07.09.15
Posted in BSD, Microsoft, Security at 12:09 pm by Dr. Roy Schestowitz

Image from the OpenSSH project
Summary: Exploring the real motivations and the real implications of Microsoft giving money to the OpenBSD Foundation
MICROSOFT is in pain. The company sees its monopoly diminished due to software becoming a commodity and platforms such as BSD and GNU/Linux taking over everything, not just the back end. Microsoft can attempt to cope with this the way it typically copes with competition (including Android as of late): Embrace, Extend, Extinguish [1, 2, 3, 4].
The other day we wrote about yet another example of openwashing from Microsoft (assimilation strategy). Microsoft booster Darryl K. Taft is the latest to call a Windows-only .NET pile of Microsoft APIs “open source” and it leads us to Microsoft’s effort to characterise its involvement in OpenSSH [1, 2] as something benign or even good.
“So it’s about putting secure Free software on an insecure proprietary software platform (with back doors), in order to promote its use.”Based on an OpenBSD Foundation announcement [1] and some press coverage [2] that says Microsoft “handed a pile of money to the OpenBSD Foundation”, we are becoming a little concerned, knowing Microsoft’s history in such circumstances (creating unnecessary financial dependencies). This story is growing feet now, even in some Linux sites, so it is hard to ignore the risk of Microsoft using BSD as a front against GNU/Linux and copyleft, as it did in past years. Prudently one can say that if things are as indicated, this won’t be the first time Microsoft uses BSD as anti-Linux front.
As Steven J. Vaughan-Nichols put it (implicitly) a couple of hours ago, it’s about “help in porting OpenSSH to Windows.”
Windows is known for gaping holes (see the latest in [3]), i.e. the very opposite of OpenBSD. For these two entities to work together (NSA resistor and the NSA’s number one partner) is to have an incompatible relationship. Nothing on top of Windows can be secured and as we pointed out in our past articles about this, SSH keys will be put at risk. Microsoft’s ‘help’ to OpenBSD reminds us of Microsoft’s ‘help’ to Novell, where the goal was to use Novell to promote Windows, even inside Linux (e.g. Hyper-V).
It’s not a payment intended to help OpenSSH development. Microsoft looks to get its money’s worth (shareholders’ money). So it’s about putting secure Free software on an insecure proprietary software platform (with back doors), in order to promote and increase its use. █
Related/contextual items from the news:
-
The OpenBSD Foundation is happy to announce that Microsoft has made a significant financial donation to the Foundation. This donation is in recognition of the role of the Foundation in supporting the OpenSSH project. This donation makes Microsoft the first Gold level contributor in the OpenBSD Foundation’s 2015 fundraising campaign.
-
Microsoft has handed a pile of money to the OpenBSD Foundation, becoming its first-ever Gold level contributor in the process.
-
Here at Univention, we are of course also concerned by the attack on the German parliament’s IT infrastructure, better known as the “Bundestag hack”. To recap: It appears that there were some bogus e-mails there including links to malware. A number of the Windows PCs in the Bundestag’s “Parlakom” network were or may still be infected with the malware, which is alleged to have searched for and copied certain confidential Word documents. According to a report in the Tagesspiegel (German) newspaper, this allowed the hackers to gain “administration rights for the infrastructure”. The attack was conducted as an “advanced persistent threat” or “APT attack” for short: in other words, a complex, multi-phase attack on the German parliament’s “Parlakom” IT network.
Permalink
 Send this to a friend
Send this to a friend
07.08.15
Posted in Microsoft, Security, Windows at 7:43 am by Dr. Roy Schestowitz
A game of perception alternation
“Well, it’s in the brand. The image you create around the brand. That’s why I need you in this company. Because nobody in this company, or in this industry, really understands that. And if we can have the perception, I can create the reality. With the combination of the reality and the perception, nobody will ever beat us.”
–Bill Gates
Summary: More AstroTurfing for Vista 10, including shameless promotion of the mere perception of it being ‘open’ and ‘secure’
THINGS must be working out pretty well for Microsoft’s PR agencies when/if even some Linux sites are willing to promote the NSA-friendly (hyper-visor runs only on Windows) Hyper-V. This is a little frustrating because it is not hard to see what it’s all about for Microsoft, whose software is made insecure by design. As FOSS Force put it the other day:
I assume that most enterprise users of Microsoft products already know not to trust Redmond to handle Windows’ security. I worry, however, about the poor consumer who plops a thousand dollars down for a laptop, and thinks it’s just fine to stop in to use the free Wi-Fi at Mickey Dee’s for a quick check of the bank account while being protected by nothing more than the best Redmond has to offer.
