05.14.15
Posted in Microsoft, Security at 7:48 pm by Dr. Roy Schestowitz
VENOM™ and Heartbleed™ do have something in common

From Microsoft management to CrowdStrike™ management
Summary: Why CrowdStrike™ is motivated to smear Free software and establish a stigma of insecurity in Free software-based virtual machines/’clouds’
The word/brand “Heartbleed” was made up by a Microsoft-connected firm — a firm that is headed by Microsoft’s former security chief. It basically took credit for a 2-year-old flaw that a Google engineer had found, publishing (along with a logo and a catchy brand name) dangerous details well before a patch could be made available and widely deployed/applied, i.e. it was an irresponsible disclosure.
CrowdStrike™ 'pulled a "Heartbleed"' in the sense that it followed some similar patterns (reminiscent of the above). XFaCE, a regular from our IRC channels, diverted our attention to the press release “CrowdStrike™ Appoints Amol Kulkarni as Vice President Engineering”, dated Dec 9, 2014 (less than half a year ago).
“Former Microsoft Bing Engineering Leader [leaving a dead/dying effort] joins Executive Team at CrowdStrike,” says the press release.
“Why is it that we so often find out-of-proportion scare (or FUD) against Free software linked to Microsoft and its ‘former’ staff or close partners?”More important a find, however, is the background of Mike Convertino from the company’s leadership team. The introduction is very telling; rather than hide his background it is noting: “Prior to his work at CrowdStrike, Convertino was the Senior Director of Network Security at Microsoft where he was responsible for protecting all of the company’s networks from intrusion and exploitation.”
So the apple doesn’t fall too far from the tree.
“They also use Microsoft Office extensively, given their job ads,” XFaCE added.
“Adam Meyers, “VP of Intelligence” at CrowdStrike™, used to work for SRA International,” XFaCE says. According to Wikipedia, “SRA provides information technology services to clients in national security, civil government, and health care and public health. Its largest market, national security, includes the Department of Defense, Homeland Security, US Army, US Air Force, and intelligence agencies.”
“Microsoft is a partner,” says XFaCE. George Kurtz, the CEO and co-founder of CrowdStrike, comes from McAfee, a common and frequent source of anti-Linux and anti-Android FUD. The famed Scottish-American founder of McAfee is now a fugitive.
Why is it that we so often find out-of-proportion scare (or FUD) against Free software linked to Microsoft and its ‘former’ staff or close partners? █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, Microsoft at 11:22 am by Dr. Roy Schestowitz
Summary: The ‘cloud’ mindset, which is promoted by surveillance fanatics, increasingly used to pretend that Microsoft has a bright future, despite declining sales
When Microsoft can no longer sell Windows and Office (its cash cows) all it will have left to sell is people’s private data, even Skype audio/chats/video. That’s what the vision of ‘cloud’ seems to be about: subscription (infinitely-recurring payments) and data (with no true promise of privacy).
Yesterday we noted that some IDG journalists are actually Microsoft staff and some are Microsoft MVPs, like this so-called ‘journalist’ who keeps promoting (advertising) Microsoft ‘cloud’ (Matt Weinberger does the same thing in other sites). One ‘analyst’ (like Gartner or IDC, but financial) went as far as hyping up Azure to upgrade Microsoft, using the ludicrous claim (among others) that “Microsoft embraces linux”, despite Microsoft obviously hating Linux. Recall the series below:
Anyone choosing to run GNU/Linux on the NSA-friendly platform called Azure is asking or begging to be snooped on. What would customers say? Microsoft’s love of surveillance is well documented. The whole ‘cloud’ nonsense works well for Microsoft and those claiming that Microsoft will do well “because cloud” are either ignorant or bribed.
Yesterday we found Vista 10 ads (in article form) in the Microsoft-friendly media because they must pretend that Microsoft matters in mobile and that Windows is free or something along those lines. Microsoft’s mouthpiece can’t help spreading the lie that Vista 10 will be 'free' (Microsoft admits it’s “marketing”, i.e. lie). Gartner has been among those promoting the 'free' Vista 10 lie.
Microsoft is simply unable to compete with free (freedom and gratis), so now it pretends that it can devour all of GNU/Linux (in Azure) or that somehow reducing the cost of Windows and moving to a subscription model will magically work out. This is utter nonsense. Only a drunk analyst, an incompetent analyst, or a bribed analyst can claim such a thing. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft, Security at 11:15 am by Dr. Roy Schestowitz
Summary: New example of media bias which completely omits Windows and spares Microsoft as that may lead to bad publicity
The VENOM® hype campaign is still occupying headlines, serving to distract from Microsoft’s ~50 vulnerabilities which were disclosed on Tuesday and hardly received any media attention.
We recently complained that the ToryGraph advertised Microsoft and deleted Netscape from history, thereby hiding Microsoft's criminal shame.
A reader has just told us that the ToryGraph fails to call out Windows when there is negative news. There is Windows ransomware again, but Windows not even named. There is no brand, no name, no logo, etc.
Microsoft Windows does not need to be infected to demand ransom, Microsoft does the job itself and has done exactly that (demanded ransom) since the first of the Vista series (before 7, 8, and 10). Microsoft no longer thinks it can convince people to pay for Windows, so this strategy is seemingly being dropped. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Security at 10:47 am by Dr. Roy Schestowitz
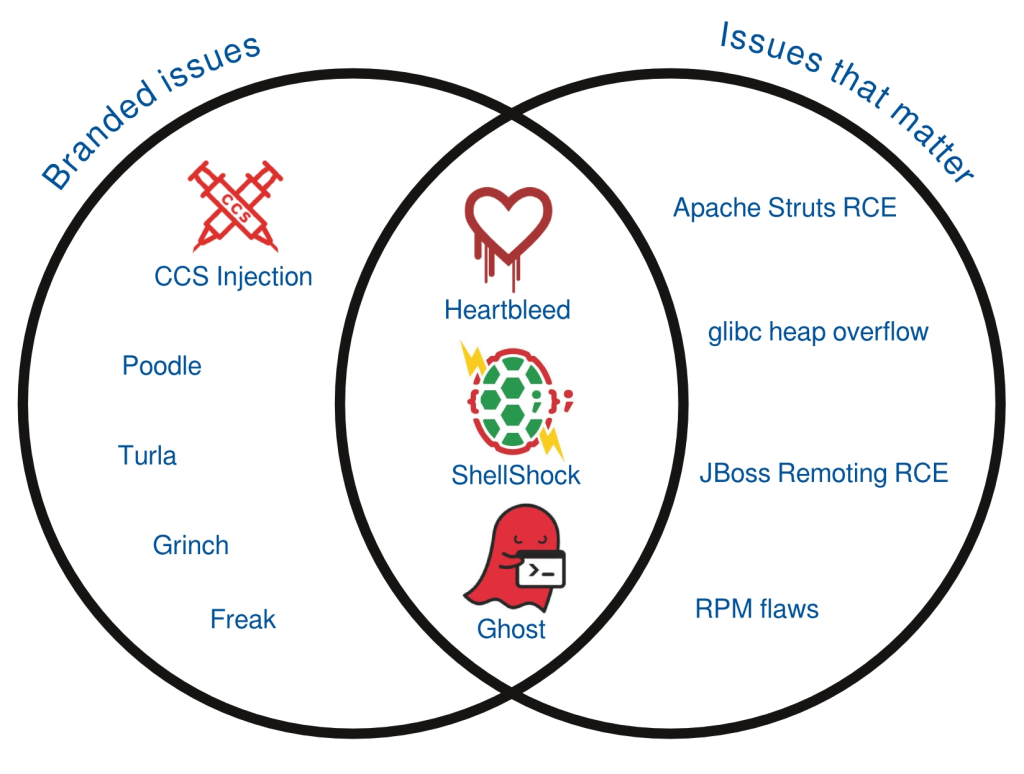
Image courtesy of Red Hat, demonstrating lack of correlation between severity and logos/brands
Summary: Many journalists bamboozled into becoming couriers of CrowdStrike, an insecurity firm which tries to market itself using a name and logo for a very old bug
THERE is a disproportionate level of coverage not of Free software but of bugs in Free software. We last wrote about it only days ago
A firm called CrowdStrike (who? Exactly!) is trying to emulate the ‘success’ of previous FUD campaigns. Now is the time to check who’s a real journalist (fact-checking) and who’s just serving PR campaigns like “VENOM”, a shameless FUD campaign from CrowdStrike.
