10.24.16
Updates Regarding EPO and BoAC: Unrest and Injustice Carry on
Hanging in the balance of Battistelli’s gross injustice

Summary: Some of the latest information which is publicly and privately available to us, in particular regarding the case of a suspended judge which represents unprecedented erosion of the appeal boards’ independence (and hence lack of justice in the Organisation)
THE EPO is in a very sad state. The culprits — those who have ruined it — still keep their jobs and even have their contracts extended/renewed. Insiders can now get the Administrative Council’s minutes from June. They came out several days ago. What took so long? Are those minutes so secretive and is the EPO afraid that outsiders will exploit them? We are going to publish these quite soon. June’s meeting was all about BoAC, whereas back in March Battistelli came under fire (or the pretense of it). Things don’t appear to have moved onwards; the latest (October) meeting gave room for hope, but December is unlikely to bring the well-overdue sacking of Battistelli. The crowdfunding of a Battistelli departure (or firing) party just continues and the money piles up. Fireworks?
“One day we hope to release more material from the March and June meetings of the Administrative Council.”For those who forgot, the June meeting was all about BoAC, brushing aside the social issues as if they didn’t matter, after the March meeting promised they would be dealt with urgently and even sort of set an ultimatum for Battistelli — one which he obviously ignored.
A person who has seen the Administrative Council’s minutes from June told us that “[i]t makes an interesting comparison with how the meeting was perceived at the time. Turns out that the BoA reform only just got through. Some great quotes from Battistelli as well about SUEPO.”
One day we hope to release more material from the March and June meetings of the Administrative Council. We already have such material, but we never got around to publishing it due to lack of time (no urgency at the time).
We have meanwhile noticed an additional comment with some links in it, relating to claims that the EPO lied about what had happened in the midst of the above meeting. The comment in IP Watch says:
The entire text of the AC’s March resolution can be found at http://www.hipo.gov.hu/en/news/sztnh-hirek/hirek-esemenyek/147th-meeting-of-the-administrative-council-of-the-european-patent
The background of the issue is explained here: http://kluwerpatentblog.com/2016/03/18/supervisory-board-european-patent-office-votes-for-reforms-increasing-the-pressure-on-president-benoit-battistelli/
Looking over at IP Kat for updates (the site itself is self-censoring, but comments continue to come out), we have:
Why is this post still in the top 5? What happened afterwards? Is the guy dismissed or not?
There is no coverage anymore. The people from IP Kat seem to not care about the EPO scandals, especially after the EPO banned the site for a day. They are self-censoring, specifically regarding EPO scandals (they still mention the EPO, but only in a positive context and UPC promotion). Not by accident, certainly!
Here is one response to the above:
No. Battistelli is still there.
The AC didn’t take any disciplinary action against him.
Casado and Topic were also renewed.
Another person wrote:
Not dismissed. Under the new regulations adopted in June, he remains suspended. Without any running procedure.
In a clear violation of judiciary independence….So, it looks like he’ll remain suspended until his end of term, and with current management no chance of reappointment.
This is a hidden disciplinary measure…
If new allegations pop up, these are likely to be the result of the previous investigation, which under national procedures would not be permitted to be used during a different procedure…
“Is there something rotten in the state of Denmark,” another comment added, linking to “Danish Press Coverage of the EPO by Berlingske” (Techrights).
A few more (newer) comments say:
Quite frankly, this is unacceptable. The EPO’s whole purpose is to uphold the law (on patents). How can they be trusted to do that properly when they do not even follow their own internal rules and procedures, let alone common principles on the rule of law (or human rights)?
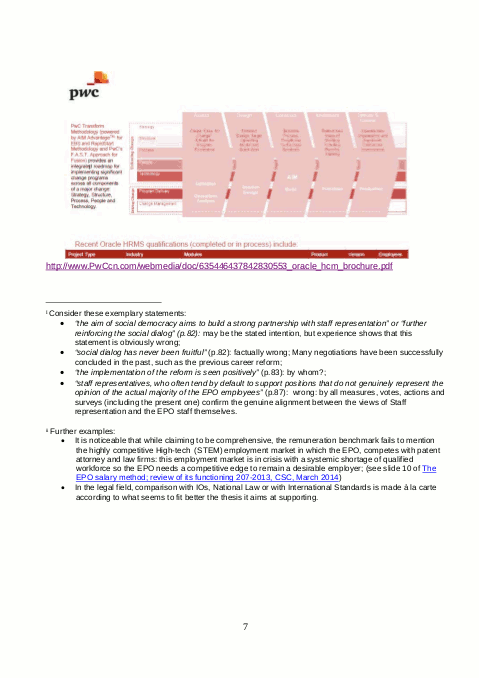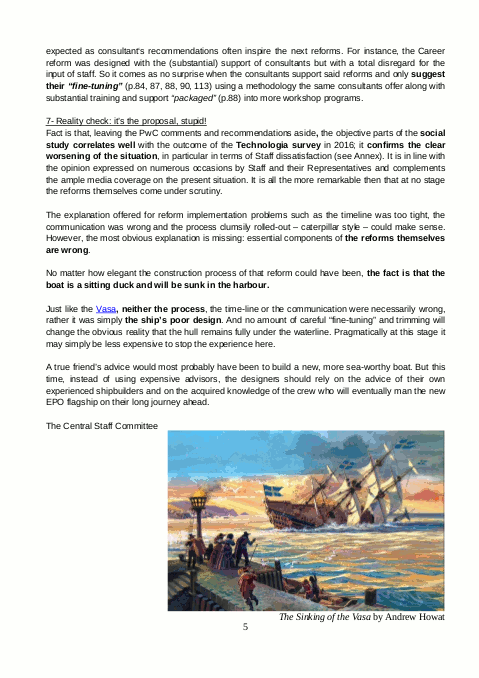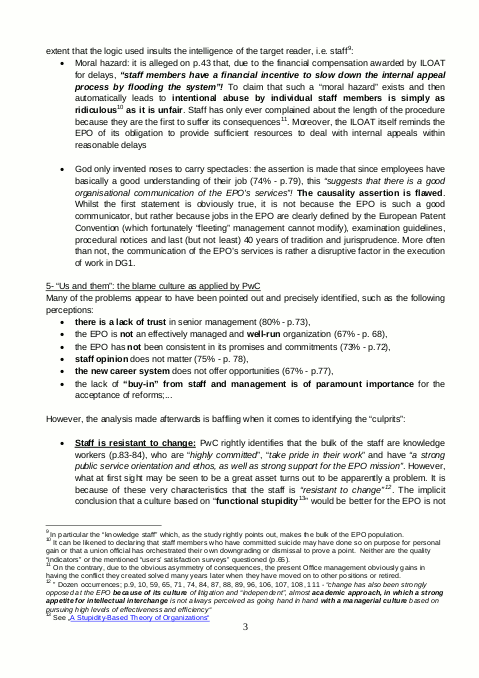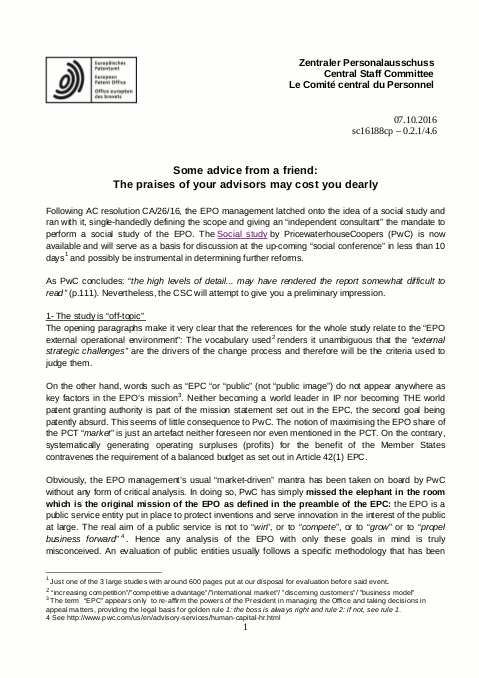
The EPO (and the AC) would do well to remember the importance of ensuring that not only is justice done but that it is seen to be done. The damage to the EPO’s reputation (and to that of all professionals working in the patent sphere) could be immense if this is not handled properly. Indeed, that ship may well have already sailed.
Quite frankly, this is unacceptable. The EPO’s whole purpose [etc. etc.]
[Yawn] …
Trop c’est trop. Battistelli doit partir (Philip Cordery, 11.10.2016)
[double Yawn] …
“Enlarged Board publishes decision: EPO President violated judicial independence”
[more Yawns] …
Et sinon, ces croquettes, ca vient?
A bit of sarcasm:
The EPO’s whole purpose is to uphold the law (on patents).
Sorry, that was yesterday, before the “much needed” reforms to “modernize” the European Patent Office.
Now the whole purpose seems to be lining the pockets of the Representatives of the AC so that they can fake [mild] outrage at what is going on – or no outrage at all at the President violating judicial independence.
The ship sailed a long time ago…..3 years ago
And the silence here is not just embarrassing its highly suspicious
The above comment says that “Casado and Topic were also renewed” — a subject we’ll explore again later this week. These renewals were publicly mentioned in the EPO’s latest update regarding the meeting of the Administrative Council of the European Patent Organisation. The overview was published online several days later (the following week in fact) and it says:
The Administrative Council of the European Patent Organisation held its 149th meeting in Munich on 12 and 13 October 2016 under the chairmanship of Jesper Kongstad, Director General of the Danish Patent and Trademark Office.
After the Chairman’s report on the most recent meetings of the Board of the Administrative Council, the Council noted the activities report given by the President of the European Patent Office, Benoît Battistelli (to be published shortly on this website). The Council was pleased with the excellent results achieved by the Office in terms of efficiency and productivity but again stressed the need to be conscious of any possible impact on quality. The Council urged staff and management to use the momentum of the Social Conference, held just ahead of the Council meeting, in order to further the social dialogue and work together to find solutions.
The Council then proceeded with a series of appointments and reappointments of members of the Enlarged Board of Appeal and a Chairman and of legally and technically qualified members of the Board of Appeals.
Later, under the heading Legal and International Affairs, the Council heard a status report on the Unitary patent and related developments, given by the Slovak delegation, representing the country holding the EU presidency for the second half of 2016.
The Council made the following appointments to the Boards of Appeal Committee each for a three-year term, starting on 13 October 2016
a) from among the delegations:
Mr Roland Grossenbacher(CH) and his alternate Mr Derk-Jan De Groot (NL),
Ms Patricia García-Escudero (ES) and her alternate Mr Jorma Hanski (FI),
Ms Bucura Ionescu (RO) and her alternate Ms Catherine Margellou (GR)
b) from among former or serving judges:
Mr Klaus Bacher (DE), Mr Justice Birss (GB) and Mr Are Stenvik (NO). Alternate members in this category would be appointed at the next Council meeting. The Council noted that the Board of Appeals Committee and the President would make a joint proposal for appointment of the President of the Boards of Appeal in time for the next Council meeting.
By way of further appointments to the Council’s own bodies, in each case for a three-year term, starting on 15 December 2016, the Council:
-elected Mr Josef Kratochvíl (CZ) deputy chairman of the Council,
re-elected Mr Lex Kaufhold (LU) deputy chairman of the Budget and Finance Committee; and
-elected Mr Vojko Toman (SI) member of the Board of the Administrative Council.
It also elected Ms Delfina Autiero (IT) member representing the Administrative Council within the Supervisory Board of the Reserve Funds for Pensions and Social Security (RFPSS) with effect from 12 October 2016.
On a proposal from the President, the Council decided to extend until 31 December 2018 the appointments of Mr Alberto Casado (ES) and Mr ZeljkoTopic (HR), Vice-Presidents in charge of Directorate-General 2 and 4 respectively.
Finally, the Council noted, as a first step in a longer process, comprehensive social and financial studies and had an exchange of views on reviewing the disciplinary procedures framework.
The above is a somewhat ‘sanitised’ version of what was posted internally (and we leaked earlier this month).
Regarding that last line, stay tuned as later this week we have much to reveal about Željko Topić. It’s not a done deal; Battistelli was rumoured to be behind this renewal. █




















 Content is available under CC-BY-SA
Content is available under CC-BY-SA