07.11.15
Posted in Microsoft at 4:40 pm by Dr. Roy Schestowitz
The ‘new Microsoft’ is smaller and more malicious

Summary: Microsoft is dying a lot more quickly than most people ever imagined and there are numerous data points that demonstrate this
SEVERAL years ago, back when Android was in the process of becoming the dominant platform (based on Linux and liberally licensed), we gradually reduced the level of Microsoft coverage. Microsoft was already — quite inevitably — in a state of decline and on its way out. Losses too were being reported.
Microsoft has just pretty much given up on phones/mobile, despite it being the undisputed growth market (even desktop/laptop OEMs are reportedly reinventing themselves to cater for that). Microsoft is now trying the infamous “embrace, extend, extinguish” strategy against Android/Linux and against BSD. Swapnil Bhartiya, remarking on the OpenBSD news, says that “Microsoft’s contribution to OpenBSD comes at an interesting time because Microsoft recently announced it is planning to cut up to 7,800 jobs and the reports are rife that their own Windows Phone platform is dead.”
“Perhaps Microsoft bets on mass surveillance — not operating systems — as its future business model.”It has been dead for quite some time. They just didn’t manage to ever resurrect anything, even after they had injected billions of dollars (in losses) into it. “Windows Phone likely dead as Microsoft sacks 7,800 employees,” says the headline from The Independent. Microsoft has basically given up on the future. The Independent claims that “Microsoft might have killed its plans to make its own phone after it sacked 7,800 staff and said it would take huge charges.”
Well, Microsoft never made its own phone. It’s just a branding exercise. Google makes no phones, either, it just has hardware partners.
The core market of Microsoft Windows is declining, still (based on the Microsoft-friendly Gartner Group) and the phone business (growth market) is ever more elusive for Microsoft because “Windows Phone” (or whatever Microsoft chooses to rename it to) is basically dead.
Worry not, however, as Microsoft is trying to tell us that it reinvents itself as a ‘cloud’ company, giving yet more data (as well as proprietary software) to its big ally, the NSA. Skype is back in the news because it’s a special target of the NSA, based on additional leaks [1,2] and over at IDG we find just Skype ads by Microsoft MVP J. Peter Bruzzese. Perhaps Microsoft bets on mass surveillance — not operating systems — as its future business model. Are any fools willing to let Microsoft host services for them? Does anyone actually believe that “Microsoft loves Linux”? Not even the company’s CEO believe this lie (told publicly by himself). █
Related/contextual items from the news:
-
The service utilizes more than 700 servers located in multiple nations, and apparently the US is not the only one using it.
-
That includes pictures, documents, voice calls, webcam photos, web searches, advertising analytics traffic, social media traffic, botnet traffic, logged keystrokes, computer network exploitation (CNE) targeting, intercepted username and password pairs, file uploads to online services, VOIP streams taken from Skype sessions, and more.
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 4:17 pm by Dr. Roy Schestowitz
Free speech? That would be too scientific for ringleader Battistelli.

Summary: The management of the EPO — not to be confused with scientists such as patent examiners — shows utter disregard for Free speech and chooses to forcibly silence its opposition rather than counter its message (refutation may not be possible)
THE INFAMOUS RING of Battistelli is digging itself deeper into the grave. We have already reported confirmed censorship by the EPO [1, 2]. This kind of fruitless censorship may not be news anymore; however, we have just found out that the EPO blacklisted our Web site a couple of days ago. They have begun domain-based censorship, as if they are the US Navy trying to keep troops misinformed and brainwashed. If they are willing to go as far as blocking the whole site and we also know that they put the site under very extensive surveillance, then who knows, maybe they are indirectly behind all those DDOS attacks too. The Hacking Team leaks show that a lot of very powerful institutions shamelessly engage in cracking and DDOS attacks by proxy, ‘as a service’ so to speak. We have hardly had such problems until we started covering the EPO scandals (we hadn’t had DDOS attacks against us since around 2009, so that’s about half a decade DDOS-free until around the very moment we wrote exclusively about the scandals last summer). Our EPO wiki has the timeline.
A source told us that “since yesterday” (the day before yesterday) Techrights is not all all accessible from the EPO. There is more about it in the latest comments on this article from one month ago. “By the way,” writes one person, “the website techrights.org has been blacklisted today, for access from inside the EPO” (this was said 2 days ago).
“Well, making the site inaccessible from work isn’t too wise a plan because of the Streisand effect (people just get even more curious about what’s being hidden).”One person responds: “Only now? Can’t imagine that anyone has dared to try recently. Self-censorship is a powerful tool. I don’t even look at ipkat from the EPO! You don’t want to be caught in possession of any anti-BB thoughts.”
Another person writes: “I can confirm that Techrights is not accessible anymore from within the Office.
“Disgusting.”
Well, making the site inaccessible from work isn’t too wise a plan because of the Streisand effect (people just get even more curious about what’s being hidden). Some parts of the US government (e.g. US Navy) tried this against Wikileaks, but people can still access the ‘naughty’ site from home (after work). The only way to prevent access to the site universally is DDOS attacks and/or cracking.
This is basically an admission of defeat; the EPO’s management is unable to counter the facts or sue for defamation (because the statements are correct and are even supported by European courts), so they are just trying to gag the messengers. China does it with the infamous DDOS ‘cannons’ (see press reports the recent DDOS attacks against GitHub, which was used to host mirrors of stories that the Great Firewall of China cannot ever effectively suppress). The EPO is trying a desperate and counter-productive censorship strategy as well. It’s going to backfire; people cannot respect an employer who actively censors and spies on employees, especially if it’s done in order to prevent the employees from finding out the truth about the employer. To make matters worse, Battistelli et al. attack journalists, not just staff. It’s a form of shameless sabotage.
I have repeatedly asked Amazon where to serve legal papers to and Amazon refuses to even answer. They guard DDOS and have officially taken a “do not reply” approach after their machines had been attacking my site and caused a lot of damage (recent attacks on my sites caused even database corruption several times recently, with repairs taking hours, let aside disruption to service).
The EPO has been targeting Techrights in a variety of confirmed ways (censorship, surveillance, and maybe more); the only attack vector that’s hard to concretely prove is DDOS, but we are going to pursue this pretty soon. SUEPO already initiated an investigation after it had come under cyber attacks. If anyone knows anything about it and has some documents that can prove it, please make an effort to anonymously send it to us. Transmission using Tor and an empty E-mail account can do the trick. We have never let down or betrayed a source (in our decade-old history with many whistleblowers). Potential sources and also the principal target audience are sadly unable to access this site from work anymore. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 3:13 pm by Dr. Roy Schestowitz

Contents
-
If you search deep enough, you’ll find even more web browsers for the Linux platform. However, the chances of you needing anything beyond what is listed here are slim. Whether you want the full-blown experience of Chrome and Firefox or you’re looking to slim down your browsing tools, Linux has what you need.
Which browser is your tool of choice?
-
In a Core Infrastructure Initiative survey of at-risk software most in need of close attention, many fundamental Linux utilities sit at the top
-
Linux Format has just printed its 200th issue and is celebrating 15-years of best-selling GNU/Linux coverage. Over 20,000 pages and more than 10 million words (no, we did not count them all) dedicated to promoting and celebrating free and open source software, alongside that ever smiling penguin we all know and love.
-
Desktop
-
I want one. Maybe I’ve just spent too long on older hardware but it’s nice to be able to use a laptop with modern specs without having to compromise on my Open Source and privacy ideals. The Librem 15 was definitely too big for me but while the Librem 13 is bigger than most of my personal laptops, it’s about the same size as a modern Thinkpad X series (but thinner and lighter). I’m more than willing to add an inch or so to the width in exchange for such a nice, large, high-res screen. Even though my X200 is technically smaller, it’s definitely heavier and just feels clunkier.
-
Server
-
Linux and UNIX are very similar to each other, but they have some common differences – discover what they are in this blog to find out which one is right for your organisation.
-
Kernel Space
-
Bill Kerr has taught Linux Foundation courses in Linux Kernel internals, debugging, device drivers and application development for many years. He helped write the original Linux Foundation Training course materials and has been working with UNIX kernels for 35 years.
-
-
-
Graphics Stack
-
I’m in the midst of a new large open-source and (separately) closed-source NVIDIA/AMD Linux graphics card comparison on the latest drivers as part of an upcoming Radeon R7 370 Linux review and to be followed by R9 Fury Linux benchmarks. However, for those interested in the Catalyst 15.7 benchmarks on Linux, I ran some quick tests with a Radeon R9 285 and R9 290.
-
-
-
Benchmarks
-
As part of the other Linux graphics tests running this week, here are the results of eight different graphics cards — from both NVIDIA and AMD — being tested on the latest open-source Linux graphics drivers under a variety of OpenGL Linux games. The software stack making up this round of testing was the Linux 4.1.1 kernel and Mesa 10.7-devel atop Ubuntu 15.04.
-
Applications
-
-
Instructionals/Technical
-
Wine or Emulation
-
Wine developers have just revealed that a new version of the application has been released, and it comes with a large number of fixes and various other improvements.
-
-
Games
-
-
As a quick follow-up to America’s Army looking at SteamOS/Linux support from earlier this week, it turns out the developers are indeed exploring a Linux client and server.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
KDE Frameworks 5.12.0 has just been released by the KDE Community, and the developers have closed a lot of bugs and various other issues. It’s just a maintenance update, but Frameworks is an important component, and any update to it will be very important.
-
-
Krita, an open-source digital painting software piece that aims to be the best in its field, has been upgraded to version 2.9.6 and is ready for download.
-
-
We are pleased to announce that Calligra Suite, and Calligra Active 2.9.6 have just been released. This recommended update brings further improvements to the 2.9 series of the applications and underlying development frameworks.
-
-
Reviews
-
If you love Debian, but miss GNOME 2; you should definitely try Point Linux. It comes with MATE desktop environment which is fork of GNOME2. The design goal of this distribution is to provide an easy to setup, user friendly, stable, fast and predictable operating system for the lovers of Linux desktop. This Linux distribution is targeted toward experienced users and IT sector. The latest version of this operating system Point Linux 3.0 is out now. Let’s see how we can install and get familiar with this distro.
-
New Releases
-
The stable version of Q4OS live CD is available for free download and use. Users are now able to perform safe Q4OS testing on a real hardware without installation. Anybody is welcome to try out and see Q4OS system in action. As an option, it’s possible to proceed Q4OS installation directly from the live environment using integrated graphical live installer. You can download the live CD iso from our website and burn it onto CD/DVD or create bootable USB stick, we can recommend to use ‘unetbootin’ or similar tools for this purpose.
-
Alpine Linux is a security-oriented, lightweight Linux distribution that uses musl libc and Busybox, which make up the terminal. A new version of this distributions is out and ready for download.
-
Q4OS is a Linux distribution based on Debian and powered by a desktop environment called Trinity DE. It receives a constant flux of updates, and the latest one brings the option to run it as a stable Live CD.
-
Slackware Family
-
Red Hat Family
-
While it’s true that an NSA analyst sent out an email about KDBUS security, it hopefully shouldn’t raise any alarm bells. The thread in question is about credential faking for KDBUS and why it’s even there. Stephen Smalley of the NSA was asking why there’s support for credential faking for this soon-to-be-in-kernel code while it wasn’t part of the original D-Bus daemon in user-space. The preference of Stephen Smalley is to actually get rood of this functionality that could be abused.
-
But Red Hat VP engineering middleware Dr Mark Little likes to see microservices as the good bits of service-oriented architecture, buoyed by the arrival of more sophisticated engineering and operations technology and techniques.
-
-
Red Hat, Inc. (NYSE: RHT), the world’s leading provider of open source solutions, today announced that Red Hat president and CEO, Jim Whitehurst, will speak at Fortune Brainstorm TECH 2015.
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
One of Canonical’s goals is to build an Ubuntu Desktop by using Snappy packages, and that is actually a difficult task. Developers need to build all the regular packages by using the Snappy, and that can take a while. From the looks of it, the first steps have been taken, although it’s not something that regular users will be ready to test just yet.
-
Canonical has just announced that a large number of Firefox vulnerabilities have been fixed and that version 39.0 of the browser has been added to Ubuntu 15.04 and all the other supported Ubuntu versions.
-
The bq Aquaris E5 is solid device. On the software side there aren’t any big issues. Also the hardware of the E4.5 and E5 is so similar that one is as good os the other when it comes to running the installed software.
-
Last month the BQ Aquaris E5 Ubuntu Phone was launched in Europe. While the hardware may not be the best out there and the Ubuntu Phone software stack is still maturing, early reviews seem fairly positive.
-
-
Advantech launched a Pico-ITX SBC and a computer that run Linux or Android on a dual-core i.MX6, and offer 4GB eMMC, dual displays, and two mini-PCIe slots.
Advantech unveiled both a 2.5-inch Pico-ITX board called the RSB-3410 and a box computer version called the UBC-220. The name, design, and distinctive blue coloring of the UBC-220 are similar to that of the recently revealed Intel Quark based UBC-221, but the limitations of the Quark compared to the multi-faceted 1GHz, Cortex-A9-based Freescale i.MX6 SoC on the UBC-221’s RSB-3410 mainboard make these very different computers.
-
OpenELEC launched a version of a WeTek media player preloaded with Kodi-ready OpenELEC Linux, and a choice of DVB-S2, DVB-C/T/T2, or ATSC broadcast tuners.
The WeTek OpenELEC (Limited Edition) Linux media player is an OpenELEC-optimized version of the Android-based WeTek Play media player, which typically offers OpenELEC Linux as one of its alternative downloads. The $90.33 (99-Euro) OpenELEC version comes with a choice of satellite (DVB-S2), cable (DVB-C/T/T2), or terrestrial broadcast (ATSC) tuners.
-
Phones
-
Android
-
-
The $15 Ethernet adapter is designed to bolster streaming via Chromecast for those with poor WiFi connectivity.
Google appears to have quietly released a $15 Ethernet adapter for Chromecast users with spotty WiFi connectivity.
It’s unclear when the company released the device, but media reports about its availability appear to have resulted in the product being sold out on Google Store.
-
Google has released the first update to its Android M developer preview, inching the mobile OS closer to its final release.
Google describes the M Developer Preview 2 as an “incremental update”. It brings thousands of tiny fixes and a few major changes to the platform and APIs, as well as other issues reported by developers.
-
An Australian high school graduate today has experience with Microsoft Word, Microsoft Excel, and Microsoft PowerPoint, and not much else. They are ready for your Windows-centered workplace, Mr. Employer!
-
When the National Security Agency (NSA) in the U.S. released the Accumulo project into open source territory in 2008, there were not a lot of details about the size and capability of the hardware it was running, although it is safe to say that the NSA found ways to make it scale across some of their larger machines. However, as one might imagine, scale alone did not define a successful NSA database system—the security also had to be robust and guaranteed.
-
The NSA has released a network security tool that it claims is designed to help organizations “fortify their networks against cyber attacks”. But, after being revealed to be spying on just about anyone it wants to, from US citizens to leaders of allied governments, while undermining major tech firms in the process, IT administrators will likely be very skeptical of adopting it.
-
The NSA today revealed it has uploaded source code to GitHub to help IT admins lock down their networks of Linux machines.
The open-source software is called the System Integrity Management Platform (SIMP). It is designed to make sure networks comply with US Department of Defense security standards, but the spy agency says it can be adapted by admins to meet individual security needs as well.
-
-
Web Browsers
-
SaaS/Big Data
-
Encryption 2.0 features a brand new set of encryption capabilities. Notably, ownCloud claims the new release includes enhancements that will enable up to a 4X performance for uploads and downloads, as well as improved scalability through efficient handling of massive parallel requests, enabling support for 50 percent more users per ownCloud server instance.
-
Most notably the server does not know the target filename of the uploaded file upfront. Also it does not know the final size or mimetype of the target file. That is not a problem in general, but imagine the following situation: A big file should be uploaded, which would exceed the users quota. That would only become an error for the user once all uploads happened, and the final upload directory is going to be moved on the final file name.
-
Oracle/Java/LibreOffice
-
The Document Foundation has released the first RC for the new LibreOffice 4.4.5 branch. It’s a maintenance update for the entire 4.4.x branch and it’s not the last one in the series.
-
-
FSF/FSFE/GNU/SFLC
-
It’s Stallman’s philosophy that ‘a program must not restrict what jobs its users do with it’ — and that includes the NSA.
-
Security and privacy seemed to be my theme this week and tonight’s news brings more. Richard Stallman, “software freedom fighter,” told Swapnil Bhartiya, “A program must not restrict what jobs its users do with it.” In related news, the same RMS was included in the Business Insider “12 most influential programmers working today” list. Back to the NSA, Michael Larabel said you should be wearing tin foil hats if you’re worried about them working on KDBUS. The NSA also uploaded code to Github for sysadmins to “lock down” their Linux machines.
-
The apps and games you use every day don’t exist in a vacuum — someone, somewhere, wrote the code.
-
Licensing
-
Open source licensing is important to GitHub in two ways: First, as the host of the world’s largest collection of code, we have a unique opportunity—and arguably an obligation based on that opportunity—to do what we can to support the open source community, and that obviously includes open source licensing. Second, as a company built on open source, it’s important that the open source code we depend on and the code we contribute to the open source community are both properly licensed so that others can use it. After all, that’s the point of open source.
-
Openness/Sharing
-
Programming
-
Over on the Chromium Blog is a new posting about the work Google is doing on a new JavaScript compiler for V8 in Chrome, codenamed TurboFan.
TurboFan is their new compiler that has started to be used for certain types of code since Chrome 41 but will be used for more code in future web browser updates. TurboFan is designed to be faster than their previous compiler (CrankShaft) while allowing for new features and functionality.
-
Standards/Consortia
-
The final draft version of the RGI (general interoperability framework), still awaiting final validation, maintains ODF as the recommended format for office documents within French administrations. This new version of the RGI provides substantiated criticism of the OOXML Microsoft format. April thanks the DISIC (French Inter-ministerial IT directorate) for not giving in to pressure and acting in the long-term interest of all French citizens and their administrations.
-
-
I had the pleasure of interviewing Rosaria Silipo about her upcoming talk at OSCON: Advanced analytics for the Internet of Things. I recently taught a group of librarians about Internet of Things and how we can use it to provide better services to our patrons, so when I saw Rosaria’s talk summary I thought it was right up my alley.
-
Health/Nutrition
-
At least five children have been left with severe burns after coming into contact with a toxic plant, whilst playing in public parks around Greater Manchester.
In two separate incidents, the children, one aged as young as seven, brushed past a hogweed plant, resulting in painful chemical burns.
-
Security
-
-
Heartbleed may have brought on a major case of heartburn last April for system admins worldwide, but a positive offshoot of the biggest of the Internet-wide bugs was that it opened a lot of eyes to the lack of support afforded even ubiquitous open source software projects.
-
The Linux Foundation Core Infrastructure Initiative (CII), backed by companies like Google, Facebook, Salesforce, HP, and others, has announced a new Census Project that automates the collection and analysis of data on different open source projects, ultimately creating a risk score for each project based on the results. It’s not the first approach to auditing open source usage, but has many unique aspects.
-
Just when you thought you were safe, a new hacking toy comes along and rocks your world. Imagine a tool exists that lets hackers pluck encryption keys from your laptop right out of the air. You can’t stop it by connecting to protected Wi-Fi networks or even disabling Wi-Fi completely. Turning off Bluetooth also won’t help you protect yourself.
-
Defence/Police/Secrecy/Aggression
-
US authorities are investigating after a United Airlines pilot flushed bullets down a toilet on a flight to Germany.
The pilot initially threw the bullets in a rubbish bin before disposing of them in the toilet, a spokeswoman for United Airlines said.
In the US, pilots are permitted to carry loaded weapons aboard planes under security measures put in place after the 9/11 attacks.
-
Ban said new information uncovered by a UN panel on the death of the former secretary-general should be probed to establish whether his plane was attacked just before it crashed in southern Africa.
After receiving the report, he said “a further inquiry or investigation would be necessary to finally establish the facts” surrounding the mysterious crash.
The panel “found new information, which it assessed as having moderate probative value, sufficient to further pursue aerial attack or other interference as a hypothesis of the possible cause of the crash,” said UN spokesman Farhan Haq.
-
Mr. Hammarskjold, a Swede, was killed with 15 others in the crash on the night of Sept. 17 to 18, 1961, in a forest in the British protectorate of Northern Rhodesia, an area that is now part of Zambia. Mr. Hammarskjold was on his way to broker a truce in the mineral-rich Katanga Province of what is now the Democratic Republic of the Congo. Mr. Hammarskjold was awarded the 1961 Nobel Peace Prize after his death.
-
The panel reported that the continued refusal by intelligence agencies of the U.S. and other governments to declassify documents may be hindering the “final revelation” into what caused the crash. The panel recommended Mr. Ban continue to urge governments to disclose or declassify the documents, or allow him “privileged access” to information the governments may possess about the circumstances of Mr. Hammarskjöld’s death.
-
Environment/Energy/Wildlife
-
-
To refute the federal agencies’ warnings, the conservative news publication turned to scientists affiliated with the fossil fuel-backed Heartland Institute. Daily Caller first quoted Canadian biologist Mitchell Taylor, who dismissed the USGS’ report because he said it is “based on climate models, not empirical data.” The agency’s climate models are “an expression of their opinion,” said Taylor, adding that “it’s simply their idea of what will happen if the carbon models are correct.”
-
Finance
-
As most of the world knew it would, the financial demands made by Europe have crushed the Greek economy, led to mass unemployment, a collapse of the banking system, made the external debt crisis far worse, with the debt problem escalating to an unpayable 175 percent of GDP. The economy now lies broken with tax receipts nose-diving, output and employment depressed, and businesses starved of capital.
-
Meet the New Boss. Same as the Old Boss. Ladies and gentlemen, I give you Alexis Tsipras, and we do get fooled again. If you will forgive me I should like to crow a little about the accuracy of my predictions on Greece in the last week or so. Now comes the bit where they stay in the Euro there is another fudge, the bankers get hold of more cash and more state assets, and nothing much changes.
-
This is an interesting assessment. Those of us who are less expert on China than the experts consulted for this article might wonder how the regime managed to survive a stock market crash between October 2007 and October 2008 in which the market lost over 60 percent of its value. This is more than twice as large a decline as the market has experienced in the current downturn. In spite of this plunge, China’s economy grew more than 9.0 percent in 2009, although it did require a substantial government stimulus program.
-
PR/AstroTurf/Lobbying
-
Despite the nonstop coverage of the 2016 presidential election—still 16 months away—it can be difficult to sort out the actual policy differences between the candidates. That’s especially true when it comes to education, where policies once seen as conservative—high-stakes standardized testing, closing public schools and replacing them with charters, weakening teacher’s unions—now share a generally bipartisan consensus in the political establishment.
Buzzwords and phrases like “accountability,” “Common Core” and “school choice” abound in media coverage of candidates’ education policy, with little explanation provided to actually unpack what it means that a candidate is pro or con these things. In a media landscape focused on the differences between Democrats and Republicans, rather than a comprehensive understanding of the policies at hand, only a small fraction of what’s at stake in education actually get covered.
-
Censorship
-
It turns out that if you suddenly fire a valuable member of the community, that community will get very angry at you. Reddit CEO Ellen Pao learned that the hard way late last week when it abruptly dismissed Victoria Taylor, the company’s former director of talent who was instrumental in popularizing the site’s “AMA” (Ask Me Anything) feature. A slew of subreddits, mostly run by volunteer moderators, went private in protest of the firing over the weekend as a result. Pao eventually posted an apology for the lack of communication and promised to improve things going forward. But in an op-ed posted today in the New York Times, those same volunteer moderators said that the apology was not enough.
-
Reddit managed to get most of our online news space in the previous weeks after the abrupt departure of Victoria Taylor. Taylor acted as the main facilitator for Ask Me Anything (AMA) sessions and was one of the most prominent employees of the company. While Taylor refused to give out any details, it was believed that she wasn’t okay with the commercializing of AMAs that the management was interested in. With stark opposition from Reddit communities who shut down several of the site’s most popular sections, today comes the big news that Ellen Pao, Reddit’s Chief Executive, is leaving the company.
-
-
Amos Yee Pang Sang is a teenage blogger, due to be sentenced today for a backdrop of last-minute hospitalization. People turned up a protest, calling the government to free Amos Yee Pang Sang.
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Perhaps ‘dissident’ is an inaccurate term to describe these critics. After all, they are neither opposition politicians nor veteran revolutionaries. Yee is clearly just an articulate teenager who is not connected to any political party. But their peaceful protests and the subsequent legal persecution they suffered highlighted the sorry state of political freedom in their own countries. They became icons of free speech even if many of their fellow citizens disagreed with their views and bold actions. By challenging the propaganda of the state, despite the existence of restrictive media laws, they somewhat earned the recognition as dissidents who could inspire others to defy authorities.
-
-
-
Privacy
-
Two new reports on EU databases have been released by the EU’s Agency for Large-Scale IT Systems (eu-LISA), which is responsible for managing and developing the Schengen Information System (SIS), the Visa Information System (VIS) and Eurodac (used by Member States to compare the fingerprints of migrants and asylum seekers). The new reports concern SIS and Eurodac.
-
United Kingdom is set to ban popular mobile messaging application, WhatsApp, under new strict laws on social media and online messaging services.
British Prime Minister David Cameron pressing ahead with new legislation which plans to stop people from sending any form of encrypted messages. If the law is passed all online messaging services which scramble communications between their users could be banned.
-
-
Tuesday, a group of cryptographers and security experts released a major paper outlining the risks of government-mandated back-doors in encryption products: Keys Under Doormats: Mandating insecurity by requiring government access to all data and communications, by Hal Abelson, Ross Anderson, Steve Bellovin, Josh Benaloh, Matt Blaze, Whitfield Diffie, John Gilmore, Matthew Green, Susan Landau, Peter Neumann, Ron Rivest, Jeff Schiller, Bruce Schneier, Michael Specter, and Danny Weitzner.
-
Late last month, the Maine House approved a bill to turn off support and resources to the NSA in the Pine Tree State, only to have it rejected by the state Senate.
Sen. Eric Brakey (R-Androscoggin) introduced LD531 on Feb. 26. The Maine Fourth Amendment Protection Act would have banned “material support or resources” from the state to any federal agency collecting electronic data without meeting one of four conditions.
-
-
-
-
The U.S. on Thursday refused to comment on a report that an American intelligence agency spied on a Turkish security meeting in 2014.
“We’re not going to comment publicly on every specific alleged intelligence or disclosure activity,” said State Department spokesman John Kirby.
Asked about a Germany-based magazine’s claims that the NSA had spied on a top Turkish security meeting that discussed Turkey’s possible intervention in Syria to protect a Turkish enclave, Kirby directed all related questions to the NSA.
The magazine’s claims include that the NSA tapped the Turkish intelligence chief’s phone and collected audio from the meeting.
-
Despite their intended roles as representatives of the United States abroad, new WikiLeaks cables reveal the extent to which US diplomats are asked to gather intelligence, the same intelligence used by the NSA to target foreigners.
Earlier on Thursday, WikiLeaks revealed that the US National Security Agency eavesdropped on the German chancellery for decades, most recently during secret briefings between German Chancellor Angela Merkel and her advisors regarding European finance plans.
-
Every week, thanks to Wikileaks, evidence of the NSA’s boundless surveillance of Germany piles higher. As a sovereign state, the Federal Republic shouldn’t put up with this, writes DW’s Matthias von Hein.
-
The US National Security Agency tapped phone calls involving German chancellor Angela Merkel and her closest advisers for years and spied on the staff of her predecessors, according to WikiLeaks.
-
Documents released by WikiLeaks appear to show the US spied on close aides of German Chancellor Angela Merkel and other officials for years. The leaks show Merkel’s private and professional opinions on a range of issues.
-
The U.S. National Security Agency tapped phone calls involving German Chancellor Angela Merkel and her closest advisers for years and spied on the staff of her predecessors, WikiLeaks said on Wednesday.
-
Less than a month after Germany abandoned its probe into alleged NSA spying on Chancellor Angela Merkel, a new Wikileaks drop suggests snooping on the Chancellory goes back decades.
The leak, published here, draws the inference that prior chancellors were targeted, based on the list of telephone numbers targeted by the NSA.
-
-
-
-
-
Restriction of cooperation, identification of personnel: U.S. intelligence expected to mirror information with harsh reactions, after it was revealed that she bugged the phone of the Chancellor. The reluctance of the German surprised her.
-
-
-
-
-
-
-
-
-
-
-
-
-
While encryption and secured messaging has long been a topic of interest in tech circles, the issue became a mainstream and hot-button issue in 2013 following a series of Edward Snowden leaks detailing the NSA’s extensive efforts to bolster their electronic snooping capabilities.
In the back and forth battle over consumer privacy, one tends to think of government cryptographers looking to outwit engineers at companies like Google and Apple who help churn out some of the most widely used software across the globe.
But playing an instrumental role in this cat and mouse game is a man you might not ordinarily expect to see in such a discussion.
-
A German magazine has claimed a video of a key high-level security meeting on Syria was recorded and leaked by the U.S. National Security Agency (NSA), according to the Turkey-based Today’s Zaman.
According to German magazine The Focus, the video, which was leaked online last year, was exposed by the NSA after it was instructed by unnamed U.S. political leadership to gather information about the “intentions” of the Turkish leadership and monitor Turkeys operations in 18 other key areas.
-
-
German weekly magazine Focus has said that last year’s leaked audio of a high-level security meeting at the Turkish Foreign Ministry about possible military action in Syria via a false flag operation was recorded and then leaked by the US National Security Agency (NSA).
-
Last Wednesday, The Intercept published an expose on the NSA’s XKeyscore program. Along with information on the breadth and scale of the NSA’s metadata collection, The Intercept revealed how the NSA relies on unencrypted cookie data to identify users.
-
Because of the Electronic Communications Privacy Act (ECPA)—passed in 1986, long before electronic communications became prevalent in the United States—email content is easily accessible to many civil and law enforcement agencies as soon as it is at least 180 days old.
-
Most Americans are familiar with the National Security Agency as the face of domestic spying.
Few, however, have heard of the U.S. Consumer Financial Protection Bureau, an agency that critics say knows more about you than even the NSA’s purveyors of bulk telephone data.
-
The government published its latest Wiretap Report on July 1. The headline finding was that encryption wasn’t foiling federal and state law enforcement officials, despite a growing chorus of people suggesting that we’re all gonna die unless the tech sector builds backdoor access into their products to enable government access.
In all, the federal agency that oversees the courts reported to Congress that there were 3,554 wiretaps in 2014, about 1 percent less than the year prior. Of the total, only four were thwarted via encryption.
But the reported number of wiretaps by the Administrative Office of the US Courts (AO) simply doesn’t add up. That’s according to Albert Gidari, one of the nation’s top privacy lawyers.
-
The NSA is gathering and eavesdropping on practically all communications emerging from South America, WikiLeaks founder Julian Assange told Chilean publication El Mostrador Tuesday.
“Ninety-eight percent of Latin American communications are intercepted by the NSA while passing through the United States to the world,” Assange said in an interview with the publication.
-
-
-
The US National Security Agency (NSA) can resume the bulk collection of telephone records, at least temporarily, a US Foreign Intelligence Surveillance Court ruled Monday.
-
The service utilizes more than 700 servers located in multiple nations, and apparently the US is not the only one using it.
-
That includes pictures, documents, voice calls, webcam photos, web searches, advertising analytics traffic, social media traffic, botnet traffic, logged keystrokes, computer network exploitation (CNE) targeting, intercepted username and password pairs, file uploads to online services, VOIP streams taken from Skype sessions, and more.
-
Edward Snowden has once again provided fodder for the surveillance fears of American citizens: New leaked documents show that the National Security Agency’s (NSA’s) XKeyscore search engine hoovers up vast amounts of private communications information, to the tune of 700,000 voice, fax and video files every day.
-
Many were not surprised when NSA-contracted analyst Edward Snowden blew the whistle on the government organization, revealing massive, likely illegal domestic spying programs.
As the details came out, the government went into full damage control, and one keyword that surfaced was “metadata.” It was just metadata they were collecting without a warrant, they said, not the kind of data that would reveal anything personal about its owner. The word left the mouth of every government official who spoke on the subject, and the common belief became that it was not wiretapping going on, just mass surveillance.
-
On July 3rd, the top choice for the UN’s first digital privacy investigator, Katrin Nyman-Metcalf, was rejected by the German president of the Human Rights Council (UNHRC), who cited complaints from activist groups that she was not a strong enough critic of government surveillance.
-
Newly released documents leaked by Edward Snowden shed light on the scale and scope of the XKeyscore program, a program described by one classified document as the “widest-reaching” system for gathering information from the internet.
-
Every time anyone uses a computer to send an e-mail, watch a video, do a Google search, or update a Facebook status, the National Security Agency (NSA) is probably collecting and collating that activity on one of its many servers.
XKEYSCORE — the codename of the computer code used by the NSA to perform these actions — is massive and more intrusive than most people understand.
-
President Barack Obama got a list of talking points that United Nations Secretary General Ban Ki-moon hoped to hit on during a one-on-one meeting, courtesy of the NSA’s X-Keyscore program.
-
-
The NSA’s Google-like search engine for the world’s private communications data, XKEYSCORE, has more information than previously thought, including router information and VoIP streams from Skype calls.
-
The evidence for these plots? As usual, none was provided. Just the word of “US officials.”
-
-
In a guest post on the Lawfare blog, FBI Director James Comey argued that “to protect the public, the government sometimes needs to be able to see an individual’s stuff,” though only “under appropriate circumstances and with appropriate oversight.”
-
On Tuesday, a who’s who of cybersecurity essentially slammed the door in the face of the United States and Great Britain. The experts’ report said giving the governments access to encrypted data passing through the likes of Apple, Twitter and Facebook represented an existential threat to the most sensitive information on the Internet.
-
-
-
-
-
-
This week, expert cryptographers, computer scientists and security specialists released a study titled “Keys Under the Door Matt,” looking at proposed mandates for government access to all data and communication. The paper concludes that “analysis of law enforcement demands for exceptional access to private communications and data show that such access will open doors through which criminals and malicious nation-states can attack the very individuals law enforcement seeks to defend.”
-
Testifying before two Senate committees on Wednesday about the threat he says strong encryption presents to law enforcement, FBI Director James Comey didn’t so much propose a solution as wish for one.
-
FBI Director James Comey is set to testify against encryption before the Senate Intelligence Committee today, as the United States and Britain push for “exceptional access” to encrypted communications. Encryption refers to the scrambling of communications so they cannot be read without the correct key or password. The FBI and GCHQ have said they need access to encrypted communications to track criminals and terrorists. Fourteen of the world’s pre-eminent cryptographers, computer scientists and security specialists have issued a paper arguing there is no way to allow the government such access without endangering all confidential data, as well as the broader communications infrastructure. We speak with one of the authors of the paper, leading security technologist Bruce Schneier.
-
Jeb Bush may be among the strongest Republican contenders in the 2016 White House race, but he is unlikely to win support from Edward Snowden after he ruled out any “leniency” for the National Security Agency (NSA) leaker, CBS News reported.
-
-
-
-
-
-
-
-
Congress recently passed a bipartisan bill (USA Freedom Act). Some of us thought a bipartisan bill outside its ken. The act curtails the National Security Agency program of storing phone records of millions of Americans, even those not suspected of any crime. Now, phone companies will store the records. Also, a special panel of experts will be added to the Foreign Intelligence Surveillance Act court to represents the public when NSA wants to obtain records.
-
Katherine Archuleta, head of the Office of Personnel Management, resigned after it was revealed that the hack affected a staggering 21.5 million people, far more than initially believed.
-
If federal authorities have their way, Facebook, Twitter and other social media sites will be forced to report users’ activities under a new provision of the 2016 Intelligence Authorization Act.
-
The European Data Protection Supervisor, Giovanni Buttarelli, who is responsible for ensuring that the machinery of EU government respects the privacy of a citizen’s data when processing their data, says that it is time to “move beyond the false fad of discussing security vs. privacy.” In an article published on The Mark News site, Buttarelli writes that governments should “focus on implementing laws that take into account privacy rights as well as the indisputable need to fight terrorism.”
Buttarelli insists that as European Data Protection Supervisor he is not necessarily “for or against any specific measure that interferes with the right to privacy and involves handling large volumes of personal information,” for example through large-scale surveillance. However, he points to a post by the security expert Bruce Schneier that shows, in the US at least, there is little evidence that mass surveillance prevents terrorist attacks.
-
The hunters become the hunted. Yesterday, hackers released what they claimed was 400 GB of internal documents stolen from Hacking Team – an Italian company that sells surveillance tools to governments and intelligence agencies.
The release of the documents has exposed the reality of the lucrative cyberweapons market.
Ever since, security experts have been poring over the files and publishing their findings. For one thing, the documents suggest Hacking Team marketed its products to a wide range of governments – including a host of repressive regimes.
-
The NSA has been spying on politicians and common citizens, domestically and abroad, for decades now. Now, a recent online hack of private documents has revealed that national governments are able to obtain software services to hack into Bitcoin and other private digital currency accounts through an Italian subcontractor.
400GB of documents captured from a popular international surveillance technology company called Hacking Team has been uncovered by CSO Online’s Steve Ragan. These documents reveal what spy technology is available and how much countries are investing in it.
-
It’s called Hacking Team. And the world knows about it, because Hacking Team has been hacked.
On Sunday, a massive load of stolen documents were uploaded to the Internet. It revealed contracts, invoices and internal presentations of Hacking Team. And it offered a glimpse into a shadowy world of selling high-powered cyber weapons — even to genocidal maniacs.
CNNMoney could not verify the authenticity of these documents. However, specific details in several separate documents form a consistent picture of Hacking Team’s business dealings.
-
Hacking Team, an Italian company offering security and surveillance services, has apparently fallen victim to exactly the thing it promises protection from: security breaches.
-
An Italian firm with the appropriate name Hacking Team suffered a massive breach in its company data Sunday, and 400GB of internal documents so far have been released and are being analyzed by reporters and security researchers. Hacking Team’s customers are government agencies, including both law enforcement and national security, and the ostensibly legal software it sells to help them intercept communications includes not-yet-exploited vulnerabilities, known as zero-days.
-
Forget about voiding your warranty and potentially rendering your iPhone unusable if something goes wrong, Apple fans now have another reason to avoid jailbreaking their smartphones: Government agencies like the NSA have the ability to spy on jailbroken iPhones, and now we have proof.
-
-
T-Mobile received nearly 351,940 government requests for data in 2014, the most out of any of the four national wireless carriers.
The nation’s fourth-largest carrier by subscriber base disclosed in its transparency report on Wednesday that it had fielded 177,549 criminal and civil subpeonas, 17,316 warrants and more than 3,000 wiretap orders.
-
The US National Security Agency (NSA) has been conducting surveillance of top-of-the-line businessmen and politicians in France and Germany for over ten years, alleges WikiLeaks that published series of new documents on June 29 and July 1, 2015.
-
Civil Rights
-
Imprisoned journalist Barrett Brown is Courage’s fifth beneficiary
Courage is raising funds for Brown’s commissary, restitution and legal costs
Brown continues to write from prison, for D Magazine and soon for The Intercept
Currently in solitary confinement, Brown needs continued support and assistance
US journalist and satirist Barrett Brown, author of Flock of Dodos and Keep Rootin’ For Putin, is the Courage Foundation’s fifth beneficiary. Brown is currently serving a 63 month sentence after being persecuted for his work. In 2012, the FBI raided his house, and later that year Barrett was indicted on 12 federal charges relating to the 2011 Stratfor hack. The most controversial charge, linking to the hacked documents, was dropped, but in 2015 Brown was still sentenced to prison.
-
PINAC correspondent Michale Hoffman was found guilty today for trespassing on public property, a decision our attorney plans to appeal immediately.
He faces up to a year in jail. He will be sentenced Thursday, which is tomorrow.
“While we are disappointed in the jury’s verdict we look forward to appealing the judge’s rulings on the First Amendment issues that the jury was not allowed to hear or consider,” said attorney Eric Friday.
Hoffman was arrested in August while standing on the property of Jacksonville International Airport holding up signs that were critical of the government, including TSA and the IRS.
However, the judge did not permit Hoffman or our Friday to use the First Amendment as a defense.
Duval County Judge Brent Shore also refused to answer the jury’s question about whether or not holding up signs on public property is illegal.
-
-
Intellectual Monopolies
-
Trademarks
-
One can appreciate the importance of this issue with Native Americans and, as the legal battle has been drawn out over the years, it seems that this combination of commercial and constitutional issues is surely destined for the Supreme Court.
Permalink
 Send this to a friend
Send this to a friend
07.10.15
Posted in Europe, Patents at 7:20 am by Dr. Roy Schestowitz
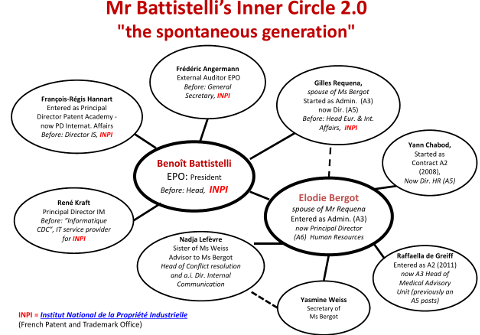
Summary: Rather than combat perception of corruption in appointments around Battistelli, the EPO does more to reinforce this perception
SUEPO has just published [PDF] “Mr Battistelli’s Inner Circle 2.0 – “the spontaneous generation” (09/07/2015)” and as the poster puts it (evident from the graph), “Mr Battistelli’s Inner Circle has evolved since 2014.”
Remember that all of these people receive astronomical (but undisclosed) salaries, sourced from European taxpayers.
Notice not only the professional relationships (bringing one’s old mates to protect oneself) but also the incestuous relationships. It’s like the Binay family (many people of the same family promoted to positions of power through corruption and money laundering). It’s akin to dynasty or royalty/monarchy. And this is the supposedly democratic European Union we’re talking about! It’s not about what you know but about who you know and who’s in your family. That is seemingly the promotion and hiring yardstick at today’s EPO. It’s not just "Balkan standards" but the standards of a third world country. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft at 6:57 am by Dr. Roy Schestowitz
Summary: Microsoft’s ‘damage control’ strategy is working, as the media helps Microsoft disguise company-wide layoffs as layoffs at another company
“So that next firing cycle came today at Microsoft,” wrote Mr. Ahonen, a renowned Nokia expert. It’s about Microsoft. These are Microsoft layoffs and the latest layoffs should be described as such.
Commenting on this subject, some Finnish media chose to focus only on the Nokia aspect. “Microsoft has announced a new round of lay-offs,” it said, “and an ‘impairment charge’ associated with its acquisition of Finnish firm Nokia’s mobile phone business. Some 7,800 jobs are to go, mainly in the devices unit bought from Nokia.”
It also showed the impact on the Finnish government:
The Finnish government will submit a supplementary budget in September to lay out its plans to deal with the fallout from Microsoft’s plans to lay off some 2,300 people in Finland.
This is a bit misleading, however, as our sources indicate that the layoffs are far more wide-reaching than the mobile unit and Nokia. Some reader from Finland claims the publication above (both articles) to be Microsoft-connected in the staff sense (at a high level), so maybe there is an attempt to misdirect and distract. Watch how the Microsoft-friendly ToryGraph frames this as a “Nokia deal” thing. It’s not. Other British media says “Microsoft writes-off Nokia purchase”, but that’s not really the news, is it? The layoffs are news. Not single department is affected and Microsoft is short on details.
“It’s quite clearly a gross propaganda pattern and it has proven effective so far”Microsoft expects (and needs) people to think that Vista 10 will be great and Windows is in good shape whilst announcing these layoffs, so the effort to blame all the layoffs on mobile failure and “Nokia” is a good distraction ahead of Vista 10′s release.
Let us state this again: Microsoft suffers cuts at many divisions other than mobile. Don’t believe the media coverage which tries to blame all of Microsoft’s problems on that. It’s quite clearly a gross propaganda pattern and it has proven effective so far. █
Permalink
 Send this to a friend
Send this to a friend
Posted in America at 6:37 am by Dr. Roy Schestowitz
Summary: The Affinity v. Direct TV case is the latest case to show how software patents can be invalidated, citing the US Supreme Court (SCOTUS)
UPLOADED just now is this decision [PDF] which shows how, yet again, Alice kills software patents. [hat tip: Patent Buddy]
This case involved the capital of patent trolls, Texas, and it it a case between Affinity and Direct TV. Alice is cited in page 5. “These categories are not patent-eligible,” says the document, then citing the Mayo case as well. SCOTUS is quoted as saying that “all inventions… embody, use, reflect, rest upon, or apply laws of nature, natural phenomena, or abstract ideas.” Let’s see how many Web sites run by patents lawyers even bother to mention this outcome… █
Permalink
 Send this to a friend
Send this to a friend
Posted in BSD, GNU/Linux, Google, Microsoft at 6:22 am by Dr. Roy Schestowitz

Image credit: Linux Veda
Summary: Cyanogen continues to expose itself for what it really is and who it is serving, owing to staff background
MICROSOFT took over not only Nokia, inciting it to attack Android (Nokia now attacks Android using patents) but also Cyanogen, the company whose agenda seems to now closely align with Microsoft’s. Many of its employees are based near Microsoft, but that’s not too shocking. It puts the NSA’s leading partner (Microsoft) right at the centre of AOSP whilst smearing Google, which developed AOSP and gave it away as Free software. We previously covered this in posts such as:
Microsoft’s proxy Cyanogen has just hired Microsoft’s Lawler, based on this article. What a surprise? Not! To quote CBS ZDNet: “Formerly Lawler was also chief technology officer of Microsoft’s Bing Maps…”
Microsoft’s strategy against Android has become utterly ugly as it includes patent extortion. Some of the media tries to nevertheless characterise Microsoft as a friend of Free software. The latest example is Windows (proprietary) promotion by payments to OpenBSD — a move that is criticised by FOSS Force, which says: “Of course, it isn’t revealed how much, in code, Microsoft is going to contribute going forward, but as long as the money is there…I guess the money is there.”
Microsoft keeps trying to use its money to disrupt Free software projects. It did this in 2006 with Novell (a GNU/Linux actor at the time) and it is still doing that with other companies or nonprofit entities. Cyanogen is one of these and OpenBSD hopefully has the moral strength to bite the new hand that feeds. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 5:15 am by Dr. Roy Schestowitz

Contents
-
What sets the Endless apart from other low cost machines is Endless OS, a highly customized version of Ubuntu Linux with Gnome (and lots of other interesting technology such as Xapian and OStree) that not only handles TVs as output devices (it scales and formats video output for readability), but also includes a huge library of applications and educational content. This is important because in emerging markets the Endless system will be useful and well-featured even if you don’t have any kind of networking services available.
-
Gumstix and KIPR have used Gumstix Geppetto to design a new Linux-on-Sitara based robot controller for upcoming K12-focused autonomous Botball contests.
The nonprofit KISS Institute for Practical Robotics (KIPR) has been holding regional and international Botball Educational Robotics competitions for K12 students since 2003. At this year’s international competition, which runs this week from July 7-11 in Albuquerque, New Mexico, KIPR joined with Linux embedded board manufacturer Gumstix to announce that the companies have designed next year’s KIPR controller device for Botball robots using the online, drag-and-drop Gumstix Geppetto hardware development tool.
-
Grandstream’s “GVC3200″ is an Android based videoconferencing device that offers 9-way SIP/Android sessions, a 12x zoom HD camera, and triple HDMI displays.
Any Android device with a front-facing camera is potentially a personal videoconferencing device, especially now that Google Play has apps like Skype and Google Hangouts. Yet, we haven’t seen many Android- or Linux-based systems that do business-class, room-sized videoconferencing, let alone non-video conferencing systems like this week’s Android-based DCN Multimedia Conferencing System from Bosch. The only recent exception we can recall is Google’s VC-ready Chromebox for Meetings, which runs the Linux-based Chrome OS.
-
“I got a very minimal Linux running (kernel 0.93p11) and then later bought a set of disks from Duke University (kernel 0.93p13still SLS),” he said. “My first really useful Linux was Kernel 1.2.8 Slackware 2.3. I couldn’t get X Windows to run but this was MS DOS days so color Bash was pretty cool. I had an offline packet reader for mailing lists from bulletin boards. I also used minicom to dial up GEnie. Later I started using SLIP to get to to the Internet and dropped GEnie.”
-
Desktop
-
Luckily, there’s a whole other world of Linux. There are dozens of smaller distros that specialize in lightweight desktops that do the basics – manage windows, and offer file browsers, launchers and sometimes a menu bar of some sort – but otherwise stay out of the way. The point, after all, is the applications. Why waste RAM running a fancy desktop when all you want to do in interact with the apps you’re running? If you have the RAM to spare, well, sure, why not? But not all of us do.
-
Kernel Space
-
Linus Torvalds was interviewed by Slashdot last week and his comments on artificial intelligence has been making the rounds since. He basically said AI would not lead to human-like robots because the neural network would remain limited. Despite that, Google has “applied for at least six patents on fundamental neural network and AI.” In other news, Kali Linux 2.0 is expected at DEFCON 23 and the Free Software Foundation has approved another Linux OS for its “fully free” list. Docker ‘Tinkerer Extraordinaire’ said Open Source is hostile to women and Megatotoro posted Pisi Linux is still alive and kicking.
-
Graphics Stack
-
-
The AMD developers have announced that a new Catalyst Linux driver, 15.7, has been released and is now available for download. It’s been a while since we had a stable version of the Catalyst driver, but it’s still not all that impressive.
-
Applications
-
As you may know, Dzip is an open-source, command-line software for file compression/decompression. It has drag and drop support, the users being able to easily create .dz files. But unlike WinZip or other software, it does not copy the extracted files to temp and move them to the destination when finished, the files being copied to the destination directly.
-
This month, we welcome Thien-Thi Nguyen as the new maintainer of GNU Superopt.
-
-
-
-
Instructionals/Technical
-
Games
-
It’s been a while since last reporting on Unvanquished (mostly because it seems their RSS feed is broken), but they’ve continued moving along with their open-source game and Daemon engine. This first person shooter is now up to its 41st monthly alpha release.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
After a month of bugfixing, we give you Krita 2.9.6! With lots of bugfixes, but bugfixes aren’t the only thing in 2.9.6, we also have a few new features!
-
-
Papyros is a new Linux distribution built from scratch that uses the Material Design guidelines. Developers chose to build an entirely new desktop shell that perfectly simulates the use of Material Design, and the team is really close to releasing the first testing version for the public.
-
I’m happy that Pisi is still with us. It has become too silent and almost secluded, but I still hope Pisi does not go extinct.
-
Reviews
-
ChaletOS is a Xubuntu-derived distribution, with very little to no publicity surrounding it. Even its official domain, a humble, unassuming Google sites page, does not offer too much information. I came across ChaletOS while reading Gizmo’s Freeware forums, and I was hooked by its rather stylish, colorful looks.
-
-
New Releases
-
The design goal for Alpine Linux is to provide a secure and lightweight distribution, which should cater the needs of most of the Linux users. It is based on musl and BusyBox; today Alpine Linux 3.2.1 has been released, in this article we will be reviewing the noteworthy features of this Linux distribution and the installation process for this latest release.
-
We’ve been awfully quiet lately, which usually means something is brewing below the surface. In the past few months we’ve been working feverishly on our next generation of Kali Linux and we’re really happy with how it’s looking so far. There’s a lot of new features and interesting new aspects to this updated version, however we’ll keep our mouths shut until we’re done with the release. We won’t leave you completely hanging though…here’s a small teaser of things to come!
-
Screenshots/Screencasts
-
Red Hat Family
-
Fedora
-
Flock is our big, annual contributor conference, where we get together to talk about what we’re working on and what we want to do in future releases, and also actually get in rooms together to hack on ideas. It’s also great fun, and a celebration of our “Friends” foundation.
-
Debian Family
-
-
Derivatives
-
Canonical/Ubuntu
-
The new Meizu MX4 Ubuntu Edition was officially released in Europe a couple of weeks ago, but it’s available only in a limited fashion. Now, Canonical has announced that the number of invites to purchase the phone has been increased so that more users can order it.
-
-
Canonical has started to improve Launchpad again, and developers have made a number of changes and improvements. It looks like the recent Git integration is not the only new feature that will be made available.
-
-
Ubuntu 15.10 is now in the middle of the development cycle, and developers are upgrading packages left and right. One of those packages is the systemd component, which has been recently made default in Ubuntu.
-
Canonical published details a couple of days ago, in a security notice, about an HAProxy problem that was identified and fixed for its Ubuntu 15.04 and Ubuntu 14.10 operating systems.
-
” It is still a WIP and it is also quite early, but if you want to try out Snappy Personal Desktop,” http://carla-sella.blogspot.co.uk/2015/07/snappy-personal-desktop.html
-
For those interested, it’s becoming possible to play with Ubuntu’s Snappy next-generation package manager from a personal desktop.
-
Lenovo is preparing to ship laptops preloaded with Ubuntu in India. The first of these systems will be the Lenovo Thinkpad L450, featuring only one of two CPUs, but the selection may widen over time and expand to other countries.
-
Canonical, the commercial sponsor of Ubuntu, has partnered with computer OEM Lenovo to launch the ThinkPad L450 series running the Linux distro in India. Starting at Rs 40,000, the laptops will be available to purchase from selected commercial resellers and distributors.
-
-
Flavours and Variants
-
A disagreement between the founder of Kubuntu and the Ubuntu Community Council has roiled the Linux community and left the project rudderless, as Jonathan Riddell left Kubuntu’s governing body late last month.
-
-
Phones
-
Android
-
The Open Source Virtual Reality (OSVR), an organization working towards an open standard for virtual reality devices, has announced that OSVR software now accommodates Android devices, adding to existing distribution for Windows and Linux.
-
-
Furthermore, the influence of a Github portfolio should not be underestimated. This may seem skin-deep, but importance lies in the fact that a high-quality Github portfolio reflects time and energy spent curating one’s projects. For instance, a good Github project is well-documented, contains a well-written README (or overview) and is well-marketed online so as to gain approval throughout the community (via stars – similar to “likes” on Facebook). The skills required to create and maintain a high-quality project speak loudly.
-
Reliance Communications (RCOM) and Sistema Shyam Teleservices, also known as MTS India, are increasingly adopting open source software as it helps them significantly cut costs.
-
-
Michelle Brush will talk at OSCON this year about how engineers and architects in tech can make better decisions by understanding their environment. How? Through behavioral economics, a discipline that, in her words, straddles psychology and economics.
-
Sprints are one of the most effective tools for building momentum and community around an open source documentation project. For the past four years, the Open Help Conference & Sprints has hosted doc sprints for a number of prominent open source projects, and often has been the first sprint venue for a project. Open Help celebrates its fifth year in 2015 with a venue upgrade and space for six doc sprints.
-
When you deal with a lot of documents every day, whatever you write—whitepapers, manuals, presentations, different marketing materials, contracts, etc.—at a certain point (most commonly, at the final stage) you have to interact with different people, specifying and discussing details, proofreading and approving them.
-
This is why we need open source more than ever, particularly in the underlying data infrastructure that undergirds the modern enterprise. You don’t need to take my word for it. You can download it. You can trust the code and your own experience.
While the cardinal virtue of open source may be that anyone is free to modify/fork the code, the reality is that few actually do. But the first virtue—free and unfettered access to code—is powerfully important, too, and it’s the right that most people associate with open source.
-
I suppose it’s rather fitting that I’m mentioned twice in the book, because that’s how many times I’ve worked at Red Hat: initially from 2005 to 2007 (my first “real” job after college) and again from 2012 to the present. In the interim, I happened to write an article for Opensource.com, which ultimately ended up quoted in the book (on page 94).
-
SaaS/Big Data
-
Mirantis, which has emerged in recent years as a leading vendor in OpenStack software and services, is helping enable cloud hardware though the launch of its new Mirantis Unlocked Appliances program.
-
The OpenStack Foundation has a problem – its’ community voted on the name ‘Meiji’ for its post-Liberty release, but apparently there are some historical challenges with the name.
-
As evidence of how hot the cloud computing space remains, the company has just announced that it has raised $83 million in new funding.
-
-
Oracle/Java/LibreOffice
-
-
-
-
In the previous article, we saw that the increasing adoption of open-source databases is causing a dent in Oracle’s (ORCL) dominance in the database market, as well as its earnings. On June 17, 2015, Oracle announced its fiscal 4Q15 and 2015 results. Software licensing and support contribute approximately half of Oracle’s overall revenues.
-
-
-
Oracle has just released a new major version for VirtualBox, which is one of the most used and powerful applications of its kind for Linux users. The 5.0 version has been in the making for quite a while, and the stable version has finally landed.
-
This blog is dedicated to the Solaris Firewall. The current firewall bundled with Solaris is IPF version 4.1.9. It has been introduced in Solaris 10u3.
-
This is one more data point among several that major players in the proprietary part of the IT landscape find real value in the technology coming out of OpenBSD, and that tracking the source closely helps their own innovation. Another recent case in point is the news of Solaris moving to PF instead of IPF, reported here recently.
-
Business
-
Semi-Open Source
-
Previously a paid product, RESTfm is now free and open source, with a paid support model so everyone has the ability to try it and see the benefits for themselves. The RESTfm source code is now available under an MIT licence from GitHub.
-
-
There’s the cathedral — where an exclusive team of developers build and produce a product that is later released with the source code, which is top-down and closed. Then there’s the bazaar — where the software is developed online and amongst numerous developers with different agendas and approaches, which is bottom-up and open.
-
The one-stop-shop value proposition has been around as long as the data center itself, but few vendors are able to deliver upon the promise nowadays due to the sheer scope of work involved in delivering applications at scale. One of the few exceptions to the rule is HashiCorp Inc., which officially launched its first commercial solution this morning to tackle the fragmentation of DevOps.
-
-
Funding
-
Project Jupyter, an open-source software project led by Fernando Perez of University of California, Berkeley and Brian Granger of California Polytechnic University, San Luis Obispo has been granted $6 million over the next three years. The grant will help expand Project Jupyter to support scientific computing and data science applications in more than 40 programming languages.
-
Openness/Sharing
-
In order to shift American culture and win our campaigns for social, environmental, and racial justice, we must have the best, latest tools available, and they need to be able to sync-up. As a communications professional who often gets roped into fundraising, website design, and other various aspects of nonprofit work, I’ve been searching for over a decade for the perfect set of tools to handle communications, marketing, and fundraising. It doesn’t exist.
-
Open Data
-
British Airways is giving developers tentative access to small amounts of its data, launching a scheme to open up some of its APIs.
-
Open Hardware
-
Jean-Michel Mourier, CTO of Blue Frog Robotics, wrote in an email to SD Times that, “About 80% of BUDDY will be open source. Today, all of the major components are open source: the brain of the robot, which controls navigation, facial expressions, object and voice recognition, interfaces that control interactions, learning, making connections as well as domotics. In addition, elements of BUDDY’s mechanics are open so that developers can build accessories.”
-
The open source essence of Beveridge’s idea is not unprecedented. In 2011, London design practice ‘00’ initiated WikiHouse, an open source project for designing and building houses that offers users the opportunity to download customizable Creative Commons-licensed plans. Using a method that has drawn comparisons to Ikea furniture, the building pieces are then cut from plywood by CNC routers and snapped together with wedge and peg connections, to be assembled onsite in less than a day.
-
Security
-
The latest OpenSSL security hole isn’t a bad one as these things go. It’s no Heartbleed, Freak, or Logjam. But it’s serious enough that, if you’re running alpha or beta operating systems, you shouldn’t delay patching it.
Fortunately, the affected OpenSSL versions are not commonly used in enterprise operating systems. For example, it doesn’t impact shipping and supported versions of Red Hat Enterprise Linux (RHEL) or Ubuntu. In the case of Ubuntu, it does affect the 15.10 development release, but the patch is already available.
-
-
-
The results are fascinating.The Census Project is very, very good at identifying projects which are still widely popular, but which are hardly maintained. This is the sweet spot for the Core Infrastructure Initiative to look into to try to identify lurking issues and help find a way to fix them before they become problems for our core infrastructure.
-
-
The Core Infrastructure Initiative (CII) has announced a new project to help determine which open-source projects are critical to Internet infrastructure, and in need of additional support and funding. The Census Project is an experimental tool meant to gather metrics and prioritize projects for CII review.
-
The open-source OpenSSL cryptographic library project came out today with a high-severity security advisory and patched a single vulnerability, identified as CVE-2015-1793. OpenSSL is a widely used technology that helps to enable Secure Sockets Layer/Transport Layer Security (SSL/TLS) encryption for Web data transport for both servers and end-user devices.
-
A ‘HIGH SEVERITY’ BUG is currently unpatched in OpenSSL, the open source software used to encrypt internet communications, and a new version is due to be released on 9 July.
-
There’s a critical vulnerability in some versions of the widely used OpenSSL code library that in some cases allows attackers to impersonate cryptographically protected websites, e-mail servers, and virtual private networks, according to an advisory issued early Thursday morning.
-
We heard another big OpenSSL vulnerability would be announced soon and today it’s been made public: OpenSSL’s latest “high” severity security vulnerability.
-
-
The OpenSSL project has disclosed a new certificate validation vulnerability.
-
If the probability of your assets being prodded by attackers foreign and domestic doesn’t scare the bejesus out of you, don’t read this article. If you’re operating in the same realm of reality as the rest of us, here’s your shot at redemption via some solid preventive pen testing advice from a genuine pro.
-
Now that’s an intriguing question, isn’t it? Just about every other computerized process has proven to be vulnerable, and as voting becomes even more technology based, it becomes increasingly vulnerable as well. Computer systems are generic processing hosts, and to a computing platform, data is simply data. The fact that certain information tallies votes rather than credit card transactions does not make it any harder to hack. Moreover, the U.S. has a long history of documented voting fraud, so there’s no reason to assume that politicians, and their backers, have suddenly become paragons of virtue. Indeed, there’s plenty of evidence to the contrary.
When you come down to it, the only thing that’s different today is that altering votes might be easier, and that those motivated so do so may be harder to catch. So why aren’t we hearing more about that risk?
-
Defence/Police/Secrecy/Aggression
-
For years now, the global jihadist movement centered in the Middle East has been split into two broad factions, represented by the al-Qaeda franchise on the one hand, and the Islamic State (also known as ISIS or ISIL) on the other. The latter is rooted, in part, in the Jama’at al-Tawhid wal-Jihad group founded by the Jordanian Bedouin Abu Musab al-Zarqawi, which was once a rival of Osama bin Laden’s al-Qaeda.
-
Environment/Energy/Wildlife
-
“BP Deal Will Lead to a Cleaner Gulf” is the headline the New York Times puts over a July 8 editorial that, in its tone and substance, makes a pretty good illustration of why it almost assuredly won’t.
-
Finance
-
Thirteen million UK families will lose an average of £260 a year due to Budget changes to working-age benefits, says the Institute for Fiscal Studies (IFS).
Tax credit changes could hit three million families, which are likely to lose an average of £1,000, it said.
Even taking into account higher wages, people receiving tax credits would be “significantly worse off,” said Paul Johnson, director of the IFS.
-
On Sunday, as we reported here, the Greek people voted NO to more loans and increased austerity measures by the ECB and IMF. It was a historic referendum result that revived that old-fashioned idea of democracy in a Europe now controlled by shady financial institutions and faceless international creditors. Winning a NO vote was an enormous victory for Greece’s ruling party Syriza, and yet shortly after the result, Finance Minister Yanis Varoufakis resigned (full story here). He had hinted that anonymous, powerful people had forced him out of his job, and in this video Varoufakis makes some more comments that should make all of us feel quite nervous about the future of our political and economic systems.
-
PR/AstroTurf/Lobbying
-
Privacy
-
The challenge to DRIPA brought by David Davis and Tom Watson was discussed in court today, as the government sought to refer key questions to the EU courts.
-
The social network is currently in the advanced stages of launching a music video service similar to YouTube that will pay artists for video streams using advertising revenue.
-
Hacking Team, a controversial Italian company that specialises in selling powerful surveillance software, has been colossally hacked. Included in a 400GB cache of files released publicly are alleged hotel bills, invoices from government agencies for computer exploits, passwords, and possibly even the source code for a number of the company’s products.
-
I knew he had fast cancer, but this news was still a gut-punch. He was practically the model of what an activist could be: someone with integrity who could go from community meetings to street marches to think-tanks to a Parliamentary inquiry to a board-meeting without ever sacrificing his integrity.
-
Civil Rights
-
Well, Spain’s officially a police state now. On July 1st, its much-protested “gag” law went into effect, instantly making criminals of those protesting the new law. Among the many new repressive stipulations is a €30,000-€600,000 fine for “unauthorized protests,” which can be combined for maximum effect with a €600-€300,000 fine for “disrupting public events.”
-
Intellectual Monopolies
-
Copyrights
-
A new study has found that blocking access to torrent and linking sites results in the opposite effect. Instead of driving people towards legal websites and services, many of the blocked sites simply move to other domain names where they enjoy a significant and sustained boost in traffic.
-
A group of prominent legal experts, including the Cato Institute, the National Association of Criminal Defense Lawyers and the Institute for Justice have come out in support of Megaupload and Kim Dotcom. The groups urge the appeals court to undo the forfeiture of millions of dollars in assets, which they describe as a dangerous violation of due process rights.
-
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »





















 Content is available under CC-BY-SA
Content is available under CC-BY-SA