07.22.16
Posted in America, Europe, Patents at 7:28 am by Dr. Roy Schestowitz
“Patent monopolies are believed to drive innovation but they actually impede the pace of science and innovation, Stiglitz said. The current “patent thicket,” in which anyone who writes a successful software programme is sued for alleged patent infringement, highlights the current IP system’s failure to encourage innovation, he said.”
–IP Watch on Professor Joseph Stiglitz
Summary: Various bits and pieces of news regarding patents and their fast-changing nature in the United States nowadays
AS WE wish to resume our EPO coverage (there is a lot more material on the way), we have decided to lump together various bits of news from the (primarily US) patent system, subdivided below and split into themes.
BlackBerry Still Dangerous
When Canadian powerhouse BlackBerry introduced not only one but several Android-based phones were were rather relieved, as at one point several years ago it seemed like BlackBerry was slowly transforming to become a patent troll or preparing to sell its very many patents to notorious trolls (or patent assertion firms/entities, PAEs for short). BlackBerry, which is still struggling based on the number of sales, may somehow be bound to become like a patent troll, judging by this new report which makes the company (now run by a Turbolinux executive who previously sold out to Microsoft on the patent front) sound like a PAE. “He also hinted at a future based around brand and technology licensing,” says the summary. Watch out for BlackBerry because if Android doesn’t give it the success it is looking for, then BlackBerry might simply choose to sue Android OEMs (directly or indirectly, like Ericsson and Nokia). They can always try to blame such aggression on “shareholders!”
China Comes Knocking, Not Knockoffs
“Watch out for BlackBerry because if Android doesn’t give it the success it is looking for, then BlackBerry might simply choose to sue Android OEMs (directly or indirectly, like Ericsson and Nokia).”Yesterday my wife and I had lunch with a businessman who is a distributor of goods from Hong Kong, Taiwan and the Philippines. He warned about Chinese protectionism via SIPO and spoke about unusual restrictions, such as the imperative registration (can take about a year) in order to proceed to the simplest of enforcement inside China (even purely defensive enforcement in the face of counterfeiting or cheap imitations).
Put old stigmas aside for a moment. China is not stupid. China is also more than an imitator. It actually brings out some innovations these days and it is willing to go abroad to sue Western rivals. It’s not just on the defensive and increasingly it’s on the offensive. “Knocking out Chinese patents may be a lot harder than you think,” IAM wrote the other day and Dr. Glyn Moody, citing his colleague (article from 6 years ago), says “Just As We Warned: A Chinese Tech Giant Goes On The Patent Attack — In East Texas”. So, how is it working out for multinational US companies which relied so much on the USPTO and faithfully (or blindly) trusted it for protectionism? “Techdirt,” Moody explains, “has been warning for years that the West’s repeated demands for China to “respect” patents could backfire badly. In 2010 [before Moody wrote for Techdirt], Mike [Techdirt founder] pointed out that Chinese companies were starting to amass huge patent portfolios, which were soon used as weapons against foreign firms operating in China, most notably Apple.”
“China is not stupid. China is also more than an imitator. It actually brings out some innovations these days and it is willing to go abroad to sue Western rivals.”Based on articles like this new one, not only Huawei is suing; it is also being sued, this time by Samsung (from Korea). Samsung and Huawei have become top Android OEMs and there is a lot of money at stake when people pay up to $1,000 per phone. IAM seems to have taken an interest in many east Asian markets recently; one new article is titled “Korea’s antitrust watchdog hints Qualcomm can expect another near $1b fine in patent probe” and another is titled “Transpacific denied Enfish lifeline as Taiwanese companies’ NPE experiment hangs in the balance”. These are IAM’s latest attempts to float software patents because of an old patent case involving Microsoft. To quote: “Sensing a glimmer of hope from the US Federal Circuit’s judgment in Enfish v Microsoft – which went some way towards clawing back patent eligibility for software inventions in the aftermath of the US Supreme Court’s ruling in Alice – Kinglite filed a motion asking that the Central California court to reconsider its decision on the invalidity of the ‘304 patent. However, this was rejected on the basis that Kinglite’s patent does not “disclose any of those mathematical algorithms that actually represent an application of the ‘abstract’ idea of securing the BIOS through authentication, nor a new concrete means of applying those algorithms… [unlike] the patent in Enfish which apparently disclosed a new method of building a database”.”
Enfish does not really change much, but IAM would use anything it can to promote the interests of its paymasters, often unproductive (or counterproductive) patent parasites like this one it has just written about.
USPTO Wants ‘Certainty’
“Samsung and Huawei have become top Android OEMs and there is a lot of money at stake when people pay up to $1,000 per phone.”Certainty (or contrariwise, uncertainty) has become one of those buzzwords that David Kappos and fellow patent maximalists (especially proponents of software patents) use to say that Alice is nasty and needs to be buried. Two more articles have been published about the efforts to trigger changes with a new memorandum [1, 2]. The latter says: “The extent to which these disparate analyses can be reconciled will depend, of course, on future case law, leaving the question of subject matter eligibility in its current state of uncertainty.”
When the author (patent maximalist who shamed even a SOCTUS Justice) says “leaving the question of subject matter eligibility in its current state of uncertainty” the simplest translation is “leaving the question of subject matter eligibility in its current state of denying software patents.”
This is a subject which was mentioned here the other day, especially in relation to IBM.
Dying Software Patents
“Certainty (or contrariwise, uncertainty) has become one of those buzzwords that David Kappos and fellow patent maximalists (especially proponents of software patents) use to say that Alice is nasty and needs to be buried.”Upon reassessment most software patents are invalidated these days. There are some exceptions like the BASCOM case and patent lawyers love latching onto those. An article from Jason Rantanen (Patently-O) is an example of this bias among professors as well. He wrote: “Since Alice v. CLS Bank, the Federal Circuit has issued four opinions rejecting a lack of patent eligible subject matter challenge: DDR Holdings, LLC v. Hotels.com, L.P., 773 F.3d 1245 (Fed. Cir. 2014); Enfish LLC v. Microsoft Corp., 2016 WL 2756255 (Fed. Cir. May 12, 2016); Rapid Litigation Management Ltd. v. Cellzdirect, Inc., 2016 WL 3606624 (Fed. Cir. 2016), and BASCOM v. AT&T, with the latter three coming the last few months.”
Well, still, those are clearly in the minority and they come from a crooked court which is responsible for bringing software patents to the US in the first place.
Another software patent has in fact just died, thanks to Alice again. Patent Buddy wrote that “PTAB Holds Lottery Patent Claims Invalid under 101/ Alice: http://assets.law360news.com/0819000/819445/cbm2015-00105_termination_decision_document_36.pdf …”
“Another software patent has in fact just died, thanks to Alice again.”PTAB is very much dedicated to elimination of such patents because it has no incentive to empower plaintiffs, unlike CAFC. The US needs a lot less of CAFC (or anything like CAFC) and more of PTAB. Don’t be misled by all those spinners who equate PTAB with “death squads”. Patent law firms, for instance, still conveniently cherry-pick cases that support software patents (see “Another Software Patent Survives an Alice Challenge” by Seyfarth Shaw LLP). They put “abstract idea” in quotes (probably scare quotes, depending on style) and even add the word “alleged”, certainly not hiding their bias too well. To quote this latest ‘analysis’ (marketing): “In a rather complex case, Yodlee again focused on the definition of the “abstract idea” by the defendant. Many times, defendants frame the alleged “abstract idea” too broadly to improve their 101 invalidity argument, and courts or the PTAB find the definition is too broad. Other times, defendants frame the abstract idea too narrowly and courts agree with the defendant on the definition of the invention, but find such a narrow definition to not be drawn to an abstract idea. Here, the defendant framed the abstract idea in a manner inconsistent with the claimed invention, and the court found no apples to apples comparison.”
Improving Patent Quality
In our previous post we praised the USPTO (or PTAB by extension) for at least working to improve patent quality somewhat. Professor Crouch says that a new U.S. Government Accountability Office (U.S. GAO) report alluded to patent quality. “Patent Office Must Define and Improve Patent Quality” says the headline and the body of the short article says: “Regarding patent quality, the GAO suggested that the USPTO’s standard of patent quality should focus solely on the basics: defining “a quality patent as one that would meet the statutory requirements for novelty and clarity, among others, and would be upheld if challenged in a lawsuit or other proceeding.” However, patent clarity must be an important element of that definition.”
“For those who don’t know it yet, when IAM precedes something with “REPORT” it’s actually a euphemism for “SPONSORED CONTENT” or “ADVERTISING” (disguised as analysis by some particular firm).”This is good news. Compare that to propaganda sites like IAM where there is a new “REPORT” (i.e. paid-for marketing placement for a firm) titled “International report – Federal Circuit distinguishes between tests for obviousness and patent-eligible subject matter”. For those who don’t know it yet, when IAM precedes something with “REPORT” it’s actually a euphemism for “SPONSORED CONTENT” or “ADVERTISING” (disguised as analysis by some particular firm).
GAO’s input basically says that the Office must tighten patent scope, whereas the latter (propaganda/marketing) offers ‘tricks’ for getting around scope restrictions.
Using Taxpayers’ Money for Patent Stockpiling
“GAO’s input basically says that the Office must tighten patent scope, whereas the latter (propaganda/marketing) offers ‘tricks’ for getting around scope restrictions.”We quite liked IP Watch‘s article “Patenting By Universities Unhelpful, Paper Says; WIPO Programme To Be Reviewed” [1]. It was published a few days ago, just in time for IAM’s ‘report’ on Harvard University’s use of patents (granted using public money) to sue the private sector. IAM wrote: “Late last month Harvard University took the very unusual step of filing two infringement lawsuits against semiconductor manufacturers Micron and Global Foundries over their alleged infringement of two patents that are owned by the Ivy League institution. That in itself is a pretty rare occurrence – combing the Lex Machina database I found that Harvard has been a co-plaintiff on just one other patent suit since 2011, so it seems that this is the only case in at least the last five years that it has been the sole plaintiff in an action.”
This isn’t the first time that we write about universities getting aggressive with patents, not just selling patents to trolls who become aggressive with these (like Intellectual Ventures). What they do here is extremely unethical and should be grounds or basis for revocation of government grants. When universities are becoming like patent trolls (not producing but suing) it’s worse than classic patent trolls because taxpayers fund it and get punished for it, usually for the enrichment of some shady people.
“When universities are becoming like patent trolls (not producing but suing) it’s worse than classic patent trolls because taxpayers fund it and get punished for it, usually for the enrichment of some shady people.”In other IAM propaganda this week, watch this spin on patent litigation decline in the US. So patent trolls, which rely on software patents more than most (and pay IAM), lose momentum. A cause for celebration or for sobbing? Probably for sobbing at IAM. Bezos-owned news site Washington Post meanwhile reports, somewhat contradictorily (in light of the latest figures from Lex Machina), that “Patent lawsuits swell and watchdog says the government is to blame” (they actually decreased year-to-year in the past few months). To quote:
Inventors are filing an exploding number of lawsuits against companies that appropriate their products illegally — and a new report puts the blame for these costly disputes squarely at the feet of the federal government.
The U.S. Patent and Trademark Office is so focused on rewarding its employees for the number of applications they review that the quality of patents they give out is in jeopardy, according to the Government Accountability Office.
The result is that licenses conferring someone’s sole right to an invention are “unclear and overly broad” and vulnerable to infringement by competitors.
“Software patents are not legal in Europe, but the likes of Battistelli don’t obey the rules anyway and more attempts to interject software patents into Europe are made by those who could not care less.”Here again we have GAO saying what it has been saying for quite some time. Will anyone listen? Will the advice be taken seriously? See what happened after an Australian (almost) equivalent had said something to the same effect. Local patent law firms got rather aggressive.
Software Patenting in Europe Still Being Attempted
Software patents are not legal in Europe, but the likes of Battistelli don’t obey the rules anyway and more attempts to interject software patents into Europe are made by those who could not care less. According to this article, there’s a Dutch dispute over a patented “superformula” (i.e. algorithm). As the author correctly notes: “Despite the noise being made by Genicap, there’s some question as to whether the company’s patent actually applies to No Man’s Sky. The European Patent Convention says directly that “discoveries, scientific theories, and mathematical methods” are not directly patentable, and US patent law also excepts “disembodied mathematical algorithms and formula” from patentability.”
“The Dutch people don’t need software patents; they’re usually just victims of such patents.”Well, such patents oughtn’t exist in the first place. The last time we heard of software patents in relation to the Netherlands it was Microsoft’s lawsuit against TomTom (Dutch company) and a Dutch developer who had his work killed [1, 2, 3] by a patent aggressor, Shazam. The Dutch people don’t need software patents; they’re usually just victims of such patents. █
Related/contextual items from the news:
-
A new publication analysing the relationship between intellectual property and access to science explores ways countries have developed to counter the potential barriers created by IP rights, and says patenting by universities is counterproductive.
Permalink
 Send this to a friend
Send this to a friend
Posted in America, Europe, Patents at 5:32 am by Dr. Roy Schestowitz
The pendency at the USPTO stands at around five years, as scrutiny has been increased
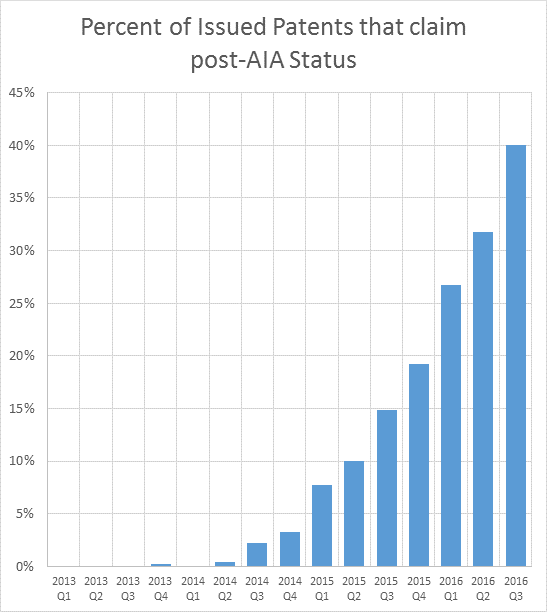
Image credit: Professor Dennis Crouch, Patently-O
Summary: While the EPO reportedly strives to eliminate pendency and appeal windows altogether (rubberstamping being optimal performance as per the yardstick du jour), the USPTO introduces changes that would strengthen the system and shield innovation, not protect the business model of serial litigants
PATENT systems across the world vary, but they’re streamlined/unified by various programs which enable litigation across nations and entire continents. We’ve covered some of these programs here before and half a decade ago we wrote numerous articles about the vision of a global patent system, at times citing leaked diplomatic cables that had been published by Wikileaks. ‘National’ patent offices are actually not so national and the ‘European’ Patent Office isn’t really about Europe (some of its member states, for example, are not in Europe). The same is true in the UK-IPO, which is going ‘to bed’ with Facebook right now (surveillance, censorship and propaganda site from another continent). Here is a new MIP article on patent litigation trends in Russia. It’s not often that we hear about Russian plaintiffs in European, Australian or American courts; domestic policy there probably does not incentivise pursuing patents in other countries (especially NATO members), either. As we shall show in a later article, China is increasingly going abroad for litigation, albeit it wasn’t traditionally the case (the West wrongly assumed all China could do was knockoffs or ‘piracy’ [sic] as the think tanks label it).
“It’s not hard to envision the beneficiaries of a global patent system and their actions.”Days ago IP Kat wrote about the Rhodia v Molycorp “patent jurisdiction tussle,” to quote the author’s headline. Here is some background for the uninitiated: “Rhodia is the exclusive licensee of the UK and German designations of a European patent entitled “Ceric Oxide and method for production thereof, and catalyst for exhaust gas clarification”. Rhodia commenced infringement proceedings in the English High Court alleging that the English domiciled Defendant, Molycorp, had infringed the UK and German designations of the patent.” Here we have a reminder of the unifying patent factor which does not even necessitate a so-called ‘unitary’ patent. Do we really need a ‘globalisation’ of patent systems? That is a rhetorical question of course. It’s not hard to envision the beneficiaries of a global patent system and their actions.
One country dominates the world’s patent systems (including the EPO where it’s ranked number one) and that country is not China, albeit it’s by far the largest population in the world. “In today’s free-trade environment, the USITC’s role is somewhat counter — protecting of U.S. industry,” Patently-O wrote the other day about the ITC, guardian of large US corporations, a nationalist body which has the word “international” in its name/acronym. To quote Patently-O, the “USITC Procedure sets up the USITC as the party prosecuting the case rather than the patentee. As such, the agency is the named respondent and will be represented by the Solicitor’s Office. I expect that the patentee BriarTek will also weigh-in. The patent at issue is U.S. Patent No. 7,991,380 and covers an emergency satellite communication system. The asserted claims were found invalid as anticipated and/or obvious. That holding was then affirmed on appeal by the Federal Circuit.”
“Suffice to say, calls to abolish CAFC altogether increased in recent years.”Well, the Court of Appeals for the Federal Circuit (CAFC), as we noted here repeatedly, is an exceptionally abusive court which not only bypasses constitutional issues but also works for large corporations and for patent lawyers rather than the public (or justice). Simply put, it’s corruptible. Suffice to say, calls to abolish CAFC altogether increased in recent years. And speaking of CAFC, MIP says: “The Federal Circuit has provided some guidance on the issue of 180 days’ notice of launch in a recent biosimilars ruling, in Amgen v Apotex, but practitioners say there will be a lot more litigation before the patent dance is fully clarified” (we are not optimistic).
About the USPTO Patently-O wrote that “Patent Filings Rising Slowly,” according to figures plotted by Professor Dennis Crouch. Is this a case of the more, the merrier? Well, for patent lawyers surely it is merrier (more profitable). Here is what Crouch wrote about it:
The chart above shows USPTO application filings for non-provisional patent applications as well as RCE’s. Both have been on the rise for many years. The filing numbers appear to have continued to rise since implementation of the America Invents Act, although at a slower rate (acceleration has slowed). The USPTO expects that applications filed today will receive a first action within 16 months.
America Invents Act (AIA), with PTAB in particular, has served to introduce some new quality control (potential slowdown and greater pendency to be expected), albeit at too slow a pace as PTAB needs to be expanded to be able to deal with more than just a couple of thousands of patents per year (such workload keeps growing fast).
Patently-O wrote another article exclusively about AIA in which it’s said:
Although more than three years have passed since the changeover date, most new patents still fall under the old-rule. This long transition period is explained by the reality that most patents that issue claim priority to a prior patent filing document such as a foreign priority filing, international PCT application, US provisional application or parent non-provisional US filing. Once the non-provisional application is filed, patent prosecution process still that typically takes around three years. This results in an average pendency from priority filing to issuance of around five years.
The chart there shows that, even though there's a patent litigation slowdown (we’ll expand on that in a later article), problems are far from over. There’s a capacity problem and there’s growing demand. An article by Zachary Kinnaird (posted on his behalf by Professor Jason Rantanen), a patent attorney with International IP Law Group, looks at the number of patent practitioners. He shows some fancy charts and notes: “The number of practitioners removed from the USPTO database reveals a practitioner percentage removal trend that can be seen as a retirement estimate for patent practitioners. This trend shows that the longer a practitioner has had a registration number, the more likely they are to have retired, or otherwise been removed, from the roster.
“The health of the patent system worldwide is oftentimes improving, except at the EPO where patent quality declines* (more on that later today) and human rights are routinely violated.”“The chart below shows the percentage of patent practitioners who still remain registered on the USPTO roster as a function of each practitioner’s year of registration. The further to the right, the more recently the practitioner earned their registration number.”
Not much can be deduced from this (the way it’s presented is not too helpful), unless one is interested in a sob story which serves the party line of the patent microcosm, or the industry associated with patent activity as opposed to production of merchandise, software, etc.
The health of the patent system worldwide is oftentimes improving, except at the EPO where patent quality declines (more on that later today) and human rights are routinely violated. As a European national I am sad and ashamed to see what was once the best patent system in the world becoming one of the worst and most notorious (unless one asks the EPO's mouthpieces). Battistelli tramples everyone and everything. █
____
* Pressured examiners, unskilled (new) examiners and expensive appeals (short duration, very high fees) in an already-understaffed department make the entire process applicants-friendly at the expense of long-term reputation (which made the EPO appealing and worth the exceptionally high prices).
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, GNU/Linux, IBM, Patents at 4:14 am by Dr. Roy Schestowitz
Read between the lines then…

Summary: Blockstream says that it comes in peace when it comes to software patents, which triggers speculations about coming Blockchain patent wars
THE PAST few years were baffling as companies equated promises not to sue with “Open Source” or “open-source” (with a dash, to help dodge the trademark perhaps). Examples we covered here included, notably, Tesla and Panasonic.
A couple of days ago we saw that Blockstream had claimed the following: “Today we are excited to announce some important steps we are taking on the patent front, why these defensive steps are necessary, and our hope that others will see merit in our approach and follow our lead.
“The system as it stands is inherently hostile towards GNU/Linux and Free/Open Source software, which is what Blockchain is all about.”“Core to the Bitcoin ethos is permissionless innovation. Without it and the level of contribution to which it gave rise Blockstream would not be on the exciting path we find ourselves today. It should not come as a surprise then that permissionless innovation is also core to Blockstream’s ethos. We firmly believe that in order for Bitcoin and related technologies’ potential to be fully realized they must be underpinned by a global platform that is free for any innovator to use without hesitation.”
As Benjamin Henrion rightly asked, “where do you have patents? which numbers?” Another person, a patent attorney who specialises in patent data/statistics, noted that “Blockstream Does Not Have Any Patents Assigned to It.” This is not entirely shocking. Having written about Blockstream in the past (we have very broad scope in our daily links), not once did we mention it in relation to patents. Patently German hypothesised: “Preparation for future #blockchain #patent wars? Blockstream announces defensive patent pledge and patent agreement…” (IBM, a patent bully with software patents, is also heavily involved in the same Linux-centric space)
IP Watch, a decent watchdog of patent matters, wrote the headline “Trust Us, We Won’t Sue You” (it sounds rather humourous or sarcastic). It said that “Blockstream, which developed the blockchain technology and bitcoin, has announced a defensive patent strategy. The crux of it: assurance that users of its technology won’t be sued.”
“It seems like shameless self-promotion or a publicity stunt with a “patents” angle.”The EFF wrote about this as follows: “We’ve written many times about the need for comprehensive patent reform to stop innovation-killing trolls. While we continue to push for reform in Congress, there are a number of steps that companies and inventors can take to keep from contributing to the patent troll problem. These steps include pledges and defensive patent licenses. In recent years, companies like Twitter and Tesla have promised not to use their patents offensively. This week, blockchain startup Blockstream joins them with a robust set of commitments over how it uses software patents.”
Bob Summerwill told me [1, 2]: “I see this as hugely positive. Looks directly analogous to what the GPL does for copyrights. Use system against itself.”
Right, but unless Blockstream actually has some patents (there is no evidence of it so far), what can they really use against the system? The system as it stands is inherently hostile towards GNU/Linux and Free/Open Source software, which is what Blockchain is all about.
Blockstream’s message is suggestive of unknown context (like something they know but are not telling us). It seems like shameless self-promotion or a publicity stunt with a “patents” angle. We have become accustomed to it. One company that should definitely do the same thing (but has not) is Red Hat. OIN membership does not guarantee this and if Red Hat got sold to some relatively hostile entity (like Sun to Oracle), there is no guarantee that Red Hat’s patents would not be used to wreak havoc (like a $10 billion lawsuit over a programming language alone, i.e. an order of magnitude worse than SCO versus IBM). █
Permalink
 Send this to a friend
Send this to a friend
07.21.16
Posted in News Roundup at 3:10 pm by Dr. Roy Schestowitz

Contents
-
Desktop
-
When I was a boy, I imagined that other languages were codes, whose words had a one-to-one correspondence to English. In the same way, many Windows users expect Linux to be an exact equivalent.
The reality, of course, is quite different. Both Windows and Linux are operating systems — the programs used to run other applications — but they often fulfill basic functions in different ways. Like any application, they have their own unspoken logic, and part of learning either is to learn their logic.
-
The very words alpha in the name of the release indicate that the Skype which was announced on 14 July is not ready for prime time. That should be apparent to anyone with the IQ of the common cockroach.
But it is apparently not evident to some Linux users.
Things do not seem to be clear to some so-called Linux writers, either. Here is one claiming that “The Skype for Linux alpha does not have all the features that will be released into the final version.”
-
Google’s Chrome OS currently relies upon Upstart as its init system, but work done by an Intel developer is pushing towards systemd support.
-
My name is Jerry Bezencon and I’m a technology consultant, investor, programmer and promoter of/advocate for free and open source software.
-
A French regulator has issued Microsoft a formal warning over Windows 10, saying the operating system collects excessive amounts of personal data, ships that information illegally out of the EU, and has lousy security.
The warning comes from the Commission Nationale de l’Informatique et des Libertés (CNIL), an independent data privacy watchdog with the power to levy fines against companies. The CNIL has been investigating Windows 10 since its launch and has now drawn up a damning list of criticisms.
“The CNIL has decided to issue a formal notice to Microsoft Corporation to comply with the Act within three months,” said the group on Wednesday.
“The purpose of the notice is not to prohibit any advertising on the company’s services but, rather, to enable users to make their choice freely, having been properly informed of their rights. It has been decided to make the formal notice public due to, among other reasons, the seriousness of the breaches and the number of individuals concerned.”
-
Server
-
Containers are more secure than apps running on a bare OS and organisations that like not being hacked therefore need to seriously consider a move, according to analyst firm Gartner.
-
Linux containers are an operating system level virtualization technology for providing multiple isolated Linux environments on a single Linux host. Unlike virtual machines (VMs), containers do not run dedicated guest operating systems. Rather, they share the host operating system kernel and make use of the guest operating system system libraries for providing the required OS capabilities. Since there is no dedicated operating system, containers start much faster than VMs.
-
As the world evolves for systems administrators, “Linux is exploding with new ideas and it’s a little scary …,” as commenter Mike Tarkowski put it.
Keeping up with emerging technologies in cloud computing such as OpenStack will be key to navigating this changing landscape, according to Randy Russell, director of certification for Red Hat.
-
Audiocasts/Shows
-
-
The official Steven J. Vaughan-Nichols LinkedIn page says, “I’ve written over 9,000 articles on business and technology subjects. Highlights include the first popular news story about the web and the first Linux benchmarks. My articles range from features to reviews to OpEd to news reporting.”
A large percentage of those articles have been about Linux and FOSS, so it was logical for us to ring up SJVN (as he is commonly known) and ask him what’s the biggest news about FOSS so far in 2016, and what we can expect in the rest of the year.
-
Kernel Space
-
A Phoronix reader pointed out to us of a new Linux hypervisor released at the end of June by Assured Information Security Inc.
-
Linux has also been a profound influence on software engineering itself – not unlike the old IBM 360 itself – as it is a spectacular example of open source software development.
Alan Cox graduated with a BSc in Computer Science from Swansea University in 1991 and received an MBA from Swansea University in 2005. He has worked for the pioneering Linux service company Red Hat for 10 years and at Intel.
Presenting the award to Mr Cox was Professor John Tucker of Swansea University’s Computer Science Department. He said: “Alan Cox is a world class programmer, an articulate champion of open source software development, and one of the UK’s top software gurus.
-
For those wishing to access EXT-based file-systems from Windows, Paragon Software Group has announced a new version of their ExtFS software for Windows with better support for EXT4 file-systems.
This commercial read-write ExtFS file-system driver for Windows comes with better EXT4 support. The EXT4 support improvements include for handling over 2TB volumes, up to twice as fast as earlier versions of ExtFS, and support for nearly all of the EXT4 mount options / format specifications. The driver is also said to work better for volumes short on space.
-
Graphics Stack
-
Applications
-
It is like when you say Ring is an alternative to Skype. No, no, it’s not. Skype is ghastly. It is proprietary; it is demonstrably insecure; there is evidence that Microsoft uses Skype to siphon off conversations to the NSA; and the GNU/Linux version still lags behind the Windows one. So no, Ring is not an alternative to Skype. Ring is a full-featured, open source product that you need to know about.
-
If I’m to pick a favorite from just these three, I suppose it’s going to be Clementine. Sure, it might be a bit more resource intensive than the other choices and a little broken in places, but I still prefer it to what iTunes has become. As far as the differences between trying new software in a Windows versus a Linux environment, I’m not going to lie: finding my way around Linux is taking some getting used to. And that’s okay — I expected as much. Just as I’d expect trying to haggle in Portuguese might be a bit rough at first if I’m just learning the language and I’ve only known English until now.
-
-
-
Proprietary
-
For those still using the cross-platform Opera web browser, a new developer build is available today that provides new features.
New to the Opera 40.0.2296.0 developer update that was released today is a built-in RSS reader. Opera admits this initial RSS reader is “pretty rough on the edges” but great to see them finally supporting it with their latest browser.
-
As we approach midsummer in this area, we would like to offer a developer update which includes one feature that was frequently asked for. You may now realize it is…
-
Instructionals/Technical
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
I love the Dell XPS 13 (2016) that Dell gave me on loan. But installing Arch Linux with UEFI enabled can be challenging for new users — especially since ‘grub’ doesn’t work on this system with Arch Linux. I talked to a lot of people in the Arch community and resorted to using systemd-boot for successful install.
Here’s how I got Arch Linux running on the Dell XPS 13 laptop.
-
Games
-
The newest installment in the episodic adventure game Kentucky Route Zero has been released after a two year wait.
-
Overlord and the Overlord: Raising Hell expansion have been ported to Linux thanks to Virtual Programming. I was able to get advanced access yesterday and here are some thoughts.
Note: The Linux release is not yet on Steam. This is a DRM free release from their own store. It’s using MojoSetup, so you can install it wherever you please.
-
I’m not usually into such survival games, but considering it’s a single-player experience where I won’t be battered to death by naked people (Hello Rust) it might be worth a shot.
-
-
Although popular “Harvest Moon”-inspired indie farming sim “Stardew Valley” had been rumored to be getting ported to consoles, creator/developer Eric Barone/ConcernedApe announced a port coming to the Mac and Linux machines
-
-
Best Buds vs Bad Guys is a very cool looking action platformer that is now fully funded and is officially heading to Linux.
I actually helped Kickstart this, as their story as a dad and son who created the idea together captured my interest. Not only that, but the game actually looks really good. Funnily enough, I think they are based only a few miles away from me in the UK.
-
I actually did some initial testing after the developer sent over a key and it does seem interesting. Some bits of it are a little clunky and the lighting is a little too flashy for me, but some of you may like it. The lights tend to flicker really quickly which makes my eyes hurt a lot, so I haven’t been able to progress far into it. I fed that back to the developer that it flickers too much and too quickly, but it’s a finished game so I don’t know if they will adjust it at all.
-
Dungeon Rushers is a game I tested for the developer a while ago when they posted it to reddit, so they sent along a key to check out properly now it’s out for Linux.
It’s actually pretty good, it has some nice art, some interesting dialogue, the battles are fun and it has a lot going for it. You travel the map in search of dungeons and while exploring you can level up, unlock new skills and equipment and so on.
It’s not just single-player either, it has a full online mode if you’re feeling truly adventurous. This is locked until you progress a bit in the single-player though.
-
Mark your calendars, fellow farmers, because Stardew Valley will finally be making its way to Mac and Linux this week. Game creator Eric Barone, AKA Concerned Ape, posted a tweet today to announce the good news. After seeing massive success since its PC launch, the dev has worked tirelessly to bring the game to other operating systems too.
-
While we already know that Life is Strange is coming to Linux from Feral, we don’t know when, but we do now know that Life is Strange episode 1 will be free from tomorrow.
-
-
BrainBread 2 is a rather amusing fast paced Source engine powered FPS that’s 100% free. It’s now on Steam!
I’ve tested it out for a little bit and it’s actually pretty fun, well worth a try if you like faster paced FPS games and you like getting stuff totally free.
Performance wise with everything cranked up to max my 980ti was bouncing between 130-200FPS+ depending on map and what was going on, so it does perform pretty well.
-
That’s obviously far short of what it has sold on Windows, still not close to Mac levels, but that’s still quite a bit of money from Linux sales.
While I’m not a fan of Rust myself, it just doesn’t click with me, I can’t deny it has appeal to people who like those sorts of games. Even though Garry doesn’t feel Linux has been worth it in his previous statements, I am still very glad it’s on Linux. It’s also nice of Garry to be so open about the sales.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Secondly, the ioslave is now completely independent from Dolphin, or any KIO application for that matter. This means it works exactly the same way across the entire suite of KIO apps. Given that at one point we were planning to make the ioslave fully functional only with Dolphin, this is a major plus point for the project.
-
GNOME Desktop/GTK
-
I write more about this on my Coaching Buttons blog, that I’m thinking about writing an ebook. Actually, it’s several ebooks. But the one that applies here is Open Source Usability.
-
Various GNOME software components were checked in today in preparation for this week’s GNOME 3.21.4 development release.
When it comes to the Mutter 3.21.4 compositor / window manager release, there are a few new features on top of fixes. This 3.21.4 release includes the frame-buffer / display work I talked about this morning that should allow multiple monitor setups to have different DPIs, among other design improvements. There is also improved X11 to/from Wayland copy/paste interaction, support for the NV_robustness_video_memory_purge extension, a screen capture API has been added to Mutter itself, and various other fixes/improvements.
-
-
-
New Releases
-
There is no shortage of Linux distributions that provide a platform for security researcher to conduct various security research. Among them is the Network Security Toolkit (NST), which was recently updated to version 24-7977. The 24 is a referenced to Fedora, which NST is based on.
Aside from simply integrating existing tools, NST goes a step further and provides a number of innovative capabilities including a new Multi-Traceroute (MTR) networking tool.
-
Screenshots/Screencasts
-
OpenSUSE/SUSE
-
Ludwig Nussel has announced the release today of the third alpha release for the forthcoming openSUSE “Leap” 42.2 update.
OpenSUSE 42.2 Alpha 3 finishes up the merge of SUSE Linux Enterprise 12 SP2 components, updates to GNOME, KDE Plasma 5.7 integration, and various other changes.
-
-
SUSE Manager is a open-source IT management solution with a centralized console for managing multiple Linux distributions, hardware platforms (x86, IBM Power Systems and z Systems), as well as physical, virtual and cloud environments. SUSE says that the solution helps customers reduce the complexities of managing their IT infrastructures, a key advantage as customers look to cut costs and increase the responsiveness required to adopt DevOps and hybrid cloud solutions.
-
Recently we implemented Tally ERP 9 solution for Antico Pumps. That itself is not interesting, the interesting part is they are using LTSP Fat client system on openSUSE. They have only one server from which all their client computers boot over the network, the clients do not have hard disk, client OS with all softwares they need including wine(Tally is Windows only software), as well as users’ data resides on the server. Once the client boots all the local resources are used so single low power server can be used to serve many clients.
-
Red Hat Family
-
Interoute was named a Certified Cloud and Service Provider by Red Hat for its networked cloud infrastructure platform, Interoute Virtual Data Centre (VDC).
-
Interoute, owner operator of a global cloud services platform and one of Europe’s largest networks, has today announced that it has been named a Certified Cloud and Service Provider by Red Hat, the world’s leading provider of open source solutions, for its global networked cloud infrastructure platform, Interoute Virtual Data Centre (VDC).
-
Finance
-
Fedora
-
Topping today’s Linux news is the wrist slapping of Microsoft by French Commission Nationale de l’Informatique et des Libertés for excessive spying. Back in Linuxland, openSUSE 42.2 Alpha 3 and Mint 18 Xfce Beta were released for early testers. Bruce Byfield compares Linux and Windows users and Dedoimedo found another distribution he likes. VarGuy Christopher Tozzi ran down five Open Source projects that didn’t work out and Sam Varghese scolds Linux users for expecting Final quality out of Alpha releases.
-
I am pleased. I am really pleased. Fedora 24 delivers an excellent, modern experience. Such a refreshing departure from all the sadness I had to deal with it in the last two months. While it’s not aimed at new users and does not offer D2D fun right away, Fedora still managed to give a most satisfying and a highly consistent experience. With a little bit of tweaking, it’s superb.
Looking across the board, we have good networking support overall with a permanent workaround for Realtek woes, good smartphone support, stability, speed, battery life, excellent hardware compatibility, a much improved package management system. After pimping, the fun extends to multimedia and some extra customization. And Gnome isn’t half as bad as it used to be. Really lovely.
There are some small problems still, here and there, the chief amongst them being the ultra short support life of a typical Fedora release. But then, just look at my CentOS 7.2 reviews, the recent Gnome and Xfce ones. You get pretty much the same experience plus a whooping 10 years of support. That’s what I’ve always been waiting for in Linux. Anyhow, Fedora 24 is a very good summer release. 9/10, and I’ve had a lot of fun sorting things out, because they remained sorted out, there are no silly errors, and the network is solid and stable. Linux as it should be. This is your pick for this season. Enjoy.
-
Fedora APAC budget panning FAD 2016 was held on 9th-10th of July 2016 in Malaysia. I was there with Fedora ambassadors from other countries within APAC region.
-
I was trying to get into code search in Pagure, thing that I land up on got really interesting and amazing. If you want to have a code searching mechanism in your website you need to look into something called Indexing.
The way search happens in some E-commerce sites like Amazon or be it the search happening on Google, with Google its web scrapping and then indexing on the results. The point being the response time , while you are searching for something you get results in few microseconds.
-
Debian Family
-
-
Derivatives
-
Canonical/Ubuntu
-
BQ Aquaris M10, the first Ubuntu-powered tablet to ship, has some flaws, but the fact that it runs traditional Linux desktop apps will make many Linux users happy
-
It has been one year since our previous review of an Ubuntu Phone, namely examining the Meizu MX4 Ubuntu Edition, and the time has come for us to take a look at the best handset powered by Canonical’s Ubuntu Touch mobile operating system that you can buy right now, the Meizu PRO 5 Ubuntu Edition.
-
The Ubuntu team is pleased to announce the release of Ubuntu 16.04.1 LTS
(Long-Term Support) for its Desktop, Server, and Cloud products, as well
as other flavours of Ubuntu with long-term support.
As usual, this point release includes many updates, and updated
installation media has been provided so that fewer updates will need to
be downloaded after installation. These include security updates and
corrections for other high-impact bugs, with a focus on maintaining
stability and compatibility with Ubuntu 16.04 LTS.
-
-
Hi there! My name is Dustin Kirkland, a Linux user for nearly 20 years, and an open source developer for almost as long. I worked on Linux at IBM for most of a decade, on site at Red Hat for a bit, and now at Canonical for nearly another decade. I started at Canonical as an engineer on the Ubuntu Server team and eventually evolved into the product manager responsible for Ubuntu as a server and cloud platform. I’ve authored many open source utilities used by millions of Ubuntu users every day. Open source software is my passion, my heart, and my soul.
I was working in Cape Town, South Africa when I received a strange call from a friend and colleague at Microsoft in January of 2016. The call was decorated with subtlety as he danced around the technology underpinning what you and I today know as “Ubuntu on Windows,” but without any detail. There was plenty of confusion. Confusion around exactly what we were talking about. Confusion about how this could even work. Confusion about how I should feel about this.
-
Flavours and Variants
-
Linux Mint 18 is a long term support release which will be supported until 2021. It comes with updated software and brings refinements and many new features to make your desktop even more comfortable to use.
-
So after the release of Linux Mint 18 sarah in the flavours of Cinnamon and MATE,now the team is focoused on working over other flavours too.As a result Xfce has been choosen to be the next flavour to be provided officially.
So,If you were waiting for Linux Mint 18 to be available in Xfce DE(Desktop Environment) then Linux Mint team has started to roll the beta release of Sarah in Xfce DE. Linux Mint team announced the release of Linux Mint 18 Xfce Beta with some already known issues and workarounds too.This xfce edition features Xfce 4.12, MDM 2.0 and it is coming with Linux Kernel 4.4.
-
While the release comes with the new X-Apps, the Mint-Y theme, new artwork, an Ubuntu 16.04 base, and version 4.4 of the Linux kernel, it still runs Xfce 4.12 and MDM 2.0, both of which were present in Mint 17.3. The reason Xfce and MDM are at the same versions is because they are the latest upstream versions. They’ll likely be updated with new point releases in the Mint 18 cycle.
-
-
-
Electronics enthusiasts looking for a small Linux powered mini PC for Internet of Things projects might be interested in the new Omega2 which has been created by Onion and is priced at just $5.
-
Phones
-
Tizen
-
Popular international communication app Zipt developed by ZipTel Ltd has been called up by Samsung to be the Marquee app for Tizen. With the launch of the next Tizen based smartphones happening possibly as early as next month, Samsung might be gearing up for a major announcement for the Tizen platform which until now has been deficient of apps that are easily available on rival platforms like Android and iOS. The Zipt negotiation could possibly be a part of this announcement. Ziptel are now working with the finest of Tizen Developers to get their app into the Tizen platform.
-
Android
-
Motorola’s Moto Mods offer more flexibility than most smartphone accessories, allowing Moto Z and Moto Z Force owners to easily bolster the phone’s abilities or add new features altogether. The Mods’ most impressive aspect is that they just work. Clicking a Moto Mod into place instantly turned my phone into a projector without any cables or hassle.
-
-
-
-
-
-
-
-
-
-
Smartphones have changed the way the world gets online, by letting you put a tiny, touchscreen computer in your pocket or handbag. But sometimes it’s still nice to have a larger screen, a full-sized keyboard, and a mouse or touchpad.
The Superbook is a smartphone accessory that gives you all those things. It looks like a laptop, but all the processing power and software comes from your phone.
-
There’s no denying the success of free and open source software projects like Linux, Apache and (probably) OpenStack. But what about the FOSS projects and companies that have enjoyed less success? Here’s a look at some free and open source software projects or businesses that had good ideas, yet never delivered on them (at least not fully).
-
German start-up deepstreamHub has launched deepstream.io, an open source, scalable, real-time server platform. The platform is designed for applications that require a network of device-resident nodes that communicate with cloud applications or with one another. Individual nodes can subscribe to topics and receive data whenever other clients publish to those topics. Nodes can also register functions that can be called by other nodes. The deepstreamHub platform is also available as a resource for additional services.
-
The excitement that comes with a college degree is memorable – not only because of the joy of accomplishment, but because of the fear of the unknown.
In the open source community, job hunting is its own unique experience. There is great optimism and opportunity in The Linux Foundation’s 2016 Open Source Jobs Report, which found that recruiting open source talent is a top priority for IT recruiters and hiring managers. The report found 65 percent of hiring managers say open source hiring will continue to increase more than any other part of their business over the next six months.
-
Web Browsers
-
SaaS/Back End
-
Cloudera, which provides a complete data management and analytics platform built on Apache Hadoop and related open source technologies, announced the beta release of Cloudera Navigator Optimizer–a tool for improved workload performance and efficiency–late last year. Essentially, the tool allowed users to modernize their analytic database or augment their data warehouse solution with Hadoop, serving up insights aimed at predictably offloading key workloads.
Now, Cloudera has announced the general availability of Cloudera Navigator Optimizer, alongside the production release of Cloudera Enterprise 5.8. Navigator Optimizer is now an entrenched part of Cloudera’s platform.
Workload management is an issue for many Hadoop-focused organizations. Within any business, there can be countless workloads being run at any given time, across multiple systems, that change based on time of day and business need. Across many of these workloads, similar pain points have emerged, like breakdowns in ETL pipelines, long wait times for BI reports, increasing system pressure from ad hoc queries, and unnecessary query complexity. When adopting new systems based on Hadoop, it’s critical that customers understand their workloads, so they can address these inefficiencies and run the right workloads in the right systems for the best results.
-
What are the target markets for StorPool? “We target based on use-case”, said StorPool CEO, Boyan Ivanov. “Companies that build public or private clouds [including] enterprises and SMEs, service providers along with IaaS/PaaS, managed service providers, telecoms and hosting companies.”
-
Pseudo-Open Source (Openwashing)
-
FSF/FSFE/GNU/SFLC
-
Licensing/Legal
-
Last week, new New York Times public editor Liz Spayd said something completely and utterly crazy: she suggested that news outlets and websites should actually listen to and interact with their visitors in news comment sections. Given this is the age where most “enlightened” media outlets are now closing their comment sections and pretentiously pretending it’s because they “value conversation,” Spayd’s comments were treated like the incoherent ramblings of a mad woman on some fronts, people claiming actually caring about readers was a form of “phony populism” and the “willfully naive” rhetoric of a bygone era.
But we’ve noted time and time again that by muzzling them or shoveling off your community to the homogonized blather of Facebook, you’re pretty clearly saying you don’t think your audience really matters. Countless editors refuse to believe this, by and large because nobody at a multi-million dollar media empire wants to actually have real conversations with the dirty plebeians they profess to be so selflessly dedicated to. The entire mechanism should be demolished, they argue, because commenters are mean and say bad things — ignoring studies suggesting this can be easily fixed by giving a damn.
-
The Software Freedom Conservancy has issued a blog post this week about community-oriented principles in GPL enforcement work and in particular pointing out a Linux developer who hasn’t agreed to these terms and is allegedly focusing upon GPL enforcement for his own financial gain.
As part of the Conservancy’s principles, “Community-oriented enforcement must never prioritize financial gain…Nevertheless, pursuing damages to the full extent allowed by copyright law is usually unnecessary, and can in some cases work against the purpose of copyleft.”
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
Upgradable portable computers have been a bit of pipe dream for the last decade.
-
Programming/Development
-
Today marks the availability of the PHP 7.1 beta as a closer step forward to this first feature update to PHP7.
PHP 7.1 introduces a number of new features including but not limited to the void return type, nullable types, generalized support of negative string offsets, class constant visibility modifiers, multi-catch, and more. PHP 7.1 beta adds asynchronous signal handling and additional context with the pcntl_signal handler.
-
-
With the spring and summer travel schedule drawing to a close, we finally have had time to sit down and run the numbers collected back in June. As always, aside from the fact that we run our own GitHub rankings now, the process used for our bi-annual programming language rankings remains the same as when Drew Conway and John Myles White first looked at the question late in 2010. We have continued this analysis, comparing the performance of programming languages relative to one another on GitHub and Stack Overflow twice a year. The idea is not to offer a statistically valid representation of current usage, but rather to correlate language discussion (Stack Overflow) and usage (GitHub) in an effort to extract insights into potential future adoption trends.
With the exception of GitHub’s decision to no longer provide language rankings on its Explore page – they are now calculated from the GitHub archive – the rankings are performed in the same manner, meaning that we can compare rankings from run to run, and year to year, with confidence.
Historically, the correlation between how a language ranks on GitHub versus its ranking on Stack Overflow has been strong, but this had been weakening in recent years. From its highs of .78, the correlation was down to .73 this time last year – the lowest recorded. For this run, however, the correlation between the properties is once again robust. As with last quarter’s ranking, the correlation between the properties was .77, just shy of its all time mark. This is arguably noise, but we believe the correlation is worth noting at a minimum.
-
Standards/Consortia
-
-
-
-
-
-
-
-
-
-
-
-
-
-
AT&T* and Orange have signed an agreement to collaborate on open source and standardization initiatives that will accelerate the standardization of software-defined networking (SDN) and network function virtualization (NFV) technologies. The companies are aligning on a strategic vision to move intelligence from customer hardware to the network, reducing cost and complexity. This effort will help the industry and business customers move faster towards a more agile, flexible and on-demand networking future.
-
Verizon Enterprise Solutions today announced its first set of virtual network services, including the usual suspects of security, WAN optimization, software-defined WANs and virtualized customer premises gear. Working with mostly established vendors, Verizon is making its services available globally on an immediate basis, and focusing heavily on giving customers lots of options for how they transition to the virtualized world. (See Verizon Launches Virtual Network Services.)
The announcement comes four days after AT&T Inc. (NYSE: T) introduced its Network Functions on Demand offer, and differences between the two services are apparent and strategic, notes Nav Chander, research manager for telecom business services with IDC. (See AT&T Offers Network Functions On Demand… Sort Of.)
-
The only major negative for Microsoft in this report comes from the usual suspect: mobile. Microsoft phone revenue fell by 71 percent, for a dollar loss estimated by the Register to be $870 million. Even search advertising, which forever was a big loser for Redmond, saw in increase of over a half billion dollars.
-
Science
-
The frigid plains of northern Siberia are becoming a hotspot for mysterious geological phenomena. Over the past couple of years, sudden craters have been exploding from the permafrost-laden ground. Last month, we reported on a giant chasm in the Sakha Republic that looms so wide and deep, locals refer to it as a “gateway to the underworld.”
Now, the frozen tundra on Siberia’s remote Belyy Island is home to the region’s newest aberration: eerie, rippling, underground bubbles.
-
Health/Nutrition
-
Patients may go to rehabilitation hospitals to recover from a stroke, injury, or recent surgery. But sometimes the care makes things worse. In a government report published Thursday, 29 percent of patients in rehab facilities suffered a medication error, bedsore, infection or some other type of harm as a result of the care they received.
Doctors who reviewed cases from a broad sampling of rehab facilities say that almost half of the 158 incidents they spotted among 417 patients were clearly or likely preventable.
“This is the latest study over a long time period now that says we still have high rates of harm,” says Dr. David Classen, an infectious disease specialist at the University of Utah School of Medicine who developed the analytic tool used in the report to identify the harm to patients.
-
Small farmers around the world are threatened by new free trade agreements, a civil society group has argued. Those agreements go beyond the requirements of agreed international intellectual property rules and jeopardise the ability of small farmers to save, produce, and exchange seeds, the group said.
GRAIN just published its latest opinion piece [pdf], part of its “Against the grain” series. This one focuses on the potential threat of free trade agreements, such as the Trans-Pacific Partnership (TPP) agreement and the Regional Comprehensive Economic Partnership (RCEP) in Asia.
-
The tobacco industry’s global efforts to use bilateral and multilateral agreements to challenge the spread of tobacco control measures such as trademark-minimising plain packages were dealt a significant blow last week when the World Bank dispute settlement body dismissed a case brought by Philip Morris against the government of Uruguay.The decision is seen a landmark for those who view the company as using test cases to continually challenge and delay public health protection measures and discourage other countries, particularly those with fewer resources, from strengthening their health regulations. Additionally, the case reasserted that trademarks are subject to government regulations and also illustrated the role that international organisations and actors can play in support of national governments defending their health measures.
-
Just three years after the Japanese government withdrew support for a vaccine against the human papillomavirus (HPV), a new report finds the country’s girls are dramatically more vulnerable to contracting the cancerous disease. Japan’s decision was solely informed by one “sensationalized” report from a non-medical anti-vaccine activist group called Vaccine Victims, which is under investigation by the Japanese government.
-
Security
-
-
A Virginia software developer announced today the release of what’s billed as the first open source information security analytics tool for managed security services providers (MSSP) and enterprise.
IKANOW says its new platform features multi-tenancy, enterprise scalability and is fully customizable.
-
Four out of five businesses lack the required infrastructure or security professionals with relevant skills to spot and defend against incoming cyberattacks.
According to a new report by US cybersecurity and privacy think tank Ponemon Institute on behalf of cybersecurity firm BrandProtect, 79 percent of cybersecurity professionals say that their organisations are struggling to monitor the internet for the external threats posed by hackers and cybercriminals.
-
After lying dormant for years, flaws in the HTTP Proxy header used in programming languages and applications, such as PHP, Go and Python, have now been fixed.
Some flaws take longer—a lot longer—than others to get fixed. The newly named HTTpoxy vulnerability was first discovered back in March 2001 and fixed in the open-source Perl programming language, but it has sat dormant in multiple other languages and applications until July 18.
The HTTPoxy flaw is a misconfiguration vulnerability in the HTTP_PROXY variable that is commonly used by Common Gateway Interface (CGI) environment scripts. The HTTPoxy flaw could potentially enable a remotely exploitable vulnerability on servers, enabling an attacker to run code or redirect traffic. The flaw at its core is a name space conflict between two different uses for a server variable known as HTTP Proxy.
-
Currently HackerOne has 550+ customers, has paid over $8.9 million in bounties, and fixed over 25,000 vulnerabilities, which makes for a safer Internet.
-
For the FOSSA pilot project to improve the security of open source software that my colleague Max and I proposed, the European Commission sought your input on which tools to audit.
The results are now in: The two overwhelming public favorites were KeePass (23%) and the Apache HTTP Server (19%). The EU has decided to follow these recommendations and audit both of these software projects for potential security issues.
-
The other week I published the “A Case Study in Attacking KeePass” post detailing a few notes on how to operationally “attack” KeePass installations. This generated an unexpected amount of responses, most good, but a few negative and dismissive. Some comments centered around the mentality of “if an attacker has code execution on your system you’re screwed already so who cares“. Our counterpoint to this is that protecting your computer from malicious compromise is a very different problem when it’s joined to a domain versus isolated for home use. As professional pentesters/red teamers we’re highly interested in post-exploitation techniques applicable to enterprise environments, which is why we started looking into ways to “attack” KeePass installations in the first place. Our targets are not isolated home users.
-
Former New York mayor Rudy Giuliani made a surprise appearance at the BlackBerry Security Summit, warning of the rapid growth of cybercrime and cyberterrorism.
Cybercrime and cyberterrorism are both growing at rates between 20% and 40%, said Giuliani, who made a brief return from the Republican National Convention in Cleveland to speak at BlackBerry’s New York event.
“Think of it like cancer. We can’t cure it… but if we catch it early we can put it into remission,” he said. The quicker you can spot an attack, the less chance there is of loss.
-
A notorious hacker has claimed responsibility for hacking Turkey’s ruling party, the AKP, and stealing more than 300,000 internal emails and other files.
The hacker, who’s known as Phineas Fisher and has gained international attention for his previous attacks on the surveillance tech companies FinFisher and Hacking Team, took credit for breaching the servers of Turkey’s ruling party, the Justice and Development Party or AKP.
“I hacked AKP,” Phineas Fisher, who also goes by the nickname Hack Back, said in a message he spread through his Twitter account on Wednesday evening.
-
Defence/Aggression
-
A failed coup in Turkey has changed the geopolitical landscape overnight realigning Ankara with Moscow while shattering Washington’s plan to redraw the map of the Middle East. Whether Turkish strongman Recep Tayyip Erdogan staged the coup or not is of little importance in the bigger scheme of things. The fact is, the incident has consolidated his power domestically while derailing Washington’s plan to control critical resources and pipeline corridors from Qatar to Europe. The Obama administrations disregard for the national security interests of its allies, has pushed the Turkish president into Moscow’s camp, removing the crucial landbridge between Europe and Asia that Washington needs to maintain its global hegemony into the new century. Washington’s plan to pivot to Asia, surround and break up Russia, control China’s growth and maintain its iron grip on global power is now in a shambles. The events of the last few days have changed everything.
-
A coalition airstrike reported on Tuesday that killed at least 85 civilians—one more than died in the Nice attack in France last week—wasn’t featured at all on the front pages of two of the top US national newspapers, the New York Times and LA Times, and only merited brief blurbs on the front pages of the Wall Street Journal and Washington Post, with the actual stories buried on pages A-16 and A-15, respectively.
According to the London Telegraph (7/19/16), the airstrike killed “more than 85 civilians” after the “coalition mistook them for Islamic State fighters.” Eight families were represented among the dead, with victims “as young as three.” The Intercept (7/19/16) reported the death toll could end up being well over 100.
-
One has to ask where the New York Times’ “journalistic detachment” was in 2002 and 2003. Rutenberg himself (2/18/03) in the lead up to the invasion reported on the use of “embedded journalists” for the first time since World War II. How “detached” from a war effort can journalists be if they are literally attached to an invading army?
It’s a subtle piece of revisionism, but an important one: For those in center-left media, the impulse to rewrite their own role in selling the Iraq War is all too tempting–to turn Fox News into a cartoon propaganda outlet, and their own editorial drum-beating, war protester-mocking, aluminum tube-peddling and Dick Cheney water-carrying as “detached” journalism, simply calling balls and strikes. Certainly Ailes’ Fox News was more naked in its war promotion, but the New York Times, with its nominal liberal reputation and air of objectivity, was almost certainly more effective.
-
It took fourteen years for the public to see this document…
-
Whatever motivated Turkey’s failed coup, President Erdogan is exploiting the outcome to round up his political enemies and consolidate his dictatorial style rule, a challenge to the U.S. and E.U., as Alon Ben-Meir describes.
-
Turkey’s failed “coup” has shaken up the region’s geopolitics, splintering the powerful Turkish military, forcing President Erdogan to focus on internal “enemies,” and undermining the Syrian rebels next door, says ex-British diplomat Alastair Crooke.
-
Despite all the articles and analysis in the wake of the Pulse nightclub shooting, one important fact seems to have been completely overlooked: the shooter validated Ron Paul’s warning that American military intervention in the Mideast causes terrorist attacks.
-
The grisly beheading of a 12-year-old boy by U.S.-backed Syrian rebels spotlights Washington’s creepy excuses for arming “moderate” jihadists who are barely distinguishable from Al Qaeda and ISIS, reports Daniel Lazare.
-
Mr. Erdogan, who has long attempted to create pliable state institutions, said that the coup was a “gift from God to us because this will be a reason to cleanse our army”. The government arrested more than 6,000 people from the military and other state institutions. Saying that the Gülen movement had become a “cancer virus” on society, Mr. Erdogan pledged to purge its membership from positions of authority. The ultimate arbiter of who is or is not in the Gülen movement will be left to Mr. Erdogan’s own loyalists, who are likely to remove those who have long resisted the President’s own bid to monopolise power. Mr. Erdogan deliberately linked the Gülen movement to the Kurdistan Workers’ Party (PKK), which the Turkish army has attacked in its bases in south-eastern Turkey and in Iraq. To call both the Gülen movement and the PKK ‘terrorists’ is a convenient way to sweep up all Erdogan enemies into one target and use the coup — a “gift from God” — as the opportunity to go after them with vehemence.
-
The attempted military coup in Turkey and the possibility of a President Trump may have more Americans considering the military option.
-
Transparency/Investigative Reporting
-
On the 50th anniversary of the Freedom of Information Act, here are ProPublica reporters’ most frustrating public record failures.
-
Environment/Energy/Wildlife/Nature
-
As the string of record-breaking global temperatures continues unabated, June 2016 marks the 14th consecutive month of record-breaking heat.
According to two US agencies – Nasa and Noaa – June 2016 was 0.9C hotter than the average for the 20th century, and the hottest June in the record which goes back to 1880. It broke the previous record, set in 2015, by 0.02C.
The 14-month streak of record-breaking temperatures was the longest in the 137-year record. And it has been 40 years since the world saw a June that was below the 20th century average.
-
Donald Trump’s reported top pick for energy secretary, oil and fracking billionaire Harold Hamm, declared on the Republican National Convention stage on Wednesday night, “Every time we can’t drill a well in America, terrorism is being funded.”
One day earlier, NASA had announced that this June was the hottest June on record, and that the same could be said for every month in 2016 — part of a long-term climate trend that has exacerbated geopolitical conflicts.
The convention adopted a platform that rejected the Paris climate agreement, the Kyoto Protocol, and the U.N. Framework Convention on Climate Change. Meanwhile, researchers published a study indicating that climate change worsened a 2003 heat wave enough to kill 570 more people in Paris and London than would have died in an unchanged world.
Rep. Marsha Blackburn from Tennessee, who will take the convention stage Thursday, told a Cleveland panel on Monday that “the earth is no longer warming and has not. For about the past 13 years, it has begun to cool.”
-
I bet not many high schoolers read the Wall Street Journal. And, as a recent graduate, I can tell you confidently it’s because we’re too busy with other things. And I don’t mean busy playing Pokémon Go. I guess I’d consider myself an outlier as an unusually high consumer of news and opinion, particularly from the Wall Street Journal. Either way, as a young person that will feel the worst effects of climate change as I get older, it’s extremely important to me that the issue receives the attention it deserves from mainstream media.
The Wall Street Journal hasn’t exactly been at the forefront when it comes to leading fair and unbiased commentary on climate change, especially on its editorial page. That’s why I was truly shocked by the full page ad series about man-made climate change currently running. I saw the first ad that ran back on June 14 and those that have run every few days since. The shock came partly just because the ad existed, but the fact that it was actually slamming the Wall Street Journal for its overt climate denial was almost unbelievable. I dug deeper and learned through a piece by the Washington Post that only for a fee higher than it normally charges for ad space was the Journal willing to place the ads… not exactly equitable. Does the WSJ charge Big Oil more to run their ads?
-
-
In an open letter sent to Congress today, a coalition of 40 national taxpayer, labor, environmental and other groups called on the federal government to repeal almost $4 billion in annual tax breaks for the oil and gas industry, calling them wasteful and lambasting Congress for subsidizing activities that will make climate change worse.
The groups called on Senators to support the FAIR Energy Policy Act, which would slowly phase out nine special tax breaks for the fossil fuel industry.
“Oil companies receive billions in tax breaks, despite being among the world’s largest and most profitable corporations,” the groups wrote. “For too long, America has subsidized the oil industry’s bottom line at middle class Americans’ expense.”
Another law passed earlier this year revokes the wind industry’s production tax credit, and the FAIR Energy Policy Act would wind down some of the oil industry’s subsidies on the same schedule.
-
Finance
-
For decades, Americans have been sold on rugged individualism and told to disdain collectivism and community, a philosophy that has starved many public institutions and fattened up the few at the top, as Lawrence Davidson explains.
-
Mr. Barroso’s appointment as Goldman Sachs non-executive chairman is shameful. As a former President of the European Commission, he should be held to higher ethical standards.
-
-
The US is hoping that a quick trade and investment deal with the UK after it leaves the EU could kickstart the stalled negotiations for the Transatlantic Trade and Investment Partnership (TTIP), which has met increasing resistance on the continent.
As well as serving the US’s purposes, such an agreement would be welcomed by the UK government as proof that it can recreate the necessary web of trade links post-Brexit.
The US secretary of state, John Kerry, has just spent two days in the UK talking with the prime minister’s officials and with the new foreign secretary, Boris Johnson, exploring what form such a UK-US trade deal might take.
As The Guardian explains: “The UK cannot formally sign any trade deals with other countries or trading blocs until it has left the EU, but it appears to be accepted that negotiations on the outline shape of such deals can start before that happens.”
-
AstroTurf/Lobbying/Politics
-
Still, I wouldn’t have missed the film for the world. After all, it’s the first action movie that — as you’ll see from TomDispatch regular Adam Hochschild’s piece today — has ever based itself in any way on a book I edited, in this case his classic King Leopold’s Ghost: A Story of Greed, Terror and Heroism in Colonial Africa. As a result, I left the theater filled with wild fantasies. (Even editors can dream, can’t they?) I began to imagine Who Rules the World?, Noam Chomsky’s latest book, absorbed into a future X-Men: Apocalypse America. Or the late Chalmers Johnson’s Dismantling the Empire as the basis for the next Jason Bourne romp. Or Ann Jones’s They Were Soldiers at the grim heart of American Sniper: The Next Generation. Or, in Tarzan-style, Andrew Bacevich’s writing on America’s twenty-first-century Middle Eastern wars as part of a reboot of Lawrence of Arabia — perhaps King David of Iraq: The Surge to Nowhere.
-
Sounding another alarm for progressives wary of the Democratic establishment’s support for Wall Street, the man said to be leading the pack of potential Hillary Clinton running mates—Virginia Sen. Tim Kaine—has just this week sent a clear message to big banks: He’s in their corner.
Kaine, who is reportedly Bill Clinton’s favorite for the vice presidential slot, signed onto two letters on Monday pushing for financial deregulation—letters that show the Clinton camp “how Kaine could be an asset with banking interests on the fundraising trail,” according to David Dayen at The Intercept on Wednesday.
The first missive, signed by 16 Democrats and every Republican senator, calls on the Consumer Financial Protection Bureau (CFPB) to exempt community banks and credit unions from certain regulations.
-
Virginia Sen. Tim Kaine, considered a leading contender for the Democratic vice presidential nomination, has spent this week signaling to the financial industry that he’ll go to bat for them.
On Monday, Kaine signed onto two letters, one to federal banking regulators and the other to the Consumer Financial Protection Bureau, urging them to loosen regulations on certain financial players. The timing of the letters, sent while Kaine is being vetted for the top of the ticket, could show potential financial industry donors that he is willing to serve as an ally on their regulatory issues.
In the letters, Kaine is offering to support community banks, credit unions, and even large regional banks. While separate from the Wall Street mega-banks like JPMorgan Chase and Bank of America, these financial institutions often partner with the larger industry to fight regulations and can be hostile to government efforts to safeguard the public, especially if it crimps their profits.
They also represent a key source of donor funds, one that has trended away from Democrats. The Independent Community Bankers of America have given 74 percent of their $873,949 in donations this cycle to Republicans, according to the Center for Responsive Politics. Regional banks like PNC Financial Services, SunTrust Bank, and First Republic Bank, have given even higher percentages to the Republicans.
-
Last Friday the U.S. government finally released 28 pages of a 2002 congressional report that detail possible ties between the Saudi Arabian government and the 9/11 hijackers.
The document lists various forms of assistance provided by Saudi agents to the hijackers, including help finding a flight school and various forms of financial support when the hijackers arrived in the United States. Many of the findings in the report have not been fully vetted as several of the Saudi agents named in the 28 pages have refused to cooperate.
But that has not stopped Saudi-funded lobbyists and media outlets from claiming that the disclosure of the 28 pages ends all speculation about the role of Saudi Arabia in the 9/11 terror attacks. Several outlets controlled by Saudi Arabia’s vast public relations machine are trumpeting the document as a vindication that closes the door on any suggestion that the Saudi government had any ties to the 9/11 terrorists.
“The question of Saudi involvement in 9/11 should be entirely put to rest,” said Fran Townsend, a former Bush administration official, in a 28 pages-related video posted on social media this week. The video was produced by Focus Washington, an interview series managed by Qorvis MSL, a lobbying firm retained by the Saudi government to influence American policymakers. The Saudi Embassy Twitter account distributed the video.
-
Cruz doesn’t disagree with Trump. He thinks Trump is a pretender to the cause, or he remains angry at how Trump personally insulted him, his wife and his father – or both.
The person who really disagrees with Trump is his vice-presidential nominee Mike Pence, who said in December that “calls to ban Muslims from entering the U.S. are offensive and unconstitutional.” In 2006 he concluded “it is not logistically possible to round up 12 million illegal aliens.” He supports NAFTA and the Trans-Pacific Partnership (TPP). And he disavowed negative campaigning 25 years ago.
-
Donald Trump may alarm Washington’s foreign policy establishment with his “America First” rhetoric but Mike Pence, Trump’s VP choice, reaffirms a commitment to the traditional “Israel First” doctrine, as Sam Husseini shows.
[...]
I’ve heard him say that before. Being a journalist based in the Washington, D.C. area, I try to ask tough questions of political figures when I can. Perhaps my favorite question is some variation of “do you acknowledge that Israel has nuclear weapons?” I’ve asked this of many political figures and virtually no one has given me a straightforward response.
-
The grubby underside of US electoral politics is on show once again as the Democratic and Republican candidates prepare to fight it out for the presidency. And it doesn’t get seamier than the battle to prove how loyal each candidate is to Israel.
New depths are likely to be plumbed this week at the Republican convention in Cleveland, as Donald Trump is crowned the party’s nominee. His platform breaks with decades of United States policy to effectively deny the Palestinians any hope of statehood.
-
As delegates at the Republican National Convention approved a platform banning women from combat, restricting a woman’s right to an abortion in cases of rape or incest, and without any mention of equal pay or paid family leave, Phyllis Schlafly looked on with a huge smile.
The notorious 91-year-old anti-feminist and RNC delegate sat in her wheelchair in the back of Missouri’s delegation, craning to get a look at Donald Trump as he entered the arena for the first time on Wednesday night. During the 1970s, Schlafly led the opposition to the Equal Rights Amendment, which would have amended the Constitution to ban discrimination based on gender. Schlafly, who has participated in every convention since 1952, told ThinkProgress that Trump is the candidate to best represent the needs of women from the White House. In fact, she said, there’s no need for a woman in the Oval Office at all.
-
On Wednesday, The Intercept published an article documenting the extraordinary journalistic fraud committed by Brazil’s largest newspaper, Folha de São Paulo, in radically distorting the views of Brazilians on the key questions of the country’s political crisis. Specifically, Folha blasted headlines to the country announcing that 50 percent of Brazilians now want the extremely unpopular interim president, Michel Temer, to complete Dilma’s term and remain as president through 2018, while only 3 percent favor new elections and only 4 percent want both Dilma and Temer to resign. That was squarely at odds with prior polling showing vast majorities opposed to Temer and favoring new elections. As we documented, the actual polling data — which Folha’s polling firm, Datafolha, only published days after the article — did not remotely support Folha’s claims.
But after our article was published, much more evidence was found — through amazing collaborative work by internet sleuths — showing how extreme Folha’s behavior was, including the discovery of a smoking gun proving that it was much worse than we knew when we published yesterday. Do not let the fact that this story involves polling data and methodologies obscure how significant this episode is:
Weeks before the conclusion of the country’s most virulent political conflict in at least a generation — the final Senate vote on Dilma’s impeachment — Folha, Brazil’s largest and most influential newspaper, not only distorted, but actively concealed, crucial polling data that completely negated what they “reported”: data that establishes that a large majority of Brazilians want “interim President” Michel Temer to resign, not remain in office as the paper claimed. Put simply, this is one of the most remarkable, flagrant, and serious cases of journalistic malfeasance one can imagine.
[...]
Most amazingly of all, this was all done in service of denying the need for democracy: deceiving the country into believing that most Brazilians support the person who seized power undemocratically and that there is no need for elections, when in fact the majority of the country wants this “interim President” to quit and new elections to be held to choose the legitimate leader.
As we noted yesterday, it’s impossible to say whether Folha acted with deliberate intent to deceive or with extreme journalistic ineptitude and recklessness, although evidence suggesting the former is certainly more abundant now than it was yesterday. But motives aside, what is now beyond debate is that Folha misled the country in fundamental ways about this generation’s most consequential political conflict, and hid from the public vital evidence that they only admitted existed once they got caught red-handed doing all this.
-
Censorship/Free Speech
-
Even as newspaper printing resumed in the Kashmir valley on Wednesday after four days, a group of journalists who gathered here for a panel discussion condemned the alleged ban as a gag on the freedom of speech and expression.
They also said that coverage by a certain section of the media was alienating the local population even further.
During the panel discussion, Rahul Jalali, president of Press Club of India said, “It was one of the most bizarre incidents of censorship that took place in the country. As of now no assurance has been given to the journalists that they are free to function and would not be touched hereafter.”
-
-
Early this year, in February, the who’s who of Delhi journalism had assembled at the Press Club of India, at Raisina Road, to defend their right to report. The reason was the attack on journalists who were covering the Jawaharlal Nehru University sedition case at the Patiala House Court.
Almost five months later, a motley group of journalists gathered at the same venue for same reasons – except this time, the attack was not on Delhi media but a ban on Kashmiri media. Barely 10 journalists sat on a dharna at about 1pm at the press club with the placard: “Journalists with Kashmir”.
-
Thailand’s military-backed government has authorized the National Broadcasting and Telecommunications Commission (NBTC) to shut down TV and radio stations which are found guilty of broadcasting programs that threaten national security. Furthermore, the junta gave NBTC officials immunity from legal accountability.
Human rights groups believe this ruling aims to prevent activists and other political forces from campaigning against the approval of a draft constitution in a national referendum scheduled for August 7.
-
Censorship must be resisted on all fronts, at all times, wherever conflict occurs. Nowhere is that message more important than in our schools, and that’s why we applaud a newly re-introduced bill aimed at preventing administrative censorship of student newspapers.
The bipartisan legislation sponsored by Assembly members Gail Phoebus, R-Sussex, and Troy Singleton, D-Burlington, would be similar to a Maryland initiative that has already been signed into law. It is rooted in concerns that oversensitive school officials have been preventing student publications from using certain stories of which they disapprove. That’s insufficient cause to ignore First Amendment principles, and the bill would forbid any requirement that all content be subject to administrative review before publication.
-
THE SABC’s protest footage ban is just one of a slew of policies and “draconian anti-journalistic practices” at the public broadcaster, one of the fired journalists said on Thursday.
“You can withdraw the protest policy but you still have an environment that is not conducive to the practice of ethical journalism in the SABC,” Thandeka Gqubule said.
-
Serbia’s ruling populists have created an exhibition highlighting media critical of their leader and his government in a bid to counter mounting allegations of censorship in the Balkan country, which is seeking EU membership
-
We are excited to announce that Onlinecensorship.org, a joint project of EFF and Visualizing Impact, is now available in Spanish. Onlinecensorship.org seeks to expose how social media sites moderate user-generated content. By launching the platform in the second-most widely spoken language in the world, we hope to reach several million more individuals who’ve experienced censorship on social media. Now, more users than ever can report on content takedowns from Facebook, Google+, Twitter, Instagram, Flickr, and YouTube and use Onlinecensorship.org as a resource to appeal unfair takedowns.
-
In Venezuela, at least 372 web portals have been blocked by main Internet service providers (ISP). Also, 43 Internet domains have been blocked by these same providers, both public and private.
Of those, 44 percent are web pages related to black market dollars. An additional 19 percent of the pages are news media and an additional 12 percent feature blogs critical of Nicolás Maduro’s administration.
-
-
-
-
-
-
-
Privacy/Surveillance
-
In early 2012, Marie Colvin, an acclaimed international journalist from New York, entered the besieged city of Homs, Syria while reporting for London’s Sunday Times. She wrote of a difficult journey involving “a smugglers’ route, which I promised not to reveal, climbing over walls in the dark and slipping into muddy trenches.” Despite the covert approach, Syrian forces still managed to get to Colvin; under orders to “kill any journalist that set foot on Syrian soil,” they bombed the makeshift media center she was working in, killing her and one other journalist, and injuring two others.
Syrian forces may have found Colvin by tracing her phone, according to a lawsuit filed by Colvin’s family this month. Syrian military intelligence used “signal interception devices to monitor satellite dish and cell phone communications and trace journalists’ locations,” the suit says.
In dangerous environments like war-torn Syria, smartphones become indispensable tools for journalists, human rights workers, and activists. But at the same time they become especially potent tracking devices that can put users in mortal danger by leaking their location.
National Security Agency whistleblower Edward Snowden has been working with prominent hardware hacker Andrew “Bunnie” Huang to solve this problem. The pair are developing a way for potentially imperiled smartphone users to monitor whether their devices are making any potentially compromising radio transmissions. They argue that a smartphone’s user interface can’t be relied to tell you the truth about that state of its radios.
-
When the federal government takes the rare step of fining medical providers for violating the privacy and security of patients’ medical information, it issues a press release and posts details on the web.
But thousands of times a year, the Office for Civil Rights of the U.S. Department of Health and Human Services resolves complaints about possible violations of the Health Insurance Portability and Accountability Act quietly, outside public view. It sends letters reminding providers of their legal obligations, advising them on how to fix purported problems, and, sometimes, prodding them to make voluntary changes.
-
Internet of Things technology holds the potential to revolutionise the healthcare industry, but not before overcoming barriers of security and data ownership.
Internet of Things (IoT) refers to any physical object embedded with technology capable of exchanging data and is pegged to create a more efficient healthcare system in terms of time, energy and cost. One area where the technology could prove transformative is in healthcare – with analysts at MarketResearch.com claiming the sector will be worth $117 million by 2020.
-
With everything else that has been happening in the UK and abroad over the past month you could be excused for missing a House of Lords debate over the Investigatory Powers Bill last week.
With the majority of the country distracted by Brexit and the upheaval among the two major political parties – including the former Home Secretary and architect of the controversial Bill Theresa May becoming the UK Primer Minister – this vital legislation has not been quite so high on the news agenda.
However, discussions around encryption at the 13 July Investigatory Powers Bill committee stage debate could have a huge impact on personal and enterprise data security – in particular the ability to ban end-to-end encryption. You can read the entire debate here.
-
Since December last year, the government’s Investigatory Powers Bill has sparked debate over the balance between privacy concerns and national security in the post-Snowden era, with controversy around encryption, bulk data and hacking being aimed at the former home secretary Theresa May.
-
When historians look back at the turmoil over prejudice and policing in the U.S. over the past few years, they’re unlikely to dwell on the case of Eric Loomis. Police in La Crosse, Wis., arrested Loomis in February 2013 for driving a car that was used in a drive-by shooting. He had been arrested a dozen times before. Loomis took a plea, and was sentenced to six years in prison plus five years of probation.
The episode was unremarkable compared with the deaths of Philando Castile and Alton Sterling at the hands of police, which were captured on camera and distributed widely online. But Loomis’s story marks an important point in a quieter debate over the role of fairness and technology in policing. Before his sentence, the judge in the case received an automatically generated risk score that determined Loomis was likely to commit violent crimes in the future.
-
Rail passengers could be forced to pay more to stand on packed trains as the country’s biggest train ticket website plans to monitor their movements to “ease congestion”.
Clare Gilmartin, chief executive of the Trainline, told The Telegraph that the website was planning to use GPS technology installed within its app constantly to let rail firms update ticket prices, under a scheme which could be rolled out in less than two years.
-
UK GOVERNMENT plans to retain communications data do not sit well with the European Court of Justice, which has warned that such plans should not be rushed through.
Advocate general Henrik Saugmandsgaard Øe and his peers have issued their opinion on British and Swedish plans to make communications providers sit on customer data for an extended period of time.
-
Over at the EU Court of Justice, the Advocate General has weighed in on the legal challenge to DRIPA, the Data Retention and Investigatory Powers Bill (DRIPA) that was rushed through the UK Parliament almost exactly two years ago. The law was challenged by a group made up of cross-party Parliament Members, and the Advocate General has sort of punted on the issue. If you don’t recall, the Advocate General’s role in the EU Court of Justice is basically to make a recommendation for the actual rulings. The court doesn’t have to (and doesn’t always) follow the Advocate General’s suggestion, but does so often enough that the opinions certainly carry a lot of weight and suggest what’s likely to happen. In this case, the opinion stated that, even though the court had previously rejected the EU-wide Data Retention Directive as intruding on privacy — the UK’s data retention law might be okay.
The opinion basically says some data retention laws may be okay if the powers are “circumscribed by strict safeguards” set up by the national courts.
-
The Marine Corps and National Security Agency have joined forces to bring cellphones to the battlefield by 2019. Working with the NSA’s new Commercial Solutions for Classified (CSfC) program should let the Marines acquire cutting-edge civilian technology swiftly without sacrificing security, said Maj. Kevin Shepherd of Marine Corps Systems Command.
-
It is 949 years since a global flood of biblical proportions. The world is reliant upon a vast grid of solar panels to power its factories around the clock. Night-time has been consigned to legend. In the aftermath of environmental catastrophe, the world’s clean water is now confined to a network of towers built by the world’s richest man.
While the dystopian scenario of Ganzeer’s debut graphic novel, The Solar Grid, is science fiction, the story is rooted in history, political and personal. The Egyptian artist, best known for murals that championed the spirit of the 2011 Cairo revolution, took inspiration from his first sighting of the Nile’s Aswan dam. As child, he felt awe. Today, Ganzeer sees the environmental impact of the dam on Egypt as emblematic of humanity’s adverse impact across the whole planet.
-
A former division chief for the National Security Agency was sentenced to prison on Tuesday for causing the 2014 death of his 3-year-old adopted special needs son by throwing him against a wall, PEOPLE confirms.
-
What’s up with Brazilian judges not understanding Whatsapp? In the last few months, judges keep freaking out that Whatsapp messages are end to end encrypted, and that the company is unable to decrypt them at all. On Tuesday morning, the news broke that Judge Daniela Barbosa had ordered Whatsapp blocked yet again, along with a $50,000 per day fine until it decrypts information that it cannot decrypt. While various ISPs set about blocking the extremely popular app, as with the previous times, it took only a few hours for a higher court to suspend Barbosa’s ruling, and to make the app available again.
Of course, this is the third time that Brazilian courts have done this particular dance. It happened in December and again in May. And who can forget the time in March where a Brazilian judge ordered a Facebook exec arrested over the same issue (Facebook owns Whatsapp).
-
In the same month as Microsoft announced its alpha WebRTC-based Skype for Linux, Redmond has put it and the native OS X Skype client on the end-of-life list due to a rebuild for Skype that will replace its peer-to-peer architecture with cloud-centric code.
-
Thiel has also postured as a libertarian, and even as his ideology shifts toward something more nihilistic — The Economist now calls him a “corporate Nietzschean” — he continues to rail against government programs like Medicare and Social Security. Meanwhile, he is chairman and co-founder of Palantir Technologies, a mass-surveillance-software company that makes a good deal of its money selling to the government; Palantir’s clients reportedly include the Department of Defense (including the NSA and various military branches), the Department of Homeland Security, the FBI, and the CIA. Thiel is, inexplicably, pro-monopoly. And don’t forget that Peter Thiel believes death is nothing but a bug in the feature set of mankind, and one he can buy his way out of.
-
Civil Rights/Policing
-
An autistic man’s therapist was shot and wounded by police in Florida while lying on the street with his hands in the air.
Charles Kinsey, who works with people with disabilities, was trying to get his 27-year-old patient back to a facility from where he wandered, North Miami assistant police chief Neal Cuevas told the Miami Herald.
Cuevas said police – who were responding to reports of a man threatening to shoot himself – ordered Kinsey and the patient, who was sitting in the street playing with a toy truck, to lie on the ground.
Kinsey, who is black, lay down and put his hands up while trying to get his patient to comply. An officer fired three times, striking Kinsey in the leg, Cuevas said. No weapon was found on either Kinsey or his patient.
-
Search through all of our stories about the supposed link between violent movies and games and real world violence by those that enjoy them, and you should come away with the impression that, at the very least, the science isn’t settled on the issue. The more specific impression you should get is that violent media might — might — have a short-term impact on behavior, but that there isn’t anything like a general agreement on the long term effects, which is obviously the vastly more important question.
-
While I think that Senator Patrick Leahy has been ridiculously and dangerously wrong on copyright issues for years, he’s actually quite good on a number of other issues that are of interest to us here at Techdirt. In particular, he’s been a strong supporter of civil liberties on the internet and protecting the 4th Amendment (it’s unfortunate that he doesn’t see how his desired copyright policies might undermine some of that, but that’s another post for another day). Thankfully, his latest move is to push back against a plan by the Senate and House Intelligence Committees to strip the federal government’s Privacy and Civil Liberties Board (PCLOB).
Back in May, we wrote about this effort, whereby Congress appeared to be deliberately stripping powers from the PCLOB in order to limit the board’s ability to actually make sure that the intelligence community wasn’t abusing its powers. Senator Leahy has now sent a fairly direct letter to Senate Intelligence chair Senator Richard Burr and vice chair Senator Dianne Feinstein calling out how terrible this plan is.
-
More than 50,000 people have been rounded up, sacked or suspended from their jobs by Turkey’s government in the wake of last week’s failed coup.
The purge of those deemed disloyal to President Recep Tayyip Erdogan widened on Tuesday to include teachers, university deans and the media.
The government says they are allied to US-based cleric Fethullah Gulen, who denies claims he directed the uprising.
-
Turkey’s president has declared a state of emergency for three months following a failed coup to oust his government.
President Recep Tayyip Erdogan said the measure was being taken to counter threats to Turkish democracy. He said the move was not intended to curb basic freedoms.
Speaking after a meeting of the National Security Council in Ankara lasting nearly five hours, he said the state of emergency was needed “to remove this threat as soon as possible”.
-
Bush administration lawyers made the law into a joke, and no one has been held accountable.
In response to an ACLU Freedom of Information Act lawsuit, the government has released several documents that shed new light on Bush administration lawyers’ attempts to evade the absolute prohibition on torture and abuse of prisoners. The documents concern the widely-discredited legal process that purported to authorize the CIA to commit war crimes and include shocking new details.
One revelation is an email by John Rizzo, the CIA’s acting general counsel, which displays the ways in which government lawyers actively undermined the laws they were sworn to uphold. Rizzo, a key architect of the torture program, has claimed, “[M]y major concern as the chief lawyer was: Were these techniques legal?”
-
Cleveland Police Chief Calvin Williams issued a warning to an undisclosed number of masked protesters outside the Republican National Convention: “If you are a member of a group that causes you to have to hide your face, then you probably need a different cause.”
-
Cole will oversee the ACLU’s Supreme Court practice and the work of the organization’s nearly 300 lawyers
We’re excited to tap David Cole, a leading constitutional law expert and litigator, to become our National Legal Director, leading our Supreme Court practice and overseeing the work of the organization’s nearly 300 lawyers. The ACLU has participated in nearly every landmark case involving political expression, freedom of the press, speech on the internet, and separation of church and state in the U.S. Supreme Court during the last 96 years. Cole will replace Steven R. Shapiro, who has served as National Legal Director for a quarter century.
In his role as National Legal Director, Cole will direct a program that includes approximately 1,400 state and federal lawsuits on a broad range of civil liberties issues. He will directly manage 100 ACLU staff attorneys in New York headquarters, oversee the organization’s U.S. Supreme Court docket, and provide leadership to more than 200 staff attorneys who work in ACLU affiliate offices in all 50 states, Puerto Rico, and Washington, D.C. Another 1,700 volunteer cooperating attorneys throughout the country are engaged in ACLU litigation. With an annual headquarters budget of $140 million, and 1.3 million supporters, the ACLU is the nation’s largest and oldest civil liberties organization.
-
We discuss the killing of three police officers in Baton Rouge and the recent nationwide protests against police brutality with Cornel West. Cornel West is a professor at Union Theological Seminary. “When I hear the authorities call for peace,” West says, “I say, yes, but it’s not the absence of tension. It’s got to be the presence of that justice and accountability.”
-
Welcome to Cleveland, where the Republican National Convention (RNC) is underway. The RNC is a highly scripted, elaborately staged and lavishly publicly funded private party. Here, credentialed Republican delegates, most of them party activists from around the country, circulate within a militarized perimeter of what authorities have designated a “national special security event.” As such, the U.S. Secret Service is handed complete control of an area, in the case downtown Cleveland. The area is ringed with a temporary but imposing black steel fence, patrolled by the full spectrum of law enforcement, from local police to federal SWAT teams. Yet because Ohio has extremely lenient gun laws, people can “open carry” here. And they do. Scores of Trump supporters have proudly shown up with their guns at their sides, including semi-automatic AR-15s, walking the downtown streets.
It is not a total free-for-all, however. Many things are banned: tennis balls, sleeping bags, selfie sticks and canned goods. To highlight the absurdity of the situation, the women’s peace organization Code Pink staged a demonstration at the security checkpoint to enter the RNC. In their bags, the dozen or so pink-clad women carried 500 pink and green tennis balls with the phrase “Ban Guns, Not Balls” written on them. They began tossing them to each other.
A line of Cleveland police officers quickly formed and tried to encircle the protest. They started to confiscate the tennis balls. There was confusion, as one officer asked a superior, “What do we do with the balls?” “Put them in your pocket,” came the exasperated reply. The police aggressively expanded their line, pushing observers, and us journalists, farther away. We managed to dodge them and got in close to ask Code Pink member Chelsea Byers what was going on: “We’re here saying that it’s ridiculous that the RNC has banned tennis balls, and yet they continue to let open carry happen in these streets. If they’re concerned about safety, they should be taking the guns off of these streets, not banning toys.” To reinforce the Cleveland police, a large contingent of Indiana State Police showed up, then riot police were deployed. Finally, a phalanx of police on horseback arrived. All this for about 15 women and one man from Code Pink and their 500 tennis balls.
The second evening of the RNC was about to begin. Thousands were packing into the Quicken Loans Arena. For the first time ever, an official from the National Rifle Association was invited to address the convention.
Code Pink co-founder Medea Benjamin told us at the protest, “We think that the NRA has, unfortunately, been setting the agenda for this entire nation, especially the Republican Party. It’s unfortunate that the NRA has so much power in this country. That’s why we see guns on our streets and people being shot every single day, every single hour of every single day.” Eventually, with all the tennis balls safely confiscated, the police marched away.
-
Internet Policy/Net Neutrality
-
We’ve talked at great lengths about how AT&T’s gruesomely cozy relationship with many state legislatures has severely damaged broadband expansion and adoption across huge swaths of the country. That’s particularly true in Tennessee, one of nineteen states where AT&T lobbyists have literally written protectionist state laws defending AT&T’s monopoly from broadband competition. AT&T’s goal has been to stop the rise of public/private partnerships, which have only emerged as a direct response to AT&T’s apathy.
AT&T lobbyists have been happily getting such laws passed for fifteen years with little attention by the media. That began to change with the rise of efforts like Google Fiber, which more clearly illustrated how public/private partnerships have become essential in bringing broadband competition to countless areas incumbent ISPs deem “not profitable enough” to care about. Last year, the FCC finally woke up from its own long slumber on the subject, stating it would be preempting measures in two such state laws (in North Carolina and Tennessee) that hindered municipal broadband efforts from expanding.
Tennessee’s response? To sue the FCC — claiming that state rights were being violated (letting AT&T write bad state law? Perfectly ok, though).
-
AT THE heart of the internet are monsters with voracious appetites. In bunkers and warehouses around the world, vast arrays of computers run the show, serving up the web – and gorging on our data.
These server farms are the engine rooms of the internet. Operated by some of the world’s most powerful companies, they process photos of our children, emails to our bosses and lovers, and our late-night searches. Such digital shards reveal far more of ourselves than we might like, and they are worth a lot of money. They are not only used to target advertising and sell stuff back to us, but also form the building blocks for a new generation of artificial intelligence that will determine the future of the web.
“Very big and powerful companies own a huge chunk of what happens on the web,” says Andrei Sambra, a developer with the World Wide Web (W3) Consortium at the Massachusetts Institute of Technology, the main standards organisation for the web. But we – the ones producing this valuable data – have lost control.
The time has come to push back. Sambra is part of a growing movement to wrest back control over our digital lives by breaking the monopolies of the server farms and the people who own them. Tweak the technology on which the web runs and we can each keep our own little part of it in our pockets, they say – and determine who or what makes money out of who we are.
-
Intellectual Monopolies
-
The World Health Organization has issued updated information on the patent status of hepatitis C medicines, including assessments of hurdles for affordable generic versions of latest drugs.
-
The invention lay in the use of certain penetration-enhancing excipients which are solid at room temperature and were therefore thought to be of limited use in assisting diffusion out of the matrix into the skin. The patent disclosed that on melting and cooling, these excipients formed so called “supercooled melts”, which have a melting point above room temperature, but remain liquid after cooling to room temperature.
-
Trademarks
-
We talk a lot about silly trademark disputes here at Techdirt. But the really infuriating trademark stories tend to deal with not just overly broad terms that have been granted marks by the USPTO, but terms that are so broad because they are simple geographic identifiers. The other aspect of trademark disputes that can be face-palm inducing are claims of confusion that are laughable in the extreme. The dispute we’re about to discuss mixes both of these, supercharging the frustration to dangerous levels.
-
In the ongoing dispute between the Sparkassen Group and Banco Santander, which led to the CJEU’s decision in cases C‑217/13 and C‑218/13, the German Federal Court of Justice (BGH) has annulled the decision of the Federal Patent Court which invalidated Sparkassen’s contourless colour mark “red” and held that the mark had acquired distinctiveness at the time of the Federal Patent Court’s decision in 2015.
Sparkassen Group has been using the colour red in connection with financial services, namely retail banking, in Germany since the 1960s. In 2002, it filed a trade mark application for the contourless colour “red” (HSK 13) for financial services, namely retail banking, which was granted – after an initial rejection – sometime in 2007. Banco Santander and Oberbank, two new entrants to the German retail banking market that also used the colour red in their home markets, filed for invalidity. In 2009, the German IPO (DPMA) dismissed the actions. On appeal, the Federal Patent Court referred several questions to the CJEU, which the CJEU answered in joined cases C-217/13 and C-218/13 in 2014.
-
US Justice Department Nails Three In Mass Mailing #Trademark Scam http://www.ip-watch.org/2016/07/20/us-justice-department-nails-three-in-mass-mailing-trademark-scam/
-
Copyrights
-
Some day, your life may depend on the work of a security researcher. Whether it’s a simple malfunction in a piece of computerized medical equipment or a malicious compromise of your networked car, it’s critically important that people working in security can find and fix the problem before the worst happens.
And yet, an expansive United States law, passed in 1998 and emulated in legal codes all over the world, casts a dark legal cloud over the work of those researchers. It gives companies a blunt instrument with which to threaten that research, keeping potentially embarrassing or costly errors from seeing the light of day.
That law is Section 1201 of the Digital Millennium Copyright Act. Simply put, Section 1201 means that you can be sued or even jailed if you bypass digital locks on copyrighted works—from DVDs to software in your car—even if you are doing so for an otherwise lawful reason, like security testing.
-
Washington D.C.—The Electronic Frontier Foundation (EFF) sued the U.S. government today on behalf of technology creators and researchers to overturn onerous provisions of copyright law that violate the First Amendment.
EFF’s lawsuit, filed with co-counsel Brian Willen, Stephen Gikow, and Lauren Gallo White of Wilson Sonsini Goodrich & Rosati, challenges the anti-circumvention and anti-trafficking provisions of the 18-year-old Digital Millennium Copyright Act (DMCA). These provisions—contained in Section 1201 of the DMCA—make it unlawful for people to get around the software that restricts access to lawfully-purchased copyrighted material, such as films, songs, and the computer code that controls vehicles, devices, and appliances. This ban applies even where people want to make noninfringing fair uses of the materials they are accessing.
Ostensibly enacted to fight music and movie piracy, Section 1201 has long served to restrict people’s ability to access, use, and even speak out about copyrighted materials—including the software that is increasingly embedded in everyday things. The law imposes a legal cloud over our rights to tinker with or repair the devices we own, to convert videos so that they can play on multiple platforms, remix a video, or conduct independent security research that would reveal dangerous security flaws in our computers, cars, and medical devices. It criminalizes the creation of tools to let people access and use those materials.
-
Section 1201 of the Digital Millennium Copyright Act forbids a wide range of speech, from remix videos that rely upon circumvention, to academic security research, to publication of software that can help repair your car or back up your favorite show. It potentially implicates the entire range of speech that relies on access to copyrighted works or describes flaws in access controls—even where that speech is clearly noninfringing.
At EFF, we’ve been worried about this law since before it was passed. We were counsel in one of the first major tests of the law, but in those early days, we failed to convince the courts of its dangerous risk to speech. Ever since, we’ve documented those speech consequences. We’ve called on Congress to reform the law, to no avail. So today, we’re going to back to court, armed with nearly twenty years of knowledge about Section 1201’s interference with lawful speech and with key Supreme Court cases that have been decided in that time. For more about the problems caused by this law, see our companion post on the issue.
Section 1201 was billed as a tool to prevent infringement by punishing those who interfered with technological restrictions on copyrighted works. After the DMCA was passed, the Supreme Court was asked to evaluate other overreaching copyright laws, and offered new guidance on the balance between copyright protections and free speech. It found that copyright rules can be consistent with the First Amendment so long as they adhere to copyright’s “traditional contours.” These contours include fair use and the idea/expression dichotomy.
-
It looks like the world’s most popular torrent website KickassTorrents is back with a new domain dxtorrent.com. The website features the same layout and seems like a mirror of notorious torrent sharing website KAT. The original KickassTorrents domain was recently seized by the U.S. Government.
-
Copyright rulings in France have occasionally been a complete disaster in the past, so it’s nice to see the High Court of Paris recognize that Google and Microsoft cannot be forced to block any searches that include the word “torrent.” The two separate lawsuits were brought by SNEP, which could be seen as the French version of the RIAA. The organization argued that since the law allowed “all appropriate measures” to be used to block infringement, it could demand that search engines block any searches that include the word torrent.
-
Because Steele and Hansmeier can’t help themselves, they appealed again, leading to this latest ruling. Believe it or not, Steele actually may be temporarily happy with this latest ruling as he actually won on one point (but may lose even bigger in the long run). Still, the court is clearly not happy with either Steele or Hansmeier. It does note that since Hansmeier has filed for a (highly questionable) bankruptcy, he cannot pursue the appeal and thus his appeal is dismissed out of hand.
-
-
-
-
-
KickassTorrent, the world’s most popular torrent website, has faced a major setback. The U.S. Government has arrested the alleged owner of the website and seized all of its domains.
-
If you only listened to entertainment industry lobbyists, you’d think that music and film studios are fighting a losing battle against copyright infringement over the Internet. Hollywood representatives routinely tell policymakers that the only response to the barrage of online infringement is to expand copyright or even create new copyright-adjacent rights.
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 2:44 am by Dr. Roy Schestowitz

Contents
-
It started back in 2009, the first year of Lynn Bender’s fantastic brainstorm “Linux Against Poverty.” Lynn’s idea and subsequent involvement with our organization, then named The HeliOS Project, would infuse our effort with an energy and inventory we still rely on today.
-
Desktop
-
Make no mistake about it. The 2016 Dell XPS 13 Developer Edition laptop is wonderful. It’s fast, its display is gorgeous, and, at less than three pounds, you can carry and code with it anywhere. But, oh, that price tag!
-
About 15 months ago, I reviewed Fedora 21 on the ASUS Zenbook UX305. As happy as I have been with that machine, a new year came along and I had the opportunity to pick up a new personal laptop. I found myself deciding between three models: the Dell XPS 13 Developer Edition, the ASUS Zenbook UX305UA, and the Lenovo Thinkpad T460s.
-
Microsoft broke my father’s computer: it made him update to Windows 10, when Windows 10 can not use two of 3 USB ports. Ouch.
-
Server
-
As I write this, I’m using Roon Server to play “Blue Moon” about my room, soon after noon. If you’re reading that, then by some miracle, all my editors laughed instead of cringed, and I can now safely relate to you what Roon Server is all about, and why you might want it. (Right after I have a macaroon.) You can read our full review here.
Crumbs swept aside…. Roon is the Stradavarius or Guarnerius of audio streaming, cataloging, and transcoding. Think of it as iTunes and Windows Media Player on steroids. Until recently, however, you had to keep a PC (or Mac, or Linux box) running 24/7 as a Roon server if you wanted to listen to your tunes any time you felt the urge. Now you can use a far more convenient-for-the-task NAS box.
-
-
A new cloud environment for business-to-business networks announced by IBM last week will allow companies to test performance, privacy, and interoperability of their blockchain ecosystems within a secure environment, the company said. Based on IBM’s LinuxONE, a Linux-only server designed for high-security projects, the new cloud environment will let enterprises test and run blockchain projects that handle private data for their customers.
The service is still in limited beta, so IBM clients will not be able to get their hands on it just yet. Once it launches, however, the company said clients will be able to run blockchain in production environments that let them quickly and easily access secure, partitioned blockchain networks.
-
Kernel Space
-
Congratulations are due to Alan Cox, who was awarded an honorary degree by Swansea University for his work with Linux. “Alan started working on Version 0. There were bugs and problems he could correct. He put Linux on a machine in the Swansea University computer network, which revealed many problems in networking which he sorted out; later he rewrote the networking software. Alan brought to Linux software engineering discipline: Linux software releases that were tested, corrected and above all stable. On graduating, Alan worked at Swansea University, set up the UK Linux server and distributed thousands of systems.”
-
Graphics Stack
-
-
Today’s the day that we can finally publish NVIDIA GeForce GTX 1060 benchmarks! Today the GTX 1060 begins shipping as NVIDIA’s $249 Pascal graphics card to take the Radeon RX 480 head-on. Here are all of the Linux benchmarks you’ve been waiting to see for the GTX 1060 under Vulkan, OpenGL, OpenCL, and CUDA. compared to various other AMD Radeon and NVIDIA GeForce GPUs on Ubuntu Linux.
-
-
While there’s been no new communication about X.Org Server 1.19, the X.Org Server 1.18.4 release is now available.
-
-
Don’t panic. Of course it isn’t. Stop typing that angry letter to the editor and read on. I just picked that title because it’s clickbait and these days that’s all that matters, right?
-
With this week’s release of libinput 1.4, Peter Hutterer has announced “libinput is done”, at least in terms of its original goal.s
Peter proclaiming “libinput is done” just comes in regards to the project’s original TODO list from when this input library was first conceived for Wayland’s needs. That list included keyboard support, touchscreen handling, support for mice, touchpad support, graphics tablet support, track sticks, a reliable test suite, proper documentation, and more.
-
Benchmarks
-
To complement yesterday’s launch-day GeForce GTX 1060 Linux review, here are some more benchmark results with the various NVIDIA x60 graphics cards I have available for testing going back to the GeForce GTX 460 Fermi. If you are curious about the raw OpenGL/OpenCL/CUDA performance and performance-per-Watt for these mid-range x60 graphics cards from Fermi, Kepler, Maxwell, and Pascal, here are these benchmarks from Ubuntu 16.04 Linux.
-
Applications
-
-
Cumulus is a stylish desktop weather app for the Ubuntu desktop. It offers various settings, including an optional Unity Launcher temperature count.
-
The Fedora Workstation has a number of features in the GNOME desktop environment to conserve power and increase security. These are both important considerations for desktop and laptop users. One of these features is the automatic screensaver lock function. By default, if idle for 5 minutes, the screen locks. This causes two things to happen:
-
Good news everyone! A new release of USBGuard is finally available. As usual there are many bugfixes, several new features and some other changes. USBGuard has gotten a D-Bus component so the integration possibilities are endless now  The usbguard-applet-qt subproject was merged into the main project repository. Thanks to that it will hopefully receive more love in the near future. One of the more important bugfixes delivered by this release is the rewrite of the USB descriptor parsing code which previously didn’t work correctly for many devices.
The usbguard-applet-qt subproject was merged into the main project repository. Thanks to that it will hopefully receive more love in the near future. One of the more important bugfixes delivered by this release is the rewrite of the USB descriptor parsing code which previously didn’t work correctly for many devices.
-
Proprietary
-
Non-Linux FOSS: Caffeine! [Ed: Promoting proprietary software not for GNU/Linux, which is odd for Linux Journal]
Okay, this program is free (beer), but not Free (speech). I wouldn’t normally include a freeware application in a “Non-Linux FOSS” piece, because quite frankly, it isn’t FOSS. But, I decided to break the rules a bit here because I realized how often I use a freeware program when I’m on OS X that I couldn’t imagine doing without.
-
Skype for Linux Alpha Draws Cheers, Jeers [Ed: When Microsoft bought Skype it had a lot less intrusive surveillance and decent GNU/Linux support. Not anymore.]
Many Linux users have voiced comments critical of Microsoft’s effort.
-
-
Instructionals/Technical
-
Games
-
Virtual Programming has announced the release date of Overlord (tomorrow!) with a new teaser video. Will be interesting to see how it performs.
-
Still, it’s weird they put up some sort of Beta on Steam for Linux with a title of “Help test the mac and linux releases!” (see it here) if they are just going to release it in a few days anyway. I should note you aren’t able to install that beta, as it complains it’s not available on your platform.
-
Stardew Valley is finally getting Mac and Linux compatibility, developer Eric “ConcernedApe” Barone said on Twitter. The game is set to arrive on both systems next Friday, July 29.
-
Stardew Valley is one of those games I’m bound to keep buying as it shows up on more platforms. I can’t help it! The pleasant farming life simulator has this soothing quality that’s just so appealing.
-
-
ConcernedApe, the developer behind Stardew Valley has revealed that the Steam indie hit will be finally coming to Mac and Linux. The info was released on the developer’s Twitter Page this morning with the announcement that it will be releasing on these platforms as soon as July 29. It is also noted that this game is still scheduled for console releases this winter for Wii U, PlayStation 4, and Xbox One. The game’s publisher, Chucklefish, will be handling the Mac and Linux ports.
-
Just one day after Virtual Programming released a new teaser video for Overlord on Linux, the OSX/Linux game porting company announced their release date for the game that is coming to Linux and Mac,
-
I have been waiting and attempting to be patient on this, Stardew Valley has now popped up on SteamDB with a Linux/Mac testing branch.
We already knew it was coming to Linux, but I hadn’t seen anything to indicate a release. It is now showing up on SteamDB. It still doesn’t mean it’s soon, even with the developer claiming back in June it would be “very soon” it’s over a month later and it’s only just popping up in a test branch on SteamDB.
-
Blossom Tales is a rather good looking Zelda-like action RPG that has been Greenlit to be on Steam and it’s heading to Linux.
-
-
-
The good news, according to this recent tweet by John Romero, is that allegedly the patch is in a such advanced stage that now you should be able to play the game on Linux without any problem.
-
We should see this coming by now. The Cossacks 3 release date has been announced and I have it confirmed personally that the Linux release is now delayed.
-
Virtual Programming has been working on porting Overlord I and Overlord II to Linux and Mac. They have just released another teaser video, perhaps indicating the ports are almost ready to ship.
Overlord is an action role-playing game first released back in 2007 and its Overlord: Raising Hell expansion having been releasedi n 2008. To date the game has just been supported on Windows and the PlayStation 3 and Xbox 360 while Virtual Programming LTD is bringing the game to Linux and Mac OS X.
-
Right after the bad news about Cossacks 3 being delayed, we have some nicer news. Virtual Programming are teasing the Linux port of Overlord in a new video.
-
This is weird. The developer of VIDEOBALL has stated that they want a Linux & Mac version, but told people essentially it’s the publisher who needs to be spoken to about it.
-
As promised, the Linux pre-alpha demo of the System Shock remake is now available to download from GOG.
-
-
Antraxx is a very interesting looking massively multiplayer mech shooter and the programmer has stated to me that Linux is a definite option.
-
Rogue Islands is a pretty good looking fast-paced shooter with blocky graphics will come to Linux and it looks good.
-
Desktop Environments/WMs
-
GNOME Desktop/GTK
-
Last Month Cosimo came Beijing, and we had a meet up with Beijing GNOME User Group and Beijing Linux User Group in SUSE Office, Cosimo introduced ‘Looking ahead to GNOME 3.22 and beyond’, the flatpak bring lots of attention. Here I just shared some photos. Thanks for Cosimo’s coming!
-
-
With extraction support in Nautilus, the next feature that I’ve implemented as part of my project is automatic decompression. While the name is a bit fancy, this feature is just about extracting archives instead of opening them in an archive manager. From the UI perspective, this only means a little change in the context menu:
-
Nautilus, the GNOME file manager, is to improve support for extracting zips, tars and other compressed archives.
-
In Diana’s usability test, she will moderate a “first experience” of GNOME. Testers will login to GNOME using a fresh “test” login, and go through the first-time experience. The testers will use a few scenario tasks to guide them through tasks that most users would usually do on a new computer (check email, copy files from a USB stick). Afterwards, Diana will interview each tester to see what they thought.
-
-
A ton of patches hit GNOME’s Mutter this morning by Jonas Ådahl as he’s been working towards multi DPI rendering and other improvements by drawing monitor contents to individual frame-buffers.
Jonas has been reworking Mutter to draw monitor contents to individual frame-buffers rather than targeting a single frame-buffer, in order to support situations of having multiple monitors with a desire to have independent DPI changes for each display (e.g. one HiDPI display and other displays that are not), etc. Jonas summarized it with this bug report.
-
-
Linux is turning 25 this year. Since its inception in 1991, what started as a “modest new OS” has ballooned into a juggernaut with 258 distributions.
To celebrate Linix’s big birthday, I have gathered together 25 pictorial representations of Linux distributions. Given a visual clue and a very brief description, how many of the Linux distributions represented here can you identify?
-
New Releases
-
PCLinuxOS/Mageia/Mandriva Family
-
Good news from OpenMandriva Community!
A while after Beta2 we are glad to announce OpenMandriva Lx 3.0 RC1 release.
Work for the RC1 has further improved stability and performance. We have now support for the Japanese and Chinese languages so we would really welcome any feedback from those who speak them.
-
-
Jim Dean today announced the release of Fedora-based Korora 24, following just one day after their EOL announcement for version 22. Kate Lebedeff announced the release of OpenMandriva Lx 3.0 RC1 today with Linux 4.6.4, Xorg 1.18.3, and KDE 5.6.5. Two reviews of the 2016 Dell XPS 13 landed today praising the newest Ubuntu laptop and Sandra Henry-Stocker continued celebrating Linux’ 25th birthday with a fairly tough quiz.
-
OpenSUSE/SUSE
-
There is a lot of excitement around the latest openSUSE Tumbleweed snapshots because of new KDE features and the newest stable Linux Kernel, which is expected in the next snapshot.
Snapshot 20160715 brought all those KDE updates Tumbleweed users were looking forward to like Framework 5.24.0, Plasma 5.7.0 and Applications 16.04.3. Breeze icons have a new feature and there is now jump list actions for tasks within an application available with KRunner thanks to the new Plasma. There is plenty of other new features with Plasma 5.7, so check out the video to see what is new.
-
SUSE today introduced a new program that allows resellers of SUSE subscriptions to host SUSE software products on behalf of their end-user customers, providing more flexibility to both resellers and end customers as they extend the benefits of SUSE products beyond customers’ on-site data centers.
“Many of our customers are finding value in partnering with a managed cloud provider so they can stay fast and lean and focus their limited resources on their core business and on driving innovation,” said Ronald de Jong, president of sales at SUSE. “SUSE Reseller Hosting enables our reseller partners to easily create new offerings to serve these customers within their existing SUSE partnership framework, while growing the important relationships our SUSE end-user customers rely on.”
-
In this years edition of Google Summer of Code, an international annual program in which stipends are awarded to students to hack on Free Software during the summer, openSUSE members are mentoring seven students who all passed their mid-term evaluation last week. Go on to read what they have to say about their first 10 weeks in the program.
-
Red Hat Family
-
-
Red Hat has given its Ansible Tower a good scrubbing down before smoothing the UI to better penetrate big money corporate accounts.
Tower is Red Hat’s paid for version of the open source Ansible automation platform, effectively a GUI and services package around the core product. Well, we say GUI, but Tower 3.0, released today, has taken a long hard look at the UI, and decided it needed fixing.
Red Hat’s head of Ansible engineering, Tim Cramer said that to date, Tower had been “designed by engineers, for engineers.” He added, “It’s crucial we don’t have people being confused when they start using tower. Hence, 3.0 has a more streamlined interface when it comes to complex deployments.
Following with the complexity/confusion theme, permissioning has been overhauled, making it easier to enact explicit permissions for specific teams or organisations.
Cramer also highlighted increased networking support, with support from Cisco, Juniper, Arista and Cumulus. This essentially builds on the networking integration added with the last major update of the core Ansible platform back in February.
-
Red Hat, Inc. (NYSE: RHT), the world’s leading provider of open source solutions, today announced the general availability of Ansible Tower 3, the latest version of its enterprise-grade agentless automation platform. Ansible Tower 3 by Red Hat gives teams the power to scale automation across the enterprise including streamlined interface, more powerful notifications, and explicit permissioning. Ansible Tower empowers users to extend their automation solutions to their entire team, so they can build, share and scale automation cross-functionally and consistently as they build out their DevOps capabilities.
-
-
Croatia-based system integrator and IT services provider Combis has become a RedHat Advanced Business Partner. RedHat is a US manufacturer of open source solutions aimed at companies of all sizes and from all industries. In order to earn the new status, Combis had to meet a number of criteria to demonstrate competence and ability, from participating in numerous professional trainings, adopting various technical and sales certifications and involvement in the presentation of Red Hat technologies.
-
They are based around the Cavium ThunderX processors that we’ve had at Red Hat for a while so they should run RHEL either out of the box or very soon after release.
-
-
Finance
-
Fedora
-
While there are many Linux-based operating systems to choose from nowadays, not all of them are great. Quite frankly, there are probably only a handful of distributions that I would truly recommend.
My absolute favorite Linux-based operating system is Fedora, but understandably, it is not ideal for all beginners. While I like the focus on free software only, some folks need some non-free stuff. Adding repos and setting up some of this software can be tricky for some. Luckily, Korora is a distro that takes the work out of setting up Fedora for beginners. Today, it achieves version 24, code-named ‘Sheldon’.
-
The Korora Project has released version 24 (codename “Sheldon”) which is now available for download.
-
The universal package is the future of Linux and both Canonical and Red Hat have their own take. Which is the better solution? Or should there be a third?
-
The 2016 July cycle of Elections is in full swing. Voting officially began on Tuesday, July 19, and ends Monday, July 25th at 23:59 UTC. Voting takes place on the Voting application website. As part of the Elections coverage on the Community Blog, most of the candidates running for seats published their interviews and established their platforms here. Are you getting ready to vote and looking for this information? You can find the full list of candidates and links to their interviews below.
-
I am happy to release the F24-20160720 updated lives isos.
as always these respins can be found at http://tinyurl.com/Live-respins2
Using the updated isos will save about 500M of updates after install YMMV (Gold MATE install updates as of 20160720 is 513M)
I would like to thank the community and the seeders for their dedication to this project.
-
If you’ve been involved in free and open source projects like Fedora for very long, you know one of the most sought-after “swag” items is a t-shirt with your projects’ logo. Until now, the easiest way to get a Fedora T-shirt has been to go to a big event like Flock, or through events organized & supported by our Fedora Ambassadors around the world.
-
Simply put, I have been actively involved and an active user of Fedora for about 4.5 years. I have been, almost exclusively, a Linux user for 10 years and I had dabbled in Linux before that. I have been a Linux sysadmin and a Linux developer (mostly a developer) for approximately 15 years.
-
As of July 19, 2016, Fedora 22 has reached its end of life for updates and support. No more updates, not even security fixes, will be provided for Fedora 22. Fedora 23 will be maintained with updated packages until approximately one month after the release of Fedora 25.
Upgrading to Fedora 23 or Fedora 24 is highly recommended for all users still running Fedora 22. For more information on upgrading Fedora, check out the DNF System Upgrade page on the Fedora Project wiki.
-
Debian Family
-
This is by no means the end of the Debconf16 experience, but actually the starting. I hope to share more of my thoughts, ideas and get as much feedback from all the wonderful people I met during Debconf.
-
-
Derivatives
-
It seems like every article one reads about the Raspberry Pi always makes a reference to Raspbian. If not, then the writer will probably write about how wonderful Ubuntu MATE is on the Raspberry Pi. Which begs the question: Are there any other OS options for the Raspberry Pi? While there’s nothing wrong with either distro, we should remember that the main appeal of using Linux is the freedom and amount of choice that is offered to the user. With that being said, here are four other distros that offer a great user experience on the Raspberry Pi.
-
Canonical/Ubuntu
-
Earlier this week we saw Canonical demo wireless display on the Bq M10 tablet — but it’s not the only device capable of cable-free convergence.
-
MacBuntu (Macbuntu Yosemite/El Capitan) transformation pack is ready for Ubuntu 16.04 Xenial. This pack contains themes for GTK (which supports: Unity, Gnome, Cinnamon, Mate and Xfce two themes dark & light for Gnome Shell, two themes for Cinnamon, two icon packs, cursors. There are some issues with 16.04 where it make some parts of the pack useless: 1) boot/splash we do not recommend you to install boot screen because there is a known bug for plymouth but we are still sharing, if you want to give it a shot; 2) Login screen, it is only offered for Ubuntu Unity and Ubuntu Gnome users but if you have multiple desktops then you can’t choose and another known problem, if you remove lightdm-webkit then you will have blank screen, to solve this issue you have to install other display manager, so better to not install it. 3) Slingscold which is known as launchpad, it does work on some desktops but it may don’t work for some users and you may see blank launcher.
-
make Ubuntu 16.04 look like MacOS with the MacBuntu 16.04 Transformation Pack.
Noobs Lab has detailed instructions on how to install it in Ubuntu 16.04 Xenial Xerus.
-
Road testing the latest daily build of VLC just got a whole heap easier on Ubuntu 16.04 LTS — a snap, you might say.
-
After months of leaks the Meizu MX6 smartphone was unwrapped at a press conference in China earlier today. But the also-rumoured MX6 Ubuntu Edition was (alas) nowhere to be seen. Interestingly the specs of the device differ slightly from those that previous leaks, and benchmark charts claime
-
-
ArduCam unveiled a 24 x 24mm module with the ARM11-based core of the original Raspberry Pi, available with 36 x 36mm carriers with one or two camera links.
The promised second-generation version of the Raspberry Pi Compute Module featuring the same quad-core, 64-bit Broadcom BCM2837 SoC as the Raspberry Pi 3 will be out within a few months, according to a recent PC World interview with Raspberry Pi Foundation CEO Eben Upton. Meanwhile, if you’re looking for a smaller computer-on-module version of the Raspberry Pi and are willing to settle for the old ARM11 foundation available on the current Raspberry Pi Compute Module, ArduCam could have you covered sooner.
-
Onion launched an “Omega2” module on Kickstarter, featuring a faster CPU, options for double the RAM and flash, and lower pricing than last year’s Omega.
Last year, Onion launched an extremely successful Kickstarter campaign for the original Omega module, with packages starting at $25. That campaign won $267,851 from 4,459 backers. Today, the company returned to the Kickstarter well seeking support for a version 2 follow-on to the Omega, appropriately dubbed Omega2. The new project has already reached more than 90 percent of its $15,000 funding goal — a modest feat, in light of the quarter of a million dollars last year’s project earned.
-
The Gateworks Ventana GW5530 SBC runs Linux on an i.MX6, and has mini-PCIe and SIM expansion, a 9-axis IMU, three video inputs, and -40 to 85°C support.
The Ventana GW5530 is the latest in the 5th generation of the Gateworks Ventana family of NXP i.MX6-based SBCs, following last year’s similarly 800MHz, dual-core GW5520. The board is designed for wirelessly connected Man Portable Units (MPUs), Unmanned Aerial Vehicles (UAVs), digital signage, and robotics.
-
In this interesting ELC video, Grant Likely, a Linux kernel engineer and maintainer of the Linux Device Tree, describes his sojourn into embedded hardware.
Sometimes the best tutorials come not from experts, but from proficient newcomers who are up to date on the latest entry-level technologies and can remember what it’s like to be a newbie. It also helps if, like Grant Likely, the teacher is a major figure in embedded Linux who understands how hardware is ignited by software.
At the Embedded Linux Conference, Likely — who is a Linux kernel engineer, and maintainer of the Linux Device Tree subsystem used by many embedded systems — described his embedded hardware journey in a presentation called “Hardware Design for Linux Engineers” — or as he put it, “explaining stuff I only learned six months ago.”
-
Phones
-
A few days ago the Intex Aqua Fish became publicly available. This is the first 3rd party phone officially running SailfishOS from Jolla.
-
Android
-
-
-
-
-
-
-
-
-
-
-
-
-
As the first wave of hands-on reactions to Motorola’s new Moto Z flagship start to surface, I can’t help but think: Man, this sure is a different company than the Motorola we knew a few short years ago.
It quite literally is, of course: As we all recall, Google sold Motorola to Lenovo in early 2014 — a mere 20 months after it took the company’s reigns and transformed it into an idealistic model of what an Android manufacturer could and should be.
-
-
-
-
-
-
-
-
-
-
-
Inexpensive Android smartphones are nothing new. Getting premium quality phones at a low price is fairly new, however. While some folks hail these respectable wallet-friendly devices as a win for consumers, others — such as yours truly — view it as a race to the bottom which could ultimately harm the Android market overall.
Today, ZTE announces the ZMAX PRO Android smartphone. This device is chock full of premium features, such as an octa-core Snapdragon 617 processor, 2GB of RAM, expandable storage, and a fingerprint reader. The truly amazing aspect, however, is the price — a shockingly low $99.
-
In life, you get what you pay for.*
*Exceptions: Costco wine, $1 New York City pizza and the Blu R1 HD smartphone, now sold by Amazon for $50. In those cases, the quality of the product far exceeds your low expectations.
Yes, you read that right, there’s an Android GOOGL, +0.56% 6.0 smartphone that costs less than family dinner at the Olive Garden. It’s cheap, but it’s not, you know, cheap.
-
The announcement this week that Splice Machine is open-sourcing its product has become just the latest reminder that — in emerging technology markets — open source is increasingly the rule, not the exception.
Open-source software is one of those overnight successes that’s been a decade and more in the making. It’s a far cry from the early aughts when Red Hat and JBoss blazed a trail that still has doubters. Arguably, there’s still the issue of whether Red Hat, a publicly-traded, open source company, is a Unicorn from a different twist. Nonetheless, today, when we get acquainted to a new startup, one of the first questions that we pop is whether they’re open source.
-
Splice Machine, the relational SQL database system that uses Hadoop and Spark to provide high-speed results, is now available in an open source edition.
Version 2.0 of Splice Machine added Spark to speed up OLAP-style workloads while still processing conventional OLTP workloads with HBase. The open source version, distributed under the Apache 2.0 license, supplies both engines and most of Splice Machine’s other features, including Apache Kafka streaming support. However, it omits a few enterprise-level options like encryption, Kerberos support, column-level access control, and backup/restore functionality.
-
This is the second in a two-part series on hiring and compensation practices in open organizations. In Want the best employees? Let them hire themselves, I introduced the concept of open hiring with examples from Drupal (the well-known CMS) and Gratipay (a payments start-up and open organization; I’m the founder). We saw how open source thinking about onboarding best practices can lead naturally to including new collaborators in money distribution.
-
Technological change forces economic growth. Technology extends the science of discovery and produces artifacts used in everyday life. It’s the small technical discoveries that make larger scientific endeavors possible. It’s also these seemingly unrelated breakthroughs that make their way into our daily lives.
-
Looking back at 10 years of Hadoop, project co-founder and Cloudera Chief Architect Doug Cutting can see two primary factors in the success of open source big data technology: a heap of luck and the Apache Foundation’s unique support.
-
Gareth Rushgrove is known by many people as the creator and editor of the popular DevOps Weekly email newsletter, and he spent several years working for the U.K. Government Digital Service (GDS) on GOV.UK and other projects. As Senior Software Engineer at Puppet, you can find him building some of the latest infrastructure automation products when he isn’t speaking at events on a wide variety of DevOps and related topics.
-
Last month I interviewed the Cockpit team about team practices. We had an interesting conversation from many different angles, but most notable were the themes we kept returning to: understanding goals, the importance of feedback loops, and committing to open and transparent communication. I found I could easily correlate each of these back to other teams I have worked with in the past. When you inspect the behaviors and inner workings of a team, these themes seem to be remarkably central to team conflict.
-
As we’ve noted, artificial intelligence and machine learning are going through aamini-renaissance right now. Google recently made a possibly hugely influential contribution to the field of machine learning. It has open sourced a program called TensorFlow that is freely available. It’s based on the same internal toolset that Google has spent years developing to support its AI software and other predictive and analytics programs.
In a related open project from the Google Brain team, dubbed Magenta, Google is calling for efforts to leverage TensorFlow and machine learning to create compelling art and music. Some of the early examples from this effort are eye-opening.
-
Nintendo NX spec rumors keep coming, and the latest chatter suggests that the console may support open-source virtual reality for certain games. This would allow the 2017 machine to compete with the likes of Oculus Rift and PlayStation VR.
The news comes to Design & Trend via Chinatimes as referenced by the sometimes-accurate Digitimes. The report should be taken with a grain of salt, but it’s certainly interesting.
As indicated by the secondary source, Nintendo allegedly has a production partnership with a certain chipmaker called Pixart. While the outfit is most known for its heart-rate monitoring hardware, mentions are also made to “tape-out chips supporting VR technology by the end of 2016.” These chips “will support next-generation Nintendo NX game machines.”
-
Playing musical scores is a heavy kind of art. The Nootka app will help you understand the basics of music notation reading, and help you improve by practicing various kinds of exercises. Nootka gives real-time feedback, has multiple difficulty levels, and is customizable.
-
If you’re in open source and looking for a job, chances are you won’t have to search long. According to recent research, businesses are going out of their way to find—and hang onto—their best open source talent. Last month, the 2016 Open Source Jobs Report found that 79% of hiring managers have increased incentives to retain their current open source professionals.
-
-
There’s a special place to chat with fellow photographers, learn about high-end FOSS photography software, and share your work with others. It’s called PIXLS.US, and it’s a large and wonderful world beyond Photoshop.
This is truly a golden age in the hobby of photography. Never before has it been so inexpensive and easy to take and share great photos. The rise of smartphones has fueled an explosion in casual photography, and the ecosystem is further extended through the proliferation of media-sharing apps like Twitter, Facebook, and Instagram. Lower costs for better cameras has enabled many budding photographers to take up the hobby. Unfortunately, while much of the underlying software that fuels the apps and platforms is built on free/open source software, there is little fanfare for the projects that are available directly to photographers.
-
Events
-
I just published the videos from Solskogen 2016 on Youtube; you can find them all in this playlist. The are basically exactly what was being sent out on the live stream, frame for frame, except that the audio for the live shader compos has been remastered, and of course a lot of dead time has been cut out (the stream was sending over several days, but most of the time, only the information loop from the bigscreen).
-
Please note that the systemd.conf 2016 Call for Participation ends in less than two weeks, on Aug. 1st! Please send in your talk proposal by then! We’ve already got a good number of excellent submissions, but we are interested in yours even more!
We are looking for talks on all facets of systemd: deployment, maintenance, administration, development. Regardless of whether you use it in the cloud, on embedded, on IoT, on the desktop, on mobile, in a container or on the server: we are interested in your submissions!
-
Web Browsers
-
Mozilla
-
Browser plugins, especially Flash, have enabled some of our favorite experiences on the Web, including videos and interactive content. But plugins often introduce stability, performance, and security issues for browsers. This is not a trade-off users should have to accept.
Mozilla and the Web as a whole have been taking steps to reduce the need for Flash content in everyday browsing. Starting in August, Firefox will block certain Flash content that is not essential to the user experience, while continuing to support legacy Flash content. These and future changes will bring Firefox users enhanced security, improved battery life, faster page load, and better browser responsiveness.
-
SaaS/Back End
-
Growth hacking often leverages customer data in the experimentation process, in the form of A/B testing. The goal is to use big data to gain a better understand of the customer, via a complete view across every touch point of the organization, in order to enable an optimal customer experience. Growth hackers—who can be anyone from marketing professionals to product manager and engineers—are seeking insights to help optimize marketing campaigns across channels, increase customer loyalty and retention, and enhance the customer experience.
-
Temasek Polytechnic (TP), Singapore and Cloudera have teamed on cultivating the next generation of data professionals through the Cloudera Academic Partnership (CAP) program.
-
Temasek Polytechnic (TP) and Cloudera are working together to cultivate the next generation of data professionals through the Cloudera Academic Partnership (CAP) program. Through this program, students from Temasek Polytechnic’s School of Informatics & IT (IIT) have access to the latest Apache Hadoop curriculum, software and skills training for the Hadoop platform.
-
-
The latest in a string of market research reports has arrived forecasting huge growth for big data analytics platform Hadoop, but not everyone agrees that Hadoop adoption is going so smoothly. According to researchers at Stratistics MRC, the global hadoop market is expected to grow at a CAGR of 53.7% over the forecast period 2015 to 2022. ” Increasing investments in data management, rising amount of structured and unstructured data, hasty growth in consumer data and rapidly increasing demand for big data analytics are the factors influencing the market growth,” the study’s authors report.
Here are some of the details, and some of the warning signs coming in pointing to too much complexity required in deploying Hadoop.
-
-
Databases
-
Splice Machine, which provides an RDBMS powered by Hadoop and Spark, has announced a cloud-based sandbox for developers to put its just launched open source Community Edition to the test. The company is making available an open source standalone and cluster download, and has announced the general availability of V2.0, and the launch of its developer community site.
-
Oracle/Java/LibreOffice
-
Yesterday I added Get around Brno page to the LibreOffice Conference website. There you can find comprehensive information about public transport in Brno, how to buy tickets, how to get to the hotel/venue if you arrive by train/bus/car/plane etc. All accompanied with maps and pictures of described places. So hopefully no one will get lost on their way to the hotel or venue, or struggle purchasing tickets.
-
In this week’s developer interview, we talk to Winfried Donkers, a Dutch coder who has been using LibreOffice (and its predecessors) for almost two decades, and today works on Calc.
-
CMS
-
Randal Schwartz, from TWiT.tv’s “FLOSS Weekly,” interviews Nicole Engard and Brendan Gallagher, about the open source Koha Integrated Library System (ILS), which originated in New Zealand in 1999. Along with being a web developer, Nicole is a prolific blogger on Opensource.com and last year was recognized by Red Hat for her significant contributions to open source advocacy.
-
Pseudo-Open Source (Openwashing)
-
Why Did Microsoft Embrace Open Source? [Ed: Did BP embrace wing power? Did Blair embrace peace? Did Hitler embrace Judaism? Loaded question here. Microsoft never embraced FOSS but hijacked what already existed and could help it make money. All core products are still proprietary.]
-
-
FSF/FSFE/GNU/SFLC
-
Public Services/Government
-
Between 17 June and 8 July, you sent the EU-Fossa project 3282 answers, to help us choose which open source software to audit.
First, thank you very much for the many interesting and encouraging comments!
-
The European Commission is preparing a software source code security audit on two software solutions, Apache HTTP server and Keepass, a password manager. The source code will be analysed and tested for potential security problems, and the results will be shared with the software developers. The audits will start in the coming weeks.
-
Land Information New Zealand (LINZ) is helping government agencies pave the way for open source software use, opening doors for software developers keen to shape new innovative software, says Land Information Minister Louise Upston.
The NZGOAL Software Extension guidelines were themselves developed using open source tools and facilitated through Loomio, an online group decision-making platform. The final drafts were crafted through GitHub, an open source repository.
-
The British government’s Digital Service is looking for a chief penguin to head up open source.
GDS has created a brand-new position for an individual to conduct open source technology projects, adoption and working practices for the government’s IT arm.
Moreover, the chosen candidate will be charged with forging relationships with individuals and projects outside government in the open-source community.
Until now, GDS had a number of people working in different roles taking the lead on open source. The new individual will be nestled in GDS’s technical architecture team.
-
Open Source Software specialist OpusVL has created a way to take the Gov.UK website theme created by the Government Digital Service (GDS) and reproduce it quickly in designing and building public sector websites.
The solution uses Bootstrap, an HTML, CSS and JavaScript framework originating from Twitter, which is used for creating front end websites and applications. With an increase in the variety of devices used to view websites, Bootstrap is a standard toolkit for building responsive design and enabling websites to be mobile and tablet friendly.
With sharing and re-use of software and technology high on the GDS agenda, OpusVL adopted the principle by importing the GDS work and “re-factoring” it in the form of the Bootstrap framework in addition to the methods originally created by GDS.
-
For decades now, open source tools and applications have been gaining enormous traction in parts of Europe, and cities such as Munich have even been involved in a multi-year effort to transform technology infrastructure by throwing out proprietary applications and using open source tools instead.
In the latest move on this front, Bulgaria recently passed legislation requiring that government software be open source. The move underscores how pervasive open source applications and platforms have become. Now, though, there is growing debate about whether Bulgaria is making a wise move, or one that could open it up to security threats.
-
Ripples from Bulgaria’s recent decision requiring all software written for the government to be open source could build into something bigger.
-
Licensing/Legal
-
The GNU General Public License (GPL) was designed to grant clear permissions for sharing software and to defend that freedom for users. GPL’d code now appears in so many devices that it is fundamental to modern technology. While we believe that following the GPL’s requirements is neither burdensome nor unreasonable, many fail to do so. GPL enforcement — the process to encourage those who fail to correct problems and join our open software development community — is difficult diplomacy.
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
While it is nice to have access to produce that is not in season, the unseen use of pesticides and other harmful additives is a difficult problem to avoid.
-
With its customizable, open-source SoCs built on the free and open RISC-V instruction set architecture, SiFive, a San Francisco start-up, is poised to reverse the industry’s rising licensing, design and implementation costs.
With on the one hand Moore’s Law ended or approaching the end and on the other, vast investments required for to develop a modern, high-performance chip, it looks impossible for smaller system designers to join the traditional economic model of chip building. However, the body of software and tools available from the open-source community under the guidance of the RISC-V Foundation, can substantially cut the cost of developing custom silicon. System designers can use the SiFive Freedom platforms to focus on their own differentiated processor without having the overhead of developing a modern SoC, fabric or software infrastructur
-
If you find the prices of the current range of robotic lawnmowers just a little too high for your budget, you might be interested in a new open source remote control lawnmower which has been created called the Lawn Da Vinci.
Okay so it’s not completely autonomous but you can still add a little extra fun to those lawn mowing days, with the addition of a little remote control to the humble petrol powered lawnmower.
-
The evidence is overwhelming that large scale collaboration leads to superior technology. FOSS showed us the way and now free and open source hardware is rapidly gaining traction. There is a growing list of open source hardware projects, which are bringing millions (billion?) of dollars of value to the world. Now a new initiative from the Open Building Institute (OBI) is adding “house” to the list of killer open hardware apps.
-
You’ve heard of open source software. But what about open source hardware? Here’s an overview of what open source hardware is, what the challenges are and why open hardware is poised to grow in importance as the Internet of Things (IoT) continues to boom.
-
Though Autodesk’s interest in 3D printing was not unknown, it may have been a bit of a surprise when the CAD developer entered the industry with its own 3D printer in 2014. Ember, Autodesk’s first hardware product, is a digital light processing (DLP) 3D printer capable of high-resolution prints for prototyping and even end part production. What may be most unique about the Ember is that both the printer and one of its materials are open-source, a bold move for a large corporation like Autodesk.
-
Standards/Consortia
-
AT&T and Orange signed a deal to tackle NFV and SDN open source and standards issues that continue to plague the telecom industry
AT&T signed a deal with European operator Orange to work on open source and standardization initiatives linked to the carrier’s push toward increasing control of its network resources using software-defined networking and network functions virtualization technology.
-
Denmark’s public administrations should overhaul their eInvoicing solutions, writes the Agency for Digitisation (Digitaliseringsstyrelsen – DIGST). The agency wants public administrations to prepare to introduce a European-wide eInvoicing standard, and to concentrate on the use of Danish 2010 eInvoicing standard, OIOUBL. Its forerunner, OIOXML, is to be phased out.
-
Recently, I got a plea from the mother of a child with special needs. She asked: “Can you do a column on how to investigate your child’s special education file?” Two thoughts flashed to my mind: 1) That’s such a fundamental and important thing to be able to investigate. And 2) I don’t know anything about it.
Luckily, one of the joys of working at ProPublica is being surrounded by super smart people. And our education reporter, Heather Vogell, is uncommonly sharp, having covered the most important stories in education for years. (Remember the cheating scandal in Atlanta schools? Heather and her colleagues at the Atlanta Journal-Constitution uncovered that.)
-
Science
-
Very few of you would be knowing about the existence of mineral oil-cooled PCs. These are custom made computers submerged in non-conductive mineral oil. Compared to regular air cooling , the mineral oil cooling setup works with up to 5-times more efficiency. If you find this interesting, you can read ahead and watch some useful videos that detail the process of making a mineral oil-cooled PC.
-
Health/Nutrition
-
Despite “remarkable” progress by some countries on addressing noncommunicable diseases like cancer and diabetes, there is a need to accelerate efforts in order to meet agreed global commitments, the World Health Organization said this week.
-
The government has broken its pledges on NHS funding and is misleading the public about how much extra money it is actually putting into the health service, a committee of MPs has said.
In a highly critical report, the House of Commons health select committee accuses Jeremy Hunt and other ministers of giving the cash-strapped NHS “less than would appear to be the case from official pronouncements”.
The cross-party group of MPs refutes the health secretary’s persistent claim the government will have given the NHS in England an extra £8.4bn by 2020-21 compared with 2015-16. That was one of the Conservatives’ key pledges in last year’s general election campaign, and was repeated many times after that by David Cameron and George Osborne while they were still the prime minister and the chancellor.
-
While the use of one toxic chemical—on our foods, lawns, and elsewhere—has its inherent risks, scientists warn that the combination of two or more such ingredients in common pesticides could have an even more noxious impact, one which is commonly overlooked.
In fact, a investigation released Tuesday by the environmental watchdog Center for Biological Diversity (CBD) found that over the past six years the U.S. Environmental Protection Agency (EPA) has approved nearly 100 pesticide products that contain these so-called “synergistic” compounds, effectively “increasing the dangers to imperiled pollinators and rare plants.”
As CBD explains, “[s]ynergy occurs when two or more chemicals interact to enhance their toxic effects,” turning “what would normally be considered a safe level of exposure into one that results in considerable harm.”
“The EPA is supposed to be the cop on the beat, protecting people and the environment from the dangers of pesticides. With these synergistic pesticides, the EPA has decided to look the other way, and guess who’s left paying the price?” asked Nathan Donley, a scientist with the Center and author of the report, Toxic Concoctions: How the EPA Ignores the Dangers of Pesticide Cocktails (pdf).
-
Security
-
-
-
-
-
-
-
-
-
-
The CrypTech project is an independent security hardware development effort that consists of an international team. CrypTech Alpha is an open source crypto-vault that stores the private/public keys and separates the digital certificates from the software using them. It has been developed as a hardware secure module (HSM) to make the implementation of strong cryptography easier.
-
One of the northwest’s best-known entrepreneurs has splashed out about £10m on a cyber-security venture that helps businesses repel hackers.
Lawrence Jones, who runs the Manchester-based internet hosting and cloud computing specialist UKFast, has bought Pentest, an “ethical hacking” firm whose staff help detect flaws in clients’ cyber-defences.
Jones, 47, will merge Pentest’s 45 staff into his own cyber-security outfit, Secarma. “It’s become obvious that there is a massive need to put emphasis on cyber-security,” said the internet tycoon, whose wealth is calculated by The Sunday Times Rich List as £275m.
-
A vulnerability in a widely used ASN.1 compiler isn’t a good thing: it means a bunch of downstream systems – including mobile phones and cell towers – will inherit the bug.
And an ASN.1 bug is what the Sadosky Foundation in Argentina has turned up, in Objective Systems’ software.
The research group’s Lucas Molas says Objective’s ASN1C compiler for C/C++ version 7.0.0 (other builds are probably affected) generates code that suffers from heap memory corruption. This could be potentially exploited to run malware on machines and devices that run the vulnerable compiler output or interfere with their operation.
-
-
-
-
-
-
Among the more plunderous cybercrime gangs is a group known as “Carbanak,” Eastern European hackers blamed for stealing more than a billion dollars from banks. Today we’ll examine some compelling clues that point to a connection between the Carbanak gang’s staging grounds and a Russian security firm that claims to work with some of the world’s largest brands in cybersecurity.
The Carbanak gang derives its name from the banking malware used in countless high-dollar cyberheists. The gang is perhaps best known for hacking directly into bank networks using poisoned Microsoft Office files, and then using that access to force bank ATMs into dispensing cash. Russian security firm Kaspersky Lab estimates that the Carbanak Gang has likely stolen upwards of USD $1 billion — but mostly from Russian banks.
-
Do you have an army of imposters online pretending to be you? Probably not, but now you can still request for a verified Twitter account.
On Tuesday, Twitter launched an official application process so that any account can be verified and receive a blue checkmark badge next to its username. Twitter users interested in applying should have a verified phone number and email address, as well as a profile photo that reflects the person or company branding.
Verified accounts get to filter their mentions to only see those from other verified accounts. But that seems to be the only real feature or perk that comes from having a blue badge–aside from bragging rights, of course. Additionally, verified accounts can’t be private, and the username must remain the same or you will have to seek verification all over again. If you are rejected, you can reapply after 30 days. Previously, the verification process was never clear-cut, and it seemed to require a direct connection to a Twitter rep.
-
A newly disclosed vulnerability could allow attackers to seize control of mobile phones and key parts of the world’s telecommunications infrastructure and make it possible to eavesdrop or disrupt entire networks, security experts warned Tuesday.
The bug resides in a code library used in a wide range of telecommunication products, including radios in cell towers, routers, and switches, as well as the baseband chips in individual phones. Although exploiting the heap overflow vulnerability would require great skill and resources, attackers who managed to succeed would have the ability to execute malicious code on virtually all of those devices. The code library was developed by Pennsylvania-based Objective Systems and is used to implement a telephony standard known as ASN.1, short for Abstract Syntax Notation One.
-
Wednesday, July 20 is the final day of EFF’s Summer Security Reboot, a two-week membership drive that focuses on taking stock of our digital security practices and bolstering the larger movement to protect digital civil liberties. Besides a reduced donation amount for the Silicon level membership, the Reboot features sets of random number generators: EFF dice with instructions on how to generate stronger and more memorable random passphrases. EFF even produced three new passphrase wordlists to improve upon Arnold Reinhold’s popular Diceware list, first published in 1995.
EFF is a longtime advocate for personal security, and over the years we have continued to fight threats to user privacy and freedom. With the Summer Security Reboot, we want the public to engage with the larger questions of how one can and should control personal information in spite of high-profile attempt after attempt to compromise our devices. The world has increasingly recognized privacy and strong crypto as integral parts of protecting international human rights. A recent Amnesty International report states encryption is “an enabler of the rights to freedom of expression, information and opinion, and also has an impact on the rights to freedom of peaceful assembly, association and other human rights.” Strong passphrase use is but one basic part of a diverse toolkit that can help you protect personal information, whether from identity thieves or government surveillance (ideally both!).
-
A security researcher has located a flaw in Facebook’s device login feature that allows one to easily authorise apps on IoT devices. Due to the lack of CSRF protection, an attacker can fool Facebook’s systems and grab the access_token of the victim. Facebook has now fixed the bug and awarded $5,000 bounty to the white hat hacker.
-
The Neutrino exploit kit (EK) added a former Internet Explorer zero-day vulnerability affecting to its arsenal.
-
Arbor Networks has published the statistics of the DDoS attacks in the first half of 2016. The largest one went up to 579Gbps. An interactive map shows the DDoS attacks made on a global level.
-
-
-
Defence/Aggression
-
When Turkish President/aspiring Sultan Recep Tayyip Erdogan landed at Istanbul’s Ataturk airport early Saturday morning, he declared the attempted coup against his government a failure, and a “gift from God.”
-
Yet another? But yet another what? One does not even know. Once more tens of people killed, many more injured. Once more, a human being has carried them over towards death and suffering in his trajectory of violence and self-destruction. And both ISIS and most western commentators rush to describe him as the soldier of a cause when one does not even know if and when he discovered it.
-
The success of peace requires not only the legal security of the agreements, but also, importantly, a grassroots political process that includes popular support. To date, the government and guerrillas have done little to win public support over the agreement. In fact, many critics have opposed the advances of the Negotiating Table in La Habana, and some, including former president Álvaro Uribe, have called for a “civil resistance” claiming that the agreement promotes impunity. Levels of citizen knowledge about the agreements are low, legitimacy and popular confidence of the peace process have decreased in the latest months, polarization continues to grow with post-paramilitary groups committing human rights abuses, and political strategies to encourage support are non-existent.
-
Note that the government benches are almost empty. The people who bothered to be present and listen to the debate were overwhelmingly those who voted against Trident. With all Scotland’s MPs but one opposing, this is yet another reason to get a move on with Indyref2. I don’t share the criticism of the Tories for calling this debate and vote – it helpfully clarifies that the representatives of Scotland are treated with contempt, and that the Blairite majority in the Parliamentary Labour Party are in hock to arms industry interests.
-
On a hot Friday afternoon in April, hundreds gather at the House of Mourning to pay their respects to the fallen youth of the Kurdish city of Diyarbakır. Among the crowd are families and friends, neighbors and colleagues, municipal officials and local politicians, as well as leaders of the Kurdish movement and many of its most committed supporters. At the invitation of our hosts, we are here to witness the funeral of Yusuf, 19, one of hundreds of young Kurds killed during recent clashes with Turkish forces in the ancient neighborhood of Sur.
-
It is to me disgusting that a politician so thoroughly disgraced as Liam Fox should be back in power. Answers were blanked on the actual purpose of the Werritty connection, and I think collectively we should try to do something about that.
-
An amateur report alleging Russian doctoring of satellite photos on the Malaysia Airlines Flight 17 case – a finding embraced by The New York Times – is denounced by a forensic expert as an “outright fraud,” reports Robert Parry.
-
Over the weekend, after the initial reports of the purge unleashed by Erdogan against Turkey’s public, we previewed the upcoming, far more dangerous counter-coup as follows: “it was the next step that is the critical one: the one where Erdogan – having cracked down on his immediate military and legal opponents – took his crusade against everyone else, including the press and the educational system.”
-
The LRAD was first deployed for use in Iraq, and quickly found its way onto Navy and commercial ships sailing amongst Somali pirates. The bad boy is a sound cannon.
The LRAD company prefers to label its product a tool to broadcast messages and pain-inducing “deterrent” tones over long distances. The device produces a sound that can be directed in a beam up to 30 degrees wide, and the military-grade LRAD 2000X can transmit at up to 162dB up to 5.5 miles away.
Fun fact: A jet engine at 100 feet is 140dB. Sound at 180db will cause tissue damage.
But of course the LRAD is non-lethal, so its maker says that anyone within a 100 meters of the device’s sound path will experience extreme pain. The version generally utilized by police departments (the LRAD 500X) is designed for short bursts of directed sound that cause severe headaches in anyone within a 300 meter range. Anyone within 15 meters of the device’s audio path can experience permanent hearing loss.
Permanent hearing loss begins at 130dB, and if the device is turned up to 140dB, anyone within its path would not only suffer hearing loss, they could potentially lose their balance and be unable to move out of the path of the audio.
-
Scores of civilians trapped in Islamic State-controlled territory in northern Syria were reportedly killed Tuesday by airstrikes from Western coalition aircraft. The reported death toll, potentially the highest ever to result from a coalition bombing in the international campaign against ISIS, continued to climb as The Intercept reached out to monitoring groups tracking operations in the area.
The Syrian Observatory for Human Rights said at least 56 civilians were killed when their convoy of vehicles attempted to slip out of an area north of the city of Manbij in the predawn darkness, as U.S.-backed forces pushed forward in an increasingly bloody offensive in the area. In a brief phone interview, a representative from the Britain-based organization said that while coalition aircraft were believed to be responsible for the air raid, the group suspected it was a “100 percent mistake.”
Airwars, a nonprofit that tracks claims of civilian casualties resulting from the international air campaign against ISIS, said incoming reports indicated the death toll may prove to be well over 100 civilians — potentially making it the largest single loss of civilian life resulting from coalition airstrikes since the U.S.-led campaign to destroy ISIS began nearly two years ago. Tuesday’s reports were the latest in a string of recent incidents in which coalition aircraft have been implicated in the deaths of civilians in the Manbij area.
“Really these civilians are in a desperate situation,” Chris Woods, head of Airwars, told The Intercept. “We’ve never seen anything like this.”
-
The Republicans were supposed to talk about how they plan to Make America Work Again last night. And I supposed Paul Ryan — and to a lesser extent Mitch McConnell, when he wasn’t being booed — presented a vision of how they think Republicans run the economy. That vision doesn’t actually resemble the protectionist big government approach Donald Trump has been running on. But given the revelation that Trump offered to let John Kasich run both domestic and foreign policy if he would be his VP candidate (Kasich was still reluctant), perhaps we should focus more on how Mike Pence wants to suffocate the economy.
Instead, as most people have focused, Republicans continued to attack Hillary (Hillary continues to attack Trump, though I suspect she will focus somewhat more on policy next week than Republicans have thus far). Many people have unpacked Chris Christie’s rabble inciting witch hunt last night, but Dan Drezner backs his review of it with some data on the risks to democracy (click through to read all of, which is worth reading).
-
It has become an article of faith among Republicans that the anti-Islam video, which had sparked protests in Cairo in the hours before the attack in Benghazi, and across the Arab world in the days after it, had absolutely nothing to do with the killing of the Americans. Inside that bubble, carefully nurtured by Fox News, any suggestion that the offensive video — a trailer for a film biography of the prophet made to antagonize Muslims — acted as a catalyst for the assault by Islamist militants was part of a cover-up by the Obama administration.
According to a subsequent investigation by New York Times reporters, however, “extensive interviews with Libyans in Benghazi who had direct knowledge of the attack” suggested that the violence was indeed “fueled in large part by anger at an American-made video denigrating Islam.”
-
The post-coup chaos in Turkey is a reminder about the risk of leaving nuclear weapons in unstable regions where they serve no clear strategic purpose but present a clear and present danger, explains Jonathan Marshall.
-
Why the long wait, and what do the 28 pages reveal?
If we’re to believe the headlines in Saudi media (e.g. Al Arabiya) and mainstream American media (e.g. Time and the Washington Times) the big news is what they don’t reveal: A “smoking gun” connecting the government of Saudi Arabia to the 9/11 attacks.
If we’re to believe the 28 pages themselves, the big news is that they do, in fact, reveal a “smoking gun” connecting the government of Saudi Arabia to the 9/11 attacks.
Here’s the opening sentence from the newly released material: “While in the United States, some of the September 11 hijackers were in contact with, and received support or assistance from, individuals who may be connected with the Saudi government.”
-
The military upheaval in Turkey, whose final consequences are yet to be seen, highlights a major weakness in worldwide efforts to promote democracy. This event underscores the need to establish binding international legal principles to ban the recognition of military regimes as a result of coups d’état. Establishment of such principles, and the creation of the legal mechanisms for applying them, would foster democracy throughout the world.
The circumstances in Turkey mimic several similar situations in recent history: the coming to power of governments without support from the military. Once confronted with a threat to their political hegemony, the military either overthrow the civilian government or refuses to surrender power to democratically elected civilians.
Overt recognition by Western democracies or implied recognition through ambivalent signs of disapproval have encouraged military officers to overthrow many constitutional governments freely chosen by the people. The military relinquish power only when forced by popular will, or when its own incapacity to govern has made its position untenable.
This happened to the Greek junta after its debacle in Cyprus, to the Chilean regime under Augusto Pinochet and to the Argentine military after the Falklands conflict. New principles could be developed, however, that would automatically bar the recognition of such de facto regimes.
Given the need to expand the role of the United Nations in keeping peace, the General Assembly and its International Law Commission could be called upon to draw up appropriate legislation. As the late Secretary-General Dag Hammarskjold once said, the United Nations is “the most appropriate place for development and change of international law on behalf of the whole society of states.”
Establishment of non-recognition of post coup d’état a universal principle raises some difficult practical questions. What about already established and recognized military regimes? These cases show the difficulties of applying the principle retroactively.
But what if a country’s military forces stage a coup against an oppressive or corrupt civilian regime? An ousted civilian government that has been freely elected by the people should not be denied recognition in favor of a post-coup military regime unless the overthrown government was responsible for gross human rights violations. Further, after a coup, recognition should be withheld until another civilian government is chosen in free and democratic elections.
-
In the wake of the two seemingly outrageous slayings of African American men by police in Minnesota and Louisiana and the equally heinous retaliatory killings of five police officers in Dallas by a black former Army Reservist, questions have been raised in all three cases about excessive police behavior.
-
A US air strike killed nearly 60 civilians, including children, in Syria on Tuesday after the coalition mistook them for Islamic State fighters.
Some eight families were hit as they tried to flee fighting in their area, in one of the single deadliest strikes on civilians by the alliance since the start of its operations in the war-torn country.
Pictures of the aftermath of the dawn strikes on the Isil-controlled village of Tokhar near Manbij in northern Syria showed the bodies of children as young as three under piles of rubble.
-
Transparency/Investigative Reporting
-
No better way to celebrate the 50th anniversary of the Freedom of Information Act than filing a lawsuit claiming an agency is refusing to comply with it. FOIA enthusiast Ryan Shapiro has done exactly that, suing the DOJ [PDF] for the FBI’s continued refusal to perform anything more than a cursory search, using its most outdated software, for responsive records.
-
Shapiro told the Guardian that the reason the DoJ gave for refusing to use its $425m Sentinel software to process Foia requests after ACS had failed to recover records was that a Sentinel search “would be needlessly duplicative of the FBI’s default ACS UNI index-based searches and wasteful of Bureau resources”.
-
Jason Leopold is back in court (is he ever NOT there?) battling the NSA and the DOJ’s Office of Legal Counsel (OLC) over the release of documents related to the NSA and FBI’s surveillance of federal and state judges. The two parties had already been told to do more looking around for responsive records by Judge Tanya Chutkan, who rejected their original request for summary judgment last July.
The two agencies went back and performed another search. And still came up empty-handed.
Let me rephrase that: the two agencies went back and performed another “search.” Here’s what that “search” actually entailed, as described in the opinion [PDF].
-
Environment/Energy/Wildlife/Nature
-
When more than 300 protesters assembled in May at the Holiday Inn in Lakewood, Colorado — the venue chosen by the Bureau of Land Management (BLM) for an auction of oil and gas leases on public lands — several of the demonstrators were in fact undercover agents sent by law enforcement to keep tabs on the demonstration, according to emails obtained by The Intercept.
The “Keep it in the Ground” movement, a broad effort to block the development of drilling projects, has rapidly gained traction over the last year, raising pressure on the Obama administration to curtail hydraulic fracturing, known as fracking, and coal mining on federal public lands. In response, government agencies and industry groups have sharply criticized the activists in public, while quietly moving to track their activities.
The emails, which were obtained through an open records act request, show that the Lakewood Police Department collected details about the protest from undercover officers as the event was being planned. During the auction, both local law enforcement and federal agents went undercover among the protesters.
The emails further show that police monitored Keep it in the Ground participating groups such as 350.org, Break Free Movement, Rainforest Action Network, and WildEarth Guardians, while relying upon intelligence gathered by Anadarko, one of the largest oil and gas producers in the region.
-
More than 285,000 people have signed a petition calling for the closure of an aquarium in southern China that is home to an animal dubbed “the world’s saddest polar bear”.
The lethargic bear, whose name is Pizza, is on show at an “ocean theme park” located inside the Grandview shopping centre in the city of Guangzhou.
The aquarium made international headlines after its opening in early January with one Hong Kong-based animal rights charity denouncing it as a “horrifying” animal prison.
-
Six years after spilling more than 27,000 barrels of oil into local rivers, Enbridge Energy Limited Partnership is finally facing the music: a $177 million settlement with the U.S. government.
The music is a little soft.
The settlement covers two spills, but one of them was a doozy. On July 25, 2010, an Enbridge pipeline ruptured, ultimately spilling 20,000 barrels of tar sands oil into the Kalamazoo River and becoming the largest ever on-shore tar sands oil spill. Tar sands oil, extracted primarily in Canada and piped into and across the United States, is heavy, thick, and mud-like. Unlike most other oils, it sinks, making it even more difficult to clean up. After the Kalamazoo spill, Enbridge had to dredge the river and then replant native vegetation. At the five-year mark of the spill, the river’s ecology had not fully returned.
-
Finance
-
The future Republican presidential nominee is right to criticize so-called ‘trade’ deals like NAFTA, but he does so for the wrong reasons.
-
The last-minute decision to include in the Republican platform a call to restore the firewall between commercial and investment banking comes as a surprise, because Donald Trump himself has never publicly addressed or endorsed such a reform in his year-long presidential run.
Trump did once say at a debate in New Hampshire, “nobody knows banking better than I do,” but a review of the transcripts of all twelve Republican debates shows that he never endorsed restoring Glass-Steagall, legislation first passed in 1933. Websites devoted to detailing Trump’s positions find no record of him having any opinion on the Depression-era law. The issues pages of Trump’s presidential website steer clear of anything related to banks or finance.
-
Sound familiar? King’s white moderate and Marx’s ostensible friend is our corporate liberal. Same spin, different decade. The corporate liberal is an embodiment of the idea that political parties are the graveyards of movements. Hedges himself wrote a book called, “Death of the Liberal Class” five years ago. It should’ve been the elegy before the interment of the Democratic Party as a serious option in electoral politics. Yet here we are, about to anoint another corporate liberal to the highest seat in the land. In that case, consider this article yet another epitaph awaiting its headstone. Let’s hope it’s not a long wait. Voices like Sawant’s and the momentum of movements like BLM give us reason to think it won’t be.
-
The city’s Department of Housing Preservation and Development is flouting a rent-reporting requirement for apartments built under the city’s single biggest housing tax break. Mayor Bill de Blasio doesn’t seem to mind.
-
AstroTurf/Lobbying/Politics
-
If he wins the presidency, Republican presidential nominee Donald Trump would seek to purge the federal government of officials appointed by Democratic President Barack Obama and could ask Congress to pass legislation making it easier to fire public workers, Trump ally, Chris Christie, said on Tuesday.
-
Some Republican convention delegates are complaining that pro-Trump thugs harassed and threatened them for not falling into line behind the nominee.
This is not a new phenomenon; there’s even a Delegate Defense Hotline set up by the Ted Cruz campaign in April that bullied delegates can call.
Kera Birkeland, a delegate from Utah, said she was confronted by two women in the bathroom at the Quicken Loans Arena Monday night. “They yelled at me, called me names,” she wrote on Facebook. “They said I should die. They said the police should be pulled from the Utah delegation and we should all die. They never touched me. They did not say they would kill me. They just said I should die.”
Paul Manafort, Trump’s campaign manager, joked about the incident on Tuesday. “I think I have a pretty good sense of what’s going on in this convention, but I haven’t gone in to the bathrooms yet,” he told reporters.
Birkeland was part of a group of delegates who unsuccessfully called for a roll call vote on the convention’s rules on Monday – widely seen as the last gasp of a #Nevertrump movement. Birkeland initially supported Rand Paul for president, then Ted Cruz.
Tommy Valentine, a 22-year-old Virginia delegate, told ThinkProgress that representatives from the Trump campaign threatened him about the petition for a roll call vote: “I had one Trump staffer who came to me and said, ‘When Trump becomes president, he will remember,’” Valentine said. “They were going around to the delegates who would sign the documents intimidating them and telling them to take their names off it.”
-
RNC delegates and convention-goers can buy merchandise calling Hillary Clinton a “bitch” and a “tramp.” On both Monday and Tuesday, the floor has broken out in chants of “lock her up!” Listening to the speaker after speaker spend a significant chunk of their time denouncing Clinton, one might be led to believe hating on Hillary is an official plank in the Republican Party’s platform.
-
-
Tuesday was “Make America Work Again” day at the Republican National Convention, which also happened to coincide with the party formally nominating Donald Trump as its nominee.
But neither jobs nor Trump got much attention as a grab-bag of Republican headliners Tuesday spent most of their time demonizing Hillary Clinton and talking about themselves without offering an affirmative case for the nominee or a concrete economic policy agenda.
The keynoter, House Speaker Paul Ryan, spoke nearly 1,500 words, but mentioned Trump’s name just twice. Promising he’ll be standing alongside “Vice President Mike Pence and President Donald Trump” at next year’s State of the Union address, Ryan spent the lion’s share of his time castigating the Democratic Party instead.
-
Appropriate progressive response to inadequate choice, says one Democratic delegate, ‘would be expressions of outrage and nonviolent protest, from the convention floor in Philadelphia to communities across the country.’
-
The Republican National Convention has been an orgy of crazy talk – mixed in with some plagiarism by Donald Trump’s wife and a vast kangaroo court convicting Hillary Clinton – a truly remarkable spectacle, as Michael Winship describes.
-
-
Years from now, bright-eyed children will look up at Grandma or Grandpa and ask, “Where were you when they nominated Donald Trump?” Far too many prominent Republicans will have to hang their heads in shame.
As the garish imperial coronation in Cleveland reaches its climax, there will be much commentary—some, no doubt, from me—about fleeting events. Did So-and-so’s speech help Trump or hurt him? Did one line of attack against Hillary Clinton seem more or less promising than another? All of this is news, but we must not lose sight of the big picture: The “Party of Lincoln” is about to nominate for president a man who is dangerously unfit for the office.
Trump is a brilliant showman, no question about that. His life’s work has been self-aggrandizement, not real estate, and all those years of practice served him well when he turned to politics. He knows how to work a crowd. He understands television and social media. He dominated and vanquished a field of experienced campaigners as if they were mere apprentices.
-
Boris Johnson was embarrassingly forced on to the back foot during his first London press conference as foreign secretary on Tuesday as he was repeatedly pressed to explain his past “outright lies” and insults about world leaders, including describing the US president as part-Kenyan and hypocritical.
Standing alongside John Kerry, the US secretary of state, Johnson claimed his remarks had been misconstrued, that his past journalism had been taken out of context, and world leaders he had met since his appointment fully understood his past remarks.
-
What happens outside Quicken Loans Arena during the 2016 Republican National Convention may be more interesting than what happens inside the star-spangled halls.
Photojournalist Michael Nigro is in Cleveland to provide Truthdig with a view of noteworthy moments from around the convention centers, where protesters and activists have gathered to express their views.
-
Boos, screams of “no,” and cries of “shame” rang throughout the Republican National Convention’s arena Monday afternoon as party leaders rejected demands from at least ten states to allow a vote on the rules that bind delegates to vote for Donald Trump.
The delegates leading the eleventh-hour rebellion, including Colorado’s Kendal Unruh, were furious. She told ThinkProgress minutes after the vote that she felt cheated by her own party and its nominee.
-
Party divisions over Donald Trump reached the floor of the Republican Convention on Monday afternoon as anti-Trump delegates attempted a complicated procedural maneuver: petitioning the convention’s chairman to force a roll call vote over the acceptance of the convention’s rules.
It was an act of desperation.
“I think Trump is the absolute worst candidate that the Republican Party could put forth,” said Craig Licciardi of Flint, an alternate delegate from Texas who said that he supported the roll call vote. (Nearly half the delegates attending the convention are technically “alternates,” who don’t get an actual vote on the floor.)
Like many from his state’s delegation, he wore a Lone Star shirt and a cowboy hat. “He’s a Democrat in disguise,” Licciardi said. “I would hope that everything he says has a measure of truth to it, but it was only a few years ago that he was praising Hillary and Bill as his good friends, and good people.”
-
The Intercept and our partners at AJ+ produced the video above documenting the GOP’s 60-year-long de-evolution
The Republican Party is poised to nominate a presidential candidate who has built his platform on promises to ban a billion people from entering the United States based on their religious faith and build a gigantic wall south of the border.
But Donald J. Trump is not an accident. The GOP has in the last 40 years relentlessly devolved away from addressing the needs of ordinary people, catering instead to extreme ideologies and the wealthiest donors.
Rather than addressing pressing problems like income inequality and climate change, the modern GOP focuses instead on cutting taxes for the super-wealthy, expanding earth-killing carbon extraction, and endless war.
But it wasn’t always this way. Sixty years ago, the Republican Party was advocating for civil rights and gender equality, a stronger welfare state, and to protect the environment. This is the story of the Republican Party that once was.
-
Last week America suffered the loss of Sydney Schanberg, widely regarded as one of the greatest journalists of his generation. Yet as I’d previously noted, when I read his long and glowing obituary in the New York Times, I was shocked to see that it included not a single word concerning the greatest story of his career, which had been the primary focus of the last quarter century of his research and writing.
The cynical abandonment of hundreds of American POWs at the end of the Vietnam War must surely rank as one of the most monumental scandals of modern times, and the determined effort of the mainstream media to maintain this enormous governmental cover-up for over four decades raises serious doubts about whether we can believe what our newspapers report about anything else.
A couple of mainstream academics, one liberal and one conservative, whose names would be recognized as those of prominent public intellectuals, dropped me notes strongly applauding my effort to reopen the POW controversy and help get the truth out at last.
-
Each day of the Republican National Convention, as tens of thousands of delegates, reporters, and curious onlookers pushed and shoved their way down a single narrow street leading to the arena’s main stage, a group of vendors hawked t-shirts and buttons attacking Democratic nominee Hillary Clinton.
-
The Republican Party came to life as the bastion of “Free Soil, Free Labor, Free Speech, Free Men.” It was a reformist party dedicated to stopping the spread of slavery and to fighting a “Slave Power” its founders saw as undermining free institutions.
The new political organization grew out of the old Whigs and reflected the faith that Henry Clay and his admirer Abraham Lincoln had in the federal government’s ability to invest in fostering economic growth and expanding educational opportunity. Its partisans embodied what John C. Calhoun, slavery’s chief ideological defender, described disdainfully as “the national impulse.” It was, in fact, a good impulse.
-
In the last 24 hours, the Donald Trump campaign has offered a number of dubious excuses for why Melania Trump’s speech at the Republican National Convention’s opening night appeared to lift passages of First Lady Michelle Obama’s 2008 Democratic Convention speech word-for-word. Former Ku Klux Klan Grand Wizard David Duke, who has enthusiastically endorsed Trump, offered a novel explanation: the Jewish agenda.
Trump initially refused to disavow the notorious white supremacist’s endorsement, eventually distancing himself from Duke after pressure from the party establishment. But Duke has continued to vociferously defend Trump against all accusations of racism, generally by blaming the Jews.
-
A central portion of Melania Trump’s speech to the Republican National Convention on Monday night, about the core values her parents instilled in her and her sister as children, seems to have been lifted almost word for word from the speech Michelle Obama gave on the first night of the 2008 Democratic National Convention.
-
A key part of Donald Trump’s campaign to become the Republican presidential nominee was based on claiming to self-fund his campaign while calling his opponents “puppets” of big contributors. But the 2016 Republican platform takes some of the most extreme positions on money in politics, measures that would force almost all politicians to seek out their own personal puppet masters.
First, the GOP platform advocates “raising or repealing contribution limits” on donations directly to politicians.
Currently individuals can give only $2,700 per election directly to a candidate. Primaries count as separate elections, so you can give Hillary Clinton’s and Donald Trump’s campaigns $5,400 – half for the primary and half for the general elections.
Thanks to Citizens United and related rulings, you can also — if you can afford to — give unlimited amounts to Super PACs that are theoretically uncoordinated with campaigns.
-
Censorship/Free Speech
-
The court also dismisses several other accusations by Albert, noting that Yelp has never solicited defamatory/misleading reviews and acts in good faith to remove defamatory or misleading postings when notified. It also points out that Albert’s claim that Yelp itself creates misleading/defamatory reviews is not supported by any available evidence.
The plaintiff has asked for the opportunity to amend her complaint (not a bad idea, considering every allegation was rebuffed), but the court points out that the anti-SLAPP statute would be completely useless if complainants were allowed to rewrite their pleadings in light of a court’s decision.
-
The high court of Paris has ruled that Google and Microsoft do not have to censor their search engines to remove all results involving the world “torrent” used in conjunction with the names of three French musicians.
The French music producers’ association “Syndicat national de l’édition phonographique” (SNEP) had sought a court order to force the US companies to remove results for searches pairing the word “torrent” with the artists’ names, which they claimed directed users to pirate sites.
As an article on the French site NextInpact explains, the Tribunal de grande instance de Paris refused to grant SNEP’s request for Google’s search results to be censored because of a legal technicality raised by Google’s lawyers. SNEP’s request referred to only three artists, and should have been on behalf of its entire membership, the high court ruled.
-
Google and Bing are not required to automatically filter “torrent” related searches to prevent piracy, the High Court of Paris has decided. The filter, requested by the local music industry group SNEP, would be too broad, ineffective, and target legitimate content as well.
-
The public broadcaster had been refusing to withdraw a decision taken to ban airing footage of protests where public property was being burned. This was despite an order made by the Independent Communications Authority (Icasa) and numerous court challenges.
-
Turkey has a pretty detailed history of banning websites that it doesn’t like, so the news that it’s now blocking Wikileaks hardly comes as a surprise. After all, following the failed coup attempt, President Recep Tayyip Erdogan wasted no time in moving forward with what appears to be a somewhat vicious crackdown on tens of thousands of people. So, when Wikileaks suddenly released 300,000 emails from the Turkish government for anyone to search and explore, it’s no surprise that all access to Wikileaks was quickly blocked.
-
Turkey has blocked access to the WikiLeaks website, the telecoms watchdog said on Wednesday, hours after it leaked thousands of ruling party emails just as Ankara grapples with the aftermath of a failed military coup.
Around 50,000 soldiers, police, judges and teachers have been suspended or detained since the attempted coup on the weekend, and Turkey’s Western allies have expressed concern over the crackdown’s reach.
WikiLeaks on Tuesday released nearly 300,000 emails from the AK Party dating from 2010 to July 6 this year. Obtained before the attempted coup, the date of their publication was brought forward “in response to the government’s post-coup purges”, WikiLeaks said on its website.
-
Parliament’s Portfolio Committee on Communications also said it noted the judgment passed by the high court in Pretoria on Wednesday and hoped that the SABC would abide by the judgement.
-
The High Court in Pretoria on Wednesday granted an order interdicting the SABC from implementing or enforcing its censorship decision.
-
THE axed SABC journalists now want to be reinstated immediately, after the public broadcaster’s controversial editorial policy banning footage of violent protests came crumbling down in court yesterday.
The scales appeared to tilt in their favour when the high court in Pretoria granted an order interdicting the public broadcaster from enforcing its censorship policy.
-
-
A red brick wall. A white paintbrush. How long would it take to paint the wall? For an artist it wouldn’t take long to give a fair estimate of the time. But in January this year, the task was entrusted upon two members of the British Board of Film Classification (BBFC) when British film-maker Charlie Lyne crowdfunded a film titled “Paint Drying” and made them sit through more than a 10-hour-long movie. All that was there in the film was a “single, unbroken shot of white paint drying on a brick wall”! On India’s Republic Day when the U certificate for the film was posted on Reddit, BBFC’s website crashed.
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Privacy/Surveillance
-
-
Algorithms make digitally mediated surveillance or watching over technically very easy. Applications can support and mitigate the damage of disasters, they can help protect people in public spaces, they can help signal health risks and in that sense, they combat disease. They help in monitoring climate change. Algorithms are being used to help companies to boost profits and countries are (in some cases) experiencing economic growth as a result – that is the claim and it can be verified. Algorithms also of course support sousveillance or undersight as Steve Mann and others call it; and so algorithmic based watching from below also supports a radical politics of resistance.
-
The FBI wants to implement a program to counter extremism in U.S. schools that’s similar to a disastrous one in the U.K.
Are these the tell-tale signs of kids at risk of committing violence: An 8-year-old who wore a t-shirt saying he wanted to be like a seventh-century Muslim leader? A 17-year-old who sought to draw attention to the water shortage in Gaza by handing out leaflets? A 4-year-old who drew a picture of his dad slicing a vegetable?
Teachers and school officials in the United Kingdom thought so, and they referred these children for investigation as potential terrorists. They were interrogated by U.K. law enforcement. They’re likely subject to ongoing monitoring, with details of their childhoods maintained in secret government files potentially indefinitely.
A report released last week by Rights Watch (UK) highlights these and other children’s experiences under a U.K. countering violent extremism (CVE) program known as Prevent. Prevent imposes a legal obligation on schools to implement policies assessing whether children have “extremist” views or are at risk of engaging in terrorism, and to “intervene as appropriate.” Intervention may include referring the child to a related program in which panels of police officers, teachers, and other government employees identify children they think are vulnerable to terrorist recruitment.
Why should any of this concern Americans? Because the FBI wants to do something a little bit too close for comfort in U.S. schools, and American schoolchildren may come under similar suspicion and scrutiny.
-
The French data protection authority on Wednesday ordered Microsoft to stop collecting excessive data on users of its Windows 10 operating system and serving them personalized ads without their consent.
The French data authority, Commission Nationale de l’Informatique et des Libertés (CNIL), said the US company had three months to stop tracking browsing by users so that Windows apps and third-party apps can offer them targeted advertising without their consent, failing which it could initiate a sanctions procedure.
A number of EU data protection authorities created a contact group to investigate Microsoft’s Windows 10 operating system following its launch in July 2015, the French privacy watchdog said.
-
The privacy software Tor has aided everything from drug dealing marketplaces to whistleblowing websites in evading surveillance on the darknet. Now that same software can be applied to a far more personal form of security: keeping hackers out of your toaster.
On Wednesday, the privacy-focused non-profit Guardian Project, a partner of the Tor Project that maintains and develops the Tor anonymity network, announced a new technique it’s developed to apply Tor’s layers of encryption and network stealth to protecting so-called “Internet of things” or “smart home” devices. That growing class of gadgets, ranging from refrigerators to lightbulbs to security cameras, are connected to the Internet to make possible new forms of remote management and automation. They also, as the security research community has repeatedly demonstrated, enable a new breed of over-the-Internet attacks, such as the rash of hackers harassing infants via baby monitors or the potential for hackers to steal your Gmail password from your fridge.
-
Kim Kardashian and Taylor Swift had an exhausting day on the internet on Monday. In the immediate aftermath of Kardashian releasing video footage confirming that Swift did, in fact, have a conversation with Kanye West about her name drop in his song “Famous,” public opinion has taken a dramatic turn against Swift.
-
Censorship on social media is a tricky issue. Platforms like Twitter and Instagram have to balance community policing with freedom of expression. When does bullying cross the line? Should hate speech be banned? And who gets to decide? It’s often a gray area — except when it’s black and white.
Since Kim Kardashian uploaded snippets on Sunday night of Kanye’s conversation with Taylor Swift — you know, the phone call about “Famous” that Swift insisted never happened — Kimye supporters have been hard-core trolling Swift’s Instagram response to the debacle. Commenters have been calling her a liar, a fake, and things much nastier than that — or simply resorting to the snake emoji, as inspired by this tweet of Kardashian’s. Not nice — but nothing egregious or unusual, either.
-
-
The federal patient privacy law known as HIPAA has not kept pace with wearable fitness trackers, mobile health apps and online patient communities, leaving a gaping hole in regulations that needs to be filled, according to a much-delayed government report released today.
The report, which was supposed to be complete in 2010, does not include specific recommendations for fixing the problem, even though Congress asked the U.S. Department of Health and Human Services to provide them.
-
It’s been a rough month for Internet freedom in Russia. After it breezed through the Duma, President Putin signed the “Yarovaya package” into law—a set of radical “anti-terrorism” provisions drafted by ultra-conservative United Russia politician Irina Yarovaya, together with a set of instructions on how to implement the new rules. Russia’s new surveillance laws include some of Bad Internet Legislation’s greatest hits, such as mandatory data retention and government backdoors for encrypted communications—policies that EFF has opposed in every country where they’ve been proposed.
As if that wasn’t scary enough, under the revisions to the criminal code, Russians can now be prosecuted for “failing to report a crime.” Citizens now risk a year in jail for simply not telling the police about suspicions they might have about future terrorist acts.
But some of the greatest confusion has come from Internet service providers and other telecommunication companies. These organizations now face impossible demands from the Russian state. Now they can be ordered to retain every byte of data that they transmit, including video, telephone calls, text messages, web traffic, and email for six months—a daunting and expensive task that requires the kind of storage capacity that’s usually associated with NSA data centers in Utah. Government access to this data no longer requires a warrant. Carriers must keep all metadata for three years; ISPs one year. Finally, any online service (including social networks, email, or messaging services) that uses encrypted data is now required to permit the Federal Security Service (FSB) to access and read their services’ encrypted communications, including providing any encryption keys.
-
Randomly-generated passphrases offer a major security upgrade over user-chosen passwords. Estimating the difficulty of guessing or cracking a human-chosen password is very difficult. It was the primary topic of my own PhD thesis and remains an active area of research. (One of many difficulties when people choose passwords themselves is that people aren’t very good at making random, unpredictable choices.)
-
The national security state steps out of bounds.
[...]
After 9/11, Hayden and a small group of White House officials, intelligence officers, and lawyers secretly put in place a warrantless wiretapping program whose purported legality relied on radical exceptions to both the Fourth Amendment and a federal statute that strictly governs foreign-intelligence surveillance on domestic soil. Even as he defends the program, codenamed “Stellarwind,” as a “logical response” to 9/11 and “not the product of demented cryptologic minds,” Hayden calls it “the agency’s edgiest undertaking in its history.” (He may be right, but he devotes just five lines to describing the program’s most legitimate competitor for that title: the vast domestic spying, detailed in the 1975 and ’76 Church Committee Reports, that he calls a “scandal” in scare quotes. He mentions government surveillance of “the likes of” Jane Fonda, Joan Baez, and Benjamin Spock; he leaves out a host of legislators and civil rights leaders, including Martin Luther King Jr.) Situating the controversy Stellarwind ignited, Hayden writes my favorite sentence in the book: “Domestic intelligence has always been countercultural in America.”
-
Using Xcode to spoof GPS locations in Pokemon Go (like we saw this morning) isn’t that much of a hack, and frankly, it’s not even a legit GPS spoof. After all, it’s not like we’re using an SDR to spoof the physical GPS signal to cheat Pokemon Go.
-
No sooner had the ink dried on the Second Circuit Appeals Court decision regarding Microsoft and its overseas servers than new legislation designed to undercut the court’s finding has been printed up by the DOJ and presented to the administration.
Microsoft successfully argued that the US government couldn’t force it to unlock a server in Dublin, Ireland, so it could rummage around for evidence. Nor could the DOJ force the company to act on its behalf, performing a search of its overseas servers for documents the US government couldn’t access otherwise.
Since that decision obviously just won’t do, the DOJ has presented proposed legislation [PDF] that would alter existing Mutual Legal Assistance Treaties (MLATs) so the agency can do the very thing a court just said it couldn’t do.
The details are discussed in, um, detail over at the Lawfare blog by none other than a former DOJ lawyer (David Kris). Needless to say, the post skews towards “supportive,” but the analysis is thorough and offers some excellent insight on what the DOJ hopes to open up — and what it’s willing to concede in return for this new power.
-
-
-
-
A former division chief for the National Security Agency, who admitted that he hurled his 3-year-old adopted son against a wall in his Maryland home, was sentenced to 12 years in prison Tuesday for the boy’s death.
-
-
-
Much of the six-hour hearing dealt with O’Callaghan’s mental state. He had served tours in Kosovo and Iraq as a Marine, saw the dead bodies of children, and was later diagnosed with post-traumatic stress disorder, testimony showed. His attorney, Steven McCool, described that history as a mitigating factor in the crime.
-
Politicians, lawyers, and civil rights groups have slammed the UK government’s present and future surveillance laws in light of the advocate general’s opinion on the Data Retention and Investigatory Powers Act (DRIPA)—which said that Theresa May’s emergency spy law is legal if strong safeguards are in place.
[...]
Labour’s deputy leader Tom Watson—who, alongside Tory MP and the government’s new Brexit chief David Davis—brought the original legal action against the UK’s DRIPA legislation, said: “This legal opinion shows the prime minister was wrong to pass legislation when she was home secretary that allows the state to access huge amounts of personal data without evidence of criminality or wrongdoing.”
Human rights group Liberty, which represented Watson in the courts, said that if the CJEU judges agree with the advocate general’s opinion, “the decision could stop the government’s fatally flawed Investigatory Powers Bill in its tracks and mark a watershed moment in the fight for a genuinely effective, lawful, and targeted system of surveillance that keeps British people safe and respects their rights.”
-
-
Civil Rights/Policing
-
America is a ticking time bomb.
All that remains to be seen is who—or what—will set fire to the fuse.
We are poised at what seems to be the pinnacle of a manufactured breakdown, with police shooting unarmed citizens, snipers shooting police, global and domestic violence rising, and a political showdown between two presidential candidates equally matched in unpopularity.
The preparations for the Republican and Democratic national conventions taking place in Cleveland and Philadelphia—augmented by a $50 million federal security grant for each city—provide a foretaste of how the government plans to deal with any individual or group that steps out of line: they will be censored, silenced, spied on, caged, intimidated, interrogated, investigated, recorded, tracked, labeled, held at gunpoint, detained, restrained, arrested, tried and found guilty.
For instance, anticipating civil unrest and mass demonstrations in connection with the Republican Party convention, Cleveland officials set up makeshift prisons, extra courtrooms to handle protesters, and shut down a local university in order to house 1,700 riot police and their weapons. The city’s courts are preparing to process up to 1,000 people a day. Additionally, the FBI has also been conducting “interviews” with activists in advance of the conventions to discourage them from engaging in protests.
-
A bizarre case comes out of the Texas court system — landing squarely in the middle of a legal Bermuda Triangle where illegal searches meet civil asset forfeiture… and everything is still somehow perfectly legal. (via FourthAmendment.com)
The facts of the case: police officers arrested Miguel Herrera and seized his 2004 Lincoln Navigator. An inventory search of the vehicle uncovered drugs and the state moved to seize the vehicle itself as “contraband” using civil (rather than criminal — this is important) asset forfeiture. Herrera argued that the stop itself was illegal and anything resulting from it — the drugs and the civil seizure of the vehicle — should be suppressed.
The Supreme Court of Texas examines the facts of the case, along with the applicable statutes, and — after discarding a US Supreme Court decision that would have found in Herrera’s favor — decides there’s nothing he can do to challenge the seizure. He can’t even move to suppress the evidence uncovered following the illegal stop — the same search that led to the state seizing his vehicle under civil forfeiture statutes.
-
In another step towards the fascist state Donald Trump has warm dreams envisioning, FBI agents and Cleveland police officers “visited” the homes of local activists in an attempt to gather intelligence on possible planned demonstrations surrounding the Republican National Convention.
-
Steve King, a Republican congressman from Iowa, insisted on Monday that there was nothing wrong with the lack of diversity at the Republican National Convention since, he said, members of other races had contributed relatively little to human civilization.
King’s literal assertion of white supremacy, in response to criticism of the party by the Esquire blogger Charlie Pierce, came during a live appearance on MSNBC, and seemed to stun the host, Chris Hayes, as well as Pierce and April Ryan, American Urban Radio Networks’ Washington bureau chief.
-
Alfred Taban, a prominent South Sudanese journalist and editor-in-chief of the Juba Monitor, was arrested by government national security service agents on Saturday, according to the East and Horn of Africa Human Rights Defenders Project (DefendDefenders). His arrest reportedly stemmed from his recent editorial calling for the removal of South Sudan’s president Salva Kiir and his first vice president Riek Machar, following a new round of bloodletting in South Sudan’s long-running civil war.
“What Alfred wrote was within the constitutional right (freedom of expression), it is not an offense,” Edmund Yakani, the executive director of Community Empowerment for Progress Organization, a civil society organization that tracks the harassment of journalists, told The Intercept by email.
-
Power-seeking demagogues appeal, unknowingly, to our dangerous instinct to fear and hate rival groups: unknowingly, partly because the scientific community denies the existence of instinct.
-
It’s really simple: Government officials cannot punish subordinates for refusing to pray.
How does a 13-year veteran of the Puerto Rico Police Department go from being a patrol officer to washing police cars? In the case of Officer Alvin Marrero-Méndez, all it took was refusing to participate in his boss’s official Christian prayers. After Officer Marrero-Méndez, an atheist, objected to the unlawful practice and declined to join his colleagues in prayer, he was demeaned by his supervisors, stripped of his gun, and effectively demoted to a messenger and car-washer.
In 2013, the ACLU and ACLU of Puerto Rico filed a federal lawsuit against Officer Marrero-Méndez’s supervisors. Today, ruling against the supervisors, a federal appeals court affirmed the obvious: The government cannot punish someone for refusing to pray, and officials who violate this basic constitutional principle can be held liable in court for their conduct.
The defendants had argued that they should be immune from liability because, according to them, the law at the time was not clearly established. But as the U.S. Court of Appeals for the First Circuit explained today, “If these actions do not establish religious coercion, we would be hard-pressed to find what would.”
-
One police officer was stabbed and another injured after a water fight in London’s Hyde Park on the hottest day of the year turned violent.
Two other people suffered stab wounds in addition to the police officer as the park descended into a “war zone”.
-
-
The first lecture in the series Foucault calls Security, Territory and Population is primarily a discussion of security. Instead of a definition, Foucault gives two sets of examples. The first group involves penal statutes. In the simplest case, there is a prohibited practice (you shall not steal) and a punishment (amputation). In the second, the disciplinary case, the prohibition and the punishment are present, but in a more complex context, including a system of supervisions, inspections and checks to identify the likelihood that a person will commit a crime; and instead of a spectacular punishment like amputation or banishment, there are incarceration and efforts at transforming the person. In the third case, the first two remain in place, but we add a supervisory regime of statistics and other efforts to understand the problem created by the prohibited practice and to set up mechanisms that are cost-effective in trying to keep the prohibited acts at a tolerable level with cost-benefit analysis and other constructs.
The second set of examples concerns illness. In the Middle Ages, leprosy was dealt with using a strict protocol of separation. A bit later, the Plague was treated with a robust series of quarantines, inspections and other regulatory steps to prevent spread. In the third case, there is smallpox, treated with inoculations, so that the crucial questions are the effectiveness of the vaccine, the modes of insuring widespread inoculation, and other more formal statistical understandings.
-
Underlying this question for the party was a question for the country as a whole, the fundamental and perennial question, ‘who is to be master?’ Is society to be dominated by a few hundred thousand bankers, industrialists and landowners? Or will the whole nation come to comprehend and control its economic policy and ‘distribute the product of its labours in accordance with some generally recognised principles of justice?’
-
One of the looming mysteries during the last several months of Brazil’s political crisis (as The Intercept has repeatedly noted) has been the complete absence of polling data from the country’s largest media outlets and polling firms. The lower house voted on April 17 — more than three months ago — to send to the Senate impeachment charges against democratically elected President Dilma Rousseff, which resulted in the temporary installation of her vice president, Michel Temer, as “interim president.”
Since then, there had been no published polls from Datafolha — the polling firm used by Brazil’s largest newspaper, Folha de.S Paulo — asking Brazilians if they favor Dilma’s impeachment, if they favor the impeachment of Temer, and/or if they want new elections to choose a new president. The last Datafolha poll prior to the impeachment vote was on April 9, and it found that 60 percent favored Dilma’s impeachment, while 58 percent favored the impeachment of Temer. It also found that 60 percent wanted Temer to resign after Dilma was impeached, and 79 percent favored new elections once they both left.
-
If you’ll recall, early on this year we wrote about the very strange story in which the at-the-time scouting director for the St. Louis Cardinals, Chris Correa, used the old passwords of a former employee who had since taken a job with the Houston Astros to break into the opposing team’s scouting database. The actions were fairly brazen, leading many to wonder how in the world Correa thought he was going to get away with this. The government charged him under the CFAA, to which Correa pleaded guilty. At the time, I concluded the post guessing that Correa, given his standing and the fact that he isn’t named Aaron Swartz, would get off with minimal if any jail time.
-
Christopher Correa, the former scouting director for Major League Baseball’s St. Louis Cardinals, has been sentenced to 46 months in federal prison for guessing the password of a Houston Astros manager.
-
In his grab-the-pitchforks address to the Republican National Convention on Monday night, former New York Mayor Rudolph Giuliani insisted the enemy wasn’t “most of Islam,” just “Islamic extremist terrorism.”
But in an interview with The Intercept on the convention floor Tuesday night, Giuliani enthusiastically defended policies that treat all Muslims like criminal suspects.
Asked whether he supports Republican presidential nominee Donald Trump’s proposals to have police spy on mosques, Giuliani replied “I was the mayor who put police officers in mosques, in New York and New Jersey.”
Giuliani even claimed credit for a longer history of police surveillance of New York area mosques than is widely known, predating the 9/11 terrorist attacks. “We did it for the eight years I was mayor,” he said. Giuliani was mayor from 1994 through December 2001.
“After the 1993 bombing of the World Trade Center by Islamic extremist terrorists from New Jersey, I did it in early January of 1994.”
After the 9/11 attacks, the New York Police Department launched a now well-documented but then-secret program of spying on every mosque within a 100-mile radius of New York City, including in New Jersey, Pennsylvania, and New England. The department acknowledged in 2012 court testimony that the program had never generated an investigative lead and in 2014, Mayor Bill De Blasio shut down the program’s most controversial unit.
-
Dozens of police officers swarmed protestors from the activist group CodePink outside a main entrance to the Republican National Convention Tuesday, because they were holding tennis balls.
In June, the City of Cleveland added tennis balls to its list of prohibited items inside a 3.3 square mile “event zone,” surrounding the Quicken Loans Arena. Other prohibited items included tape, rope, bike locks, and any stepstool that could be used to address a crowd. But the prohibition did not apply to guns – meaning that convention attendees and onlookers are allowed to openly carry firearms, including assault weapons.
Cleveland Police requested that Ohio Gov. John Kasich suspend open carry laws inside the “event zone,” but he denied the request.
-
After 14 years, the author of ‘Guantánamo Diary’ has been cleared for release from indefinite detention by the government.
After 14 long years languishing at Guantánamo without charge or trial, Mohamedou Slahi has finally been cleared for release.
Today the Periodic Review Board — a panel of national security, intelligence, and other officials — made that decision after determining that Slahi poses no significant threat to the United States. The government of his native Mauritania has said that it would welcome him home.
Slahi is the author of the best-selling memoir “Guantánamo Diary,” and he appeared before the Periodic Review Board on June 2. We provided the PRB with a slew of evidence and support for Mohamedou’s release. We especially appreciate the letter of support from a former U.S. military guard at Guantánamo who was assigned to Slahi for 10 months, and another support letter from former chief prosecutor for the Guantánamo military commissions, Col. Morris Davis.
A campaign to free Slahi spearheaded by the ACLU has gathered major support both in the U.S. and abroad. The ACLU and Change.org have collected more than 100,000 signatures calling for his release. High-profile supporters of the petition include Maggie Gyllenhaal, Mark Ruffalo, and Roger Waters. In the U.K., several members of Parliament signed a letter urging the British government to call on the U.S. to release Slahi.
-
An interagency review board has determined that Guantánamo detainee Mohamedou Ould Slahi poses no threat to the United States and has recommended that he be released, setting the bestselling author on the path to be reunited with his family.
Slahi was arrested in his native Mauritania in 2001, and was held and tortured in secret prisons in Afghanistan and Jordan before being secreted to Guantánamo, an odyssey he recounted in a memoir, Guantánamo Diary, which became a bestseller last year. He has been imprisoned for over 14 years without being charged with a crime.
In early June, Slahi made his case to the Periodic Review Board as part of a sort of parole process instituted by the Obama administration to evaluate the cases of the remaining men at Guantanamo to determine if they might be safely transferred to another country.
At that hearing, Slahi’s advocates, including his lawyer and two representatives from the military, described his plans to continue writing and to start a small business, and noted the strong network of family and other supporters who could help him. They spoke to his unusual language skills and warm relationship with his lawyers and even the guards assigned to him. The military representatives described him as “an advocate for peace,” and stated that they were “certain that Mohamedou’s intentions after Guantánamo are genuine, and that he possesses sound judgment, and that he is good for his word.” One former guard submitted a letter attesting that he “would be pleased to welcome [Slahi] into my home.” (In keeping with the general secrecy of proceedings at Guantánamo, Slahi was not allowed speak during the open portion of the review, and he declined to have his own statement from the closed session made public.)
-
Internet Policy/Net Neutrality
-
Today ends the BEREC consultation on Net Neutrality. This consultation aimed at consulting the people on the guidelines clarifying the implementation of the telecom regulation1. The version sent by La Quadrature du Net is the one written by the FDN Federation, we believe this answer is appropriate and we support its provisions.
-
With much industry fanfare last month, Dutch telco KPN announced that it had completed nationwide coverage of the Netherlands in a wireless Internet of things network. Like a traditional cellular network, but with far lower costs and energy requirements, KPN’s network can connect sensors monitoring everything from rail switches at Utrecht Central station to depth sounders at the Port of Rotterdam and baggage handling at Schiphol Airport.
-
The planned transition of the internet’s critical technical functions from the US government to a technical body may come under further attack after the Republican Party officially agreed to block it on Monday.
The Republican Platform for 2016 [PDF] was formally approved during a chaotic first day of the party’s national convention in Cleveland, and among its 66 pages of policy positions is its stance on “Protecting Internet Freedom.”
In contrast to most of the document, the effort to move ultimate control of IANA from the US Department of Commerce (DoC) to non-profit DNS overseer ICANN is covered in largely hyperbolic terms.
-
IoT Gateways connect IoT Devices to IoT back-end systems. Gateways connect to devices using interfaces like Ethernet, WiFi, Bluetooth, 6LoWPAN, RS-485 and CANbus. Gateways connect to back-end systems through the Internet, commonly using Ethernet, WiFi, or cellular connections. Gateways perform multiple tasks, including concatenation of multiple devices, protocol conversion, device management, and security. Gateways may also perform application processing.
-
DRM
-
Intellectual Monopolies
-
The Anti-Counterfeiting Rapid Intelligence System (ACRIS) is new database created by EUIPO’s Observatory in cooperation with DG Trade. The database provides EU companies with an overview of IP risks in third countries and offers a collection of IPR infringement cases. In the database, information is also given on the actions taken by third country local authorities in response to IP infringements. This information is intended to help companies to make informed decisions as to their business strategies in third countries and how to avoid and mitigate risks of IP infringement.
-
The United Kingdom-based Anti-Counterfeiting Group (ACG) industry group launched a “manifesto” earlier this month, calling on the government to establish a more effective and comprehensive response to intellectual property crime.
A summary press release and the manifesto can be found here.
The UK government is estimated by industry to lose £1.3 billion in unpaid tax from the sale of counterfeits. Additionally, whilst there has been an increase in the counterfeit products entering the UK markets, there has unfortunately been a decrease in the number of these products being seized at EU borders, the group said.
-
A new publication analysing the relationship between intellectual property and access to science explores ways countries have developed to counter the potential barriers created by IP rights, and says patenting by universities is counterproductive.
-
The lessons derived from the history of AIDS treatment have become a rallying call for civil society organisations globally. Not being able to afford AIDS medicines should not be repeated for people with other diseases, including HIV co-infections, treatment activists told world leaders here.
-
Copyrights
-
A German software company, Bitmanagement Software, is now suing the US government for copyright infringement and demanding almost $600 million. The lawsuit, which was filed in the US Court of Federal Claims (basically a special court set up just for cases involving suing the US government for money), says that the US Navy copied Bitmanagement’s 3D virtual reality software, BS Contact Geo. Apparently, the Navy had tested the software and had an evaluation license allowing the software to be used on 38 computers. And then the Navy just copied it onto hundreds of thousands of computers.
The lawsuit notes that the Navy had specifically requested the removal of Bitmanagement’s usage tracking code, and then told the company that it wanted to license the software for upwards of 500,000 computers — but also that it started doing those installs while the company was still negotiating a license. While that negotiation was ongoing, someone (accidentally, apparently) forwarded an email to Bitmanagement indicating that the software had already been installed on 104,922 computers. Apparently, a few months later, the Navy also disabled some other tracking software, called Flexwrap. This part is a bit confusing in the lawsuit, since earlier it notes that the evaluation contract required Bitmanagement to remove tracking software, but then the lawsuit notes that later on it was the Navy that removed Flexwrap, “in violation of the terms” of the license.
-
Sharing is an inherent feature of social media. But, asks Alice Gatignol, is there any way this can be reconciled with established principles of copyright protection?
-
Copyright holders running after pirates is not a new tune to our ears. Google, the biggest search engine provider on the planet, publishes regular reports of their fight against removing pirated content. They’ve managed to blank out around 523 million links from Google Search this year and will continue to remove more of them in the coming months.
-
Francis Gurry has appointed the new Deputy Director General for the Copyright and Creative Industry Sector. She is Sylvie Forbin, a national of France, and most recently Senior Vice President for Public and European Affairs, for Vivendi. Here is the WIPO announcement: as PDF.
If the past is a guide, she is a hardliner for the industry, opposing user rights and favoring very aggressive enforcement measures.
Among other things, she has described the social movements for access to knowledge as “very organized” and “opaque networks” that serve technology giants.
-
The crux of the argument is that these iconic characters currently appear to be in a bit of a death spiral. Man of Steel and Batman v. Superman met with a mixed-at-best response from fans and critics, and while both made good money in the big picture, they also showed some worrying signs — like failing to catch up to Marvel’s superhero movies (which was the whole point) and breaking records of audience drop-off between the much-hyped opening night and the following week (when word begins to get around that the movie sucks). Schmidt is not the first to attribute this to the creators’ disdain for the characters: Zack Snyder has openly expressed his lack of real interest in Batman and Superman, and made it clear that he doesn’t really understand their appeal. Writer David Goyer has made similar comments. And the same people are already hard at work on the follow-up Justice League films, which seem unlikely to break the pattern of mediocrity.
-
This might be hard to believe for non-farmers, but owners of tractors aren’t actually allowed to fix them, thanks to a set of laws designed to protect software intellectual property.
-
In the quest to stop the FCC from bringing competition to the set top box, the cable industry has trotted out all manner of misleading arguments, most of which have been pushed in editorials in newspapers nationwide without highlighting author ties to the sector. Some of them have tried to pretend that cable box competition will create a piracy apocalypse. Others have tried to somehow argue that better, cheaper hardware and choices will somehow harm minority communities. Most of those are just flimsy attempts to try and keep the FCC from cracking open a $21 billion monopoly on cable box rental fees.
Fearing their own loss of control, the entertainment industry has joined the cable sector in also claiming new cable box rules will somehow violate copyright law. Under the FCC’s original proposal (pdf), the agency simply states that existing cable content must be delivered to third-party hardware using the copy protection of the industry’s choice. Nothing in the rules will change that, or magically give third-party vendors the right to violate copyright. Still, opponents of the rules have consistently tried to claim the rules are some kind of cabal by Google to freeload off of and repackage “their innovation.”
Permalink
 Send this to a friend
Send this to a friend
07.20.16
Posted in Europe, Patents at 4:43 am by Dr. Roy Schestowitz
Patent maximalism (rubberstamping), low examination quality, fiscal preference for large corporations and much more
Summary: Conservative Benoît Battistelli is trying to impose on the European Patent Office various truly misguided policies and he viciously attacks anyone or anything that stands in his way, including his formal overseers
MYSELF and others at Techrights worry deeply. We worry that Battistelli (of UMP, the French conservative party) will turn the Office into another large corporations-leaning USPTO and London (or some other European cities) into the next Eastern District of Texas, complete with venue shifting (dragging defendants to a distant and plaintiff-friendly court), high/unbearable litigation costs that favour settlement in spite of injustice (unless the defendant has deep pockets), massive scope of injunctions (beyond an entire continent), and of course software patents (among other low-quality patents). One reader told us yesterday, “have you heard of the latest load of rubbish from the EPO?” See the above screenshot. No comment is even necessary. How much Europe is there in the ‘European’ Patent Office when foreign companies are enjoying a fast lane?
“How much Europe is there in the ‘European’ Patent Office when foreign companies are enjoying a fast lane?”EPO workers are rightly afraid. Their job security (and their entire employer) has been compromised and is now at mortal risk (stakeholders know what’s happening) because of Battistelli and his friends. Battistelli does not even seem to mind. He attacks sceptics, not just critics. He is like Munich’s Erdoğan. Stability is not the goal; implementing his self-serving vision is the goal. Megalomaniacs can never admit their mistakes and change course.
News sites have learned to distrust Battistelli. Yesterday, for example, Managing IP asked readers about the latest lies from Battistelli's PR department rather than publish an article about it, perhaps seeing it for what it really is (propaganda). Yesterday the EPO PR people were trying to spread the message, but we have not yet seen a single Web site (even IP sites) covering it. Journalists seem to have learned their lesson; Battistelli has zero credibility and zero approval rating among his staff.
“Journalists seem to have learned their lesson; Battistelli has zero credibility and zero approval rating among his staff.”Looking at IP Kat yesterday, we saw nothing but affirmation that people now know better that there is a profound problem at the EPO. “In this context,” one person wrote, “I am also reminded of persistent rumors that the EPO quality is down.” Here is the comment in full:
I reread the discussion again and it seems indeed that the days of the board of appeal are counted. Unfortunately, that also means that the examiners quality will not be controlled any more. When I talk to examiners, their main concern is that the BOA would turn over one of their decisions. THAT is what prevents them from cutting corners.
In this context, I am also reminded of persistent rumors that the EPO quality is down. And I also know that the Office is hiring less competent examiners, quite simply because the pay is not as attractive as it was. Munich is expensive, local firms are not finding the engineers they need and have raised their entry salaries accordingly while the EPO has lowered theirs.
I also read here that some patent attorneys are suggesting that the applicants use the national route, for increased legal certainty. How will that solve their problems when the competitor comes with an infrigement case based on an unclear, vague patent granted by the EPO and validated by the UPC, which will have force of law in all EU states?
Another person wrote that “at least in 2015, the EPO faced significant problems in recruiting.” We keep hearing from numerous sources that the EPO is struggling with brain drain and accordingly it lowered the recruitment bar. New workers don’t receive the same type of salaries and almost none of the benefits (not even job security). They are pressured to grant a lot of patents to justify their place at the EPO, which is exactly what happens at the USPTO (with notorious quality control in recent years). Here is the comment in full:
If you want to know the future of the EPO, take a peek at the official “social report”:
http://documents.epo.org/projects/babylon/eponet.nsf/0/CA803AEC70D6E89FC1257FF40042DAA4/$File/social_report_2015_en.pdf
Despite being nothing more than a dry and dusty collection of statistics, the report contains some interesting figures.
Some of these clearly demonstrate that, at least in 2015, the EPO faced significant problems in recruiting. For example, relative to the figures for 2014:
Numbers of advertised vacancies: up >25%
Number of job applications received: down 12%
Nationalities decreased presence: GB (-32), DE (-29), NL (-28), AT (-10), SE (-7), DK (-6), CH (-5), IE (-3), PT (-1), LU (-1)
Nationalities increased presence: RO (+9), ES (+8), IT (+6), PL (+6), TR (+4), BG (+3), RS (+3), LT (+2), FI (+1), FR (+1), HR (+1), MK (+1)
Permanent staff: down 1.3%
Contract staff: up 13.45%
New hires: down 30%
Termination of employment: up 44%
Increases in termination: retirement (+51%), resignation (+44%), invalidity (+36%)
The figures also show signs of increasingly aggressive management tactics, such as no strikes allowed in 2015 (vs. 22 days in 2014), 99% of all internal appeals rejected (vs. 88% in 2014). The trend at ILOAT, however, is going in the opposite direction (with allowed or partially allowed cases virtually doubling in percentage).
Given the shocking trends that it reveals (which appear to point to an organisation that is in crisis), I am somewhat surprised that this report was produced at all.
What do the AC have to say about this? Figures that speak for themselves surely cannot be brushed under the carpet so easily.
Responding to the above, one person wrote: “Of course they can – at the European Patent Office the money brought in by the increased productivity speaks louder than any figures.”
“It is true that the office is experiencing difficulties at recruiting,” another person noted:
It is true that the office is experiencing difficulties at recruiting. But that did not stop Minnoye to start a project to eliminate all examination stock backlog until end 2020. The project involves recruiting enough examiners to deal with the backlog (=hundreds) thereby creating “overcapacity”. The project started this month, the first applicant were sent letters requiring them to state wether they were still interested in examination.
Minnoye will push this at all cost: stock must be zero within 4 years.
The EPO’s “AC is a permanent fixture, and so will eventually have to deal with the mess that is currently being created,” one person wrote. The comment in full:
Sure, but the increase in money will only be a short-term effect. Unlike BB, the AC is a permanent fixture, and so will eventually have to deal with the mess that is currently being created. From this perspective, I still find it somewhat puzzling that the AC is doing so little to stop BB dynamiting the foundations upon which the EPO (and its reputation) is built.
It won’t be long before the general public, not just insiders at the EPO, recognise this crisis and demand change. It’s not too late to save the EPO, especially if there is public acknowledgement of the errors and then an effort to fix the errors. The main problem, however, remains; attracting again the same experienced examiners (some of whom left or retired early) is impossible and revisiting all the erroneously-granted patents would be laborious and harm ‘customer’ confidence.
Battistelli has secured his place in history books for the same reason Erdoğan has. █
Permalink
 Send this to a friend
Send this to a friend
07.19.16
Posted in News Roundup at 6:25 am by Dr. Roy Schestowitz

Contents
-
After some “going back and forth”, Bryan and I have decided it was high time we did a proper show together. Here are the details you need to know. Yes, it’s actually happening!
-
Ever since I first tried Linux on my desktop years ago, I’ve found myself wincing at what I felt were avoidable blunders. This observation doesn’t affect one distro more than another, rather it’s ongoing issues I’ve watch in utter amazement happen time and time again.
No, I’m not giving a free pass to proprietary operating systems as they also have their share of epic blunder moments. But with Linux on the desktop, I guess you could say it just hits a bit closer to home. Remember, these are not merely bugs – I’m also talking about avoidable issues that affect folks even if they don’t realize it.
-
Desktop
-
The Register claims that MS16-094 fixes a loophole that allowed users to install other operating systems on Windows RT devices, including here Linux. With Windows RT becoming an OS with no future, many have looked into ways to install a different operating system on the Surface RT, but most attempts failed because of the locked bootloader and the other security systems that Microsoft put in place.
-
Kernel Space
-
Intel developer Kan Liang has published a set of 30 patches amount to more than two thousand lines of new kernel for implementing what he calls the Kernel NET Policy.
-
As promised, Intel has open sourced an early version of its SGX tool for Linux. Intel SGX is a set of instructions that create a private region for sensitive code and data. This enclave is invisible to even the machine’s CPU with root privileges. At the moment, this release only supports Ubuntu 14.04 LTS 64-bit version.
-
At the Embedded Linux Conference, Grant Likely — who is a Linux kernel engineer, and maintainer of the Linux Device Tree subsystem used by many embedded systems — described his embedded hardware journey in a presentation called “Hardware Design for Linux Engineers” — or as he put it, “explaining stuff I only learned six months ago.”
-
Graphics Stack
-
The Linux 4.7 kernel is expected to be officially released this coming weekend, but a pile of Intel Kabylake fixes are needed if the DRM graphics support is to be in order.
Intel’s Daniel Vetter sent in a request to DRM subsystem maintainer David Airlie to consider pulling these Kabylake (KBL) fixes for Linux 4.7. He explained, “here’s the pile of kbl cherry-picks assembled by Mika&Rodrigo. It’s a bit much, but all well-contained to kbl code and been tested for a while in drm-intel-next. Still separate in case too much, but in that case I think we’d need to disable kbl by default again (which would be annoying too) in 4.7.”
-
-
-
libinput 1.4.0 is now available. New features since the RC are a reduced
middlebutton area on Dell clickpads. All Dell touchpads have a visible
marker between the left and the right button so the middle button can be
smaller too – users have a visual guide where to click.
-
Libinput 1.4 was officially released over night to add new features to this input handling library used by Wayland, X.Org, and Mir systems.
-
Applications
-
Machinery is a command line application for creating descriptions of Linux systems and working with them.
-
Proprietary
-
A $1.24 billion agreed takeover of Norwegian online browser and advertising company Opera Software by a Chinese consortium of internet firms has failed, Opera said on Monday, after warning last week the deal had yet to win regulatory approval.
As an alternative, the consortium, which includes search and security business Qihoo 360 Technology and Beijing Kunlun Tech, a distributor of online and mobile games, will take over certain parts of Opera’s consumer business for $600 million, Opera said in a statement.
Regulatory approval had not been received in time of a final deadline for the deal last Friday, the chairman of Opera Software said on Monday.
-
-
-
-
-
-
Instructionals/Technical
-
Games
-
Earlier this year a Kickstarter campaign was started to develop a System Shock remaster from the ground up. Not only has that campaign been fully funded now, it has 10 days to reach its stretch goal of $1.1 million that would allow developers to create a Linux and Mac OS port of the game. Right now the game is above $1 million so the campaign only has to raise less than $0.1 million to make this port a reality.
-
Marek Olšák of AMD has been working on some Gallium3D optimizations for boosting the performance of the popular BioShock Infinite game on Linux.
-
GDC Europe ran a survey of 800 games industry professionals who attended a previous GDC event and about 17% stated they plan a game for Linux.
It’s a really weird survey, as it pulls Windows/Mac together, but has Linux by itself. It would make more sense to have all three separated. They also say PC when they mean Windows, which is always annoying to see. Still, it’s a pretty healthy percentage considering only a few years ago it would have probably been 0-1%.
It’s also amusing to see them do the survey, have Linux as an option which beats out multiple other platforms, yet they don’t mention anything about Linux in the text.
-
-
Ballistic Overkill is the fast paced FPS game I have fallen in love with and it just gained a tasty update.
The game has down away with a single health station on the map, to now have health packs spread throughout the map. An interesting and needed change, but I feel they respawn far too quickly.
The map voting system is much better. Instead of always being on a single mode, you pick a single map and each map comes with a different game mode. That makes the game feel a lot fresher in my opinion and helps stop me getting bored in longer sessions.
-
Lost Sea is a really nice idea, mixing up action, adventure, RPG and random generation together to create something interesting. You also lose almost all progress when you die, so there’s the punishment factor here. You don’t lost everything, you get a bit of gold and XP for each tablet you get on the previous run.
You sail from island to island collecting treasures, killing monsters and collecting stone tablets that enable you to move further along in your journey. It all sounds pretty good, but I’ve found the game to be rather lacking in every aspect of its design.
The combat just seems so basic and lifeless it really lets down what could have been a very exciting game. You can upgrade your skillset to have a few nice extras but even so, it still feels a bit empty. It’s not terrible though, just not really all that challenging at all, no real excitement factor to the combat. It’s literally mash X a few times, maybe use a skill if you need too and—done.
-
-
-
Undertale recently released on Steam, but this weird 2D RPG is now also available DRM free on GOG. I know a few of you were waiting for this!
My friends at GOG sent over a key and I can confirm it seems to work fine, I didn’t encounter any obvious issues in my testing of the GOG build.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
We have recently open sourced Qt WebBrowser!
-
-
After hopping between Red Hat Linux, CentOS, Fedora, and Ubuntu LTS over the past decade, I recently decided to give KDE Neon a shot.
The potential of a cutting edge desktop environment on a stable 16.04 Ubuntu base really attracted me, the first because I’m a stickler for a good GUI based UX, and the latter because most current software is built against RHEL/Ubuntu.
However I should preface this by saying that I spend more time on Windows than the GNU/*nix based OS’s combined, and so my perspective in this review may be different than how you feel.
-
First of all I need help, but before you help me I’d like to show you what a user without development skills can do to make plasma better.
I already post about the system settings redesign and cause developer are busy with other tasks, I reviewed the existing modules and update them to fit (more) our vision. I know it’s not how I would prefere in the end but I did the changes without development skills (no compiling, no new code). I use qt-creator for edit the ui files and play around with qml.
The Mouse cursor theme was updated, by move the buttons to bottom as in most other kcm’s. The height of the resolution depandant button will be change soon. (left plasma 5.7 right 5.8)
-
-
Every year I start to create a new book, every year I delete the book folder because I think it’s going into the wrong direction, and ths year is no different, I’m starting to write a book about Qt5 programming with C++11, I hope this time things can go different. And what I usually do is setup my LaTeX enviroment (kile, texlive, a few libraries and all that) – but I was hitting a UTF8 issue that \includepackage[utf8 or utf8-x][inputenc] didn’t solved… And if you are not well versed in Tex debugging things can go hairwire in just no time.
-
-
PCLinuxOS/Mageia/Mandriva Family
-
Today in Linux news the Mageia project announced the winner of their artwork contest for upcoming version 6 as well as some of the other being included. OpenMandriva 3.0 Release Candidate 1 is available for download although the project has yet to announce it and Korora 22 is nearing the end of support. Matt Hartley identified the top six Linux desktop blunders and several Linux reviews caught my eye today.
-
We have completed the artwork contest and would like to extend our thanks to everyone that took part, there were some excellent pieces submitted and choosing the winners was a tough task.
We would like to congratulate Jacques Daugeron on winning the background contest, the runners up will be available in the extra theme package as well.
Here is the signature background for Mageia 6, it will be included in the next updates to the theme packages.
-
The first half of this year, I had the chance to work on icon and design for two big free-software projects.
First, I’ve been hired to work on Mageia. I had to refresh the look for Mageia 6, which mostly meant making new icons for the Mageia Control Center and all the internal tools.
-
Red Hat Family
-
Red Hat is the newest organization to take a stab at the persistent storage challenge for containers. Last month, the open source giant announced a new Gluster-based storage option for OpenShift, the company’s open source platform for running containerized apps.
Gluster and OpenShift are two key parts of the Red Hat technology stack. Gluster provides open source distributed storage, while OpenShift offers an integrated, one-stop platform for deploying and managing containers using Docker and Kubernetes.
-
CentOS 7.2 Xfce is the most satisfactory distribution on the market today, alongside Trusty. Not perfect, not plug-n-play, but it is supported, stable and quite friendly. I did need several hours to sort things out, and that’s the price for converting a server distro into a home operating system.
In this guise, it works well, with a few small exceptions, one or two outstanding niggles that need fixing, and the knowledge that I needed some third-party gear to achieve the level of productivity that I normally seek. That precludes CentOS 7 from being perfect or a candidate for my production setup, but it might be just the thing for you. If you’re not as bothered as I am around unofficial repos and adding some extra software on your own, then look no further. CentOS 7.2 Xfce is a slick, modern, good-looking choice with all the goodies for a healthy modern life. It is better than KDE and Gnome flavors, and comes with the unbeatable blend of simplicity and functionality.
If anyone out there is interested in making the perfect home distro, based on Red Hat, please consider my words as a template for what needs doing. Drivers (signed), third-party software, basic customization. And that’s it. So simple. Then again, so difficult. But this is the most sensible formula for desktop use you will have seen in a long, long time. Enjoy.
-
Finance
-
Fedora
-
As Korora uses Fedora as the base for our distribution and thus follow the Fedora Project’s life cycle, Korora 22 Selina will reach it’s End Of Life status on 22nd July.
-
Last week I attended the Fedora APAC budget planning FAD for FY’18. Ie. planning for Fedora activities that we expect to conduct between Mar 2017 – Feb 2018 and requisite budget for the same. Last year with Fedora.next reforms, we adopted a new approach to regional budget planning with an aim to increase transparency in the process. In this, each geographical region(ex. APAC) elects three delegates who handle major regional responsibilities. The Treasurer manages regional finance. The Logistician takes care of swag/media/banner production, dispatch and general coordination for Fedora presence at various events. And the Storyteller would collate information about regional events/activities and their impact/benefits to the Fedora project and report the same to the Fedora Community Action and Impact Lead(FCL) and the Fedora Council.
-
-
I have a degree in software engineering. For over 12 years, I’ve worked as a Unix system administrator, with a short stint as a software engineer. Currently, I work for Citi as a senior IT infrastructure analyst. My primary responsibility at work is expert-level support of a heterogeneous environment consisting of RHEL, Solaris and AIX systems, both physical and virtual machines. Working at Citi while simultaneously being a Fedora developer allowed me to see both ends of the distribution development process and made me appreciate the excellent work of Fedora contributors even more. My past jobs include development of a particle detector model at CERN and system and network administration at the supercomputing centre of the University of Warsaw.
-
Debian Family
-
Handy Linux has come out with handy Linux its new weapon in its arsenal. It is quite a simplified version to use the Linux operating system on desktop. The Handy Linux surfaced at around three years ago, however in June the latest version was released.
The developers have made it easy to remove the layers of Handy Linux to reveal the more standard Linux environments which the users can learn. The users who do not need the IT installation tools included in the initial installation can delete them using Handy2Ddebian app from Handy’s main menu.
Handy Linux is a standard Debian based OS which is light and shows some mix of Xfce desktop ecosystem. The remixed desktop is the signature mark for the Handy Linux.
-
On July 5th, 2016 Michael Biebl spoke at DebConf16 on systemd in Debian.
-
Derivatives
-
Canonical/Ubuntu
-
A video demoing wireless convergence on the Bq M10 Ubuntu Edition tablet has been shared by Canonical today.
Ubuntu phone fans will know that wireless display technology was made available to users of the Meizu PRO 5 Ubuntu phone in last month’s OTA-11 update.
But for its latest over-the-air update Ubuntu is bringing it to the Bq Aquaris M10 Ubuntu Edition slate, which went on sale earlier in the year.
“Our latest OTA-12 has just landed and we’re excited that you can now wirelessly connect your M10 tablet to a monitor,” Canonical say in the description accompanying the video.
OTA 12 is, at the time of writing, scheduled to begin phased roll out from July 27, so don’t panic if you don’t get the update just yet!
-
-
Sometimes the best tutorials come not from experts, but from proficient newcomers who are up to date on the latest entry-level technologies and can remember what it’s like to be a newbie. It also helps if, like Grant Likely, the teacher is a major figure in embedded Linux who understands how hardware is ignited by software.
-
Perfectron’s rugged “SR10M” system offers a 4th Gen Core CPU, four GbE ports, stackable expansion, -40 to 70° operation, and MIL-STD-810G ruggedization.
The SR10M is the latest in Perfectron’s Stackrack series of rugged, MIL-STD-rated stackable embedded computers equipped with Intel Haswell CPUs and designed primarily for military vehicles. The SR10M is built around an OXY5737A EBX form-factor single board computer (see farther below) equipped with the quad-core, 2.4GHz (3.4GHz turbo) Intel Core i7-4700EQ of the fourth “Haswell” generation of Core CPUs. It also offers an Intel QM76 chipset.
-
Phones
-
Android
-
HMD Global, which purchased the Nokia brand from Microsoft this past May, is said to be developing two Android smartphones with a metal design and the “famous Nokia feel,” Nokia fan blog NokiaPowerUser said on Saturday, citing “trusted sources.”
-
-
-
-
-
-
-
-
-
-
-
Looking for ways to draw meaningful conclusions from big data?
In his lightning talk at Great Wide Open 2016, Rommel Garcia gives us quick takeaways for three open source tools that help Hadoop users do just that…
-
Splice Machine is a well-kept secret though; Zweben told me the company has about 10 customers. Although he hails from the world of commercial software, Zweben believes that open sourcing the Splice Machine product will help spread the word more widely. So version 2 of the product will be available in a free and open source Community Edition with the full database engine. A paid Enterprise Edition, that includes professional support and DevOps features like integration with LDAP and Kerberos as well as backup and restore, will provide the monetization model for the company.
-
-
-
Around the time that Splice Machine announced a milestone version of its RDBMS, which it bills as “the first hybrid in-memory RDBMS powered by Hadoop and Spark,” its fortunes were starting to rise along with Hadoop’s and Spark’s. In the big data space, there is tremendous need to marry powerful data analytics tools with powerful database tools. If you’re focusing on the Big Data and NoSQL arenas, along with relational databases, Splice Machine is worth a look.
Now, Splice Machine is going open source, and it is also going live in a sandbox version on Amazon Web Services (AWS), so you can easily give it a try.
Splice Machine aims to be a database solution that incorporates both the scalability of Hadoop, ANSI SQL, ACID transactions, and the in-memory performance of Spark.
-
Almost everyone can agree the digital era is being fueled by five primary forces — mobile, social, sensor technologies, big data and the cloud. But doesn’t open source play a role in digital transformation as well?
That was one of the topics discussed last week during a roundtable discussion sponsored by MIT Technology Review Custom and EnterpriseDB (EDB). The explored how open source software is helping organizations transform their infrastructures to meet today’s data-driven demands.
-
Bitcoin is not anonymous. Anyone who has followed the dark web or the continuing regulation of the cryptocurrency should be familiar with that idea. If someone manages to link a real identity to a wallet—something that we’ve seen is possible—they can then follow other transactions around the public blockchain to see where else that person’s money has traveled.
-
Almost two years ago, I began the process of building an Impact Tracker at The Center for Investigative Reporting to help us better understand the results of our work. Flash forward to today, and we have a custom-built platform that is being used by more than 20 organizations around the world.
Today, we are releasing an open-source version, available to any organization.
-
Over 2,000 individuals wearing circuit board badges learned and talked about all things open source this past weekend at the South Towne Expo Center. The OpenWest conference is the largest regional tech conference promoting all things open— hardware, software, data, standards and more.
The conference is put on by Utah Open Source and sponsored by V School, Electronic Frontier Foundation, Podium and Protocol, among others.
Open source refers to software that anyone can see and edit. Open-source code is typically created in collaboration with both online and real-life communities. Liz Sands-Adams, OpenWest’s Director of the Privacy Education Track, said, “OpenWest survives because of a volunteer community that believes in empowering the open-source communities around them.”
-
With so many great open source projects spreading like wildfire, it is a great time to be a developer! I spend a considerable amount of time looking for great ideas across the open source community. For me, I’m always searching for modules we might include in our distributions, projects that could be enhanced and commercialized, or even crossovers into other areas for innovations. If something really resonates with our business we will apply resources to furthering that project.
Generally, the first thing I do is hit the project description to see if it makes a connection with me. If it does, I’ll try it out or tag it for further research, perhaps even mention it on Twitter or discuss internally on a relevant Slack channel. Note, I did not look at your code, I looked at the idea. If you want your code to get out into the community, and actually ignite something bigger, you need to make sure your project is discoverable.
-
Web Browsers
-
Mozilla
-
Pale Moon 27 Alpha 1 fixes various site compatibility issues, ECMAScript 6 improvements, MSE support, and more.
-
-
SaaS/Back End
-
Prometheus, an open source system for monitoring and alerting a wide spectrum of enterprise IT events, including containers, released its 1.0 revision this week.
It’s also the second product in what amounts to a portfolio assembled by the CNCF (Cloud Native Computing Foundation) for realizing the promise of a container-powered cloud built entirely on open source and open standards.
-
-
To avoid any confusion, let’s make this clear: OpenStack is a cloud-operating system. OpenStack is not a VM, but rather sits on top of VMs. Also, OpenStack is written in Python.
As you install each component, OpenStack installs a command-line tool that works in tandem with it. The problem is that each component — of which there are dozens — has its own command-line tool, each with its own name and parameters. For example, you run Keystone to install users and roles in the Identity Service. Then you run Glance to load VM images. You would then use Nova to deploy those images. After a while, the sheer number of components and their respective command-line tools can get overwhelming.
So, other than the command line, what options do we have to simplify the OpenStack installation process? Let’s have a look.
-
Pseudo-Open Source (Openwashing)
-
BSD
-
At VidiGuard, we care a lot about physical security. In fact, it’s our job. But equally important to physical security is the security of our customers’ data. We also need a robust, reliable platform that can run with minimal interaction. To make both of those happen, we employ OpenBSD in our on-premise equipment and our data infrastructure. Why OpenBSD?
-
For some time now, I’ve been running OpenWRT on an RT-N66U device. I initially set that because I had previously been using my Debian-based file/VM server as a firewall, and this had some downsides: every time I wanted to reboot that, Internet for the whole house was down; shorewall took a fair bit of care and feeding; etc.
I’ve been having indications that all is not well with OpenWRT or the N66U in the last few days, and some long-term annoyances prompted me to search out a different solution. I figured I could buy an embedded x86 device, slap Debian on it, and be set.
-
Right on schedule the LLVM 3.9 code was branched today in preparation for its formal release next month.
LLVM 3.9 is another six-month feature update to the LLVM compiler stack. We’ll have more on its features and performance in the weeks ahead, in addition to the LLVM Clang benchmarks we already do daily with it at LinuxBenchmarking.com.
-
FSF/FSFE/GNU/SFLC
-
With GCC 6.2 coming soon and GCC 5 already being quite mature, GNU Compiler Collection developers are intending to soon end maintenance on GCC 4.x.
-
Openness/Sharing/Collaboration
-
Open Hardware/Modding
-
Check out the videos below to learn more about the open source laptop project that allows you to easily build, upgrade and fix your very own portable laptop computer.
-
Programming/Development
-
I run firefox on Linux, and chrome on my ancient Google phone, but I’m not a browser wonk. Maybe I’ll have more opinions on that after our JS backend is done for Perl 6…
-
This release includes a small number of fixes to severe bugs in Pulp Platform, the RPM plugin, and the Docker plugin.
-
DevOps uses languages for software development and languages for deployment automation. If you want to be successful with either side of DevOps, these languages will help.
-
Science
-
Researchers from Delft University of Technology in the Netherlands have created a rewritable data-storage device capable of storing information at the level of single atoms representing single bits of information.
The technology, which is described in the current issue of Nature Nanotechnology, is capable of packing data as dense as 500 terabytes per square inch. Theoretically, the device could store the entire contents of the US Library of Congress within a 0.1-mm-wide cube—though the proof-of-concept demonstrated by the group topped out at 1 kilobyte.
-
Hardware
-
Like far too many things in this world, enterprise networking seems to bounce between two extremes. One year, hardware acceleration is all the rage. The next, a software-only approach seeks to transform the way networks are built and deployed altogether. In reality, new networking approaches such as software-defined networking (SDN) and networking functions virtualization (NFV) will require a balance between hardware and software.
-
The boards of directors of SoftBank and ARM have announced that they have reached an agreement on the terms of a recommended all-cash acquisition of ARM for GBP24.3 billion (US$32.2 billion).
-
UK technology firm ARM Holdings is to be bought by Japan’s Softbank for £24bn ($32bn) it confirmed on Monday.
The board of ARM is expected to recommend shareholders accept the offer – which is around a 43% premium on its closing market value of £16.8bn on Friday.
The Cambridge-based firm designs microchips used in most smartphones, including Apple’s and Samsung’s.
-
HARDWARE –
Many news reports this morning are indicating that Japan’s SoftBank is working out a deal to buy ARM Holdings and that a deal could be officially announced as soon as this morning.
-
Health/Nutrition
-
It only takes $2 and a few minutes to ruin someone’s life. Field tests for drugs are notoriously unreliable and yet they’re still considered to be evidence enough to deprive someone of their freedom and start a chain of events that could easily end in joblessness and/or homelessness.
Ryan Gabrielson and Topher Sanders — writing for the New York Times magazine — take a detailed look at these field tests, filtered through the experience of Amy Albritton, who spent 21 days in jail thanks to a false positive.
A traffic stop that resulted in a vehicle search turned up an empty syringe and a “suspicious” crumb of something on the floor. The field test said it was crack cocaine. Albritton was taken to a county jail where she spent the next three weeks after pleading guilty to possession, rather than face a trial and a possible sentence of two years.
The crumb of whatever had been sent on to a lab for verification, but with Albritton’s guilty plea, there was no hurry to ensure the substance retrieved from Albritton’s car was actually illegal. In fact, with the case adjudicated and closed, the evidence could simply have been destroyed. It wasn’t. Long after Albritton had been released, the substance was tested.
-
“Indian Point” is a film about the long problem-plagued Indian Point nuclear power plants that are “so, so risky—so close to New York City,” notes its director and producer Ivy Meeropol. “Times Square is 35 miles away.”
The plants constitute a disaster waiting to happen threatening especially the lives of the 22 million people who live within 50 miles from them. “There is no way to evacuate—what I’ve learned about an evacuation plan is that there is none,” says Meeropol. The plants are “on two earthquake fault lines,” she notes. “And there is a natural gas pipeline right there that an earthquake could rupture.”
Meanwhile, both plants, located in Buchanan, New York along the Hudson River, are now essentially running without licenses. The federal government’s 40-year operating license for Indian Point 2 expired in 2013 and Indian Point 3’s license expired last year. Their owner, Entergy, is seeking to have them run for another 20 years—although nuclear plants were never seen as running for more than 40 years because of radioactivity embrittling metal parts and otherwise causing safety problems. (Indian Point 1 was opened in 1962 and closed in 1974, its emergency core cooling system deemed impossible to fix.)
-
Last December, Techdirt wrote about Australia fending off an attempt by Philip Morris to use corporate sovereignty to overturn the country’s plain-packaging regulations. As we pointed out, this wasn’t proof that investor-state dispute settlement (ISDS) was no threat to national sovereignty, despite what some were claiming. Australia won on purely procedural grounds, not because the ISDS tribunal agreed that Australia had a fundamental right to regulate.
-
Security
-
Ubuntu support forums users should be on the lookout for dodgy emails after the website’s database of 2 million email addresses was stolen.
Canonical announced the security breach on Friday after being notified that someone was claiming to have a copy of the UbuntuForums.org database. An investigation revealed that an attacker did get access to the website’s user records through a vulnerability.
-
-
-
-
-
-
-
-
-
A known SQL injection vulnerability affecting vBulletin software was exploited by an attacker to breach the Ubuntu Forums database.
-
Ubuntu aficionados beware, as a data breach of the Ubuntu Forum has resulted in the leak of information for two million users. It should be noted that the breach has not hit Canonical Ltd., which runs the Ubuntu operating system, but rather the forum, so other services are still safe.
The notice from Canonical explains that the breach was made possible through an SQL injection vulnerability in the forum’s Forumrunner add-on, which had not been patched. By injecting certain formatted SQL into the forum database, the hacker could then reach any table, particularly the “user” table.
-
-
-
-
-
Ubuntu Forums was previously hacked in 2013.
-
Ubuntu Linux developer Canonical has confirmed that a data breach exposed personal information of two million users of its forum.
-
Gaming two-factor authentication systems with premium rate phone numbers can be very profitable – or it was until the flaws got reported.
Belgian security researcher Arne Swinnen noticed that the authentication systems used by Facebook-owned Instagram, Google and Microsoft allow access tokens to be received by a voice call as well as a text message. By linking accounts to a premium-rate phone number he controlled and could pocket money from, he was able to scam the three companies out of cash – in some cases potentially thousands of dollars a day.
-
-
In today’s market, open source professionals with security expertise are crucial players on an employer roster. The growing use of cloud and big data, as well as the overhaul and expansion of many companies’ tech infrastructures, are driving the demand and need for professionals with this skillset.
According to the 2016 Open Source Jobs Report, 14 percent of hiring managers and recruiters surveyed believe security to be the most important open source skill to date, ranking third just behind cloud technologies (51 percent) and networking (21 percent). Employers aren’t the only ones that see the value in security; 16 percent of open source professionals surveyed cited security as the most important open source skill and the biggest driver for open source growth in 2016.
-
AT&T this week unveiled a new powerful security platform, using big data analysis based on a Hadoop architecture which allows the company to ingest and analyze 5 billion security events in less than ten minutes.
-
Software security has been in the news a lot lately, between various high profile social media hacks to massive data breaches it feels like people in the industry are always talking about security, or more appropriately, the lack thereof. While having a conversation with somebody from my company’s internal security team a few weeks ago I had a bit of an epiphany: security in 2016 is much like quality was in 1999.
Let’s think back 17 years and remember what the quality process was like in 1999. Code was written in rather monolithic chunks with very little thought (if any) given to how that code was to be tested. Testers were on completely separate teams, often times denied access to early versions of the software and code. Testers would write massive sets of test cases from technical specifications and would accept large drops of code from developers only after a feature was considered completed. Automation was either a pipe dream or only existed for very stable features that had been around for a while. A manual testing blitz would then kick off, bugs would be filed, work thrown back over the wall, rinse and repeat. After several of these cycles it was the testers job to give a go/no-go on whether the product was good enough to ship, essentially acting as gatekeepers.
-
There’s no shortage of futurists, industry analysts, entrepreneurs and IT columnists who in the past year have churned out reports, articles and books touting blockchain-based ledgers as the next technology that will run the world.
In the middle of all this hype is a small fire that threatens to put some of those words to ash: The hijacking last month of around US$40 million of dollars worth of a cryptocurrency called ether – named after its blockchain platform, Ethereum — from The DAO, a crowd-sourced investment vehicle that has so far raised over US$100 million in the digital currency. Instead, the DAO has become paralyzed and on the verge of collapse.
-
Researchers at Sandia National Laboratories in New Mexico are experimenting with encrypted DNA storage for archival applications.
Husband and wife team George and Marlene Bachand are biological engineers with a remarkable vision of the future.
The researchers at the Sandia National Laboratories Center for Integrated Nanotechnologies foresee a time when a speck of DNA on a piece of paper the size of a millimeter could securely store the entire anthology of Shakespeare’s works.
-
-
-
-
A criminal gang recently found an effective way to spread malware that drains online bank accounts. According to a blog post published Monday, they bundled the malicious executable inside a file that installed a legitimate administrative tool available for download.
The legitimate tool is known as Ammyy Admin and is used to provide remote access to a computer so someone can work on it even when they don’t have physical access to it. According to Monday’s blog post, members of a criminal enterprise known as Lurk somehow managed to tamper with the Ammyy installer so that it surreptitiously installed a malicious spyware program in addition to the legitimate admin tool people expected. To increase their chances of success, the criminals modified the PHP script running on the Ammyy Web server, suggesting they had control over the website.
-
Defence/Aggression
-
Initial reports said up to 20 people had been injured but it was later revealed that at least 14 had been treated for shock.
The motive for the attack is not yet clear.
Bavarian Interior Minister Joachim Herrmann said the attacker was a 17-year-old Afghan refugee who had been living in the nearby town of Ochsenfurt.
-
Former House Speaker Newt Gingrich called for banning Sharia. Will greater war on Islam follow than already?
Wall Street Journal editors hyped Islamophobia, saying “Jihad has become the default assumption of our age.”
They urged strengthening NATO, shamelessly claiming it’s to protect freedoms from “21st-century barbarism,” ignoring the real thing.
State-sponsored war on humanity is terrorism’s most extremist form. Expect lots more coming – an endless body count of imperial victims.
-
Donald Trump has condemned the Iraq War as a “disaster,” but he showed little concern during a 60 Minutes interview, broadcast Sunday, that his vice presidential candidate, Indiana’s Republican Gov. Mike Pence, was an outspoken advocate of that invasion.
After Trump proclaimed that the United States should not have invaded Iraq because it had no involvement in 9/11, interviewer Lesley Stahl reminded him that his running mate, then-Indiana Republican Rep. Mike Pence, voted to authorize the war.
-
Turkey’s President Recep Tayyip Erdogan places the blame for this weekend’s failed coup attempt on an Islamic preacher and one-time ally, Fethullah Gulen (above), who now resides in Pennsylvania with a green card. Erdogan is demanding the U.S. extradite Gulen, citing prior extraditions by the Turkish government of terror suspects demanded by the U.S.: “Now we’re saying deliver this guy who’s on our terrorist list to us.” Erdogan has been requesting Gulen’s extradition from the U.S. for at least two years, on the ground that he has been subverting the Turkish government while harbored by the U.S. Thus far, the U.S. is refusing, with Secretary of State John Kerry demanding of Turkey: “Give us the evidence, show us the evidence. We need a solid legal foundation that meets the standard of extradition.”
In light of the presence on U.S. soil of someone the Turkish government regards as a “terrorist” and a direct threat to its national security, would Turkey be justified in dispatching a weaponized drone over Pennsylvania to find and kill Gulen if the U.S. continues to refuse to turn him over, or sending covert operatives to kidnap him? That was the question posed yesterday by Col. Morris Davis, former chief prosecutor of Guantánamo’s military commissions who resigned in protest over the use of torture-obtained evidence:
That question, of course, is raised by the fact that the U.S. has spent many years now doing exactly this: employing various means — including but not limited to drones — to abduct and kill people in multiple countries whom it has unilaterally decided (with no legal process) are “terrorists” or who otherwise are alleged to pose a threat to its national security. Since it cannot possibly be the case that the U.S. possesses legal rights that no other country can claim — right? — the question naturally arises whether Turkey would be entitled to abduct or kill someone it regards as a terrorist when the U.S. is harboring him and refuses to turn him over.
-
Once again there will be an influx of notes of sorrow, by now customary calls for unity in face of the terror gripping our cities, our streets: the spaces of our public, convivial existence.
But there is already something not-quite-right about the prime sentiment that grips some of us this morning as we skim through the endless videos of Nice’s howling urban beach-front stampede. The feeling that the city’s screaming agony is on the verge of becoming as commonplace as the street lights and the wide avenues on which it unfolds: an inseparable, however unwelcome, by-product of urban life.
-
Any aspect of instability in the state of Turkey is going to be greeted with trepidation by those partners who bank on its security role between East and West. The European Union, that rattled club of members who fear the next onslaught against its institutional credibility, have been bolstering Ankara in the hope to keep refugees at bay. There are security exchanges, and promises (always promises) of sweeter deals regarding the movement of Turkish citizens.
-
Turkish President Erdogan crushed a military coup this weekend but this victory for civilian rule will do little to revive Turkish democracy which Erdogan has been strangling with his autocratic grip on power, notes ex-CIA analyst Paul R. Pillar.
-
-
Newly installed U.K. Prime Minister Theresa May is prepared to authorize a nuclear strike that could kill hundreds of thousands of innocent people.
So she said before Parliament on Monday, as the body debated whether to renew Trident, Britain’s aging nuclear weapons system.
According to the Independent, May was challenged on her support for the program by the SNP’s George Kerevan, who asked: “Are you prepared to authorize a nuclear strike that could kill hundreds of thousands of men, women and children?”
-
As ISIS continues to have devastating effects on Iraq, the country is facing some of the most profound challenges it has seen in the last decade. Rachel Sider, Humanitarian Policy Advisor, comments on the need for governments to prioritize the area as they meet this week in the United States at a donor pledging conference.
-
Despite Israeli and neocon-led doomsday talk, the year-old Iranian nuclear agreement has achieved its principal goal of stopping Iran from getting the Bomb and has even quieted alarums from Israel, writes Trita Parsi.
-
CODEPINK will be part of the Coalition to Stop Trump and March on the RNC and the End Poverty Now! March on Monday, July 18th to protest the GOP’s corporate backers profiteering off of endless war abroad while the shameful epidemic of poverty continues unabated in the richest country on the planet.
-
President Tayyip Erdogan is taking advantage of the failed coup against him to purge the judiciary and security forces of anyone who is lukewarm toward or actively critical of him.
These steps are, of course, the opposite of the ones Erdogan should be taking– he should be attempting to bring the country together in unity and to re-include in the polity those he has isolated and excluded in recent years. Instead, he is scapegoating and purging.
Erdogan characterizes this purge as against the secretive and cult-like Gulen movement, one element in Turkey’s landscape of the religious Right. He blames the Gulen movement for the attempted coup, though its leader (in exile in Pennsylvania), Fethullah Gulen, denies the allegation.
-
Transparency/Investigative Reporting
-
-
Wikileaks says it is preparing to release more than 100,000 documents related to the Turkish government in the wake of a failed coup in the country that left hundreds dead, thousands injured and more than 7000 in custody.
-
-
-
-
-
-
Johnson had long argued that emails from his personal account weren’t subject to public records laws — even those in which government business was discussed. And, indeed, the city has no policy in place preventing officials from using personal email accounts to conduct official business. However, that’s not the same thing as saying these emails can’t be obtained with public records requests.
When that argument failed to keep the emails from being released, Johnson’s lawyer raised the good old “attorney-client privilege” as a shield against public disclosure. Judge Krueger shot that down as well.
[...]
In the end, it’s a win for the Sacramento News & Review, which was one the parties named in Mayor Johnson’s email-blocking lawsuit. Given the nature of the disputed emails, it’s easy to see why Johnson wanted to keep them out of the public’s hands. Many of the communications cover Johnson’s takeover of the National Conference of Black Mayors — a leadership position he held tenuously, briefly, and under a considerable amount of criticism.
Johnson’s 2015 attempt to obtain an injunction against his own city followed his admission that he had destroyed several public records (in this case, text messages) responsive to requests pertaining to the city’s $500 million sports arena.
Even though this legal battle has pried loose a few hundred emails over the past year, it’s still only a small percentage of Mayor Johnson’s “official business” communications safely stashed away in his personal account.
-
Environment/Energy/Wildlife/Nature
-
A building boom is underway offshore in Europe. Up to 400 giant wind turbines are due to be built off the northeast coast of the UK in what will be the world’s largest offshore wind development.
Output from the Dogger Bank project will be 1.2 Gigawatts – enough to power more than a million homes.
Next year, a 150-turbine wind farm off the coast of the Netherlands is due to start operating, and other schemes along the Dutch coast are in the works.
-
The fallout from Brexit continues. The pound has hit record lows against the dollar.
[...]
“This is shocking news. Less than a day into the job and it appears that the new Prime Minister has already downgraded action to tackle climate change, one of the biggest threats we face,” Friends of the Earth U.K. CEO Craig Bennett said in a statement emailed to ThinkProgress.
But while changing the actual name of the office that works on climate change might seem extreme, the change in branding might not be indicative of where the government plans to go.
Simon Bullock, a spokesperson for Friends of the Earth, noted that Greg Clarke, the new head of the newly formed department, is “decent” on climate. “It’s reassuring that although [climate change] is not in the new department’s title, Clark at least sees climate as a part of his role,” Bullock said in an email.
-
Finance
-
Say what you like about the UK Independence party, but do not call them economic isolationists. Ukip is mustard-keen on free trade as long as the EU is not negotiating on Britain’s behalf. Buoyed by its European election victory and clutching sweat-stained copies of David Ricardo’s pro-trade economic treatise, Ukip is promising a new trade deal as soon as Britain’s exit liberates the UK from the dead hand of European protectionism.
-
The vote on 23 June for the UK to leave the EU is beginning to expose uncertainties in the withdrawal procedure laid down by Article 50 of the EU Treaty. Among the issues currently being debated is whether it would be possible to revoke a formal Article 50 notice to withdraw from the EU before the withdrawal process has been completed. In other words, would the die have been cast irretrievably for the UK to exit the European Union once Article 50 is triggered, or could the process be reversed before its conclusion if the UK wished to do so?
-
Sanum Investments Ltd and its parent company, Lao Holdings NV, say they filed on Friday the latest move in a legal battle concerning the Savan Vegas Hotel and Entertainment Complex – a casino hotel in Savannakhet, Laos.
The legal move opposes what is known as a ‘motion to dismiss’ filed earlier by San Marco Capital Partners LLC, a U.S.-based private investment firm that had been asked by the Laos government to handle the sale of Savan Vegas.
The opposition to the motion to dismiss was filed with the United States District Court in Delaware.
-
Westminster MPs of all parties are getting a 10 per cent, £7,000, boost to their pay packets after the Independent Parliamentary Standards Authority said they were not paid enough.
-
Greenpeace has acquired the Vote Leave battle bus and parked it in Westminster where it has been covered with thousands of messages for the new Government.
They overhauled the bus to replace the “lies” about EU funding with demands for the “truth” in a stunt outside Parliament on Monday morning.
The environmental activists are calling on members of the public to send in messages for the “rebranding” of the bus.
-
If the political discourse in the coming months and years changes to successfully countering populists with “popularizers” as leaders, preserving the European (western) order, and further reforming it, we could yet be thanking the UK for saving us by the alarm bell.
-
But compare what can be termed Gates’ ‘philanthro-capitalism’ with Ford Foundation President Darren Walker’s proposal for a more appropriate approach to giving in the 21st century: “We foundations need to reject inherited, assumed, paternalist instincts… We need to interrogate the fundamental root causes of inequality, even, and especially, when it means that we ourselves will be implicated.”
In contrast, Gates specialises in top-down technicist quick-fixes – ‘silver bullets’ – which often backfire on the economic shooting range of extreme corporate influence and neoliberal policies. As Global Justice Now’s Polly Jones complained in a report last month, Gates’ “influence is so pervasive that many actors in international development, which would otherwise critique the policy and practice of the foundation, are unable to speak out independently as a result of its funding and patronage.”
Amongst the few exceptions are Katharyne Mitchell and Matthew Sparke, whose research critiques Gates’ “highly targeted investments, market-mediated partnerships, rapid technological fixes, constant assessment, quick exits, and the use of competition, benchmarking and rankings to set funding priorities.”
[...]
But the most damage done within South Africa was Gates’ promotion of intellectual property (IP) rights. Long-term monopoly patents were granted not only to Gates for his Microsoft software, but for life-saving medicines.
IP became a fatal barrier to millions of HIV+ people who, thanks to Big Pharma’s profiteering, were denied AIDS medicines which cost R150 000/year fifteen years ago. The Gates Foundation was part of the problem by insisting on Merck-branded drugs in its Botswana AIDS clinics, complained Zackie Achmat of the Treatment Action Campaign (TAC) in 2001.
[...]
Self-interest was perhaps a factor, because Gates got rich from IP illegitimately acquired thanks to blatantly anti-competitive practices, such as bundling Windows with the slow, security flaw-ridden Internet Explorer web-browser, according to US prosecutors. The emails that Gates and his colleagues sent each other unveiled their cutthroat, illegal approach to IT (and Gates’ own slipperiness), notwithstanding the internet’s massive government subsidies.
And as Edward Snowden showed, Microsoft is in league with the United States National Security Agency’s Prism snoop service to hack your computer, Outlook, Hotmail and Skype accounts.
Speaking of secrecy, Microsoft’s offshore tax-avoidance policies today earn the company more money than Gates gives annually in donations (less than $4 billion/year).
[...]
These forces show, objectively, that the world urgently needs far less corporate power – including in the hands of Bill Gates and Microsoft – and many more bottom-up activist initiatives to achieve thorough-going wealth redistribution.
-
AstroTurf/Lobbying/Politics
-
Presidents play essentially no role in amending the Constitution. Any amendment Clinton proposed would have to be passed by a two-thirds majority in both the House and Senate, and then would have to be ratified by the legislatures of three-fourths of the states.
That’s never going to happen. The U.S. has amended the Constitution just once in the past 45 years, with the non-earthshaking 27th Amendment prohibiting Congress from voting itself a pay raise that takes effect before the next election. (Moreover, the 27th Amendment was submitted to the states in 1789; it then took 203 years for three-fourths of the states to ratify it in 1992.)
So Clinton’s constitutional amendment pledge is empty grandstanding. Citizens United will either be overturned by the Supreme Court, or it will remain law.
On the other hand, Clinton’s pledge to “fight” for small-donor matching funds is genuinely important. Over the past several years, almost all Democrats in the House and many in the Senate have signed on in support of the idea, and it would change the dynamics of money in politics in a way that even overturning Citizens United would not.
-
The rift between establishment conservatives and Tea Party insurgents was on full display. The billionaire dilettante and presumptive nominee was attempting to pivot from rabble-rouser to peacemaker. It wasn’t going to be easy.
-
Liberals and progressives love to point across the aisle and accuse their opponents of racism, misogyny and xenophobia, but that’s not what the Trump campaign is all about. And that’s not what Brexit was about. While it’s true that anti-immigrant sentiment is on the rise in Europe and the US, the hostility has less to do with race than it does jobs and wages. In other words, Brexit is a revolt against a free trade regime in which all the benefits have accrued to the uber-rich while everyone else has seen their incomes slide, their future’s dim and their standard of living plunge.
-
Donald Trump has denounced his opponents as being controlled by “special interests, the lobbyists, and the donors,” but a number of pro-Trump delegates helped crush an effort by two members of the Republican Party’s rules committee last week to ban for-profit lobbyists from the Republican National Committee.
Republican state Reps. Mary Anne Kinney of Maine and Cindy Pugh of Minnesota introduced an amendment at a rules committee session that would ban registered lobbyists for for-profit entities from serving as members of the RNC.
“This amendment is meant to keep those with a financial stake in being on the RNC [out]. … Nonprofit lobbyists are exempt,” Ted Cruz delegate Kinney explained, saying that lobbyists for pro-life groups, for instance, would not be barred.
-
Protests, discord, and heightened security announced the start of the Republican National Convention (RNC) on Monday as thousands marched on downtown Cleveland calling on the GOP to reverse its racist policies and “Dump Trump.”
The peaceful March on the RNC ended with a rally outside the heavily-fortified perimeter that encircled the Quicken Loans Arena during which participants denounced the “racist, anti-immigrant, and anti-Muslim” policies of the GOP and its presumptive nominee Donald Trump.
-
When Donald Trump’s Republican Party convenes in Cleveland, three shadows will haunt the arena. They won’t talk about these shadows on television, but if you look closely you’re sure to see them.
The first shadow is that of the extremist Republican right. Since the infamous Lewis Powell memo of 1970 it has invested billions in think tanks, academia, and politics to promote its agenda of individual greed over the common good.
-
The seemingly fed up—but inevitably comical—“Late Show” host “took [his] gloves off” in his take on the Democratic presidential candidate’s email scandal, rapping, “You’re so bad at running for president, the only person you could beat is Donald Trump.”
-
Last June, as dusk fell outside Tony Schwartz’s sprawling house, on a leafy back road in Riverdale, New York, he pulled out his laptop and caught up with the day’s big news: Donald J. Trump had declared his candidacy for President. As Schwartz watched a video of the speech, he began to feel personally implicated.
Trump, facing a crowd that had gathered in the lobby of Trump Tower, on Fifth Avenue, laid out his qualifications, saying, “We need a leader that wrote ‘The Art of the Deal.’ ” If that was so, Schwartz thought, then he, not Trump, should be running. Schwartz dashed off a tweet: “Many thanks Donald Trump for suggesting I run for President, based on the fact that I wrote ‘The Art of the Deal.’ ”
Schwartz had ghostwritten Trump’s 1987 breakthrough memoir, earning a joint byline on the cover, half of the book’s five-hundred-thousand-dollar advance, and half of the royalties. The book was a phenomenal success, spending forty-eight weeks on the Times best-seller list, thirteen of them at No. 1. More than a million copies have been bought, generating several million dollars in royalties. The book expanded Trump’s renown far beyond New York City, making him an emblem of the successful tycoon. Edward Kosner, the former editor and publisher of New York, where Schwartz worked as a writer at the time, says, “Tony created Trump. He’s Dr. Frankenstein.”
-
Censorship/Free Speech
-
South Africa’s bishops have lent their support to demonstrators who have protested censorship at the state-run South African Broadcasting Corporation (SABC), including the suspension of employees who sought to cover riots.
“An impression has been created that the SABC is failing to report fully and objectively on events that have the capacity to diminish the holding of free and fair elections,” said Bishop Abel Gabuza, chairman of the justice and peace commission of the Southern African Catholic Bishops’ Conference. “Certainly, this is a serious matter that requires urgent intervention by the National Assembly.”
-
A department head at Shenkar College of Engineering, Design and Art has resigned to protest the college’s censorship of a drawing…
-
Once upon a time, all of America was a First Amendment Zone. That’s now as dead as Alexander Hamilton.
The city of Cleveland revealed part of its security plan for the Nuremberg rally Republican National Convention. Securing the convention will require a heavily policed, fenced off 3.3 square-mile First Amendment Zone. A fun fact is that the First Amendment Zone is about the same size as Baghdad’s Green Zone.
-
On Sunday, the day before the Republican National Convention (RNC) began, 100 naked women held up mirrors to the RNC-hosting Quicken Loans Arena in downtown Cleveland as a political statement against the anti-women rhetoric of the Republican party.
The staged protest artwork by the artist Spencer Tunick, titled “Everything She Says Means Everything,” was meant to “express the belief that we will rely upon the strength, intuition and wisdom of progressive and enlightened women to find our place in nature and to regain the balance within it,” Tunick wrote. “The mirrors communicate that we are a reflection of ourselves, each other, and of, the world that surrounds us. The woman becomes the future and the future becomes the woman.”
-
The two recent police shooters were ex-military. Two minds cocked and loaded by the country they turned on. The police who recently killed black citizens, also cocked, loaded and afraid. Human beings on hair triggers and for a year we have had a steady bark from a sociopath shrieking simplistic violent solutions to all issues. The two police shooters had the military training but the uniforms they targeted changed. Not sure what kind of training the policemen in Baton Rouge and St. Paul had. But an atmosphere gave the release. If you can say, which is said ad nauseum, our hearts and prayers are with the families – there was also a heartlessness and a counter prayer that preceded the killing.
-
New York University student Ella Reider had to go to China to find the freedom to debate things she’d never be allowed to say or hear in Manhattan.
That’s her surprising takeaway from the past year studying at NYU Shanghai, whose openness to controversial ideas stands in stark contrast to the American campus, which is increasingly “hostile to political views that differ from the predominant views on campus.”
-
Privacy/Surveillance
-
-
The United States is working with foreign governments to draft agreements that would allow the latter to serve warrants for email searches and wiretaps on US technology companies doing business in these countries.
According to the Wall Street Journal (paywall), the plans were discussed at a public forum in Washington DC by Brad Wiegmann, a senior Justice Department official, who said the first agreement was being worked out with the UK.
The news comes a few days after Microsoft won a landmark case to prevent the US government from using a domestic warrant to gain access to the email data of one of its clients which was stored in Ireland. The US had claimed the data was relevant to a drug-trafficking operation.
-
Germany plans new legislation to require manufacturers of cars equipped with an autopilot function to install a black box to help determine responsibility in the event of an accident, transport ministry sources told Reuters on Monday.
The fatal crash of a Tesla Motors Inc Model S car in its Autopilot mode has increased the pressure on industry executives and regulators to ensure that automated driving technology can be deployed safely.
Under the proposal from Transport Minister Alexander Dobrindt, drivers will not have to pay attention to traffic or concentrate on steering, but must remain seated at the wheel so they can intervene in the event of an emergency.
-
Facebook has outdone even Google recently, in its efforts to shake up the mobile industry and accelerate the delivery of broadband services (and its revenue generators) to the entire planet. This is no longer just about using balloons and new spectrum to push affordable wireless access to underserved communities. It is about blowing apart the traditional mobile network supply chain, and the way those networks are deployed.
First came TIP (Telecoms Infrastructure Project), a telecoms network version of its Open Compute Project to drive commoditized, massively scalable platforms. Then came its own R&D projects geared to affordable, easily deployable, but powerful open RANs, Terragraph and Aries.
And now it has announced OpenCellular, which brings the two ideas together in many ways, providing an open source platform for low cost, dense networks.
-
UK prime minister Theresa May’s Data Retention and Investigatory Powers Act (DRIPA) isn’t necessarily incompatible with European fundamental rights, a senior advisor at Europe’s top court said on Tuesday.
European Court of Justice (ECJ) advocate general Saugmandsgaard Øe has published his non-binding legal opinion on DRIPA arguing that “a general obligation to retain data imposed by a member state on providers of electronic communication services may be compatible with EU law.”
The case was brought by a cross-party alliance of British MPs—the now Brexit secretary of state David Davis and deputy Labour leader Tom Watson.
-
A core contributor to the Tor network has announced that he would be shutting down all the relays and Tor-related services under his control and leaving the project. Known as Lucky Green, he has indicated some recent development as the cause and finds them behind the bounds of ethics for initiating such action.
-
The overnight success of Pokemon GO has been on the center stage for another interesting reason — this time for acting as a potential medium for disclosure of military zones in China. The flow of posts regarding the same has begun to appear on the microblogging site Weibo
-
Thanks, but no thanks. McCain and others attending the hearing pretend the encryption problem can be solved by “working together.” But Manhattan DA Cyrus Vance used part of his testimony to basically accuse Apple of offering encryption-by-default just to spite the government. The others testifying didn’t go quite as far as Vance did in portraying the company as the enemy of justice, but there was really nothing in it for Apple. There’s no “working together” going on here, not if the committee offers three invitations to people opposed to encryption (or at least far more sympathetic to law enforcement’s requests) but the only outsider asked to attend is one that spent the running time of the last hearing listening to ignorant statements and wild allegations.
-
The United States Senate Committee on Armed Services held a hearing about the coming darkness cellphone encryption Friday morning. There was almost no attempt made to address both sides of the issue, most likely because Senator John McCain — who headed up the “discussion” — has already made up his mind on how this problem should be handled.
Testimony — all from government officials — was presented, with Manhattan DA Cyrus Vance leading off. Vance’s tune hasn’t changed. Encryption is still (apparently) an insurmountable problem and the only “answer” runs directly through Congress. Vance spent most of his speaking time [PDF] criticizing Apple and suggesting its decision to provide encryption by default on its phones was done purely to spite him and the government.
-
Given the cultural phenomenon that is Pokemon Go, it was only a matter of time before security-conscious government agencies would be forced to confront the inevitable: that their employees would be joining in the quasi-AR madness.
Kristan J. Wheaton of the Sources and Methods blog was handed an apparently official document from the Defense Department that lays down several common sense rules for employees throwing imaginary balls at imaginary creatures. (A screenshot of the original document can be seen in Thomas Rid’s tweet, embedded at the bottom of this post.
-
Thomas Drake was a 48-year-old decorated Air Force and Navy veteran, and a senior executive at the National Security Agency, the NSA, when he decided he had to speak up against what he considered the spy agency’s abuses.
That’s when he anonymously contacted a reporter at The Baltimore Sun, helping her expose wrongdoing at the agency in a series of articles. Two years later, the FBI raided his home, and the US government launched an investigation into Drake for leaking classified information and espionage.
All of a sudden, Drake faced the possibility of spending most, if not all, of the rest of his life in jail. Looking back now, after he escaped jail and only pleaded guilty to a misdemeanor, Drake says it was all worth it.
-
-
-
-
Civil Rights/Policing
-
The TSA is a multibillion dollar agency with nearly zero redeemable qualities. It can only act in hindsight, does almost nothing to make traveling safer, and seemingly devotes most of its screening efforts to toddlers, cancer patients, and ensuring carry-on liquids do not exceed three ounces.
What it lacks in competency, it makes up in misconduct. Lines at security checkpoints have slowed to a crawl. Making it through the tedious, invasive process sometimes means inadvertently “donating” expensive electronics to sticky-fingered agents. The TSA’s morale is generally on par with Congress’ approval rates. And, when it’s all said and done, the people hired to protect travelers just plain suck at their job.
[...]
As Katherine LaGrave of the Conde Nast Traveler points out, the problem is only getting worse. Complaints are up 28% over the last three years, with larger airports averaging a complaint a week. Long lines may be causing a spike in the complaints, but the misconduct detailed in the report has very little to do directly with this issue.
Attendance issues are part of the problem, but the offenses listed in the report range from missing work to smuggling drugs/humans to “engaging in child pornography activities.” Although processes are in place to handle disciplinary issues, they are both bureaucratic and inconsistently applied. Worse, the investigation found that the agency has no specific process in place to fire problem employees.
-
Despite the Transportation Security Administration’s ten-point action plan to reduce long lines at airports across the country, lengthy queues remain. Now, the TSA’s summer may be getting even worse: According to a recent report from the House Homeland Security Commission entitled “Misconduct at TSA Threatens the Security of the Flying Public”, nearly half of the TSA’s 60,000 employees have been cited for misconduct in recent years.
The bad news doesn’t stop there. Citations have increased 28.5 percent from 2013 to 2015, and in 2015, the average U.S. airport received 58 complaints each year—more than one a week. (Unsurprisingly, some of the nation’s largest and busiest airports—Los Angeles International Airport, Newark International Airport, and Boston Logan International Airport—saw the highest rates of misconduct.) The complaints can come from frustrated passengers, sure, but also from fellow TSA employees and other government workers.
-
Ex-editor and columnist for the Sun Kelvin MacKenzie caused furore on Monday with a piece asking “Why did Channel 4 have a presenter in a hijab fronting coverage of Muslim terror in Nice?”
-
-
As I watch the news on television and see another atrocity unfold in front of my eyes, innocent people crushed to death as they were celebrating Bastille Day, by the weapon of mass destruction that is a white van, the absurdity of the situation becomes hard to miss. 84 – 84 dead, many amongst them children. 84 innocent people crushed to death by a mad man behind wheels, hurling his vehicle at them with the intent to do maximum harm. And so he did, until his turn came to die an early death under the blaze of gun bullets aimed to kill. Every last second of an insignificant life laid to bare on the world stage, analyzed, repeated, studied and vilified. 84 dead. In the coming days, the lives, loves and stories of these people cut down in their prime will fill magazines. Images, anecdotes and testimonies will make them come alive again for a few moments only to heighten that feeling of loss when it is brought home again that because of a mad man behind a wheel, Stephanie will not get her dream wedding and Jeff will not play for the home team, and our eyes will well up in tears.
Meanwhile the world we knew and functioned in comfortably will have changed again to an even more aggressive and unwelcoming place to all who do not come from the West. You are blamed and asked to carry the shame of the act of a lone madman, but was he alone? Or was he following the orders of a higher entity that is fighting to destroy the freedoms the West benefits from. ISIS or IS or Al-Qaeda, these boogie men in the dark who hate western values, western freedoms and consider the rest infidels, sending their radicalized disillusioned soldiers to do Allah’s work in our midst.
-
Raines was one of some 50 current and former guards who spoke to Hager and Santo for “Inside the Deadly World of Private Prisoner Transport,” a devastating examination of the for-profit van companies used by prisons to transport inmates. The reporters found that a dozen prisoners died in such vans in the last 16 years; a dozen more suffered serious injuries; at least 60 managed to escape, and many alleged sexual and physical abuse at the hands of drivers and guards. This week the reporters join the ProPublica podcast to tell us how their effort grew from a tip on one prisoner who was beaten to death to a full and rare examination of a dangerous, virtually unregulated industry.
-
It is too early to know if the shooting of police in Dallas and Baton Rouge are the beginnings of acts of retribution against police for their wanton murders of citizens. The saying is that “what goes around, comes around.” If police murders of citizens have provoked retribution, police and those who train them need to be honest and recognize that they have brought it upon themselves.
Killings by police have gone on too long. The killings are too gratuitous, and the police have largely escaped accountability for actions that, if committed by private citizens, would result in life imprisonment or the death penalty.
There has been no accountability, because the police unions and the white community rush to the defense of the police. In rare instances when prosecutors bring charges, as in the case of Freddie Gray, the police are not convicted.
Presstitutes treat killings by police as acts of racism, and that is the way the public sees them. This infuriates black communities even more as the indifference of whites to the murders is regarded as racist acceptance of the murder of black people.
-
Before his career as an elected official, Gov. Mike Pence (R-IN) hosted both a radio and television show in the 1990s, with the name, “The Mike Pence Show.” While his commentaries from that time in defense of cigarettes and in opposition to the feminist message in Disney’s Mulan have made news, one less noticed piece suggested that adultery should be a crime in the United States. It appeared on the website for his television show on WNDY, retrieved through the Internet Archive WayBack Machine.
In May of 1997, Pence railed against the news that U.S. Air Force Lt. Kelly Flynn had received a general dischrage despite having been accused of two adulterous affairs. While Pence said he was glad she had received compassion, he took aim at society for making extramarital affairs acceptable. “Did anyone else notice the incredulous looks on the faces of Lt. Flynn’s most ardent defenders anytime the term ‘adultery’ was mentioned? Many of her defenders were less concerned, it seemed, about the facts of the case than about the fact that somewhere in this society adultery is still a crime.”
-
Over 1,100 people died when Rana Plaza garment factory building collapsed near Dhaka
-
There was a true kumbaya moment after the Dallas cop massacre similar to the moment after 9/11 when sympathy was expressed for America from many unexpected quarters around the world. That window began to close when US leaders took a hard line and vengefully attacked an un-implicated nation to counter the very sense of vulnerability that moved people of the world to sympathize with us. Similarly, the sympathy for attacked cops in Dallas may be evaporating thanks to a familiar sociological dynamic involving in-group, out-group identification.
-
America may call itself democracy’s gold standard, but it fails to guarantee the right to vote and permits the dominance of political money, a shameful anomaly that requires a constitutional amendment, writes William John Cox.
-
The shooter, who was killed at the scene, has been identified as 29-year-old Gavin Eugene Long of Kansas City, Missouri. He was honorably discharged from the Marines in 2010 holding the rank of sergeant. During his five-year stint in the service, which included a June 2008 to January 2009 deployment in Iraq, he received several medals, according to media reports citing military records.
-
The Brock Turner case has reminded us of the bitter truth of the adage that in America it is better to be guilty and rich than to be innocent and poor. In early June, Judge Aaron Persky sentenced Turner, a Stanford student who was convicted on three counts of sexual assault, to six-months in jail and three years of probation. The sentence, shorter than the six years requested by prosecutors, spurred an eruption of public outrage. Anger has poured out at Turner’s mother and father for excusing his actions and in particular at Judge Persky. The Turner case exemplifies a problematic pattern in American policymaking. The case, similar to other sensationalized instances of leniency for sexual assault, has animated calls for harsher punishments, mandatory minimums and removing judicial discretion. All of these law-and-order responses, coming particularly from the left, continue a tradition in the United States of channeling efforts to address sexual violence into demands for punishment. Far from being progressive, however, this strategy contributes to the expansion of the carceral state, which is ineffective at reducing crime, incapable of healing victims, and devastating for those caught in its web. A more substantively progressive and feminist strategy for addressing these issues is needed in order to draw the connection between sexual violence and material inequality.
-
Newt Gingrich suggested late last week on cable tv that Muslim Americans should be asked if they believe in “sharia” and if they answer yes, they should be deported. You can’t deport US citizens, so the whole remark was ridiculous.
Sharia for Muslims is the equivalent of Canon Law for Catholics, Halakhah for Jews, and I guess the entire Bible for some fundamentalists (though there are laws in Deuteronomy that it is hard to imagine anyone actually practicing). All religions have laws. Sharia is the Muslim one. But it is fluid and an arena of contention within Islam. It forbids murder, theft, adultery, and drinking. You’d think people would be happy about all that. In any case, observant Muslims would all say they believe in sharia, just as observant Jews would say that the believe in Halakhah or observant Catholics would say they believe in canon law.
-
Republican presidential candidate Donald Trump built his political career on a campaign promise to build a border wall along the U.S. border with Mexico if elected president. But a new poll has found that a large majority of residents living in major cities along the southern U.S. border with Mexico aren’t excited about that prospect.
About 72 percent of people living on the U.S. side of the border and 86 percent of people living on the Mexican side are opposed to building a wall, a poll funded by Cronkite News, Univision News, and Dallas Morning News found. Building out a border wall also isn’t on the top of their priority list — 77 percent of Mexicans and 70 percent of Americans found that the economy, crime, and education were more important than border issues. Another 69 percent of Mexicans and 79 percent of Americans said that they depend on the other country for economic survival.
-
Baltimore Police Lt. Brian Rice, the highest ranking officer charged in the death of Freddie Gray, was on Monday acquitted on all counts.
It marks the fourth time prosecutors have failed to secure a conviction in the case, the Baltimore Sun notes, and in turn “is likely to renew calls for Baltimore State’s Attorney Marilyn J. Mosby to drop the remaining charges[...] including from the union that represents the city’s rank-and-file officers.”
Rice was found not guilty of involuntary manslaughter, reckless endangerment, and misconduct in office by Circuit Judge Barry Williams in a bench trial. Williams previously handed down acquittals for officers Caesar Goodson and Edward Nero. The trial for Officer William G. Porter ended with a hung jury in December. A retrial is set for September 6.
-
The Federal Communications Commission is trying once again to limit the prices prisoners and their families pay for phone calls, proposing a new, higher set of caps in response to the commission’s latest court loss.
A March 2016 federal appeals court ruling stayed new rate caps of 11¢ to 22¢ per minute on both interstate and intrastate calls from prisons. The stay remains in place while appeals from prison phone companies are considered, but FCC Chairman Tom Wheeler and Commissioner Mignon Clyburn last week proposed new caps of 13¢ to 31¢ per minute in an apparent attempt to satisfy prison phone companies and the courts.
-
So far, the RNC has been low on organization and high on police presence.
In fact, organizers did not even release a detailed schedule of speakers until Monday afternoon, when the convention began.
The official guide for the RNC — which does not include a schedule — did, however, open with a photo of a smiling Donald Trump embraced by his wife, Melania.
[...]
Police are preparing for massive protests. Sunday did not have a lot of protest activity. The official convention began on Monday. Large demonstrations are planned to be held throughout the week.
Cleveland spent $50 million in federal grant money on police for the RNC. The city spent $20 million on riot gear and equipment — including at least 2,000 full-body riot suits, 24 sets of ballistics body armor and 300 patrol bikes. It also spent another $30 million on “personnel-related expenditures.”
The American Civil Liberties Union, or ACLU, sued Cleveland in June for “placing unacceptable restrictions on free speech and other rights of people living and visiting downtown Cleveland for the RNC.”
-
Internet Policy/Net Neutrality
-
In its report the Culture, Media and Sport Committee says BT is “significantly under investing” in Openreach, its infrastructure subsidiary. Based on a report commissioned from a panel of independent experts, the Committee concluded the shortfall in investment could potentially be hundreds of millions of pounds a year.
-
Intellectual Monopolies
-
The United Nations Conference on Trade and Development (UNCTAD) 14th Session opened here yesterday, with leaders calling for deeper and broader cooperation between trade and development.
-
Trademarks
-
How Assef came across this single post, floating in the internet backwater, is a mystery. But there it is. Before suing the Doe behind the single-post “blog,” Lincoln Crowne tried suing Google for defamation in Australia, presumably to use local laws to route around Section 230 protections. It didn’t work. Google briefly took down the blog post before restoring it.
Having failed in this attempt, Lincoln Crowne is now trying to sue the anonymous blogger, using a poorly-constructed lawsuit with more than a few deficiencies. It not only claims the content is defamatory, but that the defendant’s URL is a violation of its trademark. It’s a mess, which is somewhat surprising because the firm is being represented by lawyers who seem otherwise competent.
-
There is somebody on the other side of the Pacific Ocean who has a strongly negative perspective on Nicholas Assef, the head honcho at an Australian financial services firm called Lincoln Crowne – or at least, somebody held such views nine years ago. We know at least that much because, in 2007, an anonymous individual created a small Google blog, using the URL lincolncrowne.blogspot.com, and posted a “warning” urging people who were considering doing business with Assef and his company to do their due diligence first. And even though the blog is buried deep in the Google search results for someone entering a search using lincoln crowne as the search string (currently, it is on the tenth page of results), Assef is plainly rankled by this criticism. We know that first of all because seven years later, after Google refused to take down the blog, Lincoln Crowne sued Google for defamation in Australia (which lacks the US protection for online hosts that section 230 affords). Google initially responded to the lawsuit by taking down the blog, but later restored the blog to its DOT.COM domain. It is not clear to me whether Lincoln Crowne ever pursued the suit against Google to judgment. The company’s papers do not make reference to any judgment, so I assume there was none.
-
Copyrights
-
A couple of months ago, we wrote about how publishing giant Elsevier had purchased the open access pre-publisher SSRN. SSRN is basically the place where lots of research that we regularly report on is published. Legal and economics academics quite frequently post their journal articles there. Of course, Elsevier has a well-known reputation for being extreme copyright maximalists in dangerous ways. Having Elsevier take over SSRN concerned a lot of academics, and even led to calls for alternatives, including many asking the famed arXiv to open a social science research operation as well.
Indeed, it appears that arXiv was paying attention, because just about a week ago, SocArXiv was announced, and it already has a temporary home hosted by Open Science Framework.
-
German extortion outfit Guardaley, together with its US collaborators — Voltage Pictures and a network of ethically handicapped attorneys — has been filing frivolous, evidence-free lawsuits across the US for years, extracting millions from alleged pirates and innocents alike. To maintain the fog of legitimacy and to shield Voltage from bad publicity, dozens of shell corporations were created — one per film — to serve as (sometimes bogus) plaintiffs in thousands of copyright infringement lawsuits filed either against individual defendants or about a dozen of John Does lumped together.
-
It’s typical for these types of complaints to be layered in nuance and interpretation, with a dash of one side or the other misunderstanding how licensing, copyright, and the rights that surround public performances work. This does not appear to be one of those cases, as the agreement Madison McQueen agreed to is fairly straightforward and specifically forbids the exact use for which the music was incorporated. As Goldman notes, whereas most campaigns would simply apologize and pay to have all of this go away, the Cruz campaign instead offered up a motion to dismiss. That motion didn’t rebut any of the allegations. Instead, Cruz’s lawyers argued that the musicians had only applied for copyright registrations and had yet to have that process completed, that it’s unclear how many times it should be said that the campaign infringed on the copyrights for the songs, that Audiosocket can’t stack its copyright complaint alongside its breach of contract complaint, and that all of this is a moot point because — not making this up — Cruz lost and gave up on his candidacy.
-
The Tribunale di Roma (Rome Court of First Instance) is back with yet another decision on the liability of online intermediaries (ISPs) for third-party copyright infringements.
-
Reading coverage of the new Great Animal Orchestra exhibition got this Kat thinking about the relationship between animals, artwork, performance and IP. The “biophony” exhibition is made up of natural soundscapes – estimated to come from over 5,000 hours of sound recordings made by Bernie Krause, and edited together with visual rendering by United Visual Artists. The product is an immersive collage of squeaks, calls, howls, waves and so on, which have also somehow previously been adapted to a symphony (by composer Richard Blackford), and a ballet. The exhibition is named after Krause’s book of the same title.
The various intellectual property involved in the Great Animal Orchestra and its adaptations has not been the subject of any great, wild, public dispute – falling quite understandably behind other priorities such as drawing attention to the fact that over the 50 years of Krause’s recording, around half of the habitats have been silenced by humans. But, recently, of course, the issue of animal copyrights has been in the legal spotlight…
Permalink
 Send this to a friend
Send this to a friend
07.18.16
Posted in IBM, OIN, Patents at 9:27 pm by Dr. Roy Schestowitz
Hostile environment in which trolls thrive owing to software patents and cashless startups that must settle
 Summary: With unconvincing excuses such as OIN, large corporations including IBM continue to promote software patents in the United States, even when public officials and USPTO officials (like Bahr on the left) work towards ending those
Summary: With unconvincing excuses such as OIN, large corporations including IBM continue to promote software patents in the United States, even when public officials and USPTO officials (like Bahr on the left) work towards ending those
SOFTWARE patents remain a very major barrier not just to FOSS developers but to all software development. Such patents, unsurprisingly, are being promoted by monopolists and their facilitators, to whom they’re a major source of revenue. Those monopolists continually rig the whole system in their favour as they can definitely afford it; in fact, it might be considered part of the obligation to shareholders (protectionism through legislation).
The mainstream media or corporate media no longer talks about software patents. Instead it speaks about “patent trolls” and by patent trolls it means the small ones, not the media owners. Apple, for instance, is directly connected to some major media conglomerates, so bias in patent coverage is to be expected in some cases (we wrote about this in past years). Let’s be easily deluded and just ignore Apple demanding billions (not millions) from Android OEMs (patent aggression and sometimes trolling includes big vendors) and also forget Apple’s unique role in Intellectual Ventures (explained here several years ago), the world’s largest patent troll which goes after Android vendors. The article “Apple will pay $25M to patent troll to avoid East Texas trial” is eye-catching and so is “Newegg’s Three-Step Solution to Fighting Patent Trolls” by Gary Shapiro, President and CEO of Consumer Technology Association (CTA). This group likes to focus on patent trolls rather than patent scope. Here is some of the latest from Gary Shapiro:
Lee Cheng is a troll trapper. As chief legal officer for Newegg.com, the second-largest online only retailer in the United States, Cheng has successfully battled the almost three dozen trolls that have attacked his company in the last ten years. And not just fight them, but win.
Patent trolls — sometimes called “non-practicing entities,” or NPEs — don’t actually create any products or services. Instead, they scoop up patents for the express purpose of using them to extort money from real companies large and small that can’t or don’t want to pay high legal defense costs. NPEs focus on settlements and generally have no desire to test their generally poor-quality patents in trial and through appeal. Even bad patents can generate millions in settlement dollars.
A newly-updated Harvard Business School study finds patent trolls sue cash-rich firms “seemingly irrespective of actual patent-infringement” — because that’s where the money is. The Harvard researchers noted trolls are taking a toll on innovation at the firms they target: “After settling with NPEs (or losing to them in court), companies on average reduce their research-and-development (R&D) investment by more than 25 percent.” So instead of funding development of the Next Big Thing in consumer technology, these American small businesses are handing over legalized extortion payments to trolls.
Research estimates that patent trolls drain a prodigious $1.5 billion a week from the economy. I sat down with Lee Cheng to get a from-the-trenches account of the patent troll problem, and to let him share his lessons for taking down the trolls.
“They also rely a great deal on software patenting, as a look at their patent portfolio easily and instantly reveals.”What Gary Shapiro misses here is that patent trolls are often part of a broader shell game played by large corporations such as Microsoft. They also rely a great deal on software patenting, as a look at their patent portfolio easily and instantly reveals. All the focus is now being shifted towards trolls, both in the media and US Congress. Just see this new tweet (“VIDEO: Sen. Jeff Flake Targets Patent Trolls”).
Proskauer Rose LLP, which likes to cherry-pick cases in promotion of software patents, recently released this so-called ‘analysis’. They try to maintain a grip on software patents no matter what. Some large corporations are doing the same thing and it’s not limited to Microsoft. Consider IBM.
IBM’s commitment to Free software, especially now that it pays lobbyists like David Kappos for software patentability, should be seriously doubted. It just likes “Linux”. Manny Schecter, a patent chief at IBM, is an ardent proponent of software patents and he has just linked to “Latest very brief USPTO update to patent examiners on subject matter eligibility in view of recent cases…”
This is a PDF of a new Robert Bahr (Deputy Commissioner for Patent Examination Policy) letter regarding the Rapid Litigation case and Sequenom case (both covered here earlier this month). Herein he is alluding to Mayo and Alice as he might try to gently challenge these or begrudgingly adopt what the ‘pesky’ Supreme Court said. Here is a quote from the PDF: “In summary, the USPTO’s current subject matter eligibility guidance and training examples are consistent with the Federal Circuit’s panel decisions in Rapid Litigation Management and Sequenom. Life sciences method claims should continue to be treated in accordance with the USPTO’s subject matter eligibility guidance (most recently updated in May of 2016). Questions should be referred to Technology Center subject matter experts or your SPE.”
Where does IBM stand on the subject? It’s hardly even a mystery. IBM does not like Alice because IBM loves software patents and actively works to expand these to more countries/continents. At the same time IBM brags about OIN as though it magically makes IBM’s patent policies absolutely fine and compatible with FOSS. “I don’t think there is an alternative choice when you are small entity,” told me someone today. “When has OIN actually helped a small company? Even as a deterrent,” I replied. “When your entity is relatively small,” he said, “OIN represents a potential shield to provide you even a minimum of security.”
“Life sciences method claims should continue to be treated in accordance with the USPTO’s subject matter eligibility guidance (most recently updated in May of 2016).”
–Robert BahrBut how in practice can OIN protect one against a troll for example? It cannot. OIN is totally useless against patent trolls. Don’t ever forget that. I saw that firsthand when I was part of E-mail thread I had initiated. Small companies sometimes try taking rivals to court with their patents. If the rival is big enough, then countersuit is massive (IBM has a massive portfolio which virtually every software patents infringes on), defeating the very point of bothering with a lawsuit in the first place. Large companies may use trolls as satellites/proxies, so the lawsuits/countersuits can come from all sorts of mysterious directions.
“Intel and McAfee Sued for Patent Infringement,” writes Patent Buddy this week. Security Profiling LLC (LLCs are usually patent trolls) is suing in the Eastern District of Texas. What can Intel do about it? Nothing. Intel is now trying to sell/offload McAfee, based on last week’s news reports (see our daily links for half a dozen such reports). Has it become too much of a burden perhaps? The point about patent trolls and OIN sticks, no matter what. Steven J. Vaughan-Nichols has just fallen for the OIN public relations machine, joining the chorus which began with an 'exclusive' puff piece. OIN is not a “Linux” thing as some want it to be widely viewed; it’s mostly an IBM, Sony etc. thing. It helps legitimise software patents rather than acknowledge that they are not compatible with FOSS or Linux and thus need to be ended. █
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day
- Software Patents Continue to Collapse, But IBM, Watchtroll and David Kappos Continue to Deny and Antagonise It
The latest facts and figures about software patents, compared to the spinmeisters' creed which they profit from (because they are in the litigation business)




 Summary: With unconvincing excuses such as OIN, large corporations including IBM continue to promote software patents in the United States, even when public officials and USPTO officials (like Bahr on the left) work towards ending those
Summary: With unconvincing excuses such as OIN, large corporations including IBM continue to promote software patents in the United States, even when public officials and USPTO officials (like Bahr on the left) work towards ending those















 Content is available under CC-BY-SA
Content is available under CC-BY-SA