It looks like Vista 10 will remain as flawed and inherently insecure and its predecessors, no matter how much AstroTurfing Microsoft does (it gets worse by the day, as perception changing is the goal with official release day imminent) and how much openwashing Microsoft constantly does. It’s hard to keep up with the propaganda and refute it quickly enough.
Yesterday we spotted Microsoft’s propaganda channel (Channel 9) brainwashing Microsoft staff and readers of Channel 9, implicitly telling them that Visual Studio “open source”. Openwashing of SAP [1] and Apple [2] (below) could also be found in the news yesterday, so not only Microsoft does this. Remember that both companies were asked (if not demanded) by Russia to reveal their source code last year, for fear of back doors. We don’t know if SAP and Apple ever complied. █
Related/contextual items from the news:
-
SAP SE is dedicated to helping businesses respond to market demands around the clock, according to Steve Lucas, president of Platform Solutions at SAP. Its partnership with Red Hat, Inc. is a key part of its strategy. In an interview with theCUBE at RedHat Summit, Lucas explained further.
-
Recently, Apple released its programming language, Swift 2, to the public. By releasing Swift to the open source community, Apple is giving software developers more access to and control over the programming language. This release opens up a myriad of exciting possibilities for application development, software advancements and increased functionality.
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Red Hat, Security at 6:47 am by Dr. Roy Schestowitz
Red Hat and back doors: poll from FOSS Force
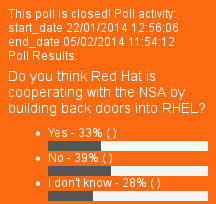
Summary: The return of XKEYSCORE to some media outlets (not news anymore) brings us back to debating Red Hat’s role (also not really news)
QUITE a few sites (see [1-3] below) seem to be talking about Red Hat’s special (but no longer secret) relationship with the NSA, which is not at all news. The NSA uses a lot of RHEL (and also Fedora) on some malicious spying equipment, based on various NSA leaks. We already wrote a great deal about this back in 2013 [1, 2, 3, 4]. The only new thing we learn from the latest articles is that Red Hat continues to refuse to remark on the subject, even when asked by journalists (see the first article below). █
Related/contextual items from the news:
-
A little over two years ago, the first disclosures about the massive surveillance operation being carried out by the NSA were made in the Guardian, thanks to an intrepid contractor named Edward Snowden.
Now comes the rather disturbing information that the NSA runs its XKEYSCORE program — an application that the Intercept, the website run by journalist Glenn Greenwald, describes as NSA’s Google for private communications — for the most part on Red Hat Linux servers.
-
If report is correct, Red Hat’s marketing department has a very tricky customer reference
-
SELinux is a product of the NSA and some worried when it was added to Red Hat, Fedora, and later many other distributions. Even before Snowden revealed the massive government spying, having the NSA anywhere near Linux activated certain Spidey-senses. Now we learn that SELinux may have had an exploit for bypassing the security enforcements. Italian software company Hacking Team, who admits to providing “technology to the worldwide law enforcement and intelligence communities,” has been selling technology to governments (most with bad human rights records) to assist in gathering surveillance data on citizens, groups, journalists, and other governments. Recently Hacking Team was hacked and their information has been leaked onto the Internet. Besides the SELinux exploit, it’s been reported that the FBI, U.S. Army, and the Drug Enforcement Agency are or were customers of Hacking Team’s services.
Permalink
 Send this to a friend
Send this to a friend
07.04.15
Posted in Microsoft, Security, Windows at 11:04 am by Dr. Roy Schestowitz
“Our products just aren’t engineered for security.”
–Brian Valentine, Microsoft executive

Summary: More timely reminders that Windows is simply not designed to be secure, irrespective of version, status of patching, etc.
GIVEN the exceptionally strong ties between Microsoft and the NSA we shouldn’t be so shocked that Microsoft constantly lets the NSA know how to break into computers with Windows installed on them. That’s a fact.
Samsung, perhaps realising that ‘updating’ Windows (or even ‘upgrading’ it) won’t make it more secure decided to altogether abandon Windows Update. As IDG put it:
This week, it’s Samsung, which has been outed as intentionally disabling Windows Update. According to independent researcher Patrick Barker, he was trying to help a customer figure out why a PC kept randomly disabling Windows Update, which caused the system to be dangerously and continuously vulnerable to open security flaws.
Remember that Windows Update can also be used (or misused) to install new back doors at any time. Richard Stallman has repeatedly warned about the danger of any such mechanism. It’s basically a remote control for one’s PC, where the controller is not the user but the software vendor and potentially crackers (like NSA and the GCHQ, as well as non-government entities). When the article above says “vulnerable to open security flaws” it probably means security flaws that are provably known to cyber criminals not affiliated with governments.
“Remember that Windows Update can also be used (or misused) to install new back doors at any time.”According to Microsoft Peter (Peter Bright), writing about how much of a farce Windows ‘security’ really is might be something that a research student cannot do. To quote the booster:
Willcox’s research investigates ways in which Microsoft’s EMET software can be bypassed. EMET is a security tool that includes a variety of mitigation techniques designed to make exploiting common memory corruption flaws harder. In the continuing game of software exploit cat and mouse, EMET raises the bar, making software bugs harder to take advantage of, but does not outright eliminate the problems. Willcox’s paper explored the limitations of the EMET mitigations and looked at ways that malware could bypass them to enable successful exploitation. He also applied these bypass techniques to a number of real exploits.
The laws here have become so ridiculous that merely pointing out that some piece of software is ‘Swiss cheese’ and ‘easy pickings’ would potentially constitute a violation of the law. Microsoft Peter, writing another article about the failing Xbox business (billions in losses), shows how Microsoft secretly tried to deal with manufacturing flaws that may have led to loss of lives (there is a famous case involving a baby who died after an Xbox-induced house fire).
It often seems like Microsoft can get away with just about anything (surveillance by the back door, house fires etc.) as long as it colludes with the state against citizens. Anyone who still believe that Windows can be made secure (intrusions-resistant) clearly is deluded, or at least misinformed. █
Permalink
 Send this to a friend
Send this to a friend
07.01.15
Posted in Free/Libre Software, FUD, Security at 5:39 am by Dr. Roy Schestowitz
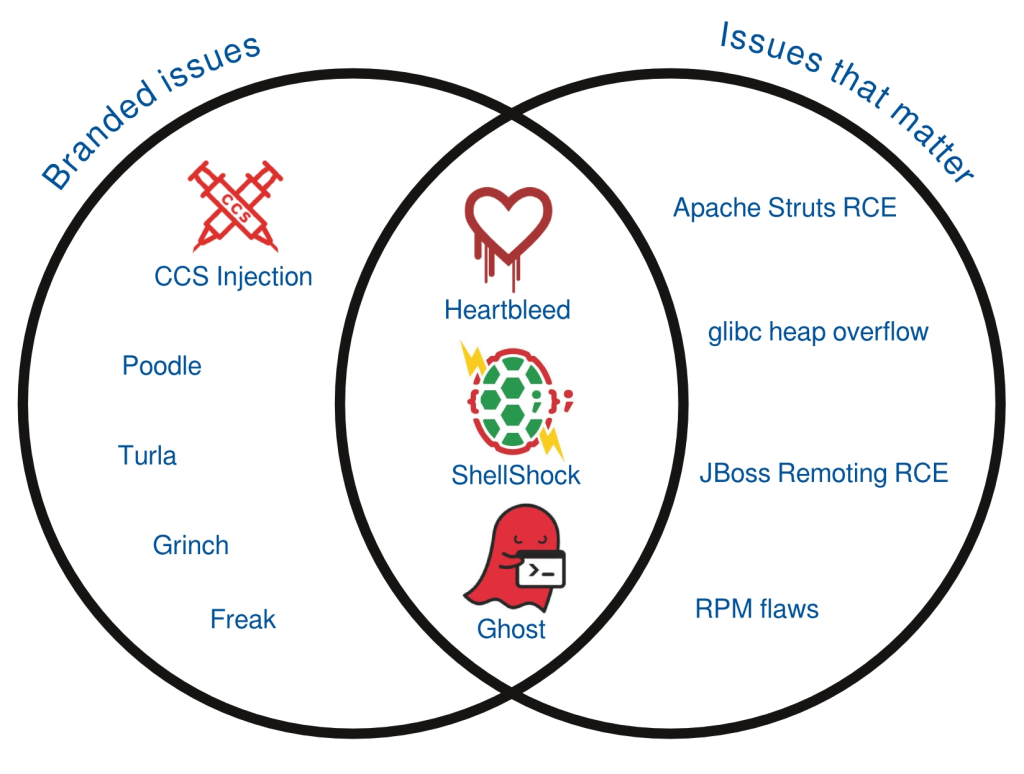
Image courtesy of Red Hat, demonstrating lack of correlation between severity and logos/brands
Summary: Some more FUD from firms such as Sonatype, which hope to make money by making people scared of Free/libre software
The corporate media is in the business of selling (for corporations), not informing. Advertising is the business model, as well as media ‘partnerships’ (euphemism for PR). Security firms too are in the business of selling, not informing. Misinformation often helps improve sales. We have already ranted quite a lot about media misdirection, designed to sell products or malign the competitors of those who try to sell unnecessary products. We must assume that this is happening because it has always been happening; it’s just that it got a lot more frequent now that Free/libre is more widely used.
The other day IDG published some promotion of Veracode. To quote one paragraph: “The scale of the problem is significant. Cryptographic issues are the second most common type of flaws affecting applications across all industries, according to a report this week by application security firm Veracode.”
This is not an independent security researcher; it is the Black Duck-connected Veracode (Black Duck came from Microsoft and VeraCode’s co-founder recently joined Black Duck), which overlooks security issues with proprietary software. Veracode is not an objective observer; it is trying to sell something. Sonatype too, a nasty company which we wrote about before [1, 2, 3, 4, 5, 6], rears its ugly head in the media, in an article provocatively titled “Open-Source Code Can Be More Dangerous Than Useful”.
So Sonatype has launched yet another FUD attack on Free software, using myths and rhetoric, capitalising on gullible ‘journalists’ who would print just about anything, along with clueless pasting of bugs with logos (for extra fear), no discussion about severe bugs in proprietary software, and many other issues. This article is relaying marketing from Sonatype and dramatises it even further. “It gets worse,” says the writer, “according to Sonatype: Many of the software companies that have built insecurities right into their products wouldn’t be able to tell which of their applications are affected by a known component flaw because of poor inventory practices.”
Well, proprietary software deliberately adds flaws to act as secret back doors. How about that in the discussion? The article totally omits that. The article then adds some talking points from the FOSS-hostile Symantec, another company which tries to sell its proprietary software based on perceptions of insecurity.
Thankfully, there are a couple of comments there (below the article) that highlight the issues with the article; both are titled “Not only open source…”
As Free/libre software becomes more mainstream we should expect more parasites like Sonatype to look out for fools who are willing to do their marketing, monetising trash-talk. █
Permalink
 Send this to a friend
Send this to a friend
06.25.15
Posted in Microsoft, Security, Windows at 5:28 am by Dr. Roy Schestowitz
Turning the alphabet into a security nightmare

Summary: Windows userbase is once again under serious threat and high risk because something as simple as fonts (rendering of text/pixels on the screen) isn’t done securely in Windows
THERE IS plenty evidence which shows that Microsoft is not interested in security, maybe because there are commitments to the NSA (the motivations are hard to reason about, but Microsoft’s reluctant to patch known holes is easily demonstrable).
Now we are being reminded that even fonts are a security risk in Windows. Yes, Microsoft continues to put users under remote execution threat because of fonts. As the British media put it:
Get patching: Google Project Zero hacker Mateusz Jurczyk has dropped 15 remote code execution vulnerabilities, including a single devastating hack against Adobe Reader and Windows he reckons beats all exploit defences.
The accomplished offensive security researcher (@j00ru) presented findings at the Recon security conference this month under the title One font vulnerability to rule them all: A story of cross-software ownage, shared codebases and advanced exploitation [PDF ] without much fanfare and published a video demonstration of the exploit overnight.
As one commenter (found by Robert Pogson) put it, “Adobe (and I guess MS as well) put font handling in the kernel from NT 4.0 to gain speed at the expense of having privileged-based protection, and against Dave Cutler’s original micro kernel plans. What could possibly go wrong?”
Proprietary software is so bad that even fonts are a huge risk. This isn’t the first such incident. It serves also as a reminder for GNU/Linux users because some users continues to install proprietary software from Adobe, despite Free/libre alternatives being equally potent.
To quote the part which shows why Windows makes things even worse: “The nastiest vulnerabilities for 32-bit (CVE-2015-3052) and 64-bit (CVE-2015-0093) systems exist in the Adobe Type Manager Font Driver (ATMFD.dll) module which has supported Type 1 and Type 2 fonts in the Windows kernel since Windows NT 4.0.” █
“Our products just aren’t engineered for security.”
–Brian Valentine, Microsoft executive
Permalink
 Send this to a friend
Send this to a friend
06.24.15
Posted in Microsoft, Security, Windows at 9:33 am by Dr. Roy Schestowitz
“Our products just aren’t engineered for security.”
–Brian Valentine, Microsoft executive

“I don’t want a back door. I want a front door.” — Director of the NSA (2015)
Summary: Microsoft decides to leave Windows with flaws in it, claiming that fixing the flaws would not be worth Microsoft’s resources
FOR A LONG period of time (3 months or more) Microsoft refused to fix a serious flaw in Windows. It only did something about it when it was too late because the public had found out. Microsoft blamed the messenger.
This is not the exception, it’s pretty much the norm. Some Windows flaws exist for as long as 15 years, but they have no "branding" like a name or a logo.
“People with access to the world’s biggest stockpile of nuclear weapons still use Windows XP.”“Dustin Childs says the company couldn’t get Microsoft to patch an IE exploit,” says this new report, pointing to HP’s Web site. “Since Microsoft feels these issues do not impact a default configuration of IE,” Childs wrote, “it is in their judgment not worth their resources and the potential regression risk” (a lot more damning information can be found in the HP Security Research Blog).
Given Microsoft’s cooperation with the NSA on back door access, this hardly surprises us. Even more sad than this is a new report about the US Navy wasting millions in taxpayers’ money to run an operating system initially released in 2001. People with access to the world’s biggest stockpile of nuclear weapons still use Windows XP. As IDG put it:
The U.S. Navy is paying Microsoft millions of dollars to keep up to 100,000 computers afloat because it has yet to transition away from Windows XP.
After the Office of Personnel Management (OPM) disaster (Windows involved), we oughtn’t be too shocked about some nuclear disaster happening because of dependence of ancient Windows. █
Permalink
 Send this to a friend
Send this to a friend
06.19.15
Posted in Patents, Security at 7:03 am by Dr. Roy Schestowitz
None for you, but good for us?

Summary: Kaspersky Lab shows that its stance on software patents (and the patent system in general) is not as strong as it claims
Kaspersky, which is based in Russia and is certainly no ally of the US, turns out to be pursing US-style software patents, despite Kaspersky (the chief) publicly slamming the patent system on numerous occasions. Kaspersky might try to argue that it does this for defensive purposes (the same excuse Google uses as it continues to hoard software patents), especially now that Microsoft-connected patent aggressors shake down security companies, but overall it shows that Kaspersky isn’t too serious about change or reform. It doesn’t play a role in it.
Meanwhile, as this London-based patent lawyers’ blog reminds us, software patents’ validity is being diminished in the US, with potential implications in Europe. “Coupled with the relatively restrictive (or realistic) ruling on patentability of software in Alice v CLS,” it says, “the question is asked whether this is a sea-change or merely a blip in the annual statistics, which will soon be corrected by regression to the norm. In Europe, ongoing work on fixing the procedural rules and institutional infrastructure of the Unified Patent Court has provided a major focal point for litigation interest.”
Kaspersky would be wise to stop wasting time and money acquiring patents. Developers need to focus on good programming and secure algorithms, not typing up papers to be submitted to lawyers for the acquisition of monopolies. Mr. Kaspersky ought to change his company’s policy to coincide with a computer scientist’s common sense. Besides, software patents may already be on their way out (bulk invalidation). █
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
























 Content is available under CC-BY-SA
Content is available under CC-BY-SA