07.16.15
Posted in Europe, Patents at 8:29 am by Dr. Roy Schestowitz

Summary: SUEPO (staff union of EPO) has just removed a post about Battistelli and his inner circle; we try to find out if union members or staff got threatened
LAST week SUEPO published some text and uploaded this PDF, which led us to writing this post.
Days later the PDF and the text both disappeared (it’s still not being reinstated and the PDF needed to be manually removed), so we have spent some time trying to find out what had happened. It’s almost certainly not accidental given the circumstances. One person told us that “the decision what is flagged public and what not is taken mostly by admins, and these are not members of the (political) SUEPO core team.”
Remember that SUEPO represents a great proportion of the EPO staff and also that the EPO engaged in censorship against SUEPO. There’s substantiate ground for fear. Battistelli’s inner circle is not speculative; this is just a list of names, their positions, and their family or professional ties. No defamation there, that’s for sure. No privacy violations, either.
We were not alone in wondering what had happened; there are already discussions about this online and offline (we may elaborate on this another day because some of the discussion is encrypted). Nobody seems to know for sure what is going on.
“No defamation there, that’s for sure. No privacy violations, either.”Does the EPO now induce self-censorship? First the EPO censored (deleted) E-mails, now it's censoring (blocking) entire Web sites such as Techrights. The People’s Republic of EPO might be a suitable new title for EPOnia, which views itself as independent from any country’s laws. Here is a new article about the EPO’s practice of censorship, composed and published yesterday morning. “EPO staff can still read TechRights at home or on mobile devices,” of course, “a fact that makes this attempt at censorship absolutely ridiculous. But it should also have access from its desktop computers at work just in case anyone finds links to prior art there.
“The EPO leadership has just scored an own goal: by blocking access to TechRights, it has now raised the profile of that blog.”
Dr. Glyn Moody, a journalist who covers issues including patents, calls it EPO “meltdown” (he wrote that 3 times over the past 24 hours). SUEPO, in the mean time, publishes another PDF, this time regarding the “120th Session of the ILO-AT” (it is a long 12-page paper).
As a side note, and it would be irresponsible to suggest that it is connected to the EPO’s actions (we have no such evidence except circumstantial), almost exactly on the same day (or the day after) the censorship was reported we got strongarmed by ICANN/ENOM to update records for the domain, as if someone complained that it was out of date. I received an authentic E-mail titled “IMPORTANT: Immediate Response Required – whois problem report: : techrights.org” on the same morning I wrote about the EPO’s censorship of techrights.org. ICANN/ENOM complaints are one way (among others) to induce domain-wide/universal blocking or expose one’s home address. I have been wrestling with this for 3 days now. It’s not as stressful as dealing with DDOS attacks, but it sure is a nuisance. █
Permalink
 Send this to a friend
Send this to a friend
07.15.15
Posted in News Roundup at 8:52 pm by Dr. Roy Schestowitz

Contents
-
Desktop
-
Adobe is not having a good time right now. Its Flash product has more security holes than Swiss cheese, making it a recurring target for hackers and bad guys. The tech world owes Steve Jobs an apology for poo-pooing his choice to disallow Flash from iOS. Things have gotten so bad, that Mozilla is blocking it by default as a major security risk.
-
If you’re looking for a new Linux distribution, don’t let the choices overwhelm you. This list of rising distributions will get you off to a great start.
-
Dabbling for the first time in Linux starts with choosing a Linux distribution. A typical “Linux” system is built up of software from many different open-source projects, including the Linux kernel. Linux distributions—or “distros”—are the projects that package all this software into an easily installable, usable operating system.
-
-
-
-
-
Each one of these laptops has one or two really great points counterbalanced by one or two unfortunate compromises. Usually, you’re either trading performance for general aesthetics and build quality or the other way around. Chromebooks with nice screens tend to have slower internals, and Chromebooks with better internals are usually generic plastic laptops with faded, cheap LCD panels. And of course, there’s always the Chromebook Pixel, perfect in pretty much every way except that $999 price tag.
-
Chromebooks have been red-hot on Amazon’s bestseller list for a long time, with many people defecting to Chromebooks from Windows and OS X laptops. The Asus Chromebook Flip is a convertible device that sells for $250. Ars Technica has a full review of the Chromebook Flip.
-
Server
-
The latest list of the world’s fastest supercomputers, Top500 June 2015, shows the fastest of the fast growing ever more powerful. It also shows Linux is still number one with a bullet when it comes to supercomputing.
-
“The real focus is the roughly $20 billion Linux server market, which is where we’re focused for growth, and we’re a small part of that today on Power,” Balog said. “So I view it as $20 billion of upside for me to go after and all of that is competitive against x86.”
-
Kernel Space
-
Sasha Levin, the maintainer of the Linux 3.18 kernel series, announced recently the immediate availability for download of Linux kernel 3.18.18, an LTS (Long Term Support) branch that receives security patches and bug fixes for a couple of years then regular kernel branches.
-
I don’t know about you, but I’ve always found the idea of operating system kernels to be some mysterious and esoteric programming skill. Its importance cannot be overstated of course, but I’ve always felt that kernel programming and regular programming were two very separate skills.
I’ve recently had some patches merged into the Linux kernel, and thought it might be interesting to describe what I learnt from this brief dip into kernel development and how someone who is new to it might go about getting into this space.
-
-
Graphics Stack
-
Nvidia is making some changes to the way it’s installing its drivers on the Linux systems and they are now using a new kernel module source layout. It’s not something that will directly impact users, but it’s interesting to see that Nvidia is starting to shake things a little bit.
-
Applications
-
-
If you work with open source servers (such as the world’s most popular web server, Apache), you know a massive number of tools are available to you. They range from security to functionality to monitoring… to just about anything you can imagine. But if you were to compile a single list of tools to include on your open source server farm, what would that list look like?
My own list tends to fluctuate on any given day. But almost always, certain tools stay on it. Here are the tools I rely on the most. (NOTE: This list does not include such things as basic Apache mod tools or the big four (Linux, Apache, MySQL, PHP— LAMP.)
-
If you’ve ever taken a digital photograph into GIMP to remove red eye or an ex-girlfriend or ex-boyfriend, or crop out a finger that got into the edge of the frame, then you are practically a compositor. A “comp artist,” as they are called in the industry, specializes in taking disparate moving images and placing them in the same frame, usually to make it appear that the different elements were shot at the same time. On the big screen, you’ll see this in nearly every movie since 1933′s King Kong (or thereabouts), but the art has reached a science in the digital realm, where some movies are practically not so much as edited as they are superimposed.
-
Instructionals/Technical
-
Games
-
Volgarr the Viking, a 2D platforming game built by Crazy Viking Studios, has been released for Linux users on the GOG.com digital distribution platform.
-
Lucius II, a third-person action game developed and published on Steam for Linux by Shiver Games, will be released for Linux users, according to an entry in the Steam database.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Together with some friends we visited the LinuxTag in Stuttgart and afterwards founded a local Free Software user group. We helped each other to install Free Software on our computers, configuring them to be routers, mail/print or file servers. I enjoyed learning with others, exchanging ideas, trying to fix problems. I subscribed to many mailing lists, and was eager to participate in Free Software events.
-
The KDevelop frontend for Krazy tools has been ported to KF5, so it now works with the KF5 version of KDevelop.
-
On the user interaction side, the past years have accompanied our interaction designers with visual artists. This is clearly visible when comparing Plasma 4 to Plasma 5. We have help from a very active group of visual designers now for about one and a half year, but have also adopted stricter visual guidelines in our development process and forward-thinking UI and user interaction design. These improvements in our processes have not just popped up, they are the result of a cultural shift towards opening the KDE also to non-coding contributors, and creating an atmosphere where designers feel welcome and where they can work productively in tandem with developers on a common goal. Again, this shows in many big and small usability, workflow and consistency improvements all over our software.
-
Krita is a KDE program for sketching and painting, although it has image processing capabilities, offering an end–to–end solution for creating digital painting files from scratch by masters. Fields of painting that Krita explicitly supports are concept art, creation of comics and textures for rendering. Modelled on existing real-world painting materials and workflows, Krita supports creative working by getting out of the way and with a snappy response.
-
We’ve addressed this in many ways so far: we’ve optimized the code for performance so it’s more responsive and starts reasonably fast, we’ve made sure most done is accessible using the keyboard so we don’t feel clumsy and overwhelmed by all the options.
[...]
One of the developments that have struck me the most during last years is Kate. Instead of focusing on the editor, it went the KDevelop route: it has started to offer all of the information at once (especially odd, given that there’s quite some feature overlapping).
-
-
New Releases
-
We have been recently informed by Zbigniew Konojacki, the creator of the 4MLinux project, that the upcoming point release of the 4MLinux 13.0 distribution has entered development and that Beta builds are now available for download and testing.
-
Alpine Linux development team announced on July 14 the availability for download of the second maintenance release of the server-oriented Alpine Linux 3.2 operating system.
-
The Solus operating system is coming along, and developers are constantly making improvements to it. The most recent iteration got a few fixes and small changes, but the most important aspect is the fact that the boot time has been reduced considerably.
-
PCLinuxOS/Mageia/Mandriva Family
-
Ballnux/SUSE
-
On July 14, SUSE LLC had the great pleasure of announcing that they will provide a new partner program expansion which brings support for 64-bit ARM server processors to their award-winning SUSE Linux Enterprise Server (SLES) 12 computer operating system.
-
-
-
-
-
-
Now that 64-bit ARM processors are starting to generate some interest inside the data center, providers of Linux distributions like Suse are starting to get in line.
Today Suse announced that version 12 of Suse Enterprise Linux will be supported on 64-bit ARM server processors from AMD, AppliedMicro, and Cavium powering servers by Dell, HP, Huawei, and SoftIron.
-
Red Hat Family
-
In infrastructure, the company has the RHEL OpenStack Platform. For application development it has OpenShift, a platform as a service now on its third version. Red Hat rolled out extensive support for containers in RHEL and OpenShift too. Cormier says Red Hat is “well into that journey” of bringing open source products across the entire infrastructure stack.
-
Being first to release a new technology can give a company an advantage in the marketplace, but when the product isn’t true to your brand, it can backfire. Red Hat, a world leader in open-source software, learned this lesson in 2008 when it acquired the tech firm Qumranet in an attempt to move into virtualization, a technology that allows computers to simultaneously run multiple operating systems.
-
Many big names in the storage industry have been jumping on the Ceph train. And why shouldn’t they? It does it all. Well, almost. Originally developed by Inktank and later acquired by Red Hat, Ceph is a software-defined scale-out data storage solution. It supports Object, Block, and File storage. It also exposes a RESTful API that supports both OpenStack and Amazon S3. What is there to not like about it?
-
-
-
Fedora
-
Many Fedora users take advantage of the fact that Fedora is internationalized, which means it can be used by people that communicate in different languages. Fedora provides support for displaying information on the screen for many different languages. There is also support for different input methods allowing users to input text for native languages where the number of characters is greater than keys on their keyboard.
-
Container technology has lead to several other areas of development and one of them being an atomic operating system that sandboxes applications and delivers updates in a single image. Red Hat started their Project Atomic to provide applications in a containerized format and produced Atomic Host as the tiny OS on which they’d run. It didn’t take long before planners began speaking of doing similar for Fedora and now developers are in the early planning stages of bringing this idea to fruition.
-
-
Debian Family
-
Marketing to FOSS is radically different from general ads to consumers or to other businesses. To start with, FOSS can be deeply suspicious about exploitation and free-riding from business outsiders. Just as importantly, FOSS contributors are often as intelligent as they like to think, and would prefer to make decisions based on information rather than emotional appeals. For these reason, FOSS marketing needs a delicate touch in order to reach its target audience.
-
Derivatives
-
Canonical/Ubuntu
-
Canonical is preparing to launch a new major update for Ubuntu phones and we now have a few more details about the new features, improvements, and fixes that are going to land very soon.
-
A libwmf vulnerability has been found and fixed in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS operating systems.
-
Canonical’s Joseph Salisbury was happy to announce a few minutes ago the summary of the Ubuntu Kernel Team meeting that took place earlier today, July 14, 2015, on the Ubuntu’s official IRC channels.
-
On July 14, Canonical’s Łukasz Zemczak sent in his daily report on the work done by the Ubuntu Touch development team, informing us that the OTA-5 software update for the Ubuntu Touch mobile operating system was delayed for the next Monday, July 20, 2015.
-
Meizu might be feeling similarly anxious, as this is its first major release in Europe, having previously focused on producing smartphones for the firm’s home nation of China.
-
Ubuntu developers are making some really interesting progress with the upcoming Wily Werewolf release, and they have revealed some of the work that’s being done for the desktop. It’s not much to look at, but there are a couple of items that should be mentioned.
-
Meizu has started shipping its MX4 Ubuntu Edition to a select few, and we now have a chance to test it. The review is not yet ready, as we’re waiting for a new major update, but we can give you a first impression, and we all know that first impressions are everything.
-
A vulnerability that would allow users to crash Bind with specially crafted network traffic has been found and repaired in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS.
-
Canonical is rolling out an over-the-air update for smartphones running its Ubuntu software. Ubuntu OTA-5 adds one key new feature, a few smaller features and bug fixes, and lays the groundwork for a very important new feature that probably won’t work on most phones currently running Ubuntu software.
-
-
-
Hardkernel unveiled a $74, open-spec “Odroid-XU4″ SBC equipped with an octacore Exynos5422 SoC, 2GB RAM, eMMC flash, a GbE port, and dual expansion headers.
-
-
The WeTek OpenELEC is a Linux media player dedicated to Kodi with OpenELEC pre-installed that gives you access to IPTV services with the extra of being compatible with modular DVB tuners.
-
Phones
-
Tizen
-
Tizen has previously made its way onto the Raspberry PI 2 Development Board, but 3D acceleration was not working at that point. Well, the good news is that the Team over at the Samsung Open Source Group have got the 3D Acceleration working now.
-
Android
-
-
-
-
-
If you want a desktop PC, you’re typically going to have to fork over several hundred dollars (Windows OEM licensing alone can make up a significant portion of that). But what if you could turn open-sourced Android into a serviceable desktop OS? That’s what Jide is trying to do, with its ultra-cheap Remix Mini PC.
-
Sub-notebooks/Tablets
-
At the recent Red Hat Summit, Red Hat CEO James Whitehurst talks with Network World about new IT processes and why companies should focus on open source.
-
Xerte Project’s Open Source Initiative membership furthers both organization’s commitment to growing open source community and collaboration within institutions of higher education.
-
The US National Security Agency has offered up one of its cyber security tools for government departments and the private sector to use freely to help beef up their security and counter threats.
-
-
Not sure which tools belong in your open source server toolkit? Here are 10 solid go-to tools to get you started.
-
Events
-
Open source software supplier Obsidian Systems invites OS enthusiasts, developers, geeks and friends to the next ‘Free Beer Session’ on 27 August 2015. This session, the 17th in the series, will offer delegates fresh insight into the open source industry, challenges and opportunities.
-
Web Browsers
-
Mozilla
-
I’ve dogfooded Firefox OS since its early beginnings and have some of the early hardware (hamachi, unagi, One Touch Fire, ZTE Open, Geeksphone Keon, Flame and ZTE Open C). It was good to hear some of the plans for Firefox OS 2.5 that were discussed at Whistler, but I wanted to take the time and model of this post and remix it for Firefox OS. Firefox OS you are great and free but you are not perfect and you can be the mobile OS that I need.
-
As the zero days in Adobe Flash continue to pile up, Mozilla has taken the unusual step of disabling by default all versions of Flash in Firefox.
The move is a temporary one as Adobe prepares to patch two vulnerabilities in Flash that were discovered as a result of the HackingTeam document dump last week. Both vulnerabilities are use-after-free bugs that can be used to gain remote code execution. One of the flaws is in Action Script 3 while the other is in the BitMapData component of Flash.
-
SaaS/Big Data
-
Recently, all-in-one appliances have been much in the news. A few days ago, I covered Mirantis Unlocked Appliances, which deliver OpenStack and all the hardware resources you need for a deployment in one hardware/software entity. Then, Cloudera, which focuses on Apache Hadoop, and Teradata, a big data analytics and marketing tools company, announced the Teradata Appliance for Hadoop with Cloudera.
-
Laura is the founder and lead consultant for SafeStack, a security training, development, and consultancy firm. What does that mean exactly? SafeStack helps organizations choose the right kind of security best practices for them. Then, Laura’s team shows them how to implement those new-found security protocols. This usually calls for a strong dose of workplace culture change, which might sound like a tall order, but Laura tells me in this interview “we want security to be any empowering tool for growth rather than a costly hindrance to innovation.”
-
In the beginning of the open source OpenStack cloud effort, there were two projects – Nova Compute and Swift Storage. Swift is an integrated part of most OpenStack distributions but it is also the focus for a standalone company called SwiftStack, which was founded by Joe Arnold.
-
Oracle/Java/LibreOffice
-
CMS
-
After over four years of development, including missed deadlines on general availability, the open source Drupal 8 content management system (CMS) finally appears to be nearing the finish line.
Drupal, one of the world’s most popular CMS technologies, is used by many high-profile organizations, notably Whitehouse.gov, the flagship website of the U.S. government. While Drupal founder Dries Buytaert in 2012 announced Drupal 8 would be generally available in December 2013, that date passed with no release.
-
Why is being open source so important to us? At its most basic, being open source means users have access to and can manipulate PrestaShop code to make improvements or develop technical answers to address specific business needs. But more importantly, open source represents accessibility and flexibility. It’s an open-door policy versus the private club mentality of proprietary software. Our community is built around this open source ethos; it’s the source of our strength and it’s how we’re contributing to a more democratic e-commerce market.
-
At Memorial Sloan Kettering (MSK), the world’s oldest and largest private cancer center, our researchers and clinicians have pushed boundaries to generate new knowledge in patient care and cancer research for more than 130 years. This culture of innovation allows our scientists to continually develop new methods for treatment and work tirelessly to discover more effective strategies to prevent, control, and ultimately cure cancer.
-
Education
-
SIGES is a free, open source, available in French, Haitian Creole, and English. It is customizable to suit the schools: primary and secondary; professional and technical; private and public; in urban and rural areas, the school networks, sponsorship organizations, educational projects, etc…
-
Business
-
Funding
-
If you need further evidence that container technology is all the rage, just follow the money. Sysdig, focused on bringing infrastructure and application monitoring to the world of containers and microservices, has announced a $10.7 million Series A funding round led by Accel and Bain Capital Ventures (BCV). In conjunction with the funding, Sysdig announced the general availability of Sysdig Cloud, which it bills as “the first monitoring, alerting, and troubleshooting platform specializing in container visibility, which is already used by more than 30 enterprise customers.
-
BSD
-
The PC-BSD crew has released version 0.8.5 of their Lumina desktop.
Lumina 0.8.5 has a speed boost for the user button, desktop icons have improved styling and appearance, a new desktop plug-in is present for monitoring system hardware sensors, and there’s a desktop plugin container for custom QML/QtQuick scripts. There are also updated translations, new PC-BSD/FreeBSD packages, etc.
-
FSF/FSFE/GNU/SFLC
-
Canonical, Ubuntu Linux’s parent company, has often rubbed other free software groups the wrong way when it came to open-source licenses. On July 15, Canonical, with support from the Free Software Foundation (FSF) and the Software Freedom Conservancy (SFC), have changed Ubuntu’s licensing terms. The FSF states that Canonical’s new intellectual property (IP) policies “unequivocally comply with the terms of the GNU General Public License (GPL) and other free software licenses.”
-
-
-
Canonical have a legal policy surrounding reuse of Intellectual Property they own in Ubuntu, and you can find it here. It’s recently been modified to handle concerns raised by various people including the Free Software Foundation[1], who have some further opinions on the matter here. The net outcome is that Canonical made it explicit that if the license a piece of software is under explicitly says you can do something, you can do that even if the Ubuntu IP policy would otherwise forbid it.
-
The Free Software Foundation (FSF) and the Software Freedom Conservancy (SFC) have been bickering with Canonical since 2013 over concerns that certain clauses of the Ubuntu IP rights policy seemed to claim to override provisions of the GNU General Public License (GPL) – something the GPL explicitly forbids.
-
Today, Canonical, Ltd. announced an updated “Intellectual Property” policy. Conservancy has analyzed this policy and confirms that the policy complies with the terms of the GNU General Public License (GPL), but Conservancy and the FSF believe that the policy still creates confusion and possible risk for users who wish to exercise their rights under GPL.
-
Compilation copyright is an idea exclusive to the US (or North America anyway). It restricts collections of items which otherwise have unrelated copyright restrictions. A classic example is a book collection of poetry where the poems are all out of copyright but the selection and ordering of poems is new and has copyright owned by whoever did it.
-
Project Releases
-
The world’s most used open-source software solution for accessing shared Windows folders over a network from GNU/Linux and Mac OS X operating systems, Samba, has recently been updated to version 4.2.3.
-
On July 14, Lubomir Rintel announced the immediate availability for download of the fourth maintenance release of the stable NetworkManager 1.0 network connection management software for GNU/Linux operating systems.
-
Openness/Sharing
-
Open Data
-
OEP is part of the Norwegian Government’s work to promote transparency and democracy within the public sector. OEP aims to make the Norwegian public sector more open and accessible to citizens. OEP is based upon the Freedom of Information Act and related regulations.
-
Programming
-
Zend, the PHP company, is updating its namesake PHP application server to version 8.5 providing new features and performance for users. The Zend Server 8.5 release builds on the Zend Server 8 milestone which debuted with the Z-Ray application insight technology.
-
Perl 6 has been 15 years in the making, and is now due to be released at the end of this year. We speak to its creator to find out what’s going on.
-
Security
-
-
I won’t pretend to be Steve Jobs—I don’t even own a mock turtleneck—but I have to repeat his words from April 2010: “Flash is no longer necessary to watch video or consume any kind of web content.” Flash is a constantly exploited, superannuated bit of technology that useful in the early days of multimedia in web browsers, and now deserves to die.
When Jobs wrote “Thoughts on Flash” over five years ago, it was in response to the notion that Flash should be available on iOS. At the time, I asked repeatedly for Adobe to stage demonstrations in private using iOS development tools to show Flash running. They never took me up on it, or any other writer that I’m aware of, even though they had the ability. Flash for Android, when it appeared, was terrible. Within two years, it was dead.
-
-
-
-
-
Defence/Police/Secrecy/Aggression
-
The corporate media in both the UK and US are attempting to portray the Iranian desire to have the arms embargo lifted, as a new and extraneous demand that could torpedo the nuclear deal. This is an entirely false portrayal.
-
There is a parallel danger in Iran. The Iraq War was totally unjustified and illegal, but Saddam Hussein might nonetheless have evaded it had he boxed a bit more cleverly and allowed some foolish inspectors to wander around his palaces prodding at the teaspoons. Yes the inspections regimes will be galling, even humiliating. But patience will have its rewards. There is real danger though that the hardliners on the Iranian side will be able to muster sufficient local points of power to hamper inspections, thus giving the US and Israeli hardliners an opportunity.
-
Environment/Energy/Wildlife
-
An American-owned water export company has launched a massive lawsuit against Canada for preventing it from exporting fresh water from British Columbia.
Sun Belt Water Inc. of California is suing Canada for $10.5 billion US, the Canadian foreign ministry said Friday.
The suit has been filed under Chapter 11 of the North American Free Trade Agreement. Sun Belt says it has been “mistreated” by the B.C. government.
-
Senator Ted Cruz, raising cash for a 2016 presidential bid, was to meet privately Monday in Denver, Colorado with executives from major oil and gas corporations, all members of the pro-fracking lobby group Western Energy Alliance (WEA), according to details of the secret meeting shared with the Center for Media and Democracy.
The Republican presidential candidate, a climate change denier, is also a leading proponent of opening up federal lands in the west–in fact virtually all lands everywhere–to energy development, and for scrapping regulations on oil and gas development.
-
Finance
-
Greece’s rampant corruption is one of the reasons why the country’s economy is in such a mess. German companies have taken advantage of the system for years in order to secure lucrative deals.
-
-
The International Monetary Fund has set off a political earthquake in Europe, warning that Greece may need a full moratorium on debt payments for 30 years and perhaps even long-term subsidies to claw its way out of depression.
-
Prof. Wolff joins GRITtv’s Laura Flanders to talk about Sanders and Socialism. Is socialism still an American taboo?
-
PR/AstroTurf/Lobbying
-
A new FAIR study finds that NPR commentary is dominated by white men and almost never directly addresses political issues.
-
Privacy
-
I’m currently working on developing a guide to securing iOS devices in a hostile environment (basically, “iPads for activists”). Although iOS is solid, iCloud backup is dangerously insecure, and must be avoided at all costs. Worse, it is enabled by default!
-
It was an unusual group. An investigative journalist, a moral philosopher, an internet entrepreneur, a cyber-law academic, a government historian, a computer scientist, a technology exec, a long-time cop, an ex-minister and three former heads of intelligence agencies. I wondered not just how but if we could agree on anything, let alone an entire set of recommendations to reform UK communications surveillance.
Yet we did. The Royal United Services Institute panel was set up by Nick Clegg, the then deputy prime minister, in response to revelations from the US whistleblower Edward Snowden about the scale of intrusion by US and British intelligence agencies into private lives. Our remit: to look at the legality, effectiveness and privacy implications of government surveillance; how it might be reformed; and how intelligence gathering could maintain its capabilities in the digital age.
-
We’ve discussed the “cybersecurity” bill, CISA, that’s been making its way through Congress a few times, noting that it is nothing more than a surveillance expansion bill hidden in “cybersecurity” clothing. As recent revelations concerning NSA’s surveillance authorities have made quite clear, CISA would really serve to massively expand the ability of the NSA (and other intelligence agencies) to do “backdoor searches” on its “upstream” collection. In short, rather than protecting any sort of security threat, this bill would actually serve to give the NSA more details on the kind of “cyber signatures” it wants to sniff through pretty much all internet traffic (that it taps into at the backbone) to collect anything it deems suspicious. It then keeps the results of this, considering it “incidental” collections of information.
-
Google has jumped on the Bluetooth Low Energy (BLE) beacon bandwagon with a set of open standards and software interfaces to give Apple’s iBeacon a run for its money.
Apple rolled out iBeacon in 2013, and has been pushing it as a way for companies to do things like tracking potential customers’ movements as they wander around retail stores.
-
Move over iBeacon—today Google is launching “Eddystone,” an open source, cross-platform Bluetooth LE beacon format. Bluetooth beacons are part of the Internet of Things (IoT) trend. They’re little transmitters (usually battery powered) that send out information about a specific point of interest, and that info is then passively picked up by a smartphone or tablet in range of the transmitter. A beacon-equipped bus stop could send out transit times, stores could send promotions to the customers currently in the store, or a museum could send people information about the exhibit they’re standing in front of.
-
-
-
-
-
-
-
-
-
-
Open Rights Group has responded to the Report of the Independent Surveillance Review by the Royal United Services Institute (RUSI).
-
Their Panel included three former senior security staff, and RUSI are themselves very close to the UK’s defence and security apparatus. Thus the tone of the report was always likely to address the concerns of GCHQ and the Foreign Office before those of civil society. Martha Lane Fox, Ian Walden and Heather Brooke will have had a tough job to help produce a relatively balanced report that does at least go some way to address wider concerns.
-
Netzpolitik, the German website defending fundamental freedoms, has been charged for “treason” on 10 July by demand of the president of the German intelligence services. The case will be lead by the federal prosecutor in charge of espionage and terrorism.
-
Civil Rights
-
Having spoken alongside Mhairi at a few meetings, and much admired her, it is rather strange to find her in danger of becoming an object of cult veneration. Just as with Nicola Sturgeon, it seems the shock of seeing the coherent and intelligent articulation of views outside the narrow consensus manufactured by the corporate media and political class, really does strike home to people. They almost never get to hear such views put; Mhairi is being given a hearing because of her youth in her position, but the marginalisation and ridicule will soon kick back in. Above all, Mhairi should remind us of how the Labour Party has completely sold out those they used to represent, and abandoned the task of proposing an intellectually compelling alternative to trickledown.
-
Intellectual Monopolies
-
What exactly is of trade secret concern here? The answer is: the aggregate email addresses of the subscribers. Anyone who wants to show the broad scope of what is protectable as a trade secret will likely mention a customer list. What could be further from patentable subject matter, yet still be of value to its owner as a trade secret, than a customer list? Email addresses of subscribers can be likened in this respect to the classic customer list. Thus misappropriation of the email addresses might be a concern.
-
Copyrights
-
Mega.co.nz has lodged legal threats against a New Zealand based search engine. MegaSearch.co.nz allows users to search Mega.co.nz for content but has attracted the attention of the file-hosting company after using its logos and trademarks without permission. Mega.co.nz is demanding a full shutdown.
-
Romanian authorities and the FBI have reportedly coordinated to shut down three sites involved in the unauthorized distribution of movies and TV shows. Several men were detained and various domains were seized amid allegations of criminal copyright infringement, tax evasion and money laundering.
Permalink
 Send this to a friend
Send this to a friend
07.14.15
Posted in America, Law, Patents at 2:31 pm by Dr. Roy Schestowitz
In Lieu of Decades of Bad Practice
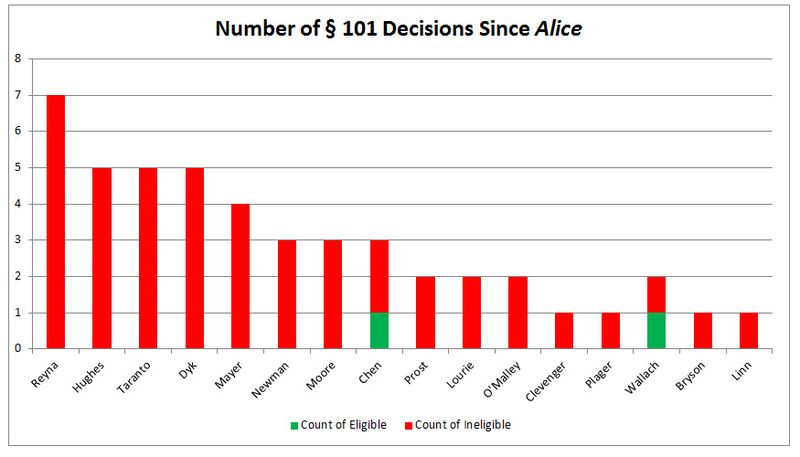
Credit: Bilski Blog
Summary: The so-called ‘AliceStorm’ is eliminating software patents (and other abstract patents) at an alarming (to patent lawyers) rate
LAST WEEK we wrote about Michelle Lee's remarks on patent law, conjoined with the report about the Alice case beating Microsoft's patent troll, Intellectual Ventures. Lee’s remarks were important because she is now the leading face of the USPTO (no matter her job title) and Alice is killing software patents very fast, impeding Microsoft’s attacks on Free software in the process. It was only four days ago that we last cited a new example where Alice slaughtered software patents, paving the way (by citation or argument/strategy) for future legal cases where software patents are at stake. This is one of the most fantastic developments that Techrights has seen in nearly a decade and if Groklaw was still active, it too would be jubilant (it partly celebrated the Alice ruling in News Picks, coming back to life after less than a year of total silence).
“Lee is finally recognising that everything has changed and therefore the USPTO needs somewhat of an examination overhaul, for courts almost always disagree on software patents granted by the USPTO.”Michelle Lee now claims that the USPTO needs more Section 101 guidance, based on this patent lawyers’ site. Lee is finally recognising that everything has changed and therefore the USPTO needs somewhat of an examination overhaul, for courts almost always disagree on software patents granted by the USPTO. Just look at the statistics.
According to Patent Buddy, this new ruling [PDF] is yet another victory. “Another case where application of Alice/101 to kill patents has jumped the fence from business methods to software,” to quote Patent Buddy, who added: “We are seeing 101/Alice rejections for everything from MRI devices to adhesives!” According to another new find from Patent Buddy, “US Pat. 6728877 and 7346766 Killed with 101/Alice in Summary Judgment in Lawsuit Against Lenovo by Tranxition in Oregon Dist. Ct.”
This isn’t being overlooked, except by patent lawyers who probably hope that nobody will pay attention. They cherry-pick the few cases where software patents somehow survive. Here is a software patents’ booster whining about this. He wrote: “Deals are still being done in the software patent world, but patent valuation is significantly less than even just a few years ago.”
It’s hardly shocking.
“The Alice/101 Kill Rate Is Accelerating,” Patent Buddy added, linking to a “MUST READ From Bilski Blog” where Robert R. Sachs coins (or advertises) the word/hashtag “AliceStorm”. To quote Sachs: “In just the first ten days of July, there have been ten decisions on patent eligibility—more decisions in first ten days of any month since Alice was decided last year. At this pace, we could see some twenty to thirty decisions this month. #AliceStorm is accelerating.”
It sure looks like even some of the most respected legal blogs (like Bilski Blog in this case) recognise that software patents are weakened by Alice orders of magnitude more often then they were weakened (or invalidated) by the famous Bilski case (it did happen albeit very infrequently). █
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, Microsoft at 1:54 pm by Dr. Roy Schestowitz

Summary: As Nokia is reduced to rubble in Microsoft’s fist (after epic entryism) the story of both companies is seriously distorted by Microsoft-friendly media in order to bolster Microsoft’s fictional version of the events
AMID the latest Microsoft layoffs we are deeply bothered to see misdirection and propaganda, almost surely coordinated behind the scenes by Microsoft's 'damage control' experts. The same thing happened some months ago when Microsoft announced an even bigger round of layoffs. Microsoft is trying to blame it all on Nokia, which is actually a victim of Microsoft, not an inherited liability. Nokia was doing a lot better before Elop (the Microsoft mole) stepped into the scene and gave Nokia to Microsoft as a gift, in exchange for a massive bonus that he was assured by Microsoft and later received from Microsoft (he has been set free again, potentially to find his next victims, Nokia not being his first).
“Actually, Nokia was starting to do pretty well with Linux (MeeGo) and was exploring Android, which now dominates the market with over 80% market share (i.e. about 2 orders of magnitude better than Windows).”The layoffs are explained a lot better by this Nokia guru, who foresaw a lot of what is happening right now. “Microsoft has now done THREE rounds of layoffs in less than 12 months,” he wrote, “firing 80% of the people it bought” (and many who are not from Nokia at all, possibly as many as 10,000 if not more, excepting temporary workers).
Watch how AOL rewrites the history of Nokia. This is “revisionism on ‘burning platform’,” as iophk put it in an E-mail to us. Some Microsoft-affiliated sites did the same thing, using euphemisms such as “Writedown” (euphemism of convenience for shutdown with layoffs) or “Misadventures” (again, for shutdown with layoffs).
“History tells us that Nokia did not defeat the odds,” wrote one person. “But inside the last five years are a number of lessons that the modern smartphone entrepreneur should think about.”
Actually, Nokia was starting to do pretty well with Linux (MeeGo) and was exploring Android, which now dominates the market with over 80% market share (i.e. about 2 orders of magnitude better than Windows). To say that Nokia was a lost cause and that it had to “defeat the odds” is to totally distract from Microsoft’s destruction of Nokia. Then again, Microsoft and its copywriters are always skilled at rewriting history in Microsoft’s favour. In the media we might even find Microsoft portrayed as the poor victim (e.g. of Nokia’s demise) rather than the predator that has had countless victims. Today’s articles about Netscape’s history are unbelievably watered down; some deleted Netscape from the history of Web browsers altogether. █
“Microsoft is, I think, fundamentally an evil company.”
–Former Netscape Chairman James H. Clark
Permalink
 Send this to a friend
Send this to a friend
Posted in Deception, GNU/Linux, Microsoft, Windows at 1:27 pm by Dr. Roy Schestowitz

Summary: Propaganda of assimilation, or trying to make Windows look comparable/on par with GNU/Linux cost and freedom, is the latest propaganda pattern
AS Microsoft so desperately combats the zero-cost advantage of GNU/Linux it uses not facts but fiction. We have grown accustomed to seeing advertising pieces like this one (journalists as Microsoft couriers or copywriters), pretending that Windows is “free” and that it may become “open source” because of some blurb from three months ago. “A per this Wired article,” wrote this author, “open sourcing is no longer optional, even for Apple. Even for Microsoft. Even for Windows.” Actually, all of these are proprietary, so evidence does not support the argument. Nice try though…
“They are blurring the distinction between “open” and “closed” or between “free” and “proprietary”.”Wired has been quite notable in the "googlebombing" of "Microsoft open source" or "Windows open source". It has been quite an effective propaganda campaign that culminated over the past year and we see more of it in light of this proprietary software release that is heralded with headlines such as “Microsoft’s Power BI is coming July 24th, adds a bit of open source and Android seasoning” and “Microsoft Says Power BI Will Come Out Of Preview On July 24, Open Sources Visualization Stack”. This is not Open Source at all, but Microsoft-friendly sites are openwashing Microsoft’s proprietary software. Sometimes even Linux sites fall for it as it’s not helping when Microsoft’s propaganda channel (Channel 9) is openwashing proprietary software such as Visual Studio. This example from Channel 9 is again fitting a pattern that we first noted one week ago. This openwashing ‘thing’ is very much ‘in’. The Microsoft-controlled Channel 9 increasingly chimes in to amplify the noise.
“Embrace, extend, extinguish” moves are now being used to make Apache software tied to Windows-powered and Microsoft-controlled servers (Azure). Isn’t that great? They are blurring the distinction between “open” and “closed” or between “free” and “proprietary”.
“Hadoop,” says ZDNet, “started out using an open source implementation of Google’s MapReduce as its exclusive processing engine.” Well, now Microsoft wants it all for itself, to run under Windows (proprietary and pricey) as well as under Microsoft’s control (with rental payments for hosting).
Microsoft is acting like a bandit, operating from the inside when it comes to Android as well (see “Windows 10 to allow easy porting of apps from Android and iOS platforms”), not to mention the underlying kenrel, Linux. Watch this new example of bad code that Microsoft has put inside Linux to promote proprietary software like Hyper-V, which runs on Windows (hyper-visor with NSA back doors implied) to control GNU/Linux guests. █
“I would love to see all open source innovation happen on top of Windows.”
–Steve Ballmer, Microsoft CEO
Permalink
 Send this to a friend
Send this to a friend
Posted in Hardware, Microsoft, Security at 12:54 pm by Dr. Roy Schestowitz
Summary: The insecurity and abundant complexity/extensibility of UEFI is already exploited by crackers who are serving corrupt regimes and international empires
TECHRIGHTS has spent many years writing about dangers of Microsoft back doors and about 3 years writing about UEFI which, according to various citations we gathered, enables governments to remotely brick (at hardware level) computers at any foreign country, in bulk! This is a massive national security threat and Germany was notable in reacting to it (forbidding the practice). Among our posts which cover this:
Today we learn that UEFI firmware updates spread to the most widely used GNU/Linux desktop distribution and yesterday we learned that “HackingTeam has code for UEFI module for BIOS persistency of RCS 9 agent (i.e. survives even HD replace)…”
Rik Ferguso wrote this with link to the PowerPoint presentation, pointing to leaked E-mails via Wikileaks. The push back against UEFI ought to be empowered by such revelations, perhaps in the same way that these leaks now threaten to kill Adobe Flash for good. █
Permalink
 Send this to a friend
Send this to a friend
Posted in News Roundup at 12:11 pm by Dr. Roy Schestowitz

Contents
-
-
Desktop
-
Canonical’s Ubuntu can be run on just about any x86 machine with a recent and compatible BIOS so who buys pre-loaded machines? HP clearly thinks there is a market for such a thing and recently announced three 15.6-inch laptops running the operating system, competition for a similar range of systems made by Lenovo aimed at the same market.
-
OS X is a solid operating system for those who enjoy Apple’s vision of the ideal desktop. It offers access to pro-level applications that many industries rely on. Yet it isn’t always the most practical operating system for the casual end user. In fact, in some cases, it’s completely overkill.
In this article, I’ll explore why I believe Linux is a more practical solution than OS X, if local techs would simply bother to support it. This article isn’t about which platform is “better.” Instead, it’s a matter of which platform is more practical.
-
-
Server
-
The use of Docker as an application container management system has become standard practice for developers and systems engineers in the space of just two years. Some like to say that haven’t seen such a technological advance since OpenSSH. Docker is now a major player and is widely used in cloud systems architectures. But more than just that: Docker knows how to win developers over.
Let’s take a look at an overview of what we’ve done with Docker, as well as an assessment of the future and of the competition that is appearing on the horizon.
-
…485 out of 500 systems were using Linux…
-
At No. 2 was Titan, a Cray XK7 system installed at the Department of Energy’s (DOE) Oak Ridge National Laboratory. Titan, the top system in the United States and one of the most energy-efficient systems on the list, achieved 17.59 petaflop/s on the Linpack benchmark.
-
Still, according to Top500, Chinese companies’ influence in the supercomputing industry is rising thanks to Lenovo, which has three systems in the top 500 under its own brand and another 20 jointly with IBM.
-
The challenge for these HPC players is that workloads can be delivered via pay-as-you go cloud models. It’s not clear what types of enterprises will rent HPC vs. build systems.
-
VMware introduces Project Photon: a lightweight Linux operating system for cloud-native apps. Star Trek and Einstein references aside, VMware’s Project Photon appears to be more than a particle or a wave.
-
Kernel Space
-
Dave Jones, a former Linux kernel engineer at Red Hat, is effectively suspending the future public development of his Trinity system call fuzzer.
Dave had been developing Trinity for the past several years as a Linux system call fuzzer with the original intention of finding Linux kernel bugs — oopses, etc, not particularly security bugs. However, he has grown frustrated by many people using Trinity without contributing back to the project. Additionally, there’s many using Trinity for trying to find security issues and not submitting their Trinity changes back upstream.
-
In part due to the recent news item about an NSA researcher looking at KDBUS and then having written a mailing list parser for finding how many Intel developers work on their open-source driver, for curiosity sake, here’s a look at the companies most active on the systemd mailing list.
-
Unless you have been living under a rock, or worse – you don’t care much about how Linux works, you must have heard of systemd, the (relatively) new init system replacing the old and outdated SysV init recently adopted by most major Linux distros.
-
The Linux 4.2 kernel that’s currently under development ships many new features, but as I’ve been writing about for a while and tweeting, the 4.2 Git code hasn’t been booting on many systems in my test lab for over one week. Various Phoronix readers have also been able to reproduce these different kernel panics that happen almost immediately into the boot process. Here’s the root problem affecting Linux 4.2 on my daily Linux benchmarking systems…
-
-
As you may know, Kernel 4.0.8 has bee recently released, but Kernel 4.0 will reach end of line soon.
Greg Kroah-Hartman has announced that Kernel 4.0.9 (which will be released next week), will be the last release from the series, the users being advised to upgrade to Kernel 4.1:
“Note, there will only be one more 4.0-stable release, please start moving to 4.1-stable at this point in time, you have been warned.”
-
The Linux Foundation is seeing increasing interest among early career IT professionals for basic Linux system administration (SysAdmin) skills as an entry point for a lucrative career.
-
I wrote earlier this month about kernel panics when trying to test the i7-5775C Broadwell H socketed processor on Linux. I ended up finding a workaround to improve the stability and that was by enabling the “CPU OC Fixed Mode” from the UEFI/BIOS on this particular Z97 motherboard, after my original Z97 test motherboard wouldn’t even boot up with the i7-5775C when equipped with the latest, Broadwell-supporting BIOS. Since then I bought a third motherboard to see how the situation plays out.
-
Benchmarks
-
If you are in the market for a new solid-state drive but aren’t too concerned about speed or storage capacity but just need something very affordable to get the job done, the ADATA SP600 is available in a 64GB model for less than $40 USD.
-
Applications
-
Often when doing performance analysis or debugging, it boils down to stare at long text trace files with the less text viewer. Yes you can do a lot of analysis with custom scripts, but at some point it’s usually needed to also look at the raw data.
The first annoyance in less when opening a large file is the time it takes to count lines (less counts lines at the beginning to show you the current position as a percentage). The line counting has the easy workaround of hitting Ctrl-C or using less -n to disable percentage. But it would be still better if that wasn’t needed.
Nicolai Haenle speeded the process by about 20x in his less repository.
-
-
A new version of RcppGSL arrived on CRAN a couple of days ago. This package provides an interface from R to the GNU GSL using our Rcpp package.
-
-
-
In the past I have reviewed QMPlay2, a video player using ffmpeg and the Qt 5 toolkit, which gets updated often and ships with some great features. The latest version is 15.07.12, released yesterday, and brings several fixes over the previous release.
-
Proprietary
-
-
-
Vivaldi, a web browser built by one of the Opera founders and his team, has been upgraded once more, and the developers seem to be preparing to exit Technical Preview 3 and enter the next stage, Technical Preview 4.
-
-
Instructionals/Technical
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Elad kindly told me that if I install the GStreamer codecs, and disable Flash, it should work. I didn’t have those codecs on my not-for-watching-TV machine, so I set to it.
-
Games
-
Valve has released a sleuth of updates for the Steam client, and the developers are preparing for another major stable update. The Linux platform didn’t get any special attention, but many of the improvements made apply to all the supported OSes.
-
Alien: Isolation is a first-person survival game developed by Creative Assembly, a studio mostly known for its Total War series. From the looks of it, a Linux version might just be in the works.
-
Guild Software has published details about a new double update for their popular Vendetta Online science-fiction massively multiplayer online role-playing game (MMORPG) for Microsoft Windows, GNU/Linux, Mac OS X, Android, and iOS operating systems.
-
Volgarr the Viking is a highly rated game that mixes action and platforming, and it’s now on GOG for Linux.
-
It seems a developer of America’s Army: Proving Grounds sent an email to Phoronix to mention they are looking to port it to Linux.
Take this with a grain of salt since it’s Phoronix, but it has been on Linux before and dropped, so it’s not out of the realm of possibility.
-
Alien: Isolation is a terrific horror game, and a franchise I get extremely excited for. Alien: Isolation is also one of the few “Alien” based games that wasn’t a let down.
-
Today I’d like to cover a game I didn’t know existed only a few days back, a game out of a genre that is heavily under represented on our beloved platform, a(n old-school) sandbox MMORPG named Albion Online!
-
A developer working on ‘X Rebirth’ responded to a user claiming they are wasting their time on the Linux version, and it’s a great response.
-
Legend Of Grimrock has sadly been unplayable for anyone on Linux with an Nvidia 900 series chip (like the 970), until now. The developers just put up a Linux beta, and it works.
-
-
Heads up GOG fans, they just recently released some more great Linux games to build up your DRM free collections. It’s really great to see them getting a bit quicker at it now, and building up their Linux catalogue is a must.
-
Postal 2′s Linux version has been lagging behind the Windows build for a long time, but no more. RunningWithScissors took the port in-house, and it’s now updated. Originally the port was maintained by Ryan “Icculus” Gordon, but he was too busy.
-
While I’m still working on my full Intel Core i7 5775C Linux review of this socketed Broadwell processor with Iris Pro Graphics 6200, and still working through some strange issues, I do have some Steam Linux gaming figures to share tonight for those interested in how Intel’s latest-generation Iris Graphics are performing with the open-source Mesa driver stack.
-
Desktop Environments/WMs
-
-
K Desktop Environment/KDE SC/Qt
-
Neophytos Kolokotronis from the Chakra GNU/Linux development team has posted news about the latest updates introduced in the current stable release of the rolling-release operating system.
-
-
Calligra is an integrated suite of applications for office, creative, and management needs. A fresh update has been released for the application, and it looks like the developers still have plans for this branch.
-
-
-
GNOME Desktop/GTK
-
In Linuxville today Eric Griffith demonstrated why GNOME is better than KDE and Attila Orosz explained what you need to know about systemd. Reviews of Semplice 7, Mint 17.2, and Mangaka caught my eye and Matt Hartley compared Linux to OS X saying, “I believe Linux is a more practical solution than OS X.”
-
It seemed to take forever. Endless PR reviews, improvements, code refactoring and hours spent working on editor, removing deprecated icons or search.
[...]
Without some exhausting descriptions, take a look at the current additions to the Getting Things GNOME!
-
This year’s GNOME Foundation Annual General Meeting will be held on the 8th of August at 15:45 (CEST). As with previous years, it is being held at GUADEC [1]. This year’s conference is at the Folkets Hus [2] in Gothenburg, Sweden.
-
-
The GNOME Foundation Board can often be a bit opaque. Generally it works in the background, and while you can get a sense of some of its activities through the minutes, it is easy to forget that the board is out there doing its thing.
-
-
Reviews
-
Originally, I wanted this post to be a comparison test. Specifically, I wanted to compare SolydK to the KDE edition of Manjaro Linux. However, it turns out that Manjaro Linux uses KDE 5 (I know this is a deliberate abuse of notation), while SolydK uses KDE 4. That doesn’t sound like a fair comparison, so I’m splitting these into separate reviews.
-
If you prefer to tweak your Linux settings to the max, you will find Mangaka and its Pantheon desktop a bit too limiting. However, if you want an unusually gorgeous background and a very simple Linux OS that has little or no learning curve, the Linux Mangaka distro can be a real joy to use.
-
It has been a few years since I last reviewed Semplice Linux. The Debian-based distribution has changed in recent years and some people asked if I would revisit this project. According to the distribution’s website, “Semplice is a GNU/Linux distribution based on Debian Unstable (Sid) with the goal to provide a simple, fast, lightweight and cool environment.” In itself, this description is not unusual. What sets Semplice 7 apart is the project’s unique desktop environment, called “vera”. The vera desktop is briefly talked about in the project’s release notes. The new desktop environment is based on GTK3 libraries (the same libraries which act as the foundation for the GNOME and Cinnamon desktops). The vera desktop ships with a new power manager, a screen shot utility and its own control centre panel. The release notes also mention vera ships with an interactive tutorial to help new users get acquainted with the young interface.
-
New Releases
-
On July 12, 2015, the developers of the nOS Linux kernel-based operating system announced that they would no longer be involved in the development process of the rolling-release distribution.
-
A new day, a new Solus update. The developers are keeping themselves busy, and they are working to improve the operating system constantly. The latest might not look like a major upgrade, but the devs have managed to refine the boot time considerably.
-
On July 13, the Manjaro Linux development team, through Philip Müller, had the great pleasure of announcing the immediate availability of the fourth update for the stable Manjaro Linux 0.8.13 distribution.
-
On July 13, François Dupoux, leader of the SystemRescueCd project, has informed users about the immediate availability for download of another maintenance release of his Live CD Linux distribution.
According to the brief changelog, which we’ve attached at the end of the blog post, the SystemRescueCd 4.5.4 release brings updates to both the standard and alternative kernels, as well as new versions of some of the most essential core components, which include e2fsprogs, xfsprogs, and btrfs-progs.
-
Screenshots/Screencasts
-
A new version of Zorin OS has been released over the weekend, and it comes with a ton of new stuff, not to mention an updated desktop design. We now take a closer look at this distro to see what’s so special about it.
-
PCLinuxOS/Mageia/Mandriva Family
-
-
I had only recently reviewed Mageia5, when I noticed an announcement for OpenMandriva 2014.2. So I was mistaken that Mageia was what was left of Mandrake/Mandriva. OpenMandriva is another fork that continues.
I have tested only from the live media. I did not do a full install to a hard drive. So this is a more limited review than I gave for Mageia5.
-
Ballnux/SUSE
-
-
The move, like so many of its other announcements lately, comes as a response to long-time rival Red Hat Inc, which launched a program to court manufacturers dealing in processors based on designs from the British semiconductor powerhouse all the way back last year. Both vendors hope to seize the rise of software-defined environments made up of small, low-cost servers that benefit from the power efficiency of ARM chips.
-
-
-
Red Hat Family
-
-
Patricia Bogoevici started off as a software developer and has graduated to consulting on Agile and DevOps projects. At the recent Red Hat Summit, Bogoevici and her co-presenter Josh Minthorne presented a talk about using Agile and DevOps methodology to achieve faster production deployment.
-
-
-
Open source solutions vendor Red Hat has announced the global launch of the Red Hat Certified Cloud and Service Provider programme, replacing Red Hat’s existing Certified Cloud Provider programme.
-
Speakers from Red Hat, Inc., SAP SE, and Intel discussed their collaborations and innovations as part of the open-source community during a General Session at the 2015 Red Hat Summit. In keeping with the open spirit, the session started with highlights from the Enable Project, which designs and distributes open-source, 3D-printed prosthetics at no cost to individuals.
[...]
After sharing an excerpt from “Open Source Stories,” Paul Cormier, president of Products and Technologies at Red Hat, took the stage to celebrate the victory of open source over the past few years. He cited the Mohandas “Mahatma” Gandhi quote: “First they ignore you. Then they laugh at you. Then they fight you. Then you win.” He went on to say, “I’m here to tell you today that Linux and the open-source community have won. And they’ve completed the Gandhi quote here. They can now check the last box.”
-
-
-
-
Shares of Red Hat, Inc. (NYSE:RHT) rose by 2.16% in the past week and 0.45% for the last 4 weeks. In the past week, the shares has outperformed the S&P 500 by 2.17% and the outperformance increases to 1.29% for the last 4 weeks.
-
-
Red Hat is replacing its existing cloud provider programme with a revamped one it claims will help provide better support for distributors, managed service providers and systems integrators. The company said the move was in response to what it sees as a broadening ecosystem of partnerships in cloud.
-
Fedora
-
I like very much the new Virtual Box and Fedora also, because it’s fast (~ 1 min) and I don’t need to start another hardware to test my linux stuff.
-
I am happy to announce the release of F22-20150629 update lives.
-
The Steam repository has received some love; changes to the Steam package will also be pushed in RPMFusion after a bit of feedback.
-
-
Bit late blogging about this, but roshi sent out the Fedora 23 Call for Test Days at the end of June.
-
The developers of the Linux AIO project have been glad to inform us about the immediate availability for download of new builds of their Linux AIO Fedora project, which is now based on the latest stable Fedora Linux release.
-
Debian Family
-
The Debian developers have decided to make GCC 5 the default compiler in Debian Unstable, but Debian 9.0 Stretch will be most likely using GCC 6 as default. Also, Ubuntu 15.10 Wily Werewolf will adopt GCC 5 in a short time.
-
Derivatives
-
Canonical/Ubuntu
-
-
A new set of OpenSSL vulnerabilities have been identified, and all Linux distributions have been quick to implement patches in order to close these issues. As it turns out, none of the supported Ubuntu OSes has been affected, and no patch has been released.
-
Dekko is a native IMAP email client for Ubuntu Touch and is coming along just fine. From the looks of it, developers are not only working to make it work on the phone but to also scale and properly function on the desktop as well.
-
-
The Ubuntu Touch platform is getting some major improvements in the coming months, and it looks like the SMS function is finally getting the attention it deserves.
-
-
-
Another week has passed, and Canonical’s David Planella has sent in his regular report that informs us about the latest work done by the Ubuntu Community Team.
-
Ubuntu MATE 15.10 has a few windows managers, and one of those is Compiz. From the looks it, the developers of the distro are making some changes so that the entire Compiz experience is more enjoyable and more stable.
-
Grooveshark is no more, and the service was also removed from Ubuntu Touch, but the developers are working to replace that with something else, and it looks like something is in the works.
-
-
-
-
Phones
-
Tizen
-
Samsung Electronics usually has their big reveal of their next big Smartphone (Note x) in September, at the IFA Event in Berlin since 2011, but it looks like Samsung are looking at moving it to mid-August, according to a person familiar with the matter. The reason behind the move is that they wanted a bit more room between their announcement and Apple Inc unveiling of the next iPhone.
-
Android
-
-
-
Google is launching brand new watch-to-watch communication features for Android Wear that are not unlike those on Apple’s Watch, according to Phandroid. Users will reportedly be able to send each other doodles, photos, stickers, messages and more using a feature called “Together.” That’s pretty similar to the Apple Watch’s Digital Touch, which allows users to relay tap patterns, drawings and even heartbeats to each other. Oddly, Android Wear users who want to share items may need to use the same the same watchface, as the feature isn’t system-wide. However, Phandroid admitted that its information on that aspect “is quite old.”
-
Apple Watch users can send each other doodles and emoji, but those with Android Wear smartwatches haven’t had the same luxury.
-
-
Google is planning to release a mysterious new watch-to-watch messaging service during its next Android Wear update, according to tech website Phandroid.
-
Since last fall, Pebble smartwatch users have been able to count their steps and track their sleep, but they’re on their own in deciding which third-party fitness app to use.
-
-
-
-
-
Blackberry and Android usually don’t go together in one sentence, but that’s about to change. The shrieks and awe built around the prospect of a Blackberry smartphone running Android is in full force this week after the revelation that BlackBerry has purchased two Android-centric domain names: AndroidSecured.com and AndroidSecured.net.
-
A new “security app” for Android claims apps like the ASTRO File Manager are vulnerable. Jack Wallen challenges this claim.
-
Last week Android M Developer Preview 2 arrived on scene. That very day I released our first “Diving into M” post for the second preview, which highlighted the changes to the launcher and the ability to now edit the status bar with the Tuner UI tool in the developer options.
-
-
If you dabbled with Google Photos when it was launched last month but decided it wasn’t for you, make sure you also turn photo backup off in your Android phone’s Google Settings menu, or else you’ll continue uploading new pictures to the service. Nashville Business Journal writer David A. Arnott discovered the quirk when hundreds of family photos appeared on Google Photos, even when he’d deleted the pictures and uninstalled the app itself from his phone.
-
-
Google has launched a new Ethernet adapter for it’s Chromecast device. The aim of this accessory is to let you connect your Chromecast directly to your router to create a fast and reliable connection for your Chromecast. The Ethernet adapter has a central hub that plugs into the wall, this will provide power to the Chromecast via a USB cable.
-
Wait — wait just one second. As a parent, I take umbrage with Pichai’s absolutist response. Especially since the Android OS he’s in charge of can be found on 80 percent of all smartphones sold worldwide.
-
Unlike last year’s budget Android One series, the upcoming Google phone is said to come packed with upgraded hardware and is expected to retail under mid-range category, thus filling the gap between entry-level and the top-end Nexus series.
-
In May, Google revealed a small-footprint operating system called Brillo, a version of Android for Internet of Things applications that will arrive in a developer preview in the third quarter. It will work with a cross-platform communications framework called Weave that will arrive in Q4.
-
Go is opinionated, and influenced heavily by Google’s use case, but Minio doesn’t mind inheriting Google’s way of building infrastructure software. Go is not as mature as Java yet, and it still has some rough edges when it comes to tooling and garbage collection; however, Go is ready for developing production-grade software. The next release of Go 1.5 implements efficient concurrent garbage collection and address the tooling issues.
-
-
-
-
News from last month, but important enough to revisit — Cloud Foundry Foundation has appointed Stormy Peters as vice president of technical evangelism.
-
Events
-
Web Browsers
-
Mozilla
-
As you may know, Thunderbird is an open-source e-mail client and chat client developed by Mozilla. Among others, it has support for email addresses, newsgroup, news feed and chat (XMPP, IRC, Twitter) Client, managing multiple accounts. Also, it has support for different themes and its power can be extended by plugins.
-
SaaS/Big Data
-
Mirantis have announced the launch of Mirantis Unlocked Appliances, a programme to allow customers to buy flexible turnkey OpenStack appliances. The appliances are certified and delivered by ‘Certified Rack Partners’, for now this list is limited to a Redmond based company called Redapt.
-
-
-
Oracle/Java/LibreOffice
-
Business
-
BSD
-
-
We are pleased to announce the availability GhostBSD 10.1 BETA2 MATE & XFCE which is available on SourceForge for the amd64 and i386 architectures.
Before going further I will like to say a special thanks Ovidiu who recently join back the project and Andrea who join the project, they have help to make GhostBSD better, add up new feature and fixed issue.
-
-
Openness/Sharing
-
Look at distributed systems, decentralized computing, open source, and lean principles. With these and other technical initiatives, we’ve pushed boundaries and improved our applications, our networks, our companies, and our lives.
-
In late June, Berkeley held a workshop to get to know what research has been underway on RISC-V. RISC-V is an open instruction set architecture (ISA) originally developed at Berkeley and based on established reduced instruction set computing principles. It is a minimal, modular ISA ready for hardware implementation, freely available to both academia and industry.
-
Open Data
-
-
The government needs to open up far more of its information and move to a culture of making decisions based on data not targets, Cabinet Office minister Matthew Hancock MP has said.
During a speech in London today, Hancock (pictured) praised progress since 2010 on opening up public sector data, with 20,000 datasets now published on the government’s portal data.gov.uk.
-
Programming
-
Facebook developers today announced the release of HHVM 3.8.0, their interpreter for PHP and their own Hack programming language.
-
-
Bruce Eckel is the author of Thinking in Java, Thinking in C++, and a number of other books on computer programming. He’s been in the computer industry for 30 years and periodically gets frustrated and tries to quit—then something like Scala comes along and offers hope and sucks him back in. He’s given hundreds of presentations around the world, and enjoys putting on alternative conferences and events like The Java Posse Roundup.
-
Code version control using Git or SVN seems like too trivial to some small project, but today’s experience taught me a lesson.
-
Standards/Consortia
-
Once upon a time, if you asked a standards setting organization (SSO) what its intellectual property policy rights (IPR) policy was, you’d get a simple answer: “We own the copyright in everything we produce.” Today, if an SSO that develops standards in the technology arena were to give an answer like that, it would find that its members were heading for the exits.
What’s changed, of course, is that information technology has infiltrated almost every aspect of our existence, and that includes standards development as well. For example, an SSO that used to limit its attention to setting construction standards relating to heating and ventilation installations will now also host working groups developing standards for sophisticated building control systems.
-
The Software Freedom Conservancy’s Bradley Kuhn is probably best known for his work in enforcing the GNU General Public License (GPL). Enforcement-by-litigation might get the headlines, but Kuhn treats the courts as a last resort.
-
Choudhary is a technology lawyer and an online civil liberties activist. She is the founding executive director of SFLC.in, a pro-bono legal services organisation based in New Delhi that focuses on free speech and expression, privacy, software patents, network neutrality, internet governance and access to knowledge.
-
The list goes on; it’s seemingly infinite. Such search terms offer insight into both our fears (“how bad is caffeine during pregnancy”) and desires (“bronies”). And thanks to thousands of poorly paid freelance writers looking to pick up some extra cash or toiling for wages, the results we’re served in these vulnerable moments are often hastily scribbled, poorly written, ungrammatical filler text. This old world relic represents a time when getting to the top of Google rankings wasn’t dependent on the quality of information you supplied but how many people linked to your site.
This kind of text—the equivalent of fast food or hangover-friendly TV—is the preserve of content mills, an Internet subculture where for-hire workers are tasked with writing vast amounts of online copy for a pittance. Today, when more media outlets and self-publishing tools exist than ever before, such word factories somehow continue to exist.
-
Science
-
A new expedition to the craters in Yamal, in northern Russia, shows how they have rapidly altered since they were first noticed last year, but also indicates the possibility that not all the craters were formed in identical ways. The holes – first noticed last year – intrigued and perplexed scientists from around the world, initially provoking a number of explanations as to their cause, the most outlandish of which was that they were caused by stray missiles or even aliens from outer space.
-
A pitcher plant species in Borneo attracts bat inhabitants by reflecting sonar signals from the flying mammals, advertising a cozy roost, and getting nitrogen-rich guano in return.
-
Security
-
-
My cert expired after a year because that seems to be the thing to do. I imagine there’s some nebulous threat model where somebody stole my server key and has been impersonating me for the past six months, but now they can’t. Although, if they stole the old key, they can probably steal the new key. I suppose we do this because revocation doesn’t work, but a six month half life is a long time to sit exposed.
-
-
An elite cyberattack group that was employed by governments and agencies was probably hacked by another country, it has said — and the attack has led to its powerful hacking tools being released into the wild.
Hacking Team was hacked last week, revealing private emails and documents as well as insights into its tools. The leaked documents showed many of the vulnerabilities that were being used by the group — such as a bug in Adobe Flash that can be exploited to get complete control of a computer — which has meant that anyone can counteract them as well as use them for their own ends.
-
-
-
After yesterday’s news that Facebook’s new chief security officer wants to set a date to kill Flash once and for all, the latest version Mozilla’s Firefox browser now blocks Adobe’s vulnerability-riddled software as standard. Mark Schmidt, the head of the Firefox support team at Mozilla, tweeted that all versions of Flash Player are blocked in the browser as of its latest update, accompanying the news with an image showing a raised fist and the phrase “Occupy Flash.”
-
Yesterday the usual tech news outlets were buzzing over an accidental tweet which the media incorrectly interpreted as Mozilla was ditching flash (Blame The Verge for the chain reaction of copied news articles) entirely as a policy. While that is not the case, I was just as excited as many at the faux-news. This got me thinking: what would it really take for the web to kill Adobe Flash? Could Mozilla really make such a move and kill Flash on its own if it wanted to?
-
Last week I released No Flash 0.5, my addon for Firefox to fix the legacy of video embedding done with Flash. If you are like me and don’t have Flash installed, sometime you encounter embedded video that don’t work. No Flash will fix some by replacing the Flash object with a HTML5 video. This is done using the proper video embedding for HTML5.
-
This message comes after it was revealed that the recently hacked “Hacking Team” was using Flash zero-day vulnerabilities to hack journalists, activists, governments and more. Alex Stamos, like other security experts, must have also gotten tired of hearing about so many security vulnerabilities that Flash has had during its entire lifetime.
-
Now more than ever, leaving Adobe Flash Player on your system is looking like a dubious proposition.
While Flash has long been a popular vector for malware, last week’s security breach of surveillance software firm Hacking Team underscored just how vulnerable Flash can be. Hacking Team was relying on at least three unpatched Flash exploits, which cybercriminals immediately adapted for their own nefarious uses. Adobe is scrambling to patch the exploits, but at least one remains unfixed as of this writing.
-
-
Dubbed the Census Project the initiative has been finding an embarrassing number of flaws in common core Linux system utilities that have network access. Some of them have nowhere near enough development relative to their importance.
-
Defence/Police/Secrecy/Aggression
-
In response to the multi-state military exercise organized by the federal government, a group of very concerned Texans have organized what they’re calling “Counter Jade Helm,” in which “citizens will participate in an unofficial fashion to practice counter-insurgency, organizational and intelligence gathering and reporting skills.”
Operation Jade Helm begins on July 15th, but as the media is barred from covering the exercise, citizen surveillance is the only option that people like retired firefighter Eric Johnson have to assuage their concerns about what the SEALs, Green Berets, and Air Force Special Ops are actually up to.
-
Environment/Energy/Wildlife
-
A newly unearthed missive from Lenny Bernstein, a climate expert with the oil firm for 30 years, shows concerns over high presence of carbon dioxide in enormous gas field in south-east Asia factored into decision not to tap it
-
It’ll take awhile, but according to a new paper published in the journal Science, the planet’s on track to see sea levels rise by at least 20 feet — and that’s only if we manage to limit global warming to 2 degrees Celsius, a target many believe we’re already doomed to surpass.
-
A hulking rig is engulfed in flame. It’s sinking, spitting out a giant plume of smoke in the process. A firing squad of rescue ships are dousing it with ocean spray. Eleven men are already dead.
-
Finance
-
Yanis Varoufakis: I’m feeling on top of the world – I no longer have to live through this hectic timetable, which was absolutely inhuman, just unbelievable. I was on 2 hours sleep every day for five months. … I’m also relieved I don’t have to sustain any longer this incredible pressure to negotiate for a position I find difficult to defend, even if I managed to force the other side to acquiesce, if you know what I mean.
-
-
PR/AstroTurf/Lobbying
-
Censorship
-
The Authors Guild has sent a letter to the U.S. Congress asking lawmakers to strengthen current copyright law. To stop dozens of millions in claimed losses, the authors want to increase liability for Internet service providers and make it mandatory for the companies to monitor and filter pirated content.
-
A 39-year-old Australian woman has been arrested and jailed in Abu Dhabi in the United Arab Emirates after she was found guilty of “writing bad words on social media”.
West Australian Jodi Magi remains in jail and it’s not known how long she will be held for.
Middle East correspondent Sophie McNeill reports.
SOPHIE MCNEIL: In February, 39-year-old Jodi Magi took a photo of a car in her apartment block in Abu Dhabi that was parked across two disabled parking spaces without any disability stickers.
-
Almost three-quarters of Sky’s internet customers have opted to block online pornographic websites after being forced to choose.
The company announced an automatic block on harmful sites six months ago in a bid to prevent children from stumbling across hardcore images and videos.
-
Powers to require online surveillance, remove content, block foreign web sites and shut down parts of the network are contained in the draft of a new Internet security law recently published by the Chinese government. Although these approaches have all been used in the past, their legal basis has sometimes been unclear. If approved, the new law will make it much easier for the Chinese authorities to force compliance from Internet service providers, which will have major knock-on effects for users in the country.
-
Privacy
-
Earlier this month, several news outlets reported on a powerful tool in the fight between those seeking anonymity online, versus those who push for surveillance and taking it away.
The tool, ProxyHam, is the subject of a recently canceled talk at DEF CON 23 and its creator has been seemingly gagged from speaking about anything related to it. Something’s off, as this doesn’t seem like a typical cancellation.
-
It’s no longer a surprise that the government is reading your emails. What you might not know is that it can readily read most of your email without a warrant.
Any email or social networking message you’ve opened that’s more than six months old can also be accessed by every law enforcement official in government — without needing to get a warrant. That’s because a key provision in a law almost three decades’ old allows this kind of access with a mere subpoena, which doesn’t require a judge.
-
UK Prime Minister David Cameron is pressing ahead with new powers that plan to stop people from sending any form of encrypted messages. Under the rather Orwellian “Draft Communications Data Bill” (nicknamed Snooper’s Charter) the legislation proposed would require ISPs and mobile providers to maintain records of each user’s internet browsing activity (including social media), email correspondence, voice calls, and mobile phone messaging services and store the records for 12 months.
-
In October 2012, then-New York Police Commissioner Ray Kelly announced a new initiative, called “Operation Crew Cut,” which would target gang activity by focusing on so-called street crews. Kelly doubled the size of the anti-gang unit to 300 police officers, assigned to the task of surveilling teenagers on Facebook. Many of these kids are under 18, some as young as 12, and just about all of them are black and brown, from low-income neighborhoods. The officers involved are encouraged to make fake Facebook profiles in order to spy on individuals’ Facebook statuses. The operation often entails reading private Facebook messages between friends and is sometimes coupled with phone and video surveillance. Soon press releases were coming out of the NYPD offices announcing dozens of alleged gang members had been arrested due to the Crew Cut initiative.
-
-
After the Edward Snowden revelations and the rise of deep web marketplaces, more and more people are using the anonymity network Tor to take back their privacy or access hidden sites, sometimes to break the law.
In response to this trend, surveillance tech company Hacking Team let slip last month that they were working on a solution to de-anonymize users of Tor for their customers, which include US law enforcement agencies and authoritarian regimes. After the massive Hacking Team leak last week, details of a work-in-progress system to monitor Tor and other encrypted traffic have emerged.
Called “Project X,” Hacking Team’s method proposes to re-route a target’s internet traffic before it enters the Tor network, so it could be monitored by the company’s clients. This is described in two PowerPoint presentations included in the 400 GB Hacking Team breach.
-
Civil Rights
-
A man has accused British Transport police of being “overzealous” and “ridiculous” after he was arrested for charging his iPhone using a socket on a London Overground train.
Robin Lee, a 45-year-old artist based in Islington, was handcuffed and taken to a British Transport Police station on Caledonian Road after his arrest for “abstracting electricity”.
-
A student who stopped to give money to a homeless person was handcuffed by a police officer who thought they were swapping drugs.
Apprentice George Wilson, from Wallasey, received a £5,000 pay out after police accepted he had been detained unlawfully.
A shocking recording of the incident reveals that when Mr Wilson denied he was behaving in a drunk and disorderly manner, as police had alleged, the officer replies: “That’s not how I’ll write it up pal.”
-
Investigative journalist Nicky Hager is set to make his case against a police raid on his Wellington home.
Mr Hager will appear in the High Court in Wellington today for a judicial review into how police obtained a warrant for, and undertook, the raid on October 2, 2014.
The 10-hour search of Mr Hager’s home was part of the police investigation into the hacking of Whale Oil blogger Cameron Slater’s emails, which were given to Mr Hager by anonymous hacker Rawshark and formed the basis of his book Dirty Politics.
-
-
Over six years, filmmaker Laura Poitras was searched, interrogated and detained more than 50 times at U.S. and foreign airports.
When she asked why, U.S. agencies wouldn’t say.
Now, after receiving no response to her Freedom of Information Act requests for documents pertaining to her systemic targeting, Poitras is suing the U.S. government.
In a complaint filed on Monday afternoon, Poitras demanded that the Department of Justice, the Department of Homeland Security, and the Office of the Director of National Security release any and all documentation pertaining to her tracking, targeting and questioning while traveling between 2006 and 2012.
-
More than a month after being sentenced to spend the rest of his life in prison, convicted Silk Road mastermind Ross Ulbricht is trying to keep his head up and help other inmates out, his mother Lyn said.
-
Intellectual Monopolies
-
Copyrights
-
Mega’s biggest shareholder, Shen Zhao Wu, has left the board of the file storage and encryption firm and transferred his stake to a Beijing-based Chinese national just days after a constitution re-write made it easier to go public, while Auckland businessman William Yan increased his influence over the company after an entity linked to his wife took a small shareholding.
-
The four founders of the piracy website, The Pirate Bay, have been acquitted on charges alleging criminal copyright infringement and abuse of electronic communications in a Belgian court. The court decided that because they sold the website in 2006 that they could not be held accountable for what the site was used for afterwards.
-
Four key Pirate Bay figures have a little something to celebrate this morning. After standing accused of committing criminal copyright infringement and abusing electronic communications, yesterday a Belgian court acquitted Gottfrid Svartholm, Fredrik Neij, Peter Sunde and Carl Lundström.
Permalink
 Send this to a friend
Send this to a friend
07.13.15
Posted in News Roundup at 9:17 am by Dr. Roy Schestowitz

Contents
-
Desktop
-
But the open source operating system Linux, with its kumbaya open-source development cycle – where anyone can use it for free, make changes and submit those changes to the group to be included in the main project – has also always attracted teens.
Business Insider recently interviewed two teens who were doing such cool work on the open source operating system that they came to the attention of the Linux Foundation, who told us about them.
-
Kernel Space
-
The Linux kernel 4.1.2 maintenance release has been announced by its maintainer, Greg Kroah-Hartman, a couple of days ago and brings updated drivers, security patches in various areas, as well as bug fixes and improvements.
-
Another week, another rc. What can I say? Call me boring, but that’s how this all works.
This is not a particularly big rc, and things have been fairly calm. We definitely did have some problems in -rc1 that bit people, but they all seemed to be pretty small, and let’s hope that -rc2 ends up having fewer annoying issues.
-
-
After having announced the release of Linux kernel 4.1.2 LTS and Linux kernel 3.10.84 LTS, Greg Kroah-Hartman published details about the forty-eighth maintenance release of the Linux 3.14 kernel series.
-
After having announced the release of Linux kernel 4.1.2 LTS, Linux kernel 3.10.84 LTS, and Linux kernel 3.14.48 LTS, Greg Kroah-Hartman has published details about the eighth point release of the stable Linux 4.0 kernel.
-
-
-
The High Performance File-System (HPFS) that was originally designed for the OS/2 operating system now has SSD TRIM support for its Linux kernel support while reading/writing from these old partitions.
While I don’t know of anyone off-hand still relying upon the OS/2 HPFS file-system support in Linux, it was updated in the post-merge-window (due to waiting on related patches, the original work was sent during the merge window but not committed) of the Linux 4.2 kernel merge window.
-
Graphics Stack
-
-
-
-
-
-
-
NVIDIA is announcing today the release of a new OpenACC Toolkit for enhancing GPU computing, but sadly it’s only free in the long-run for academia developers and researchers.
-
-
The latest patches sent out by this prolific open-source Mesa developer over the past few years add exposing sRGB visuals to the DRI Gallium3D state tracker, adding EGL_KHR_gl_colorspace support, adding support for the new features to the DRI2 render query extension, and other changes.
-
Benchmarks
-
After earlier this week looking at whether the open-source NVIDIA driver is fast enough for Steam Linux gaming, here are some benchmark results that compare the performance of the latest Nouveau Gallium3D driver code against the latest NVIDIA binary Linux graphics driver.
-
Applications
-
-
-
-
TigerVNC 1.5.0 brings IPv6 support for the VNC server, support for two passwords (full access or view only), syslog support in Xvnc, GnuTLS priority configuration, performance fixes, and other bug-fixes. This release is coming just a half-year after the introduction of TigerVNC 1.4.0 and its few point releases since that point.
-
Batch image processors are often underrated and don’t get the attention they deserve. But this type of software is worth getting familiar with. With batch image processing, a user can select a size or file type, and then convert all the selected images. This way, hundreds or thousands of images can be processed with just a few clicks. Unfortunately, there are not that many tools that do batch conversion really well. But these four tools save loads of time and effort.
-
Bugzilla 5.0 was released this week as their “most exciting new version of Bugzilla in our history” and “our best release ever” after being in development for more than two years.
-
QEMU 2.4.0-rc0 was just tagged in Git.
-
Instructionals/Technical
-
Wine or Emulation
-
Games
-
A few days ago Beamdog announced Siege Of Dragonspear, an expansion pack for Baldur’s Gate: Enhanced Edition.
For those not in the know: Baldur’s Gate: Enhanced Edition is a 2012 HD-update to the critically acclaimed role-playing game that was originally released in 1998. Baldur’s Gate is a top-down 2D isometric strategy-rolep-laying game wherein you control a party of one to six characters and attempt to bring peace to The Sword Coast region of Faerun. Baldur’s Gate Enhanced Edition was released for Linux.
-
Cossacks 3 was quite a surprise to be announced for Linux, and new details are slowly trickling in about this strategy game. We now have two short teaser videos showing them game off.
-
Desktop Environments/WMs
-
K Desktop Environment/KDE SC/Qt
-
Building local FLOSS communities isn’t that easy! It requires first communicating in a very clear and sincere way our motivations, the nature of possible contributions, their global impacts, and the technical and social benefits we potentially get back. Then, we need systematic and effective means to generate culture, support newcomers, identify their strengths, and help them to overcome the many barriers they usually face. Ultimately, we must keep such a social-technical organism alive, establishing mid- and long-term goals, learning from the ups and downs, and handling the challenges of building thriving communities in places with continental dimension such as Brazil and Latin America.
-
With more than a month remaining, my Google Summer of Code project has almost come to an end! KStars is now able to display all 88 western constellations. I want to thank my mentor, Jasem, for helping me by making a dialog box that would display constellation images with parameters in real time. This made my job simpler by a very large margin. Instead of using mathematical equations to figure out the ‘best fit’ for an image, I have simplified the task by simply noting down the RA/DEC coordinate pairs for ‘midpoints’ of constellations from Stellarium. This helped me figure out ‘where’ to translate the image in the sky map. Then I played around with the position angle, width and height for each image so as to ‘best fit’ the constellation lines. I had to do this repetitively for 88 consecutive times, but this was still a much simpler solution. Lastly I replaced all the 88 images with transparent backgrounds, so as to avoid cutting neighbouring images by the black background which was previously present. KStars looks good now, and I feel happy seeing the results! Here’s the new look of KStars!
-
-
GNOME Desktop/GTK
-
Additionally, yes… This is quite possibly a flame-bait article. I hope the community is better than that, because I do want to start a discussion and give feedback to both the KDE and Gnome communities. For that reason when I point out, what I see as, a flaw I will try to be specific and direct so that any discussion can be equally specific and direct. For the record: The alternative title for this article was “Death By A Thousand Paper Cuts”.
-
Gnote 3.16.2 “Imitation is the sincerest form of plagarism” has been released!
-
-
New Releases
-
The development cycle for Solus OS is powering on, and its developers are still making important improvements and changes to it. They recently upgraded the Linux kernel once more, and that’s just the tip of the iceberg.
-
Peter Ryzhenkov has had the great pleasure of announcing the release of his Point Linux 3.0 operating system, which is currently distributed in two editions, with the MATE and Xfce desktop environments.
-
Here it is, the second Release Candidate (RC) built for Kodi 15.0; freshly baked and ready to be served! Although we said that Kodi 15.0 is a “clean-up” edition, we still managed to squeeze in a couple of really nice features. So far we had around 1080 code change requests which were included since Kodi 14.2. This vast amount sums up in a pretty big list of improvements and clean-up being done by various developers for which we should show our everlasting gratitude. As such we will only highlight some of the bigger changes further on. Download link is also provided at the bottom.
-
-
The second release candidate to Kodi 15.0 “Isengard” is now available. Since Kodi 14.2 there have now been about 1,080 code changes so far towards this next major release.
-
-
Red Hat Family
-
-
Moreover, he said, he didn’t see the merit in attempting to pin the outage on Redhat (RHT – Get Report), the company that supplies most of the exchange’s software. “Redhat is really the best there is,” he said. “Everyone uses Redhat.” Whether or not someone was actually installing new Redhat software that caused the glitch, as multiple media sources were alleging Wednesday, Cramer ultimately believes that “we will end up thinking this was human error,” which is not a reason to start playing any investment in either direction.
-
If you ask a dozen software developers “What is DevOps?” you’re likely to get at least a dozen different answers. In this video, Red Hat professional services manager Patricia Bogoevici shares the benefit of her experience with Agile and DevOps over the past decade. She’s seen DevOps defined in a few different ways. Depending on the organization, some DevOps definitions may hold more value than others.
-
-
-
Red Hat have recently announced the global launch of Red Hat Certified Cloud and Service Provider. The new program has replaced Red Hat’s Certified Cloud Provider program and expands Red Hat’s cloud ecosystem to include and better support it’s users.
-
Debian Family
-
Derivatives
-
Canonical/Ubuntu
-
Canonical has released details in a security notice about a few NSS vulnerabilities that have been identified and repaired in Ubuntu 15.04, Ubuntu 14.10, Ubuntu 14.04 LTS, and Ubuntu 12.04 LTS, operating systems.
-
GCC is an important component in Linux distros and upgrading it is an important step. Any major changes to GCC (GNU Compiler Collection) can bring a host of problems, so any decision in this regard will care a lot of weight.
-
Once again, Kevin Gunn was more than proud to report on the latest work in the Unity 8 user interface, LXC for Xapps, and the next-generation Mir display server for the Ubuntu Linux and Ubuntu Touch operating systems.
-
Flavours and Variants
-
-
Mint 17.2 is well worth the upgrade, though much of what you want from it might be easier to get by just upgrading Cinnamon or MATE on their own. The Mint Linux upgrade guide tends to emphasize the wisdom on the old saying, “if it ain’t broke…” Those are good words to live by, but that said, I had no trouble at all upgrading from Mint 17.1. All you need to do is open Update Manager and head to the Edit menu, where you should see an option to “Upgrade to Linux Mint 17.2 Rafaela.”
Linux Mint 17.2 is an LTS release and will receive security updates until 2019. And until 2016, all Mint releases will continue to use the same base package system (Ubuntu 14.04). Maintaining desktop familiarity may never be easier.
-
-
The cherry ear net player, based on raspberry pi and HifiBerry Amp+.
-
Phones
-
Tizen
-
As we wave goodbye to the first half of 2015, we can report on the top 30 most popular apps from the Tizen Store of the first half of 2015. Much of these applications were the same as we’ve seen in May 2015 with the addition of games like Nitro Racer, Funny Face Changer, App Locker, Video Downloader and WhatsApp Status. Great progress has been made in the Tizen Store as its service coverage has recently expanded to 182 countries and the Samsung Z1 being released in India, Bangladesh and Sri Lanka, with over 1 Million handsets sold since January 2015.
-
Android
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
Believe it or not, it’s been 10 years since Google bought Android Inc., a startup that was quietly building software for cell phones. Rich Miner, a cofounder of Android Inc. and now a general partner at Google Ventures, tweeted early this morning that today is the 10-year anniversary of the deal.
-
As a platform, Android is quite flexible and part of that characteristic trickles down to Android Wear. The smartwatch-oriented OS has a few hidden quirks that developers are able to take advantage of to provide functionality otherwise unavailable officially. Sadly, that can sometimes lead to unpredictable behavior, sometimes even broken functionality. Good thing, then, that Google has chosen to officially adopt one such “hack”. According to insider sources, an upcoming major Android Wear update will finally bring official support to interactive watches faces. Plus, it could also introduce Android Wear to Android Wear communication.
-
-
-
-
-
-
-
BlackBerry and Google are having a total peanut butter and chocolate moment here. The two companies have just announced that they’re teaming up to create a more enterprise-ready version of the Android OS. The deal will see the heightened security features of BES12, BlackBerry’s enterprise device deployment service, integrated into Android’s 5.0 Lolipop build and Google Play for Work.
-
Genymobile started in France with an ambitious mission — becoming the unifying Android platform for the enterprise. The company just raised $7.7 million (€7 million) from Alven Capital, with Bpifrance also participating. It is currently working on three different products that makes using Android much easier when you are an Android developer, an IT manager or even an OEM. Genymobile works across all Android devices and makes Android’s well-known fragmentation issue a thing of the past.
-
First shown off at CES back in January, Sony’s 2015 TV line up is now available in Australia, with a heavy focus on 4K and the Android TV operating system.
Out of the 18 new TV models that Sony will sell in Australia, 14 will run on Android TV, while half will offer the 4K Ultra HD picture resolution of 3,840 x 2,160.
-
As we’ve seen countless times in the past, neither iOS nor Android is objectively “better” than the other — both platforms have pluses and minuses and there are legitimate reasons for people to choose either one. Business Insider‘s Antonio Villas-Boas had been a Galaxy S6 owner for a while who was curious enough to give the iPhone 6 a shot. However, he’s gone back to Android after just two weeks with Apple’s smartphone for three key reasons.
-
At OSCON 2013, Deb Nicholson, Community Outreach Director of Open Invention Network, gave a talk on how to delegate, like a boss. She’s returning to OSCON 2015 with a follow up talk on how to say no, like a boss. We caught up with Deb to get a preview of her upcoming talk, and we asked for a few tips on how to politely reject offers for additional work. If you have a chance to see her at OSCON, don’t miss it—her talks are always a nice mix of entertaining, with a heavy dose of practical advice.
-
Web Browsers
-
Mozilla
-
One month after having announced the release of Thunderbird 38.0.1, last week Mozilla provided us with a new maintenance release of one of the best open-source and cross-platform email clients for GNU/Linux, Mac OS X, and Microsoft Windows operating systems.
-
I’ve sat out of the discussion on Mozilla-Governance that has been ongoing over users disappointment with Pocket. I have seen other Mozillians dive in and defend the feature but I do not think this is helping at all. I read this post “Firefox, you’re supposed to be in my pocket, not the other way around” today and felt like it had many truths in it. I really do not know the rationale for adding Pocket as a default to Firefox but I assume there was some financial benefit for Mozilla involved.
-
Mozilla has rolled out a new version of its Firefox browser, an update that includes patches for four critical security vulnerabilities and several less-severe bugs.
-
-
Firefox developers are revisiting at how they build their web browser and how they can better utilize modern web technologies and in the process move away from XUL/XBL within their Gecko Engine.
-
SaaS/Big Data
-
For that reason there’s been a rising amount of interest in set of complementary open source technologies that promise to enable the development of data warehouse applications that are capable of processing massive amounts of big data in real time. While most of that data is stored in Hadoop, the three core open source technologies that will enable these applications are Storm, a real-time processing engine; Spark, a framework for building clusters; and Kafka, a distributed messaging system.
-
Oracle/Java/LibreOffice
-
In its headline, Business Insider says Oracle is using an “ugly ‘nuclear option.’” Fortune’s headline is a bit more understated: “Oracle reportedly wields audits, license disputes to push cloud agenda.” However genteel fortune’s headline, writer Barb Darrow cuts quickly to the chase: “Anyone who has ever met an Oracle sales person knows from a high-pressure sale.”
The story actually broke about a month ago, when Forbes asked: “Is Oracle Using Legal Pressure To Increase Cloud Sales?”
-
If you use Oracle’s database, try Postgresql.
-
In preparation for Windows 10, Oracle have released a major new version of VirtualBox. The 5.0 release supports Windows 10, OS X Yosemite and a bunch of other Linux Operating Systems. All platforms have easy to install packages included EXEs, DMGs, DEBs and RPMs.
-
CMS
-
Web architect Cleaver Barnes makes websites do interesting and useful things, which is to say he focuses on the code more than the visuals. His first major use of open source was Linux in the mid-’90s. It allowed him to do things that weren’t possible in Windows at the time. Since then he has worked building web apps with Java J2EE and other technologies.
-
BSD
-
The first beta of the upcoming FreeBSD 10.2 release is now available. Besides the generic FreeBSD 10.2-BETA1 spins for x86, x86_64, IA64, PowerPC, PowerPC 64-bit, and SPARC 64-bit, there are also ARMv6 spins for the Beaglebone, CuBox-Hummingboard, RaspberryPi B, and Wandboard.
-
-
Public Services/Government
-
Gaël Musquet co-founded in France the community OpenStreetMap (OSM) of which he was the first president. This project participatory, real geographical map Wikipedia launched in 2004 by Briton Steve Coast, has set a goal to create a digital map from voluntary contributions of thousands of Internet users.
-
Greenwald continues on “It uses the Apache web server and stores collected data in MySQL databases. File systems in a cluster are handled by the NFS distributed file system and the autofs service, and scheduled tasks are handled by the cron scheduling service.”
-
Openness/Sharing
-
Open Access/Content
-
-
Hyatt Hotels Corporation and Hyatt Hotels Foundation have partnered with Khan Academy to provide free access to quality online education to Hyatt’s employees, their families and communities.
-
-
Over three years ago, we wrote about a fast-growing boycott of the academic publisher Elsevier, organised in protest at that company’s high prices, its “bundling” of journals into larger collections, and its support for SOPA. Even though over 15,000 people eventually pledged not to work with Elsevier, the company is still going strong, making huge profits from the work of academics, and putting paywalls between the public and knowledge. Perhaps we should have guessed it would end like that. As we noted then, this was not the first or biggest boycott in the history of open access.
-
Open Hardware
-
Apparently London-based MyMiniFactory, a 3D printing model repository and so much more, agrees with the larger corporations which make up the new consortium in that current file formats just are not suited for the future of the industry. Where they may disagree however, is just how the new format should be set up.
-
Cadwalladr’s worry that the MPs will become seduced by Westminster has worried me too.
-
Science
-
A rare star system containing five stars, known as a quintuplet, has been discovered. This quintuplet system is 250 light-year away in the constellation Ursa Major (looks like a saucepan). The system is composed of two binary stars (two stars that orbit each other) and a lone companion.
-
Health/Nutrition
-
Afghan Brigadier General Abdul Sama was accused recently of smuggling over 40 pounds of heroin.
It should come as no surprise that an Afghan general was caught smuggling heroin, the surprise is that any high official in that country should be charged with a crime for profiting from the trade in illegal drugs while under the watchful eye of American forces.
-
After all, US officials picked him to be Afghanistan’s first post-Taliban president, armed and financed him to launch an uprising after 9/11, helicoptered him away from imminent capture after one clumsy foray inside Afghanistan in mid-October, reinserted him a few weeks later to march on Kandahar successfully, and finally foisted him on the rest of the Afghan political class at the United Nations-sponsored conference in Bonn in December 2001 as the leader they could not afford to reject.
-
Security
-
-
-
Last week FBI Director James Comey testified before a Senate Judiciary Committee about the use of encryption among terrorist groups. For anyone who understands the critical role that encryption plays in the Internet and our private data networks, many of the exchanges between Comey and the senators on the panel were not only revealing, but rather disturbing.
-
Spyware service provider Hacking Team orchestrated the hijacking of IP addresses it didn’t own to help Italian police regain control over several computers that were being monitored in an investigation, e-sent among company employees showed.
-
Try to cast your mind back to 2010/2011, BlackBerry maker, RIM, and India were at loggerheads after the state in India wanted access to RIM’s servers. India managed to get RIM to allow access to consumer messaging services but they wouldn’t give them access to the BlackBerry Enterprise Server. Documents from the Hacker Team leak now show that Hacking Team were considering a proposal to the Indian government to better intercept data sent through RIM’s servers.
-
-
-
Two major breaches last year of U.S. government databases holding personnel records and security-clearance files exposed sensitive information about at least 22.1 million people, including not only federal employees and contractors but their families and friends, U.S. officials said Thursday.
-
It has almost been a month since the Office of Personnel Management (OPM) infiltration was made public and shockwaves of the hack reverberates in Washington, D.C. and beyond. In response, officials have shut down the E-QIP background investigation system. Security and privacy professionals seem united in their demands that OPM director Katherine Archuleta be held accountable for the security lapses in the organization. Commenter after commenter diagnoses the problems in our systems, institutions, and infrastructure, demanding accountability and change. While we continue to extract negatives from the story of the OPM hack, three lessons emerge that might give us hope for a secure future.
-
Torture/Secrecy/Aggression
-
The second—and more horrifying—thing we learned in June was that the CIA crafted its own internal regulations that permitted the agency’s director to override all international law in its torture practices, and to go the furthest ends of sadism: experimentation on human beings. Again ignored by the U.S. media, it took the Guardian from London to publish the document “AR 2-2, Law and Policy Governing the Conduct of Intelligence Activities.”
-
On a trip to Iran in 1977 a bazaar vendor told Stephen Kinzer: “we used to have a democracy here but then you came and took it away from us.” As an American, Kinzer explains, a democracy in Iran did not fit with his preconceived ideas about the country so he set about investigating the vendor’s comments. He found that very little had been written on the subject of its downfall in 1953.
A new graphic novel Operation Ajax, to which he has contributed the foreword, helps to fill this information gap. In a series of comic strips author Mark Seve and illustrator Daniel Burwen reconstruct events that led up to the CIA’s first successful regime-change operation – removing Iran’s democratically elected Prime Minister and reinstating power to the authoritarian Shah, Mohammed Reza Pahlavi.
It’s 1951 and an ocean of oil is sitting under Iran. Britain may have controlled Iranian oil exports for years but now Mohammed Mossadegh is Prime Minister, the Ayatollah is his ally, and they both agree that Iran should be for Iranians. Nationalist sentiment prevails and Mossadegh nationalises Iran’s oil but not without bringing about the wrath of the UK who are on the brink of invasion to get back their share.
-
At America’s behest, some have been held and tortured at proxy sites run by foreign governments, and they have been incarcerated at US military prisons such as Bagram, Kandahar, and Guantánamo.
-
From a window in his rental home in Arlington, John Kiriakou can glimpse his old life: the peaked roof of the dream house he and his wife, Heather, built a decade ago in happier times. Not that Kiriakou shows signs of unhappiness now. His toddler son leads me past a wall hung with welcome home signs to another window overlooking a tree-lined back yard where Kiriakou has spent hours recently watching his kids play on a trampoline.
What the decorated CIA officer turned convicted felon doesn’t add is that for months his yard was as far he could go without permission from the Federal Bureau of Prisons.
-
Step one in the unhealthy pursuit of power is the dehumanization of “the enemy.” The consequences of what we do after that will always haunt us.
-
US authorities have still not agreed to hand over an uncensored report into CIA torture to help the police investigation into the use of Scottish airports for extraordinary rendition.
Lord Advocate Frank Mulholland, Scotland’s top prosecutor, has confirmed he is “still awaiting the outcome” of a request for an un-redacted copy of the US Senate study.
SNP MSP Kevin Stewart said last night it was “vital” that the secret document was sent to Scottish officers.
The police launched an inquiry in 2013 after the Press and Journal revealed new evidence that CIA planes had used Inverness, Aberdeen and Wick airports during a period when terror suspects were being illegally detained, transferred and tortured at various locations around the world.
-
-
Professional body admits it may have contributed to violations of human rights after scathing internal report into post 9/11 collusion with Pentagon
-
The largest association of psychologists in the United States is on the brink of a crisis, the Guardian has learned, after an independent review revealed that medical professionals lied and covered up their extensive involvement in post-9/11 torture. The revelation, puncturing years of denials, has already led to at least one leadership firing and creates the potential for loss of licenses and even prosecutions.
-
Senior members of the leading professional association for U.S. psychologists collaborated with the CIA and the Pentagon to bolster the credibility of harsh interrogation techniques used against terrorist suspects in the aftermath of the September 11 attacks, according to a report released Friday.
-
The report documenting the role of the American Psychological Association (APA) as an embedded accomplice to torture during the War on Terror is important for its detail, but not for its novelty. The essence of this story has been known for eight years despite APA denials, euphemisms, double-talk and whitewashing; the report simply underscores the truth of what many of us have been saying all along.
-
Earlier this year, a report put together by a human rights investigator and several prominent psychologists documented evidence that leaders of the American Psychological Association, contrary to the organization’s claims, had collaborated with CIA to help bolster the legality of the “enhanced interrogation” post-9/11 torture program.
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
-
The National Security Archive has posted several newly available documents Monday, one of them an account by Charles Duelfer of the search he led in Iraq for weapons of mass destruction, with a staff of 1,700 and the resources of the U.S. military. Duelfer was appointed by CIA Director George Tenet to lead a massive search after an earlier massive search led by David Kay had determined that there were no WMD stockpiles in Iraq. Duelfer went to work in January 2004, to find nothing for a second time, on behalf of people who had launched a war knowing full well that their own statements about WMDs were not true.
-
The fall of Srebrenica in Bosnia 20 years ago, prompting the worst massacre in Europe since the Third Reich, was a key element of the strategy pursued by the three key western powers –Britain, the US and France – and was not a shocking and unheralded event, as has long been maintained.
-
The CIA operates armed drones to engage in targeted killing operations in Pakistan, Yemen, and Somalia. That is known. But, to borrow from former Secretary of Defense Donald Rumsfeld’s iconic statement, is it a “known known” or a “known unknown”? Known knowns are things we know we know, whereas known unknowns are things we know we do not know. The third ingredient of Rumsfeld’s rhetorical mélange is the “unknown unknowns”—things we do not know we do not know. The CIA wishes its drone program was an unknown unknown. It strived for years to keep this public secret protected by offering “neither confirm nor deny” responses to journalists’ queries.
-
-
Units of British SAS troopers are in Syria, backing up forces in the region targetting Islamic State (Isis).
-
-
ISIL, by its actions, is still trying to pull Western powers into Syria and, in the meantime, it continues to kill as many Syrians as it can. There are a number of groups affiliated with ISIL who kill people in Yemen and Nigeria as well. Recently, ISIL launched another series of attacks and killed scores of people on the same day in France, Tunisia, Kuwait and Egypt’s Sinai Peninsula. So everyone knows that ISIL is no longer just a Syrian affair and the entire Mediterranean basin is under attack. In order to understand the objectives of ISIL, one thus has to look into the balances of the east Mediterranean.
-
The United States has a reported military presence in at least 150 countries. Indeed, it could be said that the sun never sets on the American empire.
Some outposts of that empire are supposed to be kept secret, however, as they are operating in countries placed off limits by treaty or by U.S. law. Somalia is such a place, but that hasn’t stopped the U.S. Defense Department from setting up bases and deploying troops in that country.
-
-
A US non-governmental organization – US Global Drones Watch – says Washington must refrain from staging a unilateral drone campaign in Somalia.
Medea Benjamin, founder of Global Drones Watch, said on Friday drone attacks in Somalia and the Middle East should be conducted through the United Nations and the African Union.
“While they may be attacking people who deserve to be attacked, I’m not saying that I like Al-Shabab, but I think it should be done through the UN and the African Union, not unilaterally by the United States,” Benjamin told Sputnik News.
-
By and large, the victims of US drone strikes are unnamed, though one AQAP leader was reported killed last week, which appears to have further emboldened the drone program to continue despite the lack of US spotters on the ground to tell what they’re shooting at.
-
Government spokesmen insisted everyone claimed was a militant.
-
There was no end to the White House’s and Contra’s kill list. In fact, 60,000 Nicaraguans were killed. A sovereign state, Nicaragua, was murdered, too, as the U.S. spent millions of dollars in engineering elections, threatening the nation with preemptive wars, and by finally militarily occupying the nation with terrorists. Exhausted, Nicaraguans eventually voted for the U.S.-backed centre-right National Opposition Union. They had had enough. Physically and psychologically terrorized, they wanted the White House’s kill list to end.
-
An unmanned Israeli reconnaissance drone crashed in the waters near northern Lebanon’s port of Tripoli Saturday, the Lebanese army and a security official said.
In a statement, the army said the drone crashed at 8.30 a.m. local time (0530 GMT) Saturday. It gave no other details but published photos that showed the aircraft largely intact in the waters and then on land after it was taken out.
It had a Jewish Star of David and Hebrew writing on it.
-
-
-
-
-
The Palestinian Bedouin women were walking away from their ramshackle farm along a lonely dirt track beside an orchard in broad daylight when their bucolic surroundings were transformed into a killing zone during last summer’s Gaza conflict.
-
One year ago, on July 7, 2014, Israel launched “Operation Protective Edge,” a massive assault on the Gaza Strip. For 51 days, Israel bombarded Gaza with more than 6,000 airstrikes. Many of them hit residential buildings. Tawfik Abu Jama, a father of eight, told UN investigators, “I was sitting with my family at the table ready to break the fast. Suddenly we were sucked into the ground. Later that evening, I woke up in the hospital and was told my wife and children had died.”
-
Protestors in Broadstairs have swarmed a drone factory, taking to the roof, with one campaigner locking himself to the gate.
One of the protestors, from a group called Block the Factory Kent, said: “We are at Instro Precision Ltd on the Pysons Road industrial estate. The company is a manufacturer of lethal unmanned drones. Today is the one year anniversary of an assault on Gaza by the Israeli air force , which killed over 2,200 Palestinians.”
-
-
They say they have targeted Instro Precision Ltd on the Pysons Road industrial estate because the company is a manufacturer of lethal unmanned drones that were used by Israel to kill Gazans this time last year.
-
-
Max Blumenthal’s latest book, The 51 Day War: Ruin and Resistance in Gaza, tells a powerful story powerfully well. I can think of a few other terms that accurately characterize the 2014 Israeli assault on Gaza in addition to “war,” among them: occupation, murder-spree, and genocide. Each serves a different valuable purpose. Each is correct.
-
I think Operation Cast Lead in 2008-2009 promoted a real shift in opinion within the political left in the U.S. But during that war, we saw the Israeli government, the government press office which hands out credentials to journalists, bar all journalists from entering the Gaza Strip. And so journalists weren’t able, except for the Palestinian journalists who were living in the Gaza Strip, to actually witness the violence up close. And this is disproportionate violence targeting civilians in a way we had never seen before in the Gaza Strip.
-
The 2014 Israel-Gaza conflict began on 8 July. By the time the bombardment ceased 50 days later, around 2,200 Palestinians had been killed, the majority of them civilians, including an estimated 500 children. On the Israeli side, 66 soldiers and six civilians lost their lives in Hamas attacks.
-
…drone warfare as the Obama administration’s signature approach to military engagement.
-
Like his predecessors, President Obama is relying heavily on aerial bombardment to wage war…
-
Advocates for even more war in the Middle East apparently have a new strategy for defeating Isis: allow the US military to kill more civilians. If you think I’m exaggerating, just read their deranged and pathological arguments for yourself.
It began in late May when the New York Times reported that both Iraqi and American officials started complaining the US was too worried about killing civilians, suggesting that the Obama administration shouldn’t be worried that indiscriminately killing innocent people might turn the Iraqi population even more against the US than it already is. (Nevermind that it could be considered a war crime.) As the Times’s Eric Schmitt wrote: “many Iraqi commanders and some American officers say that exercising such prudence with airstrikes is a major reason the Islamic State, also known as Isis or Daesh, has been able to seize vast territory in recent months in Iraq and Syria.”
-
-
-
A new truce in Yemen was pierced within an hour as Saudi-led airstrikes hit targets in the capital Sanaa and the southwestern city of Taiz following reports of ground movement and fighting, security officials said.
-
Aid groups are warning Yemen is on the brink of famine as the Saudi-led attack intensifies. More than 3,000 people, including 1,500 civilians, have died in Yemen since the U.S.-backed Saudi offensive against the Houthi rebel group began on March 26. According to the United Nations, 80 percent of Yemen’s 25 million people are now in need of some form of humanitarian aid, and more than one million Yemenis have fled their homes, as a Saudi naval blockade has cut off food and fuel supply lines for much of the country. Monday was reportedly the deadliest day since the fighting began, with over 176 people killed, including 30 people at a market in the northern province of Amran and 60 people at a livestock market in the southern town of al-Foyoush. To talk more about Yemen, we are joined by two guests. Farea Al-Muslimi is a co-founder of the Sana’a Center for Strategic Studies in Yemen. He is currently a visiting scholar at the Carnegie Middle East Center in Beirut. And here in New York is Matthieu Aikins, award-winning foreign correspondent. He’s a fellow at The Nation Institute. He was in Yemen last month reporting for Rolling Stone magazine.
-
A test pilot has some very, very bad news about the F-35 Joint Strike Fighter. The pricey new stealth jet can’t turn or climb fast enough to hit an enemy plane during a dogfight or to dodge the enemy’s own gunfire, the pilot reported following a day of mock air battles back in January.
-
An exhibition of four quilts, part of the U.S. Drones Quilt Project in memory of civilians killed in drone attacks, will be on display at the Asheville Area Arts Council in the Grove Arcade. The exhibit runs Monday, July 13-Saturday, July 25.
-
-
A little more than a year ago, President Obama asked Congress for $500 million to train and equip some 15,000 opposition fighters in Syria, arguing that the best way to defeat Islamic State terrorists was to arm local forces.
The war against Islamic State “will not involve American combat troops fighting on foreign soil,” Obama promised. “Instead, we must strengthen the opposition as the best counterweight to extremists.”
-
The U.S. has begun training only 60 fighters to take on the Islamic State in Syria, Defense Secretary Ash Carter acknowledged in a heated hearing of the Senate Armed Services Committee Tuesday morning. And not only is the number “much smaller than we hoped for at this point” — three months into the program — but the U.S. has not yet determined what it will do when those fighters are attacked by the forces of Syrian President Bashar al-Assad, Carter said.
-
US label “moderate” is an important designation in Syria because it makes a group eligible for training and support…
-
As negotiators from Iran and six major powers struggle to ink a nuclear deal this week, covert CIA agent-turned-novelist Valerie Plame Wilson is taking to social media from her Santa Fe home to promote an agreement as an alternative to armed conflict.
“Holding my breath for a deal,” Plame Wilson tweeted to her 16,800 Twitter followers on Monday, before negotiators announced they were close but needed more time. She added a link in the tweet to a New York Times article about new high-tech tools that would help inspectors charged with monitoring Iran’s nuclear program if a deal is struck.
-
ISIS has been raising presence in the Caucasus. On June 23, 2015 ISIS announced the creation of a new governorate, called Wilayat Qawqaz in the Russias North Caucasus, after several senior militants in the area pledged allegiance to ISIS. ISIS has been setting conditions to establish this governorate in support of its regional expansion campaign since at least January 2015. Declaration of Wilayat Qawqaz followed the circulation of a Russian-language audio statement on Twitter on June 21, in which supporters of ISIS in the regions of Dagestan, Chechnya, Ingushetia, and Kabarda, Balkaria and Karachay pledged allegiance to ISISs leader Abu Bakr al-Baghdadi. These areas represent four of the six subdivisions that constitute the al-Qaeda-affiliated Islamic Emirate of the Caucasus terrorist network. Militants in these four most frequently conducted domestic attacks in support of the IECs stated goals of establishing a Caucasus emirate under sharia law and waging global jihad. The two IEC subdivisions where supporters have not formally pledged to ISIS are Cherkessia and Nogay steppe.
-
In the 1980s, President Reagan funded and armed Islamic fundamentalists to defeat a Soviet-backed secular regime in Afghanistan. Now, one of those ex-U.S. clients is throwing his support behind the brutal Islamic State, a lesson about geopolitical expediency, writes ex-CIA analyst Paul R. Pillar.
-
David Petraeus, former CIA director and retired Army general, urged President Obama in an op-ed Wednesday to reconsider his plan to withdraw most U.S. troops from Afghanistan by the end of next year.
-
Before and after July 4, 2015, genocide for profit (In speculative investment driven Western Colonialism never was a different reason for it) is taking place thanks to participating and cooperating Americans in uniform and CIA in Afghanistan, Iraq, Syria, Libya, Somalia and Yemen, and surely further lives are being planned to be taken in the Ukraine and Venezuela and elsewhere as profits therefrom appear sure.
-
This film is what helped ferment a Pentagon perception of the entertainment industry as useful for this sort of promotion of core values – and so perhaps we can expect more of the same, but with a necessary, modern warfare drone factor for the sequel.
-
In the charming new animated movie, “Inside Out,” we are taken inside the head of Riley, an 11-year-old girl, to meet characters representing five of the six emotions that psychologists have characterized as universal: happiness, sadness, fear, anger and disgust. (The sixth emotion, surprise, was omitted, perhaps because movie producers, like most business people, hate surprises.) Without revealing any spoilers, suffice it to say that in Riley, as in the heads of most real girls her age, Joy cedes some mindshare to Sadness, Anger, Fear and the other, less cute members of the emotional coterie.
-
Hersh’s account has been rejected by some on the grounds that he relies on unverifiable anonymous sources. This investigation conducts a systematic review of open sources and key journalistic reports relevant to the events leading up to the bin Laden raid.
While much corroboration for Hersh’s reporting is uncovered, elements of his account and the Official History contradict a wider context of critical revelations disclosed by many other pioneering journalists. When that context is taken into account, a far more disturbing picture emerges.
-
“These warnings are an attempt by the government to show it is monitoring trends and believe that by issuing a warning they hope to either have people help deter possible attacks through vigilance or perhaps deter terrorists for carrying out a plot because of the increased attention,” Patrick Skinner, Director of Special Projects at The Soufan Group, wrote to ThinkProgress by email. “The warning might be raised after several plots have secretly been disrupted simply out of an abundance of caution or to see the reaction of groups under monitoring.”
Since 9/11, the FBI and DHS have released a number of terror warnings that never materialized into attacks. Experts worry that such warnings risk inspiring a culture of fear among Americans.
“Terrorist groups, and none more so than ISIS, feed on publicity and fear,” said Skinner. “Supporters are more motivated and energized when societies are seen reacting to the perceived menace of the group. Fund raising, recruitment, and overall energy all increase when a society in effect trembles before terrorism. Generic terror warnings are free advertisement for these groups.”
-
The warnings reflected a general consensus among counterterrorism officials that this Fourth of July was among the most dangerous periods we have seen since 9/11.
-
Across the Mediterranean Sea, American NSA agents stationed in Europe intercept a congratulatory radio transmission. “The Americans just shot down a UN plane,” an accented voice says.
The next morning, civilians approach the wreck—some say they see a fuselage riddled with artillery and a man struggling for life. An investigator observing the bodies notes bullet wounds. The plane’s lone survivor stays alive just long enough to describe a series of explosions before the craft went down.
-
During the Six-Day War in 1967, Israeli warplanes and warships tried to sink the USS Liberty, killing 34 of the spy ship’s crew. Afterwards, U.S. and Israeli officials excused the attack as an unfortunate mistake and covered up evidence of willful murder, as ex-CIA analyst Ray McGovern explains.
Israel’s chokehold over U.S. politics and politicians has been so powerful for so many decades that this obvious reality is routinely denied, a collective gagging of the truth that is itself a measure of how strong the Israeli grip is.
-
For most of the ’80s Michael Levine was a high-voltage player in America’s drug wars, until he became convinced that the government’s efforts were misguided and useless.
-
Guests will get a chance to see how secrecy and subterfuge were used by the KGB, Stasi and CIA, with about 250 objects and artifacts related to spy gear and documents, according to a news release.
-
-
While this controversial hype on establishing a new era in U.S.-Cuba relations sounds promising, there is much history and a factual basis to believe that the players in this agreement may have easily duped each other and created a false sense of security by quite possibly ignoring the intelligence and true motives of a knee-jerk and intentionally weak quid pro quo agreement.
-
An Iraqi fighter jet accidentally dropped a bomb over a Baghdad neighbourhood on Monday, killing at least 12 people on the ground, Iraqi officials said.
-
A lover’s eyes compared to a drone strike, a smile to a suicide bomb and lips to fire.
The violence of Pakistan’s bloody insurgency has been injected into catchy pop lyrics after more than a decade of war against Islamists opposed to all forms of song and dance.
-
I show how in actual operational conditions, drones do not see very well; I show that “high value targeting,” i.e. assassination, which is their principal lethal function, is entirely counterproductive, making our enemies stronger; I show how drones, with their ability to send video of a distant battlefield to a president’s desk, give our leaders a dangerous illusion of knowledge and control; I show how much of all this is a racket to line the pockets of contractors.
-
A decade later, many Britons have indeed died at the hands of terrorists overseas, from the two aid workers beheaded by Islamic State in 2014 to the 30 who were killed in the Tunisian beach massacre. But on the home front, there is one remarkable statistic that stands out: just one fatality at the hands of Islamic terrorists in the UK since 7/7.
That death was British soldier Lee Rigby, hacked with a cleaver as he returned to barracks in Woolwich, south-east London.
-
It’s not terrorism that should keep you awake at night, it’s the way our governments respond to the terrorist threat, says Alex Proud
-
Greg Rolles, who holds a Master’s degree in International Relations said “for first time in Australia, unmanned aerial systems (drones) responsible for 1000s of civilian deaths will be used in the war ‘games’. There are serious unanswered questions about this technology”
“The ADF has refused to say whether these unmanned aircraft, each capable of carrying a 250kg payload, will be armed as they fly over Rockhampton and the surrounding region.”
“I am also walking because 200 years ago, Shoalwater Bay belonged to the Indigenous Peoples of the area. It’s one of Australia’s first war sites, with European settlers attempting to kill off or remove the Darumbal People. I will pilgrimage into Shoalwater Bay to remember those First Peoples who lost their lives and culture on this land,” said Greg.
-
Transparency Reporting
-
SY: In your conversation with John Pilger, you summarized the philosophy behind WikiLeaks as thus, “The goal is justice, the method is transparency.”
As far as I understand, WikiLeaks’ philosophy is that spreading knowledge can provoke change. Knowledge will lead to organized political action by the public, and such actions will ultimately achieve justice. But there hasn’t really been a strong organized action as a result of information made available through WikiLeaks. Has the public reaction been a let down in some way?
JA: Let’s say the goal is justice, and through a long study of history of how justice is achieved and how justice is repressed, we know that knowledge is often the key ingredient. Or to put it in another way, the elimination of ignorance is often the key ingredient in the liberation of individuals, and in preventing people and organizations from doing dumb things as well. Sometimes people make mistakes and are ignorant of the damage they are doing.
You are lucky if once every two or three years you can get the population together en masse to demand something … very lucky. Society is complex, and there are many things going on. So it will never be the case that society as a whole can address the frequent injustices that happen everyday. Additionally, it is only when the mass comes together, that the masses have any power. The masses are powerless by definition.
We have always operated on the basis of playing various interests off one another, in terms of when our material is revealed. You can have political parties that are rivals, and factions within a political party that are rivals, and rivalries between states and intelligence agencies — that are affected by this kind of information. These kinds of rivalries can be used in important ways.
-
First, I want to express my deep appreciation to you for signing the petition that urged the government to drop charges against my husband, Jeffrey.
“As a whistleblower, former CIA officer Jeffrey Sterling went through channels to inform staffers of the Senate Intelligence Committee about the ill-conceived and dangerous CIA action known as Operation Merlin,” the petition said.
Unfortunately, the government went ahead with its prosecution. After a trial with huge flaws (see background links below), the jury convicted Jeffrey. Last month, he began serving a three-and-a-half year prison sentence.
-
Cohosts Mickey Huff and Peter Phillips discuss the Importance of Whistleblowing and Whistleblower Protection.
-
Do note that at the bottom of that page, you can click on ‘English’ to post a request for the document in English—javascript is required and I failed to note any significant difference.
-
Thanks to yet another FOIA lawsuit, more evidence is being produced that suggests certain federal agencies employ labyrinthine systems that seem deliberately designed to keep requesters as far away as possible from responsive documents.
-
Environment/Energy/Wildlife
-
A conflicting report from USA Today, citing data from the International Shark Attack File at the Florida Museum of Natural History, says that the 23 attacks recorded thus far in 2015 is slightly ahead of pace for the average 30 to 40 annual attacks in the United States.
-
Tony Abbott has been warned he is putting international investment at risk after ordering the $10 billion Clean Energy Finance Corporation not to finance new wind power projects.
Read more: http://www.smh.com.au/federal-politics/political-news/tony-abbott-has-escalated-his-war-on-wind-power-20150711-gia3xi.html#ixzz3fh3sx9pS
-
Eric Mathur is sitting in the backseat of an SUV, rolling south through the Arizona desert. Tall, dark, and bald, he’s dressed for a day under the sun. His linen shirt is open at the top, revealing a thick gold chain around his neck. A cream-colored Panama hat rests on his knee.
-
Finance
-
Why punish Jamaican taxpayers for governments’ abuse of usurped, unchecked, anti-democratic powers?
-
PR/AstroTurf/Lobbying
-
“But there’s Bernie!” my liberal friends are frantically screaming. “He’s a socialist. He loves the little people. He’ll save us from the jaws of the republican machine. You’ve gotta register to vote and work for Bernie.” But I can think of at least three good reasons not to embrace the donkey in order to subdue the elephant. 1. Bernie can’t win. Hillary is the chosen one. 2. Bernie is a card-carrying member of the military-industrial establishment who votes for so-called defense bills at every opportunity. 3. If hell froze over and Bernie happened to win, and Bernie happened to be way better than he appears, and was indeed the potential savior of the USA…well, see the scenario concerning spilled brains on the leather seat of an SUV in paragraph one above. And that ain’t gonna happen because…altogether now: He has owners.
-
Censorship
-
A few weeks ago the RIAA obtained a preliminary injunction requiring Cloudflare to terminate services to all domains that use “Grooveshark” in their name. As a result, the popular CDN service was forced to disconnect “groovesharkcensorship.cf,” a site specifically set up to protest overbroad censorship. However, the trouble wasn’t all for nothing.
-
An aide to Vladimir Putin has told Russians to leave Facebook after the head of the country’s telecommunications regulator was censored by the social network. As the Moscow Times reports, Maxim Ksensov was given a 24-hour time out after posting an ethnic slur for Ukranians on his personal page. The paper believes that the word has now been blacklisted by the service and will be instantly deleted if it’s found. In response, Putin aide Igor Shchegolev has instructed locals to abandon Facebook in favor of Vkontakte, its homegrown alternative.
-
Too often of late I’m reminded of George Orwell’s novel “1984.” Inside the Ministry of Truth, Winston Smith works each day erasing history. Smith’s job is to carefully delete people and events from newspaper articles that are not to Big Brother’s liking.
The state-sponsored censorship Orwell imagined more than half a century ago did not disappear with the Berlin Wall. It happens today on a larger scale than ever in China, Russia, Iran and other countries where government-sponsored “trolls” scrub the Internet of inconvenient events, such as the Tiananmen Square Massacre and popular protests in Hong Kong, Moscow and Tehran.
-
Many Internet users around the world are aware of the censorship regime of the Chinese government — this is not a well-kept secret. Yet Chinese government officials have denied on many occasions the government’s role in filtering and blocking content from overseas web platforms such as Twitter and Facebook. Among the other things, this means that there is actually no channel by which citizens or businesses can challenge government censorship online. One can pursue legal action against Internet service providers, as in the court case against China Unicom for its service failure to access Google’s online platform, but not against the government itself.
-
The Film Censorship Board (LPF) recently issued new guidelines, stating that all local production houses had to censor any lewd or extreme content in their shows.
It is learnt that the fresh guidelines were made after members of the public complained to the LPF about a scene involving a married couple in an ongoing local Malay drama series.
-
Reportedly, complaints were lodged by the public to the LPF about a local Malay drama that depicted a married couple in a bedroom scene, according to The Rakyat Post. The complaints caused by said drama, “Maid”, prompted the LPF to introduce the new guidelines.
-
-
Male nipples are having a moment, and it’s surprisingly all in the name of freeing the female body from censorship.
Last June, artist Micol Hebron posted an image of a male nipple on Facebook and suggested that women replace their nipples with the template to make them acceptable for social media.
-
The headline related to the controversial 10-second scene included in the Royal Opera House’s new four-hour production of Rossini’s Guillaume Tell in which a young girl is gang raped by army officers. Met with angry boos by its opening night audience, it was enough for the Evening Standard to give it front page coverage.
It’s often said that controversy sells tickets, but this is a dangerously misrepresented expression. More often than not, the controversy isn’t to do with the plot (as it is in Guillaume Tell) but stems from some social faux pas. In 1980, The Romans in Britain became a cause celebre in part because of its depiction of homosexual rape, but more because of its subsequent legal battle with Mary Whitehouse.
-
The Hungarian parliament has voted yes to plans to allow the government and other public authorities to charge a fee for the “human labour costs” of freedom of information (FOI) requests this week, as well as granting sweeping new powers to withhold information. It just needs the signature of President Janos Ader before it becomes law.
-
When the highest government official asks the public broadcaster whose side it is on, it inevitably makes me think of the Philippine media under Ferdinand Marcos (pictured), when the only side to be on is his. Broadcasters as well as the press came to anticipate direct interventions from Malacañang Palace; eventually, none had to be made.
[...]
If the ABC leant any way at all, it probably leans right. An empirical study of partisanship in Australian media outlets shows that over the period 1999-2007, ABC TV News had a statistically significant slant toward the Coalition. John Howard was the Prime Minister during that period, suggesting that maybe the issue isn’t ABC bias but dismal government performance. During the tumultuous Rudd-Gillard years, Labor members were known to routinely complain that the ABC was giving the Opposition a free pass.
In other words, it is not the weaknesses of the ABC that have been illuminated by the careless remark of a dubious character on its panel show. In their reaction to the incident, members of the federal government have shown theirs.
-
Privacy
-
Spiegel reported Friday that it had filed a legal complaint with its federal prosecutor’s office over the suspected surveillance.
-
Just a year ago, Washington was revealed as trying surreptitiously to gather information via surveillance of German government leaders. Additionally, the CIA endeavored in a particularly clumsy manner to recruit a German government career official.
-
Newly Available Documents Trace Evolution of Spy Units through Obama Administration
-
-
A woman has told how she has been forced to change her name by deed poll to match her “ridiculous” Facebook pseudonym after being locked out of her account.
-
Civil Rights
-
Yet some US policies and practices continue to violate the traditional norms of justice, law and democracy that Americans applauded in July 4th speeches.
-
A California man was investigated by police last week after taking photographs of his wife in their front yard.
-
In late June 2013, Christopher Catrambone, a garrulous 31-year-old American entrepreneur who had spent almost a decade travelling the world to build a multimillion-dollar company, decided to take a break. Tangiers Group, which Catrambone runs with his Italian wife Regina, provides insurance in conflict zones – to US military subcontractors, NGO workers, journalists and missionaries, among others. The business, rooted in such war-wrecked countries as Iraq and Afghanistan, was flourishing. But that summer, Catrambone decided, the company could take care of itself for three weeks.
-
Intellectual Monopolies
-
Copyrights
-
Earlier this week the Ninth Circuit heard oral arguments in the appeal of Lenz v. Universal. This was the case where Stephanie Lenz sued Universal because Universal had sent YouTube a takedown notice demanding it delete the home movie she had posted of her toddler dancing, simply because music by Prince was audible in the background. It’s a case whose resolution has been pending since 2007, despite the fact that it involves the interpretation of a fundamental part of the DMCA’s operation.
Permalink
 Send this to a friend
Send this to a friend
« Previous Page — « Previous entries « Previous Page · Next Page » Next entries » — Next Page »
Further Recent Posts
- Watchtroll a Fake News Site in Lobbying Mode and Attack Mode Against Those Who Don't Agree (Even PTAB and Judges)
A look at some of the latest spin and the latest shaming courtesy of the patent microcosm, which behaves so poorly that one has to wonder if its objective is to alienate everyone
- The Productivity Commission Warns Against Patent Maximalism, Which is Where China (SIPO) is Heading Along With EPO
In defiance of common sense and everything that public officials or academics keep saying (European, Australian, American), China's SIPO and Europe's EPO want us to believe that when it comes to patents it's "the more, the merrier"
- Technical Failure of the European Patent Office (EPO) a Growing Cause for Concern
The problem associated with Battistelli's strategy of increasing so-called 'production' by granting in haste everything on the shelf is quickly being grasped by patent professionals (outside EPO), not just patent examiners (inside EPO)
- Links 5/1/2017: Inkscape 0.92, GNU Sed 4.3
Links for the day
- Links 4/1/2017: Cutelyst 1.2.0 and Lumina 1.2 Desktop Released
Links for the day
- Financial Giants Will Attempt to Dominate or Control Bitcoin, Blockchain and Other Disruptive Free Software Using Software Patents
Free/Open Source software in the currency and trading world promised to emancipate us from the yoke of banking conglomerates, but a gold rush for software patents threatens to jeopardise any meaningful change or progress
- New Article From Heise Explains Erosion of Patent Quality at the European Patent Office (EPO)
To nobody's surprise, the past half a decade saw accelerating demise in quality of European Patents (EPs) and it is the fault of Battistelli's notorious policies
- Insensitivity at the EPO’s Management – Part V: Suspension of Salary and Unfair Trials
One of the lesser-publicised cases of EPO witch-hunting, wherein a member of staff is denied a salary "without any notification"
- Links 3/1/2017: Microsoft Imposing TPM2 on Linux, ASUS Bringing Out Android Phones
Links for the day
- Links 2/1/2017: Neptune 4.5.3 Release, Netrunner Desktop 17.01 Released
Links for the day
- Teaser: Corruption Indictments Brought Against Vice-President of the European Patent Office (EPO)
New trouble for Željko Topić in Strasbourg, making it yet another EPO Vice-President who is on shaky grounds and paving the way to managerial collapse/avalanche at the EPO
- 365 Days Later, German Justice Minister Heiko Maas Remains Silent and Thus Complicit in EPO Abuses on German Soil
The utter lack of participation, involvement or even intervention by German authorities serve to confirm that the government of Germany is very much complicit in the EPO's abuses, by refusing to do anything to stop them
- Battistelli's Idea of 'Independent' 'External' 'Social' 'Study' is Something to BUY From Notorious Firm PwC
The sham which is the so-called 'social' 'study' as explained by the Central Staff Committee last year, well before the results came out
- Europe Should Listen to SMEs Regarding the UPC, as Battistelli, Team UPC and the Select Committee Lie About It
Another example of UPC promotion from within the EPO (a committee dedicated to UPC promotion), in spite of everything we know about opposition to the UPC from small businesses (not the imaginary ones which Team UPC claims to speak 'on behalf' of)
- Video: French State Secretary for Digital Economy Speaks Out Against Benoît Battistelli at Battistelli's PR Event
Uploaded by SUEPO earlier today was the above video, which shows how last year's party (actually 2015) was spoiled for Battistelli by the French State Secretary for Digital Economy, Axelle Lemaire, echoing the French government's concern about union busting etc. at the EPO (only to be rudely censored by Battistelli's 'media partner')
- When EPO Vice-President, Who Will Resign Soon, Made a Mockery of the EPO
Leaked letter from Willy Minnoye/management to the people who are supposed to oversee EPO management
- No Separation of Powers or Justice at the EPO: Reign of Terror by Battistelli Explained in Letter to the Administrative Council
In violation of international labour laws, Team Battistelli marches on and engages in a union-busting race against the clock, relying on immunity to keep this gravy train rolling before an inevitable crash
- FFPE-EPO is a Zombie (if Not Dead) Yellow Union Whose Only de Facto Purpose Has Been Attacking the EPO's Staff Union
A new year's reminder that the EPO has only one legitimate union, the Staff Union of the EPO (SUEPO), whereas FFPE-EPO serves virtually no purpose other than to attack SUEPO, more so after signing a deal with the devil (Battistelli)
- EPO Select Committee is Wrong About the Unitary Patent (UPC)
The UPC is neither desirable nor practical, especially now that the EPO lowers patent quality; but does the Select Committee understand that?
- Links 1/1/2017: KDE Plasma 5.9 Coming, PelicanHPC 4.1
Links for the day
- 2016: The Year EPO Staff Went on Strike, Possibly “Biggest Ever Strike in the History of the EPO.”
A look back at a key event inside the EPO, which marked somewhat of a breaking point for Team Battistelli
- Open EPO Letter Bemoans Battistelli's Antisocial Autocracy Disguised/Camouflaged Under the Misleading Term “Social Democracy”
Orwellian misuse of terms by the EPO, which keeps using the term "social democracy" whilst actually pushing further and further towards a totalitarian regime led by 'King' Battistelli
- EPO's Central Staff Committee Complains About Battistelli's Bodyguards Fetish and Corruption of the Media
Even the EPO's Central Staff Committee (not SUEPO) understands that Battistelli brings waste and disgrace to the Office
- Translation of French Texts About Battistelli and His Awful Perception of Omnipotence
The paradigm of totalitarian control, inability to admit mistakes and tendency to lie all the time is backfiring on the EPO rather than making it stronger
- 2016 in Review and Plans for 2017
A look back and a quick look at the road ahead, as 2016 comes to an end
- Links 31/12/2016: Firefox 52 Improves Privacy, Tizen Comes to Middle East
Links for the day
- Korea's Challenge of Abusive Patents, China's Race to the Bottom, and the United States' Gradual Improvement
An outline of recent stories about patents, where patent quality is key, reflecting upon the population's interests rather than the interests of few very powerful corporations
- German Justice Minister Heiko Maas, Who Flagrantly Ignores Serious EPO Abuses, Helps Battistelli's Agenda ('Reform') With the UPC
The role played by Heiko Maas in the UPC, which would harm businesses and people all across Europe, is becoming clearer and hence his motivation/desire to keep Team Battistelli in tact, in spite of endless abuses on German soil
- Links 30/12/2016: KDE for FreeBSD, Automotive Grade Linux UCB 3.0
Links for the day
- Software Patents Continue to Collapse, But IBM, Watchtroll and David Kappos Continue to Deny and Antagonise It
The latest facts and figures about software patents, compared to the spinmeisters' creed which they profit from (because they are in the litigation business)






















 Content is available under CC-BY-SA
Content is available under CC-BY-SA