The whole “VENOM” nonsense was covered in a good article titled “VENOM hype and pre-planned marketing campaign panned by experts”. To quote: “On Wednesday, CrowdStrike released details on CVE-2015-3456, also known as Venom. Venom is a vulnerability in the floppy drive emulation code used by many virtualization platforms.
“However, while it’s possible that a large number of systems are impacted by this flaw, it isn’t something that can be passively exploited.
“Several security experts discussed the flaw online, focusing on the marketing and the media attention that it generated – including some over-hyped headlines. Most media organizations were briefed ahead of time about the discovery and gagged by embargo until the Venom website launched, so they had plenty of time to write.
“Many media articles compared Venom to Heartbleed, which is an apples to oranges comparison. If anything, the only commonality is the fact that both flaws had a pre-planned marketing campaign.”
Here comes the “Heartbleed” brand. Yet again. They’re using names that are scary (even all caps, like “GHOST”) because it’s so much easier to sell than “CVE-2015-3456″. Journalists rarely have the technical knowledge to analyse a bug or a flaw, so they assume bugs and logos are indicative of severity.
This patch Tuesday Microsoft revealed 40+ vulnerabilities. Not a single one had a brand name, logo, etc. Here is how IDG covered 46 flaws publicly disclosed by Microsoft just for this Tuesday (Microsoft hides even more flaws). So many flaws were collectively covered in one article and yet there are no logos; none has any branding.
“VENOM” has become the latest example of what we call bugs with branding. This has got to stop because it corrupts journalism and makes the field of computer security almost synonymous with marketing or advertising. CrowdStrike used ALL CAPS (for emphasis rather than acronym) and connotation with poison to market itself, an insecurity firm, after finding a floppy drive bug from over a decade ago. There is a logo too (the first example we found of it), not just branding for this bug, dubbed “VENOM”.
Bug branding (turning number into branding-friendly FUD) seems to have adopted the ALL CAPS convention from “GHOST”, only for extra scare. This FUD has surfaced even in Linux-centric sites, which played along with the marketing campaign. Red Hat [1] and SJVN [2], even Phoronix [3] and Softpedia [4], have covered it by now, despite no focus on security news there.
Branding for bugs leads to stupid headlines that are more poetic than factual and are very light on facts. There is little substance there. This whole recipe (bug+brand name+logo=lots of publicity without much merit) has been repeatedly exploited to give a bad name to FOSS security. A lot of headlines try to connect this to the “Heartbleed” brand. Headlines that we have found so far (links below) include “New Venom bug hits data centers, but it’s hardly Heartbleed”, “Venom bug could allow hackers to take over cloud servers – and experts say it could be worse than Heartbleed”, “New Venom flaw may be worse than Heartbleed, researchers warn”, and “Venom vulnerability more dangerous than Heartbleed, targets most virtual machines”.
Zack Whittaker (former Microsoft staff) covered it like this in the CBS-owned tech tabloid, ZDNet: “Bigger than Heartbleed, ‘Venom’ security vulnerability threatens most datacenters”
Here is that “Heartbleed” brand again. “Please Stop Comparing Every Security Flaw to Heartbleed,” said one good headline from Gizmodo (that’s just how they covered this marketing campaign).
The word/brand “Heartbleed” was made up by a Microsoft-connected firm. Watch coverage from Microsoft-friendly sites and you will find headlines like: “Heartbleed, eat your heart out: VENOM vuln poisons countless VMs”
Dan Goodin, a foe of FOSS (from a security angle), brings in the NSA and Bitcoin to add FUD amid this branded bug/buzz. He wrote about the latest branded bug not once but twice (see links below). He is squeezing the most FOSS FUD out of it (opportunism). Kim Komando chose the headline “New bug taking over the Internet”. No sensationalism here? One press release said “Better Business Bureau Says Most Don’t Need to Worry” [about the branded bug], so there is some objectivity out there too, or an effort to calm people down.
Watch carefully how the bug is marketed in the media: Logo with SVG-like transparency; for a bug! Looks like it was prepared by graphics/marketing professionals. Are insecurity firms now liaising with marketing firms to professionally draw SVG logos for bugs? More logos for simple bugs (we found several, but one main logo) are circulating, usually with photos of snakes. See the complete list [1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24, 25, 26, 27, 28, 29, 30, 31, 32, 33, 34, 35, 36] as of this morning. How much more of this FUD is going to circulate before journalists realise that they make a mountain out of a molehill? █
Related/contextual items from the news:
-
CVE-2015-3456 (aka VENOM) is a security flaw in the QEMU’s Floppy Disk Controller (FDC) emulation. It can be exploited by a malicious guest user with access to the FDC I/O ports by issuing specially crafted FDC commands to the controller. It can result in guest controlled execution of arbitrary code in, and with privileges of, the corresponding QEMU process on the host. Worst case scenario this can be guest to host exit with the root privileges.
-
The QEMU fix itself is now available in source code. Red Hat has been working on the fix since last week.
-
-
Popular virtualization platforms relying on the virtual Floppy Disk Controller code from QEMU (Quick Emulator) are susceptible to a vulnerability that allows executing code outside the guest machine.
Permalink
 Send this to a friend
Send this to a friend
05.13.15
Posted in News Roundup at 6:03 pm by Dr. Roy Schestowitz

Contents
-
What’s your Linux dream job? The Linux Foundation recently asked our Twitter followers to share their ideal Linux careers. Many responded that they’re already living the dream, working as sysadmins and developers (or by simply getting to use Linux in their everyday tasks.) While others imagine fulfilling careers not yet within their grasp. Here are 10 of our favorite responses, along with a few resources for learning more about each dream Linux career path.
-
When you moved to Linux, you went straight for the obvious browsers, cloud clients, music players, email clients, and perhaps image editors, right? As a result, you’ve missed several vital, productive tools. Here’s a roundup of five umissable Linux apps that you really need to install.
-
Yesterday on Datamation, Matt Hartley wrote what could best be described as a reminder piece about the folks using Windows XP at home or in small businesses having options when it comes to replacing that particular operating system, and that the best option — go ahead and say it with me — is Linux.
-
The idea of solar sails was first introduced in popular culture by none other than Carl Sagan, more than 40 years ago. This particular technology was not a priority for scientists in the past decades, with very few exceptions, but The Planetary Society and Bill Nye want to change that by launching a small spacecraft called CubeSat that will be powered by light.
-
Desktop
-
A slate of devices, which includes 15.6-inch notebooks and a 20-inch all-in-one desktop PC, will be sold through selected resellers and distributors across the country starting from mid-May, 2015.
-
HP is one of the big companies that provide users with computers that came with Ubuntu pre-installed, and now those PCs are going to be sold in Russia as well.
-
The Cirrus7 nimbini mini PC that is built with some great hardware and with a case from machined aluminum is now available for sale.
-
Server
-
Rackspace reported its first quarter fiscal 2015 results on May 11, with company executives sounding very optimistic about the company’s future prospects.
For the quarter, Rackspace reported net revenue of $480 million, for a 14.1 percent year-over-year gain. Net income for the first quarter was reported at $28.4 million, up from $25.4 million in the first quarter of 2014.
[...]
Rackspace’s cloud fortunes today are somewhat tied to the open-source OpenStack cloud platform, which it helped to create. Rhodes sees potential for OpenStack both in the public cloud space as well as the private.
-
Kernel Space
-
-
-
A new version of the Linux kernel, 4.0.3, has been released by Greg Kroah-Hartman and is now ready for download. As it stands right now, this is the most advanced version available, and the same can be said about the branch.
-
Graphics Stack
-
One of the latest commits to the xorg-server that’s seen relatively few commits this development cycle is support for smooth scrolling with XWayland.
-
I’ve found out from various people in the know that AMD has assembled a “tiger team” to tackle outstanding Catalyst driver issues. This tiger team isn’t Linux specific, but Linux driver issues will be fully evaluated and tackled by this new group of driver specialists.
-
Last year AMD open-sourced their VCE video encode engine code for use by their open-source Linux graphics driver stack with the Radeon DRM kernel driver and RadeonSI Gallium3D and worked out a new OpenMAX state tracker. That open-source code drop only worked on the support for “VCE2″ hardware found with the AMD GCN hardware and newer (Sea Islands, Kabini, etc). AMD’s open-source Linux team has now gained permission for providing open-source VCE 1.0 support to offer video encode to older Radeon graphics processors.
-
Nvidia has just announced that a new Linux driver has been released in the Long-Lived branch, fixing just a few issues and bringing better texture transfers.
-
Intel’s been working on open-source Linux support for Cherryview for more than one year while finally one of the last pieces of the hardware enablement puzzle has landed: OpenCL support for Cherryview.
-
Applications
-
Using Linux on the desktop on your computers will lead anyone to rely on a media or music player. A media player may not play movies (contrary to a movie player) but should be able to handle playlists, albums, and podcasts. What people quickly discover though is that the Linux platform has a many of these. A lot, actually. But it is difficult to know which one to choose, and depending on the distribution you may need to install additional codecs and other bits. Another aggravating factor is that while choice is good in these matters, no player really seems to stand out for each kind of platform. In my view, it has been already been several years that the choice of an actual media player for Linux is confusing. So confusing, sometimes, that I find myself wondering whether I shouldn’t turn directly to EMMS (yes, it’s that bad).
-
qBittorrent 3.2.0 was released recently and it includes numerous changes such as support for Qt5, rewritten WebUI code, episode filtering for RSS, per tracker re-announce and much more.
-
Two new Pithos versions were released yesterday: 1.1.0 (for GTK 3.14+ only) and 1.0.2 and they include an important bug fix which caused the app to stop playing randomly.
-
Proprietary
-
Slack is a team communication platform which features persistent chat rooms organized by topic, private groups and direct messaging, all searchable from one search box. Furthermore, the app integrates with Google Docs and Dropbox, GitHub and many others.
-
Instructionals/Technical
-
Wine or Emulation
-
Games
-
The charming sci-fi platformer was released for Windows in February to very positive reviews from press and customers, and is now finally available for Linux.
-
The popular action platformer has undergone a massive rewrite since last year to remove the dependency on XNA and to add a host of improvements. It is now nearing completion and has been made available in an open beta on Steam.
-
CO-OP : Decrypted recently added in Linux support to the rather good looking 2.5D platformer, so it’s time for an overdue look at it with some initial thoughts.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
We want to enable piwik to get meaningful statistics of kde.org visits, to be nice with privacy for that we have enabled the ip anonymizer plugin but we still need to provide a way for people to opt out.
-
This minor update includes a number of bugfixes, focusing especially on Kdenlive, Okular, Umbrello, and Marble. In addition to software bugs, issues with translations have also been addressed in this release.
-
digiKam is an Open-Source project Photos management software, specially for KDE but you can use it on Ubuntu or others distros too. In digiKam photos are organized in albums which can be sorted chronologically, by folder layout or by custom collections. Developers recently released digiKam 4.10.0 with 16 bug fixes. Developers main focus is on digiKam 5.0 release, as it is supposed to be a major release of digiKam.
-
digiKam Software Collection 4.10.0 arrived on May 12 and included numerous bug fixes reported by users since the previous version of the program, digiKam 4.9.0, which was announced back in April 2015.
-
GNOME Desktop/GTK
-
As part of the soon-to-be-released GNOME 3.16.2 desktop environment, we are happy to announce today the immediate availability of the GNOME Boxes 3.16.2 open-source virtualization software and virtual machine manager.
-
-
It’s with great sadness in our hearts that we write this article to you all, but it appears that in an email to the Foresight Linux’s mailinglist, Michael K. Johnson announces the retirement of the distribution.
-
-
It’s been a while since we heard about Papyros, the Linux distribution that used the Material Design concepts from Google, but developers have released a short video that illustrates the work they’ve done so far.
-
New Releases
-
-
On May 12, Steven Shiau announced the immediate availability for download and testing of a new development version of his famous Clonezilla Live distribution, version 2.4.1-19.
-
Slackware Family
-
Red Hat Family
-
Fedora
-
Foresight Linux officially called it quits yesterday due to a lack of developers. The project hasn’t seen a release in over two years, but it’s still sad when a distribution shuts down. Across town, Pete Travis posted a passionate open letter to Fedora on why it should remain true to its philosophy and Bruce Byfield pondered the age old mystery, “Why can’t Ubuntu play well with others?”
-
Today is an important day on the Fedora 22 schedule[1], with a significant cut-offs.
-
The Fedora Project is preparing to release their latest and greatest Linux kernel-based operating system, Fedora 22, which will arrive as expected later this month, on May 26, 2015.
-
Today marks the final freeze for Fedora 22 with plans to officially release this Red Hat sponsored Linux distribution update later in May.
-
As the Fedora 22 release approaches, there will be more benchmarks coming along with other tests (e.g. the latest X11 vs. Wayland, Fedora 22 graphics performance, etc). For today’s article I just wanted to make a few remarks about Fedora Workstation 22. Fedora Workstation 22 feels like a nice evolutionary upgrade over Fedora 21. GNOME 3.16 and these upstream improvements represent a bulk of the user-visible changes in Fedora 22. Below the hood there’s the GCC 5.0 compiler, Mesa 10.5, Perl 5.20, Linux 4.0, and many other package updates. If GNOME isn’t your thing, Xfce 4.12 is present along with the premiere of the LXQt desktop environment. The latest KDE Plasma 5 / Frameworks 5 packages are also present in Fedora 22. Many of the other Fedora 22 workstation/desktop changes have already been detailed in numerous Phoronix articles.
-
Debian Family
-
I wonder if systemd shouldn’t do more to detect problems during services initialization, as the transition to proper notification using sd_notify will likely take some time. A possibility would be to wait 100 or 200ms after the start to ensure that the service doesn’t exit almost immediately. But that’s not really a solution for several obvious reasons. A more hackish, but still less dirty solution could be to poll the state of processes inside the cgroup, and assume that the service is started only when all processes are sleeping. Still, that wouldn’t be entirely satisfying…
-
The creator of numerous GNU/Linux distributions are very excited to introduce us to RaspEX today, a distro based on the Debian GNU/Linux 8.0 (Jessie) and created to run on the Raspberry Pi 2 computer board.
-
Derivatives
-
Nearly a year after Tails 1.0, and the Tails 1.4 release is now available. Tails – short for The Amnesic Incognito Live System and is a privacy focussed Linux distribution.
-
Tails, The Amnesic Incognito Live System, version 1.4, is out.
This release fixes numerous security issues and all users must upgrade as soon as possible.
-
Tails 1.4 Updates the Windows 8 Camouflage to Work with the I2P and Unsafe Browsers
-
Canonical/Ubuntu
-
Ubuntu has been making big promises since 2011 when they chose Unity to be at the center of their universe. And while they failed to deliver on Ubuntu TV or Ubuntu for Android, they’ve got other tricks up their sleeves.
-
With its number of uses growing, the Snappy Ubuntu Core Linux operating system is now coming to network switches and refrigerators.
Canonical, the lead commercial sponsor behind the open-source Ubuntu Linux operating system, today announced an expansion of its push to embed Linux in everything from phones to refrigerators—and now network switches. The Snappy Ubuntu Core Linux operating system, a minimal version of Ubuntu Linux that provides an improved updating and security model, is designed for embedded devices and the Internet of things (IoT).
-
Canonical has published details in a security notice about an ICU vulnerability that has been found and fixed in Ubuntu 15.04, Ubuntu 14.10, and Ubuntu 14.04 LTS.
-
Although Ubuntu is best known for its desktop/server distro—which was recently updated to 15.04—the last few years have seen the project’s ambitions have grown considerably. For example, there’s the Ubuntu phone, which is beginning to win plaudits. In turn, solving the particular demands for a mobile platform led to new approaches and technologies that appeared again in Snappy Ubuntu, a “transactionally updated Ubuntu for clouds and devices.”
-
-
As we had anticipated correctly last week, Canonical has released an OTA update for Ubuntu Touch (OTA 3.5), an update which brings fixes for over 15 bugs, some 3G enhancements, fixes for a bunch oc calendar sync problems, removed some crashes regarding ubuntu-keyboard and indicator-network, fixed the bug that drained the battery when the phone was used in airplane mode, patched some routing problems and the suspend problems have been removed.
-
Today, May 12, we are happy to inform all Ubuntu Phone users that the Ubuntu Touch developers have just announced the release of the OTA 3.5 update for Canonical’s mobile operating system.
-
Last week, founder Mark Shuttleworth opened the Ubuntu Online Summit with a challenge to Linux desktop developers.
“I’m issuing a call to people who participate in every desktop environment,” he said, “to set aside our differences, to recognize that the opportunity now is bigger than those differences, to create experiences that spans phones and tablets, and PCs, to bring all of our applications, none of which are on one desktop environment or another.”
His words were rhetorically stirring — and provoked no major response whatsoever. Although some news sites reported his words without comment, probably most companies and projects have heard too many similar calls to action for this one to be effective.
-
-
Imagine if every time you wanted a Windows computer, you had to buy a Mac, format the hard drive and install Microsoft’s operating system. That would suck, right? This is pretty much how it is for Linux users, sadly. If you are a user of a Linux distro such as Fedora or Ubuntu, for the most part — unless you are a system-builder — you have to buy a Windows machine, and install your preferred operating system.
What if you want to buy a computer with an operating system such as Ubuntu pre-installed? Enter System76. The company sells computers — both desktops and laptops — running the Linux-based Ubuntu operating system. Recently, the company began selling the Meerkat — a mini computer based on Intel’s NUC. I have been using the computer for a few weeks now, with both Ubuntu and Windows 10 and I am ready to share the experience with you.
-
Now, we all know that you can use Ubuntu on a tablet device, so this may not come as news to you, but seeing the next-generation Ubuntu 15.10 Desktop Next on a Lenovo ThinkPad 8 Bay Trail tablet might interest you.
-
Today marks the start of IoT World in San Francisco, and TelecomTV is onsite to record a series of executive video interviews and product demos. As the telecoms sector shifts its focus from vertically-aligned M2M solutions towards more horizontal IoT platforms, we expected to see yet more jostling for position amongst platform providers and OS developers.
-
Announced by Mark Shuttleworth on May 4, 2015, Ubuntu 15.10 (codename Wily Werewolf) will be released later this year on October 22, 2015, according to the preliminary release schedule that was made public today.
-
-
Flavours and Variants
-
CompuLab has a long history of working with the developers of Linux Mint. The MintBox 2 is a good example of their cooperation, and it has gotten very positive reviews on Amazon. Now there’s a new product called the MintBox Mini and one of the Linux Mint developers has a preview of it.
-
A month after elementary OS “Freya” was released to the public, the developers have made public some details about the platforms that download it and the results are pretty surprising. From the looks of it, the Windows users are the main downloaders of this Linux OS.
-
Despite recent reports suggesting the contrary, Linux Mint isn’t committed to avoiding systemd, the controversial project taking Linux by storm. In fact, Clement Lefebvre, Linux Mint’s project leader, expects the next major releases of Linux Mint to use systemd by default.
No, Linux Mint isn’t switching to systemd immediately. The Linux Mint 17.x series and Linux Mint Debian Edition 2 will continue to use Upstart and SysV init, with systemd available as an option you can choose yourself. Linux Mint is giving systemd some time to mature before switching, but—with upstream projects and the Linux ecosystem as a whole moving towards systemd—Mint realizes it doesn’t have an option in the long term.
-
-
-
-
-
-
-
-
-
-
Samsung unveiled a series of IoT-focused “Artik” SoCs and modules, including dual- and octa-core COMs that integrate wireless radios and run Yocto Linux.
-
Phones
-
Android
-
Back in April the Moto X Android 5.1 Lollipop update emerged for one small market in Brazil, but so far that’s it and the millions of owners in the United States are still waiting for the latest software upgrade. Last night Motorola made some key announcements regarding the original Moto X Android 5 Lollipop update, and when we can expect it to arrive.
-
Android Wear, the wearable operating system developed by Google, has established itself as a credible option in the world of wearables. The mobile operating system platform allows for smartwatches and other wearables to take advantage of modified Android apps and gives Google a much-needed foothold in what is an increasingly important market. For enterprise customers, however, wearables are pretty much an unknown quantity. There are several studies that suggest wearables could find a suitable home in the enterprise, but for the most part, those devices have yet to show their value to corporate customers at this stage in the market’s development. To address that, Google has been courting third-party developers to build apps for Android Wear. Some of those apps can appeal to both consumers and enterprise customers. But the very fact that they can be used for the enterprise makes devices running Android Wear even more appealing. This slide show looks at some current Android Wear apps to see what might be useful for enterprise customers.
-
Google’s Android 5.1.1 update is finally pushing out in force to the Nexus 9, Nexus 7, and Nexus 10 bringing bug fixes for Lollipop problems. And while we haven’t seen widespread complaints just yet, the Android 5.1.1 update will almost certainly bring battery life problems to select Nexus users. With that in mind, we take a look at how you can go about fixing bad Nexus Android 5.1.1 battery life.
-
While we await Android Wear 5.1.1 to roll out on a wider scale, we had the opportunity to try the update out on the LG Watch Urbane. Google’s wearable platform has seen its fair share of incremental updates over the past several months, but this one is by far the biggest. You want Wi-Fi support? Done. An always-on screen? That’s here, too. Let’s take a look at what else is new.
-
Android L, also known as Android 5.0 or Lollipop, has been very slow to roll out for newer versions of Android phones, and now a lot of users want version 5.1. This is especially true for Motorola phones including the Moto G (both 1st and 2nd generation), the Moto X (also 1st and 2nd generation), and the Moto E, as well as other Motorola Android phones.
-
Sprint is giving its Galaxy S4 Spark and Note 2 customers some Android 5.0 Lollipop loving after recently releasing the said update last May 8.
-
Last month, it was revealed that Samsung was working on Android 5.1 for either device, with the update rumored to bring a Guest Mode feature, along with the ability to take images in RAW.
-
Apple still hasn’t disclosed sales figures, but it appears Apple Watch is outselling all of the Android Wear watches pushed by Google and its partners.
Never mind that those Google watches collectively hit the market long before Apple’s high-tech timepiece or that Apple is experiencing delays getting watches to buyers.
-
According to Canadian carrier Rogers, the Samsung Galaxy S6 and the S6 edge should get their Android 5.1 Lollipop update as early as next month. The carrier’s official website mentions June as the estimated release date for the update, although the website also says that the dates are subject to change.
Over this past month, we’ve heard that Samsung is already working on updating its latest flagships to Android 5.1 Lollipop, and we’ve also heard that the update should come with a new Guest Mode feature, as well as the ability to snap RAW photos. This is the first time we’re hearing about a potential release date for the update.
-
Android Wear 5.1 has reduced Google’s emphasis on talking to your wrist, which is a good thing. The new menu system makes it easier to get to apps and settings, and the simple swipe-based interface is intuitive.
The emoji-drawing support is excellent and being able to connect remotely to a smartphone using Wi-Fi is useful for when Bluetooth won’t stretch far enough.
Android Wear’s notification-handling and quick, useful interactions powered by Google Now make it the best smartwatch platform currently available, but only if your life is plugged into Google services such as Gmail, calendar and Play Music.
-
The complexity of application stacks keeps going up. Way, way up. Application stacks have always been complicated, but never like this. There are so many services, so many tools, so much more compute power available, so many new techniques to try, and always the desire, and the pressure, to solve problems in newer and cooler and more elegant ways. With so many toys to play with, and more coming every day, the toy chest struggles to contain them all.
-
It all sounds so straightforward: Put your code up on GitHub or start/join a project at the Apache Software Foundation (ASF), build a community of like-minded individuals, start a company, take in some funding, and then IPO. Or maybe not. One thing is certain: Running an open source company has unique challenges and opportunities. Although much has been written on the subject of open source and community building, I’d like to share three critical lessons learned in my travels as a co-founder and CTO of a venture-backed open source company.
-
GOG Galaxy is a new gaming client for the GOG distributions service, but for now it’s only available for the Windows platform. As a response, the GOG wish list now shows the open source GOG Galaxy client as the most requested item.
-
Events
-
Every moment spent was mesmerizing in the summit. Day 0, 7th May 2015 Thursday was the workshop day in the auditorium of the Computer Science Department. Presentations by Andika Triwidada on “GNOME Indonesia Translation”, Akshai M for “MicroHOPE(Micro-controllers for Hobby Projects and Education)”, David King on “Writing your first GNOME application”, and Ekaterina Gerasimova, Alexandre Franke on the topic “How to make your first contribution” were out of the box informative.
-
We’re happy to announce that recordings of five sessions from LibrePlanet 2015 are now online. Whether you couldn’t make it to the conference and are watching these for the first time, or attended and want to see them again, we hope you enjoy.
-
If you are interested in participating in this year’s Randa Meetings and want to have a chance to be financially supported to travel to Randa then the last 24 hours of the registration period just began.
-
Web Browsers
-
Mozilla
-
Mozilla is proud to announced that it has released the Firefox 38.0 ESR (Extended Support Release) internet browser, which brings interesting features.
-
Five of the 13 security updates for Firefox 38 are considered critical. Mozilla also disabled the RC4 cipher suite for encrypted TLS data.
-
Mozilla today launched Firefox 38 for Windows, Mac, Linux, and Android. Notable additions to the browser include digital rights management (DRM) tech for playing protected content in the HTML5 video tag on Windows, Ruby annotation support, and improved user interfaces on Android.
-
Because DRM is a ‘black-box’ technology that isn’t open source, we have designed a security sandbox that sits around the CDM. We can’t be sure how other browsers have handled the “black-box” issue but a sandbox provides a necessary layer of security. Additionally, we’ve also introduced the ability to remove the CDM from your copy of Firefox. We believe that these are important security and choice mechanisms that allow us to introduce this technology in a manner that lessens the negative impacts of integrating this type of black-box.
-
Ubuntu has been making big promises since 2011 when they chose Unity to be at the center of their universe. And while they failed to deliver on Ubuntu TV or Ubuntu for Android, they’ve got other tricks up their sleeves.
-
SaaS/Big Data
-
John Dickinson is Director of Technology at SwiftStack and Program Team Lead (PTL) of the OpenStack Swift project. Last year, he gave us an update on Swift’s progress with Storage policies: Coming to an OpenStack Swift cluster near you for Opensource.com. In this follow up interview, John offers tips for improving community collaboration on open source projects, and gives us a preview of his upcoming OpenStack Summit talk.
-
The end of 2014 was a momentous time for Hortonworks, which focuses on the Hadoop Big Data platform. The company had a successful IPO, driving home how focused many enterprises are on yielding more useful insights from their troves of data than standard data mining tools can provide.
-
-
Project Releases
-
Wireshark, the world’s most popular open-source, cross-platform, and free network analyzer software, has been updated to version 1.12.5, a release that fixes numerous issues, patches important security vulnerabilities, and updates protocol support.
-
Openness/Sharing
-
Open Access/Content
-
Students facing eye-popping costs of college textbooks could save substantial amounts of money under a bill that would encourage the use of electronic texts.
The House on Tuesday approved a pilot program and study of so-called open-source texts that faculty could assign instead of traditional books that can cost students as much as $1,200 a year. The bill, which passed 144-0, next heads to the Senate.
It would establish a task force to develop plans for the best use of open-source texts through an existing program at Charter Oak State College.
-
Security
-
Google Inc., taking a new approach to enterprise security, is moving its corporate applications to the Internet. In doing so, the Internet giant is flipping common corporate security practice on its head, shifting away from the idea of a trusted internal corporate network secured by perimeter devices such as firewalls, in favor of a model where corporate data can be accessed from anywhere with the right device and user credentials.
-
-
IBM’s Andy Thurai didn’t quite put the words into former RSA CTO Deepak Taneja’s mouth, but did prompt him by asking at the start of a TIE Startup Con panel in Cambridge, Mass., earlier this month whether Internet of Things security is a “time bomb ready to explode.”
-
CVE-2015-3456 (aka VENOM) is a security flaw in the QEMU’s Floppy Disk Controller (FDC) emulation. It can be exploited by a malicious guest user with access to the FDC I/O ports by issuing specially crafted FDC commands to the controller. It can result in guest controlled execution of arbitrary code in, and with privileges of, the corresponding QEMU process on the host. Worst case scenario this can be guest to host exit with the root privileges.
-
The QEMU fix itself is now available in source code. Red Hat has been working on the fix since last week.
-
-
Popular virtualization platforms relying on the virtual Floppy Disk Controller code from QEMU (Quick Emulator) are susceptible to a vulnerability that allows executing code outside the guest machine.
-
Defence/Police/Secrecy/Aggression
-
The U.S. military is considering using aircraft and Navy ships to directly contest Chinese territorial claims to a chain of rapidly expanding artificial islands, U.S. officials said, in a move that would raise the stakes in a regional showdown over who controls disputed waters in the South China Sea.
-
Max Fisher, now at Vox, learned well during his apprenticeship under Marty Peretz at The New Republic. This week, he was among the first to try to smear Seymour Hersh’s piece in the London Review of Books, which argued that pretty much everything we were told about the killing of Osama bin Laden was a lie. Most importantly, Hersh’s report questions the claim that Washington learned of OBL’s whereabouts thanks to torture—a claim popularized in the film Zero Dark Thirty.
There’s a standard boiler plate now when it comes to going after Hersh, and all Fisher, in “The Many Problems with Seymour Hersh’s Osama bin Laden Conspiracy Theory,” did was fill out the form: establish Hersh’s “legendary” status (which Fisher does in the first sentence); invoke his reporting in My Lai and Abu Ghraib; then say that a number of Hersh’s recent stories—such as his 2012 New Yorker piece that the United States was training Iranian terrorists in Nevada—have been “unsubstantiated” (of course, other reporters never “substantiated” Hersh’s claim that Henry Kissinger was directly involved in organizing the cover-up of the fire-bombing of Cambodia for years—but that claim was true); question Hersh’s sources; and then, finally, suggest that Hersh has gone “off the rails” to embrace “conspiracy theories.”
-
Four years after U.S. forces assassinated Osama bin Laden, Pulitzer Prize-winning investigative reporter Seymour Hersh has published an explosive piece claiming much of what the Obama administration said about the attack was wrong. Hersh claims at the time of the U.S. raid, bin Laden had been held as a prisoner by Pakistani intelligence since 2006. Top Pakistani military leaders knew about the operation and provided key assistance. Contrary to U.S. claims that it located bin Laden by tracking his courier, a former Pakistani intelligence officer identified bin Laden’s whereabouts in return for the bulk of a $25 million U.S. bounty. Questions are also raised about whether bin Laden was actually buried at sea, as the U.S. claimed. Hersh says instead the Navy SEALs threw parts of bin Laden’s body into the Hindu Kush mountains from their helicopter.
-
R.J. Hillhouse, a former professor, Fulbright fellow and novelist whose writing on intelligence and military outsourcing has appeared in the Washington Post and New York Times, made the same main assertions in 2011 about the death of Osama bin Laden as Seymour Hersh’s new story in the London Review of Books — apparently based on different sources than those used by Hersh.
-
A three-year operation to smuggle official documents out of Syria has produced enough evidence to indict President Bashar al-Assad and 24 senior members of his regime, according to the findings of an international investigative commission.
The prosecution cases against the Syrian leaders focus on their role in the suppression of the protests that triggered the conflict in 2011. Tens of thousands of suspected dissidents were detained, and many of them were tortured and killed in the Syrian prison system.
-
Fox News defended Republican presidential hopeful Jeb Bush after he said he would still have authorized the invasion of Iraq “given what we know now,” claiming that Bush simply misunderstood the question.
-
Transparency Reporting
-
They’ll be examined for evidence of any pressure brought to bear by a hereditary monarch-in-waiting on elected ministers, and for any evidence that government policy was changed following the prince’s intervention.
-
Prince Charles’ secret letters to British government ministers expressing frank views that the government has warned could undermine his political neutrality will finally be published on Wednesday.
-
Prince Charles clearly doesn’t want to talk about his ‘black spider’ memos to ministers, which are about to be released, after his aide was filmed body blocking a reporter who tried to ambush to ask about the secret letters.
The memos, written to various government departments between 2004 and 2005, will be released at 4pm after a 10-year legal battle by The Guardian.
They are understood to show Charles’ disagreeing with government policy.
As Charles arrived at Marks and Spencer’s flagship store near Marble Arch on Oxford Street in London, Channel 4 News’ Michael Crick asked if he was “worried” about the letters and if he was still writing to ministers – and whether he thought he was behaving “unconstitutionally” in doing so.
-
Secret letters that Prince Charles wrote to Tony Blair’s ministers are finally being revealed after a fight lasting several years.
It’s a battle that’s cost taxpayers more than £275,000 and needed a ruling by Britain’s highest court.
So why has there been such a long wrangle over some bits of paper? Here are all your questions answered.
-
The publication of letters Prince Charles sent to government ministers is a triumph – of sorts – for the Freedom of Information Act.
The point of the act is to enable the public to understand better how those in authority are governing us. The release of the letters allows us a limited peek behind the curtains to see how the heir to the throne has been seeking to influence government policies.
But boy, what a struggle. The government has fought very hard for a decade to prevent the disclosure of 27 pieces of correspondence between the prince and ministers in Tony Blair’s government.
-
Prince Charles said British troops were under-resourced during the war in Iraq, according to letters from him published on Wednesday which the government had tried to keep secret in case they cast doubt over the future king’s political neutrality.
The comment about the armed forces came in a letter from the 66-year-old prince to former Prime Minister Tony Blair in 2004, one of 27 letters he wrote to former ministers in 2004 and 2005 which were released to the public after a decade of government attempts to block publication.
-
The determination of Queen Elizabeth II to avoid any action or utterance that might be deemed “political” has become the status quo. Little is known about her personal passions or politics. If she has any – and she surely has – she keeps them to herself.
But monarchs and future monarchs, even since the end of executive monarchy, have always meddled. It is Elizabeth, not her son Charles, who is the exception rather than the rule.
-
People opposing a cull of badgers to prevent the spread of tuberculosis in cattle were described by Charles as “intellectually dishonest” in a letter revealing that he has long been in favour of the controversial process.
In a letter to the then Prime Minister Tony Blair in 2005, the Prince criticised what he described as the “badger lobby” for objecting to the killing of badgers while disregarding the slaughter of cattle which contract the disease.
-
A cache of secret memos between Prince Charles and senior government ministers has been released after a 10-year legal battle, offering the clearest picture yet of the breadth and depth of the heir to the throne’s lobbying at the highest level of politics.
The 27 memos, sent in 2004 and 2005 and released only after the Guardian won its long freedom of information fight with the government, show the Prince of Wales making direct and persistent policy demands to the then prime minister Tony Blair and several key figures in his Labour government.
From Blair, Charles demanded everything from urgent action to improve equipment for troops fighting in Iraq to the availability of alternative herbal medicines in the UK, a pet cause of the prince.
-
A cache of secret memos sent by Prince Charles to senior UK ministers has finally been published, following a 10-year freedom of information battle between the Guardian and the government. The letters reveal that Charles lobbied ministers, including the former prime minister Tony Blair, on a wide range of issues, including agriculture, the armed forces, architecture and homeopathy.
-
There will be many disappointed people today I’d guess. Clarence House has released a statement that the publication of these letters will “only inhibit” the Princes ability to express concerns. Complete rubbish, if a member of the Royal Family is sending letters of a non-personal nature to those in our government, its of utmost importance that UK citizens are privy to their contents.
-
Environment/Energy/Wildlife
-
Imported energy as a share of total US energy consumption last year fell to just 11.16%, continuing a dramatic downtrend since 2005, when dependency stood at 30%. This is nothing short of a revolutionary trend-change, especially when you consider the gargantuan energy consumption of the US, which stands just shy of 100 quadrillion btu per year. Because US energy consumption overall has either bottomed, or is set to advance at least a little, the next dramatic move lower in the energy deficit will come in 2017, as LNG exports really get underway. TerraJoule.us believes global currency markets have not yet discounted these coming changes. Viewpoints overall about energy use, production, renewables, and global trade remains firmly anchored to an era that ended roughly a decade ago. Moreover, it’s astonishing that anyone who was watching markets a decade ago could possibly think the US Dollar is headed for trouble today. The US will become energy independent by 2019, according to the TerraJoule.us forecast. While the swings in fossil fuel trade are the driver for this change, the gains in renewables that will start hitting harder in the latter part of the decade will perfect and ensure this new era. Energy independence has typically been a subject for geo-political analysts. However, for our purposes, it’s the effects on the US Dollar and the impact on energy transition more broadly which are the main concerns for energy-focused investment, and the energy mix to 2020.
-
In the aftermath of the 7.3-magnitude tremor in Nepal this week, Seattle-based NGO Splash has launched a campaign to raise $500,000 (£320,000) for its water projects in Kathmandu.
-
Finance
-
WTO, TPP, NAFTA, CAFTA, and a host of trade agreements are causing America to hemorrhage jobs and the resultant downward pressure on wages. Add the productivity gains realized from automation and technology and the future of jobs in America looks pretty bleak. The government is cutting back on social programs and privatized welfare systems dependent upon the whims of the wealthy didn’t work for Louis the XVI or any other aristocracy throughout history. How will American workers support their families and keep our economy vibrant? There is a way but it will take courage. However, the long-term benefits are sustainable and fair. Professor Wolff talks to Tim Danahey and tells us how.
-
I really, really dislike this, but EU law leaves me no choice. I’m not comfortable blatantly ignoring tax law. I don’t think the EU could really do anything to me, but I wouldn’t be shocked if a future EU-US treaty were to suddenly make me responsible for years of back VAT. And I would like the option of visiting the EU in the future, rather than risk trouble because I’m evading taxes.
-
PR/AstroTurf/Lobbying
-
Common Cause and the Center for Media and Democracy sent federal authorities new evidence today that the American Legislative Exchange Council (ALEC) is falsely passing itself off as a tax-exempt charity and effectively using taxpayer dollars to subsidize its lobbying on behalf of private interests.
Common Cause filed a supplement to its three-year-old tax whistleblower complaint against ALEC, and the two groups sent a joint letter to Internal Revenue Service Commissioner John Koskinen demanding an investigation, collection of fines and back taxes, and the revocation of ALEC’s status as a tax-exempt charity. Supporting evidence available here.
-
Censorship
-
We learned recently from Paris that the western world is deeply and passionately committed to free expression and ready to march and fight against attempts to suppress it. That’s a really good thing, since there are all sorts of severe suppression efforts underway in the west – perpetrated not by The Terrorists but by the western politicians claiming to fight them.
-
Privacy
-
AOL’s fastest-growing business is advertising technology, which few people understand, like, or value.
In its acquisition announcement this morning, Verizon Wireless declared its $4.4 billion acquisition of AOL, the Internet stalwart, to be a driver of its “over the top,” or Internet-delivered, content strategy.
-
The Justice Department on Tuesday withdrew its appeal of a lower court’s December ruling that said it was illegal for police to attach a webcam to a utility pole and spy on a suspected drug dealer’s house in rural Washington state for six weeks.
The government did not comment on its decision to drop the appeal in a brief filing to the 9th US Circuit Court of Appeals.
The video camera operated 24 hours a day. Footage was synced to the computer of a Kennewick Police Department detective who could operate the camera from afar via its pan-and-zoom capabilities.
-
Civil Rights
-
In fact the first focus of the Tory government is on removing rights that protect ordinary people from their betters, be they human rights or employment rights.
-
-
Today marks the 30th anniversary of a massive police operation in Philadelphia that culminated in the helicopter bombing of the headquarters of a radical group known as MOVE. The fire from the attack incinerated six adults and five children, and destroyed 65 homes. Despite two grand jury investigations and a commission finding that top officials were grossly negligent, no one from city government was criminally charged. MOVE was a Philadelphia-based radical movement dedicated to black liberation and a back-to-nature lifestyle. It was founded by John Africa, and all its members took on the surname Africa.
-
David Cameron will introduce a counter-extremism bill later in May…
Permalink
 Send this to a friend
Send this to a friend
Posted in Courtroom, Europe, GNU/Linux, Google, Microsoft, Patents at 4:33 pm by Dr. Roy Schestowitz
Image from Android Beat
Summary: The marriage of convenience between Microsoft and Cyanogen helps reaffirm CyanogenMod’s status as a Microsoft Trojan horse which must be rejected
MICROSOFT is assaulting Android from numerous angles at the same time. There is no way Microsoft can compete with Android on technical merit, so Microsoft is, as usual, resorting to underhanded tactics and dirty tricks. Our recent article about Microsoft’s assault on Android says that “Cyanogen is confirmed as a Microsoft Trojan horse also elsewhere, so it’s not merely a rumour.”
Stallman asked us for additional references for that, so we provided a few [1, 2, 3], including one from Microsoft’s unofficial mouthpiece ([1] is from the original announcement). Anyone who still thinks of Cyanogen as an independent company is clearly not paying attention. The days of CyanogenMod are gone; now there’s just a proxy called Cyanogen and it is controlled by Microsoft just like Nokia was controlled by Microsoft after Elop had taken charge.
The announcement which unofficially confirmed Cyanogen’s status as a Microsoft proxy was made a few weeks ago, but we think many of the details are still not entirely clear to some negligent observers. It is not stated explicitly, but basically, CyanogenMod would push Microsoft software at the expense of Google et al. software (also Google/Android partners), turning Android into a sort of “Microsoft Android” — a term which some other sites now casually use as well. Android is facing the threat of a classic embrace extend and extinguish manoeuvre by a Microsoft proxy.
“We are having a fundamental miscommunication,” said Stallman. “The CyanogenMod I have heard of is a system distro. Various people have told me about installing in phones.”
That was well before Microsoft harnessed the popularity of CyanogenMod to attack Android, or to turn it into “Microsoft Android” (same thing which was attempted by Amazon, Facebook, and Nokia).
“You are talking about “CyanogenMod” as some sort of entity which can do things,” said Stallman. “That is a total surprise to me. What relationship exists between those two?”
One predates the other and Microsoft needs CyanogenMod to operate like a company, e.g. Cyanogen. Microsoft requires that in order to manipulate CyanogenMod in this turf war against Google and AOSP (Android Open Source Project).
“I will look at those articles,” said Stallman regarding additional links we sent to him. “Does this mean that when people install CyanogenMod on their phones, it standardly includes Skype etc?”
I recently found out that even some companies like HP preinstall Skype on Android tablets (I found out because I bought one for my parents in law). One has to wonder who pays who and what deals are silently being made, not publicly. With respect to Cyanogen’s CM12.1, I think that their latest release contains many Microsoft apps. I have not downloaded CM12.1 or anything like this to confirm it, but it seems like an inevitability. The announcement from Cyanogen (about the Microsoft deal) was made some weeks ago, so we think some of the details are still not entirely clear (they remain to be seen in practice), but basically, CyanogenMod would push Microsoft software (spyware, or ‘cloud’) into phones. We wrote additional articles about it and will continue to write as new details emerge. More Microsoft spyware and surveillance are being spotted by the media even this month, so whatever Microsoft puts on Cyanogen is likely to be as privacy-infringing as is legally allowed (if not well beyond it).
Stallman has been eager to understand what is happening here. We explained that Microsoft ‘embraces’ Cyanogen to make CyanogenMod a distro through which Cyanogen partners will spread Microsoft spyware, hoping that this adequately explains the relationship. Stallman wanted some broader context though. “It leaves the most important question unanswered,” he wrote to us. “Will the CyanogenMod distro that users install contain these Microsoft apps? Does it contain them now?”
Seeing the confusion here, we clarified a little further; CyanogenMod and Cyanogen are synonyms only in the sense that CyanogenMod (CM), previously a username of the guy who founded the company (Cyanogen), are company-product. A quick historical roundup:
- CyanogenMod (name of person) uses AOSP (Android Open Source [sic] Project) to make his own fork/derivative of Android{tm}
- CyanogenMod (self named, like Linus and Linux) becomes popular
- CyanogenMod (the person) is hired by Samsung
- CyanogenMod leaves Samsung
- CyanogenMod establishes a company called Cyanogen
- Microsoft sues Samsung using patents, compelling it to install Microsoft spyware (by default in Android) in order to attain settlement
- VCs give money for Cyanogen to develop CyanogenMod
- Microsoft ‘embraces’ Cyanogen to make CyanogenMod a distro through which Cyanogen partners will spread Microsoft spyware
- (Coinciding with the above) After much lobbying in Europe, Microsoft paralyses Google and dubs Google apps in Android ‘anti-competitive’. This is accompanied by potential legal action.
We hope this adequately explains the relationship between CyanogenMod and Cyanogen and we hope that Microsoft’s strategy in attacking Google is better understood now. It’s an extension of the “Scroogled” PR campaign that Microsoft has sunk so much money and effort into. Microsoft, being Microsoft, is very focused on annihilating the competition rather creating its own products.
We always recommend Replicant and F-Droid, and have done so for years (even at CyanogenMod’s expense). See our articles from 2013. We sort of foresaw what is happening now, including what Microsoft does to Samsung and other Android distributors at the moment (patents as tools of extortion). According to the press in Taiwan, Microsoft now pressures companies to put Microsoft spyware in their distribution of Android or face patent lawsuits/higher patent royalties. This is extortion, blackmail, abuse of retaliatory means etc.
“I think it would help if the FSF issued some kind of statement regarding Microsoft’s behaviour,” I told Stallman, “[especially the attacks which happen] behind the scenes, countering Orwellian charm offensives that seek to paint/frame Windows as “Open Source” and insist that Microsoft “loves” [GNU/]Linux. What Microsoft has been doing recently sure increased the blood pressure levels of many Free software supporters (I wrote a lot about it this year). A high-authority, facts-based response would perhaps help counter Microsoft’s narrative.” █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, FSF, Law at 3:20 pm by Dr. Roy Schestowitz

Source: Conference by Richard Stallman, “Free Software: Human Rights in Your Computer” (2014)
Summary: Media mistreatment of the very roots of Free/Open Source software (FOSS), which is now approaching 35 years in age and increasingly thriving
IN recent weeks we have found several ‘news’ articles that gave us cause for concern. Some were shared with Richard Stallman, a regular reader of Techrights, for his views to be expressed and portions of the correspondence can be found here (cautiously redacted to reduce potential animosity/tensions).
It is not unusual, especially these days (age of openwashing), to see the label “Open Source” misused. Not too long ago we identified some very gross distortion of the term “open source” to essentially openwash Facebook’s surveillance ambitions, focusing on poor people. Facebook traffic has sunk pretty badly over the past year (based on Alexa it’s a massive drop), so Facebook is trying really hard to frame/paint itself as “ethical”, even when it tries to expand its surveillance to people too poor to get connected to the Internet. This isn’t altruism, it’s opportunism and malice. It’s definitely not “open source” and the dot org suffix (Internet.org) is clearly inappropriate, not just misleading. “Facebook mistreats its users,” Stallman explained. “Facebook is not your friend, it is a surveillance engine.”
There was also an effort to delete GNU from history — an effort that has gone rather aggressive. Stallman was in the process of speaking to editors who jad allowed this to happen (dumb lawyers called GNU and Stallman’s text “Open source Manifesto” in the article “Open source Manifesto turns 30″). Stallman asked me to show him the original publication site and tell him how to write to them. It wasn’t too clear whether to write to the editor/site or the author/law firm. The former can issue some fixes/corrections, we tend to think, superseding what was contributed by lawyers. The article comes from a formal publication which often publishes patent lawyers’ pro-software patents columns (we have seen over 100 of them over the years). The target audience is lawyers. The latest is no exception to the rule. It is an article by Leech Tishman Fuscaldo & Lampl LLC and the Web site is London-based, with Andrew Teague as the Associate Publisher, Mark Lamb as the Publishing Director, and Chris Riley handling subscriptions. When it was first published Stallman was eager to contact “Either one, or both! [editor and writer] But the sooner the better.” No correction has yet been published. It’s nowhere to be found.
GNU and Free software are 30+ years old. A lot of people contribute to the misconception that it all started when Torvalds released Linux or when the term “Open Source” (not open source intelligence) was coined by the likes of O’Reilly. Watch the “Open Source” O’Reilly nonsense starting the clock more than 10 years later than GNU: “Twenty years ago, open source was a cause. Ten years ago, it was the underdog. Today, it sits upon the Iron Throne ruling all it surveys. Software engineers now use open source frameworks, languages, and tools in almost all projects.”
Rachel Roumeliotis is advertising OSCON 2015 (OS stands for “Open Source”), but she should know about GNU and its age. These people conveniently start the clock when O’Reilly and his henchmen got involved. They want all the credit and they want people not to speak about freedom. Eben Moglen already ranted about this, right on stage in an OSCON event nearly a decade ago.
“This shows how “open source” misses the point,” Stallman wrote to us. “If the frameworks, languages and tools they use are free software, that is good for their freedom. But if what they develop with those is nonfree software, it doesn’t respect our freedom.
“So open source “won” by ducking the important battle.”
Well, the “we already won” attitude (or notion) helps a defeatist’s approach; why fight for more freedom if “we won”? That’s what those people (even developers) who open a MacBook or some ‘i’ device want to happen; some would further insist that Apple and Microsoft are now “open source” players, so “game over”…
We have noticed that Microsoft is now googlebombing with “Windows open source”, promoting the ludicrous notion that it’s now “open” (or gratis), or that it will be so one day. It started about a month ago, maybe two; dozens of articles have served this PR strategy. we wrote some rebuttals and will write another one this weekend. There is a gross distortion of what actually happened and what is happening.
“Stallman was unhappy about the increasing prevalence of proprietary software,” said the aforementioned article From Lexology, “software protected by copyright law and usually licensed on a commercial basis by its owners.”
Yes, but Free software too is protected by copyright law, it’s just twisted into copyleft. “Source code is sometimes licensed under GNU GPL terms,” says the article, “a form of
“copyleft” rather than copyright.”
OK, so surely they know what Free software is and where it comes from. Why proceed with statements like: “The “open source” movement emerged in GNU’s wake. As with GNU, users of
open source code can look at the source code and modify it. However, unlike with GNU, they are not required to share their developments with the world at large.”
“We have noticed many articles throughout this past year or so — including some from Linux Foundation staff — that basically start history in 1991 as if GNU/Linux came out of a vacuum or from Torvalds’ bedroom.”Actually, unless they are using something like the BSD licence, they usually must. Then there are issues like SaaS, which are addressed by the AGPLv3, among other licences. But either way, Free software remains Free software, there is no justification for renaming it “Open Source” and calling the GNU Manifesto “Open source Manifesto”. It’s insulting to those who started the whole thing and wish to receive fair coverage or attribution, at the very least.
The Lexology sites presents some other issues, mostly to do with access, not just paywalls. Stallman asked: “Can you email me the full text of that article? I tried to fetch the page and what I got did not include the text.”
Stallman said he “wrote to them”, but more than a month later the article remains uncorrected, not updated, etc.
Another big load of revisionism (changing history) uses the “Open Source” label to delete GNU from history. Published last month, the article titled “At Birth, Open Source Was About Saving Money, Not Sharing Code” focuses on Torvalds (see feature image) and frames the movement as one that is centered around money. Stallman asked: “Is that someone opinionated who won’t listen to me?”
It is of course worthless asking for a correction when you know in advance none would be made. It later turned out to be part of a broader series of articles, some of which did cover GNU. I personally read several hundreds of items from the author and he’s more into ‘practical’ benefits, so I don’t think it would be worth arguing over. Some people just aren’t fond of freedom in the context of computing.
We have noticed many articles throughout this past year or so — including some from Linux Foundation staff — that basically start history in 1991 as if GNU/Linux came out of a vacuum or from Torvalds’ bedroom. Quite frankly, we think it’s an insult to history. We deem it negligent at best. Of course it leads people to deducing that the success of the system in its entirety is owing to the great “Linux values”, not GNU philosophy.
In summary, in our threads of communication with Stallman we were able to reaffirm that there were factual issues in the “Open Source Manifesto” article (it speaks about the GNU Manifesto) and despite Stallman’s request for correction, nothing has been done by the publishers. It’s like people just don’t wish to speak favourably about freedom in computing. Mac Asay, a Mormon (i.e. more superstition a religion than most other religions), compares Free software people to dangerous religions — a typical smear directed at a largely secular Free software community. Perhaps there are just those who are impossible to please because they are inherently opposed to control over one’s machine and would rather buy digital prisons from Apple than work a little harder to gain control or acquire freedom-respecting tools. █
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Microsoft at 8:47 am by Dr. Roy Schestowitz
Locked inside Gates

Summary: Microsoft’s proprietary software, such as Visual Studio Code and PowerShell, thrown at GNU/Linux users in an effort to promote Microsoft’s way of doing things and re-enforce lock-in
MICROSOFT is trying very hard to confuse the population. It’s aiming at low-hanging fruit — the non-technical people who are easy to bamboozle and convince through repetition that Microsoft is now “Open Source”. Microsoft’s googlebombing, as we have stated here before, keeps pushing Microsoft and “Open Source” into headlines. Jim Martin from PC Advisor is doing the “Windows Open Source” routine even one month after something actually happened (publicity stunt in Wired Magazine) and another British news site does the “Microsoft Open Source” routine (yet again!). If one isn’t careful, he or she might be led to believe that Microsoft completely embraced “Open Source”. See yesterday’s headline “What if Windows went open source tomorrow?” Days ago we found openwashing in a puff piece from Kevin Kelleher at Time Magazine. This is propaganda. It’s effective. People repeat what the propaganda tells them.
The most serious issue with all this is perspective or perception. In this new article about “.Net Core” (as in open core) Bill Weinberg is correct about what ‘open’ (openwashed) .NET does; it’s all about Windows and Microsoft lock-in. It is about leading people, including developers, into the prisons of proprietary software (Windows, Office, SQL Server, Hyper-V and so on). Microsoft recently used some non-news about Visual Studio Code (which is as proprietary as can be) to seduce people into the fantasy of “Open Source Microsoft”. As one GNU/Linux-centric site put it: “Microsoft Visual Studio Code, as opposed to the original Visual Studio for Windows, is not a complete integrated development environment containing an its own compiler and typical tools of this kind of development environments but it’s simply a code editor like sublimetext, atom, kate or brackets.”
So it’s not only proprietary but also less potent than Free/libre software. Paul Krill, the Editor at Large at InfoWorld, continues his Microsoft apologism, going further than openwashing Visual Studio. “Continuing its overtures toward open source,” he says (loaded statement), “Microsoft is unveiling technologies for packaging applications and remotely debugging JavaScript.”
Another article, titled “Visual Studio Code For Linux: What it Means”, provides another kind of analysis and notes that ‘Linus Torvalds once said: “If Microsoft ever does applications for Linux it means I’ve won.”‘
“Bill Gates once said: “They’ll get sort of addicted, and then we’ll somehow figure out how to collect sometime in the next decade.” That very well applies to developers as well as end users. Microsoft is trying to make developers ‘addicted’ to Microsoft.”Well, but those applications are proprietary. They’re unwanted. A Microsoft promotion site wants people to run “.NET on Linux and Mac OS X” (that’s the real goal, spreading .NET). By repeating the words “open source” in relation to proprietary software Microsoft gives people the wrong/false impression that its proprietary software is suddenly “open”. Microsoft is doing that to its Web browser right now [1, 2] and by extension, by saying that this proprietary browser may run on Windows for phones, Microsoft promotion sites serve to openwash Windows Phone [1, 2]. How appalling it that? Cross-platform efforts with proprietary software and a little bit of “open core” in very few areas (getting developers ‘hooked’ on Microsoft APIs) is not “Open Source”. It’s only now that Microsoft says it may finally stop torturing the Web with ActiveX, so never mind “Open Source”, what has Microsoft ever been for standards? Bill Gates once said: “They’ll get sort of addicted, and then we’ll somehow figure out how to collect sometime in the next decade.” That very well applies to developers as well as end users. Microsoft is trying to make developers ‘addicted’ to Microsoft.
Microsoft booster Darryl K. Taft was one among several (including Adrian Bridgwater) who promoted Telerik, a longtime booster of .NET (“enhancements to its existing solutions, ongoing support for Microsoft development tooling” says the latest press release). The push for the whole world to become prisoner of .NET is reaching new heights as even Fedora 23 is chewing Mono [1,2] (after it got rid of it half a decade ago).
Let’s remind ourselves that amid all the “Microsoft Open Source” nonsense (googlebombing) there is very little that is actually open and a lot which is proprietary and geared towards lock-in. Microsoft now wants to ‘addict’ UNIX/Linux users to Microsoft’s command-line syntax [1, 2]. As if GNU/Linux hasn’tgot enough Free software shells like GNU Bash… well, apparently it needs Windows, too. Microsoft insists it needs proprietary Windows blobs like PowerShell. To quote one report: “After having shocked the world by releasing Visual Studio Code for Linux, Microsoft had the pleasure of announcing today the immediate availability for download of PowerShell Desired State Configuration (DSC) for GNU/Linux operating systems.”
Compiling a pile of Windows lock-in for another platform is not openness. It’s a proprietary trap, just like Visual Studio Code. Developers are hopefully wise enough to see through the lies and the gross spin. █
Related/contextual items from the news:
-
We announced last week that the release schedule of the upcoming Fedora 23 Linux operating system has been published and that the distribution might arrive on October 27, 2015, if everything goes according to plan and no unexpected delays occur during the development cycle.
-
Aside from the other features proposed thus far for Fedora 23, the update of the popular Red Hat sponsored Linux distribution due out in late 2015, you can add Mono 4.0 to the list.
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day
- Software Patents Continue to Collapse, But IBM, Watchtroll and David Kappos Continue to Deny and Antagonise It
The latest facts and figures about software patents, compared to the spinmeisters' creed which they profit from (because they are in the litigation business)






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA