08.14.16
Posted in America, Patents at 11:01 am by Dr. Roy Schestowitz
How long before all lawsuits are filed by purely litigation firms?
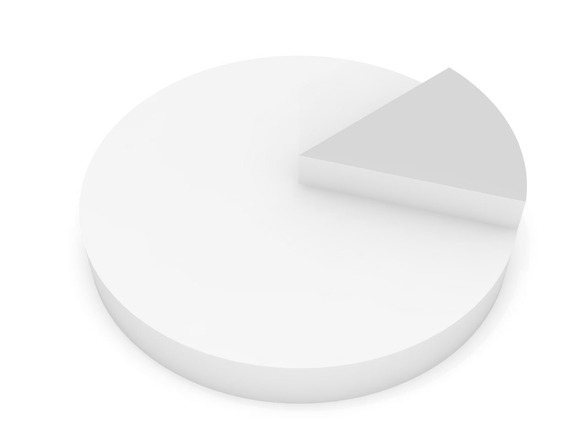
Summary: A look at the high proportion of patent lawsuits that are filed by entities that make nothing at all and thus serve no role whatsoever in innovation
TROLLS in the United States are a real problem because the USPTO sparingly grants software patents, unlike the EPO (for now).
Matt Levy, an opposer of patent trolls (for a front group, CCIA), has published in his own blog an article which was mentioned here before and refers to this trolls-friendly letter. Meanwhile, another front against trolls says: “Of the 27 patent lawsuits filed today, 22 were filed by patent trolls — 81%. It’s time for Congress to take action to #fixpatents!”
“If software patents were officially made and openly declared verboten in the US, a lot of patent trolls would vanish almost overnight as they depend nearly 100% on software patenting.”We recently saw reliable statistics which suggest that nearly 90% of technology patent lawyers are filed by patent trolls, or NPEs. One such firm (more like PAE or patent pool), RPX, made the news last week [1, 2] and turned out to be involved in patent shakedowns. To quote: “Under the terms of the agreement, RPX will receive the right to sublicense a limited number of companies to Kudelski Group patents. Kudelski will receive an upfront payment, mutual patent risk clearance, and a future transfer of patents from RPX.”
It is worth noting that much of the above is about software patents, i.e. dubious patents that may no longer be valid (because of Alice). If software patents were officially made and openly declared verboten in the US, a lot of patent trolls would vanish almost overnight as they depend nearly 100% on software patenting. █
Permalink
 Send this to a friend
Send this to a friend
Posted in America, Asia, Australia, Courtroom, Deception, Europe, Patents at 7:28 am by Dr. Roy Schestowitz
Speaking for their wallets (profit motive), misleading the public

Like the military-industrial complex and surveillance/enforcement in the age of drug wars, patent lawyers profit from endless feuds
Summary: How patent law firms are distorting the debate about software patents in hope of attracting business from gullible people who misunderstand the harsh (and worsening) reality of software patenting
Software patents should not exist in the EPO and the USPTO too is gradually cracking down on these, especially because of the US Supreme Court. It does not mean that patent law firms will take this defeat without a fightback.
Elaine Bergenthuin, “owner and managing partner of De Beer Attorneys” by her own description, has just got published this self-promotional puff piece in the South African media. It appeared there this morning and it’s not a good article, it’s more like marketing. “You cannot generally obtain patents for software in South Africa,” the article correctly states (see our Wiki page “Software Patents in South Africa”), but Bergenthuin is then finding some loopholes and promoting these, as if to say, “come to me, I’ll help you get software patents by working around the law.”
“Software developers don’t bother trying to get software patents in India, but patent law firms mislead them.”This is very typical. The press is full of this marketing spam. The local press all over the world has been reduced to advertisements in ‘article’ form.
Here is an example from India which is only days old. Software developers don’t bother trying to get software patents in India, but patent law firms mislead them. They have nothing to lose; the lawyers always get paid (irrespective of success rate), and it’s clear at whose expense.
Watch another new example that we found in the Indian press a couple of days ago. It speaks of some who “hold only a handful of patents and that too on software related to audio and keyboards.” So these are software patents. Why bother?
A site that’s preoccupied with promotion of software patents published one week ago an article titled “Hop on the Patent Prosecution Highway (PPH) via Australia”. One can guess who wrote it and it says: “While Australia isn’t usually considered a very important market since its population is so small and its manufacturing base is limited, it is our experience that there are a few US companies realising that prosecuting in Australia to use the PPH back into the US makes sense. There is always the option of filing in Australia first and using an Australian patent application as the priority application. However, one would need a foreign filing license from the US before doing so. A strategy could be to file a provisional in the US, receive the foreign filing license, and then file a standard (utility) application in Australia to take advantage of the expedited examination process at IP Australia to hop onto the Patent Prosecution Highway via Australia.”
“The press is full of this marketing spam. The local press all over the world has been reduced to advertisements in ‘article’ form.”Well, “prosecuting in Australia to use the PPH back into the US makes sense” only if software patents were actually potent there. They’re not. So once again we can see bad advice being given by the patent microcosm. What happened to journalism? Well, this isn’t journalism, it’s marketing. We recently wrote about the Patent Prosecution Highway (PPH) in relation to Australia, noting that the EPO — not just the USPTO — embraces these under Battistelli (even in rather dubious places with hardly any patents). The EPO is totally out of control when it comes to patent scope and it probably breaks the rules of the EPC when it comes to that. There is still a discussion about how this has been made possible in the first place. One person asks: “Has anything in the PPI, which must be done by the EPOff or the EPOrg, ever been done? I am thinking of the relations with the work-rules regulating organs of the host countries (Arbeitsinspectie, Gewerbeaufsicht,…)”
Well, Battistelli is “instructing the staff to sidestep part of the EPC,” one person responded. Here is the comment in full: “Yes, but what would the dispute be? According to 23(1) above, doesn’t it only arise if immunity has been claimed? Not sure that BB instructing the staff to sidestep part of the EPC would fall within that. He wouldn’t claim immunity (from what?) – he’s just doing his job.”
We worry that the EPO, especially under Battistelli, is now cooperating with the patent microcosm and just abandoning patent quality control (improving the “success” rate of patent law firms). See this new ‘article’ titled “Patents in Denmark”. “In general,” it says, “software as such is not patentable (Section 1(2) of the Patents Act). However, it is possible to patent software as part of a patent whose subject matter is a process. Further, software is patentable if it has the potential to bring about, when run on a computer, a further technical effect which goes beyond the normal physical interactions between the program and the computer.”
“There are only (formally) software patents in the US (maybe in Japan as well), but they’re being used by foreign entities outside the United States.”Actually, these are dubious claims that rely on Brimelow sidestepping the EPC. Things have become even worse in German courts and the German patent office. Here is a new example of software patents for German company in the United States. These patents have been weaponised and “[a]ccording to the complaint, the asserted patents generally relate to industrial control systems that employ advanced software to program, run, and visualize industrial control processes. In particular, the ‘226 patent relates to interfaces for connecting a computer to devices on multiple industrial control networks so that data may be communicated across the different industrial control networks to and from an application program running on the computer.”
These are software patents from the US. There are only (formally) software patents in the US (maybe in Japan as well), but they’re being used by foreign entities outside the United States. We sure hope that people will come to grips with the corrupting influence of patent law firms in this debate and also acknowledge that software patents bring nothing but negatives to society; they’re good only to patent lawyers and patent offices where the goal is to increase so-called ‘production’ as measured in terms of the number of granted patents. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Patents at 6:50 am by Dr. Roy Schestowitz
Also worth remembering is Microsoft’s active role in creating and bankrolling trolls that are overtly taxing Android/ChromeOS (GNU/Linux)

Yahoo! Blog from Sunnyvale, Creative Commons Attribution 2.0
Generic license (caption added by us, with Ballmer’s words)
Summary: Remains of Yahoo, which is effectively being liquidated, include software patents, but it’s not clear who will take over them and what will be done with them
Yahoo is a dead company and Yahoo‘s death is due to Microsoft’s intervention. Yahoo’s USPTO-granted software patents are on sale although they might not be worth much after Alice. It remains to be seen who takes these; maybe some Microsoft-backed consortium? Maybe some patent troll with “PAE” as a euphemism? This new article is titled “Next up in Yahoo’s closing down sale: The patent auction”. We can’t help but wonder who would be so foolish or overly hopeful… enough to attempt litigation with software patents in spite of this hostile atmosphere in the US courts. Well, even if the USPTO granted these patents, it does not mean they’re potent.
“We can’t help but wonder who would be so foolish or overly hopeful… enough to attempt litigation with software patents in spite of this hostile atmosphere in the US courts.”Speaking of Yahoo, a lot of patent news comes from there, so with the demise of Yahoo there will be less information. These couple of spammy articles/press releases from Yahoo [1, 2], for example, are quite revealing. Some companies are so boring that the only press releases they make public are about poor-quality software patents. The other article uses a buzzword, namely “Big Data”, in an attempt to sell proprietary software that will (supposedly) manage Intellectual Property [sic]. It surely won’t work as well as a human, but there are also some fools in suits with no scientific background who believe examination can be done by machines from start to finish. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 6:21 am by Dr. Roy Schestowitz

Contents
-
Desktop
-
The software I rely on daily includes LibreOffice Writer, Thunderbird, Audacity, SimpleScreenRecorder and Kdenlive. Accessibility applications I rely on include redshift-gtk and Workrave.
-
Audiocasts/Shows
-
Issue 21 of Linux Voice is nine months old, so we’re releasing it under the Creative Commons BY-SA license. You can share and modify all content from the magazine (apart from adverts), providing you credit Linux Voice as the original source and retain the same license.
-
Kernel Space
-
Over the years, many init systems have emerged in major Linux distributions and in this guide, we shall take a look at some of the best init systems you can work with on the Linux operating system.
-
Applications
-
Chrome Remote Desktop is a Linux remote desktop app that allows users to access any Linux computer remotely. It is developed by Google and is available for Linux systems also. It is very easy to use and let one handle computer remotely using Chromoting protocol developed by Google.
-
-
Sunflower is a twin pane, highly configurable, powerful and easy to use File Manager created for Linux with plugins support. It works with all desktop environments such as Gnome, Unity, KDE, Lxde, Xfce, Cinnamon, Mate, and others. It is open-source and developed using Python language, currently it is in active development and releasing stable versions, if you like this project then don’t forget to contribute this project in anyway you like.
-
The Inverse team is pleased to announce the immediate availability of SOGo v3.1.5. This is a minor release of SOGo which focuses on small new features and improved stability over previous versions.
-
The app uses the football-data.org API to provide past and live football scores, standings, upcoming fixtures, and player information. All major European football leagues are supported, including Premier League, La Liga, UEFA Champions League, and more.
Smaller leagues, as well as UEFA Europa League, are not supported, at least for now.s
-
Variety is an open-source wallpaper changer designed for Linux operating system, it comes with great features and easy to use. There are many wallpaper manager applications available which offers many features but Variety has its own way to get things done. It can display wallpapers from local sources or lots of various online sources, allows user to change wallpaper on a regular interval, and provides easy ways to separate the great images from the junk.
-
Variety is a wallpaper changer that can automatically download wallpapers from various sources, like Flikr, Wallhaven, Bing Photo of the Day, Unslash, Desktoppr, NASA’s Astronomy Picture of the Day, as well as a live wallpaper of the world sunlight map. It can also automatically fetch wallpapers recommended by other Variety users.
The app was updated recently with a new “safe mode” option, which can be used to avoid NSFW and sketchy images. This feature relies on user ratings, so it’s not perfect, at least until more users rate the wallpapers.
The option can be found in the Variety preferences, on the General tab.
-
Twitter is one of the most popular and massively used blogging services on the Internet today, with the ever increasing use of the this amazing social media platform, users are looking for Twitter desktop applications that can enable them perform blogging activities, send and receive messages directly from their Linux desktops.
-
A minor update to my glue script for building software with pdebuild and git-buildpackage. (Yes, still needs to get rewritten in Python.)
This release stops using the old backport location for oldstable builds since oldstable is now wheezy, which merged the backports archive into the regular archive location. The old location is still there for squeeze just in case anyone needs it.
-
Proprietary
-
-
-
A new stable version of Vivaldi, the web browser aimed at power users, was released today, and it includes custom themes, tab hibernation on Linux, enhanced privacy, and more.
-
-
Instructionals/Technical
-
Games
-
Honestly, I’ve never heard of this game before, so I can’t give an opinion about it, but I do think that its aesthetics and background score look pretty interesting. The creators clearly state they took inspiration from Limbo, but also some comparisons with Fran Bow can be made: besides the obvious fact that one of the lead characters is a little girl, the story is put in motion by an horrendous event in her house, as it’s told in the following link (check second paragraph).
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
-
-
-
-
-
-
-
-
-
-
-
It’s been over a year since I posted anything. That’s way too long. So what’s going on in the projects I care about lately?
[...]
QtSpeech has had some work done. The android and windows versions have been seeing some love lately. I’m optimistic that it can be included in an upcoming Qt release. Though I’m not sure why it hasn’t been included yet.
-
-
GNOME Desktop/GTK
-
I don’t quite remember when I read John Goerzen’s post about teaching a 4 year old to use the linux command line with audio on planet Debian. According to the byline it was published nearly 2 years before Noam was born, but I seem to remember reading it in the weeks after his birth when I was both thrilled at the prospect of teaching my kid to use the command line and, in my sleepless stupor, not entirely convinced he would ever be old enough.
-
-
-
-
-
-
Slackware Family
-
Red Hat Family
-
Finance
-
Fedora
-
-
-
Richard Jones at Red Hat has been working on bringing up RISC-V processor architecture support for Fedora.
For those who haven’t been paying attention to RISC-V, it’s an open-source instruction set architecture that is BSD licensed and is completely free and not encumbered by patents. LowRISC and SiFive are among the organizations working to bring RISC-V hardware to the real-world.
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
I’m Sylvia, an artist, illustrator and game developer from Germany. I’m a huge fan of the open source operating system Ubuntu and I love to paint animals.
The Ubuntu releases inspired me to create a series of illustrations, each illustration depicting an animal from a release, in chronological order. I’ve just completed 25 animals, starting with the Warty Warthog (Ubuntu 4.10) and finishing with the latest release, Yakkety Yak (16.10). All animals have been painted with my favorite open source software Krita.
-
-
Flavours and Variants
-
The Lubuntu team is ready to begin the migration process to LXQt, and one of the first parts of the migration is getting an image to move to. We have prepared the lubuntu-qt-desktop metapackage and we are ready for an image.
-
-
-
Need a tiny, $5 computer to build a robot that will bring you your slippers, initiate a massage chair session, and pour out your daily dose of bourbon?
The Onion Omega2 can do all that and more.
This tiny board is Arduino-compatible but also runs Linux natively. This means you can plug it in and get a command line or access the system via a desktop-like web interface. It has Wi-Fi built in and can be expanded to support cellular, Bluebooth, and GPS connections.
-
Phones
-
-
Android
-
Replicant 6.0 early work and associated efforts: At Replicant, things are moving again: Replicant is being updated from Android 4.2 to Android 6.0 by Wolfgang Wiedmeyer. The status and feedback takes place in the forums before it is reviewed and integrated in the official Replicant repositories. This work is currently being done for the Galaxy S 3 (I9300).
-
-
-
A new report from the World Economic Forum predicts that the underlying technology introduced by the virtual currency Bitcoin will come to occupy a central place in the global financial system.
A report released Friday morning by the forum, a convening organization for the global elite, is one of the strongest endorsements yet for a new technology — the blockchain — that has become the talk of the financial industry, despite the shadowy origins of Bitcoin.
“Rather than to stay at the margins of the finance industry blockchain will become the beating heart of it,” the head of financial services industries at the World Economic Forum, Giancarlo Bruno, said in a statement released with the report.
-
-
-
-
-
-
Events
-
Join us for 3 days this summer in Ann Arbor, Michigan, for the 2016 Midwest Drupal Summit and help make D8 the best version yet.
With the launch of Drupal 8, there’s a lot to be excited about in the Drupal community — and a lot left to contribute!
For this year’s Summit, we’ll gather on the beautiful University of Michigan campus for three days of code sprints, working on issues such as porting modules and writing or updating documentation. We will start around 10AM and finish around 5PM each day.
-
From 1 to 4 September 2016 the communities of KDE, Qt, FSFE, VideoLAN and KDAB join forces in Berlin for QtCon. The program consists of a mix of Qt trainings on day 1, unconference sessions, lightning talks and more than 150 in-depths talks on technical and community topics on days 2 to 4. Track topics range from KDE‘s Latest and Greatest, Testing and Continuous Integration and QtQuick to Free Software policies and politics, Community and Beyond code. Check out the program.
-
Web Browsers
-
Mozilla
-
Mozilla is giving $200,000 to Baroque Software to work on PyPy, specifically to implement support for Python 3.5. Eight other open source projects also shared $385,000 in the recent round of funding.
PyPy is a Python interpreter with an integrated JIT compiler that currently supports Python 2.7. The money from Mozilla will be used to implement the Python 3.5 features in PyPy. The money will be used over the coming year to pay four core PyPy developers half-time to work on the missing features, and on some of the big performance and cpyext issues.
-
Databases
-
The rivalry between database management systems is often somewhat heated, with fans of one system often loudly proclaiming that a competitor “sucks” or similar. And the competition between MySQL and PostgreSQL in the open-source world has certainly been heated at times, which makes a recent discussion of the pros and cons of the two databases rather enlightening. While it involved technical criticism of the design decisions made by both, it lacked heat and instead focused on sober analysis of the differences and their implications.
The transportation company Uber had long used PostgreSQL as the storage back-end for a monolithic Python application, but that changed over the last year or two. Uber switched to using its own Schemaless sharding layer atop MySQL and on July 26 published a blog post by Evan Klitzke that set out to explain why the switch was made. There were a number of reasons behind it, but the main problem the company encountered involved rapid updates to a table with a large number of indexes. PostgreSQL did not handle that workload particularly well.
-
-
Oracle/Java/LibreOffice
-
Education
-
Threading elements of the great educational experiments of Bauhaus and Roycroft Community models together with Pierre Levy’s modern definition of “collective intelligence,” La Scuola Open Source (The Open Source School) embodies the principles of the sharing movement. Its success hinges on cooperative work, co-design, shared skills, and an open source culture. The school’s 13 co-founders believe in the power of people’s collaborative qualities. Their unusual constitution is testimony to this.
I believe La Scuola Open Source has the capacity to extend from its origin in Puglia on the southern heel of Italy and inspire the acquisition of knowledge and educational development on a global scale. Recently, I talked with two of its co-founders — Lucilla Fiorentino and Alessandro Tartaglia — how digital artisans, creators, artists, designers, programmers, pirates, dreamers, and innovators are collaborating to create Italy’s most important service for social innovation and community development: education. Fiorentino and Tartaglia answered my questions in tandem.
-
Welcome to 42 US, a free (as in beer) coding school, which opened just last month. Even the optional dorms are free. (Good news: laundry is also free! Bad news: you have to pay the dorm $75 a week if you want two meals a day.) Admittedly, it sounds totally crazy.
-
Public Services/Government
-
The vast majority of companies are now realizing the value of open sourcing their software and almost all have done so for at least certain projects. These days Google, Facebook, Microsoft, Apple and almost every major company is releasing code to the open source community at a constant rate.
As is the case with many cutting edge developments it’s taking governments a while to catch on and understand the value in going open source. But now governments around the world are beginning to take the view that as their software is funded by the public, it belongs to the public and should be open for public use and are starting to define codified policies for its release.
[...]
The vast majority of code is still not classified and therefore, much higher levels of open sourcing are possible. While a bigger embrace of open source may seem like a risk, the real danger lies in small, overly-cautious implementation which is costing taxpayers by the day and making us all less secure.
-
Licensing/Legal
-
-
Linux kernel developer Christoph Hellwig has lost his case against virtualisation company VMware, which he had sued in March 2015 for violation of version 2 of the GNU General Public Licence.
The verdict was issued in the Hamburg District Court on 7 August.
Hellwig, who is the maintainer of the kernel’s SCSI sub-system, has said he would appeal. “I’m disappointed that the court didn’t even consider the actual case of reusing the Linux code written by me, and I hope the Court of Appeal will investigate this central aspect of the lawsuit,” he said in a statement.
-
Openness/Sharing/Collaboration
-
The British actor who played R2-D2 in the Star Wars films has died at the age of 81 after a long illness. Kenny Baker, who was 3ft 8in tall, shot to fame in 1977 when he first played the robot character.
-
Science
-
Our brains are apparently really good at divvying up heavy mental loads. In the decades since scientists started taking snapshots of our noggins in action, they’ve spotted dozens of distinct brain regions in charge of specific tasks, such as reading and speech. Yet despite documenting this delegation, scientists still aren’t sure exactly how slices of our noodle get earmarked for specific functions. Are they preordained based entirely on anatomy, or are they assigned as wiring gets laid down during our development?
A new study, published this week in Nature Neuroscience, adds more support for that latter hypothesis. Specifically, researchers at MIT scanned the brains of kids before and after they learned to read and found that they could pinpoint how the area responsible for that task would develop based on connectivity patterns. In other words, the neural circuitry and hookups laid down prior to reading determined where and how the brain region responsible for reading, the visual word form area, or VWFA, formed.
“Long-range connections that allow this region to talk to other areas of the brain seem to drive function,” Zeynep Saygin, lead study author and researcher at MIT’s McGovern Institute for Brain Research, said in a news release.
The finding squares with researchers’ hunch that connectivity is key, plus previous findings from studies done on ferrets. In those experiments, researcher manually re-wired the brains of the developing mustelids, rerouting the input wires from the retina to a region of the brain normally tasked with handling sound input. In response, that auditory cortex developed distinct functions involved with vision. Thus, it’s connectivity, not other intrinsic features of brain regions, that might explain functional divisions, the researchers speculated.
-
35 years ago (today), IBM launched the most influential commercial computer system of all time, the IBM PC 5150. Over the past three and a half decades, architectural descendants of this single machine have taken over the desktop, workstation, server, and even game console markets. And despite inroads from ARM-based smartphones, its digital descendants are still relied upon for just about all the heavy lifting in the computer industry.
On the anniversary of such a monumentally important computer, I thought it would be instructive to take a deeper look into the machine that started it all. How? By taking apart one of these bad boys on my trusty workbench, of course. And that’s exactly what you’ll see in the slides ahead.
-
Take a walk while I look inside your brain. Scientists have developed the first wearable PET scanner – allowing them to capture the inner workings of the brain while a person is on the move. The team plans to use it to investigate the exceptional talents of savants, such as perfect memory or exceptional mathematical skill.
All available techniques for scanning the deeper regions of our brains require a person to be perfectly still. This limits the kinds of activities we can observe the brain doing, but the new scanner will enable researchers to study brain behaviour in normal life, as well providing a better understanding of the tremors of Parkinson’s disease, and the effectiveness of treatments for stroke.
-
Health/Nutrition
-
America is facing a real crisis in regard to antibiotics resistant infections, and factory farming is one of the main reasons.
In May, the Walter Reed Army Institute of Research reported the first U.S. case of Colistin-resistant infection, involving a patient in Pennsylvania. Also that month, researchers at USDA and Health and Human Services reported finding Colistin-resistant E. coli in a pig intestinal sample. Because Colistin is a last resort drug for treating superbug (multi-drug-resistant) infections, these discoveries signal we are that much closer to what has been referred to as a post-antibiotic era, where people will die from once-treatable infections.
-
Marijuana advocates who hoped the cascade of states moving to legalize medical marijuana would soften the federal stance on the drug faced disappointment Thursday as the Drug Enforcement Administration announced it will keep marijuana illegal for any purpose.
Marijuana will remain a Schedule 1 substance under the Controlled Substances Act. Substances in Schedule 1 are determined by the Food and Drug Administration to have no medical use. States that allow marijuana for medical use or legalize recreational use remain in defiance of federal law.
The announcement to be published Friday in the Federal Register relaxes the rules for marijuana research to make it easier for institutions to grow marijuana for scientific study. The DEA currently authorizes just one grow facility in Mississippi.
-
Supporters of a saner marijuana policy scored a small victory this week when the Obama administration said it would authorize more institutions to grow marijuana for medical research. But the government passed up an opportunity to make a more significant change.
The Drug Enforcement Administration on Thursday turned down two petitions — one from the governors of Rhode Island and Washington and the other from a resident of New Mexico — requesting that marijuana be removed from Schedule 1 of the Controlled Substances Act. Drugs on that list, which include heroin and LSD, are deemed to have no medical use; possession is illegal under federal law, and researchers have to jump through many hoops to obtain permission to study them and obtain samples to study. Having marijuana on that list is deeply misguided since many scientists and President Obama have said that it is no more dangerous than alcohol.
-
Polio is back in Nigeria, just when the World Health Organization thought the virus might be gone completely. Two kids have been paralyzed by the virus for the first time in two years, the WHO announced today. Both live in northeastern Nigeria, where it has been hard to vaccinate kids because the area is controlled by terrorist group Boko Haram. The government is now preparing an emergency immunization program as researchers fear a possible outbreak.
-
The farming community is disappointed by the terms of the government’s draft budget proposal presented earlier this week. Some say that they feel betrayed, that the government has failed to keep promises made to the hard-pressed agricultural sector following a tractor march protest in the capital last spring. They intended to bring their protest, and their tractors, back to Helsinki to try again.
-
Security
-
Two top electronic security firms have discovered a new powerful malware suite being used to target just dozens of high-value targets around the world. The research shows that it was likely developed on the orders of a government engaging in cyber espionage.
The California-based Symantec has labeled the group behind the attack Strider, while Moscow-based Kaspersky Labs dubbed it ProjectSauron. Both are references to J. R. R. Tolkien’s Lord of the Rings, a nod to the fact that the original malware code contained the word “Sauron.”
-
The Web Proxy Auto-Discovery Protocol (WPAD), enabled by default on Windows and supported by other operating systems, can expose computer users’ online accounts, web searches, and other private data, security researchers warn.
Man-in-the-middle attackers can abuse the WPAD protocol to hijack people’s online accounts and steal their sensitive information even when they access websites over encrypted HTTPS or VPN connections, said Alex Chapman and Paul Stone, researchers with U.K.-based Context Information Security, during the DEF CON security conference this week.
-
A wave of denial of service (DDoS) attacks on state and city websites followed immediately after Anonymous delivered their statement. The group boasted taking down at least five sites, including www.brasil2016.gov.br, www.rio2016.com, www.esporte.gov.br, www.cob.org.br and www.rj.gov.br. They broadcast their exploits using the hashtags #OpOlympicHacking, #Leaked and #TangoDown, some of which were set up months ago.
-
There are a lot of different reasons why organizations choose to move to the cloud and many reasons why they do not. Speaking at a press conference during the Black Hat USA security event, security researcher Dan Kaminsky provided his views on what’s wrong with the Internet today and where the cloud can fit in.
“There’s a saying we have,” Kaminsky said. “There is no such thing as cloud, just other people’s computers.”
While the cloud represents a utility model for computing, Kaminsky also suggests that there are ways to use the cloud to improve overall security. With the cloud, users and applications can be isolated or ‘sandboxed’ in a way that can limit risks.
With proper configurations, including rate limiting approaches, the impact of data breaches could potentially be reduced as well. As an example, Kaminsky said that with rate limiting controls, only the money from a cash register is stolen by a hacker, as opposed to stealing all of a company’s corporate profits for a month.
-
-
ProtonMail is not vulnerable to the recently announced Linux TCP Vulnerability
-
A new and dangerous computer virus has been targeting Linux servers, its goal: to turn computer servers into Bitcoin miners. The attack is aimed at environments running the Redis NoSQL database, the virus is also able to probe the network interfaces of its hosts to propagate itself.
Approximately more than 30,000 servers running the Redis database are in danger due to the lack of an access password. The virus is named “Linux.Lady” and it was discovered first by the Russian IT-security solutions vendor Dr. Web. The company released a report on the virus, classifying it into the Troyan subcategory.
-
In 2013, when University of Birmingham computer scientist Flavio Garcia and a team of researchers were preparing to reveal a vulnerability that allowed them to start the ignition of millions of Volkswagen cars and drive them off without a key, they were hit with a lawsuit that delayed the publication of their research for two years. But that experience doesn’t seem to have deterred Garcia and his colleagues from probing more of VW’s flaws: Now, a year after that hack was finally publicized, Garcia and a new team of researchers are back with another paper that shows how Volkswagen left not only its ignition vulnerable but the keyless entry system that unlocks the vehicle’s doors, too. And this time, they say, the flaw applies to practically every car Volkswagen has sold since 1995.
-
The first affects almost every car Volkswagen has sold since 1995, with only the latest Golf-based models in the clear. Led by Flavio Garcia at the University of Birmingham in the UK, the group of hackers reverse-engineered an undisclosed Volkswagen component to extract a cryptographic key value that is common to many of the company’s vehicles.
-
A little-known feature of many modern smartphones is their ability to duplicate video on the device’s screen so that it also shows up on a much larger display — like a TV. However, new research shows that this feature may quietly expose users to a simple and cheap new form of digital eavesdropping.
Dubbed “video jacking” by its masterminds, the attack uses custom electronics hidden inside what appears to be a USB charging station. As soon as you connect a vulnerable phone to the appropriate USB charging cord, the spy machine splits the phone’s video display and records a video of everything you tap, type or view on it as long as it’s plugged in — including PINs, passwords, account numbers, emails, texts, pictures and videos.
-
Defence/Aggression
-
-
Aaron Driver was boarding a taxi outside his sister’s home in the small Canadian town of Strathroy, Ontario when armed law enforcement agents moved in to arrest him. Driver, 24, was known to local authorities as a prolific online supporter of Islamic State. He had previously been placed under government surveillance due to his social media postings and had received a judicial order in February banning him from use of the internet.
Acting on a tip that Canadian authorities say came from the FBI, police on Wednesday descended on the home of Driver’s sister on suspicion he was planning to carry out an imminent terrorist attack. In Driver’s possession were two explosive devices. As police approached, he detonated one device while sitting in the backseat of the taxi, before being shot. He died in the encounter, while his taxi driver escaped with minor injuries.
-
Word comes from Politico that Hillary Clinton is courting the endorsement of Henry Kissinger. No surprise. Kissinger and the Clintons go back a ways, to when Bill in the early 1990s sought out Kissinger’s support to pass NAFTA and to, in the words of the economist Jeff Faux, serve as “the perfect tutor for a new Democratic president trying to convince Republicans and their business allies that they could count on him to champion Reagan’s vision.” Hillary has continued the apprenticeship, soliciting Kissinger’s advice and calling him “friend.”
Still, Bernie Sanders, and Sanders supporters and surrogates, should use the Politico story to draw a line, making clear that they will withdraw their support of Clinton if Clinton accepts Kissinger’s endorsement. If Sanders stands for anything, it is the promise of decency and civil equality, qualities that he has worked hard to bestow on Clinton since the Democratic National Convention. By accepting Kissinger’s endorsement, Clinton wouldn’t just be mocking that gift. She’d be sending the clearest signal yet to grassroots peace and social-justice Democrats that her presidency wouldn’t be a “popular front” against Trumpian fascism. It would be bloody business as usual.
Kissinger is a unique monster. He stands not as a bulwark against Donald Trump’s feared recklessness and immorality but as his progenitor. As Richard Nixon’s aide-de-camp, Kissinger helped plan and execute a murderous, illegal foreign policy—in Southeast and South Asia, Southern Africa, the Middle East, and Latin America—as reckless and immoral as anything Trump now portends. Millions died as a result of his actions. Kissinger and Nixon threatened to use nuclear weapons, and, indeed, Kissinger helped inscribe the threat of “limited nuclear war” into doctrine. Kissinger, in the 1970s, not only dug the hole that the greater Middle East finds itself in, but, as an influential cheerleader for both the first Gulf War in 1991 and its 2003 sequel, helped drive the United States into that ditch.
-
While Khizr and Ghazala Khan expressed much needed moral clarity about Donald Trump, their testimony helps to further remove from national consciousness and justify the immorality of our bi-partisan government’s invasion and occupation of Iraq. A war that world-renowned political analyst, activist and author Noam Chomsky has called, not a “mistake” but “the worst war crime in this Century.” (“Noam Chomsky: 2003 ‘Invasion of Iraq is the Worst Crime of 21st Century,” sputniknews.com, 10-28-2015)
Three days after Khizr Khan’s powerful speech, Democratic presidential nominee Hillary Clinton, speaking in a church, distanced herself from her support of the 2003 invasion of Iraq, and turned morality on its head. She said to a Christian congregation, “Mr. Khan paid the ultimate sacrifice in his family, didn’t he? . . . And what have we heard from Donald Trump?,“ she continued. “Nothing but insults, degrading comments about Muslims, a total misunderstanding of what made our country great.” (“Donald Trump’s Confrontation With Muslim Soldier’s Parents Emerges as Unexpected Flash Point,” By Alexander Burns, Maggie Haberman and Ashley Parker, The New York Times, July 31, 2016) Never mind that Clinton herself is directly implicated in the unnecessary “ultimate sacrifice” of Khizr and Ghazala Khan’s son. Here, “what makes our country great” requires the all-encompassing moral universe to disappear for Iraqi children and mothers and fathers.
-
Transparency/Investigative Reporting
-
There are signals from Ecuador suggesting that Swedish prosecutors soon might interview Wikileaks editor in chief Julian Assange, in the country’s embassy in London – where he has been taking refuge for some four years.
From the Swedish prosecutor’s office (where everyone important seems to be on summer retreat) there are only vague comments. There are reasons to believe that the Swedes are in no hurry to get this done and over with.
As the case has dragged out in time, there seems to be some confusion in medias reports. To refresh our memory…
The Swedish case about sexual misconduct against Assange is very thin. There are reasons to believe that the case will be dropped altogether as soon as an interview has been conducted.
-
Sweden has made a formal request to Ecuador to interview WikiLeaks founder Julian Assange in Quito’s embassy in London, where he has been holed up for more than four years.
There was a standing offer from Ecuador to Sweden to conduct such an interview. Signs of a thaw in the impasse were reported last month.
A request from Sweden to the Ecuadorian attorney-general has met with a positive response, according to a published report.
“In the coming weeks a date will be established for the proceedings to be held at the Embassy of Ecuador in the United Kingdom,” according to a statement issued by Ecuador’s Foreign Ministry.
-
Environment/Energy/Wildlife/Nature
-
Amidst the cries of “protect our water, protect our land, protect our peoples,” Native Americans, ranchers and farmers are standing their ground along a highway in North Dakota. They are blocking the crews of Energy Transfer Partners — a Dallas-based company whose workers are protected by both police and armed, private security personnel — from accessing the site of the construction of the Dakota Access Pipeline.
The roughly 1,200-mile-long pipeline would transfer about a half million barrels of oil a day from North Dakota to Illinois. Opponents of its construction worry that a leak or rupture would spell disaster for not only the Standing Rock Indian Reservation, but for all communities along the Missouri River that depend on it for drinking and agriculture.
-
It took seven years of protests, sit-ins, letter writing, and, finally, a presidential review to prevent the Keystone XL oil pipeline from being built. Now, in a matter of months, America’s newest mega-pipeline—the Dakota Access Pipeline Project (DAPL)—has quietly received full regulatory permission to begin construction. Known also as the Bakken Pipeline, the project is slated to run 1,172 miles of 30-inch diameter pipe from North Dakota’s northwest Bakken region down to a market hub outside Patoka, Illinois, where it will join extant pipelines and travel onward to refineries and markets in the Gulf and on the East Coast. If that description gives you déjà vu, it should: The Bakken Pipeline is only seven miles shorter than Keystone’s proposed length.
-
Southern California is experiencing its worst smog in years this summer as heat and stagnant weather increase the number of bad air days and drive up ozone pollution to levels not seen since 2009.
Where pollution is worst, in the Inland Empire, hospitals and asthma clinics are reporting increases in patients seeking treatment for respiratory illness, their breathing difficulties exacerbated by the persistent heat and pollution.
Ozone, the lung-searing gas in smog that triggers asthma and other health problems, has exceeded federal standards on 91 days so far this year compared to 67 days over the same period last year, according to South Coast Air Quality Management District data through Monday.
In June, only four days had healthy air across the South Coast basin, which spans Los Angeles, Orange, Riverside and San Bernardino counties. In July, ozone levels violated federal health standards every day except July 31.
-
Firefighters on the Portuguese island of Madeira continued on Thursday to battle wildfires that have reached Funchal, the island’s largest city, killing three people and destroying over 150 homes, while the national government sought help to deal with nearly 200 blazes on the mainland.
Prime Minister António Costa planned to travel to Madeira on Thursday, and Portugal activated a European Union plan to get emergency assistance. Italy has already sent one firefighting aircraft. Madeira is the largest island in an archipelago in the Atlantic Ocean that lies about 360 miles off the Moroccan coast, and about 600 miles southwest of Lisbon.
The biggest fire on Madeira broke out on Monday and rapidly encroached on the residential outskirts of Funchal, home to about 110,000 people.
-
Last year, some of the biggest fires in recent history burned through parts of Indonesia.
The fires sent huge clouds of smoke across Indonesia and its neighbors. They also produced large amounts of carbon dioxide. Studies have linked increasing carbon dioxide levels to rising temperatures in Earth’s atmosphere.
For years, Indonesian farmers and businesses have cleared land for agriculture by setting fire to fields and undeveloped areas. This year’s fire season is to begin soon. But measures to limit the burning are now in place.
-
Asean countries agreed on contents within its roadmap to control the haze problem in a meeting on Thursday (Aug 11) to discuss the region’s next step to combat the perennial issue, but stopped short of exerting more pressure on Indonesia to take serious action against culprits of plantation fires.
“We work together to overcome any problem but we can’t bulldoze through… We must respect others’ sovereignty,” Malaysian minister of natural resources and environment Wan Junaidi Tuanku Jaafar said at a joint press conference with his Asean counterparts at the end of the one-day 12th conference of the parties to the Asean Agreement on Transboundary Haze Pollution (AATHP) in Kuala Lumpur.
-
It’s less than eight months into 2016 and the ominous day is already nearly upon us: Earth Overshoot Day, previously known as Ecological Debt Day, is a reminder of the enormous toll we take on the Earth.
The day marks the juncture when humanity’s demand for ecological resources exceeds what the planet can replenish annually. In 2016, it falls on Monday, which means people have already consumed an entire year’s worth of the world’s resources ― and we still have four months to go until the year’s end.
For the rest of 2016, we’ll be “living on resources borrowed from future generations,” as the World Wildlife Fund pointed out when we failed last year.
Troublingly, this year’s Overshoot Day is happening earlier than ever before.
-
Resistance against a new Bakken crude pipeline stepped up this week with the arrest of 12 people on Thursday near the Standing Rock Sioux reservation in North Dakota.
“They’re trying to lay a pipe across our water. They’re trying to poison our future,” said one of the people taking part in the action.
-
Authorities in North Dakota have arrested a dozen people protesting the $3.8 billion Dakota Access Pipeline.
Morton County Sheriff Kyle Kirchmeier said the 12 arrests as of Thursday evening were for disorderly conduct or criminal trespass.
He says some protesters encroached on a zone established for workers’ safety. Those arrested were brought to the Morton County Correctional Center.
-
Dakota Access—a subsidiary of Texas-based Energy Transfer Partners LP—has proposed a $3.7 billion, 1,168-mile pipeline that will transfer up to 570,00 barrels of crude oil per day from the North Dakota Bakken region through South Dakota and Iowa into Illinois.
The DAPL, also referred to as the Bakken pipeline, would cross the Missouri River less than a mile away from the Standing Rock Reservation that stands in North and South Dakota. The Missouri River, one of the largest water resources in the U.S., provides drinking water for millions of people.
The people of Standing Rock, often called Sioux, warn that a potential oil spill into the river would threaten the water, land and health of their reservation.
In DiCaprio’s tweet, the Oscar-winning actor and clean energy advocate said he was “standing with the Great Sioux Nation to protect their water and lands,” and linked to a Change.org petition that urges the U.S. Army Corps of Engineers to stop the construction of the Dakota Access Pipeline.
-
The Environmental Protection Agency’s (EPA) Science Advisory Board, a panel of independent scientists, is calling on the agency to revise last year’s much-maligned report that declared fracking to have “no widespread, systemic impacts on drinking water resources.”
-
Science advisers to the Environmental Protection Agency Thursday challenged an already controversial government report on whether thousands of oil and gas wells that rely on hydraulic fracturing, or “fracking,” systemically pollute drinking water across the nation.
That EPA draft report, many years in the making and still not finalized, had concluded, “We did not find evidence that these mechanisms have led to widespread, systemic impacts on drinking water resources in the United States,” adding that while there had been isolated problems, those were “small compared to the number of hydraulically fractured wells.”
The conclusion was widely cited and interpreted to mean that while there may have been occasional contamination of water supplies, it was not a nationwide problem. Many environmental groups faulted the study, even as industry groups hailed it.
But in a statement sure to prolong the already multiyear scientific debate on fracking and its influence on water, the 30-member advisory panel on Thursday concluded the agency’s report was “comprehensive but lacking in several critical areas.”
It recommended that the report be revised to include “quantitative analysis that supports its conclusion” — if, indeed, this central conclusion can be defended.
-
An Environmental Protection Agency panel of independent scientists has recommended the agency revise its conclusions in a major study released last year that minimized the potential hazards hydraulic fracturing poses to drinking water.
The panel, known as the Science Advisory Board (SAB), issued on Thursday its nearly yearlong analysis of a June 2015 draft EPA report on fracking and water. In a letter to EPA Administrator Gina McCarthy that accompanied the analysis, the panel said the report’s core findings “that seek to draw national-level conclusions regarding the impacts of hydraulic fracturing on drinking water resources” were “inconsistent with the observations, data and levels of uncertainty” detailed in the study.
“Of particular concern,” the panel stated was the 2015 report’s overarching conclusion that fracking has not led to “widespread, systemic impacts on drinking water resources in the United States.” The panel said that the EPA did not provide quantitative evidence to support the conclusion.
“The SAB recommends that the EPA revise the major statements of findings in the Executive Summary and elsewhere in the final Assessment Report to clearly link these statements to evidence provided in the body of the final Assessment Report,” the panel wrote to McCarthy.
-
-
This week the Center for Biological Diversity filed Freedom of Information Act requests with the federal agencies that oversee oil and gas leasing. The Aug. 11 filings came in response to a recent report by The Intercept that revealed several participants in a May protest of a fossil fuel auction in Lakewood, Colorado, were actually undercover agents sent by law enforcement to monitor the demonstration, and that they were relying on intelligence gathered by Anadarko Petroleum, a major Texas-based oil and gas producer.
-
A dramatic video shows a woman and a dog being rescued after their car got swept up by floodwaters.
Three men in a small boat battled to pull the woman from the convertible that had been swallowed by the flooded river in Baton Rouge in Louisiana.
The woman could be heard yelling: “Oh my god, I’m drowning.”
-
Finance
-
The US’s slow recovery from the 2008 recession is due to Republican policies on the local, state and federal level, according to a new study published by the left-leaning Economic Policy Institute (EPI).
-
Our current political chaos has a simple explanation. The economic system is driving environmental collapse, economic desperation, political corruption, and financial instability. And it isn’t working for the vast majority of people.
-
-
Hillary and Bill Clinton released their 2015 tax returns on Friday, showing they paid $3.6 million in taxes on adjusted gross income of $10.6 million.
The release appeared to be aimed at drawing renewed attention to Donald Trump’s refusal to release his own tax records.
-
Deliveroo, a popular on-demand restaurant food delivery startup in Europe, has raised another $275 million in funding, a Series E investment that we have heard from sources values the company at around $1 billion. This latest round is led by new investor, Bridgepoint, previous investors DST Global and General Catalyst, and also had participation from existing investor Greenoaks Capital.
Deliveroo says the investment will go into growing its service in both new and existing markets, where it’s now live in 84 cities. It’s also going to keep investing in its new initiatives. These include a new B2B remote kitchen service, RooBox, which gives restaurants access to delivery-only kitchens in key locations. Other new services have included an expansion into alcohol delivery.
Deliveroo, which is not confirming its valuation, has now raised $475 million to date.
This latest funding comes at a time when the startup is facing a lot of heat from others who are also targeting the higher, foodie end of the prepared food market (typical Deliveroo restaurants include artisanal pizza and burger joints, trendy Middle Eastern delis, and hipster donut bakeries).
-
Particularly for younger voters and voters with families, she has to capture their imaginations with a bold, simple, and common sense proposal to address one of the most critical financial and social problems currently facing a generation: the student loan crisis. And she needs to do so in a way that can do the most immediate good for the nation at large.
-
Big airport restrooms get messy fast. So, the management at Schiphol International Airport in Amsterdam came up with a clever solution: The airport etched an image of a black fly near the drain in the airports’ urinals. According to their measures, cleanliness increased by 80 percent. As New Republic put it, “It turns out that, if you give men a target, they can’t help but aim at it.”
-
In the summer of 1988 I worked in Lowell, Massachusetts painting houses.
The pay was lousy, the heat oppressive, and the work was exhausting. Many nights I would collapse, fully clothed, on my mattress on the floor of the dingy, mouse-infested apartment I rented.
But before I hit the sack, there was one thing I usually looked forward to: your Superbar (now defunct). For about $3.00 I could get my fill of salad, fruit, Mexican food, and pasta.
And that’s the only reason I’m writing you today, Wendy’s. I have nostalgic feelings for your SuperBar, even though I now know it’s tainted. But I’m offering you a heads up anyway: the Coalition of Immokalee Workers (CIW) is coming for you, and you will lose.
-
Evidence suggests that human rights treaties provide a reputational shield for companies to invest in the worst rights-violating countries.
-
The latest response to discrimination and police brutality is renewed calls to #BankBlack and bring economic empowerment to struggling communities.
-
What does Donald Trump have to hide? The New York Times interviewed tax and real estate experts and reports that it’s likely the billionaire and Republican presidential candidate pays zero taxes – legally – taking full advantage of the loopholes available to the superwealthy.
The previous nine Republican nominees have released their tax information – it’s a routine request. Mitt Romney balked about releasing his federal returns, understandably since they showed he paid about 14 percent of his income in taxes, well below the burden shouldered by everyday folks the U.S.
-
Despite the vast differences between Donald Trump and Hillary Clinton, there were some striking similarities between the economic speeches they delivered this week. They both spoke in Michigan, where they both talked a lot about manufacturing, with both of them insisting that they would obtain fairer trade deals.
-
-
AstroTurf/Lobbying/Politics
-
In 2007, Trump was suing a reporter who exposed unflattering facts about his true level of wealth. The Washington Post reports on a 2007 deposition, related to Donald Trump’s failed lawsuit over the expose, in which he was nailed to a series of “falsehoods and exaggerations” remarkable in just how pointless and stupid they were.
-
A report in Politico describes the various things Ms. Clinton has said over the past year with respect to her e mail usage while serving as Secretary of State. It then contrasts her statements with FBI Director, James Comey’s testimony before the House Benghazi Committee in early July. Among other things, Mr. Comey contradicted Ms. Clinton’s assertion (a) that while serving as Secretary of State she used only one device (he said she used four), (b) that she returned all work-related e mails to the state department (he said thousands were not returned), and (c) that she did not e mail “any classified material to anyone on my email” (Comey said “there was classified material emailed.”)
When Ms. Clinton was speaking to a convention of black and Hispanic journalists in Washington on August 5 2016, the e mail question once again presented itself. Ms. Clinton asserted that she did not lie to the FBI (which no one has disputed since no one knows what she said to the FBI) but then made a convoluted explanation that introduces us to the new use of the word “short circuit.” She told the assembled journalists: “What I told the FBI-which he [Comey] said was truthful-is consistent with what I have said publicly.” That, of course, seems to be untrue when considered in the context of Mr. Comey’s testimony before the Congressional Subcommittee. Continuing her explanation to the assembled journalists she said: “I may have short circuited, and for that, I will try to clarify.” Here follows an example of how those two words can be used in common situations in which readers may, from time to time, find themselves.
-
Hey everyone, we need help looking for a friend of ours. We got into an argument; we said “Pokemon is the only video game that could translate to the real world,” and he said, “No, you totally could make Donkey Kong into a real-life game,” and the last time we heard from him, he was trying to rent a gorilla and a bunch of barrels and have them delivered to the top of Trump Tower. Any assistance would be greatly appreciated, thanks!
Meanwhile, on the ground, more emails spell more trouble for Clinton after a new crop show some uncomfortable closeness between her team at State and the Clinton Foundation. But she got some good news when a ton of Republicans and independents joined her team.
-
Officials have acknowledged that the Russian hackers gained access to the Democratic Congressional Campaign Committee, which is the fund-raising arm for House Democrats, and to the Democratic National Committee, including a D.N.C. voter analytics program used by Mrs. Clinton’s presidential campaign.
But the hack now appears to have extended well beyond those groups, and organizations like the Democratic Governors’ Association may also have been affected, according to Democrats involved in the investigation. However, in a statement Thursday, the governors association said it “was informed that our analytics data was not compromised as part of the D.N.C. breach that affected the Clinton campaign.”
The group added that “we have no reason to believe that any D.G.A. emails were compromised by the D.N.C. breach.”
-
It seems like some Hillary Clinton supporters are now fully on-board with the time-tested mafia-favored strategy of “kill-the-guy.” Democratic strategist Bob Beckel, referring to Wikileaks founder Julian Assange, told a Fox Business host panel that “a dead man can’t leak stuff,” and that someone should “illegally shoot the son of a b*tch.” These comments come after the famed whistle-blower implied that 27 year-old DNC staffer Seth Rich, recently (and mysteriously) murdered in Washington DC, was a Wikileaks source connected to the DNC email scandal.
-
Trump’s buffoonery is so outrageous, you just couldn’t make this stuff up. He may have topped himself in last night’s performance at his rally in Sunrise, Florida, when he went on about how horrible it was that Hillary Clinton allowed the Orlando terrorist Omar Mateen’s father to sit behind her at one of her rallies this last week.
“When you get those seats, you sort of know the campaign, so when she [Hillary Clinton] said, ‘Well we didn’t know’…They knew!” Trump shouted. “Wasn’t it terrible when the father of the animal that killed the wonderful people in Orlando was sitting with a big smile on his face?” Trump turned to the people behind him. “How many of you people know me? A lot of you know me!”
And here is the punchline. Disgraced animal ex-congressman Mark Foley was sitting right behind Trump at his rally, and even raised his hand to say that yes, he knows Trump. Mark Foley was a republican congressman from 1995-2006, but had to resign after he was caught sending explicitly sexual emails and instant messages to teenage boys. He and Trump have been chums since 1987.
-
The hacker or hackers known as Guccifer 2.0 on Friday claimed credit for a new leak of information, this time from the Democratic Congressional Campaign Committee, writing on their blog, “It was even easier than in the case of the DNC breach.”
Guccifer 2.0 already claimed responsiblity in June for three document dumps from the DNC, or Democratic National Committee, servers. The separate hack of the Democratic Congressional Campaign Committee, or DCCC, meanwhile, was first reported in late July.
The newly published documents include “cellphone numbers and other personal information of nearly 200 current and former congressional Democrats,” as the Wall Street Journal reported; they also appear to include “shared passwords for the committee shared accounts to various news services, Lexis, and a federal courts public access system called PACER,” NBC News adds.
Further, they include “what purports to be documents stolen from the computer of Nancy Pelosi, the highest-ranking Democrat in Congress,” as the International Business Times reports.
The hacker continues: “As you see the U.S. presidential elections are becoming a farce, a big political performance where the voters are far from playing the leading role. Everything is being settled behind the scenes as it was with Bernie Sanders.”
“I wonder what happened to the true democracy, to the equal opportunities, the things we love the United States for. The big money bags are fighting for power today. They are lying constantly and don’t keep their word. The MSM [corporate media] are producing tons of propaganda hiding the real stuff behind it. But I do believe that people have [the] right to know what’s going on inside the election process in fact.”
-
Now that the Democratic and the Republican Party conventions are over, the U.S. presidential campaign is entering its last phase before the actual vote in November. Normally this should the point at which each party is very internally united and focusing on presenting its own program and attacking the opponent. However this time around, it seems each party continues to be more divided than ever. More and more Republicans are defecting from Donald Trump. And on the Democratic side, the debate is still raging about who supporters of Bernie Sanders should vote for in November. With us to present his analysis of the post-conventions and the U.S. elections, is Michael Hudson. Michael is a distinguished research professor of economics at the University of Missouri Kansas City. His latest book is “Killing the Host: How Financial Parasites and Debt Bondage Destroy the Global Economy.”
-
The NRA has spent $6 million in TV ads on behalf of the Republican presidential candidate, which is $6 million more than the Trump campaign has spent on itself. (A super PAC, Rebuilding America Now, claimed in June to have $32 million in commitments from four donors, but has only spent $5 million on ads to date. Casino magnate Sheldon Adelson once made a pledge to create his own $100 million super PAC, but as of July has not followed through.)
-
Hillary Clinton is the first woman ever to get the presidential nomination from a major political party in the history of the United States. This is, of course, a historic, and long overdue, moment. For many feminists, the nomination is a pretty straightforward, unambiguous victory for women and cause for celebration. For others, however, it’s complicated.
Of course, no feminist would defend the uninterrupted male lineage of the presidency. For feminist critics of Clinton, the problem lies not in her gender but in her track record, policies and positions, many of which have had a less than liberating effect on women.
As a feminist, I find myself moved, from time to time, when I think of how hard so many people have fought over the generations to make such a nomination possible. The undeniable sexism, misogyny and double standards Clinton has faced (though not on a structural level) occasionally fill me with a sense of compassion, solidarity, “get it girl” camaraderie and pride.
-
Merriam-Webster defines sacrifice as “the act of giving up something that you want to keep especially in order to get or do something else or to help someone.” Trump was not able to name one true sacrifice. Trump has only and always taken for himself.
In the past week, Trump got away with another whopper. After dominating the news cycle for 36 solid hours with his ridiculous claim that President Obama is the founder of Islamic State, he chastised the media for not recognizing that he was being “sarcastic.”
He clearly doesn’t know the meaning of the word.
He could have said he was being silly, ridiculous or unserious, but sarcastic? Sarcasm requires that the words used convey a meaning opposite to what the speaker truly believes or means. Had Trump said, “Obama is the greatest president in world history,” the media would immediately understand that he was being sarcastic because so much of what he has said indicates the true disdain in which he holds the president.
-
Pulitzer Prize-winning reporter James Grimaldi of The Wall Street Journal, who has covered the Clinton Foundation for years, looks at the relationship between the Clinton Foundation and the State Department during Hillary Clinton’s time as secretary of state, and what it would be if she became president. Newly released State Department emails include exchanges between top members of the Clinton Foundation and Clinton’s top State Department advisers, including Huma Abedin and Cheryl Mills. The FBI reportedly wanted to investigate the Clinton Foundation earlier this year, but US Attorney General Loretta Lynch pushed back.
-
Echoing those promises, a shadowy group calling itself “Better For America,” funded by Mitt Romney associate John Kingston III, has been doing prep work for that unnamed candidate.
On August 8 the suspense, such as it was, came to an end. The candidate is David Evan McMullin, a name unfamiliar to voters but well-known on Capitol Hill. Starting as an adviser to congressional Republicans on national security issues, he rose to the position of GOP House policy chief. Now he’s running for president.
-
Members of Congress do not have time for this responsibility when they are spending so much of their workday asking for money and implying agreement with the demands of the “monied interests,” to use Thomas Jefferson’s phrase.
This is why Congressman Jolly introduced the “Stop Act,” which would ban all federally-elected officials from directly soliciting donations. Members of Congress can attend fund-raisers but others would have to ask for the money. No more direct telephone calls to the “fat cats” for checks. So far he only has nine co-sponsors for his bill.
Congressman Jolly says this is not “campaign finance reform,” it is “Congressional reform,” adding “members of Congress spend too much time raising money and not enough time doing their job. Get back to work. And do your job.”
Hey America! No more withdrawal cynicism. Shaping up or shipping out your members of Congress can be our great national civic hobby! There are plenty of opportunities for improvement and it could be lots of fun. Don’t forget there are only 535 of them and they put their shoes on every day like we do!
Start small and build. Announce to your lawmakers with a letterhead – “Congress Watchdogs from the xxx Congressional District. The people want you to do your jobs!” The benefits of this effort are better lives and livelihoods for all Americans.”
-
Right now I am working to build such a WSDE with my Rhode Island Media Cooperative (RIMediaCoop.org). On the front end, it is intended to be a news aggregator for progressive/leftists, particularly Sanders supporters, that brings together RSS feeds from various news websites that are willing to be anti-imperial and critical of the Democratic Party, such as RT, TeleSur, PressTV, CounterPunch, and a few other favorites. This is augmented by original content from local media creators (actors, filmmakers, artists, writers) that effectively showcases material for potential clients.
On the back end, the intention is to get enough members who want to go to our local healthcare exchange, HealthSourceRI, to buy a small group insurance plan that would be complimented with a health savings account (HSA) to pay for expenses like copays and deductibles. We also would work on retirement by having a meeting to select a financial institute with which we would all open individual retirement accounts (IRAs). After a year of paying into the institute, say 20 people putting in $1,000 each, you have people with $20,000 worth of leverage that can be utilized when cosigning a loan for cooperative business infrastructure. This method can also be utilized, by the way, with the aforementioned small businesses that would transition to a cooperative.
Wolff has created here a schematic that uses the culture shift from Keynesian to neoclassical economics in public policy to the advantage of the working class. It is meeting neoliberals like Gov. Raimondo on their turf and using free markets and deregulation to build a new society from where the old has absconded their responsibilities. The neoliberal state is the exoskeleton in which a WSDE economic order can grow until it is ready to burst out of that shell and give way to the withering of the state. And this is because he has effectively created a dialectical antithesis of a union organizing drive while keeping democratic control central.
This year is the 80th anniversary of the start of the Spanish Civil War, an event that has reached a fetishized level of adulation on the Left for reasons that are beyond the scope of this discussion. Yet in all the debate that occurs over who is responsible for the fall of the Republic, there is, objectively speaking, a failure to account for how the Republic survived. It was the Mondragon cooperative, founded by Basque Father José María Arizmendiarrieta Madariaga, which came about under Franco’s rule that serves as the model Wolff has adopted for this project. The corollary of that story is that such a movement must have within its orientation room for those who are not leftists. So too must things be here in America. By creating full employment, we create far less pressure on the working class, the primary engine of reactionary chauvinism driving the Trump base. Simultaneously, we begin to have the conversations with white workers that politically educates them about chauvinism with what Fr. Madariaga would have called grace.
Putting it another way, conventional wisdom in Providence is that you don’t vote for politicians, you buy them. In that vein, why not get the best democratic socialism money can buy and cut the middleman, the state, out of the process like they wish to be?
-
Video of the comments from NBC News showed that Trump then accused the media of intentionally distorting his words, pointing at the assembled press corps and telling the crowd, “these people are the lowest form of life.”
As his supporters cheered, the candidate then executed another half pivot. “They are the lowest form of humanity!” Trump bellowed. “Not all of them, they have about 25 percent that are pretty good actually, but most of them.”
The meandering, jokey way Trump speaks, riffing on subjects like a stand-up comic working out his material live on stage, makes the task of reporting his comments unusually challenging.
-
Newly released emails from Hillary Clinton’s tenure as secretary of state raise questions about the nature of the department’s relationship with the Clinton Foundation.
Judicial Watch, a conservative watchdog group, released 296 pages of emails from the Democratic presidential nominee, including 44 that Judicial Watch says were not previously handed over to the State Department by Clinton. The emails, many of which are heavily redacted, raise questions about the Clinton Foundation’s influence on the State Department and its relations during her tenure.
-
-
Bernie Sanders bore down on Donald Trump’s economic agenda in a series of tweets on Friday morning, calling him “the poster child of failed trade policies.”
The social media take-down began with Sanders posting a link to a Washington Post story from earlier this week, which revealed how a “little-noticed provision in Donald Trump’s tax reform plan has the potential to deliver a large tax cut to companies in the Republican presidential nominee’s vast business empire.”
-
-
Hillary Clinton may not have heeded progressives’ call to clearly say she’ll urge the White House and her fellow party members to oppose a “lame-duck” vote on the Trans Pacific Partnership, but Sen. Bernie Sanders (I-Vt.) has done just that, calling on Democratic Congressional leadership to publicly oppose a post-Election Day vote on the “job-killing trade deal.”
-
-
Daily newspaper Dagbladet has tracked $89.6 million of contributions back to Norway. Foreign Minister Børge Brende violated the government’s own policies by handing $3.57 million from the foreign aid budget to the Clinton Foundation, according to an internal memo.
The government and the Norwegian Agency for Development Cooperation both split up donations into different channels of the Clinton Foundation in an attempt to make each contribution look smaller than it was.
-
Former President Bill Clinton received $5.6 million in fees from a Dubai-based firm that teaches Sharia law through a network of more than 100 schools worldwide.
Clinton served as the honorary chairman of the company GEMS Education from 2011 to 2014, the Daily Caller reported this week, citing Clinton’s federal tax returns.
GEMS Education teaches Sharia law in over 100 schools around the world, including in the Middle East, Asia, and Africa. One of the company’s schools, located in Jeddah, Saudi Arabia, taught 1,600 students in 2013. Saudi Arabia is known for enforcing Wahhabism, a fundamentalist view of Islam that strictly adheres to Sharia law.
Sharia law is an Islamic legal system that many in the West believe violates human rights and represses women and various minority groups.
-
Labour MPs are appealing to David Miliband to return to UK politics in a desperate bid to oust Jeremy Corbyn .
Senior backbenchers want Miliband, who quit politics to run a charity in the US, back here as quickly as possible.
And they say one possible route would be for him to stand in the Batley and Spen seat left empty by the killing of Jo Cox.
No date has been set for a by-election but rumours are growing that the solid Labour seat would be ideal for Miliband.
-
Censorship/Free Speech
-
Using access-to-information laws, The Free Press pushed to obtain the until-then-unknown “draft” of London’s business case for building the single biggest project in London history, a rapid transit system.
But city officials, who had discretion to make it completely public, opted to redact all or part of nearly half its 46 pages, further angering Londoners who remain upset over a confusing pivot by city hall to drop the push for light rail.
Mayor Matt Brown, whose stated pledge for transparency has at times clashed with his actions, drew criticism, perhaps unfairly, over the staff-dictated censorship.
-
The gunman creeps to a pillar supporting a skyscraper. A man filming seems to shake when the first shot is fired. Panicked words sputter in the background.
-
-
-
-
Privacy/Surveillance
-
Just over a week ago, at the BlackHat hacker convention in Las Vegas, Ivan Krstić, Head of Security Engineering and Architecture at Apple gave a talk entitled “Behind the scenes of iOS Security,” the slides of which are available here.
It’s a historic talk for a couple of reasons. First, Apple is traditionally very secretive about how it technically does security on its devices. Apple also announced its first bug bounty program. So far, so newsworthy.
But something else happened at that talk. Unbeknownst to the presenter or anybody in the audience, Apple just reopened the “Going Dark” dispute between the FBI and the privacy community, and it turned the entire dispute on its head. In the cold light of day, I suspect Apple, the US government, and privacy activists are going to be rather unhappy when they digest the sobering implications of the talk, though they will likely be upset for entirely different reasons.
-
Facebook will disable the ad-blocker’s blocker blocking
The back-and-forth between Facebook and ad-blocking software companies has become almost farcical at this point: After Facebook said it would block the use of ad blockers, the leading ad-blocking company announced that it will block the use of Facebook’s ad-blocker blocker. And now Facebook says it is rolling out a fix that will disable the ad-blocker’s blocker blocking.
As humorous as this cat-and-mouse battle may seem, there is a serious principle at stake for Facebook. If it can’t reliably ensure that users are seeing its advertising, then the $1 billion it currently makes on desktop ads is potentially in jeopardy, and questions might also be raised about its ability to display ads on mobile too, which is a $5-billion business.
-
Data thieves used a massive “botnet” against professional networking site LinkedIn and stole member’s personal information, a new lawsuit reveals.
The Mountain View firm filed the federal suit this week in an attempt to uncover the perpetrators.
“LinkedIn members populate their profiles with a wide range of information concerning their professional lives, including summaries (narratives about themselves), job histories, skills, interests, educational background, professional awards, photographs and other information,” said the company’s complaint, filed in Northern California U.S. District Court.
“During periods of time since December 2015, and to this day, unknown persons and/or entities employing various automated software programs (often referred to as ‘bots’) have extracted and copied data from many LinkedIn pages.”
It is unclear to what extent LinkedIn has been able to stymie the attack. A statement from the firm’s legal team suggests one avenue of penetration has been permanently closed, but does not address other means of incursion listed in the lawsuit.
-
One of the most famous quotes about the web says that “the Net interprets censorship as damage and routes around it.” But what about surveillance? Is it possible to make the internet route around spying?
In the last few years, especially after revelations of pervasive monitoring by the NSA and its British sister spy agency the GCHQ, some countries, Brazil being the most vocal, have publicly announced their intentions to avoid sending internet traffic to the US and the UK in an effort to dodge surveillance.
As it turns out, all internet pipes lead to surveillance. Or, at least, it’s really hard—if not impossible—to avoid routing web traffic through surveillance states like the United States, according to a recent paper by a group of Princeton University researchers.
-
All he wanted was to disable a device in his car: An always-on, net-connected “helper” that provides the car’s driver with app connections, turn-by-turn navigation, and roadside assistance… at the expense of personal driving data. Similar devices track how fast you’re going, how hard you ride the brakes, even your final destination. And all that info gets sent back to the manufacturer. Scannell wanted out. Unfortunately, it was easier said than done.
You see, Scannell is a security guy. And, while Scannell thought these features of the Car-Net system in his new Volkswagen Golf were pretty neat, for him the system was a lot more than the “partner” that VW advertises. But he’s been in privacy for years. In fact, it’s literally his job — he’s an adviser for security start-ups. And he knows all too well how simple it is to hack into a system with an open internet connection. For him, Car-Net wasn’t a helper. It was an opening for companies to spy on him. For a hacker to take control over his steering wheel. To find himself in a potentially dangerous situation.
It’s a reality that is present in basically every single new car that hits the market these days. Our cars are all waking up and coming online. The companies that manufacture them are filling each one full of hundreds of sensors that capture endless amounts of data about us and how we drive. It’s the last bastion of consumer information.
And just like your mobile phone, which has been spying on you for years, your car is not your friend.
-
ANONYMITY ENGINE and gateway to the dark web Tor has announced what it calls a “social contract” with its users, guaranteeing that the group won’t install backdoors or other nasties.
Tor, formerly an abbreviation of The Onion Router, actually received a great deal of the money that keeps it alive from the US government (although not the NSA obviously) and the Tor Social Contract should act as further reassurance that there is no conflict of interest.
The organisation is already licking its wounds after one of its developers, Jacob Appelbaum, was forced to step down in June amid allegations of sexual misconduct.
Meanwhile, the FBI is said to have cracked Tor using students with funding from the US Department of Defence. That’s a lot of government organisations at odds.
-
If you expect text messages privately sent to others to not be used against you in court, you might need to tweak that expectation in a big way, if a new ruling from the Ontario Court of Appeal sets a future precedent, reports Vice.
The case at hand centers around Nour Marakah and Andrew Winchester, both of whom authorities charged with gun trafficking. Through an investigation launched against Winchester sometime in 2012, law enforcement learned that he legally purchased 45 firearms during a six-month span, only to turn around and illegally sell them.
-
OpenPGPjs is the world’s most popular JavaScript PGP email encryption library and is used by millions of end users and hundreds of developers.
-
In brief, Home Assistant is a Python-based tool that provides a single web interface for a wide range of individual IoT devices. Freitas’s contribution is a network configuration that routes Home Assistant’s web interface over a Tor Hidden Service (so that it can only be accessed by a Tor-enabled browser via a special .onion domain name).
-
The US National Security Agency (NSA) has helped German investigators to decipher coded messages sent by the Daesh jihadist group’s masterminds to the perpetrators of recent terror attacks in Bavaria, local media reported Saturday, citing sources close to the probe.
-
According to chats with the IS affiliate, the Wurzburg attacker, 17-year-old Riaz Khan Ahmadzai, who injured five people with an axe and a knife on a train on July 18, was initially supposed to drive a car into a crowd. The plan was later abandoned because the minor didn’t have a driving license, and Ahmadzai said he would attack commuters on a train instead.
-
Remember, of course, that much of the planning and communications for the Paris attacks last year were done without encryption, and in fact much of the planning was done fairly out in the open with little effort to mask what was happening. Of course, that won’t always be true — and certainly it’s quite likely that people are plotting all sorts of nasty stuff with encryption — but even then that doesn’t actually result in law enforcement “going dark” as they’d have you believe. First of all, encryption is still difficult to use and easy to mess up. In fact, most reports suggest that ISIS is pretty bad about its opsec when it comes to encryption. And, even if they are successfully using encryption, they still leave plenty of other breadcrumbs for law enforcement and the intelligence community to track.
-
Civil Rights/Policing
-
How many children are Tasered by school police officers? It’s hard to tell. This investigation found at least 84 incidents of children being Tasered by school police — and that number is probably a huge underestimation, because there is no organization that tracks use of Tasers in schools.
-
Children are being Tasered by school-based police officers. No one knows how often it’s happening or what impact it’s having on students.
-
Privately operated government prisons, which mostly detain migrants convicted of immigration offenses, are drastically more unsafe and punitive than other prisons in the federal system, a stinging investigation by the US Department of Justice’s inspector general has found.
Inmates at these 14 contract prisons, the only centers in the federal prison system that are privately operated, were nine times more likely to be placed on lockdown than inmates at other federal prisons and were frequently subjected to arbitrary solitary confinement. In two of the three contract prisons investigators routinely visited, new inmates were automatically placed in solitary confinement as a way of combating overcrowding, rather than for disciplinary issues.
The review also found that contract prison inmates were more likely to complain about medical care, treatment by prison staff and about the quality of food.
-
On Thursday the U.S. Department of Justice inspector general released a scathing report on the Federal Bureau of Prisons’ monitoring of “contract prisons,” a shadow network of private, for-profit prisons that hold about 11 percent of the nation’s 193,000 federal prisoners.
-
-
Human sensibility has been given another sound beating with the leak of 2,116 incident reports from Australia’s remorseless detention camp on Nauru. The reports total some 8,000 pages covering the period of May 2013 to October 2015 and were published by the Guardian on Wednesday.[1]
The newspaper notes that children are heavily, in fact “vastly over-represented in the reports” featuring in a total of 1,086 incidents despite making up only 18 percent of the detained population. Even the bureaucratic “ratings” of harm and risk given by the private security firm Wilson’s can’t varnish the brutalities.
-
One of the more pertinent observations about Donald Trump’s comment this week on what gun owners could do about a Hillary Clinton presidency comes from columnist Thomas Friedman, who recalls the assassination in Israel 21 years ago of prime minister Yitzhak Rabin. The assassination was preceded by a stream of hateful invective with violent overtones directed by elements on the Israeli right against Rabin — for his having taken a step, in the form of the Oslo accords, toward making peace with the Palestinians.
The invective was condoned rather than condemned by prominent political leaders on the right, including current Prime Minister Benjamin Netanyahu. The inflammatory rhetoric and its widespread toleration helped to convince the assassin that his lethal act would be not only widely accepted but even legitimate. This whole tragic and abominable story is told in detail in Dan Ephron’s gripping book Killing a King, wh
-
With high-profile hacks in the headlines and government officials trying to reopen a long-settled debate about encryption, information security has become a mainstream issue. But we feel that one element of digital security hasn’t received enough critical attention: the role of government in acquiring and exploiting vulnerabilities and hacking for law enforcement and intelligence purposes. That’s why EFF recently published some thoughts on a positive agenda for reforming how the government, obtains, creates, and uses vulnerabilities in our systems for a variety of purposes, from overseas espionage and cyberwarfare to domestic law enforcement investigations.
Some influential commentators like Dave Aitel at Lawfare have questioned whether we at EFF should be advocating for these changes, because pursuing any controls on how the government uses exploits would be “getting ahead of the technology.” But anyone who follows our work should know we don’t call for new laws lightly.
To be clear: We are emphatically not calling for regulation of security research or exploit sales. Indeed, it’s hard to imagine how any such regulation would pass constitutional scrutiny. We are calling for a conversation around how the government uses that technology. We’re fans of transparency; we think technology policy should be subject to broad public debate, heavily informed by the views of technical experts. The agenda in the previous post outlined calls for exactly that.
-
Amidst the graft, excess, sniping, jingoism, and social and environmental devastation that is the Olympics in Rio – where so many poor residents have been internally displaced some observers have dubbed it “the city of shame,” the poignant presence of Olympic refugees has suggested the alarming normalization of mass exile as a Refugee Nation, and protesters have organized The Exclusion Games because the real ones are “not for the people who live here” – there have been many moments of remarkable drama and athletic perfection. Mostly notable have been the gold-winning triumphs of the two young African-American Simones – the gymnast Simone Biles and the swimmer Simone Manuel. But their and others’ real achievements were too often met by stunningly tone-deaf, face-palm-worthy media coverage that repeatedly exposed the rampant sexism, racism and cultural obliviousness of so much mainstream America journalism.
Biles’ astonishing performances were met with well-earned praise – some have hailed her the world’s greatest athlete – but also insulting lapses, like Fox inexplicably covering not her astonishing floor performance but bad Russian ones from the past and stammering coverage of her difficult childhood and adoption; she quickly shut it down with the concise, “My parents are my parents.” Manuel’s surprise victory in the 100-meter freestyle – making her the first African-American woman to win an individual medal in swimming – the same night as a Phelps victory was heralded in one blindingly offensive headline: “Michael Phelps Shares Historic Night with African-American.” The ensuing outrage brought a change of headline and some suggested improvements, like, “Simone Manuel Shares Historic Night with White Guy.” At every turn, the athletes rose above their often-tawdry treatment: After her victory, a tearful Manuel acknowledged “the weight of the black community” and declared, “This medal is not just for me. It’s for a whole bunch of people that came before me and have been an inspiration to me. It’s for all the people after me, who believe they can’t do it.” Ultimately, Biles offered the best-ever retort to the idiocy: “I’m not the next Usain Bolt or Michael Phelps,” she said. “I’m the first Simone Biles.”
-
It was after midnight when the small refugee Olympic team strode into the stadium in Rio, the very last before host country Brazil’s huge contingent danced in to the samba-driven opening ceremonies. Ten amazing athletes, originally from four separate countries but sharing their status as unable to return home, marching under the Olympic flag.
-
On Thursday night, American swimmer Simone Manuel tied with Canadian Penny Oleksiak for a historic gold medal in the 100m freestyle. NBC didn’t air Manuel’s medal ceremony right away — even though she’s the first African American woman to win gold for an individual swim.
Instead, the network aired a delayed broadcast of Russian gymnasts. The BBC, however, did air the medal ceremony as it was happening. Watch the contrast between both programs here.
The sexism and racism aren’t limited to broadcast coverage. The San Jose Mercury News didn’t even bother to include Manuel’s name in a headline that read: “Olympics: Michael Phelps shared historic night with African-American.”
Throughout the first week of the Rio Olympics, sexism has been on display again and again in the coverage of the athletic prowess of thousands of incredible women athletes…
-
In early July, the citizens of Kabul were faced with a confronting sight. Armed with a loudspeaker, novice rapper Elinaa Rezaie hit the streets, lifted the front of her burqa and displayed a bandaged face to passersby in the Pul-i-Surkh district of the city.
Rezaie stood before the Afghan Independent Human Rights Commission building, protesting violence against women and the acid attacks she and others feared. That day, Nafisa Nouri, a wife and mother of two girls, was hospitalized after an attack. Nouri’s 7-year-old daughter Parinaz and another female relative of the family also suffered burns to their bodies and face from the acid.
Mobilzed by her anger, Rezaie rapped against the government’s weak response to violence against women. “I went to visit the acid victims in the hospital to tell them I feel their pain,” Rezaie told Women in the World. “Then I decided to demonstrate … because the rest of the world seems to have forgotten about us.”
-
The study, headed by Sir Eric Pickles, found that authorities are not doing enough to stamp out bullying and religious intimidation among Asian authorities during the lead up to elections.
The report has even called for a dramatic overhaul of the electoral system, warning the “integrity of democracy” is at stake.
-
In my old workplace, right next to the comfortable couches where we would take breaks, we kept a voting machine. Instead of using the screen to pick our preferred candidate, we played Pac-Man. We sent Pac-Man’s familiar yellow chomping face after digital ghosts with the same kind of machine that had been used in 2008 in more than 160 jurisdictions with about nine million registered voters.
This was at the Center for Information Technology Policy at Princeton University, where researchers had been able to reprogram the voting machine without even breaking the “tamper evident” seals.
Voting isn’t a game, of course, and we need to trust the machines that count our votes. Especially this year. Donald J. Trump, the Republican presidential nominee, raised the possibility of “rigged” elections, and his former adviser Roger J. Stone Jr. has warned of a “blood bath” in such a case. A recent poll found that 34 percent of likely voters believed the general election would be rigged.
It’s unclear what mechanism the Trump campaign envisions for this rigging. Voter fraud through impersonation or illegal voting is vanishingly rare in the United States, and rigging the election by tampering with voting machines would be nearly impossible. As President Obama pointed out in a news conference last week, where he called charges of electoral rigging “ridiculous,” states and cities set up voting systems, not the federal government. That’s true, and it means the voting machine landscape is a patchwork of different systems, which makes the election hard to manipulate in a coordinated way.
But it’s still a bleak landscape.
-
Egyptian judoka Islam El Shehaby was loudly booed at the Rio de Janeiro Olympics after his first-round loss to Israel’s fifth-ranked Or Sasson, when he refused to bow or shake Sasson’s hand, in a major breach of judo etiquette.
Sasson defeated El Shehaby with two throws for an automatic victory, with about a minute and a half remaining in the bout.
Afterward, El Shehaby lay flat on his back for a moment before standing to take his place before Sasson, in front of the referee. When Sasson extended his hand, El Shehaby backed away, shaking his head. El Shehaby refused to comment afterward.
Judo players always bow or shake each other’s hands before and after the match as a sign of respect in the Japanese martial art.
El Shahaby had come under pressure from Islamist-leaning and nationalist voices in Egypt to withdraw entirely from the fight.
-
The Dallas Police Department is trying to suppress all evidence it has relating to its use of a bomb robot to kill the man suspected of killing four police officers at a Black Lives Matter protest last month. It has asked the Texas attorney general to allow it to withhold information that is “embarrassing” and has said that much of the evidence is “of no legitimate concern to the public.”
Dallas Police Chief David Brown said the department took the unprecedented measure of using “our bomb robot” after Micah Johnson had holed up in a parking garage and had apparently exchanged gunfire with law enforcement.
“We saw no other option than to use our bomb robot and place a device on its extension to detonate where the suspect was,” Brown said at a press conference soon after Johnson was killed. “Other options would have exposed our officers to grave danger.”
-
An eye witness to the fatal shooting of a Florida retiree during a citizen police academy drill in which she was playing a role said Wednesday at first they thought it was “theater” when she suddenly collapsed.
But when they saw that Mary Knowlton was bleeding, they realized this was no act, witness John Wright told NBC News
-
A 27-year-old Irishman who American prosecutors believe was a top administrator on Silk Road named “Libertas” has been approved for extradition to the United States.
According to the Irish Times, a High Court judge ordered Gary Davis to be handed over to American authorities on Friday.
In December 2013, federal prosecutors in New York unveiled charges against Davis and two other Silk Road staffers, Andrew Michael Jones (“Inigo”) and Peter Phillip Nash (“Samesamebutdifferent”). They were all charged with narcotics trafficking conspiracy, computer hacking conspiracy, and money laundering conspiracy.
After a few years of operation, Silk Road itself was shuttered when its creator, Ross Ulbricht, was arrested in San Francisco in October 2013. Ulbricht was convicted at a high-profile trial and was sentenced to life in prison in May 2015.
-
The case prompted roughly 50 Evangelical leaders from across the county to write to Gov. Greg Abbott (R) and Texas Board of Pardons and Paroles on Monday, urging them to stop the execution. “Officials have a moral obligation to rectify this mistake and stop this execution while they still can,” they wrote, adding, “It deeply troubles us when the criminal justice system concludes that some of the most vulnerable in society can be executed and disposed of.”
From the Washington Post’s lengthy reporting Friday on the case: “If executed this month, Wood will be the ‘least culpable person executed in the modern era of death penalty,’ said Scott Cobb, president of Texas Moratorium Network, a group that advocates against capital punishment.”
-
The scheduled execution is Wood’s punishment for the 1996 death of a man he did not kill — and, by some accounts, did not know was going to be killed.
Legal experts say his case is rare, even in Texas, the execution capital of America — and a state that allows capital punishment for people who did not kill anyone or did not intend to kill.
-
The third lecture by Michel Foucault in Security, Territory and Population begins with a discussion of the systems of law and discipline considered from the standpoint of “norms”. In the system of law, norms are the acceptable behaviors,derived from sacred texts or societal customs or the will of the sovereign. They are then codified and made mandatory. In disciplinary systems, the goal is to identify the best way to do some act, and the people are taught those actions and punished or reeducated for not doing them. In a security system, the ideas of the new sciences of understanding of the nature of the human species are brought to bear on the problem, with the goal of freeing people from the problem, or channeling their behavior into the best known forms. Normalization in the security regime consists in recognizing a problem, and working out solutions using analysis and planning.
He illustrates the latter with a detailed discussion of the introduction of inoculation and the related advances in medicine, administrative controls and statistics, showing that the basic idea of security as a method of government is to treat the population as a whole. There is a nice example of this here. In fact, once you get used to thinking about government as Foucault describes it, you see examples everywhere.
In a law regime, the determination of norms is based on the will of the sovereign, or some sacred text or long-established custom. In a disciplinary regime, the determination of norms is made to fulfill the desires of the powerful, including the sovereign. The examples given, how to load guns, how to form up for a battle, make this clear. Foucault does not discuss the way that norms and the process of normalization are derived in the security regime. How is the decision made as to what problem should be solved, or what behavior should be encouraged or discouraged? These decisions are made through relationships of power, so perhaps we will get more on this later.
-
There is a repeated primitive accumulation throughout the history of capitalism required by capitalist expansion itself, which must commodify not yet commodified spaces in order to develop.
-
We are a global community of survivors of child sexual abuse and advocates. We were heartened when, under your editorial direction, the Columbia Journalism Review published a piece by Steve Buttry, Director of Student Media at LSU: “The voiceless have a voice. A journalist’s job is to amplify it.” We would like to ask you and The New York Times to consider amplifying our collective voice; we reiterate our request, emailed to you on July 11, 2016.
-
Internet Policy/Net Neutrality
-
All summer, kids have been hanging out in front of the Morris Park Library in the Bronx, before opening hours and after closing. They bring their computers to pick up the Wi-Fi signal that is leaking out of the building, because they can’t afford internet access at home. They’re there during the school year, too, even during the winter — it’s the only way they can complete their online math homework.
Last year, the Federal Communications Commission reaffirmed what these students already knew: Access to broadband is necessary to be a productive member of society. In June, a federal appeals court upheld the commission’s authority to regulate the internet as a public utility.
-
DRM
-
Fast Company’s Mark Sullivan asked me to explain what could happen if Apple went through with its rumored plans to ship a phone with no analog sound outputs, only digital ones — what kind of DRM badness might we expect to emerge?
Start by understanding this: copyright lets you do a lot of stuff without permission (and even against the wishes) of rightsholders. For example, it let Apple launch the Ipod and Itunes, both of which were bitterly denounced by the record industry at their launch — as far as they were concerned, “Rip, Mix, Burn” was an invitation to piracy, and Apple was wrong to encourage this behavior. But because copyright has limits — fair use, and the limits on copyrightability itself — Apple was able to revolutionize music.
Enter the DMCA: in 1998, Congress passed the Digital Millennium Copyright Act, Section 1201 of which says that breaking DRM, even to accomplish those legal activities that lead to so much improvement and innovation in the entertainment industry (like Itunes and Ipods and Iphones) is illegal.
-
It’s almost a certainty that Apple has removed the standard headphone jack from the next iPhone, which will be announced in a matter of weeks. The new phone will deliver sound through the Lightning port at the bottom of the phone, or via Bluetooth to wireless headphones. These are both digital outputs; the analog output of the headphone jack is probably gone for good.
This is good and bad. The end-to-end digital audio stack will allow for higher quality audio and some new features, but it’ll also open the door for increased DRM control over music content by the record labels that own it.
“If Apple creates a circumstance where the only way to get audio off its products is through an interface that is DRM-capable, they’d be heartbreakingly naive in assuming that this wouldn’t give rise to demands for DRM,” Electronic Frontier Foundation special advisor Cory Doctorow told Fast Company in an email exchange Monday.
If a consumer or some third-party tech company used the music in way the rights holders didn’t like, the rights holders could invoke the anti-circumvention law written in Section 1201 of the Digital Millennium Copyright Act (DMCA).
-
Intellectual Monopolies
-
Copyrights
-
The 4th Circuit Court of Appeals ruled Friday in favor of the American government’s seizure of a large number of Megaupload founder Kim Dotcom’s overseas assets.
In the US civil forfeiture case, which was brought 18 months after the initial criminal charges brought against Dotcom and Megaupload, prosecutors outlined why the New Zealand seizure of Dotcom’s assets on behalf of the American government was valid. Seized items include millions of dollars in various seized bank accounts in Hong Kong and New Zealand, multiple cars, four jet skis, the Dotcom mansion, several luxury cars, two 108-inch TVs, three 82-inch TVs, a $10,000 watch, and a photograph by Olaf Mueller worth over $100,000.
-
Following a court win by its client BMG over Cox Communications this week, Rightscorp has issued an unprecedented warning to every ISP in the United States today. Boasting a five-year trove of infringement data against Internet users, Rightscorp warned ISPs that they can either cooperate or face the consequences.
-
The Electronic Frontier Foundation (EFF) today filed a petition on behalf of its client Stephanie Lenz asking the U.S. Supreme Court to ensure that copyright holders who make unreasonable infringement claims can be held accountable if those claims force lawful speech offline.
Lenz filed the lawsuit that came to be known as the “Dancing Baby” case after she posted—back in 2007—a short video on YouTube of her toddler son in her kitchen. The 29-second recording, which Lenz wanted to share with family and friends, shows her son bouncing along to the Prince song “Let’s Go Crazy,” which is heard playing in the background. Universal Music Group, which owns the copyright to the Prince song, sent YouTube a notice under the Digital Millennium Copyright Act (DMCA), claiming that the family video was an infringement of the copyright.
Permalink
 Send this to a friend
Send this to a friend
08.13.16
Posted in News Roundup at 11:03 am by Dr. Roy Schestowitz

Contents
-
Server
-
Kernel Space
-
-
It has been confirmed that Linux kernel 4.9 release will be the next LTS kernel branch. This Long Term Release is expected to receive fixes and updates for a couple of years. If everything goes as expected, kernel 4.9 will arrive towards the end of November 2016.
-
Graphics Stack
-
It has been less than one week since the Linux 4.8-rc1 release and already Intel OTC developers have sent in their first batch of updates to DRM-Next for in turn landing with Linux 4.9.
-
-
Applications
-
Youker Assistant is Linux system maintenance software built by Ubuntu Kylin, an official Ubuntu subproject for chinese users. Youker assistant helps maintain system by cleaning system trash files, cache, cookies and all other history trace. There are couple of more built-in tools in Youker Assistant.
-
Ardour 5.0 is now available for Linux, OS X and Windows. This is a major release focused on substantial changes to the GUI and major new features related to mixing, plugin use, tempo maps, scripting and more. As usual, there are also hundreds of bug fixes. Ardour 5.0 can be parallel-installed with older versions of the program, and does not use the same preference files. It will load sessions from Ardour 2, 3 and 4, though with some potential minor changes.
-
Proprietary
-
-
Whenever I write about Microsoft’s change in attitude toward Linux, I get pushback from a segment of the Linux user community. That makes me wonder if it’s really ‘okay’ to use Microsoft products on Linux. If not, why?
-
Instructionals/Technical
-
Games
-
Earlier this week the deferred flushes change landed in Radeon Gallium3D code for reportedly offering 23%+ performance improvements in BioShock Infinite as one example. I’ve tested out BioShock Infinite and other changes to confirm the performance differences.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Development on KDE Plasma 5.8 continues to move along with the feature freeze for it being next month. Plasma 5.8 when released in October is going to be the first Long-Term Support (LTS) release of Plasma 5.
Plasma 5.8.0 is expected for release on 18 October while the feature freeze and beta release is due for 29 September. With some weeks to go until that freeze, developers are quickly working on the changes they’d like to see for this next version.
-
Plasma 5.8 will be our first long term support release of Plasma 5 and together with Qt 5.6 also being an LTS release this makes for a rock-solid combo. Let’s have a look at some of the tweaks I did on the occasion.
-
GNOME Desktop/GTK
-
So if you are around Karlsruhe (Germany), do not hesitate to come by (GUADEC is a free GNOME event) at the Karlsruhe Institute of Technology. Otherwise, you can see us on the live streaming of the event (direct link for live streaming) and the recording will remain viewable afterwards from the CCC streaming website.
-
-
For those that may be interested in the Clear Linux distribution for improved performance or other innovative functionality, the third “Clear Linux Highlights” newsletter has been published to share more of the recent changes to this Linux distribution out of the Intel Open-Source Technology Center.
Recent changes to Clear Linux include making HTTP/2 the default Internet protocol, both for client and server components packaged by Clear Linux — just not any web browser default.
-
New Releases
-
The Alpine Linux project is pleased to announce the immediate availability of version 3.4.3 of its Alpine Linux operating system.
This is a bugfix release of the v3.4 musl based branch, based on linux-4.4.17 kernels.
-
PCLinuxOS/Mageia/Mandriva Family
-
The wait is over for those of us who appreciate the hard work of the developers at OpenMandriva: today, this blog announces that the new release is ready!
OpenMandriva Lx 3 comes with KDE Plasma 5.6.5, three launchers (Kickoff, Kicker, and a full screen one) and F2FS support for SDDs.
-
Work on the RC1/RC2 releases has further improved stability and performance. We have now support for the Japanese and Chinese languages so we would really welcome any feedback from those who speak them.
-
-
OpenSUSE/SUSE
-
-
It appears that SUSE and the OpenStack company Mirantis have teamed up to pull a play from the Oracle playbook. The deal brings full enterprise Linux support to Mirantis’s OpenStack customers which is not limited to SLED but includes full support for RHEL and CentOS. Maybe that plan will work better for them than it did for Oracle.
-
Red Hat Family
-
Finance
-
Fedora
-
Fedora developers have been working to come up with a schedule for Fedora 26 to succeed the November release of Fedora 25.
The current proposed schedule has the mass rebuild happening in January, an alpha release at the end of February, the beta release middle of April, and the official Fedora 26 release on 16 May.
-
-
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
Flavours and Variants
-
Lubuntu-Next images are being prepared that shift this Ubuntu derivative from using the lightweight LXDE desktop to using the newer LXQt desktop.
-
-
Phones
-
DataWind launched the PocketSurfer GZ in India for Rs 1,499. DataWind has partnered with Reliance Communication to offer free internet on the device for a year. The device ships with the Linux Operating System. There are no details on specifications as of now.
-
Tizen
-
Here we have a list of the Top 20 most downloaded apps / games from Tizen Store in july for Samsung Z1 and Z3 smartphones. At the top we have WhatsApp which is still holding its number one place followed by ShareIt and a new game Candy Rain 3, which is similar to the famous Candy Crush game. Another new one is Yoddha: Deva Sangram which is a role playing game which was exclusively launched for Tizen devices.
-
Android
-
-
-
-
-
-
-
-
Chinese technology company LeEco might be slowly inching toward a U.S. launch sometime this fall, but that does not mean it will sit on its laurels until then. On the contrary, LeEco is rumored to be launching the Le 2S, which is seemingly a refreshed version of the Le 2 and the first Android phone to include a whopping 8GB RAM.
You did not read that wrong — according to GizChina, the Le 2S will include 8GB RAM, practically unheard of in the Android world. As we have seen with Samsung’s 2015 flagship phones and the OnePlus 3, however, the RAM amount does not matter as much as how it is utilized. Even so, the 8GB RAM will finally turn our dream of playing five games at the same time a reality.
-
-
-
Almost two years ago, we covered the Flow Home launcher as a rather innovative take on the Android home screen. It gave you the things you usually want to check on your phone – Facebook feed, Twitter, Instagram, the weather – and put it together in a kind of timeline flow. At its time, it was a totally new thing.
As the whole Android ecosystem has moved forward in over 2 years, we’ve realized that people kind of want to stay with a standard home launcher – this is why the successful launchers like Nova and Action Launcher don’t change a lot in the basic Android proposition for a home screen. HTC’s Blinkfeed – quite similar to Flow Home – has gotten a small following, but like Flow Home it hasn’t quite caught the masses’ attention.
-
Following on from Facebook’s decision to override users’ ad blocking tools, Adblock Plus has fired one more shot, saying that it will continue the fight for the right to an ad-free social networking experience.
After finding a way to prevent Facebook blocking ads, which Facebook then bypassed once again, Adblock Plus says that while the game of cat and mouse may continue, it wants to use what it describes as “probably be the last time we talk about it for a while” to say that the open source community will fight the good fight for users.
-
Web Browsers
-
Mozilla
-
ozilla plans to support plugin-free streaming on Netflix and Amazon Video on Firefox for Linux starting with version 49 stable of the browser.
The streaming world is slowly moving towards using HTML5 for streaming purposes and away from using plugins such as Microsoft Silverlight or Adobe Flash.
-
Way Cooler is another project to add to the list of interesting Wayland compositors / window managers from the futuristic NEMO-UX to Swap to many others.
Way Cooler advertises itself as a tiling window manager written in Rust and targeting Wayland. Similar to Sway, Way Cooler features i3-style tiling. This new open-source project also has client application support via an IPC, a Lua scripting environment to extend the window manager, and there is support for XWayland X11 programs.
-
Oracle/Java/LibreOffice
-
Besides the Free Software Foundation issuing their first-ever annual report this week, The Document Foundation has come out this week as well with their 2015 annual report.
Their annual report covers new advisory board members, the releases made by LibreOffice over the course of the year, financials, conferences / events, and more.
-
Pseudo-Open Source (Openwashing)
-
Public Services/Government
-
With the presidential election season upon us, I’m often asked whether the U.S. government efforts to encourage use of open source software (OSS) will continue when a new administration comes into office in January.
As I’ve written before, there has been a shift, going back almost a decade, away from the debate over whether to use open source to a focus on the how to. The release by the Office of Management and Budget (OMB) of the U.S. Federal Source Code Policy on August 8th is the latest manifestation of this shift. It achieves the goal laid out in the Obama administration’s Second Open Government National Action Plan (PDF) for improved access to custom software code developed for the federal government. The plan emphasized use of (and contributing back to) open source software to fuel innovation, lower costs, and benefit the public. It also furthers a long-standing “default to open” objective going back to the early days of the administration.
-
The recent announcement of a new policy framework providing guidance to public agencies on the licensing of open source software (OSS) will lead to better results across government and industry by enabling more collaboration. The policy is significant as it increases the likelihood of future government web services being developed using open source code and allowing external parties to copy, adapt or integrate their features. It will drive more efficient use of public money, more integrated government web services, local innovation and economic growth. However, perhaps most remarkable is the transparent and collaborative online consultation and drafting process through which this ambitious idea became a robust policy in less than a year.
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
-
-
With an incredibly important national election coming up, it’s more critical than ever that everyone who can vote does — and is able to. Election tech firm Free and Fair is hoping to help avoid overflowing voting locations with a simple, open source device that automatically monitors waiting times and keeps voters and officials informed.
Free and Fair creates open source software for polling places, from checking in voters to actually taking and tallying votes — but Qubie is the company’s first original hardware, created for the Hackaday Prize. Founder Daniel Zimmerman explained that it was just another aspect of the voting process that struck them as out of date.
“In the last few elections there have been reports of long queue times, people giving up and going home,” he told TechCrunch. “Election technology is in a pretty sorry state — we thought it’d be nice to gather data on that rather than anecdotes.”
-
Standards/Consortia
-
As many of my readers have probably figured out, I am a fan of the stuff that’s “out there.” You don’t even have to use it. It doesn’t need to be something that will necessarily set the world on fire. If there’s passion in its development and design, I’m pretty much on board. And I can’t wait to try it.
To understand the philosophy behind Haiku, it’s a good idea to examine the word. Of course, it is the Japanese word referring to a short poem in which you have two philosophical, often conflicting, elements. It is also defined as the essence of the act of cutting, which is translated as the Japanese word “kiru”. No, I don’t speak Japanese but I really, really like sushi; and that has nothing to do with anything.
-
Chances are, I can name five tech devices that are in your home — or pocket — right now. That’s because about half of all U.S. households today own at least one television, smartphone, tablet and laptop/desktop.
Collectively, these five consumer technology product categories have represented more than 40 percent of industry revenue since 2011 — and more than 50 percent in the past four years.
But the products we own and the ways we use them are changing.
-
Hardware
-
For a corporate desktop PC I think the ideal design would have only M.2 internal storage and no support for 3.5″ disks or a DVD drive. That would allow a design that is much smaller than a current SFF PC.
-
Security
-
The White House unveils a new open source government policy and new research estimates the government’s zero-day exploit stockpile to be smaller than expected.
-
The idea of governments releasing their proprietary code isn’t some pipe dream, it’s slowly becoming a reality in many countries and starting a much needed public discussion in others. Governments around the world are beginning to understand that their software is funded by the public, and therefore belongs to the public and should be accessible for their use. Bulgaria just passed a law which mandates that all code written for the government must be released as open source. Similarly, the United States is starting a 3-year pilot requiring all US agencies to release at least 20% of all federally-funded custom code as open source. France, Norway, Brazil and other countries have also initiated their own government open source programs to ensure more government funded code will be released as open source.
-
-
Seven autonomous supercomputers faced off against each other in DARPA’s Cyber Grand Challenge (CGC) event on the first day of the DEFCON security conference. In the end, a system known as ‘Mayhem’ won the $2 million grand prize and in the process helped solve a decade-old security challenge that revolved around detecting a particular type of vulnerability.
Mike Walker, the DARPA program manager responsible for CGC, commented during a press conference that some bugs are so well known that they become famous. One such example is CrackAddr, the name of a function that can split up parts of an email address.
-
-
-
In other words, VW created a backdoor, and assumed that it would remain hidden. But it did not.
This is exactly the kind of point that we’ve been making about the problems of requiring any kind of backdoor and not enabling strong encryption. Using a single encryption key across every device is simply bad security. Forcing any kind of backdoor into any security system creates just these kinds of vulnerabilities — and eventually someone’s going to figure out how they work.
On a related note, the article points out that the researchers who found this vulnerability are the same ones who also found another vulnerability a few years ago that allowed them to start the ignition of a bunch of VW vehicles. And VW’s response… was to sue them and try to keep the vulnerability secret for nearly two years. Perhaps, rather than trying to sue these researchers, they should have thrown a bunch of money at them to continue their work, alert VW and help VW make their cars safer and better protected.
-
The time has come that I must speak out against the inappropriate rhetoric used by those who (ostensibly) advocate for FLOSS usage in automotive applications.
There was a catalyst that convinced me to finally speak up. I heard a talk today from a company representative of a software supplier for the automotive industry. He said during his talk: “putting GPLv3 software in cars will kill people” and “opening up the source code to cars will cause more harm than good”. These statements are completely disingenuous. Most importantly, it ignores the fact that proprietary software in cars is at least equally, if not more, dangerous. At least one person has already been killed in a crash while using a proprietary software auto-control system. Volkswagen decided to take a different route; they decided to kill us all slowly (rather than quickly) by using proprietary software to lie about their emissions and illegally polluting our air.
Meanwhile, there has been not a single example yet about use of GPLv3 software that has harmed anyone. If you have such an example, email it to me and I promise to add it right here to this blog post.
-
Transparency/Investigative Reporting
-
That has changed. With the publication of e-mails expressly aimed at damaging Hillary Clinton’s presidential candidacy, WikiLeaks has shifted from a global platform for whistleblowers to something less exalted—and lately, a bit strange. Julian Assange, the site’s founder, hinted darkly in a Dutch television interview on Tuesday that a young Democratic National Committee staffer who had been murdered in Washington on July 10 had been killed because he had provided information to WikiLeaks, which posted a $20,000 reward for information on the July 10 death of Seth Rich. “Whistleblowers go to significant efforts to get us material and often very significant risks,” Assange said. “There’s a 27-year-old who works for the DNC who was shot in the back, murdered, just a few weeks ago, for unknown reasons as he was walking down the streets in Washington.”
-
Trump allies, WikiLeaks and Russia are pushing a nonsensical conspiracy theory about the DNC hacks [Ed: Shooting the messenger: calling Wikileaks “conspiracy theory” (for showing original evidence or asking questions). Wikileaks did not even suggest what news sites are saying; that's people misinterpreting what Wikileaks actually said.]
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
It’s time for new revelations now. All of you may have heard about the DCCC hack. As you see I wasn’t wasting my time! It was even easier than in the case of the DNC breach.
As you see the U.S. presidential elections are becoming a farce, a big political performance where the voters are far from playing the leading role. Everything is being settled behind the scenes as it was with Bernie Sanders.
I wonder what happened to the true democracy, to the equal opportunities, the things we love the United States for. The big money bags are fighting for power today. They are lying constantly and don’t keep their word. The MSM are producing tons of propaganda hiding the real stuff behind it. But I do believe that people have right to know what’s going on inside the election process in fact.
-
AstroTurf/Lobbying/Politics
-
The Pirate party, whose platform includes direct democracy, greater government transparency, a new national constitution and asylum for US whistleblower Edward Snowden, will field candidates in every constituency and has been at or near the top of every opinion poll for over a year.
-
The recent hacking attacks on the Democratic National Committee and the Democratic Congressional Campaign Committee, allegedly commissioned by the Russian government, have made cyber security a hot-button issue once again. And according to security blogger Bruce Schneier, America’s voting machines may be next.
On the latest episode of Too Embarrassed to Ask, The Verge reporter Russell Brandom joined Recode’s Kara Swisher and The Verge’s Lauren Goode to explain how these hacks occurred and what happens if Schneier’s nightmare scenario comes true.
“You’re not hacking Bank of America, where someone has spent a lot of money to make sure that no one can get into that,” Brandom said. “I’m worried about voting machines just not working. I don’t know if it’s extremely likely, but the results would be so catastrophic to the body politic.”
The scary problem, Brandom said, is that we might not be able to say with 100 percent confidence that a hack had really happened.
-
Donald Trump was thundering about a minority group, linking its members to murderers and what he predicted would be an epic crime wave in America. His opponents raged in response—some slamming him as a racist—but Trump dismissed them as blind, ignorant of the real world.
No, this is not a scene from a recent rally in which the Republican nominee for president stoked fears of violence from immigrants or Muslims. The year was 1993, and his target was Native Americans, particularly those running casinos who, Trump was telling a congressional hearing, were sucking up to criminals.
Trump, who at the time was a major casino operator, appeared before a panel on Indian gaming with a prepared statement that was level-headed and raised regulatory concerns in a mature way. But, in his opening words, Trump announced that his written speech was boring, so he went off-script, even questioning the heritage of some Native American casino operators, saying they “don’t look like Indians” and launching into a tirade about “rampant” criminal activities on reservations.
-
On Friday, the online persona behind a high-profile hack of the Democratic National Committee took credit for a separate breach of the Democratic Congressional Campaign Committee. To prove they were responsible, the leaker known as Guccifer 2.0 published a massive amount of personal information belonging to hundreds of Democratic representatives.
-
Censorship/Free Speech
-
-
One of the most vital duties of a journalist — in any democracy — is to report on the day-to-day operations of a country’s parliament. Journalism schools devote much time to teaching the deciphering budgets and legal language, and how to report fairly on political divides and debates.
I recalled these studies when I read an email Wednesday morning from an Ankara-based colleague. I smiled bitterly. The message included a link to an article published in the Gazete Duvar, which informed that 200 journalists had been barred from entering the home of the Grand National Assembly of Turkey. Security controls at the two entrances of the failed-coup-damaged building had been intensified and journalists were checked against a list as they tried to enter.
The reason for the bans? Most of those who were blocked worked for shuttered or seized outlets alleged to be affiliated with the Gülenist movement.
Parliament, though severely damaged by bombing during the night of the coup attempt, is still open. For any professional colleague, these sanctions mean only one thing: journalism is now at the absolute mercy of the authorities who will define its limits and content.
-
-
-
-
-
In a massive development set to rock the Censor Board and the film industry, the monitoring body is likely to be stripped off its ‘censoring’ powers and will be left only with the authority to ‘certify’.
According to Information and Broadcasting (I&B) sources, the ministry is working on major changes in the Cinematography Act and the bill will be introduced in the winter session of Parliament.
In the wake of the recent furore by the film industry under Central Board of Film Certification (CBFC) Chairperson Pahlaj Nihalani, the government has expressed its desire to avoid any further controversies.
Sources further stated the entire film certification process will be reworked and changed, adding there will be two committees: one for reviewing and the other for monitoring.
-
-
-
Twitter has made a name for itself as a champion of free speech around the world. Following the recent coup attempt in Turkey, however, something has changed in the way it approaches censorship, and the company refuses to talk about it.
Twitter’s policy toward Turkey—limited “censoring to avoid a ban”—puts the company between a rock and a hard place: If Twitter does not comply with Turkey’s ever-increasing censorship requests to silence dissidents, it may face a nationwide ban that silences everyone. But this bullying has just gained more ground against press freedoms in Turkey with Twitter censoring journalists’ accounts that Turkish government wants banned.
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Privacy/Surveillance
-
At what ought to have been the height of preparations for the 2016 census, its head, Duncan Young, sent his colleagues in the Bureau of Statistics executive a crisis memo.
“As most of you are aware, the census program has alerted its steering committee and board that it has assessed its status as RED,” he wrote in February.
-
We know what automatic license plate readers are good for: collecting massive amounts (billions of records) of plate/location data housed by private companies and accessed by law enforcement for indefinite periods of time. What we don’t know is how effective ALPRs are at fighting/investigating crime.
George Joseph at Citylab has done some digging into the effectiveness of license plate readers and hasn’t found much that justifies the expense, much less the constant compilation of plate info.
-
Civil Rights/Policing
-
The year 2016 is only a couple of hours old when the orgy in Jacob Appelbaum’s apartment in a pre-World War II building in Berlin’s Prenzlauer Berg district really gets going.
Somebody has unfolded the sofa in the living room. Two couples are having sex at the same time in the room. Some guests had already taken synthetic party drug MDMA, which induces a state of euphoria and increases the need for emotional warmth, at another party. A third couple is going at it in the bedroom. Later, a crime allegedly took place in Mr. Appelbaum’s bed or on the fold-out sofa.
[...]
Among others, there is an account by a woman who calls herself “Forest.” She tells of how she found herself forced to repulse his insistent advances. When she has assumed that everything had been cleared up in a friendly manner between them, she spent the night in Mr. Appelbaum’s apartment and slept next to him in bed.
Forest writes that at apparently, some point she woke up to find that Mr. Appelbaum had unzipped her pants and stuck his finger in her underwear. She wrote that she tried to wake him, but he then rolled over. When the woman angrily confronted Mr. Appelbaum about it later, she claimed he made the terse excuse that he had dreamed that his fiancée was lying next to him.
-
Lawyers for Sgt. Bowe Bergdahl, who was held prisoner by the Taliban for nearly five years after abandoning a remote Army outpost in Afghanistan and faces criminal charges for leaving his unit, on Friday accused his top commander of burning more than 100 letters regarding the case.
The defense, in a court motion, asked a judge to remove Gen. Robert Abrams from the case and to cancel a scheduled Feb. 6 trial because Abrams told Bergdahl’s defense team Monday that he burned the letters, which were sent to him by supporters and detractors of their client.
-
Intellectual Monopolies
-
Trademarks
-
For over a decade, I’ve blogged about 1-800 Contacts’ campaign to suppress competitive keyword advertising, including its legislative games (e.g., those times when 1-800 Contacts asked the Utah legislature to ban competitive keyword advertising) and at least 15 lawsuits against competitors costing millions of dollars in legal fees. I’ve also marveled at its duplicity; 1-800 Contacts historically employed the same competitive keyword advertising practices it subsequently sought to suppress.
Things have been quiet on the 1-800 Contacts front for the past several years, after it suffered a major blow in the 10th Circuit’s Lens.com ruling, but sometimes the machinery of justice keeps turning quietly in the background. This week, the FTC sued 1-800 Contacts for antitrust violations. I believe this is the FTC’s first foray into keyword advertising issues, and it’s left some folks scratching their heads.
-
Copyrights
-
Readers here likely have begun to associate the attempted twisting of copyright law to go after video game cheaters with Blizzard. After all, between its StarCraft and Overwatch properties, the gamemaker has made something of a name for itself by attempting to assert a combination of “you only bought a license” and “breaking the EULA creates a copyright violation” theories into a “we can sue you for hacking our games” legal sandwich. It’s a terribly frustrating thing to watch Blizzard do, as it tries to pretzel copyright law in a way never intended, and typically to achieve little if any legal success by doing so.
Permalink
 Send this to a friend
Send this to a friend
08.12.16
Posted in Apple, GNU/Linux, Google, Samsung at 5:45 pm by Dr. Roy Schestowitz

Summary: Apple’s frivolous lawsuits against Android OEMs win the support not of technology companies (these actually oppose Apple’s actions) but of some “non-tech companies, high-profile designers and intellectual property associations”
A few days ago we mentioned Florian Müller‘s latest article on Samsung v Apple (or vice versa) — an article which he later corrected for errors (amici overlooked or simply not yet listed at the time). It turns out that Müller wasn’t far from the truth, however, as technology companies pretty much reject Apple’s position. Müller has since then continued to highlight Samsung matters such as this likely new IPO or Google’s antitrust worries in Korea [1, 2], the home of Samsung. “The South Korean government has delayed a decision on whether it will accept Google’s request to export South Korea’s detailed map data,” one of those articles says. “Less than 2 months to go until the Samsung v. Apple Supreme Court hearing on design patent damages,” he wrote about the case which involves patents granted by the USPTO in spite of their low quality (the EPO made similar mistakes under Battistelli).
“It turns out that Müller wasn’t far from the truth, however, as technology companies pretty much reject Apple’s position.”Not too long afterwards MIP published this article that says: “Ahead of a showdown over design patents at the Supreme Court in October, Samsung has received more support from US technology companies whereas Apple has received the backing of non-tech companies, high-profile designers and intellectual property associations” (i.e. not quite producing companies). Patently-O wrote about this as well, noting that Apple’s “visual design is critically important in the sales of complex products.” That’s just branding and hype (or compelling marketing), i.e. the bread and butter of Apple. Patent-granting should be a scientific process, entirely disconnected from hype or brand recognition. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 5:09 pm by Dr. Roy Schestowitz
FTI Consulting helps the EPO ‘manage’ Dutch and German media (new contract recently signed), but that does not always work

Summary: The mass media is catching up with Battistelli’s alienation, segregation or isolation of the boards of appeal as part of his plan to phase them out of existence and maintain systematic exacerbation of patent quality for production’s sake, where “production” is inaccurately and improperly measured
THE media has been rather quiet regarding the EPO recently. The only “EPO” we see in the news is actually the drug, typically in relation to doping in the Olympic games.
“For your information,” told us one of several readers who alerted us about Süddeutsche Zeitung, the local paper “finally breaks the silence on the EPO…”
It is an article composed not by one of the more familiar writers (who ought to be quite familiar with EPO matters) and several people told us about it.
“I noticed the following article which has just appeared in the Süddeutsche Zeitung,” one reader told us. “It is mainly about the planned move of the EPO Boards of Appeal to Haar and it refers to the recent coverage of this story on Techrights.” (see for example [1, 2])
It is good to know that they follow Techrights. We typically get the stories here earlier than the corporate media.
“Battistelli’s plans to send the Boards of Appeal into “exile” in Haar are eerily reminiscent of the methods employed by Željko Topić during his time at the Croatian SIPO,” told us this reader, “as previously reported by Techrights” (see for example [1, 2])
“The difference,” continued this reader, “is that in his previous role Topić could only inflict damage on the IP system in Croatia. It seems that with Battistelli’s backing he has managed to manoeuvre himself into a position where he can now operate on a European scale.”
This is pretty bad as it brings what we once saw dubbed “Balkan standards” into the whole of Europe. We previously made note of exactly the above point (similarity to Topić’s history in Croatia).
These problems at the EPO are real and there is no solution in sight for them (not in summertime anyway). European Inventor Award 2017 (EIA2017) is already being planned as if everything will be fine for another year to come and the PR people are 'spamming' for it (there have been yet more examples of that since, albeit not as much if anything at all after we published the article). “Inventors who aren’t European nationals but have been granted a European patent can also be nominated for this Award,” the EPO stated in relation to EIA2017. It’s not “European Inventor Award 2017″ just as “European Patent Office” is not really European, I’ve told them, considering the fact that there is even discriminatory prioritisation which puts small European businesses at the back of the line.
“I would replace “in Europe” by “at the EPO”,” wrote Benjamin Henrion in response to software patents advocacy in Europe. I told him that that EPO “is not European, it just has the word “European” in its name, like Federal Express which isn’t Federal.” The EPC does not permit software patenting either, but that does not exactly prevent EPO management from trying to work around the exclusions.
A lot of the above relates to how detached from the EPC Battistelli’s EPO has gotten. It’s jaw-dropping that he managed to get away with it. The EPO now has a Brexit-like 'Constitutional Crisis' (dealing with deviation from founding documents like EPC and EU/Lisbon Treaty). Apparently, with help with his marionette called Kongstad, there is something Battistelli can do. A discussion about it is buried inside a very long, multi-page comments thread (the only remaining suitable place as IP Kat barely covers EPO these days). To quote the latest in this discussion:
Hmmm. Not sure I agree that the founding fathers “made arrangements” for arbitration. For example, they failed to provide a description of how arbitration should work, and who should be the arbiter.
At best, the PPI merely provides for the possibility of arbitration. However, there are many practical barriers to that possibility being exploited. For a start, there is the complete apathy upon the part of the representatives to the AC (who, it must be remembered, come from national offices whose income from renewal fees will increase if examination standards at the EPO are lowered). Then there is the total absence of any formal procedure for initiating a dispute.
So who do you see “getting the ball rolling” in this context?
Read Article 24 of the PPI.
I keep posting the text of the Article but the comment doesn’t seem to get through …
http://www.epo.org/law-practice/legal-texts/html/epc/2016/e/ma5.html
There is a very detailed description of how the arbitration is to take place.
The President of the ICJ has a role in selecting the committee.
It’s all there in black and white.
You just need to RTFM …
Do not overlook Article 23 (2) PPI:
If a Contracting State intends to submit a dispute to arbitration, it shall notify the Chairman of the Administrative Council, who shall forthwith inform each Contracting State of such notification.
That is how the ball starts rolling.
A notification is sent to the Chairman of the AC.
It’s that simply.
Thanks. You are quite correct, of course. Interesting that Art. 24(2) PPI states that “This panel shall be established as soon as possible after the Protocol enters into force and shall be revised each time this proves necessary”. This implies that the relevant panel should have been established almost 40 years ago. So which panel is it? And what rules of procedure for that panel have been established according to Art. 24(4)? Or are those yet further provisions of the EPC that the AC has neglected to follow?
I suspect that this could very well be the case.
To the best of my knowledge the details of the “panel” – if it has been established – have never been published.
Normally one would expect that kind of information to appear in the Official Journal. However there does not seem to be any explicit requirement for publication of the membership of the panel.
From that I conclude that either the provision has been ignored or else it’s a well-kept secret.
Can Battistelli simply bend the rules and make up new rules to justify his abuses retroactively? If some time in the past he simply broke the rules, as he did as far back as 2014 (if not further back), why does he get to keep his job and astronomical salary? EPO mouthpieces have certainly helped that and based on internal documents we saw, Battistelli still cites these same mouthpieces for ‘evidence’ and ‘support’ regarding patent quality. He is fooling the delegates at times when they growingly express concerns about patent quality. Battistelli is a chronic liar. Maybe he does this without even realising (the hallmark of sociopaths, learning to believe one’s own lies and reject critical voices). █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 3:57 pm by Dr. Roy Schestowitz

Contents
-
Desktop
-
Thanks to its lightweight chassis, gorgeous screen and epic battery life, the Dell XPS 13 has been our favorite laptop overall for more than 18 months now. Though it’s not targeted directly at business users, the laptop’s industry-leading design and strong performance make it a great choice for workers, especially coders. The XPS 13 Developer Edition ($1,049 to start, $1,550 as tested) is a version of the notebook running Ubuntu Linux 14.04 that is primed for, you guessed it, developers.
-
Microsoft has backed down on its plan to hustle owners of certain PCs to Windows 10 by crimping support options.
Redmond revealed the plan last January, when it decreed that PCs running 6th-generation Core i5 or Core i7 CPUs and Windows 7 would only get limited security and stability support until mid-2017. By March it backed off a little, extending support for another year and promising critical patches would flow until end of life.
-
You can no longer dictate to the world what folks will do with the hardware they own.
-
-
Here’s some unhelpful back-to-school advice: Don’t buy a laptop. Borrow one, steal one from a family member, buy a piece of junk for 40 bucks on Craigslist. If you can find a way to wait a couple of months before dropping serious coin on a new clamshell, you’ll be glad you did.
Later this fall, Apple’s almost certainly going to release a new MacBook Pro, which is desperately in need of a revamp. And there will be Windows PCs practically falling from the ceiling—maybe even a few made by Microsoft itself. But the real reason to hold off on your purchase is to wait for the new breed of Chromebooks that are on their way.
-
Kernel Space
-
-
-
After announcing the release of Linux kernel 4.6.6 and Linux kernel 4.4.17 LTS, renowned kernel developer and maintainer Greg Kroah-Hartman announced the release of Linux kernel 3.14.75 LTS.
-
Just a few moments ago, renowned Linux kernel developer and maintainer Greg Kroah-Hartman had the great pleasure of announcing that the next LTS (Long-Term Support) kernel branch will be Linux 4.9.
-
Applications
-
Ardour is a free and open source digital audio workstation which can be used to record and mix music, podcasts, or just about anything else. The software has been available for Linux and Mac for over a decade.
-
-
-
Today, August 12, 2016, Calibre developer Kovid Goyal proudly announced the release of a new maintenance update for the popular, open-source and cross-platform Calibre ebook library management software.
Calibre 2.64 is now the latest and most advanced version of the application designed for book lovers who prefer to use digital e-book readers to store their books in various file formats, as well as convert and organize ebooks from a format to another, if it’s supported by Calibre, of course.
-
Linux offers an abundance of music players; how do you choose which one to use?
Back in June, 2016, I wrote about the apparent passing of my favorite open source music player, Guayadeque. I described the six things I really liked about Guayadeque, and looked at two obvious alternatives: Quod Libet and gmusicbrowser. Since that time, I have been living with gmusicbrowser on my laptop, while continuing to use mpd on the computer attached to the home stereo. Meanwhile, several kind readers have offered other suggestions as to their favorite music players.
With all this input available, I decided to formalize my “six things” list and apply it to a list of candidates for my laptop music playing needs.
-
Want to watch Twitch.tv streams on your desktop, without Flash? You can with this awesome Twitch app for Linux, which also supports chat & notifications and more.
-
Instructionals/Technical
-
Games
-
Also, another review which is one of the most comprehensive reviews you can find, and it’s one of the ‘Most Helpful’ ones as well (source) where the player has put in over one thousand hours, is also negative.
Though, you may already know it isn’t the first time these developers are in the middle of a controversy, as you can see in the readers’ comments in this recent GOL article.
Therefore, if you were planning to buy Rust because of the current bundle from Humble Bundle, think twice and be aware of all these issues before making a decision.
-
Hot on the heels of their patch for Company of Heroes 2, Feral has now patched Life is Strange. Nvidia Pascal users will be most pleased about this one.
-
At least he was honest and conclusive instead of other cases where a Linux port is hinted or directly promised but it ends up never seeing the release. But still, sometimes I tend to think that small games like this have a guaranteed port but unfortunately it isn’t always the case, and considering that at the moment of writing this article Hexoscope has 85 positive reviews and not a single negative one, it IS truly a shame…
-
I was quite the fan of the original The Spatials and now that The Spatials: Galactology came out as a day-1 release I have been keen to take a look.
If you’re into management sims and building games this will probably be right up your street, as it is a very cool indie game. It’s essentially the first The Spatials with a ton of expanded content and improvements all around.
Note: It’s currently in Early Access, as they continue to add in new content and features. Most recently they added in creating your own spaceships to the mix.
-
Since DEADBOLT recently came to Linux and GOG provided me with a copy, I took a look at this indie attempt at stealth and action.
I’m going to be honest, it’s one game that sadly got bumped down in my list a bit as so many other things kept coming up. I’m sad that happened, as what I found with DEADBOLT has truly impressed me.
First annoyance for me: The game starts on the wrong screen on my multiple monitor setup, luckily setting it to windowed mode and moving it over to my main screen and then setting it back to fullscreen was possible.
-
As promised, Turmoil, a tongue-in-cheek take on the simulation genre is now officially available on Linux.
-
Desktop Environments/WMs
-
GNOME Desktop/GTK
-
GNOME and Flatpak development Bastien Nocera reports the other day on his personal blog about an upcoming feature that’s about to be implemented in the next release of the Flatpak universal binary format.
The GUADEC conference for GNOME developers is taking place these days in Karlsruhe, Germany, between August 12-14, and it looks like Mr. Nocera was supposed to present a lightning talk about what’s coming to Flatpak later in the year, as well as to run a contest related to his presentation, whose prize was a piece of hardware.
“Unfortunately, I didn’t get a chance to finish the work that I set out to do, encountering a couple of bugs that set me back,” said Bastien Nocera in the blog announcement. “Hopefully, this will get resolved post-GUADEC, so you can expect some announcements later on in the year.”
-
-
-
-
OpenSUSE/SUSE
-
-
-
We are happy to announce that Ramadoni Ashudi design from Indonesia is selected as official logo for openSUSE.Asia Summit 2016 in Yogyakarta, Indonesia. As the winner Ramadoni Ashudi will receive a “magic box” from the committee.
-
Red Hat Family
-
Red Hat, through Scott McCarty, is happy to announce the general availability of Red Hat Enterprise Linux Atomic Host 7.2.6, a maintenance update that adds many performance improvements for most of the included components.
For those behind their Red Hat Enterprise Linux Atomic Host reading, we’ll take this opportunity to inform them that Red Hat’s Atomic Host offering for the commercial Red Hat Enterprise Linux (RHEL) operating system is a specially crafted version of the OS that has a small footprint and it’s designed to run containerized workloads.
-
Recently, Red Hat Inc (NYSE: RHT) has taken a back seat to Ubuntu in low cost cloud infrastructure. Ubuntu Linux has been a key rival of Red Hat and has experienced major success in capturing cloud infrastructure totaling to over a 65 percent share of all cloud server operating system instances.
Deutsche Bank’s Karl Keirstead commented on Red Hat’s potential to fulfill its opportunities in cloud infrastructure. Keirstead’s comments came after he met with Ubuntu company management.
-
Red Hat defended its decision to take a stand against North Carolina’s House Bill 2 when asked about it by a Washington think tank at Thursday’s shareholders meeting in Raleigh.
Justin Danhof, general counsel for the National Center for Public Policy Research, attended the meeting to seek an explanation from Red Hat about its decision to join an amicus brief along with 67 other companies, such as IBM and Cisco, in support of the U.S. Department of Justice’s opposition to the law. He posed his questions to Red Hat Chief Executive Jim Whitehurst, but company General Counsel Michael Cunningham responded.
-
A lawyer for a conservative think tank who appeared at Red Hat’s annual shareholder meeting Thursday to question the software company’s support of a lawsuit challenging North Carolina’s House Bill 2 characterized his move as part of a broader effort to reshape public perception of the law.
-
Finance
-
Fedora
-
So we have two jobs openings in the Red Hat desktop team. What we are looking for is people to help us ensure that Fedora and RHEL runs great on various desktop hardware, with a focus on laptops. Since these jobs require continuous access to a lot of new and different hardware we can not accept applications this time for remotees, but require you to work out of out office in Munich, Germany. We are looking for people with people not afraid to jump into a lot of different code and who likes tinkering with new hardware. The hardware enablement here might include some kernel level work, but will more likely involve improving higher level stacks. So for example if we have a new laptop where bluetooth doesn’t work you would need to investigate and figure out if the problem is in the kernel, in the bluez stack or in our Bluetooth desktop parts.
-
This was my last week at RedHat and I feel I had really good learning experience so far. I am happy that I had great mentors like Maririn Duffy, Ryan Lerch, Paul Frields, Pierre and Sayan who always helped me out whenever needed. For me personally, the biggest advantage has been the opportunity to work with some really wonderful people. Open source allowed me to make connections far outside my normal circle of co-workers. Having access to such a huge pool of talented people was daunting to me at first. I had to deal with issues I have not encountered before, like getting feedback for your design work or working with people from different time zones. But all this was a good learning experience. Working on open source projects allowed me to develop my skills and gain valuable experience working in highly collaborative software project. I learnt how to be able to function as a part of a team and contribute my time not to only to technical tasks but also to several side projects with respect to conferences like FAD, Flock etc. Lastly, I feel the experience that I have gained here will prove invaluable for my future career.
-
I spent previous week in Kraków at Flock. It is a conference of Fedora developers and users.
-
This week, we kicked off an initiative for engaging more women contributors in Fedora. Sumantro Mukherjee helped me guide new contributors on this Hangouts call. The purpose was to bring in more woman contributors to the Fedora Project and help them be industry-ready. As buzzwords in the industry boom, these meet-ups are focused to generate awareness in the first few rounds. Then, they address fields like the Internet of Things (IoT), ML, and mobile app development, to mention a few.
-
Last week, I got to attend the 2016 edition of Flock — the Fedora Contributor Conference. As always for Flock, the 2016 edition of Flock (in Krakow, Poland) provided an amazing opportunity to meet up and work alongside many of my fellow Fedora contributors for a week of talks, hackfests, workshops, and evening events.
-
Flock, the Fedora Contributors conference held annually in August has happened again. This year the conference was in Krakow, Poland. I was one of the organizers and my employer, Red Hat, paid for my trip. I continue to be thankful to Red Hat for their support of the Fedora community and, in this case, me. Completely without bias (hah!) I must also point out that this is the single best organized conference I have ever attended in my life. So strap in, this is a long roundup!
-
Debian Family
-
-
Derivatives
-
GNU/Linux developer Arne Exton informs us about the availability of a new build of his very popular ExLight Linux Live DVD operating system based on the latest Ubuntu and Debian technologies.
ExLight Linux Build 160810 is here to rebased the entire OS to the recently released Ubuntu 16.04.1 LTS (Xenial Xerus) operating system, as well as to upgrade the default desktop environment to Enlightenment 0.20.99.0 from 0.19.12, and move to a kernel from the Linux 4.6 series, specially optimized by Arne Exton to support more hardware.
-
ExLight Linux Live DVD has been downloaded about 2000 times per week the last two months. I have therefore made a new upgraded version of ExLight today (160810). I have also created a new special WordPress site for ExLight.
-
Canonical/Ubuntu
-
Canonical, through Sergio Schvezov, has had the great pleasure of announcing the release and general availability of Snapcraft 2.14 Snap creator tool for the Ubuntu 16.04 LTS (Xenial Xerus) operating system.
Coming hot on the heels of Snapcraft 2.13, the new 2.14 maintenance update is here to introduce a bunch of new plugins, namely rust, godeps, and dump. You can find more information about each one by running the “snapcraft help dump|rust|godeps ” command in a terminal window.
-
One of our readers was asking us last week if we have any news on when Ubuntu Touch will switch to a newer version of Ubuntu? The official answer came a few days ago from Canonical’s Łukasz Zemczak, who reveals the fact that the Ubuntu mobile OS will soon be rebased on Ubuntu 16.04 LTS (Xenial Xerus).
It appears that this is not the first time the Ubuntu Touch developers have been asked by Ubuntu Phone and Ubuntu Tablet users what’s the state of operating system’s baseline, which right now is still using the packages from the now deprecated Ubuntu 15.04 (Vivid Vervet) release.
-
Flavours and Variants
-
Today, August 12, 2016, Lubuntu Linux maintainer Simon Quigley announced something that many of you have expected for so long, the migration of the lightweight Ubuntu flavor to the modern LXQt desktop environment.
-
-
The most exciting developments in maker movement electronics is happening with low-cost Linux devices. In case you might not have heard of it, the Omega2 is a very small, very low-cost IoT Linux computer that you can program using many of the programming languages you already know. Check out the compelling Kickstarter video here.
-
IEI’s wide temperature “Hyper-BW” Pico-ITX SBC expands upon Intel’s Braswell chips with 2x mini-HDMI, 4x USB, and 2x serial, plus SATA, M.2, and GbE.
IEI’s 100 x 72mm Hyper-BW recently showed up on an IEI product page with a “preliminary” tag, and without an announcement. The SBC follows earlier IEI Pico-ITX boards like the Bay Trail Celeron based Hyper-BT and the AMD G-Series SoC based Hyper-KBN. The Hyper-BW moves up to the latest Pentium and Celeron models within Intel’s 14nm “Braswell” line of SoCs, and can be compared with boards like Commell’s Braswell-based LP-176 Pico-ITX SBC.
-
-
MediaTek’s Helio X30, due mid-2017, will likely be one of the first 10nm SoCs, and among the first to tap ARM’s new Cortex-A73 cores.
MediaTek has revealed an upcoming Helio X30 system-on-chip (SoC) that will likely be one of the first 10nm fabricated SoCs to arrive when it ships in mid-2017. The deca-core mobile SoC will also be one of the first to use ARM’s new Cortex-A73 successor to the Cortex-A72, according to PhoneRadar, which based its story in part on an EETimes China interview [translated] with MediaTek CTO Zhu Shangzu.
-
Phones
-
DataWind has launched its PocketSurfer GZ smartphone in India. Priced at Rs 1,499, the handset is powered by Linux operating system. DataWind has partnered with Reliance Communications for the device. Consequently, the PocketSurfer GZ comes bundled with RCom’s offerings which will enable users to enjoy free internet access for a year.
-
Android
-
-
-
-
-
-
-
-
-
Google has been hit by a $6.75 million antitrust fine in Russia for requiring phone manufacturers to preinstall its apps on Android mobile devices. The majority of smartphones and tablets solid in Russia run on Android, and domestic search engine rival Yandex filed a complaint last year that the US company was abusing its position. The fine itself is small — less than what the company makes in an hour, notes Recode — but the decision shows increasing enmity to Google in Europe.
One of the many antitrust complaints currently being levied against Google by the EU focuses on the same issue: accusing the company of abusing its dominant position in the market by forcing manufacturers to preinstall its services on Android devices. Unlike the rest of Europe, though, Russia has a viable competitor to Google — Yandex has about 60 percent of the search market in the country. With the shift to mobile, though, the company seems worried it’s being out-maneuvered by Google for the future of search.
-
-
In 1998, I was part of SGI when we started moving to open source and open standards, after having been a long-time proprietary company. Since then, other companies also have moved rapidly to working with open source, and the use and adoption of open source technologies has skyrocketed over the past few years. Today company involvement in open source technologies is fairly mature and can be seen in the following trends:
-
The web app is using open source technologies such as PHP, Bootstrap, MySql and Apache and the team is working on making the web application code as well as the image recognition algorithm open source.
-
-
Open source’s momentum is building in the telecom industry due in part to the appeal of a more collaborative development process between vendors, users and developers. Open source also has the potential to reduce development cycle times and costs; lay the foundation for improved software interoperability and customization across different companies; and deliver new solutions, such as those needed to support NFV.
-
GigaSpaces, a provider of in-memory computing (IMC) technologies, announced the launch of XAP 12, the company’s first open source initiative for its high-performance data grid. The open core enables developers to build upon a proven IMC platform that’s been utilized by hundreds of Fortune 500 companies worldwide, including top banks, leading retailers, and many of the world’s largest transportation, telecommunications and healthcare companies.
-
If you’re not using Simplenote, you’re missing out. This… well, simple note app has been a standby and lifesaver for me for years, though occasionally I have worried about its future: Will it survive if Automattic, which bought it back in 2013, goes under or gets bought itself? What if the servers go down? Is there a god, and if so, does he or she use Simplenote, too?
At least a couple of those worries are alleviated with the news that Automattic is open-sourcing the Simplenote apps on iOS, Mac and Android. The Windows app was already open, so this doesn’t come as a total surprise, but it’s still good news.
-
-
Simplenote is a lightweight yet full-featured note taking app that’s cross-platform on Android, iOS, Windows and Mac. It’s a great alternative to Evernote and their new pricing, and offers syncing and sharing as well as the ability to work while offline. And as of today, it’s now open source on all platforms.
-
-
Databases
-
Percona unveiled a new open sourced platform for MongoDB called the Percona Memory Engine for MongoDB.
With Percona Memory Engine for MongoDB, Percona has now delivered an open source in-memory storage engine that works with Percona Server for MongoDB, the open source drop-in replacement for the MongoDB Community Edition that includes enterprise-grade features and functionality.
-
Oracle/Java/LibreOffice
-
The Document Foundation today released its annual accounting report highlighting accomplishments for the year. “TDF Annual Report starts with a Review of 2015, with highlights about TDF and LibreOffice, and a summary of financials and budget.” LibreOffice saw two major and 12 minor releases that year earning €1.1 million in donations. The project now sports over 1000 contributors with 300 making commits in 2015.
This years report covered a long list of topics beginning with the City of Munich and Russian RusBITech joining The Document Foundation’s Advisory Board. The migration team got a honorable mention before the diagram of the power structure. But the best portion was that dedicated to the releases. Two major releases were announced in 2015, 4.4 and 5.0, as well as 12 minor updates, 4.3.6 through 5.0.4.
-
Pseudo-Open Source (Openwashing)
-
FSF/FSFE/GNU/SFLC
-
I hadn’t realized until now that it’s the Free Software Foundation’s first time issuing an annual report since it was formed thirty years ago.
The Free Software Foundation published its first annual report today, which covers their 2015 fiscal year from 1 October 2014 to 30 September 2015.
-
-
-
-
-
Public Services/Government
-
Over the next three years, US federal agencies will be required to publish at least 20 percent of their newly-made custom software as open source. This requirement is part of a pilot established by the Federal Source Code Policy published last week by the President’s Executive Office.
-
The Obama administration has released a new federal open-source policy for improving access to software developed by or for federal agencies.
-
In short: All new code developed for the federal government needs to be made available to other federal government organizations. And then a small portion of that is going to be looked at being released to the public.
I’m still reading through everything—it’s a rather dull read—but I was surprised at what was not included. Specifically, there’s no mention of the GNU Public License (GPL) whatsoever. In fact, the only mention of GNU or free software is one word tucked away at the bottom of the document under a definition of “Open Source.” I’m not surprised, but still it’s a bit disappointing.
-
Licensing/Legal
-
-
While the GPL family are the most popular copyleft licenses, they are by no means the only ones. The Mozilla Public License and the Eclipse Public License are also very popular. Many other copyleft licenses exist with smaller adoption footprints.
As explained in the previous section, a copyleft license means downstream projects cannot add additional restrictions on the use of the software. This is best illustrated with an example. If I wrote MyCoolProgram and distributed it under a copyleft license, you would have the freedom to use and modify it. You could distribute versions with your changes, but you’d have to give your users the same freedoms I gave you. If I had licensed it under a permissive license, you’d be free to incorporate it into a closed software project that you do not provide the source to.
But just as important as what you must do with MyCoolProgram is what you don’t have to do. You don’t have to use the exact same license I did, so long as the terms are compatible (generally downstream projects use the same license for simplicity’s sake). You don’t have to contribute your changes back to me, but it’s generally considered good form, especially when the changes are bug fixes.
-
They wanted line by line evidence, not pointers to the lines. You’d think there would be a script for that…
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
Open Source Hardware Camp 2016 will take place place in the Pennine town of Hebden Bridge. For the third year running it is being hosted as part of the Wuthering Bytes technology festival, featuring 12 talks on the Saturday and 4 hands-n workshops on the Sunday.
-
“Fuchsia”
-
-
-
Google appears to be working on a new operating system that’s written from scratch and appears to be target both phones and PCs, among other form factors.
This new OS is called Fuchsia and powered by what they call the Magenta and LK kernel options. Google hasn’t formally announced this new OS while the Git repository cites it as “Pink + Purple == Fuchsia (a new Operating System).” This Git repository is the main source of Fuschia/Magneta information right now.
-
Nigel Farage has spent his time post-Brexit working on his facial hair.
The usually clean-shaven former UKIP leader wowed social media with his daring new look.
-
Science
-
I am always impressed with how smoothly a trained lawyer can present “facts” without presenting any… facts. Below is CSPAN video of once-Congressman Mike Pence (who would later go on to become Governor of Indiana and the official Republican nominee for Vice President of the United States) arguing against the “theory” of evolution on the Congressional floor in an attempt to reinsert creationism (masquerading under the new term “intelligent design”) back into public school – using the Bible as his source of…, what? Evidence?
-
Health/Nutrition
-
The West’s anti-Russian bias is so strong that normal standards of fairness are cast aside whenever a propaganda edge can be gained, a factor swirling around the treatment of Russian athletes at the Rio Olympics, Rick Sterling says.
-
This week on CounterSpin: One of the legacies of Michael Brown’s killing, two years ago this week, was the exposure of police departments like Ferguson, Missouri’s, that have a system for profiting from fines and fees for low-level infractions that targets African-Americans disproportionately. That’s only one aspect of the interrelationship between economics, race and criminal justice our guest says calls out for scrutiny. Donna Murch is associate professor of history at Rutgers and author of Living for the City: Migration, Education and the Rise of the Black Panther Party in Oakland, California. We’ll talk about her new essay, “Paying for Punishment: The New Debtors Prison.”
-
“For many years, chemicals with unknown toxicities, such as PFASs, were allowed to be used and released to the environment, and we now have to face the severe consequences,” said lead author Xindi Hu, a doctoral student in the Department of Environmental Health at Harvard Chan School and Environmental Science and Engineering at SEAS. “In addition, the actual number of people exposed may be even higher than our study found, because government data for levels of these compounds in drinking water is lacking for almost a third of the U.S. population—about 100 million people.”
-
Security
-
-
-
-
-
-
-
-
There’s been a bunch of coverage of this attack on Microsoft’s Secure Boot implementation, a lot of which has been somewhat confused or misleading. Here’s my understanding of the situation.
Windows RT devices were shipped without the ability to disable Secure Boot. Secure Boot is the root of trust for Microsoft’s User Mode Code Integrity (UMCI) feature, which is what restricts Windows RT devices to running applications signed by Microsoft. This restriction is somewhat inconvenient for developers, so Microsoft added support in the bootloader to disable UMCI. If you were a member of the appropriate developer program, you could give your device’s unique ID to Microsoft and receive a signed blob that disabled image validation. The bootloader would execute a (Microsoft-signed) utility that verified that the blob was appropriately signed and matched the device in question, and would then insert it into an EFI Boot Services variable[1]. On reboot, the boot loader reads the blob from that variable and integrates that policy, telling later stages to disable code integrity validation.
-
-
Defence/Aggression
-
Well, this was an interesting one. As I was stepping out of the shower this morning, my phone rang – RT asking if I could do an interview asap.
The subject under discussion? A former acting head of the CIA apparently recommending that the USA covertly start to murder any Iranian and Russian citizens operating against ISIS in Syria, and bomb President Assad “to scare him, not to kill him”.
-
The area of Speakers’ Corner has been cordoned off, while pictures show a number of police cars on the scene.
Police were alerted shortly before 6am after a member of public found a man with injuries.
A Metropolitan Police spokesman said: “Police in Westminster were called to Hyde Park, W2 at 05:50hrs on Friday, 12 August, following concerns for a man.
“Officers attended and found a man deceased. This incident is being treated as suspicious.
-
A series of coordinated blasts across Thailand has targeted tourist towns leaving four dead and many injured, with reports of more explosions.
In the popular resort town of Hua Hin four bombs exploded over the last 24 hours. Several blasts also hit the island of Phuket on Friday.
No group has said it carried out the attacks, but suspicion is likely to fall on separatist insurgents.
The timing is sensitive, as Friday is a holiday marking the queen’s birthday.
-
At least four people have been killed in a series of bombings targeting some of Thailand’s most popular tourist resorts.
The attacks started with two explosions in the beachside town of Hua Hin that were detonated remotely just minutes apart in a bar area popular with foreigners.
Police said a Thai woman was killed and 21 people were injured, sparking chaos as crowds fled and local shops and restaurants were shut down on Thursday night.
-
This year marks the anniversary of the Battle of Verdun, which raged from 21 February to 18 December 1916. By the end of this terrible struggle, one of the longest and bloodiest battles of the First world war, some 143,000 German and 162,000 French soldiers had been killed. But because British forces were not involved in this battle, this part of the Western Front is less visited by the British than are the more westerly battlefields such as those of the Somme and the Marne. And yet the whole area, throughout the length of the war, saw some of the worst battles of the entire conflict – not least in the hilly, forested area south west of Verdun, known as the Argonne. Such spots can teach us a great deal about the past and draw lessons for the future, but as I discovered, in these raw post-Brexit times, even what they tell us is a matter of controversy.
-
Donald Trump, who has railed against the political influence of military contractors, denounced wasteful Pentagon spending, and promised a less interventionist foreign policy has nevertheless added to his transition team the leader of a group of defense contractors who advocate greater American militarism.
Michael Rogers, the hawkish former chair of the House Intelligence Committee, will be advising the Trump transition team on national security, the Wall Street Journal reported on Tuesday.
After leaving Congress, Rogers founded a pressure group called Americans for Peace, Prosperity, and Security, intended to “help elect a president who supports American engagement and a strong foreign policy.”
-
The Cold War was pointless except for the Dulles brothers’ interests and those of the military/security complex. The Soviet government, unlike the US government today, had no world hegemonic asperations. Stalin had declared “Socialism in one country” and purged the Trotskyists, the advocates of world revolution. Communism in China and Eastern Europe were not products of Soviet international communism. Mao was his own man, and the Soviet Union kept Eastern Europe from which the Red Army drove out the Nazis as a buffer against a hostile West.
-
The Pentagon announced an additional $1.15 billion in weapons sales to Saudi Arabia this week, even as a three-month cease-fire collapsed and the Saudi-led coalition resumed its brutal bombing campaign of the Yemen capital Sana.
The U.S. has already sold more than $20 billion in weapons to Saudi Arabia since the war began in March 2015, defying calls from Human Rights Watch and Amnesty International to cut off support. The Saudi-led coalition is responsible for the majority of the 7,000 deaths in the conflict, which has left more than 21 million people in need of urgent humanitarian assistance. Saudi Arabia has been accused of intentionally targeting homes, factories, schools, markets, and hospitals.
On Tuesday, the coalition targeted and destroyed a potato chip factory, killing 14 people (see top photo). The Yemeni press has since reported that coalition has conducted hundreds more airstrikes across the country, killing dozens of people.
-
But how about a report by the Pentagon’s Office of Inspector General saying that the US Army had $6.5 trillion in unaccountable expenditures for which there is simply no paper trail? That is 6,500 billion dollars! Have you heard about that? Probably not. That damning report was issued back on July 26 — two whole weeks ago — but as of today it has not even been reported anywhere in the corporate media.
-
The Pentagon confirmed this week that U.S. forces are indeed on the ground in Libya as the fight against the Islamic State (ISIS) continues.
A “small number of U.S. forces have gone in and out of Libya to exchange information with these local forces in established joint operations centers, and they will continue to do so as we strengthen the fight against [ISIS] and other terrorist organizations,” Deputy Defense press secretary Gordon Trowbridge said Wednesday.
The news comes just days after the U.S. launched new airstrikes in Libya, centering largely around the strategic port city of Sirte, on August 1. At the time, defense officials claimed there were no troops on the ground supporting the bombings.
On Tuesday, the Washington Post reported that “U.S. Special Operations forces are providing direct, on-the-ground support for the first time to fighters battling the Islamic State in Libya,” quoting U.S. and Libyan officials.
-
The U.S. foreign policy establishment cloaks its desire for global dominance in the language of humanitarianism and “democracy promotion” even when the policies lead to death and chaos, as James W Carden describes.
-
Paul Kagame led his country away from genocide and war, but today his regime is upheld by authoritarian controls and political violence.
[...]
In 1994, Paul Kagame and his rebel forces, the Rwandan Patriotic Front (RPF), took Rwanda’s capital Kigali from Hutu extremists, bringing an end to the genocide that saw close to a million people killed in 100 days. Although only officially elected president in 2000, Kagame has been the de facto leader ever since and, following recent changes in the nation’s constitution that allow him to run for a third term, he could remain in power until 2034. Rwanda has seen great progress during his incumbency and has been held up by many in the international community as an exemplary model of development in Sub-Saharan Africa.
-
Who was in charge of U.S. foreign policy when Hillary Clinton was secretary of state? That is a legitimate question to consider in light of the most stunning revelation yet mined from the Wikileaks hack. George Soros is suggesting an intervention in domestic Albanian politics, and getting his way!
-
It’s the secret code that cadets at the U.S. Merchant Marine Academy are advised to use if things get really rough during their year-long shipboard training on merchant vessels thousands of miles from shore, or at ports far from home. Women — and men, in some cases — can use it as a fail-safe if the lewd comments and unwanted advances from fellow sailors escalate to something worse. The government will bring them ashore.
-
As the Times also notes, CSIS is funded largely by Western and Gulf monarchy governments, arms dealers and oil companies, such as Raytheon, Boeing, Shell, the United Arab Emirates, US Department of Defense, UK Home Office, General Dynamics, Exxon Mobil, Northrop Grumman, Chevron and others.
Anyone with a seven-year-old’s understanding of causality can conclude that CSIS would, in the aggregate, promote the expansion of the military and surveillance state, since that’s who pays their bills; what the Times did was reveal a specific, rather direct example, using heretofore secret documents.
-
You know how it is. You just get back from a trip to the store and your significant other says “Honey, I just realized we are all out of AK-47s. And while you’re at the market, could you also grab a couple of mortars and some grenades in case your mother stops by again unexpectedly?”
Yes, it could be Texas, but it actually is what’s going on in Baghdad.
Iraq news site Niqash tells us about a market in Baghdad’s Sadr City, where masked men display their wares on open tables the same way vegetable sellers do in other city markets. Next to grenades on the tables are rockets, mortars and plenty of other weaponry, with markings that indicate they come from a number of different sources. Welcome one and all to Maridi market, one of Baghdad’s, if not, Iraq’s, most famous “illegal” arms markets.
(The photo above shows beautiful Sadr City back in the good old days, when America liberated it.)
There are a lot of ways he obtains weapons, said one trader in the market. The most significant route is across unguarded border crossings from NATO ally Turkey. The guns and other weapons enter Kurdistan (another American ally) and are then brought to Baghdad; checkpoints (manned by Iraqi security forces the U.S. pays for) don’t seem to be a problem and if they are, counterfeit ID cards or a bribe will often work.
-
Not mentioned at all in this narrative is the role played by Joshua Goldberg, a Jewish guy who adopted many avatars online to incite all kinds of violence, including, under the name of Australi Witness, Garland. In December Goldberg was deemed incompetent to stand trial, though in June it was decided with more treatment he might become competent enough to stand trial, so they’re going to check again in four months.
So, the cell that committed the Garland attack consisted of the two now-dead perpetrators, four informants, an undercover FBI officer, a mentally ill troll, and Hendricks.
[...]
Has the FBI simply lost track of who are real and who are the people it is paying to play a role? Or is it possible someone from another agency, claiming to be FBI, recruited Hendricks (don’t laugh! That’s one potential explanation for Anwar al-Awlaki’s curious ties to US law enforcement, a story that wends its way through a related mosque in VA)?
Sure, maybe Hendricks is making all this up (at the very least, it may necessitate the BoP to protect him in prison since he has now publicly claimed to be a narc). But FBI’s network of informants sure is getting confusing.
-
American media love the rich. Besides constant, assiduous attention to the things they buy and eat and wear, we see lists of the richest people alongside numbers indicating what we straightforwardly refer to as their worth. Of less interest is how the rich got and stay that way.
And the same holds true for corporations, which, of course, are a big part of how rich people got and stay that way. Success is success after all, and for all the tales of a muckraking media, our guest’s experience suggests that when it comes to one of the most stupendously successful US industries, the press corps don’t seem all that eager to look behind the curtain.
-
Washington’s foreign policy hot shots are flexing their rhetorical, warmongering muscles to impress Hillary Clinton, including ex-CIA acting director Morell who calls for killing Russians and Iranians, notes ex-CIA analyst Ray McGovern.
Perhaps former CIA acting director Michael Morell’s shamefully provocative rhetoric toward Russia and Iran will prove too unhinged even for Hillary Clinton. It appears equally likely that it will succeed in earning him a senior job in a possible Clinton administration, so it behooves us to have a closer look at Morell’s record.
My initial reaction of disbelief and anger was the same as that of my VIPS colleague, Larry Johnson, and the points Larry made about Morell’s behavior in the Benghazi caper, Iran, Syria, needlessly baiting nuclear-armed Russia, and how to put a “scare” into Bashar al-Assad give ample support to Larry’s characterization of Morell’s comments as “reckless and vapid.” What follows is an attempt to round out the picture on the ambitious 57-year-old Morell.
-
A report issued on Thursday by a Republican congressional task force confirmed that military leaders doctored intelligence analyses in order to paint a rosier picture of the war on the Islamic State (ISIL).
The investigation confirms Daily Beast reporting first published last year on the integrity of those intelligence reports, which originated from US Central Command (CENTCOM)—the arm of the Pentagon that oversees operations in the Middle East, North Africa and Central Asia.
Rep. Brad Wenstrup (R-Ohio), one of the task force’s members, noted that the findings are preliminary. There is still a Pentagon inspector general investigation into the allegations, which were brought to the watchdog last year by fifty whistleblowers.
“We still do not fully understand the reasons and motivations behind this practice and how often the excluded analyses were proven ultimately to be correct,” Wenstrup said, according to The Hill.
In its report, the task force noted that it “did not receive access to all the materials it requested.” The group said it would “continue its work following the conclusion of the [Department of Defense inspector general] investigation and other ongoing efforts.” That probe is supposed to wrap up by the fall.
-
There’s a missing page to this recipe, one that has been deliberately deleted like a classified email from The Book Of Days. Trump runs around blaming Secretary Clinton for the state of the economy while arguing in tandem that Clinton and President Obama created ISIS out of thin air. “He’s the founder of ISIS,” Trump said on Wednesday. “He’s the founder of ISIS. He’s the founder. He founded ISIS. I would say the co-founder would be crooked Hillary Clinton.” The corporate “news” media lap it up because its “good television,” and even his most ardent opponents fail to say the one missing word.
Bush.
Noam Chomsky explained the phenomenon best, and it is remarkable to watch it unfold in real time. According to Chomsky, the most effective way to control a populace is to severely limit the parameters of debate, but have the debate within those hedged parameters be vigorous so people think something of worth is actually taking place. Hence, they shout and stomp about responsible budget priorities without ever discussing the bloated “defense” budget, because that topic has been deemed off limits. Likewise, they shout and stomp about ISIS and the economy without ever mentioning George W. Bush, because he is simply too embarrassing to too many people sitting behind important desks with a lot to lose.
-
Environment/Energy/Wildlife/Nature
-
Citing an investigation that revealed federal agents went undercover to spy on environmental activists, the Center for Biological Diversity (CBD) on Thursday filed nine Freedom of Information Act requests seeking information on surveillance of peaceful protests at federal fossil fuel auctions.
As they wrote at The Intercept in July, journalists Lee Fang and Steve Horn obtained emails showing that in May, local law enforcement and federal agents monitored and infiltrated a “Keep it in the Ground” protest at a Bureau of Land Management (BLM) auction in Lakewood, Colorado.
“The emails, which were obtained through an open records act request, show that the Lakewood Police Department collected details about the protest from undercover officers as the event was being planned,” they wrote. “During the auction, both local law enforcement and federal agents went undercover among the protesters.”
-
Environmentalists and industrialists were both shocked by the move from the coastal county once known as “Wide Open Whatcom” for its welcoming of oil refineries and a massive aluminum smelter.
-
Yesterday (August 11), approximately 200 protestors from the Oceti Sakowins (commonly known as the Sioux people)—joined by “Divergent” actress Shailene Woodley—blocked crews constructing the $3.7 billion Dakota Access Pipeline set to run through their land. Though the group remained peaceful, the Morton County Police Department arrested 12 for disorderly conduct or criminal trespass, reports the Associated Press.
-
Finance
-
There seems at the moment some confusion in the Brexit camp: is all the bad news just wishful imagination by Remainers, or is it real but caused by Remainers. Some specific thoughts on the extraordinary Telegraph editorial are here, but one event that was not in anyone’s imagination was the depreciation in sterling as the result became known. Brexiters tend to think markets know what they are doing, so they have resorted to all kinds of arguments why this depreciation was not really bad news.
First, the reason why it is bad news. A depreciation in sterling makes everyone in the UK poorer, because the goods we buy that are made overseas or sold in world markets (oil) will cost more. That this depreciation happened as a result of the vote is beyond dispute. So what do Leave apologists have to say in response? So far I have heard the following.
-
Democratic presidential nominee Hillary Clinton on Thursday offered her “strongest words yet against the TPP,” according to one progressive organization—but whether it will be enough to convince skeptics remains to be seen.
In an economic policy speech delivered in Warren, Michigan, Clinton said her “message to every worker in Michigan and across America is this: I will stop any trade deal that kills jobs or holds down wages—including the Trans Pacific Partnership. I oppose it now, I’ll oppose it after the election, and I’ll oppose it as President.”
-
One of Bernie Sanders’s most important proposals didn’t receive enough attention and should become a law even without a president Sanders. Hillary Clinton should adopt it for her campaign.
-
A new economic working paper reinforces an important reality: We need more government spending to repair the economy for millions of working Americans. Unfortunately, our political debate is being held back by an economic myth – one that has yet to be challenged in political debate, despite an ever-growing body of evidence against it.
-
Jill Stein and the Green Party filed their petitions for ballot access in 3 more states this week: Connecticut, New Hampshire, and Utah. The campaign is confirmed on the ballot in 28 states, and awaits state government confirmation in 7 others where we have filed in the last month. 12 more states have pending deadlines where we will be filing between now and September 9.
-
Fiscal austerity in the wake of the Great Recession—imposed by Republicans on the federal, state, and local levels—is responsible for the sluggish pace of economic recovery since 2009, states a new paper that undercuts conservative attempts to pin the blame on President Barack Obama.
“By far the biggest drag on growth throughout the recovery from the Great Recession has been the fiscal policy forced upon us by Republican lawmakers in Congress and austerity-minded state legislatures and governors,” wrote Josh Bivens of the Economic Policy Institute (EPI), which put out the analysis on Thursday.
Because the “ability of conventional monetary policy to spur recovery following the Great Recession was more limited than in any other post-war recovery,” Bivens explained, increases in government spending and federal aid to states were necessary to help working Americans following the recession that began in December 2007 and ended in June 2009.
-
Everyone loves the Olympics. They allow people all over the world to set aside their political and religious differences and enjoy a few weeks of healthy competition between a few thousand people who have spent years honing their skills.
At least, this is what we tell ourselves.
In fact, not everyone loves the Olympics. Often, the poorest sectors of society within the host countries experience displacement and other forms of oppression as authorities work hard to impress visiting athletes and spectators. In Brazil, the first South American country to serve as the international showcase, this was certainly true; more than 20,000 families were displaced to make way for Olympics-related infrastructure. In fact, the state of Rio de Janeiro, where the games are being held, is in such desperate financial circumstances that state workers are not being paid and health care centers cannot even afford to take on the Zika virus crisis. Rio declared bankruptcy ahead of the games, and the state’s governor declared a “state of calamity.”
But the mayor of Rio de Janeiro was quick to assure the world that the economic disaster “in no way delays the delivery of Olympic projects and the promises assumed by the city of Rio.” Apparently, delivering basic services to the city’s residents is a lower priority than accommodating the Olympics.
-
AstroTurf/Lobbying/Politics
-
Clutching Momentum and socialist party banners, and placards reading “Geordies got ya back Corbyn”, a crowd of about 50 people swarmed around the Labour leader as he arrived at the Hilton hotel in Gateshead on Thursday evening, chanting his name as he got out of his car. Owen Smith received no such welcome.
-
The shadow health secretary, Diane Abbott, a staunch Jeremy Corbyn supporter, has dismissed suggestions that the Labour party is being infiltrated by hard-left activists, saying the claims are being peddled by “people within the Westminster bubble”.
Abbott said the Labour deputy leader Tom Watson’s claims that the party was vulnerable to a takeover by Trotskyist entryists were a “distraction”.
Her comments come ahead of a court of appeal ruling on whether tens of thousands of new members of the Labour party will have the right to vote in the forthcoming leadership election between Corbyn and Owen Smith.
-
Every day he continues his spiral downward—and after his call for gun owners to commit acts of violence against Mrs. Clinton, it is clear he needs help, serious help. His comments and behavior have become more and more bizarre and detached from reality. He is in need of an intervention. And I believe only you can conduct it.
-
Federal Election Commission member Ann Ravel on Tuesday proposed a ban on political contributions by domestic subsidiaries of foreign corporations.
Ravel’s proposal cites The Intercept series last week reporting that American Pacific International Capital, a California corporation owned by two Chinese nationals, donated $1.3 million to Right to Rise USA, the main Super PAC supporting Jeb Bush’s presidential run.
Ravel wrote that as a result of Citizens United and subsequent Supreme Court decisions, “our campaign finance system is vulnerable to influence from foreign nationals and foreign corporations through Domestic subsidiaries and affiliates in ways unimaginable a decade ago.”
-
Like or hate Trump, the media bias against him for challenging the neoliberal order is astonishing, harkening back to Cold War thinking. He is vilified out of fear he might shake the old order up: Reorder NATO, work with the Russian president, focus money on US infrastructure.
[...]
The New York Times, Washington Post, mainstream/cable news reek of polemic and government “officials” in a stunning disinformation campaign while at the same time they try to dismiss Clinton’s continued flirtation with the FBI/IRS over email, the shenanigans of the Clinton Foundation, and her militaristic “love a man in uniform”, and her coup instigating past. Even former military commanders and the CIA have gotten in on 2016 presidential campaign.
-
When Bernie Sanders ended his run for the Democratic nomination, the small donor narrative seemed over for this presidential cycle. But last week, small donors roared back, reportedly fueling Donald Trump and the Republican National Committee’s huge July fundraising take.
At a rally last week, Trump announced that he had raised $35.8 million from 517,000 small donors with an average contribution of $69.
As usual, Trump’s numbers don’t quite add up. The total July fundraising take was $82 million. The campaign announced it had raised $64 million from an email and snail mail campaign, the bulk from small donors. But was the $69 average from a $35.8 million subset of one of these amounts? No telling until the official numbers are filed with the Federal Elections Commission later this month.
Until then, Trump won’t let the details get in the way. He boasted at a Columbus, Ohio, rally that small donors were keeping him honest: “I’m going to do what’s right for you,” he said. “[Hillary Clinton] has got to do right for her donors.”
-
If you turn on MSNBC or CNN any morning, all you’ll hear is the hosts and guests arguing about the latest absurd thing that Donald Trump has said.
On Monday, Trump laid out his economic plan, but the media ignored the details and the fact that his plan is Voodoo Economics 2.0, and they instead focused on the fact that he called Hillary Clinton unfit to serve as president.
[...]
Honestly, it doesn’t matter what day of the week or what time of day a person tunes into the 24-hour news networks, he or she can always find out the latest vapid and boorish insult that’s spewed from Trump’s lips.
The problem is… it isn’t news!
It’s nothing but pure infotainment.
The corporate commercial networks are much, much happier presenting personal drama in the form of packaged infotainment and faux outrage rather than any sort of programming in the public interest.
-
Officials from the FBI and Department of Justice met several months ago to discuss opening a public corruption case into the Clinton Foundation, according to a US official.
At the time, three field offices were in agreement an investigation should be launched after the FBI received notification from a bank of suspicious activity from a foreigner who had donated to the Clinton Foundation, according to the official.
FBI officials wanted to investigate whether there was a criminal conflict of interest with the State Department and the Clinton Foundation during Clinton’s tenure. The Department of Justice had looked into allegations surrounding the foundation a year earlier after the release of the controversial book “Clinton Cash,” but found them to be unsubstantiated and there was insufficient evidence to open a case.
-
Multiple FBI investigations are underway involving potential corruption charges against the Clinton Foundation, according to a former senior law enforcement official.
The investigation centers on New York City where the Clinton Foundation has its main offices, according to the former official who has direct knowledge of the activities.
-
There are 15 states with new voting laws that have never before been used during a presidential election, according to a report by the Brennan Center for Justice. These laws include restrictions like voter ID requirements and limits on early voting. Many are making their way through the courts, which have already called a halt to two laws in the past month — one in North Carolina and one in North Dakota.
“All the sides were pushing for opinions over the summer so that nobody would run into the concern that it was all of a sudden too late to shift what the state had been planning to do,” said Jennifer Clark, counsel for the Brennan Center’s Democracy Program.
We’re tracking the new laws and the suits against them in the run-up to Election Day. We’ll keep this updated as decisions roll in.
-
Here’s a news flash: if you’re a progressive, you can and should critique Hillary Clinton right now – and that doesn’t have to mean that you want Donald Trump to be president.
It means we are still using our brains, “That we are not checkmated,” as Michelle Alexander puts it, that engaging in discourse is not just possible, but necessary in a race with less than terrific choices. No matter who you ultimately vote for, don’t stop demanding a candidate endorse policies that benefit you in order to get your support, even if you vote for them.
Clinton should be pushed relentlessly by the left on her economic policies and history, for starters. While she made fun of Trump on the stump for having “a dozen or so economic advisers he just named: hedge fund guys, billionaire guys, six guys named Steve, apparently,” she is living in a glass house funded by Goldman Sachs and should be throwing no stones. We’ll see whether she does in the big economic policy speech she is due to give on Thursday.
-
There are lots of reasons to question the infatuation of pundits with polls and how too much of a fuss is made over statistically insignificant changes in their results. Post RNC and DNC, a lot of noise was made in terms of convention bumps and who was in the lead. Historically presidential candidates get convention bumps but after a couple of weeks it fades. No news here. Pundits nonetheless angst over them, especially when they pay for them and make them their main news story, such as what CNN has done recently.
Finally, aggregate public opinion polls in presidential races are meaningless–remember it is not the popular but the electoral vote that determines the president. The race for the presidency is really 51 separate elections, of which only about ten really matter because that is how few swing states there are.
-
Last week, I received the same response from a crowd of Bernie Sanders backers that I had seen another group of his supporters give the man himself the prior week in Philadelphia – they jeered me. I was kind of flattered, actually. In Bernie’s case, the negative reaction was in response to his support for the election of Hillary Clinton, against whom we had all campaigned for so long. In my case, I didn’t even argue against voting for Green Party candidate, Jill Stein, in California, a “non-battleground” state, but I did express the hope that no one who did so would mistake a protest vote for a strategy. In other words, we shouldn’t abandon the Democratic Party – where we may not feel loved – for the Green Party, where we may feel better, but go nowhere.
I found a bit of personal irony in the situation, in that I had come in for a quite similar response just down the hall in the very same building a little over four years ago. That night I sat on a panel with Rocky Anderson, a former mayor of Salt Lake City then seeking the presidency on the Justice Party ticket. What had met with audience disapproval then was my argument that, while my co-panelist seemed like a fine candidate, the problem was that if we had really wanted to effectively take on Barack Obama, what Anderson or someone else should have done was enter the Democratic primaries. Anderson ultimately did not make it onto the ballot in California; he received 86 write-in votes in San Francisco, some no doubt from that audience. He got 43,018 nationwide, 0.03 percent of the total.
-
House Speaker Paul Ryan is a servile political “eunuch” twisting himself to meet the capricious whims of Republican nominee Donald Trump, smirked Late Night host Stephen Colbert.
Yet Ryan is “the most powerful Republican politician in America,” according to the astute MSNBC host Lawrence O’Donnell, a long-time observer of American politics.
So which is it? Actually, Ryan fits both descriptions. Shamelessly endorsing Trump despite repeated racist and inflammatory statements, Ryan wants to display just enough support for Trump in this campaign to avoid alienating Republican voters who oppose both “free trade” and immigration.
-
Was it wrong for Senator Tim Kaine to accept $201,600 in corporate gifts –many of them from businesses and lobbyists seeking favors from state– during his eight years as Virginia’s lieutenant governor and then governor? That’s the question voters may ask as Mr. Kaine campaigns as Hillary Clinton’s vice-presidential running mate.
Sadly, our courts and state ethics commissions seem to be turning a blind eye to conflicts of interest.
Neither former Governor Kaine nor his successor Bob McDonnell broke any law when they accepted costly gifts from businessmen who had pending business interests before the state– because the State of Virginia had no conflict of interest law on the books when they accepted their gifts.
-
Pulitzer Prize-winning reporter James Grimaldi of The Wall Street Journal, who has covered the Clinton Foundation for years, looks at the relationship between the Clinton Foundation and the State Department during Hillary Clinton’s time as secretary of state, and what it would be if she became president. Newly released State Department emails include exchanges between top members of the Clinton Foundation and Clinton’s top State Department advisers, including Huma Abedin and Cheryl Mills. The FBI reportedly wanted to investigate the Clinton Foundation earlier this year, but U.S. Attorney General Loretta Lynch pushed back.
-
The group took inspiration from Ken Burns’ 2016 commencement speech at Stanford University. Burns’ performance in fact brings to the fore some of Fish’s points, and in particular the issue of the deportment of intellectuals in public. Burns was welcomed at Stanford as a celebrated documentary filmmaker — the level of recognition he was awarded was matched only by how comfortable the audience seemed to be to welcome the man who taught them so much about baseball, jazz, the Civil War and many other subjects.
However, when he launched into a bitter and urgent tirade against Donald Trump, the mood changed. At first, especially amongst the graduates, there was surprise and wild applause. But as Burns kept on that topic, digging deeper into Trump’s mendacity and utter lack of qualifications, as Burns began to talk about fascism and totalitarianism, there was less applause. He seemed to have overstayed his welcome.
Why is this important to note? Because it points to something that Richard Hofstadter noted half a century ago in his magisterial Anti-intellectualism in American Life — even when they approach others with humility, academic intellectuals are still often viewed with suspicion and written off as inherently arrogant and unnecessary to everyday life. And this is especially true when they appear in public. Then they may be intolerable. Fish takes on the job of putting them in their place: “Professors are at it again, demonstrating in public how little they understand the responsibilities and limits of their profession.”
-
Decades of voting for the corporate-controlled neoliberal elite has led to perpetual wars, the complete disintegration of several nations, resulting in millions of dead and millions of refugees on a scale not seen since WWII, to Al Qaeda-turned ISIS, to a situation on the brink of a catastrophic war between NATO and Russia, and to a nearly complete demise of the once vibrant middle class in most advanced economies. This in turn has resulted in extreme political discontent and a polarized political order rejecting the centrist “business as usual” neoliberal order. This rebellion of sorts is manifested by the rise of the ‘radical’ left in Greece, Spain and even the United States, countered by the rise of the far-right with France’s Le Pen, Germany’s AfD, Greece’s Golden Dawn, leading to a trend that has recently resulted in a Brexit vote in the UK and the rise of the Donald Trump phenomenon in the United States.
-
And quoting Martin Luther King, Jr., Lewis added, “We must be hopeful. We must be optimistic. We must never hate. As Dr. King would say, hate is too heavy a burden to bear.”
Lewis also maintains that non-violence is key.
“You were a founder of the SNCC, which was a student council that was specifically designed around nonviolence,” Noah pointed out. “That was an important distinction that you had to make—I’ve always been fascinated as to why you made that distinction.”
-
Why anti-racism and migrants rights activism need to be central to anti-austerity campaigning.
-
In what is a consolation victory for the Labour Party’s establishment in the Court of Appeal, it has been revealed by WikiLeaks that there may be more to the decision than meets the eye.
After Sir Philip Sales QC overruled the previous High Court decision to allow the 130,000 disenfranchised Labour Party members to vote in the up and coming leadership election – notorious whistle-blower Wikileaks revealed that Sales had been a Blair insider for years, having been recruited as Junior Counsel to the Crown in 1997.
-
Censorship/Free Speech
-
BuzzFeed had a long and interesting article earlier this week noting Twitter’s ongoing difficulty in figuring out an appropriate way to deal with harassment and abuse that is often heaped upon certain users — especially women and minorities. The article is interesting — even as Twitter disputes some of its claims. It’s also noteworthy that this debate is not even remotely new. Last year, I wrote about it, suggesting that one possible solution is to switch Twitter from being a platform into being a protocol — on which anyone could then build services. In that world, Twitter could then offer various filters if it wanted — while other providers could compete with different filters or services. Then the tweets could flow without Twitter having to take responsibility, but there would be options (possibly many options) for those who were dealing with abuse or harassment.
Not surprisingly, that kind of suggestion is unlikely to ever be adopted, but reading through the BuzzFeed article, something else struck me. To some extent, the article seemed a bit unfair in portraying some of Twitter’s execs as willfully clueless about the abuse and harassment. It repeatedly portrays those who support freedom of expression as somehow being unreasonable extremists.
-
Another day, another case of Facebook disappearing a video that it should have left up. A politician in Hong Kong says that Facebook banned him from the site for 24 hours for a “terms of service violation” after he posted a video of him confronting men who had been following him around for weeks.
-
Privacy/Surveillance
-
-
Rapidly developing technology exposes communities of color to near-constant surveillance and over-policing.
-
La Quadrature du Net supports Reporters Without Borders with its action against the German bill on BND surveillance, which would allow the German foreign intelligence service to spy on foreign journalists. This bill is a direct attack on freedom of information, and thus undermines democracy and fundamental rights. German MPs must refuse to yield on values that they would defend for their own country just as well as foreign surveillance is concerned. Fundamental rights cannot simply be accommodated whenever convenient.
La Quadrature du Net seizes the opportunity to remind that attacks on the rights of journalists, which are indeed intolerable, must not distract from massive infringement on the fundamental rights of the whole of the population, as entailed in the various surveillance laws passed in the recent years across European Union Member-States and which, far too often, are in contradiction with the principles of the Charter of Fundamental Rights of the European Union.
Similarly, foreign surveillance laws should serve as warnings on conditions by which intelligence, individually targeted or wide-ranging, is being shared between European Member-States and third parties, as well as on agreements to share or access interception systems : usually downright absent from the laws on foreign intelligence (in France or elsewhere), these provisions constitute a grave danger of collateral surveillance being carried out in the greatest opacity and with no avenue of appeal.
-
Illinois has joined the growing ranks of states limiting how police may use cell-site simulators, invasive technology devices that masquerade as cell phone towers and turn our mobile phones into surveillance devices. By adopting the Citizen Privacy Protection Act, Illinois last month joined half a dozen other states—as well as the Justice Department and one federal judge—that have reiterated the constitutional requirement for police to obtain a judicial warrant before collecting people’s location and other personal information using cell-site simulators.
By going beyond a warrant requirement and prohibiting police from intercepting data and voice transmissions or conducting offensive attacks on personal devices, the Illinois law establishes a new high watermark in the battle to prevent surveillance technology from undermining civil liberties. Illinois also set an example for other states to follow by providing a powerful remedy when police violate the new law by using a cell-site simulator without a warrant: wrongfully collected information is inadmissible in court, whether to support criminal prosecution or any other government proceedings.
-
Let’s take Turkey, for instance. Yes the country with the petulant and easily-upset President Tayyip Erdogan, also has some reporters that truly just make stuff up. For instance, you can read about one reporter who managed to find some secret documents from the plotters of the recently failed coup attempt against Erdogan, and you can see an image of the secret codes she found below.
[...]
Yup, those are cheat codes for Grand Theft Auto 4. The reporter, meanwhile, apparently insisted that these were secret communications by the plotters against Erdogan. And you have to admit that that doesn’t make any sense, because if those plotters could get more guns and health just by repeating a video game cheat code, the coup probably would have went off without a hitch.
-
Civil Rights/Policing
-
The social media gripped-world has now started to think about the consequences of the skyrocketing presence of websites like Facebook in their life.
No one would have thought, a simple Facebook post would invite a life-threating experience for a 74-year-old man. But it happened.
Australia-based Kenneth Rothe used to run two hotels, Nirvana Village and Blue Dolphins, in Nambucca, New South Wales. Everything was going fine until a dark day came when a Facebook post popped up out of nowhere and destroyed Rothe’s life thereon.
The following post was made by an electrician named David Scott in March 2014,
“Pedophile [sic] warning:- Nambucca has been used as a relocation for these monsters – blue dolphin –nirvana hotel and above the Indian restaurant! …Bus stops are right out front of theses hotels for our children?”
Rothe accommodated the ones affected by family disputes but he never allowed pedophiles and people with a criminal history to stay at his properties.
After the post, Rothe started experiencing anonymous calls with consent for hanky-panky acts. He even requested Scott for an apology regarding the problems he was facing due to the post but his request only fell upon deaf ears.
-
Donald Trump says it would be “fine” to try Americans suspected of terrorism at the Guantanamo Bay detention center if possible.
The Miami Herald asks Trump whether he’d approve new detentions at the prison if he’s elected president. The Republican says he wants to ensure the U.S. has a “safe place” to keep a “radical Islamic terrorist.”
-
Nearly 100 people have been shot in Chicago in less than a week, pushing the number of shooting victims so far this year to more than 2,500 — about 800 more than this time last year, according to data kept by the Tribune.
Between last Friday afternoon and early Thursday, at least 99 people were shot in the city, 24 of them fatally. At least nine people were killed on Monday alone, the deadliest day in Chicago in 13 years, according to Tribune data. Among the wounded that day was a 10-year-old boy shot in the back as he played on his front porch in Lawndale.
-
British and NZ governments are facing calls to summon Australian high commissioners to explain revelations of child abuse and sexual assault
-
The late Duke of Westminster is characterised as a “philanthropist” by mainstream media even though the percentage of both his income and his wealth he gave to charity was less than most ordinary people’s mite, myself included, and I am willing to bet that what he did do, was tax-deductible. That a parasite who sat on £9 billion of unearned money in a country where disabled people commit suicide from poverty, and who got two O levels from Harrow, was Prince Charles’ closest friend, cuts through the lying propaganda about the Royal family we are constantly fed.
-
One day last fall, Niya Kenny was sitting in her math class at Spring Valley High School in Richland County, South Carolina, when a police officer came into the classroom. A girl in her class had refused to put away her cell phone, and the teacher had summoned an administrator, who called on the officer assigned to the school.
Niya thought the officer was bad news — his name was Ben Fields, but he was so aggressive that students knew him as Officer Slam. As soon as he entered the room, she called out for other students to record him.
-
Ash-Lee Woodard Henderson: “We have always said that state violence was bigger than just police murdering black people.”
-
“Violence is never the answer” is a sentiment I often hear parroted by people who celebrate the 4th of July in America, a holiday commemorating a violent and deadly rebellion. People have a habit of glorifying violence in history, while condemning violence in modern times.
I’ve seen people who claim to love Malcolm X denounce modern day revolutionaries who embody the same principals that made X who he was. It seems that there are many people who only like the idea of revolution if they’re reading about it in a history book.
-
Internet Policy/Net Neutrality
-
It was mid-March 1992, and Mark McCahill had never been to San Diego before. Back home in Minneapolis, the skies had been dumping snow for six months, and would keep at it for several more weeks. McCahill checked into the Hyatt Islandia, an 18-story high-rise hotel overlooking Mission Bay. “There were palm trees,” he recalls. “Boy, was it nice.”
-
The digital divide is alive and well in 2016 and there are still millions of people in the United States living without internet access. And a court decision that came down this week hasn’t helped matters.
On Wednesday, the 6th Circuit Court of Appeals blocked the FCC’s 2015 order to preempt state-level restrictions in North Carolina and Tennessee on municipalities seeking to build their own high-speed broadband networks.
-
Intellectual Monopolies
-
Trademarks
-
Copyrights
-
Some long-time moderators of KickassTorrents have come together with a common aim to bring back the website to its former glory. To achieve this goal and maintain the community website Katcr.co, the KickassTorrents crew has asked for donations. They are accepting donations via PayPal and a Gofundme campaign.
-
It is an irony of these formerly high-tech holdings that they are far less durable than old-fashioned paper-based systems. And researchers studying them face problems of compatibility that simply don’t arise with paper. This is a major issue that is only now being faced, as cultural figures of Greer’s generation pass on their archives to universities and libraries, who must start to grapple with the core tasks of deciphering and preserving them.
The good news is that once they have been decoded, they can be transferred to other media, and in more open formats that will be easier to access in the years to come. But that still leaves the problem of how to store all these archives in a way that will stand the test of time. Perhaps they will be encoded as data held on the ultimate storage medium, DNA. Or maybe it would just be easier to print the lot out on paper.
-
A few weeks ago this Blog explored the possible of implications of a case currently pending before the Court of Justice of the European Union (CJEU), Marc Soulier C-301/15, in particular should the Court follow the Opinion of Advocate General (AG) Wathelet. This reference for a preliminary ruling from France concerns the compatibility with EU law of the 2012 loi (Law No 2012-287 of 1 March 2012) adopted to allow and regulate the digital exploitation of out-of-print 20th century books.
The AG held the view that such law is not really compatible with EU law because it envisages a mechanism that, contrary to Articles 2 and 3 of the InfoSoc Directive, gives approved collecting societies – rather than authors – the right to authorise the reproduction and the representation in digital form of out-of-print books.
In my comment to the Opinion, I highlighted how the law on out-of-print books might not be the only case of potential incompatibility with EU law. In particular, in early July France introduced Loi No 2016-925 on la liberté de la création, l’architecture et patrimoine (freedom of creation, architecture and cultural heritage), which introduces new provisions into the French Intellectual Property Code (IPC) to regulate the publication of a plastic, graphic or photographic work by an online communication service. In particular, new Article 136-2(1) IPC provides that the publication of a plastic artwork, graphic or photographic work by an online communication service is subject to the consent, not of authors, but rather … one or more collective management organisations (CMOs) appointed to this end by the French Ministry of Culture.
-
We’ve noted a few times recently that the Copyright Office has inserted itself into policy disputes where it has no business being. It’s important to note that the role of the Copyright Office is supposed to be a rather specific one: to handle the registration of copyrights. It has little official roles in terms of actual policymaking — the role is more about executing on the policy decisions of Congress. And, yet, over the years the Copyright Office has become a revolving door way station for execs from the entertainment industry, where they seek to use the Copyright Office as something of a taxpayer funded pro-legacy industry lobbying arm. Just in the last few months, we’ve reported on how the Copyright Office was flat out lying to the FCC about how copyright works in an effort to support the cable industry’s plan to stop competition in set top boxes. Then there’s its plan to strip websites of their safe harbors by making it a bureaucratic nightmare. Oh, and also its new plan to mess up the part of copyright law that protects libraries and archives. And let’s not forget the absolutely ridiculous hearings the Copyright Office held a few months ago about the DMCA safe harbors, where they seemed 100% focused on pushing the RIAA/MPAA’s plan to blame Google for everything.
What the hell is going on with the Copyright Office? This is not in its mandate and yet it’s run like a government-funded lobbying arm of Hollywood? The folks over at Public Knowledge have now started putting together a long list (much longer than the above examples) of the Copyright Office incorrectly weighing in on policy issues, taking positions that favor the desires of the legacy copyright industries, rather than what the law actually says. It’s a long and very troubling list.
-
Last year, there was a series of very troubling rulings by a district court in a case related to the criminal prosecution of Kim Dotcom. This wasn’t, technically, part of the actual criminal case against him, but rather a separate effort by the government to steal his money. We’ve been covering the ridiculous process of civil asset forfeiture for a while, and it’s really problematic in general. In Dotcom’s case, it’s something of a farce. Remember, civil asset forfeiture is the situation where the US government effectively files a civil (not criminal) lawsuit against inanimate objects, rather than people. In this case, it basically filed a lawsuit against all of Kim Dotcom’s money, arguing that it was the proceeds of a crime and therefore, the government should just get it all. Again, this is entirely separate from the actual criminal trial of Kim Dotcom, which has been put on hold while the extradition battle plays out in New Zealand (determining if Dotcom can be forcibly sent to the US to stand trial).
Just the whole process of civil asset forfeiture is troublesome enough. As we’ve detailed over and over again, it’s basically a system whereby law enforcement gets to steal money and other stuff (cars are popular) from people, simply by claiming that they were used in a criminal endeavor. Since the lawsuit is against the stuff, if people want it back, they have to go and make a claim on it, and it’s a fairly convoluted process. In this case, things were even more ridiculous, because the government argued that because Dotcom was resisting extradition from New Zealand, he could be declared “a fugitive” and the judge overseeing the case (the same one overseeing his criminal case, Judge Liam O’Grady) agreed. That effectively meant that Dotcom had no legal right to protest the government simply taking and keeping all of his assets — and they moved forward and did exactly that.
It is difficult to see how this can be legitimately described as anything but theft by the US government. It got someone locked up in New Zealand, based on questionable legal theories, and while he was (quite reasonably) fighting extradition to the US (a place he’s never visited and where he has no business ties), it initiated a separate legal process to keep all his money, no matter what happens in his extradition fight and criminal trial. On top of that, it effectively barred him from making an official claim on that money by having him declared a fugitive for exercising his legal due process rights to fight extradition. So while he exercises his legal due process rights in New Zealand, he’s blocked from doing so in the US. And all of his money goes to the US government.
As we said after O’Grady’s ruling came out, even if you think that Dotcom is guilty of a criminal copyright conspiracy, and even if you think he should be extradited, tried and locked up this should concern you. Let him go through the full legal process, with all that due process entails, and then determine what should happen to his assets. To take them before that’s happened, through this questionable side process is immensely problematic.
-
Earlier this year, we noted that Facebook had launched its own ContentID clone, called Rights Manager, which was a response to a bunch of angry YouTubers who were annoyed at people “freebooting” popular YouTube videos onto Facebook. We noted that, like ContentID, we fully expected the system to be abused to take down content. While we haven’t heard examples of that just yet, it does appear that Rights Manager had some serious vulnerabilities that enabled anyone else who was signed up for Rights Manager to manipulate the information and rules on any other video in the system (including, obviously, those claimed by other users).
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA