06.26.15
Posted in Site News at 8:12 pm by Dr. Roy Schestowitz
Summary: Some numbers to show what goes on in sites that do not share information about their visitors (unlike Windows-centric sites which target non-technical audiences)
THE common perception of GNU/Linux is that it is scarcely used, based on statistics gathered from privacy-hostile Web sites that share (or sell) access log data, embed spyware in all of their pages, and so on. Our sites are inherently different because of a reasonable — if not sometimes fanatic — appreciation of privacy at both ends (server and client). People who read technical sites know how to block ads, impede spurious scripts etc. These sites also actively avoid anything which is privacy-infringing, such as interactive ‘social’ media buttons (these let third parties spy on all visitors in all pages).
Techrights and Tux Machines attract the lion’s share our traffic (and server capacity). They both have dedicated servers. These are truly popular and some of the leaders in their respective areas. Techrights deals with threats to software freedom, whereas Tux Machines is about real-time news discovery and organisation (pertaining to Free software and GNU/Linux).
The Varnish layer, which protects both of these large sites (nearly 100,000 pages in each, necessitating a very large cache pool), handles somewhere between a gigabyte to 2.5 gigabytes of data per hour (depending on the time of day, usually somewhere in the middle of this range, on average).
The Apache layer, which now boasts 32 GB of RAM and sports many CPU cores, handled 1,324,232 hits for Techrights (ranked 6636th for traffic in Netcraft) in this past week and 1,065,606 for Tux Machines (ranked 6214th for traffic in Netcraft).
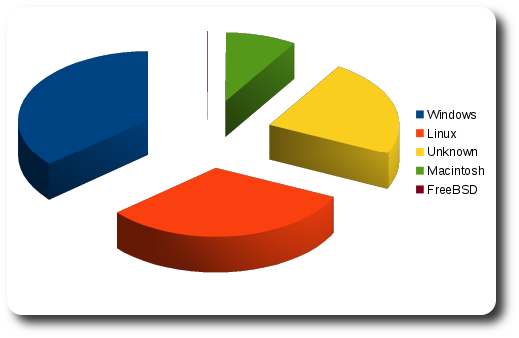
Based on VISITORS Web Log Analyzer, this is what we’ve had in Techrights:
Windows: (36.2%)
Linux: (31.8%)
Unknown: (e.g. bots/spiders): (23.0%)
Macintosh: (8.8%)
FreeBSD: (0.1%)
As a graph (charted with LibreOffice):
Tux Machines reveals a somewhat different pattern. Based on grepping/filtering the of past month’s log at the Apache back end (not Varnish, which would have been a more sensible but harder thing to do), presenting the top 3 only:

One month is as far as retention goes, so it’s not possible to show long-term trends (as before, based on Susan’s summary of data). Logs older than that are automatically deleted, as promised, for both sites — forever! We just need a small tail of data (temporarily) for DDOS prevention. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 7:34 pm by Dr. Roy Schestowitz

Contents
-
Server
-
Customers already pay Docker to host private image repositories on Docker Hub. But the subscriptions are cheap and the initial plans lacked features that enterprise customers demand, like granular access controls and the ability to integrate with their existing authentication systems.
-
Docker and CoreOS today are jointly announcing that they’re working with several major tech companies on a new Linux Foundation initiative called the Open Container Project. The idea is for everyone — users and vendors — to agree on a standard container runtime and image format and prevent unnecessary fragmentation.
-
The wrap up of DockerCon on Tuesday also marked the ushering in of a new era for the convention’s namesake company and the containerization ecosystem in general. One visible, real-world sign of the shift came when Docker founder and CTO Solomon Hykes and CoreOS CEO Alex Polvi met on stage to shake hands and announce the launch of the Open Container Project.
-
If you only read the press release — or worse, if you only read the business press produced by people who only read the press release — you’d have gotten the impression that the likes of Microsoft, Google, HP, Cisco, Red Hat, and Goldman Sachs had all rallied together under a flag of truce to declare the existence of a new standard for virtualization that the whole world would agree upon forever.
-
Kernel Space
-
Version 4.1 of the Linux kernel was released this week, and it includes a number of new features in the following areas.
-
A few days ago I set out to try out BCache on the Linux 4.1 kernel now that this caching feature has matured in the mainline Linux kernel for a while. BCache serves as a cache to the Linux kernel’s block layer whereby a solid-state drive (or other faster drive) can serve as a cache to a larger-capacity, traditional rotating hard drive.
-
The libata updates for the Linux 4.2 kernel may be of interest this time around for solid-state drive owners thanks to some NCQ TRIM improvements.
-
Lead developer and SUSE employee Jean Delvare announced the LM-Sensors 3.4.0 update a short time ago for this Linux sensor monitoring project. For the LM-Sensors library and sensors command is now support for temperature min and critical min hysteresis. The fan control program of LM-Sensors has been updated with reduced memory consumption and other fixes. Lastly, the sensors-detect utility has detection support of new devices and avoids probing graphics cards by default.
-
Graphics Stack
-
-
For X11 the library consists of 3 layers:
QObject wrapper for XInput (XInputDevice, XInputDeviceManager)
Adapters that map XInput objects to the common interface (XInputDeviceAdapter, XInputDeviceManagerAdapter)
Interface classes (InputDevice, InputDeviceManager)
-
Applications
-
The GStreamer development team had the great pleasure of announcing the immediate availability for download and testing of the second milestone towards the highly anticipated GStreamer 1.6 open-source and cross-platform multimedia backend.
-
-
Instructionals/Technical
-
Wine or Emulation
-
The Wine development release 1.7.46 is now available.
What’s new in this release:
Improvements in the BITS file transfer service.
Still more progress on DirectWrite implementation.
Support for shared user data on 64-bit.
Various C++ runtime improvements.
Some more support for the 64-bit ARM platform.
Various bug fixes.
-
-
-
-
The chains are loosening. DirectX still binds many PC games to Windows. Now, CodeWeavers expects CrossOver to support DirectX 11 by the end of the year, with Wine gaining compatibility shortly afterwards.
-
Games
-
Her Story is a new game developed by Sam Barlow, the creator of Silent Hill: Shattered Memories and Aisle. A Steam for Linux version is also available for purchase.
-
After three weeks from the release of Unreal Engine 4.8, Epic Games announced recently the immediate availability for download of the first maintenance release, Unreal Engine 4.8.1, which fixes over 30 bugs that were present in the previous version.
-
Crytek’s powerful game engine, CryEngine, just got more powerful than ever.
-
Valve has just published a new stable version of SteamOS, which brings a number of security updates and a new font for the main interface. It’s not a big update, but the addition of the new font should make it interesting.
-
The release candidate to the Unigine 2.0 Engine is now available.
-
Ticket to Ride, an adaptation of the well-known Days of Wonder board game, is now available on Steam for Linux with a massive 80% discount that will only last for a few more hours.
-
The Spring 99.0 release features improved performance, custom menu support, support for recursively drawing exploded pieces, a new rotateable default camera, Lua improvements, internal weapon refactoring, and many other changes.
-
Desktop Environments/WMs
-
For those closely following the work on Enlightenment, there’s now work finally materializing in supporting XWayland.
-
K Desktop Environment/KDE SC/Qt
-
GNOME Desktop/GTK
-
The GNOME software stack is home to a lot of applications and Notes is just one of them. The developers are looking to make some serious improvements to it in order to make it more appealing and more useful.
-
-
When the time comes around for your distribution of choice to release a new iteration of its platform, you are faced with a seemingly simple choice—to upgrade or do a fresh installation. On one hand, you wind up having to do less work. On the other, the end result is a clean, fresh start.
-
New Releases
-
The special release of Makulu 9 Aero edition might seem like one flexible Linux offering too many. However, anyone hankering for a Windows-like operating system and the best of what is easy about using Linux could not make a better choice.
-
I am happy to announce SparkyLinux 4.0 code name “Tyche”.
Sparky 4 is based on and fully compatible with Debian 9 testing “Stretch”.
The new iso images feature a set of applications for daily usage, wireless drivers, multimedia codecs and plugins, and they are available in a few flavors, such as :
– LXDE
– LXQt
– KDE
– MATE
– Xfce
-
The SparkyLinux developers were more than happy to inform us a few minutes ago about the immediate availability for download of the final release of their Debian-based SparkyLinux 4.0 distribution.
-
Ballnux/SUSE
-
openSUSE developers are preparing a new major release, but they are going to call it 42 and not 13.3 or something else. The changes are so profound that a completely new release was needed.
-
-
Deep thought and some additional core SUSE Linux Enterprise source code have given The openSUSE Project a path forward for future releases.
-
Red Hat Family
-
Does technology really matter? Craig Muzilla, Red Hat, Inc. senior vice president, Applications Platforms Business, kicked off his keynotes at Red Hat Summit 2015 asking attendees that very question.
-
While there has been a lot of oooh-ing and ahhh-ing over what’s been coming out of the Red Hat Summit in Boston this week, probably the most intriguing news to come out of the proceedings is that Red Hat and Samsung Electronics America “announced a strategic alliance to deliver the next generation of mobile solutions for the enterprise,” according to Red Hat’s PR department.
-
Red Hat has ratcheted up its software defined storage portfolio, taking the wraps off Ceph Storage 1.3 and Gluster Storage 3.1 at its marquee customer event in Boston this week.
The vendor played up the ability of both products to help customers manage storage at “petabyte scale”. Which one matters most to you depends, of course, on exactly what you’re looking to do with your infrastructure in general, and storage in particular.
-
If Red Hat wasn’t a “container company” before, it’s one now — and in ways that matter to more than just admins dealing with Red Hat products.
Among the announcements the company put out this week at its annual Red Hat Summit, the two biggest were about Red Hat as a container (and, by that token, application) platform. Both expand on existing work Red Hat has done with containers, and both are aimed at app developers, rather than just those tasked with keeping installations of Red Hat products fed and happy.
