08.07.13
Posted in Apple at 4:38 pm by Dr. Roy Schestowitz
Summary: Apple continues to expand its patents collection and a patent troll is suing Apple again, gaining a lot of press coverage in the process
Hype-mastering companies like Apple cannot keep up with cheaper products that offer more features and higher customer satisfaction. The USPTO has become Apple’s complaints department, or rather, it is the facilitator of Apple’s calls for embargo through the ITC. Apple is said to have just gained another 41 patents, says an Apple boosting site. To quote:
The US Patent and Trademark Office officially published a series of 41 newly granted patents for Apple Inc. today. In our summary report we highlight five interesting patents, illustrate a number of design patents and provide you with a comprehensive list of the remaining patents that were published today.
Design patents are ridiculous, especially Apple's.
Meanwhile, reveals the press, VirnetX hits Apple with another patent lawsuit. Will Apple join the sane side of the industry which tries to abolish rather than glorify patents? Not likely. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Microsoft at 3:47 pm by Dr. Roy Schestowitz
Summary: Rape allegation against Microsoft program manager
Microsoft as a working environment has been exceptionally hostile towards women [1, 2, 3, 4] for quite some time. We occasionally point this out and provide examples only because Microsoft boosters like to portray FOSS as hostile towards women (Stallman too was targeted). The misuse of women’s right by men who seek to advance political agenda is a large and complicated topic that Techrights won’t delve into, but claims that demonising one’s opposition by appeal to women’s pleas is a popular tactic would not be challenged by many. Even prominent feminists routinely complain about it. Occasionally, even rape allegations are used to discredit people, so we’ll reserve judgment of the following until there is a court ruling.
“We occasionally point this out and provide examples only because Microsoft boosters like to portray FOSS as hostile towards women (Stallman too was targeted).”“Here’s one that’s not going to be in the press much,” wrote one reader (he is wrong on this one because a simple Google search on his name reveals plenty of articles [1, 2, 3, 4, 5, 6] coming from different countries). “I guess that could be tied to earlier complaints about the work environment especially parties.”
The article this reader sent us says that “A Microsoft program manager accused of sexually assaulting another worker on the corporation’s Redmond campus has been charged with rape.
“King County prosecutors contend that Vineet Kumar Srivastava raped a cleaning worker after luring her into his office on July 22. Srivastava, 36, is alleged to have told police that the woman forced him to have sex with her.
“Srivastava was employed by Microsoft at the time. A company spokeswoman said he no longer works there.”
So he may have been fired over it. Is that enough for Microsoft to distance itself from the case? They seem to think this case has merit if there was a firing. We shall see. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, Windows at 11:18 am by Dr. Roy Schestowitz

Summary: The TOR project asks users to abandon Microsoft Windows, which helped the NSA (based on identified IP blocks) crack anonymity
THE thing about proprietary software is, it infects any system it is surrounding, making everything penetrable if the underlying layer has a back door, which Windows has. Activists who challenge authority must never rely on proprietary software, suggests experience [1, 2],
More GNU/Linux distributors should start promoting their products based on privacy as a selling point, not just software freedom, especially now that a lot of people are concerned about mass surveillance. Sadly, however, even some of these distributors are now compromising their users' privacy inside Azure, whose host is in bed with the NSA.
“Several mainstream articles are publishing the Tor Project’s recommendation to drop Windows,” told us iophk, noting also the poor headline at the Telegraph. He gave this better example from IDG:
The TOR Project is advising that people stop using Windows after the discovery of a startling vulnerability in Firefox that undermined the main advantages of the privacy-centered network.
The zero-day vulnerability allowed as-yet-unknown interlopers to use a malicious piece of JavaScript to collect crucial identifying information on computers visiting some websites using The Onion Router (TOR) network.
There is more here. “In the pre-Mono days,” iophk says, “I would have expected Canonical and Ubuntu to be all over that. Shuttleworth could make an invitation like he did to the Suse developers. However, with their Community “Manager” defending MS, that may not happen. Speaking of the “manager”, his and the others' responses to your old post here has elicited denial of the problem as well as a bit of an attack. I think the topic is very worth revisiting at least once a month.”
Here is another post about this subject. It is reproduced as follows from JoinDiaspora:
The exploit of Tor by JavaScript
Who were affected?
- Window Users
- People who enabled JavaScript
- Used the Tor Browser Bundle
~Windows~
Most of the users were windows users, I’m not claiming that Linux or
Gnu|linux users are superior but to be more accurate, some windows
users don’t have the mentality of security or common sense when it comes to
protecting them self and their devises. Gnu|linux users or Unix users are more
aware of their surrounding and what goes within their Systems, now that said
Windows users need to understand that to be safe and secure you need to take
away all of those applications that would cause a back door to your system.
These are the following said applications:
Javascript - There are multiple ways of disabling this, but
my favorite way is to add an add-on called, “NoScript”. This disables script’s
to be activated and or used within your browser, you have nothing to worry about, you are able to
fully activate or deactivate JavaScript if needed.
Flash - Yes Flash, there are ways of doing this, either
deleting the flash application or never going to YouTube ( I doubt you’ll be doing this). There are multiple add-ons for your browser that will disable the usability of flash and allowing Html5 to
take over.
Cookies - Cookies are a great way of entering your system and
gather some useful information about said system and maybe you. There are
add-ons for disabling these little critters. there are multiple said add-ons like
Self-Destructing Cookies or going into your system and deleting them yourself.
~JavaScript~
JavaScript is not safe cause it has bugs. This holds true
for the various implementations of JavaScript, as well as the browsers that
JavaScript runs in. Some bugs can, when discovered, be exploited to bypass
the said sandbox, or to perform other malicious actions on your machine, like
what the FBI did to a specific Tor network. So JavaScript is not safe in most occasions, anybody
running JavaScript can be the target for something malicious.
~Using Tor Bundle~
Tor bundle uses an old version of Firefox and is easily
exploited, add-ons are not implemented within the browser. Even if you
were using Tor you would of gotten targeted. Using a different applications
for the same cause will allow users to be much safer than having a bundle and
thinking that no one can actually hack|crack into said system. This is false when
using anything, just keep in mind that you could always be Hacked|cracked by
someone or a specific organization.
Forgot to mention one thing, passwords. People please, don’t
create a password that is easily created like, your name, age, birth
place, or someone or something. The best way of creating a good
passphrase is to use Uppercase letters as well as other symbols for instance
if your name is jonny michaels use Joney_M1ch_els.
keep in mind that this example is just a bare minimum for a truly secure Password.
If you have any questions on what to use or just have anything
to ask me just ask.
Like alway, happy hacking
And if you don’t use free software, the hacking (or cracking) is all on you. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Free/Libre Software, Google, Patents at 11:04 am by Dr. Roy Schestowitz

Summary: A Mannheim court impedes Nokia’s assault on Free software, letting WebM stay free and GPL-compatible
Germany made a lot of headlines when its politicians called for the end of software patents [1, 2]. They were not alone. Professor Becker [1, 2], for example (German name but US citizen) continues to generate headlines to this effect (most of the media is occupied with patent trolls) and the Nokia assault on WebM/VP8 (through MPEG-LA) has just fallen flat on its face in Germany. To quote the WebM project site:
Today a court in Mannheim, Germany, ruled that VP8 does not infringe a patent owned and asserted by Nokia. This decision is an important and positive step towards the WebM Project’s ultimate goal: ensuring the web community has an open, high-quality, freely licensed video codec. Google’s intervention in the underlying lawsuit (Nokia v. HTC) was a strong show of support for open standards like VP8.
This ruling from Mannheim will probably be daemonised or publicly distorted by anti-Android lobbyists (e.g. Florian Müller), but it is what it is. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Hardware, Patents at 10:50 am by Dr. Roy Schestowitz
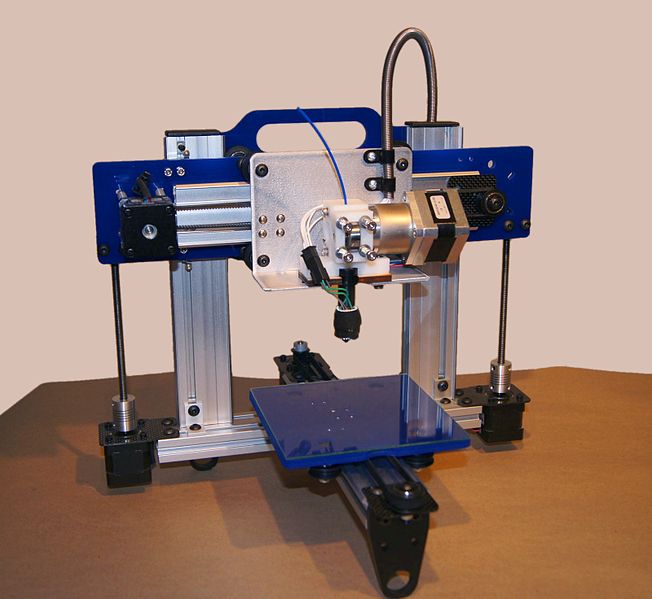
Summary: Design patents and the implication of those patents in the age of 3-D printing
Popular Science, a high-authority publication, has this new article about 3-D printing. It says that “New York lawyer Martin Galese has an idea. He’s turned drawings from expired patents into digital blueprints for 3-D printers. That means anybody can get his very own plastic hat holder, cup for drinking without spilling in bed, or combination pen-holder-bookmark (if you still have any paper books).”
“Just as the USPTO sort of criminalises some people who code in their bedrooms there’s this push to do the same to people who print in their bedrooms or garage.”Now that Apple has gone as far as asserting patents on rounded corners and some are trademarking colours (yes, colours!) we know that we have entered the crazy fantasy world of greedy patent lawyers who advocate patents on designs (which copyright law can already cover to a reasonable degree).
People should ask themselves, given the possibility of printing for oneself anything (like copying bits around or coding with no need for manufacturing, as in the case of software), why facilitate these artificial barriers? Just as the USPTO sort of criminalises some people who code in their bedrooms there’s this push to do the same to people who print in their bedrooms or garage. █
Permalink
 Send this to a friend
Send this to a friend
Posted in Patents at 10:35 am by Dr. Roy Schestowitz

Summary: The fight against patent trolls is gaining a lot of momentum, but other patent-related issues get sidelined as a result
Patent changes are afoot, but it does not seem likely that anything other than patent trolls will change. Timothy B. Lee, who has written about patents for years, says that reform is sought even by Conservatives and a government-focused site has a new Commentary titled “It’s Time for Congress to Take on Patent Trolls” (trolls are already the focus of the White House [1, 2, 3, 4, 5, 6, 7, 8, 9]). A political site, Politico, does the same and some say that the Obama administration intervention in an important patent case is a bad sign to “Patent Holding Companies”.
Patent trolls are almost definitely going to be negatively affected soon. It is a step in the right direction but also a step short of Utopia.
Apparently, says Troll Tracker, the state of Nebraska is going after trolls in another interesting way, targeting the lawyers:
I was heretofore unaware of Nebraska’s even having cans of whoop-ass, but oh my do they ever. Have y’all seen this by Scott Bialecki?
There is this new study which says “nuisance patent litigation” — not just patent trolls — costs customers billions of dollars. It alludes to a high-profile case which involves Android:
For the first time in 25 years, an American president, represented by U.S. Trade Representative Michael Froman, vetoed an earlier decision by the International Trade Commission that would have prevented some models of older Apple iPads and iPhones from entering the U.S. The models in question may now be imported. The case is at the heart of patent litigation between Apple and Samsung.
Prior to that, this whole case which Apple had started by suing Android backers including Samsung, almost had some Samsung devices banned [1, 2\. This whole dispute shows that the biggest problem is not trolls but the coordinated attacks by cartels like CPTN members against low-cost competition. How long before this bigger problem is tackled? █
Permalink
 Send this to a friend
Send this to a friend





















 Content is available under CC-BY-SA
Content is available under CC-BY-SA