07.16.15
Posted in Microsoft, Security, Windows at 8:49 am by Dr. Roy Schestowitz

Summary: The United Airlines Web site, which uses Microsoft software, gets cracked, but the corporate media ignores the role of the underlying platform
“United hackers given million free flight miles,” says the BBC right now. Go to the United Airlines Web site and you will immediately see that they use Windows (ASPX is exposed at the URL of the front page, which is bad security practice in its own right). The United Airlines site is hiding behind Akamai (i.e. GNU/Linux), but it still shows a lot about the back end, which suggests that Microsoft frameworks are largely to blame (maybe poor programming, too).
This comes at an interesting time because, to quote other British media, “Microsoft Ends Windows Server 2003 Support But What Now?”
“The bottom line is, nobody should ever trust Microsoft for hosting of any kind of site.”Well, any company that still chooses Microsoft for public-facing site hosting would have to be dumb or seriously irresponsible. Microsoft is now hoping to also become the host of GNU/Linux sites. Microsoft’s booster Pedro Hernandez re-announces Microsoft propaganda right now (“Microsoft Rolls Out Linux Support Services on Azure”) even though it is not new, it is merely entrapment by Microsoft. Microsoft’s propaganda network “1105 Media”, featuring Microsoft’s booster Kurt Mackie, adds to it [1, 2] and promotes hosting by Microsoft. The latest Microsoft Channel 9 propaganda (we saw quite a bit of that recently), goes as far as openwashing Azure.
The bottom line is, nobody should ever trust Microsoft for hosting of any kind of site. The company is incompetent and it puts the NSA’s interests (e.g. back doors) first. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Europe, Patents at 8:29 am by Dr. Roy Schestowitz

Summary: SUEPO (staff union of EPO) has just removed a post about Battistelli and his inner circle; we try to find out if union members or staff got threatened
LAST week SUEPO published some text and uploaded this PDF, which led us to writing this post.
Days later the PDF and the text both disappeared (it’s still not being reinstated and the PDF needed to be manually removed), so we have spent some time trying to find out what had happened. It’s almost certainly not accidental given the circumstances. One person told us that “the decision what is flagged public and what not is taken mostly by admins, and these are not members of the (political) SUEPO core team.”
Remember that SUEPO represents a great proportion of the EPO staff and also that the EPO engaged in censorship against SUEPO. There’s substantiate ground for fear. Battistelli’s inner circle is not speculative; this is just a list of names, their positions, and their family or professional ties. No defamation there, that’s for sure. No privacy violations, either.
We were not alone in wondering what had happened; there are already discussions about this online and offline (we may elaborate on this another day because some of the discussion is encrypted). Nobody seems to know for sure what is going on.
“No defamation there, that’s for sure. No privacy violations, either.”Does the EPO now induce self-censorship? First the EPO censored (deleted) E-mails, now it's censoring (blocking) entire Web sites such as Techrights. The People’s Republic of EPO might be a suitable new title for EPOnia, which views itself as independent from any country’s laws. Here is a new article about the EPO’s practice of censorship, composed and published yesterday morning. “EPO staff can still read TechRights at home or on mobile devices,” of course, “a fact that makes this attempt at censorship absolutely ridiculous. But it should also have access from its desktop computers at work just in case anyone finds links to prior art there.
“The EPO leadership has just scored an own goal: by blocking access to TechRights, it has now raised the profile of that blog.”
Dr. Glyn Moody, a journalist who covers issues including patents, calls it EPO “meltdown” (he wrote that 3 times over the past 24 hours). SUEPO, in the mean time, publishes another PDF, this time regarding the “120th Session of the ILO-AT” (it is a long 12-page paper).
As a side note, and it would be irresponsible to suggest that it is connected to the EPO’s actions (we have no such evidence except circumstantial), almost exactly on the same day (or the day after) the censorship was reported we got strongarmed by ICANN/ENOM to update records for the domain, as if someone complained that it was out of date. I received an authentic E-mail titled “IMPORTANT: Immediate Response Required – whois problem report: : techrights.org” on the same morning I wrote about the EPO’s censorship of techrights.org. ICANN/ENOM complaints are one way (among others) to induce domain-wide/universal blocking or expose one’s home address. I have been wrestling with this for 3 days now. It’s not as stressful as dealing with DDOS attacks, but it sure is a nuisance. █
Permalink
 Send this to a friend
Send this to a friend
07.15.15
Posted in News Roundup at 8:52 pm by Dr. Roy Schestowitz

Contents
-
Desktop
-
Adobe is not having a good time right now. Its Flash product has more security holes than Swiss cheese, making it a recurring target for hackers and bad guys. The tech world owes Steve Jobs an apology for poo-pooing his choice to disallow Flash from iOS. Things have gotten so bad, that Mozilla is blocking it by default as a major security risk.
-
If you’re looking for a new Linux distribution, don’t let the choices overwhelm you. This list of rising distributions will get you off to a great start.
-
Dabbling for the first time in Linux starts with choosing a Linux distribution. A typical “Linux” system is built up of software from many different open-source projects, including the Linux kernel. Linux distributions—or “distros”—are the projects that package all this software into an easily installable, usable operating system.
-
-
-
-
-
Each one of these laptops has one or two really great points counterbalanced by one or two unfortunate compromises. Usually, you’re either trading performance for general aesthetics and build quality or the other way around. Chromebooks with nice screens tend to have slower internals, and Chromebooks with better internals are usually generic plastic laptops with faded, cheap LCD panels. And of course, there’s always the Chromebook Pixel, perfect in pretty much every way except that $999 price tag.
-
Chromebooks have been red-hot on Amazon’s bestseller list for a long time, with many people defecting to Chromebooks from Windows and OS X laptops. The Asus Chromebook Flip is a convertible device that sells for $250. Ars Technica has a full review of the Chromebook Flip.
-
Server
-
The latest list of the world’s fastest supercomputers, Top500 June 2015, shows the fastest of the fast growing ever more powerful. It also shows Linux is still number one with a bullet when it comes to supercomputing.
-
“The real focus is the roughly $20 billion Linux server market, which is where we’re focused for growth, and we’re a small part of that today on Power,” Balog said. “So I view it as $20 billion of upside for me to go after and all of that is competitive against x86.”
-
Kernel Space
-
Sasha Levin, the maintainer of the Linux 3.18 kernel series, announced recently the immediate availability for download of Linux kernel 3.18.18, an LTS (Long Term Support) branch that receives security patches and bug fixes for a couple of years then regular kernel branches.
-
I don’t know about you, but I’ve always found the idea of operating system kernels to be some mysterious and esoteric programming skill. Its importance cannot be overstated of course, but I’ve always felt that kernel programming and regular programming were two very separate skills.
I’ve recently had some patches merged into the Linux kernel, and thought it might be interesting to describe what I learnt from this brief dip into kernel development and how someone who is new to it might go about getting into this space.
-
-
Graphics Stack
-
Nvidia is making some changes to the way it’s installing its drivers on the Linux systems and they are now using a new kernel module source layout. It’s not something that will directly impact users, but it’s interesting to see that Nvidia is starting to shake things a little bit.
-
Applications
-
-
If you work with open source servers (such as the world’s most popular web server, Apache), you know a massive number of tools are available to you. They range from security to functionality to monitoring… to just about anything you can imagine. But if you were to compile a single list of tools to include on your open source server farm, what would that list look like?
My own list tends to fluctuate on any given day. But almost always, certain tools stay on it. Here are the tools I rely on the most. (NOTE: This list does not include such things as basic Apache mod tools or the big four (Linux, Apache, MySQL, PHP— LAMP.)
-
If you’ve ever taken a digital photograph into GIMP to remove red eye or an ex-girlfriend or ex-boyfriend, or crop out a finger that got into the edge of the frame, then you are practically a compositor. A “comp artist,” as they are called in the industry, specializes in taking disparate moving images and placing them in the same frame, usually to make it appear that the different elements were shot at the same time. On the big screen, you’ll see this in nearly every movie since 1933′s King Kong (or thereabouts), but the art has reached a science in the digital realm, where some movies are practically not so much as edited as they are superimposed.
-
Instructionals/Technical
-
Games
-
Volgarr the Viking, a 2D platforming game built by Crazy Viking Studios, has been released for Linux users on the GOG.com digital distribution platform.
-
Lucius II, a third-person action game developed and published on Steam for Linux by Shiver Games, will be released for Linux users, according to an entry in the Steam database.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Together with some friends we visited the LinuxTag in Stuttgart and afterwards founded a local Free Software user group. We helped each other to install Free Software on our computers, configuring them to be routers, mail/print or file servers. I enjoyed learning with others, exchanging ideas, trying to fix problems. I subscribed to many mailing lists, and was eager to participate in Free Software events.
-
The KDevelop frontend for Krazy tools has been ported to KF5, so it now works with the KF5 version of KDevelop.
-
On the user interaction side, the past years have accompanied our interaction designers with visual artists. This is clearly visible when comparing Plasma 4 to Plasma 5. We have help from a very active group of visual designers now for about one and a half year, but have also adopted stricter visual guidelines in our development process and forward-thinking UI and user interaction design. These improvements in our processes have not just popped up, they are the result of a cultural shift towards opening the KDE also to non-coding contributors, and creating an atmosphere where designers feel welcome and where they can work productively in tandem with developers on a common goal. Again, this shows in many big and small usability, workflow and consistency improvements all over our software.
-
Krita is a KDE program for sketching and painting, although it has image processing capabilities, offering an end–to–end solution for creating digital painting files from scratch by masters. Fields of painting that Krita explicitly supports are concept art, creation of comics and textures for rendering. Modelled on existing real-world painting materials and workflows, Krita supports creative working by getting out of the way and with a snappy response.
-
We’ve addressed this in many ways so far: we’ve optimized the code for performance so it’s more responsive and starts reasonably fast, we’ve made sure most done is accessible using the keyboard so we don’t feel clumsy and overwhelmed by all the options.
[...]
One of the developments that have struck me the most during last years is Kate. Instead of focusing on the editor, it went the KDevelop route: it has started to offer all of the information at once (especially odd, given that there’s quite some feature overlapping).
-
-
New Releases
-
We have been recently informed by Zbigniew Konojacki, the creator of the 4MLinux project, that the upcoming point release of the 4MLinux 13.0 distribution has entered development and that Beta builds are now available for download and testing.
-
Alpine Linux development team announced on July 14 the availability for download of the second maintenance release of the server-oriented Alpine Linux 3.2 operating system.
-
The Solus operating system is coming along, and developers are constantly making improvements to it. The most recent iteration got a few fixes and small changes, but the most important aspect is the fact that the boot time has been reduced considerably.
-
PCLinuxOS/Mageia/Mandriva Family
-
Ballnux/SUSE
-
On July 14, SUSE LLC had the great pleasure of announcing that they will provide a new partner program expansion which brings support for 64-bit ARM server processors to their award-winning SUSE Linux Enterprise Server (SLES) 12 computer operating system.
-
-
-
-
-
-
Now that 64-bit ARM processors are starting to generate some interest inside the data center, providers of Linux distributions like Suse are starting to get in line.
Today Suse announced that version 12 of Suse Enterprise Linux will be supported on 64-bit ARM server processors from AMD, AppliedMicro, and Cavium powering servers by Dell, HP, Huawei, and SoftIron.
-
Red Hat Family
-
In infrastructure, the company has the RHEL OpenStack Platform. For application development it has OpenShift, a platform as a service now on its third version. Red Hat rolled out extensive support for containers in RHEL and OpenShift too. Cormier says Red Hat is “well into that journey” of bringing open source products across the entire infrastructure stack.
-
Being first to release a new technology can give a company an advantage in the marketplace, but when the product isn’t true to your brand, it can backfire. Red Hat, a world leader in open-source software, learned this lesson in 2008 when it acquired the tech firm Qumranet in an attempt to move into virtualization, a technology that allows computers to simultaneously run multiple operating systems.
-
Many big names in the storage industry have been jumping on the Ceph train. And why shouldn’t they? It does it all. Well, almost. Originally developed by Inktank and later acquired by Red Hat, Ceph is a software-defined scale-out data storage solution. It supports Object, Block, and File storage. It also exposes a RESTful API that supports both OpenStack and Amazon S3. What is there to not like about it?
-
-
-
Fedora
-
Many Fedora users take advantage of the fact that Fedora is internationalized, which means it can be used by people that communicate in different languages. Fedora provides support for displaying information on the screen for many different languages. There is also support for different input methods allowing users to input text for native languages where the number of characters is greater than keys on their keyboard.
-
Container technology has lead to several other areas of development and one of them being an atomic operating system that sandboxes applications and delivers updates in a single image. Red Hat started their Project Atomic to provide applications in a containerized format and produced Atomic Host as the tiny OS on which they’d run. It didn’t take long before planners began speaking of doing similar for Fedora and now developers are in the early planning stages of bringing this idea to fruition.
-
-
Debian Family
-
Marketing to FOSS is radically different from general ads to consumers or to other businesses. To start with, FOSS can be deeply suspicious about exploitation and free-riding from business outsiders. Just as importantly, FOSS contributors are often as intelligent as they like to think, and would prefer to make decisions based on information rather than emotional appeals. For these reason, FOSS marketing needs a delicate touch in order to reach its target audience.
-
Derivatives
-
Canonical/Ubuntu
-
Canonical is preparing to launch a new major update for Ubuntu phones and we now have a few more details about the new features, improvements, and fixes that are going to land very soon.
-
A libwmf vulnerability has been found and fixed in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS operating systems.
-
Canonical’s Joseph Salisbury was happy to announce a few minutes ago the summary of the Ubuntu Kernel Team meeting that took place earlier today, July 14, 2015, on the Ubuntu’s official IRC channels.
-
On July 14, Canonical’s Łukasz Zemczak sent in his daily report on the work done by the Ubuntu Touch development team, informing us that the OTA-5 software update for the Ubuntu Touch mobile operating system was delayed for the next Monday, July 20, 2015.
-
Meizu might be feeling similarly anxious, as this is its first major release in Europe, having previously focused on producing smartphones for the firm’s home nation of China.
-
Ubuntu developers are making some really interesting progress with the upcoming Wily Werewolf release, and they have revealed some of the work that’s being done for the desktop. It’s not much to look at, but there are a couple of items that should be mentioned.
-
Meizu has started shipping its MX4 Ubuntu Edition to a select few, and we now have a chance to test it. The review is not yet ready, as we’re waiting for a new major update, but we can give you a first impression, and we all know that first impressions are everything.
-
A vulnerability that would allow users to crash Bind with specially crafted network traffic has been found and repaired in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS.
-
Canonical is rolling out an over-the-air update for smartphones running its Ubuntu software. Ubuntu OTA-5 adds one key new feature, a few smaller features and bug fixes, and lays the groundwork for a very important new feature that probably won’t work on most phones currently running Ubuntu software.
-
-
-
Hardkernel unveiled a $74, open-spec “Odroid-XU4″ SBC equipped with an octacore Exynos5422 SoC, 2GB RAM, eMMC flash, a GbE port, and dual expansion headers.
-
-
The WeTek OpenELEC is a Linux media player dedicated to Kodi with OpenELEC pre-installed that gives you access to IPTV services with the extra of being compatible with modular DVB tuners.
-
Phones
-
Tizen
-
Tizen has previously made its way onto the Raspberry PI 2 Development Board, but 3D acceleration was not working at that point. Well, the good news is that the Team over at the Samsung Open Source Group have got the 3D Acceleration working now.
-
Android
-
-
-
-
-
If you want a desktop PC, you’re typically going to have to fork over several hundred dollars (Windows OEM licensing alone can make up a significant portion of that). But what if you could turn open-sourced Android into a serviceable desktop OS? That’s what Jide is trying to do, with its ultra-cheap Remix Mini PC.
-
Sub-notebooks/Tablets
-
At the recent Red Hat Summit, Red Hat CEO James Whitehurst talks with Network World about new IT processes and why companies should focus on open source.
-
Xerte Project’s Open Source Initiative membership furthers both organization’s commitment to growing open source community and collaboration within institutions of higher education.
-
The US National Security Agency has offered up one of its cyber security tools for government departments and the private sector to use freely to help beef up their security and counter threats.
-
-
Not sure which tools belong in your open source server toolkit? Here are 10 solid go-to tools to get you started.
-
Events
-
Open source software supplier Obsidian Systems invites OS enthusiasts, developers, geeks and friends to the next ‘Free Beer Session’ on 27 August 2015. This session, the 17th in the series, will offer delegates fresh insight into the open source industry, challenges and opportunities.
-
Web Browsers
-
Mozilla
-
I’ve dogfooded Firefox OS since its early beginnings and have some of the early hardware (hamachi, unagi, One Touch Fire, ZTE Open, Geeksphone Keon, Flame and ZTE Open C). It was good to hear some of the plans for Firefox OS 2.5 that were discussed at Whistler, but I wanted to take the time and model of this post and remix it for Firefox OS. Firefox OS you are great and free but you are not perfect and you can be the mobile OS that I need.
-
As the zero days in Adobe Flash continue to pile up, Mozilla has taken the unusual step of disabling by default all versions of Flash in Firefox.
The move is a temporary one as Adobe prepares to patch two vulnerabilities in Flash that were discovered as a result of the HackingTeam document dump last week. Both vulnerabilities are use-after-free bugs that can be used to gain remote code execution. One of the flaws is in Action Script 3 while the other is in the BitMapData component of Flash.
-
SaaS/Big Data
-
Recently, all-in-one appliances have been much in the news. A few days ago, I covered Mirantis Unlocked Appliances, which deliver OpenStack and all the hardware resources you need for a deployment in one hardware/software entity. Then, Cloudera, which focuses on Apache Hadoop, and Teradata, a big data analytics and marketing tools company, announced the Teradata Appliance for Hadoop with Cloudera.
-
Laura is the founder and lead consultant for SafeStack, a security training, development, and consultancy firm. What does that mean exactly? SafeStack helps organizations choose the right kind of security best practices for them. Then, Laura’s team shows them how to implement those new-found security protocols. This usually calls for a strong dose of workplace culture change, which might sound like a tall order, but Laura tells me in this interview “we want security to be any empowering tool for growth rather than a costly hindrance to innovation.”
-
In the beginning of the open source OpenStack cloud effort, there were two projects – Nova Compute and Swift Storage. Swift is an integrated part of most OpenStack distributions but it is also the focus for a standalone company called SwiftStack, which was founded by Joe Arnold.
-
Oracle/Java/LibreOffice
-
CMS
-
After over four years of development, including missed deadlines on general availability, the open source Drupal 8 content management system (CMS) finally appears to be nearing the finish line.
Drupal, one of the world’s most popular CMS technologies, is used by many high-profile organizations, notably Whitehouse.gov, the flagship website of the U.S. government. While Drupal founder Dries Buytaert in 2012 announced Drupal 8 would be generally available in December 2013, that date passed with no release.
-
Why is being open source so important to us? At its most basic, being open source means users have access to and can manipulate PrestaShop code to make improvements or develop technical answers to address specific business needs. But more importantly, open source represents accessibility and flexibility. It’s an open-door policy versus the private club mentality of proprietary software. Our community is built around this open source ethos; it’s the source of our strength and it’s how we’re contributing to a more democratic e-commerce market.
-
At Memorial Sloan Kettering (MSK), the world’s oldest and largest private cancer center, our researchers and clinicians have pushed boundaries to generate new knowledge in patient care and cancer research for more than 130 years. This culture of innovation allows our scientists to continually develop new methods for treatment and work tirelessly to discover more effective strategies to prevent, control, and ultimately cure cancer.
-
Education
-
SIGES is a free, open source, available in French, Haitian Creole, and English. It is customizable to suit the schools: primary and secondary; professional and technical; private and public; in urban and rural areas, the school networks, sponsorship organizations, educational projects, etc…
-
Business
-
Funding
-
If you need further evidence that container technology is all the rage, just follow the money. Sysdig, focused on bringing infrastructure and application monitoring to the world of containers and microservices, has announced a $10.7 million Series A funding round led by Accel and Bain Capital Ventures (BCV). In conjunction with the funding, Sysdig announced the general availability of Sysdig Cloud, which it bills as “the first monitoring, alerting, and troubleshooting platform specializing in container visibility, which is already used by more than 30 enterprise customers.
-
BSD
-
The PC-BSD crew has released version 0.8.5 of their Lumina desktop.
Lumina 0.8.5 has a speed boost for the user button, desktop icons have improved styling and appearance, a new desktop plug-in is present for monitoring system hardware sensors, and there’s a desktop plugin container for custom QML/QtQuick scripts. There are also updated translations, new PC-BSD/FreeBSD packages, etc.
-
FSF/FSFE/GNU/SFLC
-
Canonical, Ubuntu Linux’s parent company, has often rubbed other free software groups the wrong way when it came to open-source licenses. On July 15, Canonical, with support from the Free Software Foundation (FSF) and the Software Freedom Conservancy (SFC), have changed Ubuntu’s licensing terms. The FSF states that Canonical’s new intellectual property (IP) policies “unequivocally comply with the terms of the GNU General Public License (GPL) and other free software licenses.”
-
-
-
Canonical have a legal policy surrounding reuse of Intellectual Property they own in Ubuntu, and you can find it here. It’s recently been modified to handle concerns raised by various people including the Free Software Foundation[1], who have some further opinions on the matter here. The net outcome is that Canonical made it explicit that if the license a piece of software is under explicitly says you can do something, you can do that even if the Ubuntu IP policy would otherwise forbid it.
-
The Free Software Foundation (FSF) and the Software Freedom Conservancy (SFC) have been bickering with Canonical since 2013 over concerns that certain clauses of the Ubuntu IP rights policy seemed to claim to override provisions of the GNU General Public License (GPL) – something the GPL explicitly forbids.
-
Today, Canonical, Ltd. announced an updated “Intellectual Property” policy. Conservancy has analyzed this policy and confirms that the policy complies with the terms of the GNU General Public License (GPL), but Conservancy and the FSF believe that the policy still creates confusion and possible risk for users who wish to exercise their rights under GPL.
-
Compilation copyright is an idea exclusive to the US (or North America anyway). It restricts collections of items which otherwise have unrelated copyright restrictions. A classic example is a book collection of poetry where the poems are all out of copyright but the selection and ordering of poems is new and has copyright owned by whoever did it.
-
Project Releases
-
The world’s most used open-source software solution for accessing shared Windows folders over a network from GNU/Linux and Mac OS X operating systems, Samba, has recently been updated to version 4.2.3.
-
On July 14, Lubomir Rintel announced the immediate availability for download of the fourth maintenance release of the stable NetworkManager 1.0 network connection management software for GNU/Linux operating systems.
-
Openness/Sharing
-
Open Data
-
OEP is part of the Norwegian Government’s work to promote transparency and democracy within the public sector. OEP aims to make the Norwegian public sector more open and accessible to citizens. OEP is based upon the Freedom of Information Act and related regulations.
-
Programming
-
Zend, the PHP company, is updating its namesake PHP application server to version 8.5 providing new features and performance for users. The Zend Server 8.5 release builds on the Zend Server 8 milestone which debuted with the Z-Ray application insight technology.
-
Perl 6 has been 15 years in the making, and is now due to be released at the end of this year. We speak to its creator to find out what’s going on.
-
Security
-
-
I won’t pretend to be Steve Jobs—I don’t even own a mock turtleneck—but I have to repeat his words from April 2010: “Flash is no longer necessary to watch video or consume any kind of web content.” Flash is a constantly exploited, superannuated bit of technology that useful in the early days of multimedia in web browsers, and now deserves to die.
When Jobs wrote “Thoughts on Flash” over five years ago, it was in response to the notion that Flash should be available on iOS. At the time, I asked repeatedly for Adobe to stage demonstrations in private using iOS development tools to show Flash running. They never took me up on it, or any other writer that I’m aware of, even though they had the ability. Flash for Android, when it appeared, was terrible. Within two years, it was dead.
-
-
-
-
-
Defence/Police/Secrecy/Aggression
-
The corporate media in both the UK and US are attempting to portray the Iranian desire to have the arms embargo lifted, as a new and extraneous demand that could torpedo the nuclear deal. This is an entirely false portrayal.
-
There is a parallel danger in Iran. The Iraq War was totally unjustified and illegal, but Saddam Hussein might nonetheless have evaded it had he boxed a bit more cleverly and allowed some foolish inspectors to wander around his palaces prodding at the teaspoons. Yes the inspections regimes will be galling, even humiliating. But patience will have its rewards. There is real danger though that the hardliners on the Iranian side will be able to muster sufficient local points of power to hamper inspections, thus giving the US and Israeli hardliners an opportunity.
-
Environment/Energy/Wildlife
-
An American-owned water export company has launched a massive lawsuit against Canada for preventing it from exporting fresh water from British Columbia.
Sun Belt Water Inc. of California is suing Canada for $10.5 billion US, the Canadian foreign ministry said Friday.
The suit has been filed under Chapter 11 of the North American Free Trade Agreement. Sun Belt says it has been “mistreated” by the B.C. government.
-
Senator Ted Cruz, raising cash for a 2016 presidential bid, was to meet privately Monday in Denver, Colorado with executives from major oil and gas corporations, all members of the pro-fracking lobby group Western Energy Alliance (WEA), according to details of the secret meeting shared with the Center for Media and Democracy.
The Republican presidential candidate, a climate change denier, is also a leading proponent of opening up federal lands in the west–in fact virtually all lands everywhere–to energy development, and for scrapping regulations on oil and gas development.
-
Finance
-
Greece’s rampant corruption is one of the reasons why the country’s economy is in such a mess. German companies have taken advantage of the system for years in order to secure lucrative deals.
-
-
The International Monetary Fund has set off a political earthquake in Europe, warning that Greece may need a full moratorium on debt payments for 30 years and perhaps even long-term subsidies to claw its way out of depression.
-
Prof. Wolff joins GRITtv’s Laura Flanders to talk about Sanders and Socialism. Is socialism still an American taboo?
-
PR/AstroTurf/Lobbying
-
A new FAIR study finds that NPR commentary is dominated by white men and almost never directly addresses political issues.
-
Privacy
-
I’m currently working on developing a guide to securing iOS devices in a hostile environment (basically, “iPads for activists”). Although iOS is solid, iCloud backup is dangerously insecure, and must be avoided at all costs. Worse, it is enabled by default!
-
It was an unusual group. An investigative journalist, a moral philosopher, an internet entrepreneur, a cyber-law academic, a government historian, a computer scientist, a technology exec, a long-time cop, an ex-minister and three former heads of intelligence agencies. I wondered not just how but if we could agree on anything, let alone an entire set of recommendations to reform UK communications surveillance.
Yet we did. The Royal United Services Institute panel was set up by Nick Clegg, the then deputy prime minister, in response to revelations from the US whistleblower Edward Snowden about the scale of intrusion by US and British intelligence agencies into private lives. Our remit: to look at the legality, effectiveness and privacy implications of government surveillance; how it might be reformed; and how intelligence gathering could maintain its capabilities in the digital age.
-
We’ve discussed the “cybersecurity” bill, CISA, that’s been making its way through Congress a few times, noting that it is nothing more than a surveillance expansion bill hidden in “cybersecurity” clothing. As recent revelations concerning NSA’s surveillance authorities have made quite clear, CISA would really serve to massively expand the ability of the NSA (and other intelligence agencies) to do “backdoor searches” on its “upstream” collection. In short, rather than protecting any sort of security threat, this bill would actually serve to give the NSA more details on the kind of “cyber signatures” it wants to sniff through pretty much all internet traffic (that it taps into at the backbone) to collect anything it deems suspicious. It then keeps the results of this, considering it “incidental” collections of information.
-
Google has jumped on the Bluetooth Low Energy (BLE) beacon bandwagon with a set of open standards and software interfaces to give Apple’s iBeacon a run for its money.
Apple rolled out iBeacon in 2013, and has been pushing it as a way for companies to do things like tracking potential customers’ movements as they wander around retail stores.
-
Move over iBeacon—today Google is launching “Eddystone,” an open source, cross-platform Bluetooth LE beacon format. Bluetooth beacons are part of the Internet of Things (IoT) trend. They’re little transmitters (usually battery powered) that send out information about a specific point of interest, and that info is then passively picked up by a smartphone or tablet in range of the transmitter. A beacon-equipped bus stop could send out transit times, stores could send promotions to the customers currently in the store, or a museum could send people information about the exhibit they’re standing in front of.
-
-
-
-
-
-
-
-
-
-
Open Rights Group has responded to the Report of the Independent Surveillance Review by the Royal United Services Institute (RUSI).
-
Their Panel included three former senior security staff, and RUSI are themselves very close to the UK’s defence and security apparatus. Thus the tone of the report was always likely to address the concerns of GCHQ and the Foreign Office before those of civil society. Martha Lane Fox, Ian Walden and Heather Brooke will have had a tough job to help produce a relatively balanced report that does at least go some way to address wider concerns.
-
Netzpolitik, the German website defending fundamental freedoms, has been charged for “treason” on 10 July by demand of the president of the German intelligence services. The case will be lead by the federal prosecutor in charge of espionage and terrorism.
-
Civil Rights
-
Having spoken alongside Mhairi at a few meetings, and much admired her, it is rather strange to find her in danger of becoming an object of cult veneration. Just as with Nicola Sturgeon, it seems the shock of seeing the coherent and intelligent articulation of views outside the narrow consensus manufactured by the corporate media and political class, really does strike home to people. They almost never get to hear such views put; Mhairi is being given a hearing because of her youth in her position, but the marginalisation and ridicule will soon kick back in. Above all, Mhairi should remind us of how the Labour Party has completely sold out those they used to represent, and abandoned the task of proposing an intellectually compelling alternative to trickledown.
-
Intellectual Monopolies
-
What exactly is of trade secret concern here? The answer is: the aggregate email addresses of the subscribers. Anyone who wants to show the broad scope of what is protectable as a trade secret will likely mention a customer list. What could be further from patentable subject matter, yet still be of value to its owner as a trade secret, than a customer list? Email addresses of subscribers can be likened in this respect to the classic customer list. Thus misappropriation of the email addresses might be a concern.
-
Copyrights
-
Mega.co.nz has lodged legal threats against a New Zealand based search engine. MegaSearch.co.nz allows users to search Mega.co.nz for content but has attracted the attention of the file-hosting company after using its logos and trademarks without permission. Mega.co.nz is demanding a full shutdown.
-
Romanian authorities and the FBI have reportedly coordinated to shut down three sites involved in the unauthorized distribution of movies and TV shows. Several men were detained and various domains were seized amid allegations of criminal copyright infringement, tax evasion and money laundering.
Permalink
 Send this to a friend
Send this to a friend
07.14.15
Posted in America, Law, Patents at 2:31 pm by Dr. Roy Schestowitz
In Lieu of Decades of Bad Practice
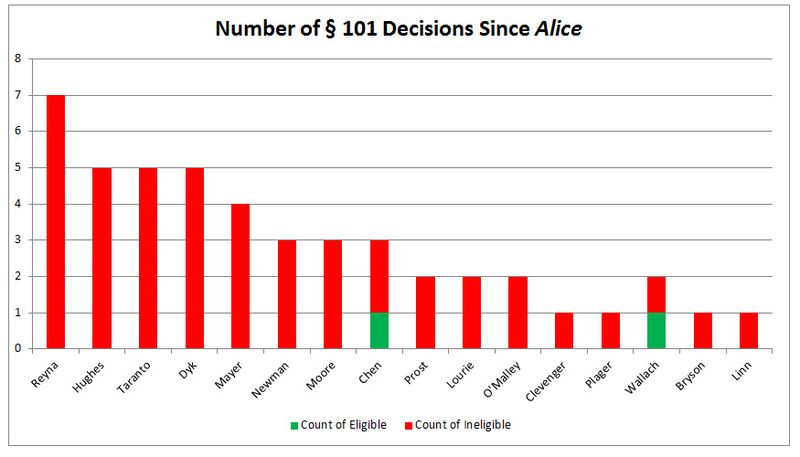
Credit: Bilski Blog
Summary: The so-called ‘AliceStorm’ is eliminating software patents (and other abstract patents) at an alarming (to patent lawyers) rate
LAST WEEK we wrote about Michelle Lee's remarks on patent law, conjoined with the report about the Alice case beating Microsoft's patent troll, Intellectual Ventures. Lee’s remarks were important because she is now the leading face of the USPTO (no matter her job title) and Alice is killing software patents very fast, impeding Microsoft’s attacks on Free software in the process. It was only four days ago that we last cited a new example where Alice slaughtered software patents, paving the way (by citation or argument/strategy) for future legal cases where software patents are at stake. This is one of the most fantastic developments that Techrights has seen in nearly a decade and if Groklaw was still active, it too would be jubilant (it partly celebrated the Alice ruling in News Picks, coming back to life after less than a year of total silence).
“Lee is finally recognising that everything has changed and therefore the USPTO needs somewhat of an examination overhaul, for courts almost always disagree on software patents granted by the USPTO.”Michelle Lee now claims that the USPTO needs more Section 101 guidance, based on this patent lawyers’ site. Lee is finally recognising that everything has changed and therefore the USPTO needs somewhat of an examination overhaul, for courts almost always disagree on software patents granted by the USPTO. Just look at the statistics.
According to Patent Buddy, this new ruling [PDF] is yet another victory. “Another case where application of Alice/101 to kill patents has jumped the fence from business methods to software,” to quote Patent Buddy, who added: “We are seeing 101/Alice rejections for everything from MRI devices to adhesives!” According to another new find from Patent Buddy, “US Pat. 6728877 and 7346766 Killed with 101/Alice in Summary Judgment in Lawsuit Against Lenovo by Tranxition in Oregon Dist. Ct.”
This isn’t being overlooked, except by patent lawyers who probably hope that nobody will pay attention. They cherry-pick the few cases where software patents somehow survive. Here is a software patents’ booster whining about this. He wrote: “Deals are still being done in the software patent world, but patent valuation is significantly less than even just a few years ago.”
It’s hardly shocking.
“The Alice/101 Kill Rate Is Accelerating,” Patent Buddy added, linking to a “MUST READ From Bilski Blog” where Robert R. Sachs coins (or advertises) the word/hashtag “AliceStorm”. To quote Sachs: “In just the first ten days of July, there have been ten decisions on patent eligibility—more decisions in first ten days of any month since Alice was decided last year. At this pace, we could see some twenty to thirty decisions this month. #AliceStorm is accelerating.”
It sure looks like even some of the most respected legal blogs (like Bilski Blog in this case) recognise that software patents are weakened by Alice orders of magnitude more often then they were weakened (or invalidated) by the famous Bilski case (it did happen albeit very infrequently). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, Microsoft at 1:54 pm by Dr. Roy Schestowitz

Summary: As Nokia is reduced to rubble in Microsoft’s fist (after epic entryism) the story of both companies is seriously distorted by Microsoft-friendly media in order to bolster Microsoft’s fictional version of the events
AMID the latest Microsoft layoffs we are deeply bothered to see misdirection and propaganda, almost surely coordinated behind the scenes by Microsoft's 'damage control' experts. The same thing happened some months ago when Microsoft announced an even bigger round of layoffs. Microsoft is trying to blame it all on Nokia, which is actually a victim of Microsoft, not an inherited liability. Nokia was doing a lot better before Elop (the Microsoft mole) stepped into the scene and gave Nokia to Microsoft as a gift, in exchange for a massive bonus that he was assured by Microsoft and later received from Microsoft (he has been set free again, potentially to find his next victims, Nokia not being his first).
“Actually, Nokia was starting to do pretty well with Linux (MeeGo) and was exploring Android, which now dominates the market with over 80% market share (i.e. about 2 orders of magnitude better than Windows).”The layoffs are explained a lot better by this Nokia guru, who foresaw a lot of what is happening right now. “Microsoft has now done THREE rounds of layoffs in less than 12 months,” he wrote, “firing 80% of the people it bought” (and many who are not from Nokia at all, possibly as many as 10,000 if not more, excepting temporary workers).
Watch how AOL rewrites the history of Nokia. This is “revisionism on ‘burning platform’,” as iophk put it in an E-mail to us. Some Microsoft-affiliated sites did the same thing, using euphemisms such as “Writedown” (euphemism of convenience for shutdown with layoffs) or “Misadventures” (again, for shutdown with layoffs).
“History tells us that Nokia did not defeat the odds,” wrote one person. “But inside the last five years are a number of lessons that the modern smartphone entrepreneur should think about.”
Actually, Nokia was starting to do pretty well with Linux (MeeGo) and was exploring Android, which now dominates the market with over 80% market share (i.e. about 2 orders of magnitude better than Windows). To say that Nokia was a lost cause and that it had to “defeat the odds” is to totally distract from Microsoft’s destruction of Nokia. Then again, Microsoft and its copywriters are always skilled at rewriting history in Microsoft’s favour. In the media we might even find Microsoft portrayed as the poor victim (e.g. of Nokia’s demise) rather than the predator that has had countless victims. Today’s articles about Netscape’s history are unbelievably watered down; some deleted Netscape from the history of Web browsers altogether. █
“Microsoft is, I think, fundamentally an evil company.”
–Former Netscape Chairman James H. Clark
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, GNU/Linux, Microsoft, Windows at 1:27 pm by Dr. Roy Schestowitz

Summary: Propaganda of assimilation, or trying to make Windows look comparable/on par with GNU/Linux cost and freedom, is the latest propaganda pattern
AS Microsoft so desperately combats the zero-cost advantage of GNU/Linux it uses not facts but fiction. We have grown accustomed to seeing advertising pieces like this one (journalists as Microsoft couriers or copywriters), pretending that Windows is “free” and that it may become “open source” because of some blurb from three months ago. “A per this Wired article,” wrote this author, “open sourcing is no longer optional, even for Apple. Even for Microsoft. Even for Windows.” Actually, all of these are proprietary, so evidence does not support the argument. Nice try though…
“They are blurring the distinction between “open” and “closed” or between “free” and “proprietary”.”Wired has been quite notable in the "googlebombing" of "Microsoft open source" or "Windows open source". It has been quite an effective propaganda campaign that culminated over the past year and we see more of it in light of this proprietary software release that is heralded with headlines such as “Microsoft’s Power BI is coming July 24th, adds a bit of open source and Android seasoning” and “Microsoft Says Power BI Will Come Out Of Preview On July 24, Open Sources Visualization Stack”. This is not Open Source at all, but Microsoft-friendly sites are openwashing Microsoft’s proprietary software. Sometimes even Linux sites fall for it as it’s not helping when Microsoft’s propaganda channel (Channel 9) is openwashing proprietary software such as Visual Studio. This example from Channel 9 is again fitting a pattern that we first noted one week ago. This openwashing ‘thing’ is very much ‘in’. The Microsoft-controlled Channel 9 increasingly chimes in to amplify the noise.
“Embrace, extend, extinguish” moves are now being used to make Apache software tied to Windows-powered and Microsoft-controlled servers (Azure). Isn’t that great? They are blurring the distinction between “open” and “closed” or between “free” and “proprietary”.
“Hadoop,” says ZDNet, “started out using an open source implementation of Google’s MapReduce as its exclusive processing engine.” Well, now Microsoft wants it all for itself, to run under Windows (proprietary and pricey) as well as under Microsoft’s control (with rental payments for hosting).
Microsoft is acting like a bandit, operating from the inside when it comes to Android as well (see “Windows 10 to allow easy porting of apps from Android and iOS platforms”), not to mention the underlying kenrel, Linux. Watch this new example of bad code that Microsoft has put inside Linux to promote proprietary software like Hyper-V, which runs on Windows (hyper-visor with NSA back doors implied) to control GNU/Linux guests. █
“I would love to see all open source innovation happen on top of Windows.”
–Steve Ballmer, Microsoft CEO
Permalink
 Send this to a friend
Send this to a friend
Posted in Hardware, Microsoft, Security at 12:54 pm by Dr. Roy Schestowitz
Summary: The insecurity and abundant complexity/extensibility of UEFI is already exploited by crackers who are serving corrupt regimes and international empires
TECHRIGHTS has spent many years writing about dangers of Microsoft back doors and about 3 years writing about UEFI which, according to various citations we gathered, enables governments to remotely brick (at hardware level) computers at any foreign country, in bulk! This is a massive national security threat and Germany was notable in reacting to it (forbidding the practice). Among our posts which cover this:
Today we learn that UEFI firmware updates spread to the most widely used GNU/Linux desktop distribution and yesterday we learned that “HackingTeam has code for UEFI module for BIOS persistency of RCS 9 agent (i.e. survives even HD replace)…”
Rik Ferguso wrote this with link to the PowerPoint presentation, pointing to leaked E-mails via Wikileaks. The push back against UEFI ought to be empowered by such revelations, perhaps in the same way that these leaks now threaten to kill Adobe Flash for good. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 12:11 pm by Dr. Roy Schestowitz

Contents
-
-
Desktop
-
Canonical’s Ubuntu can be run on just about any x86 machine with a recent and compatible BIOS so who buys pre-loaded machines? HP clearly thinks there is a market for such a thing and recently announced three 15.6-inch laptops running the operating system, competition for a similar range of systems made by Lenovo aimed at the same market.
-
OS X is a solid operating system for those who enjoy Apple’s vision of the ideal desktop. It offers access to pro-level applications that many industries rely on. Yet it isn’t always the most practical operating system for the casual end user. In fact, in some cases, it’s completely overkill.
In this article, I’ll explore why I believe Linux is a more practical solution than OS X, if local techs would simply bother to support it. This article isn’t about which platform is “better.” Instead, it’s a matter of which platform is more practical.
-
-
Server
-
The use of Docker as an application container management system has become standard practice for developers and systems engineers in the space of just two years. Some like to say that haven’t seen such a technological advance since OpenSSH. Docker is now a major player and is widely used in cloud systems architectures. But more than just that: Docker knows how to win developers over.
Let’s take a look at an overview of what we’ve done with Docker, as well as an assessment of the future and of the competition that is appearing on the horizon.
-
…485 out of 500 systems were using Linux…
-
At No. 2 was Titan, a Cray XK7 system installed at the Department of Energy’s (DOE) Oak Ridge National Laboratory. Titan, the top system in the United States and one of the most energy-efficient systems on the list, achieved 17.59 petaflop/s on the Linpack benchmark.
-
Still, according to Top500, Chinese companies’ influence in the supercomputing industry is rising thanks to Lenovo, which has three systems in the top 500 under its own brand and another 20 jointly with IBM.
-
The challenge for these HPC players is that workloads can be delivered via pay-as-you go cloud models. It’s not clear what types of enterprises will rent HPC vs. build systems.
-
VMware introduces Project Photon: a lightweight Linux operating system for cloud-native apps. Star Trek and Einstein references aside, VMware’s Project Photon appears to be more than a particle or a wave.
-
Kernel Space
-
Dave Jones, a former Linux kernel engineer at Red Hat, is effectively suspending the future public development of his Trinity system call fuzzer.
Dave had been developing Trinity for the past several years as a Linux system call fuzzer with the original intention of finding Linux kernel bugs — oopses, etc, not particularly security bugs. However, he has grown frustrated by many people using Trinity without contributing back to the project. Additionally, there’s many using Trinity for trying to find security issues and not submitting their Trinity changes back upstream.
-
In part due to the recent news item about an NSA researcher looking at KDBUS and then having written a mailing list parser for finding how many Intel developers work on their open-source driver, for curiosity sake, here’s a look at the companies most active on the systemd mailing list.
-
Unless you have been living under a rock, or worse – you don’t care much about how Linux works, you must have heard of systemd, the (relatively) new init system replacing the old and outdated SysV init recently adopted by most major Linux distros.
-
The Linux 4.2 kernel that’s currently under development ships many new features, but as I’ve been writing about for a while and tweeting, the 4.2 Git code hasn’t been booting on many systems in my test lab for over one week. Various Phoronix readers have also been able to reproduce these different kernel panics that happen almost immediately into the boot process. Here’s the root problem affecting Linux 4.2 on my daily Linux benchmarking systems…
-
-
As you may know, Kernel 4.0.8 has bee recently released, but Kernel 4.0 will reach end of line soon.
Greg Kroah-Hartman has announced that Kernel 4.0.9 (which will be released next week), will be the last release from the series, the users being advised to upgrade to Kernel 4.1:
“Note, there will only be one more 4.0-stable release, please start moving to 4.1-stable at this point in time, you have been warned.”
-
The Linux Foundation is seeing increasing interest among early career IT professionals for basic Linux system administration (SysAdmin) skills as an entry point for a lucrative career.
-
I wrote earlier this month about kernel panics when trying to test the i7-5775C Broadwell H socketed processor on Linux. I ended up finding a workaround to improve the stability and that was by enabling the “CPU OC Fixed Mode” from the UEFI/BIOS on this particular Z97 motherboard, after my original Z97 test motherboard wouldn’t even boot up with the i7-5775C when equipped with the latest, Broadwell-supporting BIOS. Since then I bought a third motherboard to see how the situation plays out.
-
Benchmarks
-
If you are in the market for a new solid-state drive but aren’t too concerned about speed or storage capacity but just need something very affordable to get the job done, the ADATA SP600 is available in a 64GB model for less than $40 USD.
-
Applications
-
Often when doing performance analysis or debugging, it boils down to stare at long text trace files with the less text viewer. Yes you can do a lot of analysis with custom scripts, but at some point it’s usually needed to also look at the raw data.
The first annoyance in less when opening a large file is the time it takes to count lines (less counts lines at the beginning to show you the current position as a percentage). The line counting has the easy workaround of hitting Ctrl-C or using less -n to disable percentage. But it would be still better if that wasn’t needed.
Nicolai Haenle speeded the process by about 20x in his less repository.
-
-
A new version of RcppGSL arrived on CRAN a couple of days ago. This package provides an interface from R to the GNU GSL using our Rcpp package.
-
-
-
In the past I have reviewed QMPlay2, a video player using ffmpeg and the Qt 5 toolkit, which gets updated often and ships with some great features. The latest version is 15.07.12, released yesterday, and brings several fixes over the previous release.
-
Proprietary
-
-
-
Vivaldi, a web browser built by one of the Opera founders and his team, has been upgraded once more, and the developers seem to be preparing to exit Technical Preview 3 and enter the next stage, Technical Preview 4.
-
-
Instructionals/Technical
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Elad kindly told me that if I install the GStreamer codecs, and disable Flash, it should work. I didn’t have those codecs on my not-for-watching-TV machine, so I set to it.
-
Games
-
Valve has released a sleuth of updates for the Steam client, and the developers are preparing for another major stable update. The Linux platform didn’t get any special attention, but many of the improvements made apply to all the supported OSes.
-
Alien: Isolation is a first-person survival game developed by Creative Assembly, a studio mostly known for its Total War series. From the looks of it, a Linux version might just be in the works.
-
Guild Software has published details about a new double update for their popular Vendetta Online science-fiction massively multiplayer online role-playing game (MMORPG) for Microsoft Windows, GNU/Linux, Mac OS X, Android, and iOS operating systems.
-
Volgarr the Viking is a highly rated game that mixes action and platforming, and it’s now on GOG for Linux.
-
It seems a developer of America’s Army: Proving Grounds sent an email to Phoronix to mention they are looking to port it to Linux.
Take this with a grain of salt since it’s Phoronix, but it has been on Linux before and dropped, so it’s not out of the realm of possibility.
-
Alien: Isolation is a terrific horror game, and a franchise I get extremely excited for. Alien: Isolation is also one of the few “Alien” based games that wasn’t a let down.
-
Today I’d like to cover a game I didn’t know existed only a few days back, a game out of a genre that is heavily under represented on our beloved platform, a(n old-school) sandbox MMORPG named Albion Online!
-
A developer working on ‘X Rebirth’ responded to a user claiming they are wasting their time on the Linux version, and it’s a great response.
-
Legend Of Grimrock has sadly been unplayable for anyone on Linux with an Nvidia 900 series chip (like the 970), until now. The developers just put up a Linux beta, and it works.
-
-
Heads up GOG fans, they just recently released some more great Linux games to build up your DRM free collections. It’s really great to see them getting a bit quicker at it now, and building up their Linux catalogue is a must.
-
Postal 2′s Linux version has been lagging behind the Windows build for a long time, but no more. RunningWithScissors took the port in-house, and it’s now updated. Originally the port was maintained by Ryan “Icculus” Gordon, but he was too busy.
-
While I’m still working on my full Intel Core i7 5775C Linux review of this socketed Broadwell processor with Iris Pro Graphics 6200, and still working through some strange issues, I do have some Steam Linux gaming figures to share tonight for those interested in how Intel’s latest-generation Iris Graphics are performing with the open-source Mesa driver stack.
-
Desktop Environments/WMs
-
-
K Desktop Environment/KDE SC/Qt
-
Neophytos Kolokotronis from the Chakra GNU/Linux development team has posted news about the latest updates introduced in the current stable release of the rolling-release operating system.
-
-
Calligra is an integrated suite of applications for office, creative, and management needs. A fresh update has been released for the application, and it looks like the developers still have plans for this branch.
-
-
-
GNOME Desktop/GTK
-
In Linuxville today Eric Griffith demonstrated why GNOME is better than KDE and Attila Orosz explained what you need to know about systemd. Reviews of Semplice 7, Mint 17.2, and Mangaka caught my eye and Matt Hartley compared Linux to OS X saying, “I believe Linux is a more practical solution than OS X.”
-
It seemed to take forever. Endless PR reviews, improvements, code refactoring and hours spent working on editor, removing deprecated icons or search.
[...]
Without some exhausting descriptions, take a look at the current additions to the Getting Things GNOME!
-
This year’s GNOME Foundation Annual General Meeting will be held on the 8th of August at 15:45 (CEST). As with previous years, it is being held at GUADEC [1]. This year’s conference is at the Folkets Hus [2] in Gothenburg, Sweden.
-
-
The GNOME Foundation Board can often be a bit opaque. Generally it works in the background, and while you can get a sense of some of its activities through the minutes, it is easy to forget that the board is out there doing its thing.
-
-
Reviews
-
Originally, I wanted this post to be a comparison test. Specifically, I wanted to compare SolydK to the KDE edition of Manjaro Linux. However, it turns out that Manjaro Linux uses KDE 5 (I know this is a deliberate abuse of notation), while SolydK uses KDE 4. That doesn’t sound like a fair comparison, so I’m splitting these into separate reviews.
-
If you prefer to tweak your Linux settings to the max, you will find Mangaka and its Pantheon desktop a bit too limiting. However, if you want an unusually gorgeous background and a very simple Linux OS that has little or no learning curve, the Linux Mangaka distro can be a real joy to use.
-
It has been a few years since I last reviewed Semplice Linux. The Debian-based distribution has changed in recent years and some people asked if I would revisit this project. According to the distribution’s website, “Semplice is a GNU/Linux distribution based on Debian Unstable (Sid) with the goal to provide a simple, fast, lightweight and cool environment.” In itself, this description is not unusual. What sets Semplice 7 apart is the project’s unique desktop environment, called “vera”. The vera desktop is briefly talked about in the project’s release notes. The new desktop environment is based on GTK3 libraries (the same libraries which act as the foundation for the GNOME and Cinnamon desktops). The vera desktop ships with a new power manager, a screen shot utility and its own control centre panel. The release notes also mention vera ships with an interactive tutorial to help new users get acquainted with the young interface.
-
New Releases
-
On July 12, 2015, the developers of the nOS Linux kernel-based operating system announced that they would no longer be involved in the development process of the rolling-release distribution.
-
A new day, a new Solus update. The developers are keeping themselves busy, and they are working to improve the operating system constantly. The latest might not look like a major upgrade, but the devs have managed to refine the boot time considerably.
-
On July 13, the Manjaro Linux development team, through Philip Müller, had the great pleasure of announcing the immediate availability of the fourth update for the stable Manjaro Linux 0.8.13 distribution.
-
On July 13, François Dupoux, leader of the SystemRescueCd project, has informed users about the immediate availability for download of another maintenance release of his Live CD Linux distribution.
According to the brief changelog, which we’ve attached at the end of the blog post, the SystemRescueCd 4.5.4 release brings updates to both the standard and alternative kernels, as well as new versions of some of the most essential core components, which include e2fsprogs, xfsprogs, and btrfs-progs.
-
Screenshots/Screencasts
-
A new version of Zorin OS has been released over the weekend, and it comes with a ton of new stuff, not to mention an updated desktop design. We now take a closer look at this distro to see what’s so special about it.
-
PCLinuxOS/Mageia/Mandriva Family
-
-
I had only recently reviewed Mageia5, when I noticed an announcement for OpenMandriva 2014.2. So I was mistaken that Mageia was what was left of Mandrake/Mandriva. OpenMandriva is another fork that continues.
I have tested only from the live media. I did not do a full install to a hard drive. So this is a more limited review than I gave for Mageia5.
-
Ballnux/SUSE
-
-
The move, like so many of its other announcements lately, comes as a response to long-time rival Red Hat Inc, which launched a program to court manufacturers dealing in processors based on designs from the British semiconductor powerhouse all the way back last year. Both vendors hope to seize the rise of software-defined environments made up of small, low-cost servers that benefit from the power efficiency of ARM chips.
-
-
-
Red Hat Family
-
-
Patricia Bogoevici started off as a software developer and has graduated to consulting on Agile and DevOps projects. At the recent Red Hat Summit, Bogoevici and her co-presenter Josh Minthorne presented a talk about using Agile and DevOps methodology to achieve faster production deployment.
-
-
-
Open source solutions vendor Red Hat has announced the global launch of the Red Hat Certified Cloud and Service Provider programme, replacing Red Hat’s existing Certified Cloud Provider programme.
-
Speakers from Red Hat, Inc., SAP SE, and Intel discussed their collaborations and innovations as part of the open-source community during a General Session at the 2015 Red Hat Summit. In keeping with the open spirit, the session started with highlights from the Enable Project, which designs and distributes open-source, 3D-printed prosthetics at no cost to individuals.
[...]
After sharing an excerpt from “Open Source Stories,” Paul Cormier, president of Products and Technologies at Red Hat, took the stage to celebrate the victory of open source over the past few years. He cited the Mohandas “Mahatma” Gandhi quote: “First they ignore you. Then they laugh at you. Then they fight you. Then you win.” He went on to say, “I’m here to tell you today that Linux and the open-source community have won. And they’ve completed the Gandhi quote here. They can now check the last box.”
-
-
-
-
Shares of Red Hat, Inc. (NYSE:RHT) rose by 2.16% in the past week and 0.45% for the last 4 weeks. In the past week, the shares has outperformed the S&P 500 by 2.17% and the outperformance increases to 1.29% for the last 4 weeks.
-
-
Red Hat is replacing its existing cloud provider programme with a revamped one it claims will help provide better support for distributors, managed service providers and systems integrators. The company said the move was in response to what it sees as a broadening ecosystem of partnerships in cloud.
-
Fedora
-
I like very much the new Virtual Box and Fedora also, because it’s fast (~ 1 min) and I don’t need to start another hardware to test my linux stuff.
-
I am happy to announce the release of F22-20150629 update lives.
-
The Steam repository has received some love; changes to the Steam package will also be pushed in RPMFusion after a bit of feedback.
-
-
Bit late blogging about this, but roshi sent out the Fedora 23 Call for Test Days at the end of June.
-
The developers of the Linux AIO project have been glad to inform us about the immediate availability for download of new builds of their Linux AIO Fedora project, which is now based on the latest stable Fedora Linux release.
-
Debian Family
-
The Debian developers have decided to make GCC 5 the default compiler in Debian Unstable, but Debian 9.0 Stretch will be most likely using GCC 6 as default. Also, Ubuntu 15.10 Wily Werewolf will adopt GCC 5 in a short time.
-
Derivatives
-
Canonical/Ubuntu
-
-
A new set of OpenSSL vulnerabilities have been identified, and all Linux distributions have been quick to implement patches in order to close these issues. As it turns out, none of the supported Ubuntu OSes has been affected, and no patch has been released.
-
Dekko is a native IMAP email client for Ubuntu Touch and is coming along just fine. From the looks of it, developers are not only working to make it work on the phone but to also scale and properly function on the desktop as well.
-
-
The Ubuntu Touch platform is getting some major improvements in the coming months, and it looks like the SMS function is finally getting the attention it deserves.
-
-
-
Another week has passed, and Canonical’s David Planella has sent in his regular report that informs us about the latest work done by the Ubuntu Community Team.
-
Ubuntu MATE 15.10 has a few windows managers, and one of those is Compiz. From the looks it, the developers of the distro are making some changes so that the entire Compiz experience is more enjoyable and more stable.
-
Grooveshark is no more, and the service was also removed from Ubuntu Touch, but the developers are working to replace that with something else, and it looks like something is in the works.
-
-
-
-
Phones
-
Tizen
-
Samsung Electronics usually has their big reveal of their next big Smartphone (Note x) in September, at the IFA Event in Berlin since 2011, but it looks like Samsung are looking at moving it to mid-August, according to a person familiar with the matter. The reason behind the move is that they wanted a bit more room between their announcement and Apple Inc unveiling of the next iPhone.
-
Android
-
-
-
Google is launching brand new watch-to-watch communication features for Android Wear that are not unlike those on Apple’s Watch, according to Phandroid. Users will reportedly be able to send each other doodles, photos, stickers, messages and more using a feature called “Together.” That’s pretty similar to the Apple Watch’s Digital Touch, which allows users to relay tap patterns, drawings and even heartbeats to each other. Oddly, Android Wear users who want to share items may need to use the same the same watchface, as the feature isn’t system-wide. However, Phandroid admitted that its information on that aspect “is quite old.”
-
Apple Watch users can send each other doodles and emoji, but those with Android Wear smartwatches haven’t had the same luxury.
-
-
Google is planning to release a mysterious new watch-to-watch messaging service during its next Android Wear update, according to tech website Phandroid.
-
Since last fall, Pebble smartwatch users have been able to count their steps and track their sleep, but they’re on their own in deciding which third-party fitness app to use.
-
-
-
-
-
Blackberry and Android usually don’t go together in one sentence, but that’s about to change. The shrieks and awe built around the prospect of a Blackberry smartphone running Android is in full force this week after the revelation that BlackBerry has purchased two Android-centric domain names: AndroidSecured.com and AndroidSecured.net.
-
A new “security app” for Android claims apps like the ASTRO File Manager are vulnerable. Jack Wallen challenges this claim.
-
Last week Android M Developer Preview 2 arrived on scene. That very day I released our first “Diving into M” post for the second preview, which highlighted the changes to the launcher and the ability to now edit the status bar with the Tuner UI tool in the developer options.
-
-
If you dabbled with Google Photos when it was launched last month but decided it wasn’t for you, make sure you also turn photo backup off in your Android phone’s Google Settings menu, or else you’ll continue uploading new pictures to the service. Nashville Business Journal writer David A. Arnott discovered the quirk when hundreds of family photos appeared on Google Photos, even when he’d deleted the pictures and uninstalled the app itself from his phone.
-
-
Google has launched a new Ethernet adapter for it’s Chromecast device. The aim of this accessory is to let you connect your Chromecast directly to your router to create a fast and reliable connection for your Chromecast. The Ethernet adapter has a central hub that plugs into the wall, this will provide power to the Chromecast via a USB cable.
-
Wait — wait just one second. As a parent, I take umbrage with Pichai’s absolutist response. Especially since the Android OS he’s in charge of can be found on 80 percent of all smartphones sold worldwide.
-
Unlike last year’s budget Android One series, the upcoming Google phone is said to come packed with upgraded hardware and is expected to retail under mid-range category, thus filling the gap between entry-level and the top-end Nexus series.
-
In May, Google revealed a small-footprint operating system called Brillo, a version of Android for Internet of Things applications that will arrive in a developer preview in the third quarter. It will work with a cross-platform communications framework called Weave that will arrive in Q4.
-
Go is opinionated, and influenced heavily by Google’s use case, but Minio doesn’t mind inheriting Google’s way of building infrastructure software. Go is not as mature as Java yet, and it still has some rough edges when it comes to tooling and garbage collection; however, Go is ready for developing production-grade software. The next release of Go 1.5 implements efficient concurrent garbage collection and address the tooling issues.
-
-
-
-
News from last month, but important enough to revisit — Cloud Foundry Foundation has appointed Stormy Peters as vice president of technical evangelism.
-
Events
-
Web Browsers
-
Mozilla
-
As you may know, Thunderbird is an open-source e-mail client and chat client developed by Mozilla. Among others, it has support for email addresses, newsgroup, news feed and chat (XMPP, IRC, Twitter) Client, managing multiple accounts. Also, it has support for different themes and its power can be extended by plugins.
-
SaaS/Big Data
-
Mirantis have announced the launch of Mirantis Unlocked Appliances, a programme to allow customers to buy flexible turnkey OpenStack appliances. The appliances are certified and delivered by ‘Certified Rack Partners’, for now this list is limited to a Redmond based company called Redapt.
-
-
-
Oracle/Java/LibreOffice
-
Business
-
BSD
-
-
We are pleased to announce the availability GhostBSD 10.1 BETA2 MATE & XFCE which is available on SourceForge for the amd64 and i386 architectures.
Before going further I will like to say a special thanks Ovidiu who recently join back the project and Andrea who join the project, they have help to make GhostBSD better, add up new feature and fixed issue.
-
-
Openness/Sharing
-
Look at distributed systems, decentralized computing, open source, and lean principles. With these and other technical initiatives, we’ve pushed boundaries and improved our applications, our networks, our companies, and our lives.
-
In late June, Berkeley held a workshop to get to know what research has been underway on RISC-V. RISC-V is an open instruction set architecture (ISA) originally developed at Berkeley and based on established reduced instruction set computing principles. It is a minimal, modular ISA ready for hardware implementation, freely available to both academia and industry.
-
Open Data
-
-
The government needs to open up far more of its information and move to a culture of making decisions based on data not targets, Cabinet Office minister Matthew Hancock MP has said.
During a speech in London today, Hancock (pictured) praised progress since 2010 on opening up public sector data, with 20,000 datasets now published on the government’s portal data.gov.uk.
-
Programming
-
Facebook developers today announced the release of HHVM 3.8.0, their interpreter for PHP and their own Hack programming language.
-
-
Bruce Eckel is the author of Thinking in Java, Thinking in C++, and a number of other books on computer programming. He’s been in the computer industry for 30 years and periodically gets frustrated and tries to quit—then something like Scala comes along and offers hope and sucks him back in. He’s given hundreds of presentations around the world, and enjoys putting on alternative conferences and events like The Java Posse Roundup.
-
Code version control using Git or SVN seems like too trivial to some small project, but today’s experience taught me a lesson.
-
Standards/Consortia
-
Once upon a time, if you asked a standards setting organization (SSO) what its intellectual property policy rights (IPR) policy was, you’d get a simple answer: “We own the copyright in everything we produce.” Today, if an SSO that develops standards in the technology arena were to give an answer like that, it would find that its members were heading for the exits.
What’s changed, of course, is that information technology has infiltrated almost every aspect of our existence, and that includes standards development as well. For example, an SSO that used to limit its attention to setting construction standards relating to heating and ventilation installations will now also host working groups developing standards for sophisticated building control systems.
-
The Software Freedom Conservancy’s Bradley Kuhn is probably best known for his work in enforcing the GNU General Public License (GPL). Enforcement-by-litigation might get the headlines, but Kuhn treats the courts as a last resort.
-
Choudhary is a technology lawyer and an online civil liberties activist. She is the founding executive director of SFLC.in, a pro-bono legal services organisation based in New Delhi that focuses on free speech and expression, privacy, software patents, network neutrality, internet governance and access to knowledge.
-
The list goes on; it’s seemingly infinite. Such search terms offer insight into both our fears (“how bad is caffeine during pregnancy”) and desires (“bronies”). And thanks to thousands of poorly paid freelance writers looking to pick up some extra cash or toiling for wages, the results we’re served in these vulnerable moments are often hastily scribbled, poorly written, ungrammatical filler text. This old world relic represents a time when getting to the top of Google rankings wasn’t dependent on the quality of information you supplied but how many people linked to your site.
This kind of text—the equivalent of fast food or hangover-friendly TV—is the preserve of content mills, an Internet subculture where for-hire workers are tasked with writing vast amounts of online copy for a pittance. Today, when more media outlets and self-publishing tools exist than ever before, such word factories somehow continue to exist.
-
Science
-
A new expedition to the craters in Yamal, in northern Russia, shows how they have rapidly altered since they were first noticed last year, but also indicates the possibility that not all the craters were formed in identical ways. The holes – first noticed last year – intrigued and perplexed scientists from around the world, initially provoking a number of explanations as to their cause, the most outlandish of which was that they were caused by stray missiles or even aliens from outer space.
-
A pitcher plant species in Borneo attracts bat inhabitants by reflecting sonar signals from the flying mammals, advertising a cozy roost, and getting nitrogen-rich guano in return.
-
Security
-
-
My cert expired after a year because that seems to be the thing to do. I imagine there’s some nebulous threat model where somebody stole my server key and has been impersonating me for the past six months, but now they can’t. Although, if they stole the old key, they can probably steal the new key. I suppose we do this because revocation doesn’t work, but a six month half life is a long time to sit exposed.
-
-
An elite cyberattack group that was employed by governments and agencies was probably hacked by another country, it has said — and the attack has led to its powerful hacking tools being released into the wild.
Hacking Team was hacked last week, revealing private emails and documents as well as insights into its tools. The leaked documents showed many of the vulnerabilities that were being used by the group — such as a bug in Adobe Flash that can be exploited to get complete control of a computer — which has meant that anyone can counteract them as well as use them for their own ends.
-
-
-
After yesterday’s news that Facebook’s new chief security officer wants to set a date to kill Flash once and for all, the latest version Mozilla’s Firefox browser now blocks Adobe’s vulnerability-riddled software as standard. Mark Schmidt, the head of the Firefox support team at Mozilla, tweeted that all versions of Flash Player are blocked in the browser as of its latest update, accompanying the news with an image showing a raised fist and the phrase “Occupy Flash.”
-
Yesterday the usual tech news outlets were buzzing over an accidental tweet which the media incorrectly interpreted as Mozilla was ditching flash (Blame The Verge for the chain reaction of copied news articles) entirely as a policy. While that is not the case, I was just as excited as many at the faux-news. This got me thinking: what would it really take for the web to kill Adobe Flash? Could Mozilla really make such a move and kill Flash on its own if it wanted to?
-
Last week I released No Flash 0.5, my addon for Firefox to fix the legacy of video embedding done with Flash. If you are like me and don’t have Flash installed, sometime you encounter embedded video that don’t work. No Flash will fix some by replacing the Flash object with a HTML5 video. This is done using the proper video embedding for HTML5.
-
This message comes after it was revealed that the recently hacked “Hacking Team” was using Flash zero-day vulnerabilities to hack journalists, activists, governments and more. Alex Stamos, like other security experts, must have also gotten tired of hearing about so many security vulnerabilities that Flash has had during its entire lifetime.
-
Now more than ever, leaving Adobe Flash Player on your system is looking like a dubious proposition.
While Flash has long been a popular vector for malware, last week’s security breach of surveillance software firm Hacking Team underscored just how vulnerable Flash can be. Hacking Team was relying on at least three unpatched Flash exploits, which cybercriminals immediately adapted for their own nefarious uses. Adobe is scrambling to patch the exploits, but at least one remains unfixed as of this writing.
-
-
Dubbed the Census Project the initiative has been finding an embarrassing number of flaws in common core Linux system utilities that have network access. Some of them have nowhere near enough development relative to their importance.
-
Defence/Police/Secrecy/Aggression
-
In response to the multi-state military exercise organized by the federal government, a group of very concerned Texans have organized what they’re calling “Counter Jade Helm,” in which “citizens will participate in an unofficial fashion to practice counter-insurgency, organizational and intelligence gathering and reporting skills.”
Operation Jade Helm begins on July 15th, but as the media is barred from covering the exercise, citizen surveillance is the only option that people like retired firefighter Eric Johnson have to assuage their concerns about what the SEALs, Green Berets, and Air Force Special Ops are actually up to.
-
Environment/Energy/Wildlife
-
A newly unearthed missive from Lenny Bernstein, a climate expert with the oil firm for 30 years, shows concerns over high presence of carbon dioxide in enormous gas field in south-east Asia factored into decision not to tap it
-
It’ll take awhile, but according to a new paper published in the journal Science, the planet’s on track to see sea levels rise by at least 20 feet — and that’s only if we manage to limit global warming to 2 degrees Celsius, a target many believe we’re already doomed to surpass.
-
A hulking rig is engulfed in flame. It’s sinking, spitting out a giant plume of smoke in the process. A firing squad of rescue ships are dousing it with ocean spray. Eleven men are already dead.
-
Finance
-
Yanis Varoufakis: I’m feeling on top of the world – I no longer have to live through this hectic timetable, which was absolutely inhuman, just unbelievable. I was on 2 hours sleep every day for five months. … I’m also relieved I don’t have to sustain any longer this incredible pressure to negotiate for a position I find difficult to defend, even if I managed to force the other side to acquiesce, if you know what I mean.
-
-
PR/AstroTurf/Lobbying
-
Censorship
-
The Authors Guild has sent a letter to the U.S. Congress asking lawmakers to strengthen current copyright law. To stop dozens of millions in claimed losses, the authors want to increase liability for Internet service providers and make it mandatory for the companies to monitor and filter pirated content.
-
A 39-year-old Australian woman has been arrested and jailed in Abu Dhabi in the United Arab Emirates after she was found guilty of “writing bad words on social media”.
West Australian Jodi Magi remains in jail and it’s not known how long she will be held for.
Middle East correspondent Sophie McNeill reports.
SOPHIE MCNEIL: In February, 39-year-old Jodi Magi took a photo of a car in her apartment block in Abu Dhabi that was parked across two disabled parking spaces without any disability stickers.
-
Almost three-quarters of Sky’s internet customers have opted to block online pornographic websites after being forced to choose.
The company announced an automatic block on harmful sites six months ago in a bid to prevent children from stumbling across hardcore images and videos.
-
Powers to require online surveillance, remove content, block foreign web sites and shut down parts of the network are contained in the draft of a new Internet security law recently published by the Chinese government. Although these approaches have all been used in the past, their legal basis has sometimes been unclear. If approved, the new law will make it much easier for the Chinese authorities to force compliance from Internet service providers, which will have major knock-on effects for users in the country.
-
Privacy
-
Earlier this month, several news outlets reported on a powerful tool in the fight between those seeking anonymity online, versus those who push for surveillance and taking it away.
The tool, ProxyHam, is the subject of a recently canceled talk at DEF CON 23 and its creator has been seemingly gagged from speaking about anything related to it. Something’s off, as this doesn’t seem like a typical cancellation.
-
It’s no longer a surprise that the government is reading your emails. What you might not know is that it can readily read most of your email without a warrant.
Any email or social networking message you’ve opened that’s more than six months old can also be accessed by every law enforcement official in government — without needing to get a warrant. That’s because a key provision in a law almost three decades’ old allows this kind of access with a mere subpoena, which doesn’t require a judge.
-
UK Prime Minister David Cameron is pressing ahead with new powers that plan to stop people from sending any form of encrypted messages. Under the rather Orwellian “Draft Communications Data Bill” (nicknamed Snooper’s Charter) the legislation proposed would require ISPs and mobile providers to maintain records of each user’s internet browsing activity (including social media), email correspondence, voice calls, and mobile phone messaging services and store the records for 12 months.
-
In October 2012, then-New York Police Commissioner Ray Kelly announced a new initiative, called “Operation Crew Cut,” which would target gang activity by focusing on so-called street crews. Kelly doubled the size of the anti-gang unit to 300 police officers, assigned to the task of surveilling teenagers on Facebook. Many of these kids are under 18, some as young as 12, and just about all of them are black and brown, from low-income neighborhoods. The officers involved are encouraged to make fake Facebook profiles in order to spy on individuals’ Facebook statuses. The operation often entails reading private Facebook messages between friends and is sometimes coupled with phone and video surveillance. Soon press releases were coming out of the NYPD offices announcing dozens of alleged gang members had been arrested due to the Crew Cut initiative.
-
-
After the Edward Snowden revelations and the rise of deep web marketplaces, more and more people are using the anonymity network Tor to take back their privacy or access hidden sites, sometimes to break the law.
In response to this trend, surveillance tech company Hacking Team let slip last month that they were working on a solution to de-anonymize users of Tor for their customers, which include US law enforcement agencies and authoritarian regimes. After the massive Hacking Team leak last week, details of a work-in-progress system to monitor Tor and other encrypted traffic have emerged.
Called “Project X,” Hacking Team’s method proposes to re-route a target’s internet traffic before it enters the Tor network, so it could be monitored by the company’s clients. This is described in two PowerPoint presentations included in the 400 GB Hacking Team breach.
-
Civil Rights
-
A man has accused British Transport police of being “overzealous” and “ridiculous” after he was arrested for charging his iPhone using a socket on a London Overground train.
Robin Lee, a 45-year-old artist based in Islington, was handcuffed and taken to a British Transport Police station on Caledonian Road after his arrest for “abstracting electricity”.
-
A student who stopped to give money to a homeless person was handcuffed by a police officer who thought they were swapping drugs.
Apprentice George Wilson, from Wallasey, received a £5,000 pay out after police accepted he had been detained unlawfully.
A shocking recording of the incident reveals that when Mr Wilson denied he was behaving in a drunk and disorderly manner, as police had alleged, the officer replies: “That’s not how I’ll write it up pal.”
-
Investigative journalist Nicky Hager is set to make his case against a police raid on his Wellington home.
Mr Hager will appear in the High Court in Wellington today for a judicial review into how police obtained a warrant for, and undertook, the raid on October 2, 2014.
The 10-hour search of Mr Hager’s home was part of the police investigation into the hacking of Whale Oil blogger Cameron Slater’s emails, which were given to Mr Hager by anonymous hacker Rawshark and formed the basis of his book Dirty Politics.
-
-
Over six years, filmmaker Laura Poitras was searched, interrogated and detained more than 50 times at U.S. and foreign airports.
When she asked why, U.S. agencies wouldn’t say.
Now, after receiving no response to her Freedom of Information Act requests for documents pertaining to her systemic targeting, Poitras is suing the U.S. government.
In a complaint filed on Monday afternoon, Poitras demanded that the Department of Justice, the Department of Homeland Security, and the Office of the Director of National Security release any and all documentation pertaining to her tracking, targeting and questioning while traveling between 2006 and 2012.
-
More than a month after being sentenced to spend the rest of his life in prison, convicted Silk Road mastermind Ross Ulbricht is trying to keep his head up and help other inmates out, his mother Lyn said.
-
Intellectual Monopolies
-
Copyrights
-
Mega’s biggest shareholder, Shen Zhao Wu, has left the board of the file storage and encryption firm and transferred his stake to a Beijing-based Chinese national just days after a constitution re-write made it easier to go public, while Auckland businessman William Yan increased his influence over the company after an entity linked to his wife took a small shareholding.
-
The four founders of the piracy website, The Pirate Bay, have been acquitted on charges alleging criminal copyright infringement and abuse of electronic communications in a Belgian court. The court decided that because they sold the website in 2006 that they could not be held accountable for what the site was used for afterwards.
-
Four key Pirate Bay figures have a little something to celebrate this morning. After standing accused of committing criminal copyright infringement and abusing electronic communications, yesterday a Belgian court acquitted Gottfrid Svartholm, Fredrik Neij, Peter Sunde and Carl Lundström.
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
































 Content is available under CC-BY-SA
Content is available under CC-BY-SA