’s not surprising. Libby’s lies served to cover up Cheney’s orders to leak stuff to Judy Miller (not in the meeting she newly focuses on, but in the meeting during the week of Novak’s article).
-
“Did the use of pressure cooker bombs,” the jury in the Dzhokhar Tsarnaev trial was asked in several different ways on Wednesday afternoon, “cause the death of Martin Richard?”
“Yes,” the jury declared Tsarnaev’s guilt in the murder of Richard, the 8-year old boy watching the race from the finish line killed in Tsarnaev’s attack on the Boston Marathon two years ago. “Yes,” the jury said, over and over. The jury gave the same response when asked about Tsarnaev’s responsibility for killing Lingzi Lu, a Boston University statistics student; Krystle Campbell, a 29-year old restaurant manager; and Sean Collier, an MIT cop, all of whom he and his brother killed. The jury found Tsarnaev guilty of all 30 counts against him.
-
Last month, Archbishop Desmond Tutu wrote a letter to Leonie Brinkema, the judge in the Jeffrey Sterling trial, calling on her to prove cynicism wrong in her sentencing of Sterling. The letter was docketed this week.
-
We, the undersigned organizations, are writing to urge you to remove the Department of Commerce’s Inspector General, Todd Zinser. Through his actions both before his appointment as IG and since, Mr. Zinser has proven that he is not fit for the position.
IGs are supposed to root out fraud, waste, and abuse—a job they would not be able to do without whistleblowers. If there is anyone in government who should understand the importance of utilizing and protecting whistleblowers, it is an IG.
This is why it is particularly worrisome that there have been multiple allegations and investigations of Mr. Zinser’s own retaliation against whistleblowers. A 2013 report by the Office of Special Counsel found that Mr. Zinser had shielded two top deputies charged with threatening two employees with retaliation if they blew the whistle on mismanagement at the Commerce IG’s office.
Intellectual Monopolies
-
Copyrights
-
Back during the SOPA fight, in a discussion with someone who was working with the politicians pushing SOPA, I pointed out that such a law would encourage much more encryption — and the response was “that’s no problem, because we’ll just ban encryption next.” As stupid and impossible as such a statement is, it shows the mindset of some copyright extremists. Thus, it should be no surprise that they’re actually starting down just such a path in New Zealand. As we noted last year, Kiwi ISPs, frustrated that their users kept running up against geoblocks, have started offering VPN services that get around geoblocks as a standard feature there. Basically, this is nothing more than a recognition that the internet really is global and attempts to pretend otherwise are pretty fruitless.
Permalink
 Send this to a friend
Send this to a friend
04.08.15
Posted in Europe, Patents at 7:00 pm by Dr. Roy Schestowitz
Large corporations increasingly cast their shadow over European society

Summary: Recent articles about the EPO and the Unitary Patent are bundled together to highlight truly disturbing developments whereby those in power beget power through instruments of state-sanctioned power, such as the EPO (stateless entity within a continent-wide ‘island’)
OUR coverage of the EPO-targeting French article will hopefully lead to an English translation pretty soon (more suicides inside the EPO), but in the mean time we wish to take stock of recent European-centic patents-related developments which we have not found the time to properly cover (at least not yet). We will separate and partition this post, then set some headlines to help digestion of the important news.
Unitary Patent
Techrights has written about the Unitary Patent for quite a few years, even before it was called or referred to as “Unitary Patent”. In a series titled “UPC Mock Trial” [1, 2] (Unitary Patent Court is UPC) IP Kat provides some interesting information. Since a lot of this stuff is discussed behind closed doors (like TPP and other globalisation treaties) it has not been easy to keep track of what’s going on. In part it’s about serving huge corporations (multinational and often tax-exempt through loopholes) and it’s about software patents. The folks from the FFII (former and current presidents) are fighting back, calling the Unitary Patent unconstitutional. To quote their summary, which made some waves on the Web last week, “ESOMA and iMatix has filed an appeal against the Unitary Patent ratification by Belgium at the Constitutional Court. Equality of languages, separation of powers, and the irresponsibility of the EPO in front of courts are violating the Belgian Constitution. A central patent court will become the single point of failure to validate software patents Europe-wide. Small Software companies cannot afford to go to court or pay damages.”
There are similar actions elsewhere. They are fighting back.
European Free Software Foundation
The Free Software Foundation Europe (FSFE), OpenForum Europe and others (such as OIN from the US) were mentioned the other day in this post about the EU patent debate. We deem some of the text quite important (and unique). It states: “I already mentioned earlier the plans to present about the situation of the Open Source community as a consumer of the patent system at the conference on “Innovation in a European Digital Single Market – The Role of Patents” in Brussels on March 17. FSFE, OpenForum Europe, colleagues at OIN and fellow Open Source supporters provided great feedback for the presentation. Many thanks to everybody who contributed! In the end, the concept for the presentation (which was a short introduction to a following panel discussion) was to explain five concrete difficulties the patent system causes in a collaborative production environment.”
Towards the bottom it says that “Sage joined the Open Invention Network. OIN is the world’s largest patent non-aggression community with the mission to protect Linux and Open Source. It speaks for the credibility that patent non-aggression has achieved and for how OIN represents that idea in the Open Source space when a publicly listed company that grew to success long before Linux really took off subscribes to it. Thanks, Sage! More large and small companies are considering this step. Your company should do so, too. If you have any questions, feel free to contact me.”
As we have pointed out before, the problem with OIN is that it does not fight software patents; additionally, it is selective in who is protects and how. Still, for many purposes (not all), it is a lot better than nothing.
Want to Patent Nature? EPO Approves
The EPO is an utter, corrupt, greedy disgrace. On numerous occasions we have shown how the EPO’s management, including Benoît Battistelli himself, gloated and bragged about expanding the scope of patents, reducing the quality bar etc. just to increase profits. This is systemic corruption and this in its own right should suffice to oust Battistelli.
Techrights is especially focused on software patents, but it is deeply disturbed to learn just how low the EPO’s management can stoop. As it turns out, the EPO now permits patenting natural foods – not just GMO and algorithms. This surely can motivate more EPO staff to rebel against greedy-beyond-control managers. We sure hope to see people standing up and fighting against this abuse by EPO architects, whose priority has become to serve large corporations, not people. See articles such as “Unpatentable Vegetables Are Now Patentable In Europe”, “EPO Backs Patents On Conventional Plants: Broccoli, Tomato Cases Decided”, and “A Kat revisits Broccoli & Tomatoes, part deux – what does it all mean?” IPKat reported on it quote early on (to its credit).
Software Patents in Europe
Patent scope has gone out of control in Europe. Patents not only on natural things but also on abstract things are now permitted, if not by law then by de facto ‘law’ (see our wiki page about software patents in Europe). Glyn Moody warned some weeks ago that “Spain [Was] About To Bring In Software Patents — Just As US Starts Moving Away From Them”.
Quoting Moody: “Last year, Techdirt noted how the Supreme Court’s decision in Alice v. CLS Bank seemed to be having a positive effect on limiting the patentability of software. Against that background, it’s regrettable that Spain appears to be moving in the other direction with its new Patent Act (original in Spanish), which is being brought in without any public debate, it seems. The key section of the proposed law is Article 4, which spells out patentability. It specifically says (Section 4c) that “computer programs” are excluded from patentability — but then goes on to add (Section 5) that it is only software “as such” that is excluded.”
Greedy patent lawyers from the US (such as Gene Quinn in this case) are already licking their lips over this. “The European technical standard as a guide for drafting software patents” is the title of one recent article from Gene Quinn, one of the most vocal proponents of software patents (he makes money from it).
And guess who he interviews for this article? “Micky Minhas is Chief Patent Counsel for Microsoft Corporation. He is also someone that I have know for over 20 years, which is almost hard to believe.”
Yes, Microsoft!
Welcome to Europe, Microsoft. A truly European company!
Microsoft has been lobbying for software patents in Europe for so many years and we wrote many articles about it. Microsoft also paid several proxies to do this lobbying behind the scenes. Among these lobbyists we have had the BSA and ACT listed.
Microsoft’s Minhas says: “I’ve been here about two and a half years in my role as Chief Patent Counsel. The Patent Strategy team is roughly 110 people and we are responsible for all of our new patent filings and preparation. We also have a large analysis group that analyzes a lot of our issued patents and our pending patents and supports our licensing programs. As to the daily life, the job ranges anywhere from issues with the PTO, or any other patent office around the world, to issues supporting our licensing programs. Sometimes it’s acquisition related activities; sometimes it’s risk mitigation projects. I’m having a lot of fun. It’s interesting particularly because Microsoft is in so many different businesses, so the legal issues and the intellectual property issues are often pretty unique. Sometimes what is in the best interest of one division may not be in the best interest of another division. Intellectually, it leads to some pretty interesting strategy assessments and discussions.”
So, while Europeans are busy typing computer code, testing, improving, testing again (among other things) Microsoft is working with lawyers to undermine these Europeans and take them to court if they ever become successful and can thus be extorted (like TomTom in Holland). Welcome to Europe’s new patent regime?
Fight the System Before It’s Too Late
Patent examiners in Europe (scientists, not lawyers) should work hard to prevent the EPO from becoming another USPTO with lots of software patents, patent trolls, and reign by massive corporations such as IBM. Benoît Battistelli seems to be trying to emulate the notorious US patent system, not a saner system whose priority is service to local (European) citizens. Once corporations take over such systems (in a coup d’état fashion) it becomes incredibly difficult to regain control of them, as the US model serves to show. We will provide examples of this in the coming days. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 6:10 pm by Dr. Roy Schestowitz
The high cost of Battistelli’s tyranny

Summary: The EPO has become so rogue that it might as well be renamed the Euthanasia-Prodding Organisation
SOMEONE has sent us “an interesting article about the [European patent] office,” to quote his or her own description of it. The EPO is no stranger to scandals and corruption, so we are not surprised to learn that yet more suicides are being reported.
The original article is in French and behind a paywall, but we have acquired a full text version [PDF] which we can publish in full if it is translated to English (fair use).
Sadly, nobody has come forth with a translation (we asked in numerous places for 4 days now), so if anyone is reading this right now, please kindly consider helping with this. The translation needn’t be perfect, just readable and accurate enough to pass muster (not mislead). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, FUD, Microsoft, Red Hat, Security at 5:52 pm by Dr. Roy Schestowitz
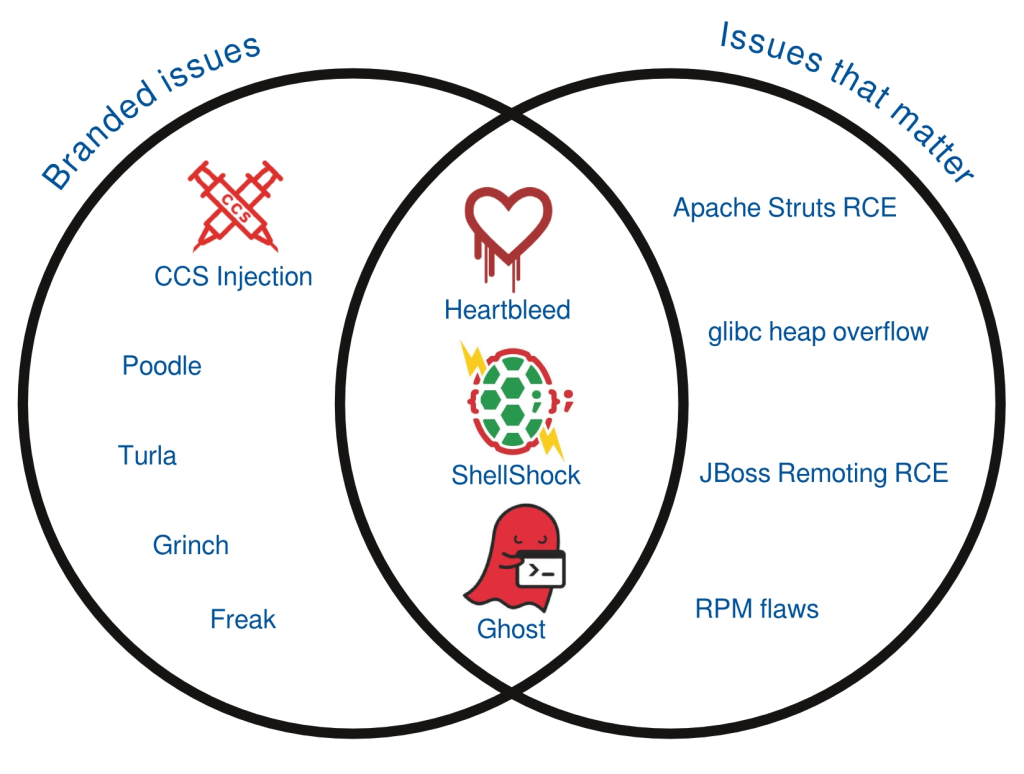
Image courtesy of Red Hat
Summary: Old news is ‘new’ again, as Microsoft-friendly media decides to keep knocking hard on the reputation of Free software, using words rather than substance
A YEAR ago there was a curious (first of its kind for Free/Open Source software) “branding” of a 2-year-old FOSS bug by a Microsoft-linked firm that did not even find the bug. An engineer from Google had found it and sought to responsibly disclose it so as to patch it properly before the Microsoft-linked opportunists blew off the lid and called it “Heartbleed”, set up a Web site to ‘celebrate’ the bug, and even made a professionally-prepared logo for it. This whole “Heartbleed” nonsense — however serious it may have been for a day — was blown out of all proportions in the media and tarnished the name of Free software because it was so ‘successfully’ marketed, even to non-technical people. It was a branding ‘success’ which many firms would later attempt to emulate, though never with the same degree of ‘success’ (where success means bamboozling the public, especially non-technical decision-making people).
“Microsoft must be laughing quite hard seeing all that media manipulation.”“Dear journalists,” I said earlier today in social media (Diapora), “bugs don’t have birthdays. Stop finding excuses to bring “Heartbleed” BS (MS name for old bug) to headlines.” I spoke to one author about it and challenged him for floating these “Heartbleed” logos and brands yet again. To us it seems quite evident that Microsoft keeps attacking Free software and GNU/Linux like no time before; it’s just more subtle and hidden in more sophisticated ways. The person who heads the incognito firm that’s known only for the “Heartbleed” brand (they control the brand) came from Microsoft (he was head of security there) and also from the FBI, whose stance on encryption is widely known by now; they actively seek to break security of software, so knowing about the 2-year-old OpenSSL bug would make sense. Some reputable media reports said that the NSA had known about this bug for about a year before it was known to the public and the NSA cooperates with the FBI on breaking software security, sharing personal (illegally intercepted) data, etc.
Anyway, the same publication (as above) also floated the “Heartbleed” nonsense in another article today. Would they do just about anything to keep it in headlines? Even a year later? They are now citing some firm called Venafi (never heard of it before), which basically relies on misleading misuse of statistics. It’s FUD from a company that tries to make money from perceived dangers and accentuates these dangers in an effort to acquire clients. What kind of ‘journalism’ is this? incidentally, Black Duck is now joining the list of such parasitic companies, with new hires and multiple press releases, so clearly it’s a growth area and the Microsoft link is easy to see. It is FUD season again this spring as more publications now float this whole nonsense. This is hardly journalism, it’s just throwback.
Thankfully enough, Red Hat demonstrates what “branding” of FOSS bugs practically means, even using the image above. There is no correlation between the naming of bugs and their severity, but press coverage sure loves a good brand. This is an important (albeit belated) response from Red Hat to “branding” of a FOSS bug by Microsoft-linked firms like the one behind “Heartbleed”.
“It’s been almost a year since the OpenSSL Heartbleed vulnerability,” says Red Hat, “a flaw which started a trend of the branded vulnerability, changing the way security vulnerabilities affecting open-source software are being reported and perceived. Vulnerabilities are found and fixed all the time, and just because a vulnerability gets a name and a fancy logo doesn’t mean it is of real risk to users.”
Well, Microsoft folks sure squeezed everything they could from this bug, seeking to discredit not just OpenSSL but the whole development process of Free software (due to just one small bug, or a few lines of code). And Microsoft still pretends that it is warming up to Open Source? Who are these frauds kidding?
There’s a lot of companies which continue to use platforms with back doors, such as Windows, but the Wintel-oriented media would rather we just obsess over this one bug from one year ago (which was patched as soon as it became publicly-known).
We are rather disappointed to see a decent journalist like Sean Michael Kerner, along with colleagues at eWEEK, swallowing the bait and serving to promote the misleading claims to advertise this company that controls the “Heartbleed” brand, among other opportunists (like fish swimming around a shark for some leftovers). Microsoft must be laughing quite hard seeing all that media manipulation. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, FUD, Microsoft, Security at 5:13 pm by Dr. Roy Schestowitz
Summary: Black Duck ups the ante on Free software-hostile messages, embeds FUD in the media almost instantaneously
THERE IS an attack on Free software going on, but it’s shrewdly disguised as ‘concern’ for Free software. We are led to believe that not proprietary software with back doors is the problem but Free software that may have bugs, especially bugs that users don’t bother to patch despite having the ability (or freedom) to do so. It’s free.
The other day we wrote about Black Duck entering the security FUD market, targeting Free software, as one ought to expect (it had already done the compliance FUD, neglecting to mention EULA-related issues in proprietary software). To repeat some facts for the uninitiated, Black Duck was started as an anti-GPL company, by its very own admission. Very shortly after hiring a parasite, whose company exploits security fears, Black Duck’s scope of FUD expands further and there’s an effort in the media to advertise this.
“Taft, who often promotes Microsoft PR, doesn’t mind covering something that seemingly relates to Free software if it makes Free software look bad.”Darryl K. Taft, a booster of Microsoft, already helps this anti-GPL company (Black Duck) by doing this Microsoft-esque advertising at this very moment. Taft, who often promotes Microsoft PR, doesn’t mind covering something that seemingly relates to Free software if it makes Free software look bad. No wonder Black Duck came from Microsoft. Other Microsoft boosting sites like TechFlash promoted this nonsense and spread it to media with broader reach. Watch how they wrongly describe Black Duck: “Burlington-based open-source software firm Black Duck software is making big bets on helping to make open-source software more secure for companies”
Black Duck is most definitely not “open-source software firm”, it is an anti-Open Source software firm whose products are proprietary, with software patents that relate to them. This is the kind of openwashing that has become so common when it comes to proxies of Microsoft (Microsoft works together with Black Duck, it’s not just that Black Duck came from Microsoft).
Black Duck, as we noted the other day, had hired a key person from Veracode, whose output is mostly FUD even today. Right now it promotes itself in CBS and other networks by saying some nonsense about a nonsense buzzword (“Internet of Things”) that means nothing in particular. To quote the CBS tabloid: “In a new report released by enterprise security firm Veracode, researchers discovered during testing of common, household IoT devices that security is not up to scratch — paving the way for exploits, data theft, robbery and potentially even stalking.”
That is just some embedded marketing for a FUD firm, one whose co-founder is now inside Black Duck.
Truth be told, Black Duck is trying to diversify or re-brand itself ‘pro-security’ as it did ‘pro-compliance’, but actually, what it really is about should be FUD. It uses fear, spreads existing fear to sell, creates more fear to sell, and overall it makes Free software look bad.
IDG is another large network that helped Black Duck advertise itself the other day. The headline is misleading because it says “Black Duck’s mission: To seek out insecure open source code in the enterprise”.
No, Black Duck’s mission is to sell its proprietary software by telling the press, enterprises etc. that Free software is not secure and needs some ‘medicine’ (Black Duck’s proprietary snake oil).
Here are the press releases from Black Duck [1, 2]. Clearly enough there is a media manipulation campaign going on and some journalists — other than Microsoft boosters disguised as ‘journalists’ — have already fallen for it. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft at 4:41 pm by Dr. Roy Schestowitz
Classic cruelty

Summary: Very insensitive Microsoft layoffs show that it is Microsoft that’s the greatest enemy of its own employees, not the company’s competition or its critics
THROUGHOUT the day today Techrights received a lot of support from former Microsoft staff, which now knows what Microsoft is really like (having become victimised). A post of ours from earlier this year went viral, reaching perhaps 100,000 people.
“Microsoft fired its previous Chief Privacy Officer for suggesting real privacy…”The context of it all and what got it all started was a post of mine about the latest Microsoft layoffs. “Acquisitor of Nokia’s mobile phone business,” said Microsoft-friendly media, “technology firm Microsoft is planning major reductions to its IT department. The cuts are to be included in the 1,050 jobs that last August the company announced would be culled from its Finnish operations.”
Notice the date. This is how Microsoft celebrates Easter in Finland, having just recently fired many Chinese on Chinese New Year. It’s part of a trend of sadistic Microsoft layoffs, often disguised as anything but layoffs. People from Microsoft have told me that the work environment is getting worse, as more employees get squeezed into smaller offices and some are laid off without being accounted for (contracting tricks with no assurances of continuation).
Microsoft dropped a real privacy officer, which says a lot about Microsoft’s real attitude towards privacy. Microsoft only ever needs to pretend to care about privacy (e.g. using a show trial in Ireland for media manipulation) while creating back doors in their products. Anything else cannot be tolerated.
Microsoft fired its previous Chief Privacy Officer for suggesting real privacy and the existing Microsoft “Chief Privacy Officer” is doing it ‘right’; he has just dropped privacy (news from 5 days ago) and then sought to justify it. “Microsoft chief privacy officer,” according to this article, is the very opposite of pro-privacy. It’s just like heading “trustworthy” computing for Microsoft, meaning the very opposite of what it’s called.
Microsoft wants to hire sociopaths, retain liars, and get rid (fire) those who don’t fit such criteria. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 4:03 pm by Dr. Roy Schestowitz

Contents
-
I adore Linux because I can do what I want on it. My first PC way back in 1994ish was an Apple something. It was fun, and then I got an IBM PC running Windows 3,1 and DOS 5. Windows was useless, so I spent a lot of time in DOS. Then I learned about Linux and never looked back. And Windows is still useless, and Apple is too confining. They both have their little walled gardens, and their primary purpose is lock-in and to keep selling you junk whether you want it or not, and whether or not it’s any good. They think they retain ownership of your stuff that you have purchased, which is a concept that needs to die.
-
Desktop
-
-
Windows 7 – 33.8%
Mac OS X – 21.5%
Linux – 20.5%
Windows 8 – 19.5%
-
Server
-
Gene Kim: It’s called “The DevOps Cookbook,” and it was actually supposed to come out before “The Phoenix Project.” The goal of the book is to put into context the cultural norms, principles, and observed patterns in high-performing organizations that enable fast flow of features from dev to ops while preserving world-class reliability and stability. For me, I think the big surprise three years into this project is that it’s as much about organizational learning as it is about key performance measures.
-
Cloud is the next big front for some serious tech warfare and CoreOS just got the much needed ammunition.
First things first. CoreOS is a company that offers a solution with the same name. And this solution is an extremely light and minimalistic operating system based on Google’s Chrome OS (or you can also call it a fork).
-
Kernel Space
-
Linus Torvalds is mostly known for developing the Linux kernel, but he’s also the one who made Git, the distributed revision control system that’s used today for numerous projects, including the kernel. The project just turned ten years old, and Linus made some comments about this fact.
-
Git has come a long way in the 10 years since Linux creator Linus Torvalds released the first version of the now-popular distributed revision control system. For example, the addition of pull requests came three years after the original release, according to Atlassian. And over time it has added more collaboration tools, code review tools, integration to continuous integration systems, and more, recalls Qt Project core maintainer and software architect at Intel, Thiago Macieira.
-
Radhika Hirannaiah, is currently working as an intern at OpenDaylight. She received a PhD degree in Electrical Engineering from Wichita State University in 2014. Her interests include Software Defined Networking (OpenFlow, OpenDaylight etc), Voice over IP, wireless and working on open source software projects.
-
Systemd’s logind and systemctl components have added support for rebooting to the EFI firmware setup. Running systemctl –firmware-setup (or accessing via systemd’s logind interfaces) will cause the system’s firmware UEFI setup utility to show at next boot as another alternative to just hitting DEL/F2 at boot time or newer distributions that add a boot menu entry to GRUB2 for EFI firmware configuration. Of course, this will only work for newer systems that were originally booted in the EFI mode.
-
Graphics Stack
-
There’s more improvements in Mesa Git to talk about this week for Intel open-source customers, including those still on older “Gen4″ graphics hardware.
-
FreeGLUT, the open-source replacement to GLUT for handling system-specific setup tasks like windowing system configuration and OpenGL initialization, now is natively supported on Wayland.
-
Chris Wilson of Intel’s Open-Source Technology Center hasn’t yet managed the xf86-video-intel 3.0 DDX release, but over in kernel-space, he’s just published a set of 70 new DRM patches for the Intel kernel driver.
-
The Khronos UK Chapter is holding a meeting at the LLVM conference happening one week from today at the Goldsmiths University in London. Vulkan, SPIR-V, and OpenCL 2.1 will be the primary discussion items for the event lasting the afternoon.
-
If you’re not on the NVIDIA 349 Linux beta but rather an older version of NVIDIA’s binary Linux driver, today they released the 346.59 bug-fix release as the latest in their long-lived series.
-
Tom Stellard of AMD has landed initial support into the AMD GPU LLVM back-end for the assembler and supporting inline assembly.
-
Benchmarks
-
It’s been a while since last running any Linux file-system tests on a hard drive considering all of the test systems around here are using solid-state storage and only a few systems commissioned in the Linux benchmarking test farm are using hard drives, but with Linux 4.0 around the corner, here’s a six-way file-system comparison on Linux 4.0 with a HDD using EXT4, Btrfs, XFS, and even NTFS, NILFS2, and ReiserFS.
-
Applications
-
The Qt Installer Framework allows for offline and online installers for Windows, Linux, and OS X. This framework is focused on Qt’s needs but can also be used by other applications as an installer/updater.
-
The application is very simple, lightweight and doesn’t get in your way. In fact, it doesn’t even come with a GUI by default and instead, it only shows an entry in the Ubuntu Sound Menu which allows you to play various relaxing sounds like forest, storm, rain, wind, night, fire, coffee shop or sea.
-
For any object moving through a fluid, forces are applied to the object as the fluid moves around it. A fluid can be something like water, or even something like the air around us. When the object is specifically designed to maximize the forces that the fluid can apply, you can designate these designs as airfoils. A more common name that most people would use is a wing. The shape of a wing, or airfoil, determines the forces that are applied to it when it moves through a fluid or the air. These forces also depend on the speed of motion through the fluid and the direction of flow around the airfoil.
-
In fact, I spent the last month porting Choqok bits from Qt 4 to Qt 5, but I also fixed minor bugs you discover when doing this kind of work. Regressions could happen, so please report them and we’ll fix them!
-
darktable 1.6.4 has been released recently bringing a wide range of improvements, support for new cameras, new white balance presets, new noise profiles, and several updated translations.
-
-
It will probably be a cold day in you-know-where before we ever see a native version of iTunes for Linux. Apple just isn’t interested in supporting Linux. But you actually can run iTunes in Linux via WINE, and if that doesn’t float your boat then there are some native Linux alternatives to iTunes that are worth considering.
-
Most of patool seems to work as command-action-target format, so extracting a file — just about any compressed file, I might add — is as simple as patool extract file. The extension of the file appears to be irrelevant to patool — if I rename a file to show a different extension, it manages to extract it anyway.
-
-
Instructionals/Technical
-
Games
-
It’s so damn good to see Humble back on form with a true Humble Indie Bundle, we just gained access to new games too!
-
We announced the Humble Indie Bundle 14 game sale initiative at the beginning of the month, a great occasion for Linux, Windows, and Mac gamers to get their hands on a fabulous collection of cross-platform games.
-
Tripwire have announced that Killing Floor 2 will be released on the 21st of April into Early Access, but we have it confirmed Linux is not in the initial release.
-
-
-
Desktop Environments/WMs
-
The Enlightenment crew at Samsung have released their first alpha version of the upcoming EFL 1.14.0 library set.
-
K Desktop Environment/KDE SC/Qt
-
NetworkManagerQt is officially a Frameworks now. As a consequence the repository has been renamed from libnm-qt to networkmanager-qt and NMQt version number now follows Frameworks version number (currently 5.8.0).
-
In February 2015 the Plasma developers met in the Blue Systems office in Barcelona to discuss and plan out where we would take Plasma over the duration of the next year. The sprint consisted of active Plasma developers and visual designers from around the world, from Canada to India.
-
The digiKam development team has announced a few hours ago, on April 7, the immediate availability for download of the digiKam Software Collection 4.9.0 image viewer and organizer application for the KDE desktop environment.
-
-
-
We have released another plasma-nm version for KDE 4. It’s possible that this release will be the last one, because every distribution is now switching to Plasma 5 and given our irregular releases it’s possible that current distributions wouldn’t pickup the updated version anyway. I’ll keep backporting fixes from Plasma 5 to our KDE 4 branch if possible, so if you want to keep running on KDE 4 from some reason, you will still have a way how to get at least some fixes. There is also a new release of networkmanager-qt for KDE 4, which is required for below mentioned OpenConnect fixes.
-
A Linux user has started an LKML discussion over compiling the kernel with -O3 for driving performance improvements out of a more-optimized kernel binary.
-
GNOME Desktop/GTK
-
The GTK+ development team has announced the immediate availability for download of the first maintenance release of the GTK+ 3.16 GUI toolkit used in the GNOME 3.16 desktop environment.
-
GNOME 3.16 was released last week and is the result of more than 30000 commits by over 1000 persons, I am always impressed by those numbers, thank you all!
-
GNOME/GTK+ developers are finally preparing themselves to drop support for Microsoft Windows XP.
While Microsoft no longer offers public support for Windows XP and most modern software has done away with XP support, GNOME’s tool-kit continues to support Windows going back to XP. It’s been discussed before about dropping XP and this discussion has resurrected once again.
-
-
Papyros is a new Linux distribution designed around a Material Design framework, and it promises to be one of the most interesting releases in the Linux ecosystem. After a month that brought no news about its progress, the devs explained that the project is not dead, but alive and kicking.
-
Ubuntu developers are preparing to launch the last OTA update for the current branch of Ubuntu Touch RTM, and they are also working to change the base of the system to 15.04 (Vivid Vervet).
-
Reviews
-
There are people out there that will want all of the verbose options, giving access to every available installation option but maybe there could be a general installer and a custom installer to make it easier for the masses.
-
Void is an independent distribution and offers a rolling release approach to package management. There are many Void editions we can download. There are Void images for the BeagleBone and Raspberry Pi computers along with builds for 32-bit and 64-bit x86 machines. In addition, there are spins of Void for specific desktop environments and we can download images for Cinnamon, Enlightenment, MATE and Xfce flavours. I decided to begin my trial with the 64-bit Cinnamon build of Void. The download for the Cinnamon image is 454MB in size.
-
New Releases
-
With pleasure SalentOS Team announces the release of SalentOS 14.04.2.
-
Screenshots
-
Slackware Family
-
The set has been spiced up with the latest Long Term Support (LTS) sources that I took from KDE Applications 14.12.3, specifically the newest versions of kde-workspace, kdelibs and kdepim. Essentially, I have used the exact same sources from which I built my KDE 4.14.3 packages for Slackware-current before.
-
Red Hat Family
-
Pat Riehecky from the Scientific Linux development team has announced today, April 7, the immediate availability for download and testing of the second and last Release Candidate (RC) version of the forthcoming Scientific Linux 7.1 operating system.
-
Besides the speeches, 170 1-hour breakout sessions are planned. Breakout sessions are presentations by industry experts on topical issues. Some speakers include Thomas Cameron, John Shakshober, and Matt Hicks. A Partner Pavillion will be open showcasing many of Red Hat’s partners and their wares. Labs will let attendees test out Red Hat’s latest tech. For those wanting still more add-ons include in-depth training courses with expert instructors and certification exams in Red Hat OpenStack. Developers can attend DevNation for “a week of keynotes, technical sessions, BoFs, evening programming events, and more” with folks from some of the top tech companies around.
-
Speaking to ChannelBuzz.ca ahead of the company’s North American Partner Conference here, Mark Enzweiler, senior vice president of global channel sales and alliances at Red Hat, described a shift in the conversation his company and its partners are having with their customers. Gone are the days of convincing customers that open source is “for real” in the enterprise. Now everybody’s got an opinion on open source – not just Linux, but other major projects as well, most notably OpenStack. Now, they want to know more, and that means partners have to know more.
-
Fedora
-
DNF is the next-generation Yum and after being available for the past few Fedora releases, with Fedora 22 it’s ready for prime-time. Kevin Fenzi last week started a mailing list thread about dnf replacing yum and dnf-yum. DNF is installed by default as part of the “core” group, DNF-Yum is also installed by default, Yum is still installed so if something still depends directly on it or a user manually wants it, and the Yum RPM package now requires dnf-yum.
-
Using the XFS file-system as the default within an LVM has been part of the Fedora Server technical spec while with Fedora 22 it’s finally happened. The default layout for Fedora Server 22 installations is using XFS atop LVM while /boot is outside the LVM setup.
-
Debian Family
-
As a follow-up to my post about bootstrapping arm64 in Debian, we’ve had more hardware given to Debian for us to use in porting and building packages for arm64. Applied Micro sent me an X-Gene development machine to set up and use. Unfortunately, the timing was unlucky and the machine sat on my desk unopened for a few weeks while I was on long holiday in Australia. Once I was back, I connected it up and got it working. Out of the box, a standard Jessie arm64 installation worked using network boot (dhcp and tftp). I ran through d-i as normal and installed a working system, then handed it over to the DSA and buildd folks to get the machine integrated into our systems. Easy! The machine is now up and running as arm-arm-03.debian.org and has been building packages for a few weeks now. You can see the stats here on the buildd.debian.org site.
-
Derivatives
-
Canonical/Ubuntu
-
Canonical revealed details about Oxide vulnerabilities that have been found and fixed in Ubuntu 14.10 and Ubuntu 14.04 LTS. This update brings a few fixes, but it’s nothing all that important.
-
Ubuntu 15.04 (Vivid Vervet) is about to be released in a little over two weeks, and the developers have announced that they settled on Linux kernel 3.19.3, a couple of days before the kernel freeze.
-
Every once in a while Ubuntu developers made improvements to the Unity desktop environment, but that usually happens for new Ubuntu releases, like 15.04 for example. That doesn’t stop them from porting those improvements to older releases, such as Ubuntu 14.04 LTS.
-
Hello Linux Geeksters. As you may know, Firefox 37.0.1 has been recently released, coming with important bug-fixes. Not long after that, Canonical has patched it and added it to the default repositories of all the supported Ubuntu systems.
-
The much requested Unity feature to always show the menus, which is already available in Ubuntu 15.04 Vivid Vervet for almost three months, has been backported to Ubuntu 14.04 LTS.
-
In recent months we’ve covered an Ubuntu tablet with a 1TB hard drive, another sketchy Ubuntu tablet, and other awkward devices looking to ship Ubuntu in tablet/mobile form without any support from Canonical. There’s yet another tablet to talk about today.
-
Details about a Mailman vulnerability in Ubuntu 14.10, Ubuntu 14.04 LTS, Ubuntu 12.04 LTS that has been found and fixed were published in a security notice by Canonical.
-
Flavours and Variants
-
Uri Herrera from Nitrux S.A. recently announced the immediate availability of Nitrux OS 4.15 Linux operating system that is currently used in their NXQ mini PC unveiled a couple of months ago.
-
CompuLab is working hard on the MintBox Mini. SMT (Supervised Manufacturer’s Testing) was done, and they’re now soldering, testing, starting mechanical assembly and packing of the units.
-
The name of the next Linux Mint 17.2 release has been chosen and it’s going to be “Rafaela.” The project continues with the feminine names, so the new code name should be no surprise.
-
Ostensibly, Information and Communication Technologies (ICTs) have significantly permeated our society, yet their integration in our educational system has not been achieved. The glaring disparity among students who are ICT literate and those who are not, is evidence of this. Understandably though, there are several priorities and challenges that may be responsible for the slow progress in this area. Fortunately for us, we have a few Liberians in our educational system who possess the dynamism needed to bring significant changes. However, these changes must parallel those of the global community’s. In doing so, we will effectively be eliminating one of the barriers that young Liberians graduating from high school face when they submit applications for employment; the ubiquitous, “must be computer literate” listed as a job requirement. In today’s article, I will discuss how EDUBUNTU, a Free and Open Source Software (FOSS), can help us integrate ICTs in schools to achieve some level of equilibrium with regard to basic ICT literacy among Liberian students.
-
-
Embedian has launched a SMARC COM that runs Linux on a Freescale i.MX6, and offers up to 2GB RAM, 4GB eMMC, -40 to 85°C operation, and a Mini-ITX baseboard.
-
Phones
-
The Jolla community has put together an application called Jolla Communicator that allows users to send and receive messages on Ubuntu, which connected to a Sailfish OS-powered smartphone.
-
Android
-
Back in January HTC announced they’d miss the deadline they set themselves for the HTC One M8 Android 5.0 Lollipop update, but since then we’ve received plenty of good news as it’s rolling out to multiple carriers in the United States. It first kicked off for owners back in January, and over the past few weeks has continued to arrive for more and more proud owners.
-
We all know there are good reasons why Android will never be rolled out as efficiently as the way Apple rolls out new versions of iOS. That said, surely the process can be better than it is right now… can’t it?
-
Motorola has begun rolling out the Android 5.1 Lollipop update for the Moto G Google Play Edition (GPE), and it is possible that other versions of the phone could receive the update anytime soon.
-
Check the Amazon Instant Video splash page and you’ll see the news: You can officially stream videos from Amazon to your Google Android tablet. I say “officially” because tech savvy folks may have already sideloaded, or manually installed, the phone version some time ago. But for the mainstream masses who typically get their apps from the Google Play Store — a smart move for security reasons — this is new.
-
The mobile companion game for Mortal Kombat X is available for download on both iOS and Android. Mortal Kombat X Mobile can be downloaded for free (with in-app purchases) on the Apple App Store and the Google Play Store, according to Hardcore Gamer. The Mortal Kombat X Mobile is the full Mortal Kombat X experience built for mobile devices.
-
-
There are many Android fans who aren’t enamored with Chrome OS. They cite lack of apps for the latter, and the wealth of features that make up the great utility of the former. There has long been speculation that Google will eventually merge the two platforms into one OS. I hope that never happens.
-
What is a smartwatch, and what can it do? The Apple Watch arrives in a landscape filled with things for your wrist. How does it stack up? Great in some ways, and not so wonderfully in others. Let’s look at the closest competition and see.
-
Owners of the Google Play Edition of the HTC One M7 and M8 should stay tuned for Android 5.1.
In a tweet late Tuesday, HTC vice president of product management Mo Versi said that “approval for both M8 & M7 GPE versions have been granted by Google for 5.1 OS. OTA out shortly!” That means an over-the-air update should reach both models soon if it hasn’t already. The Google Play Editions of such phones come with pure Android, which excludes any customizations typically made by the manufacturers.
-
Itching to make your shiny new Android Wear watch really yours? You’re in luck — Google’s curating not only the best watchfaces to throw on your teensy wrist-display, but some of the handsome watchbands you should lash onto it too. Android Wear product manager Jeff Chang pointed out new (and mostly leather, sadly) straps available from E3 Supply Co., Worn & Wound and Clockwork Synergy in a post on the Official Android Blog earlier today. Thing is, you can’t actually buy these accessories straight from the Play Store proper — you’ll still have to mosey on over to each retailer’s site to lay claim to your next bit of wrist candy so the approach isn’t exactly as seamless as we would’ve hoped.
-
We’re going to take the scenic route in getting to the point today. If you don’t want to wait, you can go down to the bottom where it says, “The moral of the story…” But the point of today’s exercise is that we in the decentralized FOSS realm are a creative bunch, and in that creativity is our strength.
-
Etsy attributes recent accomplishments in data center efficiency in large part to using the Facebook-developed, open source HipHop Virtual Machine (HHVM), according to software engineer Dan Miller on Etsy’s blog. Etsy is an extremely popular marketplace for handmade, vintage and unique items. The company is expected to IPO soon.
-
Open source, popular as it has been, has hardly killed off proprietary software. While margins and new license revenues have suffered across the enterprise software spectrum, it is the cloud, more than open-source software, that is to blame (or thank, depending on whose stock you own). Yes, open source built the cloud, but it is the cloud that gets all the credit (and cash).
-
Events
-
Open source developers can create an immense amount of value for any company that relies on open source software by giving it the ability to direct and influence aspects of the open source community. This allows the company to shape the tools they rely on and make them better fit company needs, a phenomenon otherwise known as “scratching their own itch.”
Although an open source developer’s primary skill is writing good code, their value extends far beyond technical skills. Adopting open source practices requires participation in diverse communities that have a number of stakeholders who each have their own itches to scratch. Open source developers find themselves in a complex position that requires them to be experts not only in their technical field, but also in communication and collaboration.
-
To defend against targeted attacks based on spoofed emails he proposed to detect whether the writing style of an email corresponds to that of previously seen emails of the presumed contact. In fact, their research shows that they are able to tell whether the writing style matches that of previous emails with very high probability.
-
Web Browsers
-
Chrome
-
Behind the bug A bug in the most recent version of the Chrome allows miscreants to crash browser tabs simply by embedding a link with a malformed URL in the HTML of a page.
-
Mozilla
-
Mozilla issued the Firefox 37.0.1 update, which disables the opportunistic encryption feature that was just introduced in Firefox 37.
Mozilla has had a change of heart regarding opportunistic encryption—for now. The company rolled out its open-source Firefox 37 Web browser on March 31, with one of the key new features being a capability known as opportunistic encryption. However, due to a security issue related to opportunistic encryption, Mozilla disabled the feature in the Firefox 37.0.1 update released April 3.
-
SaaS/Big Data
-
I’ve been involved in the ASF since 2005 when I got involved in the Apache Nutch project. I was a PhD student at USC taking Search Engines class and also working at NASA JPL. My final project in the class was an RSS parsing plugin (NUTCH-30) that got integrated. It was a budding, awesome community, and I got more and more excited after my patch and started helping out on the lists. I also saw a big use for Nutch and what eventually became Hadoop at NASA.
-
This weekend, NASA is hooking up with IBM’s BlueMix cloud platform in an unprecedented development effort. More than 10,000 developers, scientists, entrepreneurs and students in 62 countries will work in tandem on a code-a-thon aimed at building technology for space exploration. Here are more details.
-
PLUMgrid, which focuses on virtual network infrastructure for OpenStack cloud deployments, has announced the latest SDN software PLUMgrid Open Networking Suite 3.0 for OpenStack with new operational tools, features for dynamic routing, and expanded service insertion for third party virtual, physical and container based appliances. Based on OpenStack Juno, PLUMgrid ONS 3.0 is Red Hat certified with RHEL OSP 6.
-
Barzan Mozafari, Assistant Professor of Computer Science and Engineering at the University of Michigan (Ann Arbor), will be giving a talk on the predictability of performance in database systems at the OpenStack Live conference in Santa Clara, California on Tuesday, April 14.
-
Education
-
This February, EBSCO Information Services announced plans to provide funding and technical assistance for contributors to the Koha open source ILS platform. Led by the Koha Gruppo Italiano (KGI)—founded by the American Academy in Rome, American University of Rome, and the Pontificia Università della Santa Croce—with development support from ByWater Solutions, Catalyst IT, and Cineca, the partnership will enable an upgrade of Koha’s core search engine to Elasticsearch, the popular open source, multitenant-capable full-text search engine.
-
Funding
-
It is my sad duty to inform the community that Chris Yeoh passed away this morning. Chris leaves behind a daughter Alyssa, aged 6, who I hope will remember Chris as the clever and caring person that I will remember him as. I haven’t had a chance to confirm with the family if they want flowers or a donation to a charity. As soon as I know those details I will reply to this email.
-
FSF/FSFE/GNU/SFLC
-
This year the GNU Cauldron Conference is going to be held in Prague, Czech Republic, from August 7 to 9, 2015.
The GNU Cauldron Conference is a gathering of users and hackers of the GNU toolchain ecosystem.
Meaning that if you are interested in projects remotely related to the GNU C library, GNU Compiler Collection, the GNU Debugger or any toolchain runtime related project that has ties with the GNU system you are welcome!
-
Openness/Sharing
-
Open Access/Content
-
“Open Access: Is a national licence the answer?” is a proposal by David Price and Sarah Chaytor of University College London for a mechanism to provide full access to everyone within the UK to all published research. It was published on 31 March 2015 by the Higher Education Policy Institute (HEPI) whose director, Nick Hillman, wrote the foreword.
-
Programming
-
April Fool’s Day is well behind us, so all the pranks should be over, right? I ask because today, Google announces that it is making its Santa Tracker project open source on GitHub. The fact that it is open source is great, but the timing is odd. The last thing I expected to read about in April is friggin’ Santa Claus, but here we are.
-
Christmas may be a distant memory by now and the thought of Christmas 2015 might seem just as distant, as April has only just begun. However, it seems Christmas is not too far away from Google’s mind today, as the Search giant have just opened sourced their popular Santa Tracker software. If you are unfamiliar with Santa Tracker, then it is rather self-explanatory. Each year, around about Christmas time, Google releases its Santa Tracker offering the ability to track Santa while he is out and about and delivering his presents to all the boys and girls. That said, the tracker software is not just for tracking Santa and this is why last year Google released the Tracker as early as December 1st.
-
Performance on these kinds of questions is at best a discrete skill that can be improved through practice, eliminating their utility for assessing candidates. At worst, they rely on some trivial bit of information or insight that is withheld from the candidate, and serve primarily to make the interviewer feel clever and self-satisfied. They have little if any ability to predict how candidates will perform in a job.
-
The Guardian has published an open appeal to Tory and Lib Dem voters to vote Labour in Dundee West. I think that tells you all you need to know about the Red Tories and their priorities. It is also a new low in journalism even for the fanatic and increasingly desperate Severin Carrell, who is a total disgrace to his profession. The costs of publishing the Guardian ought to be counted against Marra’s election expenses: this is not journalism in any sense, merely a puff piece for a candidate.
-
Security
-
Defence/Police/Secrecy/Aggression
-
Nasir al-Din Shah, Shah of Iran from 1848-1896, sold Baron Julius de Reuter the right to operate all of Iran’s railroads and canals, most of the mines, all of the government’s forests, and all future industries. The famous British statesman Lord Curzon called it “the most complete and extraordinary surrender of the entire industrial resources of a kingdom into foreign hands that has probably ever been dreamed of.” Iranians were so infuriated that the Shah had to rescind the sale the next year.
[...]
Our rhetoric on Iran seems nonsensical: Do U.S. leaders actually believe Iran would engage in a first nuclear strike on Israel or the U.S., given that would lead to a quick and devastating retaliation from those well-armed nuclear powers?
Even conservative U.S. foreign policy experts know that’s incredibly unlikely. They’re not worried that we can’t deter a nuclear-armed Iran — they’re worried that a nuclear-armed Iran could deter us. As Thomas Donnelly, a top Iran analyst at the American Enterprise Institute, put it in 2004, “the prospect of a nuclear Iran is a nightmare … because of the constraining effect it threatens to impose upon U.S. strategy for the greater Middle East. … The surest deterrent to American action is a functioning nuclear arsenal.”
-
Finance
-
Fox News’ campaign of misinformation surrounding food assistance programs may be continuing to influence GOP legislation, as lawmakers in both Missouri and Kansas consider measures addressing “fake problems” within their state’s benefit programs.
Republican lawmakers in Kansas recently introduced legislation restricting where recipients of Temporary Assistance for Needy Families (TANF, formerly known as “welfare”) can spend their money and what they can buy. The bill would limit the daily spending allowance to $25 and ban recipients from using benefits at psychics and tattoo parlors. Another measure, introduced by the House GOP in Missouri, will similarly limit how recipients of the Supplemental Nutrition Assistance Program (SNAP, formerly knowns as “food stamps”) can use their benefits, prohibiting them from buying “steak, seafood, soda, cookies, chip[s], and energy drinks.”
-
PR/AstroTurf/Lobbying
-
There is nothing like a journalistic plane crash to inspire newsroom loudmouths to jump on their desks and lecture colleagues about the collapse of standards and crow that they’re such exemplars of the craft that never in a trillion years could they or their publication be snookered by a fabulist, a hoaxer, a dissembler or a liar.
-
The author accuses news outlets of doing exactly what he himself and the U.S. mainstream media in general does when reporting about foreign policy issues such as Ukraine: they “systematically [regurgitate U.S. propaganda, spread] lies, half-truths, and conspiracy theories.” The advantage they have is that they don’t need to translate anything. Apparently for Rohac an article written in Russian has to be Russian propaganda. It’s that simple: Russians are just not producing any honest journalistic content. This argument about texts being “directly translated from Russian sources” is not only weak, it is xenophobic.
-
Censorship
-
Nintendo’s never-ending desire to control how YouTubers review its games or do “let’s plays” has been laughable from the start. From the trust-destroying agreement YouTubers had to enter into in order to get access to visual content to the beauracratic nightmare individuals had to wade through just to get a video approved for monetization, the whole thing started off on messy footing. And the biggest issue in all of this: Nintendo still can’t seem to grasp that these YouTubers are giving the company free advertising. Gamers love the kinds of videos these YouTubers produce. They use them to make purchasing decisions, to become interested in new games, and to fuel word-of-mouth advertising that no trumped up ad campaign could ever possibly hope to achieve. Why make any of that more complicated by creating an approval system for the videos? And, more importantly, why take away the incentive for fans to promote your games by demanding a share of their YouTube revenue?
-
This seems to happen every political season. When he was a Presidential candidate, John McCain got annoyed at YouTube taking down political videos based on copyright claims. During the last Presidential election, a Mitt Romney TV ad featuring President Obama singing an Al Green song was taken down via a copyright claim. And now, 2016 Presidential candidate Rand Paul has discovered that his announcement speech from Tuesday morning has been taken down.
-
Privacy
-
The U.S. government started keeping secret records of Americans’ international telephone calls nearly a decade before the Sept. 11 terrorist attacks, harvesting billions of calls in a program that provided a blueprint for the far broader National Security Agency surveillance that followed.
For more than two decades, the Justice Department and the Drug Enforcement Administration amassed logs of virtually all telephone calls from the USA to as many as 116 countries linked to drug trafficking, current and former officials involved with the operation said. The targeted countries changed over time but included Canada, Mexico and most of Central and South America.
-
Rand Paul’s campaign kickoff just concluded with a rousing speech by the libertarian-leaning U.S. senator from Kentucky in which he promised that his first act as president would be to stop the NSA’s illegal spying on American citizens. He vowed to win the White House while clutching the Bill of Rights in one hand and the Constitution in the other.
-
Bill Binney, a former U.S. National Security Agency employee turned whistleblower, is on a mission to expose the agency’s domestic spying programs and violations of constitutional rights.
In an interview with AJ+’s Dena Takruri, Binney discusses why he thinks President Barack Obama is “violating the public trust” and what Americans can do to protect themselves from unwarranted surveillance.
-
The U.S. government started keeping secret records of Americans’ international telephone calls nearly a decade before the Sept. 11 terrorist attacks, harvesting billions of calls in a program that provided a blueprint for the far broader National Security Agency surveillance that followed.
-
The Drug Enforcement Administration (DEA), under approval from the top echelons of the Department of Justice, ran a secret, extensive phone metadata bulk collection program for over two decades, amassing billions of records, according to a new report published Tuesday in USA Today.
This database had previously been revealed to a lesser extent earlier this year, but neither its operational details nor its scope had been revealed until now.
-
Note that it actually makes sense to use a one-time pad in this instance. The message is a ten-digit number, and a one-time pad is easier, faster, and cleaner than using any computer encryption program.
-
Data brokers, which track browsing habits to sell to third parties, are not governed by any laws stating what can and can’t be done with the data. But they are not the same as hackers, who could theoretically access information about membership to porn sites. Vice said hackers would be more likely to sell the credit card information than release it online for no gain.
Neither brokers nor hackers have a vested interest in creating Thomas’s nightmare vision of a searchable porn-user database. But that doesn’t mean the data isn’t out there. Even a browser in incognito mode will send tracking information to data brokers that according to one privacy researcher is “all sitting in a database somewhere”.
Vice said that shouldn’t surprise internet users: “It’s a truth about the modern internet that just about anywhere you go, you’re being tracked.”
-
TrueCrypt’s relative clean bill of health last week has now spawned a new focus on existing alternatives to the open source encryption software, namely VeraCrypt and CipherShed.
-
ORG supporters are invited to our General Election Training run by ORG staff on how we can make an impact this election! We’ll give you all the knowledge you need to be confident and effective digital rights activist this election.
-
An Australian court has ordered internet service providers (ISPs) to hand over details of customers accused of illegally downloading a US movie.
-
Civil Rights
-
Hours after police removed an illicit bust of Edward Snowden from its perch in a Brooklyn park on Monday, artists replaced it with a hologram.
-
John Oliver’s Monday night interview of Edward Snowden — which in 24 hours has been viewed by 3 million people on YouTube alone — renewed all the standard attacks in Democratic circles accusing Snowden of being a traitor in cahoots with the Kremlin. What’s most striking about this — aside from the utter lack of evidence for any of it — is how identical it is to what Nixon officials said to smear the last generation’s greatest whistleblower, Daniel Ellsberg (who is widely regarded by Democrats as a hero because his leak occurred with a Republican in the White House).
-
The Intercept revealed last month that it is quite easy to be deemed a “suspected terrorist” at airports in the United States. A leaked checklist used by the Transportation Security Administration shows an expansive list of “suspicious signs” for screening passengers, including yawning, fidgeting, whistling, throat clearing and staring at one’s feet. All of these, according to the TSA, are considered behaviors that indicate stress or deception. Well now The Intercept has revealed who the program actually targets: not terrorists, but undocumented immigrants. Taking a five-week period at a major U.S. airport, The Intercept found that 90 percent of all those arrested were detained for being in the country illegally. Not a single passenger was arrested or suspected for ties to terrorism. The overwhelming detention of undocumented immigrants bolsters criticism that government screening programs have targeted passengers with racial profiling. We speak to the reporter who broke this story, Jana Winter.
-
As the economic landscape in China continues to shift, an awakening working class is demanding fair treatment and higher wages—and the movement is picking up steam.
The Associated Press on Monday highlighted the emerging resistance to workplace exploitation and authoritarian government policies that has steadily grown over the past four years, with numbers of strikers doubling annually since 2011 until they reached more than 1,300 last year.
-
The police department in Erie County, New York fought hard to prevent the New York Civil Liberties Union from obtaining records about its use of a controversial surveillance tool known as a stingray.
-
Internet/Net Neutrality
-
Following copyright threats from large media companies a Kiwi ISP has taken down its VPN service. Lightbox, MediaWorks, SKY, and TVNZ had threatened legal action against services that bypass geo-restrictions on sites such as Netflix and Hulu. Other ISPs offering similar products are currently standing firm.
-
Intellectual Monopolies
-
The peak lobby group for American pharmaceutical manufacturers has been given privileged access to negotiations for a major regional trade pact that could see the cost of medicines skyrocket in Australia.
Public health advocates and business groups are concerned that pharmaceutical giants will be able to advance their commercial interests in the once-in-a-lifetime pact through their seat at the negotiating table, while the details are kept secret from the Australian public.
-
The draft of the investment chapter published by Wikileaks last week outlines the controversial investor‐state dispute settlement mechanism which would allow foreign corporations to sue governments in offshore tribunals.
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- 2017: Latest Year That the Unitary Patent (UPC) is Still Stuck in a Limbo
The issues associated with the UPC, especially in light of ongoing negotiations of Britain's exit from the EU, remain too big a barrier to any implementation this year (and probably future years too)
- Links 7/1/2017: Linux 4.9.1, Wine 2.0 RC4
Links for the day
- India Keeps Rejecting Software Patents in Spite of Pressure From Large Foreign Multinationals
India's resilience in the face of incredible pressure to allow software patents is essential for the success of India's growing software industry and more effort is needed to thwart corporate colonisation through patents in India itself
- Links 6/1/2017: Irssi 1.0.0, KaOS 2017.01 Released
Links for the day
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day























 Content is available under CC-BY-SA
Content is available under CC-BY-SA