-
RED HAT is continuing its slew of announcements from its Boston Summit with the reveal of a preview edition of Red Hat Enterprise Linux for ARM processors (RHELA).
-
-
-
-
-
-
-
-
-
-
-
Fedora
-
After proposing Frappe Web framework, two-week Fedora Atomic Host releases, system firmware updates for UEFI, default local DNS resolver, and SELinux policy store migration, Jan Kurik comes today, June 26, with the proposal of a Fedora Astronomy Spin.
-
-
Varnish is a high-performance HTTP accelerator, widely used over the Internet. To use varnish with https, it is often fronted by other general http/proxy servers like nginx or apache, though a more specific proxy-only high-performance tool would be preferable. So they looked at stud.
hitch is a fork of stud. The fork is maintained by the Varnish development team. stud seems abandoned by its creators, after the project was taken over by Google, with no new commits after 2012. The varnish developers have tried to contact the old stud upstream without success, so they forked and took up development again.
-
This is a post oriented to Fedora, Centos and RedHat distributions, although, most of the info is valid for any RPM distribution, with some minor differences
-
The Release Tools and Infrastructure Fedora Activity Day happened recently at the Red Hat office in Westford, Massachusetts. The goal was to bring our release tooling and processes up to speed with the current and future demands of the Fedora Project. Since there are a ton of moving parts of the Fedora Release Engineering community that need work, many of us split out into groups to tackle various components.
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
The Ubuntu Touch family has just received a new member, and the developers will need to take into account the fact that a new platform is out there, in the hands of regular users. It also means that a new code name is needed, and in this case it’s “arale.”
-
Canonical and Meizu have set up a rather complicated way of getting the new Meizu MX4 Ubuntu Edition, but it’s all done on purpose. Unfortunately, not everyone sees this and this has led to some strange conclusions and comments from the community.
-
On June 26, Canonical’s David Planella sent in his regular report to inform Ubuntu developers and users alike about the work done by Ubuntu Community Team in the week that passed.
-
-
Ubuntu is one of the most popular Linux distributions — arguably the most popular — which is very much deserved. Canonical has taken the complicated and intimidating world of Linux and transformed it into an inviting operating system for the masses. While not as user-friendly as Windows or OS X, Ubuntu is certainly easier to use than Fedora or the dreaded Arch.
-
Flavours and Variants
-
TheeMahn, the creator of the Ultimate Edition (formerly Ubuntu Ultimate) GNU/Linux operating system, announced a few days ago that testers are need to test the Beta release of the upcoming Ultimate Edition 4.7 release.
-
The first Alpha for Kubuntu 15.10 was made available yesterday, but the announcement itself was overshadowed by a worrying statement from the developers. It looks like the future of Kubuntu, in the greater Ubuntu family, is uncertain.
-
-
-
Marvell unveiled two new Kinoma IoT prototyping mini-PCs, including a “Kinoma HD” stick running Linux and the open source JavaScript 6 KinomaJS framework.
Marvell successfully launched its Linux-based $99 Kinoma Create JavaScript prototyping device on Indiegogo in March 2014, and sold it retail at $150. In March of this year, the company open sourced the KinomaJS JavaScript framework that runs on the Create, and now it has announced two new IoT-focused Kinoma devices — the FreeRTOS-based Kinoma Element and Linux-based Kinoma HD — with tempting pre-order price tags of $20 and $25, respectively. The devices ship in the fourth quarter.
-
96boards is an idea from Linaro to produce some 32 and 64-bit ARM boards. So far there were two boards released in “consumer” format and few more announced of rumoured. The specification also lists “extended” version which has space for some more components.
-
-
-
Phones
-
Android
-
The Google Play Store has come a long way since its humble beginnings. It’s no longer known solely for apps with viruses in them and illegal emulators—some of the best apps in the world live on the Google Play Store. We’ve put together a list of the apps that we think pretty much everyone needs to have on their Android devices.
-
That second-gen FLIR One thermal camera we saw earlier this year is now available for iPhones and iPads, with the Android version shipping in July. If the last time you’ve heard about it was back in 2014, this might come as a surprise, as the first-gen camera was embedded in an iPhone 5/5s case. This one is is a standalone accessory with a built-in battery that attaches to iOS devices via a Lightning connector and to Android phones and tablets via microUSB. It also has an updated thermal camera with four times the resolution of the one inside the first-gen cases.
-
-
If you own a smartwatch, put it to work! After all, there’s a fine line between wrist-worn gimmick and ever-accessible information machine. The difference is in the software. Here are some handy-dandy Android Wear apps to get you started.
-
To streamline Android development efforts, Google will focus on building tools for Android Studio. The company will also stop supporting other Integrated Development Environments (IDE) at the end of this year, like Eclipse.
-
The Verizon Motorola DROID Turbo is still running Android 4.4 KitKat nearly 8 months after it was announced, and the update to Android 5.1 Lollipop has been rumored for months. However, the past few weeks have been promising, and now it looks like Verizon and Motorola are finally ready to deliver the highly anticipated Android 5.1 update for the DROID Turbo.
-
-
-
-
-
The company is now readying a Kickstarter campaign for the Remix Mini, a small box much like a Chromebox that runs the Remix OS. It is aimed at those wanting a cheap system in a tiny form that becomes a desktop system with a monitor, keyboard, and mouse.
-
-
Recognizing successful open source projects need a variety of “developers” to create everything from code to community, the OSI Internship Program seeks participants from across academic disciplines–Business, Communications, Sociology, Informatics, and of course Computer Science to name a few–the program seeks to provide real life experiences common across open source projects and the communities that support them, giving students first hand experiences as well as opportunities to work with some of the most influential projects and people in open source software and the technology sector.
-
Events
-
The next (virtual) Ceph Developer Summit is coming.
-
Web Browsers
-
Chrome
-
New Chromium builds will no longer download/install the Hotword Shared Module and will automatically remove the module on startup if it was previously installed.
-
SaaS/Big Data
-
BlueData Software Inc., an infrastructure startup focused on Big Data, is working on solutions to the problem. The company recently announced that it is adding support for Docker containers on its BlueData EPIC platform. BlueData was founded by VMware veterans, and is focused on making Hadoop and Spark easy to deploy in a lightweight container environment.
-
BSD
-
If you use a free and open source operating system, it’s almost certainly based on the Linux kernel and GNU software. But these were not the first freely redistributable platforms, nor were they the most professional or widely commercialized. The Berkeley Software Distribution, or BSD, beat GNU/Linux on all of these counts. So why has BSD been consigned to the margins of the open source ecosystem, while GNU/Linux distributions rose to fantastic prominence? Read on for some historical perspective.
-
Notes and thoughts on various OpenBSD replacements and reductions. Existing functionality and programs are frequently rewritten and replaced for the sake of simplicity or security or whatever it is that OpenBSD is all about. This process has been going on for some time, of course, but some recent activity is worth highlighting.
-
Project Releases
-
Oz is a program for doing automated installation of guest operating systems with limited input from the user.
-
Public Services/Government
-
The government has played an important role as champion of open source in the public sector and this has been essential to the great progress that has been made to date. As the new government lays out its strategy, it should publicly reaffirm its commitment to open source software. This will add impetus to those in the public sector considering open source if the government acknowledges its value in relation to its agile vision.
-
Given the growing need for advanced databases with multiple levels of security to store geospatial intelligence, NRO contractor Lockheed Martin along with partners like Red Hat and Crunchy Data Solutions rolled out an open source relational database at a geospatial intelligence symposium in Washington this week that is billed as supporting multilevel security.
-
Openness/Sharing
-
Open Hardware
-
It’s an open source project designed for home use, and Felfil is an extruder for plastic 3D printing filament, designed by a team of young makers from the Politecnico of Turin.
They say the device was built in answer to a desire by users of 3D printers to produce their own plastic filament. It’s all about reducing the cost of printing, saving on materials, and being able to experience the potential of 3D printing.
-
Programming
-
With an uncharacteristic lack of fanfare, Google has decided to hang around the kitchen at the code repository party.
-
Literacy used to be the domain of scribes and priests. Then the world became more complicated and demanded that everyone read and write. Computing is also a form of literacy, but having it only understood by a priesthood of programmers is not going to be enough for our complex, online world. “Learn to code” has become a mantra for education at all ages. But after clearing away the hype, why do people need to learn to code? What does it get us exactly?
Not everyone needs to become a software engineer, but almost every office worker uses a laptop as a daily tool. Computers are such a huge productivity booster because they support a large market of programs and apps designed for these workers. But commercial and open source software have a “last mile” problem: that they don’t automate every conceivable task. There are still computing chores that require a lot of repetitive (and fairly mindless) typing and clicking. Even if you have an intern to push these tasks on, they’re tasks that require a human because there’s no software to automate it. These tasks are too small-scale or specific to your organization’s workflow for it to be economical for a software company to create a custom solution.
-
libnice, everyone’s favourite ICE networking library, is now mirrored on GitHub (and GitLab), to make contributing to it easier — just submit a pull request. The canonical git repository is still on freedesktop.org.
-
Security
-
Defence/Police/Secrecy/Aggression
-
Friday’s attacks in France, Tunisia and Kuwait came at roughly the same time, and days after the Islamic State terror group called for such operations during the Muslim holy month of Ramadan. But there was no immediate indication that they had been coordinated.
-
Privacy
-
The hated Care.data programme is one of four government IT projects progressing so poorly its delivery has been deemed “unachievable”, according to a government watchdog report.
The scheme has been flagged with the highest “red” risk rating by the Major Projects Authority, along with the NHS choices website, the Health and Social Care Network, and the Ministry of Justice’s National Offender Management Services ICT programme.
The scheme has encountered serious delays, following an outcry from the public who largely objected to the idea of their personal information being shared with world+dog without their consent.
So far, 700,000 individuals have requested to opt out of having their data shared with third parties. However, concerns have been raised that the Health and Social Care Information Centre has been unable to implement those objections.
-
Wikileaks has published some NSA SIGINT documents describing intercepted French government communications. This seems not be from the Snowden documents. It could be one of the other NSA leakers, or it could be someone else entirely.
As leaks go, this isn’t much. As I’ve said before, spying on foreign leaders is the kind of thing we want the NSA to do. I’m sure French Intelligence does the same to us.
-
Internet/Net Neutrality
-
Americans won big on net neutrality in February, when the FCC voted to adopt new rules that would allow it to rein in the abusive and discriminatory practices of big telecommunications operators, such as blocking or throttling of Internet data, and charging content providers for access to an Internet “fast lane.”
-
Intellectual Monopolies
-
Copyrights
-
It is the so called freedom of panorama, which of course has its roots in a beloved piece of EU legislation, the InfoSoc Directive, more specifically its Article 5(3(h). This provision allows Member States to introduce into their own national copyright laws an exception to the rights of reproduction, communication/making available to the public and distribution to allow “use of works, such as works of architecture or sculpture, made to be located permanently in public places”.
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, Microsoft, Windows at 11:21 am by Dr. Roy Schestowitz
“Our products just aren’t engineered for security.”
–Brian Valentine, Microsoft executive
Summary: Remarks on the recent revelations about code and communication interceptions targeting insecurity firms and Microsoft’s claim that ‘transparency’ alone would be enough to assure security
RECENT reports about state surveillance on anti-malware/virus software (which could not detect Stuxnet, for example, making this more like snake oil) have led to the claim that Microsoft Windows cannot be made secure, not even with additional ‘security’ software. “Security by obscurity” does not work when the state can see everything and also sponsors the world’s biggest (and best funded) cybercrime operations. Windows is simply not designed to be secure and security is not the goal as the underlying design serves to prove. As Pogson put it this week:
Given That Other OS is just about everywhere and is helpless without anti-malware software, the NSA and others have studied the anti-malware software to exploit it as a back door to TOOS… Ironic, isn’t it?
Microsoft and security don’t belong in the same sentence. As FOSS Force reminds us, this NSA ally with worst of spyware uses the “transparency centers” [1] sham that we wrote about earlier this month. They are replacing software freedom with “transparency” nonsense. They pretend that “transparency” somehow improves security. It doesn’t.
The only way to perpetually and universally verify (by audit) the security of software, or pressure its maker/distributor to pursue genuine security at all times, is to ensure the software is Free software. Microsoft’s longtime employee (on and off for years at a time) and occasional mole inside FOSS [1, 2, 3, 4] says that Free software has not won and even uses a picture of a pig to prove it or at least make his case (crass, but typical of him). Don’t let these people shape the consensus; after the NSA leaks a lot of semi-technical people can easily understand that Free software is the only way to go. Secrecy, like secret (proprietary) code, is as trustworthy as politicians. It’s time for proprietary software to go. Backbone infrastructure sure is heading towards Free software-only (as a matter of policy), as several consortia already serve to demonstrate. It’s going to be a harsh reality for Microsoft. █
Related/contextual items from the news:
-
Poor Microsoft. The beleaguered company just can’t catch a break. We’ve already told you about how Snowden’s revelations have forced the pride of Redmond to spend who knows how many millions opening two “transparency centers” to allow government IT experts to pore through source code to prove there’s no back doors baked into Windows or other Microsoft products. Trouble is, while its engineers have been busy plastering over all traces of old back doors, they’ve left a side door standing wide open, waiting to be exploited.
[...]
The spooks have been reverse engineering. They’ve been dismantling Karpersky’s software, searching for weaknesses. They’ve been mining sensitive data by monitoring the email chatter between Kaspersky client and server software. In other words, while IT security folks outside the U.S. have been keeping a wary eye on their Windows servers while trusting their antivirus to be a tool to help them secure the unsecurable…well, their antivirus software has been being a Trojan in the truly Homeric sense of the word.
[...]
In the meantime, Windows becomes less safe by the minute for corporations and governments hoping to keep private data private. I’m certain that Red Hat, SUSE, and even Ubuntu are taking advantage.
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 6:55 am by Dr. Roy Schestowitz
Corporations now run the European Patent Office (EPO)

Summary: The shameful management of the EPO, which Benoît Battistelli constructed based on his nefarious self-serving agenda, keeps pushing forth in a direction that greatly harms European citizens while mistreating the EPO’s technical staff (scientists and examiners)
THE EPO scandals continue and there is no denying that there is trouble when a huge proportion of the staff goes out to demonstrate right in front of the employer. Only a shameless liar would try to blame some “disgruntled employee” or “defamation”. The EPO, more so these days than ever before, is not a public service. It just sucks in public money. It is essentially a corporate entity masquerading as a public institution because it provides benefits like legal immunity, welfare (“too big to fail”), etc.
The EPO Administrative Council (AC), which has become Benoît Battistelli’s number one fan after some entryism, is trying to destroy the European industry with more patent monopolies and fees. According to patent lawyers’ media, Mr Kongstad’s office is at the forefront of this atrocious move:
The Select Committee of the EPO Administrative Council, which represents the 25 EU states expected to be covered by the Unitary Patent, adopted the so-called true top 4 proposal by a three-quarter majority yesterday.
One of the selling points of the planned Unitary Patent is that a single annual renewal fee payable to the EPO will maintain the right in the participating EU member states, meaning that national fees will no longer have to be paid.
The above says that the AC “represents the 25 EU states”, but in reality it seems to represent Battistelli and his rich friends, who want to become even richer.
The AC’s Kongstad is finding himself under fire again, this time from his own staff. SUEPO’s Web site says that “Ms Bergot, Principal Director of Human Resources of the EPO, has scheduled new meetings of the working group on “union recognition” between the administration and union officials. However, Mr Kongstad (Chairman of the Administrative Council) has still not reacted to the letter sent by SUEPO Central concerning the investigation of staff representatives and/or union executives during trilateral talks.
“Pending Mr Kongstad’s written answer, as also reiteratered in the Council meeting of 24/25 June 2015, SUEPO regrets it must decline the invitation at present. Of course, SUEPO is looking forward to developments making the resumption of meaningful discussions possible.”
SUEPO has this PDF reply letter, sent to Ms Bergot:
Dear Ms Bergot,
You have scheduled new meetings of the working group on “unions recognition” between the administration and union officials.
You must be aware of the letter sent by SUEPO Central to the Chairman of the Administrative Council, Mr Kongstad, which was made public on 10 June 2015 (*).
Pending Mr Kongstad’s written answer to our requests, as also reiteratered in the Council, we regret we must decline your invitation at present. Of course, we look forward to developments making the resumption of meaningful discussions possible.
Recall that Gilles Requena, the EPO’s Administrator (Presidential Office), is the spouse of Ms Bergot [PDF]. Bergot, the Principal Director of Human Resources, is clearly there because of connections, not skills. She’s far from the only such instance. Battistelli has quickly turned the EPO into an international laughing stock. It’s time to reclaim the EPO or reboot it. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 6:03 am by Dr. Roy Schestowitz

Contents
-
In a previous post I discussed how to introduce users to Linux, where the focus was on the software side of the conversation. This post is all about the hardware.
The reason I put hardware second is because if we can’t provide the user with the software they need there is no point in swapping out their hardware. Hardware is always a compromise, whereas software is not.
-
WOW. Fifteen years ago today I made the first post ever at LQ, introducing it to the world. 15 Years. I know I’ve said it before, but 5,354,618 posts later the site and community have exceeded my wildest expectations in every way. The community that has formed around LQ is simply amazing. The dedication that the members and mod team has shown is both inspiring and truly humbling. I’d like to once again thank each and every LQ member for their participation and feedback. While there is always room for improvement, that LQ has remained a friendly and welcoming place for new Linux members despite its size is a testament to the community. Reaching this milestone has served to energize and refocus my efforts on making sure the next fifteen years are even better than the first fifteen.
-
While part-time hobbyists do plenty of great work on GNU/Linux, most of the code thesedays comes from paid developers. So for our upcoming podcast, we want your opinions: which company does the most for Linux? You might argue that Red Hat or SUSE contribute the most with their patches and efforts to get Linux into enterprises, or you may say that Intel or Canonical are doing the best work.
-
Desktop
-
I don’t know how many of you out there are aware of a new TV series called Mr. Robot starting Rami Malek as a computer hacker that goes by the name of Elliot and uses Linux kernel-based operating systems to hack various entities.
-
-
Server
-
I have been writing this blog since 2012 and I have been asked a number of times by other bloggers why I still use Google’s Blogger service as opposed to a hosted WordPress site.
The truth is that I still very much see Everyday Linux User as a hobby. It isn’t a job and I am not actively trying to make money by doing it. I find the Blogger interface easy to use and the spam filters work quite well. I tried using WordPress a while back and it became quickly apparent that with more power came more responsibility as I spent more time trying to keep WordPress from being bombed by spammers than actually writing.
-
Kernel Space
-
Based on the native encryption support added to EXT4 with the Linux 4.1 kernel, Linux 4.2 is bringing encryption support to the F2FS file-system.
-
Ted Ts’o has sent in the big batch of EXT4 file-system updates for the Linux 4.2 kernel merge window.
Following EXT4 adding encryption support to Linux 4.1, there’s many fixes/clean-ups in Linux 4.2 for the new encryption code. Beyond sprucing up the EXT4 encryption code there’s many other cleanups and fixes, including some xfstest failures that have been taken care of.
-
The release of the Linux 4.1 kernel is more significant than most, and not only because it was designated as a long term stable (LTS) release, or that it included contributions from 1,539 developers, the most in in Linux history. The release improves Btrfs file-system support for massive servers, adds encryption support to the latest ext4 file system, and offers enhanced support for Chrome OS, RAID 5/6 storage, and ACPI power management on 64-bit ARM systems.
-
David Airlie has sent in the main DRM driver updates for the Linux 4.2 kernel. There’s a lot of open-source graphics driver work represented by this pull request, but sadly no Nouveau (open-source NVIDIA) changes were incorporated for Linux 4.2
-
-
Interested in starting a new career in IT? Linux is one of the hottest technologies in the market today, with tens of thousands of job openings, and salaries outpacing many other IT specialties. This presentation demonstrates the steps you should take to launch your career in Linux.
-
The Linux Foundation’s Core Infrastructure Initiative has selected three security-oriented projects to receive a total of $500,000 in funding.
-
Linux 4.1 was officially released by Linus Torvalds on June 21, marking the first major update to the Linux 4.0 kernel which first debuted in April.
-
Applications
-
Oracle announced just a few moments ago that the second RC (Release Candidate) version of the upcoming VirtualBox 5.0 open-source and cross-platform virtualization software was available for download and testing for all supported operating systems.
-
-
On June 25, Paul Davis from the Ardour project had the great pleasure of announcing the immediate availability for download of the Ardour 4.1 DAW (Digital Audio Workstation) software, a major release that adds new functionality and fixes bugs.
-
The Ardour project is pleased to announce the release of 4.1 with a great line-up of new features such as input gain control, Save As for projects, click-free changes to processor order and meter position, relative snapping, faster waveform rendering, Hi-DPI/Retina support and more! As usual, quite a few bugs have been mercilessly slayed. Encouragingly, we also have one of our longest ever contributor lists for this release.
-
The Mars release (v4.5) of Eclipse is now available as the tenth annual release train. Eclipse Mars brings many new features to this popular, cross-platform integrated development environment.
-
Proprietary
-
Today we have some great news for all you WhatsApp fans out there, as it appears that there’s now an unofficial desktop client for all mainstream operating systems, including GNU/Linux, Mac OS X, and Microsoft Windows.
-
CodeWeavers, the developer of the commercial and cross-platform CrossOver application that lets Linux and Mac users run Windows apps and games, wants to know on which Windows programs they should concentrate their efforts.
-
Instructionals/Technical
-
Games
-
This has been a long time coming, as the request for the Linux editor is very high on their voting system. This request has also been updated to state that it has been started.
-
Looks like an early birthday present is on its way to me, as the Terraria developers have officially stated Linux & Mac builds should be out in July.
-
The list of the most sold games on Steam for Linux is a very good tool to find out what the community is preferring and what they are playing right now. If something ends up on this rather exclusive list, then you know you’ll probably have a great time with it. Some of the games have been around for some time now, so we already know that they are good, but there are also a few new entries that should prove more than interesting.
-
LEGO Minifigures Online originally appeared on SteamDB back in March, but the developers Funcom said to us directly Linux wasn’t planned. Their official site, and SteamDB entry now officially mention Linux as a supported platform. Bring on the bricks.
-
Imagine you find yourself trapped in another world. You’re not entirely sure how you got there, other than that you tripped through a rift, more or less. Your surroundings are a mysterious mix of city ruins, wrecked pirate ships and space-ships from an unknown future. You seem to be trapped there, and to make matters worse, monstrous giants roam the land.
-
Looks like an early birthday present is on its way to me, as the Terraria developers have officially stated Linux & Mac builds should be out in July.
-
Just days after pushing out Dota 2 Reborn for Linux gamers, Valve has released a massive update to this Source Engine 2 game and it includes some driver/rendering fixes.
-
Valve developers have issued a new patch for Dota 2 Reborn, and it looks like they managed to fix some important problems, including the support for the AMD open source drivers.
-
Well I do love SteamDB, as it appears STAR WARS™ Knights of the Old Republic™ II – The Sith Lords™ has a Linux icon added, so it looks like the previous ESRB leak about a Linux version could be true after all.
-
Geometry Wars 3 has been out on Linux for a while now, but sadly it was left outdated for too long with issues. The update is out, so how is the game on Linux?
-
ARK: Survival Evolved sadly won’t hit the release date today for the Linux & Mac versions, but they sent word that it will release on Tuesday the 30th of June.
-
Desktop Environments/WMs
-
Cinnamon 2.6 has been officially released with many interesting changes and improvements. Cinnamon 2.6 will be used in Linux Mint 17.2 “Rafaela” that is planned to be released in end of June. In this article I’m going to review this release and tell you how you can install it on Ubuntu or derivatives. I hope you will like to use it. One more thing, when you use it please give your feedback.
-
K Desktop Environment/KDE SC/Qt
-
To be fair, Plasma is not the only desktop whose development has become cautious. The years 2008-2012 saw user revolts against major changes to GNOME and KDE, and a mediocre reception to the introduction of Unity. In the aftermath, the developers of desktop environments were left understandably nervous, and remain concerned about the pace of change.
Also, in the last few years, Plasma has been ported to the Qt5 framework, and much of it rewritten. This process was unavoidable, and seems to have resulted in greater responsiveness, although questions of speed are notoriously subjective in computer interfaces.
Yet at the same time that this process has happened, KDE as a community has done little to extend the concept of the desktop. The innovations that marked Plasma 4, such as Activities, tabbed windows, and desktop layout, have received only minor tweaks — the Activities window, for example, scrolls vertically in the latest Plasma releases instead of horizontally as in the first releases.
-
-
We are in good way to have a stable version for 15.08.
-
After several month of packaging in kde overlay and almost a month in tree, we have lifted the mask for KDE Plasma 5.3.1 today. If you want to test it out, some infos how to get it.
-
Jaroslaw Staniek, one of the developers of the Kexi open-source database creation tool distributed as part of the Calligra office suite for the acclaimed KDE desktop environment, has unveiled details about the development progress of Kexi 3.0.
-
GNOME Desktop/GTK
-
Carlos Garcia Campos had the pleasure of announcing the immediate availability for download and testing of a new snapshot towards the upcoming WebKitGTK+ 2.10 WebKit rendering engine for the GNOME desktop environment.
-
The GNOME Project will soon release the third milestone towards the GNOME 3.18 desktop environment, GNOME 3.17.3, which means that most of the core components have been updated in the last couple of days, including the GNOME Boxes virtual machine manager tool.
-
The GNOME developers are hard at work these days, preparing to unveil the third milestone towards the highly anticipated GNOME 3.18 desktop environment, which means that many of the core components received major updates, including GTK+.
-
The development of the next GNOME release, 3.17, is going on and a new snapshot, 3.17.3, is now available. Give it a shot! Some of us will gather in San Francisco next week for the West Coast Summit 2015, and a month later we will all gather for GUADEC in Gothenburg, Sweden (no relation whatsoever with a conspiracy that doesn’t even exist).
-
Since last blog post I have been designing and implementing a room menu for Polari.
-
Frederic Peters has just informed us about the immediate availability of the third snapshot for the upcoming GNOME 3.18 desktop environment, due for release on September 23, 2015.
-
-
This is the second in a series of posts about recent design work for GNOME’s core applications. As I said in my previous post, the designs for many of these applications have evolved considerably, and we have major plans for them. Help is needed if these plans are going to become a reality though, so we are looking for contributors to get involved.
-
-
MythTV is a free, Open-Source and a complete Home Media Center Hub also available for Linux. MythTV is capable to record videos. It is an alternative to Windows Media Center or Tivo. Personally I like MythTV very much. This tutorial will walk you through a quick look at the interesting features of MythTV and also How to install MythTV Latest version 0.27.5 on Ubuntu 15.05/14.10/14.04 or Linux Mint Rafaela/Rebecca or Other Ubuntu Derivatives.
-
Ballnux/SUSE
-
It has been around 10 days since the last update to opensuse Tumbleweed. That would have been snapshot 20150612. This is a brief note to explain the delays.
-
Red Hat Family
-
Red Hat had the great pleasure of announcing the availability of the first Development Preview of their upcoming Red Hat Enterprise Linux Server 7.1 for ARM operating system.
-
The way that DevOps can work in an enterprise organization is to first understand that innovation is de-centralized, with the best ideas coming from the best sources, wherever they might be.
It’s also important to have an open and collaborative culture in order to facilitate innovation and organizations need to be modular to be able to react to change.
-
Paul Cormier, Red Hat EVP and president of products and technologies, discusses two new products announced today at the Red Hat Summit.
-
Chris Wright, chief technologist for Red Hat, sat down with theCUBE cohosts Dave Vellante and Stu Miniman to discuss new developments in the open source world and NVF in telcom networks.
As the person who helps define Red Hat’s strategic vision, Wright has seen conversations shift from cost of ownership to innovation. “Today, there is a shift to operationalize complex systems,” he says. “There has been a change in open source technology from commoditization to a place where real innovation is happening, and new services are introduced quickly.”
-
RHEL 7.2 will also bring live kernel patching to RHEL, which Dumas sees as a critical security measure. Using elements of the KPATCH technology that recently landed in the upstream Linux 4.0 kernel, RHEL users will be able to patch their running kernels dynamically.
-
Yes, Red Hat is a Linux company. But, it’s more than that. Back in 2011, Red Hat CEO Jim Whitehurst told me the Platform-as-a-Service (PaaS) cloud would be Red Hat’s future. Today, at Red Hat Summit in Boston, Red Hat made it clear that it wants to be a cloud analytic powerhouse as well.
-
Red Hat hasn’t shirked with its latest product release in this vein and has labelled its most recent release the Red Hat Atomic Enterprise Platform.
-
Red Hat is adding features to its virtualization software to stay competitive, but is also worried about staying relevant as the industry moves to embrace cloud and containers.
-
-
This release of OpenShift, traditionally known to techies as a platform-as-a-service or PaaS, hits lots of buzzwords. First, it embraces the popular Docker container technology. That means a developer can, theoretically, build an application, test it, and run it in its own server room or on a variety of clouds. Second, it supports Kubernetes, an orchestration scheme backed by Google GOOG that promises to ease the placement and management of lots and lots of containers across environments.
-
Attendees went nuts on social media – displayed on the big screen at the Summit – as they awaited a keynote from Red Hat CEO Jim Whitehurst.
-
At its recent Summit, Red Hat announced that the preview version of its latest enterprise-class operating system (OS) was running on AppliedMicro’s 64-bit ARM server processors. At the event itself, HP had a live demonstration running on 10 X-Gene m400 cartridges in one of its ProLiant “Moonshot” servers. The demo was running Red Hat Development Preview Edition 7.1 and showing enterprise-class real-time data analytics. The key take away from the announcement and the demo is that ARM servers are available today and are fully capable of supporting enterprise-class data analytics workloads. This example system at the Summit showed a full functioning enterprise stack – including 64-bit ARM processors, the server platform, the Red Hat operating system, hypervisor, and Apache Spark applications. There is a “top-to-bottom” solution available for ARM.
-
Looking to establish itself as the leader in the nascent container technology market, Red Hat has enabled one of its flagship products to support containers fully and released a new container management platform, too.
Containers are a hot topic at the Red Hat Summit taking place this week in Boston, the same week the container industry is meeting in San Francisco for Dockercon, a conference dedicated to the operating system-level virtualization.
-
Red Hat thinks the 64-bit ARM architecture will be ready for the data center and cloud someday soon. The release of Red Hat Enterprise Linux Server for ARM (RHELA) to beta may be this year or early 2016.
-
Red Hat continues to make inroads into the enterprise storage software market, improving two of its core storage technologies and striking partnerships with key IT system resellers.
-
Red Hat have announced two new products at its Red Hat Summit event: OpenShift Enterprise 3 and Red Hat Atomic Enterprise. Both of these will both incorporate the Docker and Kubernetes projects, two hugely successful container projects.
-
-
-
Red Hat CEO Jim Whitehurst discusses how he considers potential acquisitions and where he might be looking for new companies.
-
Red Hat Ceph Storage and Red Hat Gluster Storage are open source, scale-out software-defined storage solutions that run on commodity hardware and have durable, programmable architectures. Validated to work with leading partner hardware and software solutions, each Red Hat Storage product is well-suited for different enterprise workloads, bringing compelling benefits to enterprises.
-
RED HAT has announced the release of OpenShift Enterprise (OSE) 3, a new version of its Platform-as-a-Service offering.
Based on Red Hat Enterprise Linux (RHEL)7, Openshift is built on Docker Linux containers with Kubernetes orchestration using technology developed in collaboration with Google.
-
Forget that software is eating the world. By now, it’s a foregone conclusion.
-
Equities researchers at Oppenheimer upped their target price on shares of Red Hat (NYSE:RHT) to $88.00 in a research report issued on Thursday. Oppenheimer’s price target indicates a potential upside of 12.07% from the stock’s previous close.
-
Wall Street analysts liked what they heard at Red Hat’s annual Analyst Day, which was held in Boston on Wednesday.
-
-
Cantor Fitzgerald reiterated its Buy rating and price objective of $90, following the Red Hat Summit and Analyst meeting
-
Red Hat has used its 2015 ‘Summit’ event in Boston to take the wraps off of JBoss Fuse 6.2 and Red Hat JBoss A-MQ 6.2 – with both products introducing new capabilities for developers working on enterprise application and messaging initiatives.
-
Red Hat has launched its Mobile Application Platform, at the company’s Summit under way in Boston.
The Mobile Application Platform consists of tools and templates for building mobile applications combined with back-end services to handle features including authentication, data, and integration with existing systems. It is based on FeedHenry, which Red Hat acquired in October 2014.
-
-
Developers traveling to Boston for the Red Hat Summit, one of the industry’s premier open source technology events, are in for a treat! They will get a sneak peek at some exciting new 64-bit ARM® development platforms featuring the AMD Opteron™ A1100 Series processor (codenamed “Seattle”).
-
Shortly after I joined Red Hat, we had nothing short of a revolution when organizational changes led to the content services teams being positioned alongside customer-facing roles such as technical support, account managers, and customer experience managers.
-
I’m probably one of the last people you want to comment on how to effectively lead and develop an organization. During my career, I twice held team lead positions. Both times I… well, I wasn’t a disaster, but I do feel I could have been more effective.
-
Fedora
-
Yet another feature being worked on for Fedora 23 is to make it easy to test cloud images locally from the Fedora Workstation/Server.
Currently this program only works on Fedora Linux and requires libvirt, libguestfs, and python-requests for supporting this local cloud testing. Testcloud makes it a one-step process for downloading, booting, and gaining access to a cloud image on your local system.
-
Since we use Fedora as the base for our distribution and thus follow the Fedora Project’s life cycle, it means that Korora 20 Peach reached it’s End Of Life status yesterday on June 23.
-
Korora Project has informed its users that the Korora 20 “Peach” Linux distribution reached EOL (End of Life) status on June 23, 2015, which means that it will no longer receive security patches and software updates.
-
I’d written about pdfpc earlier. I packaged it for Fedora and you can now install it directly using DNF. It’s still in the testing repositories, so you’ll need to enable the repository for the time being. I’m leaving the copr repository as it is, but please note that I will not update the packages there any more.
-
Kiara spoke about the importance of using Fedora on engineering careers. Then I shared the new features that Fedora 22 include. After that, we ate pizza.
I appreciate the work done by Luis Segundo and Universidad Tecnológica de Panamá coordinating the space.
-
-
I indent to discontinue and remove perl-Mail-GnuPG from Fedora.
-
Basically, it integrates with the vacation calendar of fedocal to show on the packager’s info page if the person is on vacations or not.
-
Release Candidate versions are available in remi-test repository for Fedora and Enterprise Linux (RHEL / CentOS) to allow more people to test them. They are only available as Software Collections, for a parallel installation, perfect solution for such tests.
-
Debian Family
-
Derivatives
-
Brewmaster is Valve’s codename for the next version of SteamOS currently available in a preview state. SteamOS Brewmaster is based on Debian 8.1 stable.
SteamOS Brewmaster is in an early preview state where Valve is soliciting the feedback of the gaming community. SteamOS Brewmaster is available in ISO and ZIP format and is the successor to SteamOS Alchemy. Brewmaster is powered by the Linux 3.18 LTS kernel with various SteamOS patches on top.
-
On June 25, Valve was more than happy to announce the immediate availability for download and testing of the first preview release of the next major version of its SteamOS Linux distribution, dubbed Brewmaster.
-
Canonical/Ubuntu
-
System76 teased all Ubuntu users with their brand-new Twitter campaign, which starts today, June 25, on Twitter, of course, as the well-known hardware company plans one of its biggest sales ever on July 4, 2015.
-
This week, Dustin Kirkland announced the Ubuntu Fan Project.
To steal from the description, “The Fan is not a software-defined network, and relies on neither distributed databases nor consensus protocols. Rather, routes are calculated deterministically and traffic carries no additional overhead beyond routine IP tunneling. Canonical engineers have already demonstrated The Fan operating at 5Gpbs between two Docker containers on separate hosts.”
-
In a recent email entitled “Getting ready for Python 3.5,” Canonical’s Barry Warsaw unveils the company’s plans for switching to the Python 3.5 dynamic programming language as the default Python 3 version in the upcoming Ubuntu 15.10 (Wily Werewolf) operating system, due for release on October 22, 2015.
-
Entroware is a UK-based company that specialized in selling hardware powered only by Linux operating systems. Proteus is the top-of-the-line laptop from Entroware, and it comes with either Ubuntu 15.04 or Ubuntu MATE 15.04.
-
After announcing the implementation of the Fan overlay network system in Ubuntu Linux, Canonical’s Ben Howard had the pleasure of introducing the first ever cloud images that contain the new technology.
-
-
Red Hat is dominating the headlines today with their announcements and related from the Red Hat Summit 2015, but several interesting tidbits appeared from other projects as well. Tumbleweed hasn’t been updated in quite a while, Neil Rickert knows why. Christine Hall reviewed Mageia 5 Monday and Dark Duck posted more screenshots today. Fedora and Korora 20s have reached their end of life and a new Ubuntu phone hits e-shelves.
-
Another Ubuntu phone, the Meizu MX4 Ubuntu Edition, has been made available in Europe – but you’ll have to jump through a few hoops to secure one.
Canonical finally delivered the first smartphone powered by the Linux-based Ubuntu OS earlier this year. It swiftly followed up on the launch of the BQ Aquarius E4.5 with news of a follow-up, the Aquaris E5 HD Ubuntu Edition, which will also be made by Spain’s BQ.
-
It’s only been a few weeks since Canonical unveiled a new Ubuntu phone, but the company is already back with another handset for the European market. This time the hardware comes from Chinese firm Meizu, packing a slick design and some pretty nice specs.
-
Canonical has announced that a few Tomcat vulnerabilities have been identified and corrected in its Ubuntu 15.04, Ubuntu 14.10, and Ubuntu 14.04 LTS operating systems.
-
Canonical published details about a couple of Python vulnerabilities that had been found and corrected in its Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS operating systems.
-
Canonical, through Adam Conrad, announced earlier the immediate availability for download and testing of the first Alpha versions for some of the official flavors of the upcoming Ubuntu 15.10 (Wily Werewolf) operating system.
-
Meizu announced yesterday that the new MX4 Ubuntu Edition smartphone would be made available on its website through a system of invites, and that system is now live. If you’re lucky enough, you might be able to buy one.
-
-
It has just been brought to our attention that there’s a video on YouTube where a guy shows us how easy (or hard) it is to install the Ubuntu 15.04 distribution on Microsoft’s Surface Pro 3 laptop.
-
-
Over the last few years, there have been several releases of mobile phones designed with open-source operating systems: Mozilla, Canonical, Samsung, and Jolla to name a few companies that have ventured into that industry. Their operating systems aim to break through the global dominance of Android and iOS — although Android has been their biggest challenge as phones based on it are the most popular in countries in which those companies have targeted customers. But none of these companies has been successful on a large scale; they have seen success with niche groups of customers, but nothing that can make a dent in Android’s global presence. Still, they haven’t thrown in the towel, and in some cases, have done quite the opposite.
-
-
After months of anticipation, the high-end Meizu MX4 Ubuntu Edition smartphone is going on sale—sort of.
-
The MX4 Ubuntu Edition will be available in Europe starting tomorrow, Canonical announced on the Ubuntu Insights blog, but will only be available to those who obtain an invite through an “interactive origami wall” on the Meizu website. The origami wall will be “filled with fun and interesting glimpses” of the latest Ubuntu phone, alongside the occasional randomly-generated invite.
-
Flavours and Variants
-
There is no doubt that Ubuntu MATE is slowly becoming one of the most used operating systems in the Ubuntu family and the Linux ecosystems as well, but it’s interesting to see that the Raspberry Pi version is one of the most downloaded.
-
Jonathan Riddell is no longer a member of the Kubuntu Community Council and the situation created by the Ubuntu Community Council, and the Kubuntu developers seems to have ended peacefully.
-
We reported earlier that the first Alpha releases of the upcoming Ubuntu 15.10 (Wily Werewolf) operating system are now available for download and testing, as announced by Canonical’s Adam Conrad.
-
-
Lubuntu is one of the Ubuntu flavors that participates in the Alpha 1 release of the upcoming Wily Werewolf (Ubuntu 15.10) operating system, so we took it for a quick test drive to discover what is new.
-
Attendees were treated to a peak into upcoming Red Hat Enterprise Linux 7.2 with Denise Dumas today during Red Hat Summit 2015. Elsewhere, Jonathan Riddell resigns his post at Kubuntu and Bodhi Linux founder Jeff Hoogland describes the four basic types of Open Source users. Lastly, Linux Voice wants to know which company does the most for Linux.
-
-
-
Today, June 24, the Ubuntu MATE team had the great pleasure of announcing that the Ubuntu MATE Boutique is now open for business and will offer you all sorts of interesting products.
-
-
Whether you want to keep an eye on devices on your home network or wish to monitor the performance of your website, the open source Nagios monitoring tool should be your first port of call. Although you’ll need a Linux box, the Nagios software is quick to install and straightforward to configure.
-
The Internet of Things is big marketplace and we keep hearing about companies like Intel, Dell, and Canonical who are trying to make some headway, but there are other competitors out there that are working just as hard and who are also using Linux as backbone, like Sierra Wireless for example.
-
Spire Payments’ new suite of Linux-based POS terminals (the SP range) continues to gain global acceptance by achieving Compass Plus approval for TranzWare system.
-
Arrow Electronics, Inc. (NYSE:ARW) today announced at the Freescale Technology Forum that it is now offering an open-source, specification-compliant board that is based on the new Freescale i.MX 7 microprocessor. Arrow also collaborated with Qualcomm Atheros Inc., a subsidiary of Qualcomm Incorporated, on the board’s Bluetooth & Wi-Fi capabilities and with Linear Technologies on the board’s power supply.
-
Phones
-
Tizen
-
The current “Tizen community” setup is transparently “community theater” rather than being a real community model.
-
Tizen’s architecture is appealing to both Web and Native developers alike. We have a Web API that allows app developers to create programs using HTML/CSS/JavaScript, and also a Native API that allows you to code in C / C++. Tizen is going to target a whole array of devices including TV’s, smart phones, watches, tablets, In-Vehicle Infotainment, and smart appliances.
-
The Schedule for the upcoming Tizen Developer Summit India 2015 in Bengaluru, India 30-31 July. This is a technical two day event aimed at application and platform developers that want to learn more about the Tizen Operating System (OS). There will be technical content for App developers, platform designers, ISVs, OEMs, hardware vendors, software vendors, open source enthusiasts, and anyone who wants to learn more about Tizen.
-
-
Android
-
-
There are a few big changes to the Google Play Music app in v6.0, but there are changes coming to your wearable too. There’s a new Android Wear companion app in there (v2.0), and with it comes real download management for music synced to the watch. Finally!
-
Kenwood today announced that its two aftermarket CarPlay and Android Auto systems unveiled at CES 2015 are now shipping to retailers with a suggested price of $900 to $950 each. The Kenwood DDX9702S and Kenwood Excelon DDX9902S are the only aftermarket units that allow drivers to switch between CarPlay and Android Auto without having to manually change settings or reset the unit.
-
-
-
As much as I wish the Apple Watch could do more, I find it the best smartwatch available, given its polished design and wide range of apps.
But there may be reasons to consider something else. For one thing, Apple Watch requires an iPhone. Pebble Time, in particular, works with both iPhones and Android devices and excels at battery life. But it falls short elsewhere.
-
-
-
-
The case that BlackBerry should give up development of its own platform and switch to using Android is one that never seems to lie down. One of the pioneers of the mobile phone industry, BlackBerry followed in the footsteps of the others – Nokia and Motorola – who helped shape the industry but unlike its peers, BlackBerry refuses to go down without a fight.
-
Amazon, following its monthly schedule, has made live a new Amazon Appstore for Android Free App of the Day Bundle, which features a total of 22 paid apps and games worth over $50 (roughly Rs. 3,150) available for free until Wednesday 11:59pm PDT (Thursday 12:29pm IST).
-
-
-
-
-
-
Medium made the announcement through a quirky blog post, explaining that the app went through a lot of testing before reaching the public.
-
We’ve never really been fans of skinning Android. Adding new features is fine, but OEMs try to “brand” the software by changing the colors and icons, which usually makes things look worse and really only serves to make things harder for new users. No OEM tries to “brand” the Windows UI—you can happily hop from one computer to another and all the icons and buttons will be the same. Similarly, on Android, when you hop from phone to tablet to watch to TV to car, if would be nice if all the designs and buttons on those devices looked the same.
-
Just over a week after LG said that it currently has no plans to update the G3 to Android 5.1 Lollipop, the company has given a similar heads-up about the G4 Android 5.1.1 update.
-
-
-
You might be forgiven for thinking that the Apple Watch is the only smartwatch worth buying. But watches running Android Wear are alive, kicking, and getting better.
-
Automakers like Chevrolet, Buick, and Hyundai have committed to offering Android Auto and Apple CarPlay connectivity in their production vehicles, but there’s still a big aftermarket community clamoring for smartphone functionality.
-
From the variety of devices and apps available to the near-endless array of customizations — everything from basic home screen arrangements to advanced tools that change how a phone or tablet is used — there’s practically no limit to the possibilities for making the operating system your own.
-
Like many walkers and runners, I like to do walks/runs with RunKeeper and Pandora. Before I got my Sony SmartWatch 3, if I needed to see the name of a song or my RunKeeper stats while I was running, I would need to dig my phone out of my pocket, press the button to activate it, unlock it, navigate to the appropriate app, try to see the data in the bright sunlight by cupping my hands over the screen, then re-lock the phone, and try to put it back in my pocket without accidentally unplugging my earbuds. Needless to say it tended to take me out of the zen of my run.
-
The open-source nature of Android means that you can run the mobile operating system on just about anything if you’ve got the know-how. Case in point: A YouTube user named Josh Max has managed to get it running on his Texas Instruments TI-Nspire CX. If that name conjures up images of middle school algebra exams, it’s because it’s a graphing calculator.
-
Today in our ongoing series of people putting one thing into another thing, we present Android running on a Texas Instruments TI-Nspire CX, a robust graphing calculator popular with the pre-calc set.
-
Over the last fifteen years, I’ve tailored most of what I do personally and professionally to the open source way. It puts the needs of others first in my life, and I love showing people how they can use a secure and stable operating system on new or aging hardware to accomplish all of their technology needs and desires. I’ve also seen the open source community grow and hundreds of new, and constantly improving, projects and products emerge. I’m a regular user of OpenOffice and LibreOffice. And, I use Firefox, Audacity, OpenShot, VirtualBox, WordPress, Drupal, Moodle, and more!
It’s been exciting to see open source software and the open source way arrive from the periphery to center stage.
-
Source code repository company GitHub today released version 1.0 of its Atom text editor for working with code.
Contributors to the Atom open-source project have made several improvements to the software in recent months, adding features like preview tabs, cutting down on memory usage for large files, making text more readable by default, and, of course, squashing bugs.
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Web Browsers
-
Chrome
-
Google has removed an extension from Chromium, the open source sibling to the Chrome browser, after accusations that the extension was installed surreptitiously and subsequently eavesdropped on Chromium users.
-
After including closed-source code that enabled Chromium to listen in to a computer’s microphone, Google bowed to backlash and removed it from the open-source browser.
-
Mozilla
-
We’re happy to announce the completion of the first release cycle after Rust 1.0: today we are releasing Rust 1.1 stable, as well as 1.2 beta.
Read on for details the releases, as well as some exciting new developments within the Rust community.
-
-
SaaS/Big Data
-
-
Mirantis, Inc. have announced the general availability of Mirantis OpenStack 6.1, which is based on the Juno release 2014.2.2 of OpenStack. The release is optimised to run on Ubuntu 14.04.1 and CentOS 6.5.
-
Databases
-
Crunchy Data Solutions, Inc. (Crunchy), a provider of enterprise PostgreSQL support, technology and training, today announced the release of Crunchy MLS PostgreSQL, an open source database distribution supporting multi-level security.
-
Oracle/Java/LibreOffice
-
Libreoffice is steadily nearing its 5.0.0 release moment. According to the release schedule, this is supposed to be unearthed somewhere early August. The source code for its first release candidate was made available a few days ago.
-
In LibreOffice 5.1 I’ve added an equalize width/height pair of adjustments to the “shapes” submenu when multiple objects are selected. Equalize Width and Equalize Height which adjusts the width/height of the selected objects to the width/height of the last selected object.
-
Business
-
So many companies fall prey to the idea that “If you build it, they will come” that it is refreshing to encounter a CEO who accepts the brutal reality of business, that no one cares, that nobody wants your product unless they are systematically convinced, that creating successful company goes far beyond building a technology product but actually involves building a business.
-
Funding
-
Redis Labs says a $15m funding injection announced today will help the NoSQL database firm expand sales and marketing, as well as step up its software engineering activities.
-
Project Releases
-
The wonderful developers behind Git, the world’s most popular open-source distributed version control system, were more than happy to announce the immediate availability for download of Git 2.4.5.
-
Openness/Sharing
-
In 2002, an article in the Washington Monthly explored a new trend called “open-source biology.” It asked, “Can a band of biologists who share data freely out-innovate corporate researchers?” The basic idea: Instead of squirreling away their research so no one else could use it, scientists would pool their findings.
[...]
But this week, researchers at the Defense Advanced Research Projects Agency’s “Biology Is Technology” conference have a reality check to share: Open-source scientific data is grossly underutilized and kind of a mess.
-
-
-
Open Hardware
-
Despite the involvement of the military and private companies, the robotics field has had a remarkably open ethos. With robots in their toddler stage, it has still proven worthwhile to share research and techniques widely. The Open Source Robotics Foundation are working to keep it that way, with an open ethic that might just shape our future with robots.
-
-
Programming
-
Google hasn’t announced it yet, but the company earlier this year started offering free beta access to Cloud Source Repositories, a new service for storing and editing code on the ever-expanding Google Cloud Platform.
-
BMW is bringing software back in-house so it can deliver seamless digital experiences for its customers – something more valued than horsepower or engines in today’s market, its digital business models lead said.
-
Science
-
Digital tape is about the hardest-to-kill storage IT there is, unless you count carving out data onto rocks, the way it was done hundreds of thousands of years ago. Tape technology celebrated its 63rd birthday on May 21; IBM first made available its IBM 726 Magnetic tape reader/recorder in 1952. Strangely, unlike later IBM tape drives, the original 726 could read tape backward and forward. Tape has managed to get better with age. When tape first went to market, the media itself weighed 935 pounds and held 2.3MB of data. In 2015, that much tape weighs closer to 12 pounds, and 2.3MB would comprise one large photo or a short pop song. Tape storage densities are broken regularly; IBM’s tape team recently demonstrated an areal recording density of 123 billion bits of uncompressed data per square inch on low-cost, particulate magnetic tape. The breakthrough represents the equivalent of a 220TB tape cartridge that could fit in the palm of your hand. Companies such as Iron Mountain, Spectra Logic, IBM and others maintain large installed bases of tape storage around the world. Here are some key facts about tape storage.
-
Security
-
Defence/Police/Secrecy/Aggression
-
When a white male kills people in a mass shooting in the US, the corporate media follow an algorithm not unlike the Kübler-Ross model of the five stages of grief.
First, media deny that the attack constitutes terrorism. In their view, acts of political violence carried out against civilians are indisputably terrorism when they are committed by a Muslim, but this is not necessarily the case when they are committed by a white person.
This is the stage in which most media coverage of shootings by white Americans remains stuck. When Elliot Rodger massacred six people and injured 14 more in May 2014, he was not classified as a terrorist–even though he explicitly stated that his attack was motivated by an intense hatred of women, and that he sought to “punish” women, collectively, for “rejecting” him in the past.
Yet because of mounting pressure and criticism from independent media, activists and social media, in the wake of mass shooting after mass shooting carried out disproportionately by white men, corporate media are no longer able to remain in a state of such denial.
-
The “surprise” is that more people are killed by “white supremacists, antigovernment fanatics and other non-Muslim extremists than by radical Muslims”: 48 vs. 26 since 9/11, according to a study by the New America Foundation. (More comprehensive studies cited in a recent New York Times op-ed–6/16/15–show an even greater gap, with 254 killed in far-right violence since 9/11, according to West Point’s Combating Terrorism Center, compared to 50 killed in jihadist-related terrorism.)
The Times suggests that “such numbers are new to the public”–but they won’t come as much of a surprise to those familiar with FAIR’s work. In articles like “More Terror, Less Coverage” (Extra!, 5/11) and “A Media Microscope on Islam-Linked Violence” (Extra!, 8/13), FAIR’s Steve Rendall has debunked the claim that terrorism is mostly or exclusively a Muslim phenomenon, pointing out that white, right-wing Christians are responsible for the bulk of political violence in the United States.
-
Transparency Reporting
-
Classified documents appear on WikiLeaks.org, revealing that the American government is spying on its allies. American officials rush to deal with a sudden diplomatic crisis while publicly refusing to comment on leaked materials. And WikiLeaks proclaims that it’s just getting started.
-
Environment/Energy/Wildlife
-
Every night, Donna Young goes to bed with her pistol, a .45 Taurus Judge with laser attachment. Last fall, she says, someone stole onto her ranch to poison her livestock, or tried to; happily, her son found the d-CON wrapper and dumped all the feed from the troughs. Strangers phoned the house to wish her dead or run out of town on a rail. Local nurses and doctors went them one better, she says, warning pregnant women that Young’s incompetence had killed babies and would surely kill theirs too, if given the chance.
[...]
Then there’s pollution of the eight-wheeled sort: untold truck trips to service each fracking site. Per a recent report from Colorado, it takes 1,400 truck trips just to frack a well — and many hundreds more to haul the wastewater away and dump it into evaporation ponds. That’s a lot of diesel soot per cubic foot of gas, all in the name of a “cleaner-burning” fuel, which is how the industry is labeling natural gas.
-
Finance
-
We are in the middle of the first great mass extinction since the end of the age of the dinosaurs.
That’s the conclusion of a shocking new study published Friday in a journal called Science Advances.
The study, which was conducted by a group of scientists from some of the United States’ leading universities, found that over the past century-plus, vertebrate species have gone extinct at a rate almost 114 times faster than average.
See more news and opinion from Thom Hartmann at Truthout here.
That’s right – not one, not two, not 50, but 114 times faster than average!
The study also found that as many 477 different vertebrate species have disappeared since 1900, a mind-boggling statistic because it usually takes between 800 to 10,000 years for that many species to disappear.
-
The U.S. Senate has paved the way for the passage of Fast Track legislation, to give the White House and the U.S. Trade Representative almost unilateral power to negotiate and finalize secret anti-user trade deals like the Trans-Pacific Partnership (TPP). Yesterday a “cloture” vote was held—this was a vote to end debate on Fast Track and break any possibility for a filibuster, and it passed by the minimum votes needed—60 to 37. Today, the Senate voted to pass the legislation itself. TPP proponents only needed 51 votes, a simple majority, to actually pass the bill, and they got it in a 60 to 38 vote. Following months and months of campaigning, Congress has ultimately caved to corporate demands to hand away its own constitutional mandate over trade, and the President is expected to the sign the bill into law as early as tonight or later this week.
-
he Senate voted Wednesday to approve fast-track authority, securing a big second-term legislative win for President Obama after a months-long struggle.
The 60-38 Senate vote capped weeks of fighting over the trade bill, which pitted Obama against most of his party — including Senate Democratic Leader Harry Reid (Nev.) and House Minority Leader Nancy Pelosi (D-Calif.).
Passage of the bill is also a big victory for GOP leaders in Congress, including Senate Majority Leader Mitch McConnell (R-Ky.) and Speaker John Boehner (R-Ohio). The Republican leaders worked closely with an administration they have more frequently opposed to nudge the trade bill over the goal line.
-
The government says it will delay or cut back a number of modernisation projects planned for Network Rail.
Transport Secretary Patrick McLoughlin says rising costs and missed targets make the £38.5bn plan untenable.
He blamed Network Rail, saying it should have foreseen the improvements would cost more and take longer.
Labour said it had warned the government needed to change how the railways were run but had “dithered” over taking action.
Network Rail said the plan, which was launched last year as the “largest modernisation of the railways since Victorian times”, was too ambitious.
Network Rail controls 2,500 stations as well as tracks, tunnels and level crossings.
-
Pope Francis’ much-anticipated climate change encyclical, released last week, is every bit as strong as environmentalists and other proponents of dramatic action on climate change had hoped. The pontiff affirms the scientific consensus that climate change is largely the result of human activity, calls for “urgent action” to develop renewable energy alternatives, and slams global development paradigms that create an “ecological debt” between the Global South and the wealthier North.
Many are predicting that the encyclical will be a game changer that will mobilize religious groups and galvanize lagging western nations, particularly the United States, to address climate change. And the encyclical will undoubtedly give the cause a huge moral push, especially at the upcoming international climate negotiations. But there are ominous warning signs already that a significant percentage of American Catholics — the very faith constituency that should be most receptive to the pope’s message — may turn a deaf ear to Francis. This means that not only are they unlikely to give up their SUVs, but also to support policies to address climate change or the candidates that back them.
-
Scott Walker is taking heat for claiming that supporting equal pay for women “pit[s] one group of Americans versus another.”
Here in Wisconsin, howls of laughter could be heard echoing through the marble walls of the state capitol: after all, this is a governor whose divisive approach has helped make his state one of the most bitterly polarized in the country.
-
PR/AstroTurf/Lobbying
-
This fact—that there are always young kids at Mondawmin (it’s a major transportation hub, and the only way thousands of kids can get home)—is erased entirely from the equation. The use of the term “juveniles” is meant to prejudice the reader and criminalize otherwise legal and peaceful assembly. From the beginning of the Baltimore Uprising, in other words, it’s been evident the Baltimore Police Department was far more interested in manipulating the press and hyping the threat than they were protecting First Amendment activity and people’s property.
-
Censorship
-
Privacy
-
Dropbox made itself a household name by giving away cloud storage. The eight-year-old company, valued at $10 billion, had 300 million registered users a year ago; now it’s got 400 million. Its two-year-old effort to make money from business users has been less impressive. While Dropbox led the $904 million global market for business file-sharing last year with about a 24 percent share, No. 2 Box and No. 3 Microsoft each took about 21 percent and doubled their slice of the pie, growing almost twice as fast, according to researcher IDC.
-
Poor Microsoft. The beleaguered company just can’t catch a break. We’ve already told you about how Snowden’s revelations have forced the pride of Redmond to spend who knows how many millions opening two “transparency centers” to allow government IT experts to pore through source code to prove there’s no back doors baked into Windows or other Microsoft products. Trouble is, while its engineers have been busy plastering over all traces of old back doors, they’ve left a side door standing wide open, waiting to be exploited.
[...]
The spooks have been reverse engineering. They’ve been dismantling Karpersky’s software, searching for weaknesses. They’ve been mining sensitive data by monitoring the email chatter between Kaspersky client and server software. In other words, while IT security folks outside the U.S. have been keeping a wary eye on their Windows servers while trusting their antivirus to be a tool to help them secure the unsecurable…well, their antivirus software has been being a Trojan in the truly Homeric sense of the word.
[...]
In the meantime, Windows becomes less safe by the minute for corporations and governments hoping to keep private data private. I’m certain that Red Hat, SUSE, and even Ubuntu are taking advantage.
-
-
On the 16 of June, Ministers in the Justice Council have sealed a general approach on the Commission proposal on the Data Protection Regulation. Modern, harmonised data protection rules will contribute to making Europe fit for the digital age and are a step forward to the EU Digital Single Market. Trilogue negotiations with the Parliament and the Council will start in June; the shared ambition is to reach a final agreement by the end of 2015.
-
La Quadrature du Net, French Data Network and the FDN Federation are publishing an essay to accompany their legal action before the French Constitutional Court against the French Surveillance Bill. The three associations, opposed to the French Surveillance Bill since its introduction in the Council of Ministers on 19 March, continue their mobilisation against this unjust law, in spite of its adoption in the National Assembly1 and the Senate2. Citizens are invited to support this approach by sharing and commenting on this essay by Thursday 7am to bring their thoughts or suggestions for improvement before sending it to the Constitutional Council.
-
Would you change what you said on the phone, if you knew someone malicious was listening? Whether or not you view the NSA as malicious, I imagine that after reading the NSA coverage on Linux Journal, some of you found yourselves modifying your behavior. The same thing happened to me when I started deploying servers into a public cloud (EC2 in my case).
Although I always have tried to build secure environments, EC2 presents a number of additional challenges both to your fault-tolerance systems and your overall security. Deploying a server on EC2 is like dropping it out of a helicopter behind enemy lines without so much as an IP address.
In this article, I discuss some of the techniques I use to secure servers when they are in hostile territory. Although some of these techniques are specific to EC2, most are adaptable to just about any environment.
-
Civil Rights
-
The French proposal would grant for-profit arbitrators, working in a system that creates perverse incentives, vast discretionary powers. This creates a serious risk on expansionist interpretations. Foreign investors would be able to use this biased system to challenge governments. As it is practically impossible to withdraw from trade agreements, the EU would be locked in.
-
Internet/Net Neutrality
-
BT is calling on the communications watchdog to let it scrap the traditional telephone network, as part of a campaign to loosen regulations that it says will help telecoms companies compete better with US internet companies such as Apple and Facebook.
The telecoms giant is planning to move all domestic and business customers to internet-based voice calls within a decade, but under current Ofcom rules must continue to provide a traditional phone service.
-
Study finds significant degradations of networks for five largest ISPs, including AT&T and Time Warner, representing 75% of all wireline households in US
-
Intellectual Monopolies
-
Copyrights
-
Cox Communications, one of the largest Internet providers in the United States, has asked the court to order anti-piracy firm Rightscorp to hand over its tracking source code. The ISP describes the company’s settlement scheme as extortion and hopes to punch a hole in its evidence gathering techniques.
Permalink
 Send this to a friend
Send this to a friend
06.25.15
Posted in Europe, Patents at 7:01 am by Dr. Roy Schestowitz
Summary: Earliest coverage of yesterday’s protest against EPO corruption and abuses
THE EPO — like Microsoft — spies on people for business reasons, not for security reasons. Staff of the EPO decided to protest again, as we wrote earlier this week, and Microsoft Florian was there to document it.
Florian Müller, who used to lobby against software patents before defecting (Microsoft and other companies paid him for this), was there at the scene to cover the protest. “Yesterday,” he wrote early this morning, “the Staff Union of the European Patent Office (SUEPO) held a demonstration in front of the EPO’s main building in Munich. While there have already been various other SUEPO demonstrations in Munich, a couple of which I reported on, yesterday’s protest had a new (though not exclusive) focus: surveillance by means of hidden cameras and keyloggers. Participants in the demonstration carried signs showing surveillance cameras…”
There is an estimate of the number of staff in attendance. “It appears credible to me,” he said, that “approximately 1,000 EPO employees participated — a fairly high percentage of all Munich-based EPO staff.”
There are some photos there to prove it (without people’s faces, obviously for their own protection, knowing Benoît Battistelli’s modus operandi).
Separately, the London-based patent lawyers’ blog IP Kat warns us of the threat of UPC looming over the UK:
But first, a digression, which may be of more general interest than the specifics of the particular consultation. The IPKat, ever eager to seek news for his dear readers, took the opportunity to ask whether there was any truth in the speculation that has appeared repeatedly in comments on this blog and elsewhere that the current UK Government might delay ratification of the UPC Agreement until after the UK Referendum on membership of the EU, which is not scheduled until 2017. The Intellectual Property Office, as it turns out, has an answer prepared for this question, and the IPKat is delighted to share it with you.
The horrible UPC (making patents even worse and more wide-reaching) is trying to creep into Europe as quickly as possible (while the public is mostly asleep). The EPO is largely responsible for this and more scrutiny is needed. It’s similar to those awful ‘trade’ agreements, but awareness among the public is severely lacking. █
“Staff at the European Patent Office went on strike accusing the organization of corruption: specifically, stretching the standards for patents in order to make more money.
“One of the ways that the EPO has done this is by issuing software patents in defiance of the treaty that set it up.”
–Richard Stallman
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft, Security, Windows at 5:28 am by Dr. Roy Schestowitz
Turning the alphabet into a security nightmare

Summary: Windows userbase is once again under serious threat and high risk because something as simple as fonts (rendering of text/pixels on the screen) isn’t done securely in Windows
THERE IS plenty evidence which shows that Microsoft is not interested in security, maybe because there are commitments to the NSA (the motivations are hard to reason about, but Microsoft’s reluctant to patch known holes is easily demonstrable).
Now we are being reminded that even fonts are a security risk in Windows. Yes, Microsoft continues to put users under remote execution threat because of fonts. As the British media put it:
Get patching: Google Project Zero hacker Mateusz Jurczyk has dropped 15 remote code execution vulnerabilities, including a single devastating hack against Adobe Reader and Windows he reckons beats all exploit defences.
The accomplished offensive security researcher (@j00ru) presented findings at the Recon security conference this month under the title One font vulnerability to rule them all: A story of cross-software ownage, shared codebases and advanced exploitation [PDF ] without much fanfare and published a video demonstration of the exploit overnight.
As one commenter (found by Robert Pogson) put it, “Adobe (and I guess MS as well) put font handling in the kernel from NT 4.0 to gain speed at the expense of having privileged-based protection, and against Dave Cutler’s original micro kernel plans. What could possibly go wrong?”
Proprietary software is so bad that even fonts are a huge risk. This isn’t the first such incident. It serves also as a reminder for GNU/Linux users because some users continues to install proprietary software from Adobe, despite Free/libre alternatives being equally potent.
To quote the part which shows why Windows makes things even worse: “The nastiest vulnerabilities for 32-bit (CVE-2015-3052) and 64-bit (CVE-2015-0093) systems exist in the Adobe Type Manager Font Driver (ATMFD.dll) module which has supported Type 1 and Type 2 fonts in the Windows kernel since Windows NT 4.0.” █
“Our products just aren’t engineered for security.”
–Brian Valentine, Microsoft executive
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft at 5:13 am by Dr. Roy Schestowitz
Ghostwriting and PR disguised as ‘news’

Summary: Signs serve to indicate that Microsoft is already tightening its grip on technology news sites, ensuring that they give Microsoft disproportionate levels of coverage
“Welcome to the Microsoft Slashdot,” wrote a reader to us, alluding to the recent bias (more extreme than before) of that once-upon-a-time-decent news site. This reader is obviously concerned about Slashdot AstroTurfing, especially after what we saw recently, in part because of Microsoft Nick, who had joined as "Senior Editor".
We are already seeing puff pieces about Vista 10, basically Microsoft marketing framed as ‘news’. Microsoft AstroTurfing must have officially begun for Windows, for several sites such as Ars Technica UK (launched with aid from Microsoft ads, conditional upon them appearing in every page and editors thus unable to fearlessly criticise Microsoft), Slashdot, and The Register are truly stuffed.
“Microsoft is now trying to save its biggest cash cow by making Android essentially a Microsoft Office platform.”“Currently on the Slashdot front page,” wrote the reader, “9 mentions of Microsoft and 11 mentions of Windows. They’re getting almost as bad as the Register and this (arstechnica.co.uk) shower. It’s all fake adverts being pushed by a Microsoft still desperately trying to be relevant. [At] arstechnica.co.uk 8 mentions of Windows and 4 mentions of Microsoft…”
Microsoft is a company that shrinks (with layoffs), but it doesn’t mean it can no longer control the media through its extensive network of unethical PR agencies (Microsoft has copywriters). Over time Microsoft may be less able to bribe officials, journalists and hire/commission assault teams (euphemistically called "compete teams" because they are inherently anti-competitive). It’s going to be increasingly hard or challenging because the budget is smaller. Microsoft fired many of its marketing staff last year. Nevertheless, we need to keep watching. Microsoft is a master of manipulation of the media. It has decades of experience and it has no ethical constraints, as we have demonstrated over the years.
Microsoft is now trying to save its biggest cash cow by making Android essentially a Office Microsoft platform. Data is being transmitted to Microsoft, but does anyone care? Even Linux sites carry water for Microsoft right now (regarding Android), not just Microsoft media moles (former staff) like Sarah Perez at AOL (seeding further coverage). Don’t think that Microsoft isn’t playing dirty games behind the scenes to make it so. █
“Working behind the scenes to orchestrate “independent” praise of our technology, and damnation of the enemy’s, is a key evangelism function during the Slog.”
–Microsoft, internal document [PDF]
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA