08.13.15
Posted in Microsoft, Vista 10, Windows at 7:00 pm by Dr. Roy Schestowitz
Summary: More people realise that even with configuration to fit one’s preferences, Vista 10 remains an Orwellian piece of spyware
VERY counter-intuitively, Vista 10 should be scary to its users, but not to GNU/Linux users. Vista 10 poses plenty of dangers to people who are using it (i.e. used by it) and it is not gaining market share because a lot of people quickly realise that adopting Vista 10 means becoming a product for Microsoft to sell. Microsoft always brags about ‘sales’/number of useds [sic], but not this time. Vista 10 is demonstrably a huge failure, despite the low initial advertised cost (gratis ‘upgrade’).
Last week we reminded readers that settings in proprietary software from Microsoft are often decorative, meaning that they serve no function other than give users the illusion of control. With proprietary software, especially from Microsoft, the software controls the user. Microsoft has been ignoring user settings (regarding privacy and other critical things such as automatic updates) for at least 14 years. This isn’t a shocking new development as it has been done since Windows XP, if not beforehand as well.
British media made it top news today that Vista 10 “contacts OneDrive, MSN and other services even if a user has activated privacy-protecting options” (i.e. Microsoft ignores these).
“Microsoft has been ignoring user settings (regarding privacy and other critical things such as automatic updates) for at least 14 years.”Almost all the articles are linking to Microsoft Peter (a British Microsoft booster), but some, such as Phil Muncaster, frame Microsoft’s attack on privacy based on the company’s own words. “The offending clause was spotted by eagle-eyed journalists who waded through the new 12,000 word terms of use,” Muncaster wrote and other British journalists, along with US counterparts, focused on Microsoft Peter (some have explained why forced automatic updates that cannot be disabled are a “Dangerous New Direction”).
“Microsoft’s claims that it makes great software are open to dispute,” said this article the other day and The New American, a reasonably high profile site, went with the headline “Windows 10 Is Spyware”. There is a trend here. Vista 10 is quickly becoming synonymous with spyware and there is finally a Wikipedia page titled “Microsoft Spyware”. It’s actually a Wikipedia article on Microsoft Spyware, providing some preliminary examples.
iophk reminded us this morning that “Slashdot used to tag articles ‘vista failure’ for a few weeks.” Having just checked Techrights traffic again, for the past 4 days (since Sunday), Vista 10 market share is up to just 1.1%. Still pathetic given that the ‘upgrade’ is advertised as gratis.
FOSS Force published this article this morning, reminding us that Vista 10 AstroTurfing, like a lot of Microsoft AstroTurfing in general, relies on trying to “create stories that find the positive within the negative” because “a story that simply states that “Windows 10 is great!” might not make the cut as a news story, even with the always lowering standards on what passes as news sites these days.”
“The job for the Mad ad men,” explains Christine, “is to create stories that find the positive within the negative — which they’re doing with great abundance, mainly because Windows never fails to offer a surfeit of negative.” It’s drowning the signal with noise, turning negatives into positives. It’s a classic PR strategy which we wrote about in past years. █
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Lenovo, Microsoft at 6:37 pm by Dr. Roy Schestowitz

Photo courtesy/source: Twitter profile
Summary: Malice from Microsoft is being framed as malice from Lenovo, owing to some shrewd spin from a longtime Microsoft booster
Peter is a brave man. Despite his love for Microsoft, he has been hanging out in our main IRC channel for a number of years. He probably joined after we had criticised many of his articles and pointed out the gross bias, which sometimes got a lot more severe and clearly upset a lot of readers, even employees of companies like Opera. Factual inaccuracies, outright errors, semi-truths, spin etc. are a standard routine.
Today we wish to discuss this article because it helps raise awareness of malicious things that Microsoft has been doing. What Microsoft Peter calls “anti-theft feature” is neither “anti-theft” nor a feature but an antifeature. It is part of Wintel’s attack on general-purpose computers or home PCs, tying these to Microsoft software at the hardware level (like OS signatures to be accepted or rejected at the motherboard level).
Microsoft Peter uses a cleverly-crafted argument of diversion; “Lenovo used Windows anti-theft feature to install persistent crapware” is the headline, but it might as well have said that Microsoft had turned many computers against their users and Lenovo merely borrowed this facility from Microsoft.
“The criticism is going to Lenovo for using this when it should be going to Microsoft for even allowing it.”
–Ryan Farmer
In our IRC channel, Ryan Farmer, a former Microsoft MVP (albeit no longer loyal to them), wrote: “Turns out there’s a Windows 8/10 “feature” that runs Windows programs that OEMs can put in the EFI firmware. But it works in Windows 7 as well because of a Microsoft extension to ACPI that lets the firmware pass Windows executables to Windows, which it executes even if they’re not related to power management. Seems like the last version of Windows that wouldn’t do this was maybe Vista. The criticism is going to Lenovo for using this when it should be going to Microsoft for even allowing it. In theory, it’s there to make it impossible for laptop thieves to remove anti-theft software, but since there’s no limitation on how it can be used…”
This article is debated right now by people without an understanding of the technical details. It’s talked about in some other sites and forums, even corporate media like Time. Microsoft Peter managed to get people angry at Lenovo rather than Microsoft (the culprit). Cory Doctorow fell for it and everyone else is directing the anger only at Lenovo (just take a glimpse at those headlines while they last in Google’s index, there at least two dozen of them at the moment).
We wish to remind readers to properly research before buying a PC without GNU/Linux already installed. Microsoft has been setting up artificial obstacles, culminating in Vista 10 with the latest/newest dual-boot complications, set aside UEFI ‘secure’ boot barriers (Microsoft now allows for no “off” switch to be present). Yesterday, a site specialising in this area reported =”GRUB-Install errors while attempting to dual-boot Windows 10 and Linux distributions” (check out the screenshots). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, Patents at 5:56 pm by Dr. Roy Schestowitz

Summary: Analysis of Cisco’s claims that it is making a new video codec ‘royalty-free’ in an effort to fight trolls (probably MPEG-LA et al.)
Cisco, itself somewhat of a troll these days (reversal of a previous stance and previous actions), is trying very hard to paint itself ‘anti-trolls’ right now (picked by LWN by now), leading to misleading press coverage like “Cisco hands license-busting troll-hammer to THOR”. To quote:
Cisco is sick of the state of patent licensing for video codecs, so has decided to set a royalty-free of its own loose on the world.
The Borg’s problem is twofold: on the one hand, the licensing pools for H.264 fail to represent many of the participants in the industry; on the other, the successor, H.265, can be vastly more expensive.
Is Cisco ever going to stand up to MPEG-LA? Cisco enters a space already populated by Google’s WebM/VP9 and Ogg Theora/Vorbis (here is Monty Montgomery’s initial response to Cisco making its codec free, but not Free software like his own ‘baby’). It would be nice to see Cisco throwing its weight against MPEG-LA, and by extension MPEG-LA backers such as Apple and Microsoft. Some sites frame Cisco’s software as “H.264 and H.265 alternative”. Let’s see how they cope with the patent troll, MPEG-LA. Sooner or later we are bound to find out.
It is no secret that Techrights distrusts Cisco, even for reasons other than patents. Today in the news there are damaging allegations about (and also from) Cisco. Cisco claims that its gear can be hijacked (Cisco’s very own back door must not have helped and instead contributed to it). Perhaps Cisco found out that letting only the “Good Guys” get into everything from Cisco rarely works in practice. Cisco is a back doors industry leader, with public attempt to even standardise the practice and Web pages that boast about it (Cisco may have removed or watered down these pages since the Snowden-provided leaks). Does anyone wish to actually use Cisco products, irrespective of the codecs used, to transmit audio and video inside a private business? Sensitive data is being passed around, making it an attractive target for espionage. Cisco gear is a bug waiting to be remotely accessed (or its communications intercepted) by Cisco’s partners in high places, such as the NSA. Remember that Cisco’s stacks are almost entirely proprietary, no matter how much openwashing the company habitually resorts to. █
Permalink
 Send this to a friend
Send this to a friend
Posted in America, Australia, Europe, Patents at 5:31 pm by Dr. Roy Schestowitz
Summary: The plot to monopolise more of what is public (e.g. public domain, common knowledge) gradually unravels as people secretly (dodging public participation) congregate to centralise power structures, opportunistic predation, costly litigation, and enforcement of demands from corporations (like I.S.D.S.)
IT IS saddening to see that despite some patent progress which is being made in the US, owing for the most to SCOTUS*, other countries/islands/continents regress and essentially derail their own economy. It’s a class war waged between multinational corporations, i.e. plutocrats without borders, and everyone else, irrespective of nationality. It’s a large-scale heist cleverly disguised as harmonisation of national and international laws.
Not too long ago we explained how the software patents debate in New Zealand was being bypassed or worked around in secret. Some vigilant people caught this secretive ploy and alerted the media, calling for action while fighting back against software patents. Now there is a press release and resultant/accompanying media coverage from the local/national media, even ZDNet outside the country [1, 2, 3, 4]. Will this be enough? Well, it’s only the beginning of what could become a very long struggle. New Zealand has already devised the same loophole that Europe is sneakily using in order to allow software patenting, provided it’s tied to some unspecified device.
Speaking of Europe, the Unified Patent Court (UPC) ‘harmonisation’ ploy is well under way as here in Britain, without public consent (no referendum, no polling, not even a Parliamentary debate), the London division of the UPC [is surprisingly] announced”. Yes, the patent parasites (practitioners) just jump the gun and according to this report, “UK Intellectual Property Office has announced the new location of the London section of the Unified Patent Court.”
So UK-IPO basically ignores the standard authorities and procedures, just like the EPO‘s management. One might say that they virtually operate outside the law, much like the Mafia. They know what’s good for them and they don’t bother consulting the public. According to IP Kat, a blog of patent maximalists from London, the Enlarged Board (tackling EPO disputes) finally has something to reveal.
Just like these secret (and now notorious) ‘trade’ deals which we rarely write about (even though more is known about them now), these patent conspiracies (or collusions) serve to just enrich a meta-industry of people who profit from taxation of real practitioners — people whose practice is producing stuff like software and machines. █
_____
* According to Patent Buddy, the SCOTUS ruling in Alice keeps squashing software patents. “New PTO eMod system,” allegedly (no link to the source), “seamlessly generates automated § 101 rejection on every appl’n, saving the PTO millions of $$ a year in exam costs.”
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 4:22 pm by Dr. Roy Schestowitz

Contents
-
We’re looking for someone who is both a great writer and knows their way around a Linux distro, along with the ability to write a bit of code and use a Raspberry Pi. Not only will you be tasked with writing articles for the magazine and website, you’ll also be able to pitch your own features for every part of the magazine that could make it to the cover.
-
Desktop
-
Windows 10 is out, and everyone is talking about it. It’s clear that Microsoft did something right for a change and that the latest version of the OS is better than the previous releases. This is actually a good thing.
-
-
Libreboot support makes the C201 a fairly free-software-friendly device plus that it uses Google’s embedded controller that’s backed by free software. One hairy part about this device is the Broadcom BCM4354 for WiFi and Bluetooth does require a proprietary firmware module in its open-source driver.
-
Chromebooks and Chromeboxes have done very well in terms of sales at Amazon and other retailers. But what about Chrome OS itself? Google has made some changes to it over the years and one redditor is wondering if Chrome OS has become ugly.
-
The $64,000 question is the operating system. The ThinkPad P Series comes with Windows 10, of course, but Ubuntu and Red Hat Enterprise Linux are also available.
-
Kernel Space
-
The Ubuntu Kernel Team is still preparing to land Linux 4.2 within Ubuntu 15.10 “Wily Werewolf” for its release in October.
There are many new features to Linux 4.2 and the Ubuntu Kernel Team has been working to get their packages into shape so it can be incorporated into Ubuntu 15.10.
-
Online retailer and cloud computing provider Alibaba has joined the Linux Foundation as a silver member, and its cloud computing subsidiary, Aliyun, is a new Advisory Board member of the open-source Xen hypervisor, which is hosted at the Linux Foundation.
-
-
-
I spend a lot of my day working on framework software for other programs to use. I enjoy this plumbing, and Red Hat gives me all the time I need to properly design and build these tricky infrastructure-type projects. Sometimes, just one person isn’t enough.
-
Applications
-
-
-
In my discussion on IRC with “bkidwell” (see the Non-Linux FOSS article for more on our talk), we were discussing how we connect to IRC. My main method is to SSH in to my co-located Raspberry Pi in Austria and connect to a screen session I have running that is constantly connected to IRC with Irssi. This works really well for me, and I never miss messages when I’m away. The big problem I have is occasionally I’m away from a laptop, and so I can’t efficiently use the terminal to chat. It might be technically possible to IRC chat via an SSH app on my phone, but it would mean super-tiny text and awkward keyboard shortcuts.
-
The open-source container technology now benefits from technology that can digitally sign and verify application containers.
-
Server and cloud developers love Docker and containers, but they’re also more than a little worried about container security. Now, in its latest release, Docker 1.8, Docker is tackling the problem head on with Docker Content Trust (DCT).
-
-
Instructionals/Technical
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
I’ve started to use Pocket a few months ago to store my backlog of things to read. It’s especially useful as I can use it to read content offline since we still don’t have any Internet access in places such as airplanes or the Paris metro. It’s only 2015 after all.
[...]
Yesterday, I thought about that and decided to start hacking on it. LWN provides a feature called “Subscriber Link” that allows you to share an article with a friend. I managed to use that feature to share the articles with my friend… Pocket!
As doing that every week is tedious, I wrote a small Python program called lwn2pocket that I published on GitHub. Feel free to use it, hack it and send pull requests.
-
-
-
-
-
-
-
-
Games
-
-
-
-
-
-
While the game came out back in May of 2011 on PC, it has since been ported to almost every other platform imaginable, including Playstation 3, Playstation 4, PS Vita, Xbox 360, Xbox One, and finally iOS and Android.
-
-
-
-
Good news VR fans, it seems the HTC Vive plans to have Linux/SteamOS support included for day 1 at release.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
KDE Frameworks 5.13.0 has just been released by the KDE Community, and developers have made a large number of changes and improvements.
-
-
-
-
As retrofitting high DPI support into such a large range of both KDE and third party applications is risky to do without breakage, progress is deliberately slow and gradual in order to do this right.
-
-
It’s actually a little more complicated than that. I started to work on the KF5 port of KSnapshot (EDIT: no, contrary to what Phoronix claims this port is not my work; I simply wanted to fix anything that needed fixing) sometime in early March this year, before I realised that the codebase, while perfectly in order for being a X11-only screenshot taker for KDE (yes, KSnapshot actually has a complete and fairly decent KF5 port in its frameworks branch on KDE Git), was in need of a major overhaul if we were going to get proper Wayland support in.
-
It has been one month exactly, since my previous update. This was due to opening fall semester of my college on mid-July, then went to participate at hackIndia, where we developed Corazon, Corazon-backend and at last conducted Mozilla Marketplace Day.
-
Now you might say we already have KNotifications, that’s right. KNotifications is awesome if you are a KDE application and running in a Plasma setup. Snorenotify aims at providing less features than KNotifications but also at being standalone and being directly integrated in an application.
-
GNOME Desktop/GTK
-
I was lucky enough to get a chance to interview Colin and find out more about his upcoming LinuxCon talk, what he hopes his audience will gain from attending, and his fresh, diverse viewpoint on disability—as well as why accessibility is actually an integral part of the open source community.
[...]
Part of accomplishing this is about having a good design, but it would be silly to have to implement text to speech conversion, alternative controls, screen magnification, etc. in every application you build. Luckily there are accessibility APIs that can facilitate communication between your application and assistive technologies that provide those additional functions. The people working on GNOME created open accessibility APIs (ATK and AT-SPI) to facilitate that communication and to give an open source friendly alternative to the APIs created by Microsoft and Apple. Though you can implement the calls to and from those APIs yourself, QT and GTK+ both implement them with all the widgets they provide, so if you are working within one of those frameworks a lot of work has been done for you.
-
This Saturday the GNOME Project celebrates its 18th birthday, over the years it has gone from being the top dog in desktop environment land to seeing a slump in usage after launching GNOME 3 (although this has somewhat recovered now), its usage share has also not been helped with the two most popular Linux distros, Ubuntu and Linux Mint, shifting to Unity and Cinnamon respectively.
-
This is a great chance to tell the world why you love GNOME, inspire others to give it a try, give back to the community, and just wish GNOME a happy birthday.
-
-
Reviews
-
The antiX distribution is a lightweight operating system based on Debian. The latest release was put together using packages from Debian 8 “Jessie” and ships with SysV init software instead of systemd. The latest release, antiX 15, is available in three editions: Core-libre (233MB), Base (582MB) and Full (686MB). There are 32-bit and 64-bit x86 builds of each edition. The antiX wiki tells us that the Core edition ships with virtually no software pre-selected for us, allowing us to customize the operating system to our needs. The Base edition is for older computers, like Pentium II and Pentium III machines, while the Full edition is for more modern computers and people who want a complete desktop experience. I opted to download antiX’s Full edition.
-
New Releases
-
Kali Linux 2.0 is released on today (August 11, 2014 EST). I downloaded 64-bit full version and installed it on VirtualBox 5.0. The host computer has Intel Celeron(R) CPU N2930 @ 1.83GHz × 4 and 8 GB RAM. I assigned 5 GB RAM to Kali Linux 2.0. It is quite slow for it to run with 5GB RAM on my VirtualBox 5.0. Meanwhile, the sound always mute on every start up even you have set it before.
-
-
-
Kali, formerly known as BackTrack Linux, has long been one of the most popular security focused Linux distributions. Kali Linux is Debian based and now with Kali LInux 2.0 it’s moving to Debian Jessie as a base for a rolling distribution.
-
-
The Alpine Linux project is pleased to announce the immediate availability of version 3.2.3 of its Alpine Linux operating system.
This is a bugfix release of the v3.2 musl based branch. This release is based on the 3.18.20 kernel which has some critical security fixes.
-
Arch Family
-
Manjaro GNOME, a Linux distribution based on Arch Linux and fully compatible with the Arch repositories, has been finally upgraded to version 0.8.13.1 and is now ready for download.
-
Ballnux/SUSE
-
SUSE may not get the headlines, but it’s still a major Linux server power. That’s why the news that SUSE is enabling its customers to use its SUSE Manager in the public cloud via SUSE’s “bring-your-own-subscription” program is a big deal.
-
As a preview of next week’s LinuxCon in Seattle, we asked keynote speaker Michael Miller of SUSE to answer some questions about openness in IT infrastructure and what it means for Linux and SUSE.
For more from Michael Miller, check out his keynote presentation at LinuxCon, “Open Source Code: It’s in our DNA,” in which he will talk about open source, the progress that has been made, and why now is the perfect time to be building the future of open source together.
-
Red Hat Family
-
Red Hat Satellite 6.1 is Red Hat’s systems management solution for managing Red Hat servers and services. It’s not been that long since Red Hat Satellite 6.0 appeared — in September 2014. But, Red Hat’s push into the cloud, DevOps, and containers combined to make the need for an update urgent.
-
-
The CEO of Tesora, whose new round of funding totals $5.8 million, explains where containers will play a role in the future of cloud databases.
Cloud database-as-a-service (DBaaS) vendor Tesora today announced that it has completed a new round of funding, bringing in $5.8 million. The new round included the participation of Red Hat, Rho Canada Ventures, and existing investors General Catalyst and Point Judith Capital. Total funding to date for Tesora now stands at $14.5 million.
-
Coming almost a year after the original product’s launch, Satellite 6.1 will extend the service’s core capabilities to container deployments, which isolates software to maintain performance across different environments and to protect data.
-
Thinking about all the current and future employees who join Red Hat directly out of school is exciting. By starting their careers at Red Hat, they will hopefully avoid some of the corporate frustrations I experienced throughout my 20s. They will understand the power of intentional corporate culture, transparency, and open communication. Their careers will be rooted in a non-traditional understanding of corporate organization. As they become the future leaders at Red Hat and elsewhere they will bring this perspective with them. The Henry Ford era of management philosophy may finally begin to change.
-
-
Fedora
-
The Free Software Foundation today announced their 30th birthday party to take place in Boston, Massachusetts in October. Also celebrating is GNOME, who turns 18 this Saturday, August 15. Elsewhere, Kali Linux 2.0 was announced, but one early review says it’s not ready. Fedora 23 Alpha arrived yesterday as well bringing “wide changes” and Italo Vignoli looks at the numbers from LibreOffice 5.0 a week after its announcement.
-
For now, Chromium is not added to the default Fedora repositories because it does not respect the distro’s policy about bundling of system libraries, but some developers are already working towards achieving this. The issue is caused by the fact that Chromium depends on its own libraries and FFmpeg, which is also absent from the repos.
-
Fedora 23 is scheduled for a release at the end of the October. Among many other improvements, this release will include new version of NetworkManager, the service that manages network connectivity.
-
Fedora 23 final is not due until the end of October but today the project released the Alpha build for early adopters and developers to test out. This release will be succeeded by a Beta release next month which will ship with patches for bugs found in the Alpha, the Beta will also be code complete and resemble what a user will find in the final release.
-
-
Fedora 23 development is moving on and the time to release is not long anymore, so it is time to open the submission phase for Fedora 23 Supplemental Wallpapers.
-
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
The Ubufox package has been upgraded by Canonical for the Ubuntu 15.04, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS operating systems.
-
BQ has created an Ubuntu global store where people from around the world can buy an Aquaris Ubuntu Edition handset.
This follows the successful European launches of the BQ Aquaris E4.5 Ubuntu Edition and it’s slightly larger brother, the BQ Aquaris E5 HD Ubuntu Edition.
-
The Ubuntu developers have set up a dedicated PPA for proprietary drivers, and for now, only the Nvidia video cards are supported. This is a great step forward made by Canonical, but a lot more work needs to be done.
-
The Ubuntu 15.10 (Wily Werewolf) development cycle is powering on and it looks like Canonical is determined to have Linux kernel 4.2 available as soon as possible.
-
-
-
-
Flavours and Variants
-
Bodhi Linux has had some hard times a period, when the main developer has dropped the project, but he came back and things got returned to normal.
-
-
Bodhi is an operating system based on Linux that uses a new desktop environment named Moksha. Bodhi Linux 3.1.0 is the first release in the series to use Moksha.
-
-
The Raspberry Pi crew is looking to add a firmware driver for their hardware to the Linux 4.3 kernel.
The Raspberry Pi firmware driver is needed for communicating with the VPU, which in turn has exclusive control of some peripherals. It was Eric Anholt that sent out this RPi firmware driver per this mailing list post.
-
This Raspberry Pi DRM/KMS driver makes use of the RPi firmware driver and why hours ago it looked like the new driver was on approach, and now it’s panned out with the latest mailing list activity. However, for easing review, Eric posted just the basic VC4 DRM driver support that brings up frame-buffer console support over KMS and utilizes the xf86-video-modesetting driver on X.Org.
-
As we continue to see how Artificial Intelligence can make our lives easier including everything from natural language processing to self-driving cars, it was only a matter of time before the technology broke out of the private domain of large companies and into the world of open source.
-
-
Aaeon’s rugged “FWS-2260″ network appliance runs Yocto Linux on a 14nm Intel “Braswell” SoC and has six GbE ports, SATA and CFast, and dual mini-PCIe slots.
-
Phones
-
Android
-
Hardkernel’s Odroid project is shipping a replacement for its community-backed Odroid-C1 single-board computer, which debuted last December, and came in fourth place in this June’s LinuxGizmos/Linux.com Linux/Android SBC reader survey out of a field of 53. According to the project, the $37 C1+ “replaced” the original $35 C1 as of July, and the original cases and heatsink will not work with the C1+. Otherwise, processor, memory, and other details are the same, including the 40-pin GPIO connector, which is said to be compatible with later generation Raspberry Pi SBCs.
-
-
-
Android was created as an open and flexible platform, giving people more ways to come together to imagine and create. This spirit of invention has allowed developers to push the boundaries of mobile development and has helped make Android the go-to platform for creative projects in more places—from phones, to tablets, to watches, and beyond. We set out to find a way to celebrate the creative, experimental Android work of developers everywhere and inspire more developers to get creative with technology and code.
-
-
-
-
-
Android Wear owners will gain several new features in a future firmware update, including interactive watch faces, an updated Weather app and a way to share information with others who have an Android Wear watch.
-
Google is rolling out new Android 5.1.1 builds to its Nexus devices and the Nexus 5 is on the list. With an OTA underway, we want to take a look at the most important things to know about this new August Nexus 5 Android 5.1.1 Lollipop update and its release.
-
At a time when even a company the size of Microsoft cannot succeed in the smartphone market, a new company called Nextbit thinks it can join Apple and Samsung at the top table. Headed by former HTC and Google staff, it has a secret weapon in the form of a phone that it says will get better with age.
-
-
-
-
-
-
-
-
-
-
-
The 2010s have not been so kind to BlackBerry, but the company could be close to readying a phone that could put it back on the map. BlackBerry’s first Android smartphone, codenamed “Venice,” might have just made its debut on Twitter.
Back in July, we got our first look at a BlackBerry handset running Android. Or, at least, an artist’s rendering of what it might look like. The phone we’re seeing today looks quite different, to say the least. It features a display that curves around its edges, much like Samsung’s Galaxy S6 Edge. The most notable difference is that the Venice is said to offer a slide-out keyboard in case you don’t want to type on the screen. It just wouldn’t be BlackBerry without some sort of physical keyboard.
-
The Ouya. The Nexus Player. The Fire TV. The Shield TV. The Forge TV. These devices run the gamut from “unmitigated disaster” to “pretty decent set-top box,” but each one raises the same question: What is the point of an Android console?
-
I wish there were a more “official” way to go.
-
Motorola took to Twitter earlier where it said “On Sep 3, you’ll see what real love is like. Choose #MotoX for a more powerful connection.” It later then revoked the tweet for an unknown reason.
-
Earlier, Bassel won the Index on Censorship Digital Freedom Award, which helped get him moved from a horrifically bad jail to a less hostile Adra Prison. Winning this award will further increase the spotlight on Bassel, which increases the pressure to release him, your fellow Free Software engineer and Creative Commons activist.
-
Lightning Network is a proposal for an off-blockchain network that would support super-fast transactions and boost Bitcoin scalability. Wednesday, miner hosting company HashPlex unveiled an alpha Lightning Network hub implementation, as developers continue to refine the layer (sometimes called layer-2) on testnets.
-
The word “Kubernetes” may not roll off the tongue as easily as the word “Google,” but it is nonetheless an important project many outside the software community have probably not ever heard of.
-
-
The investment bank is giving away some of its trading technology to clients through open source software, according to The Wall Street Journal.
-
-
Market researchers are predicting that by 2020, more than 20 billion devices will be connected to the Internet. These objects and devices will produce massive amounts of data 24-7, which will be a pain in the backbone to manage, unless tackled efficiently. To a great extent, the solution to the influx of IoT data rests in the effectiveness of the data infrastructure supporting cross-device communication—or, in other terms, in the effectiveness of IoT middleware. I firmly believe that in order to succeed in its purpose, this infrastructure should be founded on open-source platforms and technologies.
-
The Internet of Things (IoT) has the potential to be one of the most powerful technological innovations to date. In fact, its reach will be so extensive—encompassing billions of connected endpoints across the globe—that it will completely change the way companies and consumers connect with one another and share information.
-
For about a year, a small dedicated team has been building the Guardian’s new image management service.
From the beginning, the vision was to provide a universal and fast experience accessing media that is well organised and using it in an affordable way to produce high-quality content.
-
Effective open source advocacy on Twitter requires you to go wide. You need to find and participate in communities of people who are not focused on open source. Maybe people passionate about arts education. Public health advocates. Bicycling enthusiasts or bridge players or pet rescuers or Habitat for Humanity people or meditation people or Esperanto speakers or folk music singer/songwriters.
-
The increasing number of open-source initiatives in existence leads some to catch a dose of initiative-fatigue. What’s really going on here?
-
To open source or not to open source, that is the question for many IT teams that are struggling with deciding on the best approach to mobile application development. There is no doubt that today’s broad array of open source offerings appear to offer development nirvana – free, community driven, customizable software.
-
Non-profit foundations can help encourage fully open source software (FOSS) collaboration across industry and community. A relative newcomer is the prpl Foundation, an open-source non-profit foundation focused on enabling next-generation datacenter-to-device portable software and virtualized architectures. One of prpl’s focus areas is OpenWrt, a Linux distribution for embedded devices. Industry and community collaboration on a common FOSS baseline software stack can help facilitate new IoE products, applications and technologies, and enable easier connectivity and data exchange across a variety of platforms in the market.
-
Events
-
There are many similarities between Linux and the blockchain and so I was thrilled that Greg Maxwell, one of the core Bitcoin maintainers and a long term open source and cryptogrophy developer, accepted my invitation to keynote LinuxCon this year. I recently caught up with him to talk about his speech and the potential he sees for the Blockchain.
-
-
Web Browsers
-
Mozilla
-
Mozilla has already announced the launch of Firefox 41 Beta and opened up the final cycle to the upcoming version of the famous web browser.
-
Mozilla has released Firefox 40, featuring a new look for Windows 10, better protection against uncertified add-ons, and an attempt to resist Microsoft’s effort to make Edge the default browser.
-
SaaS/Big Data
-
Oracle/Java/LibreOffice
-
Saying LibreOffice or OpenOffice to people can lead to interesting reactions. For some people, LibreOffice is the darling of the open source world, and for others, it is a crappy Microsoft Office alternative that they look down on.
I believe that LibreOffice plays an important function in the world, and one that spans beyond the mere function of an office suite. Before we get to that though, I think looking back through the tremendous journey that led to the LibreOffice project we know today is important.
-
Following the announcement, donations have doubled in comparison to the previous weeks. As a consequence, we have reached the threshold of 150,000 donations since May 2013, when we started keeping track of the numbers. A huge thanks to all donors! With their money, they make LibreOffice sustainable, supporting the costs of the entire organization.
-
LibreOffice, the non-Microsoft and (to many) beloved office suite, has reached a new milestone with the release of version 5. It’s of particular interest to Linux mavens, but the rest of LibreOffice users will benefit as well, thanks to an impressive boost in performance through GPU hardware and some interesting new features.
-
CMS
-
The Czech government-owned public TV broadcaster Česká televize has switched to using the open source content management system Drupal for its CT 24 news website, it announced on 6 August. One month earlier, the government-owned Český rozhlas (Czech Radio) also began using Drupal.
-
Funding
-
Open-source app management startup WSO2 raised $20 million in funding on Thursday to expand the company’s global operations.
-
-
BSD
-
We’re quickly approaching our two-year anniversary, which will be on episode 105. To celebrate, we’ve created a unique t-shirt design, available for purchase until the end of August. Shirts will be shipped out around September 1st. Most of the proceeds will support the show, and specifically allow us to buy additional equipment to record on-site interviews at conferences.
-
FSF/FSFE/GNU/SFLC
-
Richard Stallman, the father of the Free Software movement and president of the Free Software Foundation, will participate on the 8th edition of the International Workshop on eHealth in Emerging Economies,IWEEE 2015, in Las Palmas de Gran Canaria, Spain, on September 26th.
-
-
-
-
-
Licensing
-
These facts brought to you by “let me just stick the GPL in an ACPI table so I can install the damn thing already”.
-
Programming
-
I’ve used Perl for several years, beginning in 2002 on Solaris, then moving to Debian and working on Koha in 2008. Surprisingly (bafflingly, in retrospect), I had not connected with the larger Perl community at all in that time, choosing to stay within the smaller communities I was already embedded in.
-
Whether you’re a TDD zealot, or you just occasionally write a quick script to reproduce some bug, it’s a rare coder who doesn’t see value in some sort of automated testing. Yet, somehow, in all of the new-age “Infrastructure as Code” mania, we appear to have forgotten this, and the tools that are commonly used for implementing “Infrastructure as Code” have absolutely woeful support for developing your Infrastructure Code. I believe this has to change.
-
-
Inspired by Quora’s Moving Fast With High Code Quality post, we are thus implementing a review routing system – the code is live on GitHub at phabricator-utils. It’s written in Python (hey, we’re a Java/JS/Python shop), though we do plan to contribute closer to the Phabricator codebase itself and that will be in PHP.
-
Science
-
Vinter acknowledged that MassCAN’s campaign is driven in part by self-interest: Google and other companies are worried about a lack of programmers and developers, specialists that are highly in demand in the booming Massachusetts tech industry.
-
I think we can all agree that open source is a good way to spread knowledge and empower people in many different ways, but it’s also true that competition, natural in a meritocracy, can and often does privilege those who can invest in the competition itself; minorities are being outspent and thus left aside by those who can afford to work, basically, for free.
-
Security
-
Once upon a recent time, Linux was more secure than it is today. Only the root user could mount external device, and in many distributions new users were automatically assigned a few groups that limited the hardware they could access. Distributions followed the principle of least privilege (aka least access), under which users, applications, and devices receive only the access to the system that they absolutely require.
-
-
Why do they do it? Run “2003” in 2015! It’s not cost, because Debian GNU/Linux would cost $0. It’s lock-in whether by habit or by application. Lots of folks have invested heavily in applications that still work so they are willing to risk everything, perhaps by adding other layers of security. Why?
-
Visiting Las Vegas can feel a bit like being a metal sphere in a pinball machine—you’re tossed from bright lights to blaring shows and back again until you eventually (hopefully) emerge out a hole at your home airport. When you visit Vegas with a swarm of hackers and security researchers, the dizziness gets amped up tenfold and can be laced with a dose of dark mischief.
-
An attacker can swap out the device’s firmware with altered, malicious software.
-
It’s one thing to talk about security vulnerabilities in a product, but another to provide a proof-of-concept demonstration showing the device being hacked.
That’s what occurred last month when BlackBerry Chief Security Officer David Kleidermacher and security professional Graham Murphy showed how easy it is for hackers to take control of a hospital drug infusion pump by overwriting the device’s firmware with malicious software.
-
…Adobe released updated Flash player plugins which adddress many new vulnerabilities (as usual).
-
Defence/Police/Secrecy/Aggression
-
-
TONY Blair has warned Labour members that Jeremy Corbyn’s election as leader will “annihilate” the party – prompting claims the former Prime Minister is running scared of the threat of a war crimes trial.
-
Reg Keys, whose son Lance Corporal Tom Keys was killed in Iraq in 2003, criticises former prime minister as families threaten legal action over Chilcot
-
Finance
-
The Chinese e-commerce giant announced a $4bn share buyback scheme and posted a 28pc rise in quarterly revenues
-
Kimmo Kalliola knows the feeling that thousands of Finns have been dealing with over the last couple of years. He spent more than a decade working on geolocation positioning at Nokia, a highly technical job, but the Finnish tech giant hit hard times. In late 2012, Mr. Kalliola and 10,000 others at the company were laid off.
-
PR/AstroTurf/Lobbying
-
Yes, Donald Trump, a Fox News political creation, was set to appear on Fox News to discuss his “relationship” with Fox News. But in the end, Fox hosts didn’t even ask Trump about his suddenly newsworthy relationship with Fox. Despite Doocy opening the interview by telling Trump, “glad we’re friends again” — to which Trump responded by assuring him, “we’ve always been friends” — there was no attempt to discuss Trump’s recent feud with Megyn Kelly and the network. Huh? Were they under orders from Fox chief Roger Ailes to ignore the friction?
-
Newly-released court filings undermine claims from Scott Walker and his allies that prosecutors were on a “partisan witch hunt” with the ultimate goal of taking down the governor.
-
The 2016 presidential race is a bonanza of fossil fuel cash for Republican presidential candidates, even 15 months out from election day.
Just 17 billionaires and businesses with ties to fossil fuel interests have pumped $67 million into Super PACs to support the ambitions of eight Republicans, according to a new analysis by Greenpeace and the Center for Media and Democracy (which publishes PRWatch.org). The Guardian broke the story.
-
The New York Times claimed that Carly Fiorina has emerged as the Republican Party’s “weapon against [the] ‘War on Women’ charge,” ignoring how her policy positions are actually harmful to women.
-
-
Privacy
-
Facial recognition software, which American military and intelligence agencies used for years in Iraq and Afghanistan to identify potential terrorists, is being eagerly adopted by dozens of police departments around the country to pursue drug dealers, prostitutes and other conventional criminal suspects. But because it is being used with few guidelines and with little oversight or public disclosure, it is raising questions of privacy and concerns about potential misuse.
-
If you’re about to start an internship at one of the world’s biggest social networks, it might not be in your interest to publicly embarrass it shortly before you begin. It’s a lesson that Harvard student Aran Khanna learned the hard way after creating an app that took advantage of a privacy flaw within Facebook Messenger. Khanna had found that, whenever you chat to your friends, the system automatically shares your location. As such, he built a browser plugin, called the “Marauder’s Map,” that showed you where your buddies were as they were talking to you.
-
Civil Rights
-
Earlier this year, Texas legislator Jason Villalba attempted to shortchange the First Amendment in the name of “officer safety” by making it illegal to film police officers from within a 25-foot, constantly-moving radius. His proposed law was greeted with criticism (and death threats, according to Villalba) and was consequently discarded because it was a terrible, arbitrary law that had only the briefest of flirtations with reality and logic.
For one thing, the law would have prompted officers to split their attention between the job at hand (whatever crime they were responding to/investigating) and Villalba’s directive. Of course, officers could easily choose not to enforce this bad law, but far too many officers have been filmed leaving crime scenes just to hassle citizens with cameras. And the instant the officer started closing the gap between him and the photographer, a law would have been violated in letter, if not in spirit. Villalba is a staunch supporter of law enforcement agencies and his proposal was just an attempt to give officers a little less accountability.
-
DRM
-
Get ready folks, ads are coming to Netflix
-
Intellectual Monopolies
-
Copyrights
-
Piracy monetization firm Rightscorp has signed an agreement to provide lawfirm Flynn Wirkus Young with the IP-addresses of persistent pirates. The data will be used to target U.S. Internet users who ignore DMCA notices and settlement offers sent by copyright holders. The first cases are already in progress.
Permalink
 Send this to a friend
Send this to a friend
08.12.15
Posted in Microsoft, Security, Windows at 4:51 pm by Dr. Roy Schestowitz

“I don’t want a back door. I want a front door.” — Director of the National Security Agency (NSA), April 2015
Summary: Microsoft Windows continues to be inherently insecure, at the very least because Microsoft worked to make intrusion possible by shady agencies that operate outside the law (much like cyber gangs)
IT IS no secret that Microsoft works closely with the NSA and other Five Eyes agencies. It is also no secret that Stuxnet was developed by those agencies and targets Microsoft Windows. After it had targeted Iran it sort of ‘spilled out’ and caused many billions in damages all around the world (we covered examples). Having gotten out of hand, Microsoft’s back doors for espionage agencies were soon exploited also by the “bad guys” (not that espionage agencies can be described as “good guys”). There is no substitute for absolute, scientifically-verifiable security and strong encryption. People who sell “Golden Key” dreams are non-technical war-loving liars. Based on this new article (Dan Goodin finally targets Microsoft for a change, having repeatedly bashed just Free software), a new Windows “exploit is reminiscent of those used to unleash Stuxnet worm.” To quote Goodin: “The vulnerability is reminiscent of a critical flaw exploited around 2008 by an NSA-tied hacking group dubbed Equation Group and later by the creators of the Stuxnet computer worm that disrupted Iran’s nuclear program. The vulnerability—which resided in functions that process so-called .LNK files Windows uses to display icons when a USB stick is plugged in—allowed the attackers to unleash a powerful computer worm that spread from computer to computer each time they interacted with a malicious drive.”
“GNU/Linux is designed for security from the ground up and if one does not believe it, one can freely scrutinise the code.”Any design that lets a USB device trigger commands at such high levels is a design that’s clearly not designed by security professionals. Many other issues tied to this design have been reported for over a decade and Microsoft is not fixing it. According to last year’s explosive report, titled “N.S.A. Devises Radio Pathway Into Computers”, the NSA “relies on a covert channel of radio waves that can be transmitted from tiny circuit boards and USB cards inserted surreptitiously into the computers.”
The media may go on about how Microsoft no longer delivering security patches is an issue, but as Microsoft tells the NSA about holes before patching them, what difference does it make? All versions of Windows, no matter how up to date they are, are vulnerable. It’s not an accident. “Both Microsoft and HP were insistent companies that hadn’t refreshed [Windows Server 2003] after 14 July,” said the report, “are exposing themselves to all sorts of security attacks, and that up-to-date patches and firmware are needed.”
No, their first mistake is that they use Windows anything (never mind Windows Server, irrespective of the version too). Windows is not designed to be secure. It has back doors and front doors. GNU/Linux is designed for security from the ground up and if one does not believe it, one can freely scrutinise the code. █
“The continuous and broad peer-review enabled by publicly available source code supports software reliability and security efforts through the identification and elimination of defects that might otherwise go unrecognized by a more limited core development team.”
–CIO David Wennergren, Department of Defense (October 2009)
Permalink
 Send this to a friend
Send this to a friend
Posted in Vista 10, Windows at 4:25 pm by Dr. Roy Schestowitz
“No” is not an option
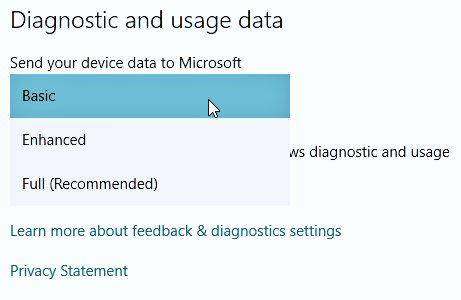
Summary: Looking at Vista 10 a fortnight after the release, it’s everything we expected it to be (utter failure)
20 days ago, based on information that we got from inside Microsoft, we said that Vista 10 was going to fail. So far, judging by a lot of metrics, we are proven correct. Based on what we can gather, very few people actually use Vista 10 right now, even two weeks later. Those that use it often get it ‘bricked’ and then go back to older versions of Windows, if not to another operating system (like GNU/Linux). Some people report this to us because they see it in their own eyes. As for governments and businesses, many are not able to adopt Vista 10 even if they wanted to. The EULA of Vista 10 is legally incompatible with many businesses (like legal firms), including Microsoft in fact, but some will adopt it regardless, at least until they get in trouble or customers complain, never mind auditors. Microsoft took a huge gamble and it lost not only Windows revenue but also made Windows unsuitable for a lot of environments, especially those which are the company’s wealthiest customers. As a Microsoft booster unintentionally reminds us today, Microsoft is listening to audio (like a bug) inside businesses.
“It’s an inevitable bricking process one cannot get around or shield oneself from, except by paying Microsoft or pulling the plug.”Microsoft’s Mouth shows us that Vista 10 is so broken that Microsoft already delivers a second mega update which is more like a re-release of the operating system, judging by the size. The British media [1, 2, 3, 4] and even US media (it’s easier for us to see local news, but this is definitely an international story by now) both concurrently report that these updates basically brick many PCs, although the euphemism ‘reboot loop’ is often used instead. Remember that remote updates by Microsoft cannot be switched off. It’s an inevitable bricking process one cannot get around or shield oneself from, except by paying Microsoft or pulling the plug.
‘Upgrade’ issues are a recurring theme in the media right now and IDG says Vista 10′s market share is at around 3%, contradicting early lies that claimed 50 million installations just few days after the release (i.e. more than now). That’s pretty bad for a supposedly gratis ‘upgrade’ which the majority of Windows users are eligible to download and install at any time. █
Permalink
 Send this to a friend
Send this to a friend
Posted in GNU/Linux, Microsoft, Vista 10, Windows at 3:52 pm by Dr. Roy Schestowitz
Microsoft: Doing to the operating system what Facebook does to uploaded data

Summary: Corporate media helps Microsoft take charge of every device, even devices running Linux, in order to sell data and perform data-mining (extremely gross violations of privacy)
ALONG with the synthetically Microsoft-manufactured Vista 10 hype came a lot of shameless marketing that piggybacks reputable products. One of these products was Raspberry Pi.
The people behind Raspberry Pi have actively helped (we suspect in exchange for payments/incentives) the abusive monopolist, Microsoft, and the company or Foundation even helps distribute/spread spyware (Windows). That’s hardly beneficial for education, except it helping Microsoft ‘study’ the users. Microsoft has, in a sense, reverse-engineered the purpose of Raspberry Pi, turning it into a device that subjugates users. Raspberry Pi lost its way when it first announced (or let Microsoft announce) its role in Windows integration — a truly tactless move which we recalled earlier this week.
Watch how Microsoft turns Raspberry Pi into a publicity stunt for malware. It exploits the project to promote Vista 10 [1, 2, 3, 4, 5, 6] and as one person told me: “Despite Eben’s assurance when questioned, I am not convinced there is mutual promotion there for free.”
“Watch how Microsoft turns Raspberry Pi into a publicity stunt for malware.”Microsoft and the spyware known as Vista 10 are hardly a promotion for or of education. Microsoft gets marketing/PR out of Raspberry Pi, whereas Raspberry Pi gets nothing but shame. “One way or another,” wrote the same person, “using Windows to promote an educational board for #Freesw [Free software] is bad news all round.”
Because of Microsoft’s money or power, now it is Raspberry Pi that neglects its goal/spirit, just like OLPC before it. This morning I had the displeasure of eating a whole large pack of semi-rotten raspberies (left in the fridge for too long by mistake), but it wasn’t as displeasing as seeing yesterday’s news littered with headlines that associate the British Raspberry Pi project/initiative, i.e. computing education, with spyware such as Vista 10. The Foundation is financially supported in part by Google, so it oughtn’t be desperate for endorsement from the likes of Microsoft.
“The Foundation is financially supported in part by Google, so it oughtn’t be desperate for endorsement from the likes of Microsoft.”Only hours ago we also saw Steven J. Vaughan-Nichols (SJVN) using non-news and a provocative headline (“Canonical and Microsoft working together on containers”) to associate Microsoft with GNU/Linux. Yesterday we saw the Linux Foundation posting this interview with Microsoft Ramji, saying that “you can try it on code, as downloads, like with Microsoft Azure” (Microsoft endorsement from Linux Foundation staff).
What is going on here? See the trend? Cade Metz from Condé Nasty is once again openwashing Microsoft, having groomed Bill Gates and Microsoft for years. Where does the money come from? Cade Metz is now painting Microsoft as GNU/Linux steward and “open”, attributing these claims to a Microsoft mouthpiece (Mark Russinovich) who claims “Linux now drives about 25 percent of the activity on Azure” (GNU/Linux is just universally far more dominant than Windows in many areas in the back room, so this isn’t too shocking).
It seems as though Microsoft attracted enough fools or lazy people (those who use existing fiscal accounts) to also set up GNU/Linux instances, only to be monitored and spied on by Microsoft, whose host operating systems have back doors. Mark Russinovich’s blurb has also been spun against Google while shameless ads from Microsoft MVPs (minions that IDG employs for Microsoft promotion) continued to be posted, encouraging people to do all their work on Microsoft’s own servers, even work which involves sensitive data (like customers’ information). The business press now says that “Microsoft’s $15 billion cloud bet ended up at the center of the company” and given the company’s special relationship with the NSA, only fools would head in this direction. For a lot of companies, in fact, doing so would be a violation of law (if enforced rather than overlooked or selectively applied). █
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day
- Software Patents Continue to Collapse, But IBM, Watchtroll and David Kappos Continue to Deny and Antagonise It
The latest facts and figures about software patents, compared to the spinmeisters' creed which they profit from (because they are in the litigation business)






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA